热门标签
热门文章
- 1Android Sensor HAL层分析_sensor hal service
- 2git提交后冲突的解决办法_git push冲突怎么解决
- 3软件测试最新一个资深测试工程师面试一来就问我这些题目_三十位真实乱口述(3),2024年最新腾讯软件测试面经
- 4Typora+PicGo+Gitee环境搭建(windows)(需要的软件下载打包在一起了)_picgo设置gitee
- 5基于AI的智能聊天机器人ChatTTS,自然语言处理和机器学习技术的完美结合!_基于tts的智能聊天机器人
- 6mysql set 命令的用法_mysql命令用法复习笔记
- 7数据库---索引和事务_事务,索引,主键
- 8LLM漫谈(三)| 使用Chainlit和LangChain构建文档问答的LLM应用程序
- 9汽车软件开发中如何应用敏捷框架_汽车软件敏捷开发,2024必看-Golang高级面试题总结_敏捷开发 汽车软件
- 10实现基本数据结构之链表_数组模拟栈效率
当前位置: article > 正文
Linux安全基线检查--centos7_centos7基线脚本
作者:Guff_9hys | 2024-07-01 04:18:17
赞
踩
centos7基线脚本
版权声明:本文为CSDN博主「淡定波007」的原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接及本声明。 原文链接:https://blog.csdn.net/qq_28721869/article/details/114682119
Linux安全基线检查
以下脚本针对于centos7系统。
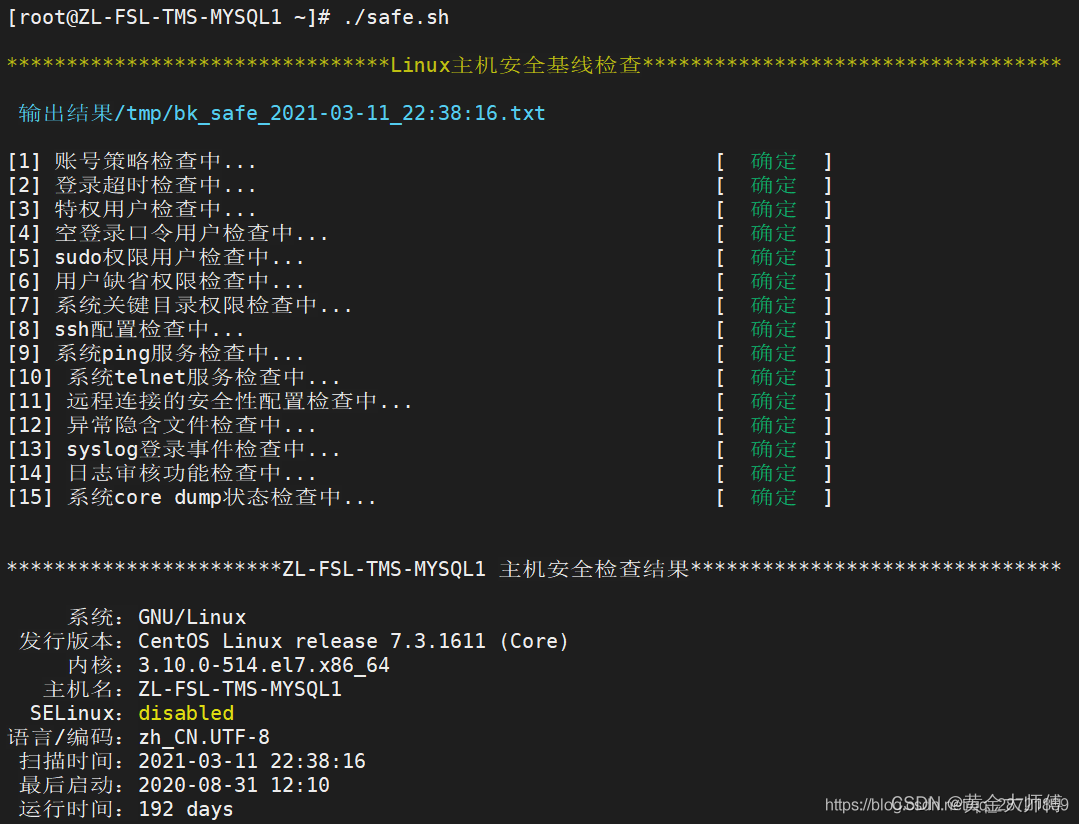
#! /bin/bash ###################################### # linux主机安全基线检查 # copyright by hwb # date:2020-12-17 ###################################### scanner_time=`date '+%Y-%m-%d_%H:%M:%S'` scanner_log="/tmp/checkResult_${scanner_time}.log" #调用函数库 [ -f /etc/init.d/functions ] && source /etc/init.d/functions export PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin:/root/bin source /etc/profile #Require root to run this script. [ $(id -u) -gt 0 ] && echo "请用root用户执行此脚本!" && exit 1 #报错日志记录 [ -f ${scanner_log} ] || touch ${scanner_log} function getSystemStatus(){ echo "" if [ -e /etc/sysconfig/i18n ];then default_LANG="$(grep "LANG=" /etc/sysconfig/i18n | grep -v "^#" | awk -F '"' '{print $2}')" else default_LANG=$LANG fi export LANG="en_US.UTF-8" Release=$(cat /etc/redhat-release 2>/dev/null) Kernel=$(uname -r) OS=$(uname -o) Hostname=$(uname -n) SELinux=$(/usr/sbin/sestatus | grep "SELinux status: " | awk '{print $3}') LastReboot=$(who -b | awk '{print $3,$4}') uptime=$(uptime | sed 's/.*up \([^,]*\), .*/\1/') echo " 系统:$OS" echo " 发行版本:$Release" echo " 内核:$Kernel" echo " 主机名:$Hostname" echo " SELinux:$SELinux" echo "语言/编码:$default_LANG" echo " 扫描时间:$(date +'%F %T')" echo " 最后启动:$LastReboot" echo " 运行时间:$uptime" export LANG="$default_LANG" } bk_safe(){ echo "" echo -e "\033[33m********************************Linux主机安全基线检查***********************************\033[0m" echo "" echo -e "\033[36m 输出结果"/tmp/bk_safe_$scanner_time.txt" \033[0m" echo "" echo "" >> ${scanner_log} echo "***********************`hostname -s` 主机安全检查结果*******************************" >> ${scanner_log} getSystemStatus >> ${scanner_log} echo "" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} echo "`hostname -s`账号策略检查结果" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} action "[1] 账号策略检查中..." /bin/true passmax=`cat /etc/login.defs | grep PASS_MAX_DAYS | grep -v ^# | awk '{print $2}'` passmin=`cat /etc/login.defs | grep PASS_MIN_DAYS | grep -v ^# | awk '{print $2}'` passlen=`cat /etc/login.defs | grep PASS_MIN_LEN | grep -v ^# | awk '{print $2}'` passage=`cat /etc/login.defs | grep PASS_WARN_AGE | grep -v ^# | awk '{print $2}'` if [ $passmax -le 90 -a $passmax -gt 0 ];then echo "[Y] 口令生存周期为${passmax}天,符合要求" >> ${scanner_log} else echo "[N] 口令生存周期为${passmax}天,不符合要求,建议设置不大于90天" >> ${scanner_log} fi if [ $passmin -ge 6 ];then echo "[Y] 口令更改最小时间间隔为${passmin}天,符合要求" >> ${scanner_log} else echo "[N] 口令更改最小时间间隔为${passmin}天,不符合要求,建议设置大于等于6天" >> ${scanner_log} fi if [ $passlen -ge 8 ];then echo "[Y] 口令最小长度为${passlen},符合要求" >> ${scanner_log} else echo "[N] 口令最小长度为${passlen},不符合要求,建议设置最小长度大于等于8" >> ${scanner_log} fi if [ $passage -ge 30 -a $passage -lt $passmax ];then echo "[Y] 口令过期警告时间天数为${passage},符合要求" >> ${scanner_log} else echo "[N] 口令过期警告时间天数为${passage},不符合要求,建议设置大于等于30并小于口令生存周期" >> ${scanner_log} fi echo "" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} echo "`hostname -s`登录超时检查结果" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} action "[2] 登录超时检查中..." /bin/true checkTimeout=$(cat /etc/profile | grep TMOUT | awk -F[=] '{print $2}') if [ $? -eq 0 ];then TMOUT=`cat /etc/profile | grep TMOUT | awk -F[=] '{print $2}'` if [ $TMOUT -le 600 -a $TMOUT -ge 10 ];then echo "[Y] 账号超时时间${TMOUT}秒,符合要求" >> ${scanner_log} else echo "[N] 账号超时时间${TMOUT}秒,不符合要求,建议设置小于600秒">> ${scanner_log} fi else echo "[N] 账号超时不存在自动注销,不符合要求,建议设置小于600秒" >> ${scanner_log} fi echo "" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} echo "`hostname -s`特权用户检查结果" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} action "[3] 特权用户检查中..." /bin/true UIDS=`awk -F[:] 'NR!=1{print $3}' /etc/passwd` flag=0 for i in $UIDS do if [ $i = 0 ];then flag=1 fi done if [ $flag != 1 ];then echo "[Y] 不存在root账号外的UID为0的异常用户" >> ${scanner_log} else echo "[N] 存在非root但UID为0的异常用户,请立刻进行排查" >> ${scanner_log} fi echo "" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} echo "`hostname -s`空登录口令用户检查结果" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} action "[4] 空登录口令用户检查中..." /bin/true userlist=`awk -F: 'length($2)==0 {print $1}' /etc/shadow` [ ! $userlist ] && echo "[Y] 不存在空登录口令用户" >> ${scanner_log} for i in $userlist do echo "[N] $i登录密码为空,不符合要求,建议为该用户设置密码!" >> ${scanner_log} done echo "" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} echo "`hostname -s`具有sudo权限用户检查结果" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} action "[5] sudo权限用户检查中..." /bin/true sudolist=`cat /etc/sudoers |grep -v '^#' |grep -v Defaults| grep -v '^$'` echo "$sudolist" >> ${scanner_log} echo "" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} echo "`hostname -s`用户缺省权限检查结果" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} action "[6] 用户缺省权限检查中..." /bin/true umask1=`cat /etc/profile | grep umask | grep -v ^# | awk '{print $2}'` umask2=`cat /etc/csh.cshrc | grep umask | grep -v ^# | awk '{print $2}'` umask3=`cat /etc/bashrc | grep umask | grep -v ^# | awk 'NR!=1{print $2}'` flags=0 for i in $umask1 do if [ $i != "027" ];then echo "[N] /etc/profile文件中所所设置的umask为${i},不符合要求,建议设置为027" >> ${scanner_log} flags=1 break fi done if [ $flags == 0 ];then echo "[Y] /etc/profile文件中所设置的umask为${i},符合要求" >> ${scanner_log} fi flags=0 for i in $umask2 do if [ $i != "027" ];then echo "[N] /etc/csh.cshrc文件中所所设置的umask为${i},不符合要求,建议设置为027" >> ${scanner_log} flags=1 break fi done if [ $flags == 0 ];then echo "[Y] /etc/csh.cshrc文件中所设置的umask为${i},符合要求" >> ${scanner_log} fi flags=0 for i in $umask3 do if [ $i != "027" ];then echo "[N] /etc/bashrc文件中所设置的umask为${i},不符合要求,建议设置为027" >> ${scanner_log} flags=1 break fi done if [ $flags == 0 ];then echo "[Y] /etc/bashrc文件中所设置的umask为${i},符合要求" >> ${scanner_log} fi echo "" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} echo "`hostname -s`系统关键目录权限检查结果" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} action "[7] 系统关键目录权限检查中..." /bin/true file1=`ls -l /etc/passwd | awk '{print $1}'` file2=`ls -l /etc/shadow | awk '{print $1}'` file3=`ls -l /etc/group | awk '{print $1}'` file4=`ls -l /etc/securetty | awk '{print $1}'` file5=`ls -l /etc/services | awk '{print $1}'` #检测文件权限为400的文件 if [ $file2 = "-r--------" ];then echo "[Y] /etc/shadow文件权限为400,符合要求" >> ${scanner_log} else echo "[N] /etc/shadow文件权限不为400,不符合要求,建议设置权限为400" >> ${scanner_log} fi #检测文件权限为600的文件 if [ $file4 = "-rw-------" ];then echo "[Y] /etc/security文件权限为600,符合要求" >> ${scanner_log} else echo "[N] /etc/security文件权限不为600,不符合要求,建议设置权限为600" >> ${scanner_log} fi #检测文件权限为644的文件 if [ $file1 = "-rw-r--r--" ];then echo "[Y] /etc/passwd文件权限为644,符合要求" >> ${scanner_log} else echo "[N] /etc/passwd文件权限不为644,不符合要求,建议设置权限为644" >> ${scanner_log} fi if [ $file5 = "-rw-r--r--" ];then echo "[Y] /etc/services文件权限为644,符合要求" >> ${scanner_log} else echo "[N] /etc/services文件权限不为644,不符合要求,建议设置权限为644" >> ${scanner_log} fi if [ $file3 = "-rw-r--r--" ];then echo "[Y] /etc/group文件权限为644,符合要求" >> ${scanner_log} else echo "[N] /etc/group文件权限不为644,不符合要求,建议设置权限为644" >> ${scanner_log} fi echo "" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} echo "`hostname -s`SSH配置检查结果" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} action "[8] ssh配置检查中..." /bin/true remoteLogin=$(cat /etc/ssh/sshd_config | grep -v ^# |grep "PermitRootLogin no") if [ $? -eq 0 ];then echo "[Y] 已经设置root不能远程登陆,符合要求" >> ${scanner_log} else echo "[N] 已经设置root能远程登陆,不符合要求,建议/etc/ssh/sshd_config添加PermitRootLogin no参数" >> ${scanner_log} fi echo "" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} echo "`hostname -s`ping服务检查结果" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} action "[9] 系统ping服务检查中..." /bin/true pingd=`cat /proc/sys/net/ipv4/icmp_echo_ignore_all` if [ "$pingd" = "1" ]; then echo "[Y] 服务器已禁ping" >> ${scanner_log} else echo "[N] 服务器未禁ping" >> ${scanner_log} fi echo "" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} echo "`hostname -s`telnet服务检查结果" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} action "[10] 系统telnet服务检查中..." /bin/true telnetd=`rpm -qa|grep telnet | wc -l` if [ $telnetd = "0" ]; then echo "[Y] 系统未安装telnet服务 " >> ${scanner_log} else echo "[N] 检测到安装了telnet服务,不符合要求,建议禁用telnet服务" >> ${scanner_log} fi echo "" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} echo "`hostname -s`远程连接的安全性配置检查结果" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} action "[11] 远程连接的安全性配置检查中..." /bin/true fileNetrc=`find / -xdev -mount -name .netrc -print 2> /dev/null` if [ -z "${fileNetrc}" ];then echo "[Y] 不存在.netrc文件,符合要求" >> ${scanner_log} else echo "[N] 存在.netrc文件,不符合要求" >> ${scanner_log} fi fileRhosts=`find / -xdev -mount -name .rhosts -print 2> /dev/null` if [ -z "$fileRhosts" ];then echo "[Y] 不存在.rhosts文件,符合要求" >> ${scanner_log} else echo "[N] 存在.rhosts文件,不符合要求" >> ${scanner_log} fi echo "" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} echo "`hostname -s`异常隐含文件检查结果" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} action "[12] 异常隐含文件检查中..." /bin/true hideFile=$(find / -xdev -mount \( -name "..*" -o -name "...*" \) 2> /dev/null) if [ -z "${hideFile}" ];then echo "[Y] 不存在隐藏文件,符合要求" >> ${scanner_log} else echo "[N] 存在隐藏文件,建议仔细检查:" >> ${scanner_log} for i in ${hideFile} do echo $i >> ${scanner_log} done fi echo "" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} echo "`hostname -s`syslog登录事件检查结果" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} action "[13] syslog登录事件检查中..." /bin/true if [ -f "/etc/syslog.conf" ];then logFile=$(cat /etc/syslog.conf | grep -V ^# | grep authpriv.*) if [ ! -z "${logFile}" ];then echo "[Y] 存在保存authpirv的日志文件" >> ${scanner_log} else echo "[N] 不存在保存authpirv的日志文件" >> ${scanner_log} fi else echo "[N] 不存在/etc/syslog.conf文件,建议对所有登录事件都记录" >> ${scanner_log} fi echo "" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} echo "`hostname -s`日志审核功能检查结果" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} action "[14] 日志审核功能检查中..." /bin/true auditdStatus=$(service auditd status 2> /dev/null) if [ $? = 0 ];then echo "[Y] 系统日志审核功能已开启,符合要求" >> ${scanner_log} fi if [ $? = 3 ];then echo "[N] 系统日志审核功能已关闭,不符合要求,建议service auditd start开启" >> ${scanner_log} fi echo "" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} echo "`hostname -s`系统core dump状态检查结果" >> ${scanner_log} echo "****************************************************" >> ${scanner_log} action "[15] 系统core dump状态检查中..." /bin/true limitsFile=$(cat /etc/security/limits.conf | grep -V ^# | grep core) if [ $? -eq 0 ];then soft=`cat /etc/security/limits.conf | grep -V ^# | grep core | awk {print $2}` for i in $soft do if [ "$i"x = "soft"x ];then echo "[Y] * soft core 0 已经设置" >> ${scanner_log} fi if [ "$i"x = "hard"x ];then echo "[Y] * hard core 0 已经设置" >> ${scanner_log} fi done else echo "[N] 没有设置core,建议在/etc/security/limits.conf中添加* soft core 0和* hard core 0" >> ${scanner_log} fi echo "" cat ${scanner_log} echo "" } bk_safe
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
- 166
- 167
- 168
- 169
- 170
- 171
- 172
- 173
- 174
- 175
- 176
- 177
- 178
- 179
- 180
- 181
- 182
- 183
- 184
- 185
- 186
- 187
- 188
- 189
- 190
- 191
- 192
- 193
- 194
- 195
- 196
- 197
- 198
- 199
- 200
- 201
- 202
- 203
- 204
- 205
- 206
- 207
- 208
- 209
- 210
- 211
- 212
- 213
- 214
- 215
- 216
- 217
- 218
- 219
- 220
- 221
- 222
- 223
- 224
- 225
- 226
- 227
- 228
- 229
- 230
- 231
- 232
- 233
- 234
- 235
- 236
- 237
- 238
- 239
- 240
- 241
- 242
- 243
- 244
- 245
- 246
- 247
- 248
- 249
- 250
- 251
- 252
- 253
- 254
- 255
- 256
- 257
- 258
- 259
- 260
- 261
- 262
- 263
- 264
- 265
- 266
- 267
- 268
- 269
- 270
- 271
- 272
- 273
- 274
- 275
- 276
- 277
- 278
- 279
- 280
- 281
- 282
- 283
- 284
- 285
- 286
- 287
- 288
- 289
- 290
- 291
- 292
- 293
- 294
- 295
- 296
- 297
- 298
- 299
- 300
- 301
- 302
- 303
- 304
- 305
- 306
- 307
- 308
- 309
- 310
- 311
- 312
- 313
- 314
- 315
- 316
- 317
- 318
- 319
- 320
- 321
- 322
- 323
- 324
- 325
- 326
- 327
- 328
- 329
- 330
- 331
- 332
- 333
- 334
- 335
- 336
- 337
- 338
- 339
- 340
- 341
- 342
- 343
- 344
- 345
- 346
- 347
- 348
- 349
- 350
- 351
- 352
- 353
- 354
- 355
- 356
- 357
- 358
- 359
- 360
- 361
- 362
- 363
- 364
- 365
- 366
- 367
- 368
- 369
- 370
- 371
- 372
- 373
- 374
- 375
- 376
- 377
- 378
- 379
- 380
- 381
- 382
- 383
- 384
- 385
- 386
- 387
输出结果

在这里插入图片描述


声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/Guff_9hys/article/detail/775032
推荐阅读
相关标签



