- 1elasticsearch 基础介绍及使用 (high-level-client)_elasticsearch highlevelclient
- 2Android基础-SharedPreferences详解_android sharedpreferences
- 3阿里云服务器基础linux指令实验(一到五)_do echo -n “$i: “; cat $i
- 4【C语言】static关键字的使用
- 5SpringBoot整合Dubbo,dubbo提供的服务无法注册进zookeeper的坑_dubbo 注册没报错 但是zookeeper上没有注册信息
- 6如何在Tomcat上部署web项目_tomcat部署web项目
- 7python启动方法_linux开机自启动python程序代码方法
- 8workflow源码解析:http客户端(一)
- 9【自学Docker】Docker cp命令
- 10【转载】Python 修改DataFrame列名的四种方法_8、将以上dataframe的列名改为:英文/中文
windows下ssh、telnet、rdp、smb、ftp暴破事件日志分析_wireshark抓包rdp协议
赞
踩
以下日志来自火绒剑采集的事件、wireshark抓包以及windows自身记录的登录事件,其中ssh、telnet、rdp、smb、ftp都是使用的默认端口,只有默认端口wireshark才能显示相应的protocol,因为应用层协议是通过端口号识别的,如果修改端口号,wireshark不会显示相应的protocol。
rdp暴破,被暴破机器上会向攻击机返回带有3389端口的数据,但攻击机用的端口是随机的。Wireshark在被暴破机器上抓包,能看到rdp协议。
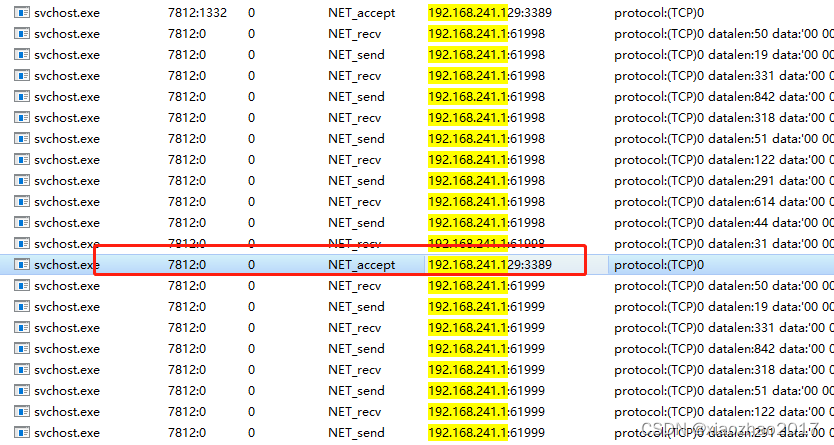


日志
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Microsoft-Windows-Security-Auditing" Guid="{54849625-5478-4994-a5ba-3e3b0328c30d}" />
<EventID>4625</EventID>
<Version>0</Version>
<Level>0</Level>
<Task>12544</Task>
<Opcode>0</Opcode>
<Keywords>0x8010000000000000</Keywords>
<TimeCreated SystemTime="2022-12-15T06:29:15.3988176Z" />
<EventRecordID>17399</EventRecordID>
<Correlation ActivityID="{e5085619-1031-0001-a556-08e53110d901}" />
<Execution ProcessID="704" ThreadID="476" />
<Channel>Security</Channel>
<Computer>DESKTOP-IFP1LHO</Computer>
<Security />
</System>
<EventData>
<Data Name="SubjectUserSid">S-1-0-0</Data>
<Data Name="SubjectUserName">-</Data>
<Data Name="SubjectDomainName">-</Data>
<Data Name="SubjectLogonId">0x0</Data>
<Data Name="TargetUserSid">S-1-0-0</Data>
<Data Name="TargetUserName">44444444</Data>
<Data Name="TargetDomainName">
</Data>
<Data Name="Status">0xc000006d</Data>
<Data Name="FailureReason">%%2313</Data>
<Data Name="SubStatus">0xc0000064</Data>
<Data Name="LogonType">3</Data>
<Data Name="LogonProcessName">NtLmSsp </Data>
<Data Name="AuthenticationPackageName">NTLM</Data>
<Data Name="WorkstationName">DESKTOP-QMONA1D</Data>
<Data Name="TransmittedServices">-</Data>
<Data Name="LmPackageName">-</Data>
<Data Name="KeyLength">0</Data>
<Data Name="ProcessId">0x0</Data>
<Data Name="ProcessName">-</Data>
<Data Name="IpAddress">192.168.241.1</Data>
<Data Name="IpPort">0</Data>
</EventData>
</Event>
Hydar暴破ftp,被暴破机上的登录失败日志,登录方式为8,processname为Advapi 。
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Microsoft-Windows-Security-Auditing" Guid="{54849625-5478-4994-a5ba-3e3b0328c30d}" />
<EventID>4625</EventID>
<Version>0</Version>
<Level>0</Level>
<Task>12544</Task>
<Opcode>0</Opcode>
<Keywords>0x8010000000000000</Keywords>
<TimeCreated SystemTime="2022-12-15T03:50:21.1626073Z" />
<EventRecordID>11879</EventRecordID>
<Correlation ActivityID="{e5085619-1031-0001-a556-08e53110d901}" />
<Execution ProcessID="704" ThreadID="6812" />
<Channel>Security</Channel>
<Computer>DESKTOP-IFP1LHO</Computer>
<Security />
</System>
<EventData>
<Data Name="SubjectUserSid">S-1-5-18</Data>
<Data Name="SubjectUserName">DESKTOP-IFP1LHO$</Data>
<Data Name="SubjectDomainName">WORKGROUP</Data>
<Data Name="SubjectLogonId">0x3e7</Data>
<Data Name="TargetUserSid">S-1-0-0</Data>
<Data Name="TargetUserName">11111111</Data>
<Data Name="TargetDomainName">
</Data>
<Data Name="Status">0xc000006d</Data>
<Data Name="FailureReason">%%2313</Data>
<Data Name="SubStatus">0xc0000064</Data>
<Data Name="LogonType">8</Data>
<Data Name="LogonProcessName">Advapi </Data>
<Data Name="AuthenticationPackageName">MICROSOFT_AUTHENTICATION_PACKAGE_V1_0</Data>
<Data Name="WorkstationName">DESKTOP-IFP1LHO</Data>
<Data Name="TransmittedServices">-</Data>
<Data Name="LmPackageName">-</Data>
<Data Name="KeyLength">0</Data>
<Data Name="ProcessId">0x804</Data>
<Data Name="ProcessName">C:\Windows\System32\svchost.exe</Data>
<Data Name="IpAddress">-</Data>
<Data Name="IpPort">-</Data>
</EventData>
</Event>
Wireshark抓包,能看到有ftp协议
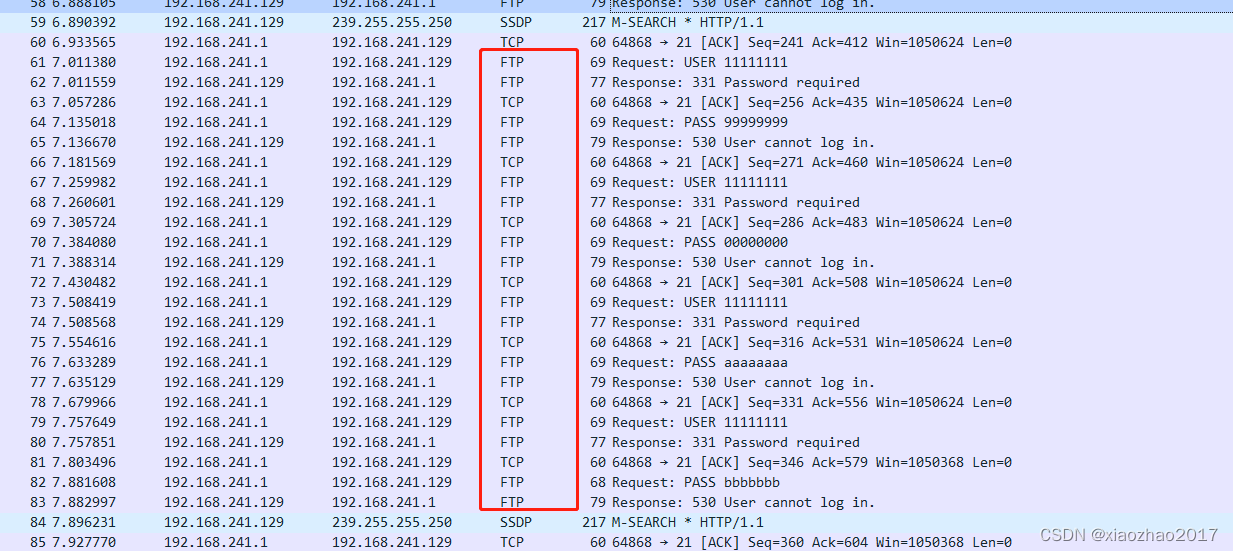
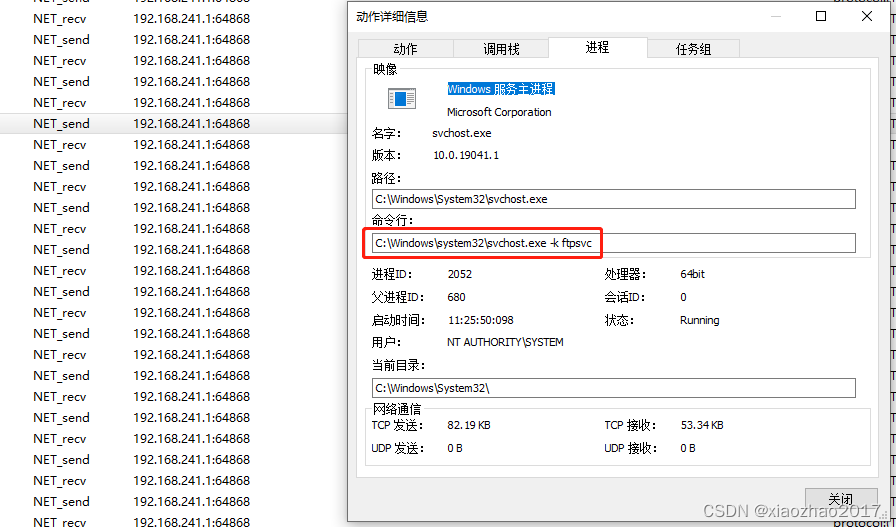
火绒剑网络事件中,可以看到svchost带的参数有ftpsvc
Hydra暴破smb,wireshark抓包可以看到smb协议。
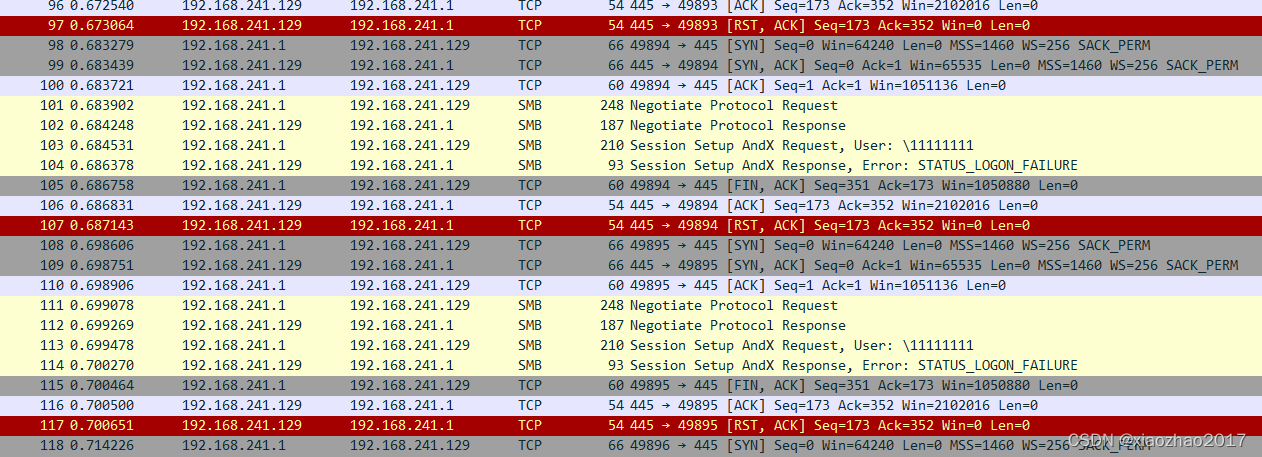
命令行为空

日志
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Microsoft-Windows-Security-Auditing" Guid="{54849625-5478-4994-a5ba-3e3b0328c30d}" />
<EventID>4625</EventID>
<Version>0</Version>
<Level>0</Level>
<Task>12544</Task>
<Opcode>0</Opcode>
<Keywords>0x8010000000000000</Keywords>
<TimeCreated SystemTime="2022-12-15T04:10:55.8872452Z" />
<EventRecordID>15882</EventRecordID>
<Correlation ActivityID="{e5085619-1031-0001-a556-08e53110d901}" />
<Execution ProcessID="704" ThreadID="7088" />
<Channel>Security</Channel>
<Computer>DESKTOP-IFP1LHO</Computer>
<Security />
</System>
<EventData>
<Data Name="SubjectUserSid">S-1-0-0</Data>
<Data Name="SubjectUserName">-</Data>
<Data Name="SubjectDomainName">-</Data>
<Data Name="SubjectLogonId">0x0</Data>
<Data Name="TargetUserSid">S-1-0-0</Data>
<Data Name="TargetUserName">zzzzzzzz</Data>
<Data Name="TargetDomainName">
</Data>
<Data Name="Status">0xc000006d</Data>
<Data Name="FailureReason">%%2313</Data>
<Data Name="SubStatus">0xc0000064</Data>
<Data Name="LogonType">3</Data>
<Data Name="LogonProcessName">NtLmSsp </Data>
<Data Name="AuthenticationPackageName">NTLM</Data>
<Data Name="WorkstationName">\\192.168.241.1</Data>
<Data Name="TransmittedServices">-</Data>
<Data Name="LmPackageName">-</Data>
<Data Name="KeyLength">0</Data>
<Data Name="ProcessId">0x0</Data>
<Data Name="ProcessName">-</Data>
<Data Name="IpAddress">192.168.241.1</Data>
<Data Name="IpPort">51211</Data>
</EventData>
</Event>
Hydra暴破Ssh,登录日志及抓包可以看到有ssh协议的包
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Microsoft-Windows-Security-Auditing" Guid="{54849625-5478-4994-a5ba-3e3b0328c30d}" />
<EventID>4625</EventID>
<Version>0</Version>
<Level>0</Level>
<Task>12544</Task>
<Opcode>0</Opcode>
<Keywords>0x8010000000000000</Keywords>
<TimeCreated SystemTime="2022-12-16T07:05:06.9861163Z" />
<EventRecordID>19503</EventRecordID>
<Correlation ActivityID="{e5085619-1031-0001-a556-08e53110d901}" />
<Execution ProcessID="704" ThreadID="780" />
<Channel>Security</Channel>
<Computer>DESKTOP-IFP1LHO</Computer>
<Security />
</System>
<EventData>
<Data Name="SubjectUserSid">S-1-5-18</Data>
<Data Name="SubjectUserName">DESKTOP-IFP1LHO$</Data>
<Data Name="SubjectDomainName">WORKGROUP</Data>
<Data Name="SubjectLogonId">0x3e7</Data>
<Data Name="TargetUserSid">S-1-0-0</Data>
<Data Name="TargetUserName">NOUSER</Data>
<Data Name="TargetDomainName">DESKTOP-IFP1LHO</Data>
<Data Name="Status">0xc000006d</Data>
<Data Name="FailureReason">%%2313</Data>
<Data Name="SubStatus">0xc0000064</Data>
<Data Name="LogonType">8</Data>
<Data Name="LogonProcessName">Advapi </Data>
<Data Name="AuthenticationPackageName">Negotiate</Data>
<Data Name="WorkstationName">DESKTOP-IFP1LHO</Data>
<Data Name="TransmittedServices">-</Data>
<Data Name="LmPackageName">-</Data>
<Data Name="KeyLength">0</Data>
<Data Name="ProcessId">0x1c38</Data>
<Data Name="ProcessName">C:\Windows\System32\OpenSSH\sshd.exe</Data>
<Data Name="IpAddress">-</Data>
<Data Name="IpPort">-</Data>
</EventData>
</Event>

火绒数据可以看到命令行中有sshd.exe。

HYDRA暴破telnet,火绒可以看到网络事件中命令行为tlntsvr.exe

登录日志中,登录方式为2,进程为Advapi
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Microsoft-Windows-Security-Auditing" Guid="{54849625-5478-4994-A5BA-3E3B0328C30D}" />
<EventID>4625</EventID>
<Version>0</Version>
<Level>0</Level>
<Task>12544</Task>
<Opcode>0</Opcode>
<Keywords>0x8010000000000000</Keywords>
<TimeCreated SystemTime="2022-12-15T08:45:49.567746800Z" />
<EventRecordID>788</EventRecordID>
<Correlation />
<Execution ProcessID="460" ThreadID="3600" />
<Channel>Security</Channel>
<Computer>WIN-FILDP297CD8</Computer>
<Security />
</System>
<EventData>
<Data Name="SubjectUserSid">S-1-5-19</Data>
<Data Name="SubjectUserName">LOCAL SERVICE</Data>
<Data Name="SubjectDomainName">NT AUTHORITY</Data>
<Data Name="SubjectLogonId">0x3e5</Data>
<Data Name="TargetUserSid">S-1-0-0</Data>
<Data Name="TargetUserName">22222222</Data>
<Data Name="TargetDomainName">WIN-FILDP297CD8</Data>
<Data Name="Status">0xc000006d</Data>
<Data Name="FailureReason">%%2313</Data>
<Data Name="SubStatus">0xc0000064</Data>
<Data Name="LogonType">2</Data>
<Data Name="LogonProcessName">Advapi </Data>
<Data Name="AuthenticationPackageName">Negotiate</Data>
<Data Name="WorkstationName">WIN-FILDP297CD8</Data>
<Data Name="TransmittedServices">-</Data>
<Data Name="LmPackageName">-</Data>
<Data Name="KeyLength">0</Data>
<Data Name="ProcessId">0xdd4</Data>
<Data Name="ProcessName">C:\Windows\System32\tlntsess.exe</Data>
<Data Name="IpAddress">-</Data>
<Data Name="IpPort">-</Data>
</EventData>
</Event>



