- 1python编程游戏代码大全,python简单的小游戏代码_python小游戏代码
- 2时间序列预测模型实战案例(二)(Holt-Winter)(Python)结合K-折交叉验证进行时间序列预测实现企业级预测精度(包括运行代码以及代码讲解)_holt-winters
- 3❀工信工实验参考——《VHDL实验2——数码管及分频器》_数码管显示vhdl
- 4接口测试流程、测试点和测试工具_接口联调测试
- 5基于区块链/Hyperledger Fabric的商品交易溯源系统搭建步骤_在hyperledger fabric设计一个交易系统
- 6【HarmonyOS】鸿蒙操作系统架构
- 7使用X2Keyarch迁移CentOS至浪潮信息KeyarchOS体验
- 8web3 React dapp项目通过事件从区块链中拿到 已取消 已完成 和所有的订单数据 并存入redux中
- 9DNS域名解析,以及A、AAAA、CNAME、MX、NS、TXT、SRV、SOA、PTR说明_a记录和aaaa记录
- 10图像处理:Tiler制作你的专属卡通头像和LOGO(圣诞特别篇)_像素卡通头像制作
Spring Security 0auth2 认证服务器和资源服务器实现_preauthenticatedauthenticationprovider
赞
踩
一,OAuth2开放授权协议/标准
OAuth(开放授权)是⼀个开放协议/标准,允许⽤户授权第三⽅应⽤访问他们存储在另外的服务提供者
上的信息,⽽不需要将⽤户名和密码提供给第三⽅应⽤或分享他们数据的所有内容。
允许⽤户授权第三⽅应⽤访问他们存储在另外的服务提供者上的信息,⽽不需要将⽤户名和密码提供给
第三⽅应⽤或分享他们数据的所有内容
client_id :客户端id(QQ最终相当于⼀个认证授权服务器,木瓜餐饮就相当于⼀个客户端了,所以会
给 ⼀个客户端id),相当于账号
secret:相当于密码
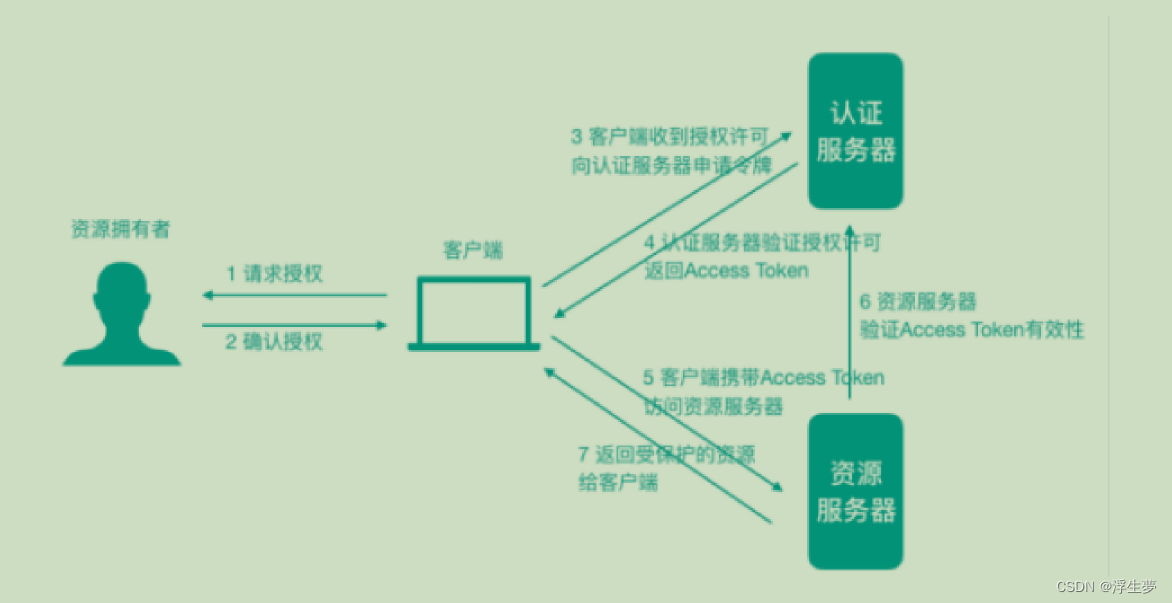
资源所有者(Resource Owner):可以理解为⽤户⾃⼰
客户端(Client):我们想登陆的⽹站或应⽤,⽐如淘宝
认证服务器(Authorization Server):可以理解为微信或者QQ
资源服务器(Resource Server):可以理解为微信或者QQ
二、什么情况下需要使用OAuth2
第三⽅授权登录的场景:⽐如,我们经常登录⼀些⽹站或者应⽤的时候,可以选择使⽤第三⽅授权登录
的⽅式,⽐如:微信授权登录、QQ授权登录、微博授权登录等,这是典型的 OAuth2 使⽤场景。
单点登录的场景:如果项⽬中有很多微服务或者公司内部有很多服务,可以专⻔做⼀个认证中⼼(充当
认证平台⻆⾊),所有的服务都要到这个认证中⼼做认证,只做⼀次登录,就可以在多个授权范围内的
服务中⾃由串⾏。
OAuth2的颁发Token授权⽅式
1)授权码(authorization-code)2)密码式(password)提供⽤户名+密码换取token令牌
3)隐藏式(implicit)
4)客户端凭证(client credentials)
授权码模式使⽤到了回调地址,是最复杂的授权⽅式,微博、微信、QQ等第三⽅登录就是这种模式。我
们说接⼝对接中常使⽤的password密码模式(提供⽤户名+密码换取token)。
三、Spring Cloud OAuth2 + JWT 实现
Spring Cloud OAuth2 是 Spring Cloud 体系对OAuth2协议的实现,可以⽤来做多个微服务的统⼀认证
(验证身份合法性)授权(验证权限)。通过向OAuth2服务(统⼀认证授权服务)发送某个类型的
grant_type进⾏集中认证和授权,从⽽获得access_token(访问令牌),⽽这个token是受其他微服务
信任的。
注意:使⽤OAuth2解决问题的本质是,引⼊了⼀个认证授权层,认证授权层连接了资源的拥有者,在
授权层⾥⾯,资源的拥有者可以给第三⽅应⽤授权去访问我们的某些受保护资源
1,授权服务器
1,pom 导入
2,资源服务器
pom
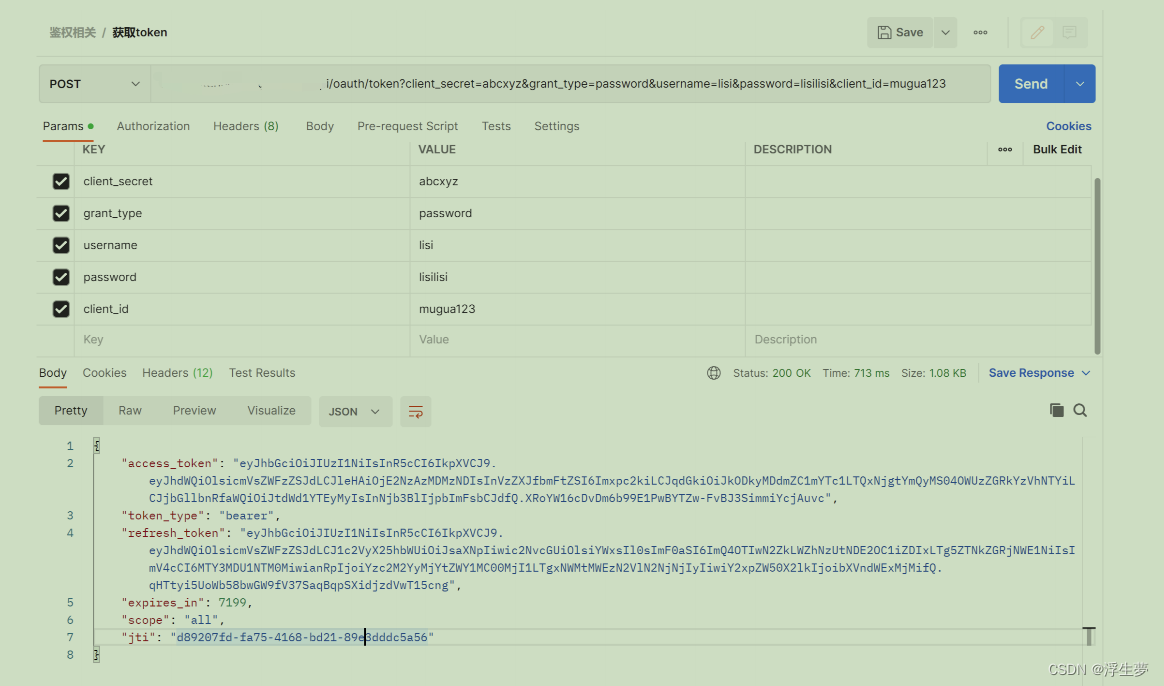
- 获取token AND 刷新token
- http://地址:端口/oauth/token?
- client_secret=abcxyz&grant_type=password&username=muguauser&password=iuxyzds&client_id=mugua123
-
- 获取token携带的参数
- client_id:客户端id
- password:密码客户单密码
- grant_type:指定使⽤哪种颁发类型,password
- username:⽤户名
- password:密码
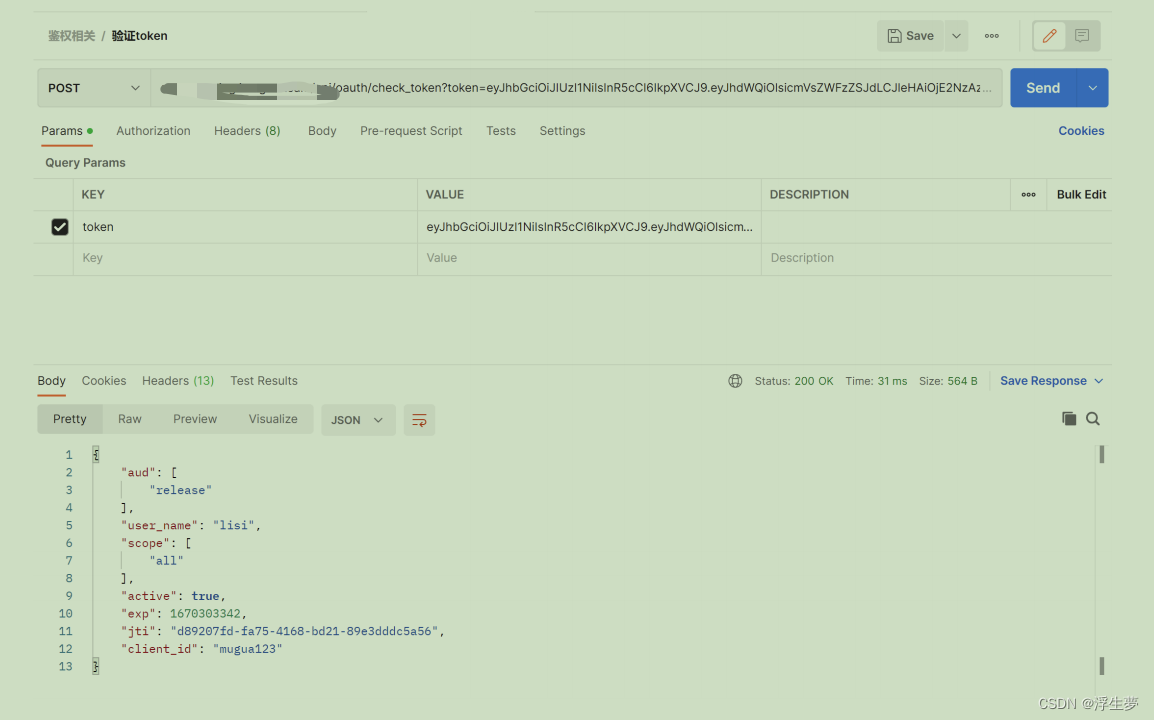
三、验证
刷新token
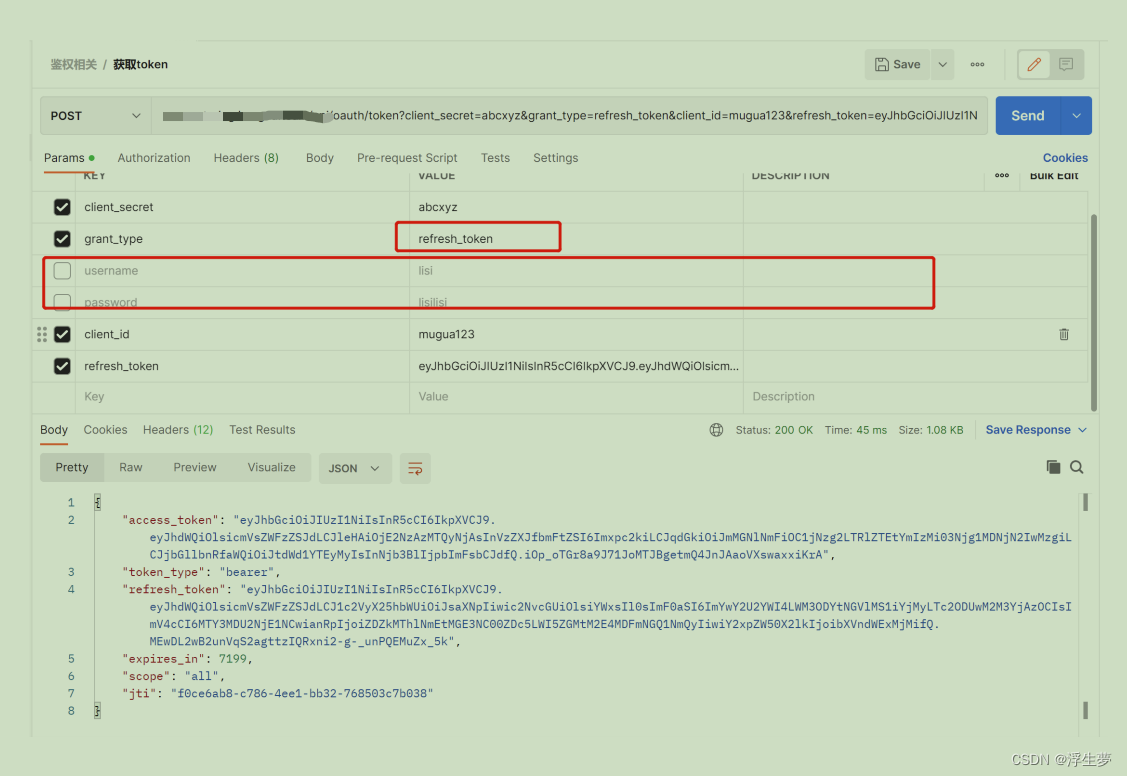
这里是没有指定用户名和密码的,并把grant_type改为了refresh_token
验证token