热门标签
热门文章
- 1Request对象及其常用方法_request 那些方法使用到流
- 2linux gpu 测试工具,推荐 7 大 Linux GPU 监控和诊断命令行工具
- 3SVR模型&python应用
- 4鸿蒙软件开发2-1 部分基础知识了解_arkts hap har区别
- 5【备战春招】3月23日美团-第一题-塔子哥的01矩阵
- 6网络&信息安全:nginx漏洞收集(升级至最新版本)_nginx1.2.2 越界写入漏洞
- 7ts&3.0&3.x cocos实现九宫格/跑马灯抽奖_cocoscreator3.x九宫格抽奖
- 8【Unity 学习笔记】规则瓦片和动态瓦片的应用_unity规则瓦片
- 9双口ram存储器_C程序如何存储在RAM存储器中
- 10【深度学习】图像去噪:一种基于流的图像去噪神经网络
当前位置: article > 正文
使用openssl命令行产生密钥对、签发证书[详细]
作者:weixin_40725706 | 2024-03-25 08:37:40
赞
踩
openssl命令
openssl的相关参数
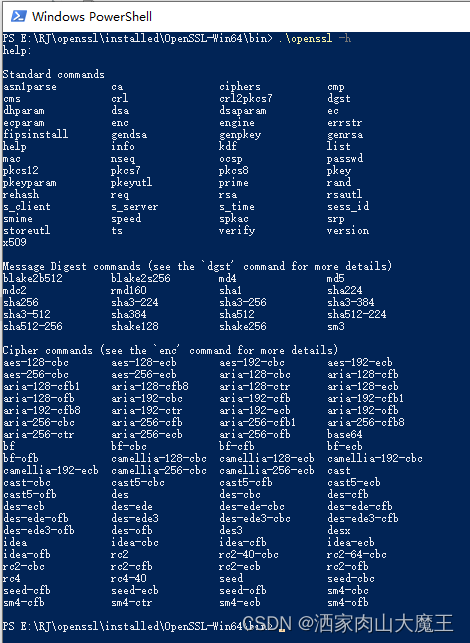
1. 产生密钥对
注意:以下操作命令均在openssl的bin目录内执行。
1.1 RSA密钥对
- # 产生RSA私钥
- openssl genrsa -out rsa_private_key.pem 1024
- # 根据私钥产生公钥
- openssl rsa -in rsa_private_key.pem -pubout -out rsa_public_key.pem
- # 私钥PKCS1转为PKCS8格式
- openssl pkcs8 -topk8 -in rsa_private_key.pem -out pkcs8_rsa_private_key.pem -nocrypt
- # 私钥PKCS8转为PKCS1格式
- openssl rsa -in pkcs8_rsa_private_key.pem -out pkcs1_rsa_private_key.pem
1.2 SM2密钥对
- # 生成SM2密钥参数和私钥
- openssl ecparam -name SM2 -out ec_param.pem -param_enc explicit -genkey
- # 查看私钥信息
- openssl ecparam -in ec_param.pem -text
- # 验证参数
- openssl ecparam -in ec_param.pem -check
- # 将私钥转换为PKCS8编码
- openssl pkcs8 -topk8 -inform PEM -in ec_param.pem -outform PEM -nocrypt -out sm2_private_key_pkcs8.pem
- # 根据私钥产生公钥
- openssl ec -in ec_param.pem -pubout -out sm2_public_key.pem
符合0009规范标准的SM2密钥对
首先看一下0009 SM2密码算法适用规范中定义的SM2公钥:


产生SM2密钥对命令:
- 1)生成SM2私钥
- openssl ecparam -genkey -name SM2 -out SM2PrivateKey.pem
- 2)生成SM2公钥
- openssl ec -in SM2PrivateKey.pem -pubout -out SM2PublicKey.pem
打开SM2公钥文件: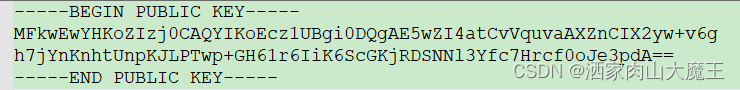
用工具对密钥主体内容转码:

红框内容即符合0009规范定义的SM2公钥结构体(04||X||Y):

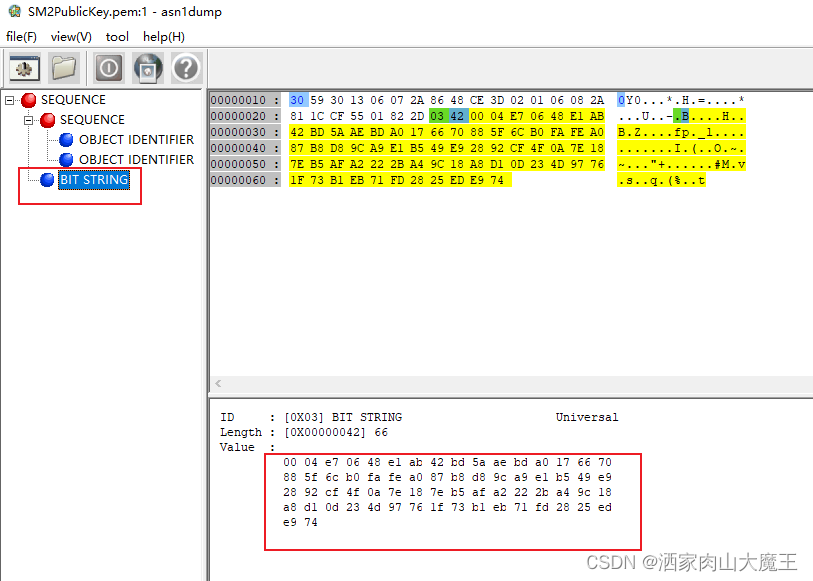
这个公钥内容的前半部分是什么呢?这里我们在asn1View里再看一下:
SM2椭圆曲线OID:
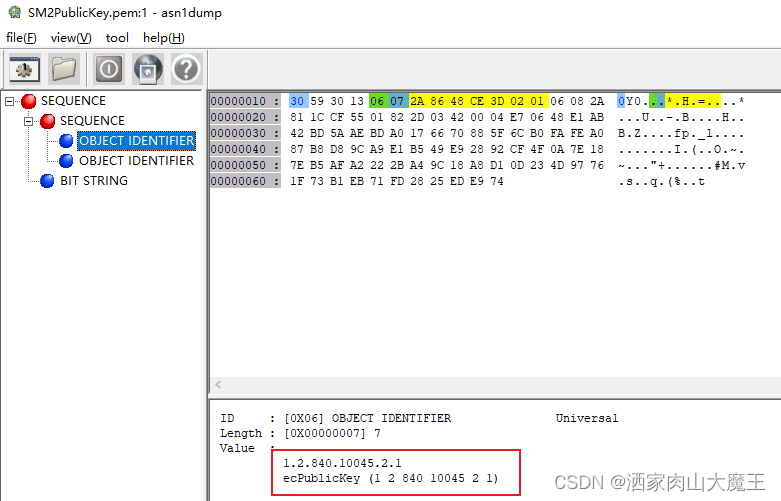
SM2算法标识OID:
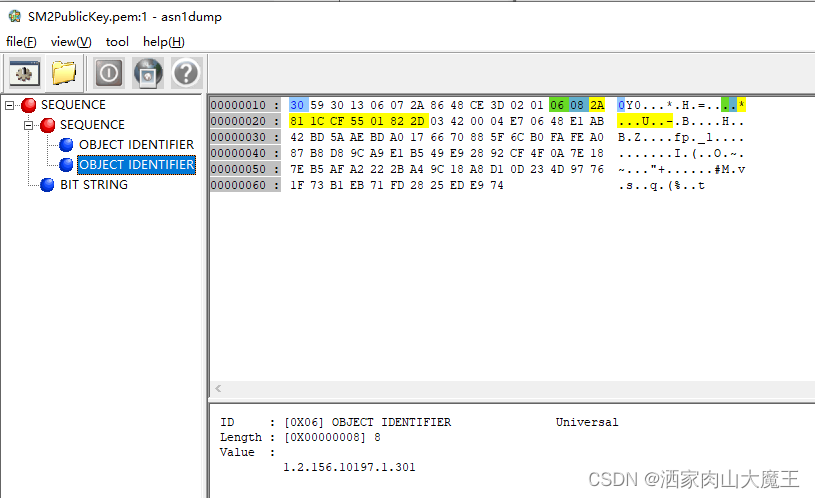
1.3 ECC密钥对
1.3.1 产生SECP256R1曲线的ECC密钥对
注意:openssl产生ECC密钥对时,暂不支持SECP256R1曲线参数,可以使用prime256v1曲线代替
- # 产生ECC私钥(带曲线参数)
- openssl ecparam -genkey -name prime256v1 -param_enc explicit -outform pem -out ec_prime256v1_prikey.pem
- # 产生ECC私钥(不带曲线参数 RFC5915)
- openssl ecparam -genkey -name prime256v1 -param_enc explicit -outform pem -noout -out ec_prime256v1_prikey.pem
- # 显示私钥
- openssl pkey -in ec_prime256v1_prikey.pem -text
- # 产生ECC公钥
- openssl ec -in ec_prime256v1_prikey.pem -pubout -out ec_pubkey.pem
1.3.2 产生SECP256K1曲线的ECC密钥对
- openssl ecparam -genkey -name secp256k1 -param_enc explicit -outform pem -noout -out ec_secp256k1_prikey.pem
-
- openssl ec -in ec_secp256k1_prikey.pem -pubout -out ec_secp256k1_pubkey.pem
-
- openssl req -x509 -new -days 3650 -key ec_secp256k1_prikey.pem -out ec_secp256k1.cer
2. 查看ASN1编码文件
openssl asn1parse -i -in pkcs1.pem
3. 证书相关
- # 产生证书请求文件
- openssl req -new -key rsa_private_key.pem -out rsaCerReq.csr
- # 生成证书
- openssl x509 -req -days 3650 -in rsaCerReq.csr -signkey rsa_private_key.pem -out rsaCert.crt
- # 生成RSA密钥并生成证书
- openssl req -x509 -nodes -newkey rsa:1024 -keyout keyfile.key -out certificate.cer
- # 签名(不带证书)
- openssl smime -sign -md sha1 -binary -nocerts -noattr -in data.txt -out data.txt.signed -outform der -inkey keyfile.key -signer certificate.cer
- # 签名(带证书)
- openssl smime -sign -md sha1 -binary -noattr -in data.txt -out data.txt.signed -outform der -inkey keyfile.key -signer certificate.cer
-
- # 产生ECC证书
- openssl req -x509 -new -days 3650 -key ec_prime256v1_prikey.pem -out ec.cer
4. 签名验签
- # 生成PKCS7签名结构
- openssl smime -sign -md sha1 -binary -noattr -pk7out -in data.txt -out data.txt.signed -outform der -inkey keyfile.key -signer certificate.cer
- # 从PKCS7结构中提取签名值
- dd if=data.txt.signed of=signed-sha1.bin bs=1 skip=$[212+3] count=128
- # 查看签名数据(签名数据最后128字节)
- hexdump -C signed-sha1.bin
- # 解析签名结果(最后一个OCTET STRING即为签名值)
- openssl asn1parse -inform der -in data.txt.signed
- # 从证书中提取公钥
- openssl x509 -inform pem -in certificate.cer -noout -pubkey > pubkey.pem
- # 验证签名(verifyed.bin中为数据的HASH值)
- openssl rsautl -verify -pubin -inkey pubkey.pem < signed-sha1.bin > verifyed.bin
- # 查看验签结果
- openssl asn1parse -inform der -in verifyed.bin
- # 对原文计算HASH
- sha1sum data.txt
- # 对比结果一致
5. CA签发证书
- # 1.初始化目录
- mkdir -p ./myDemo/demoCerts
- touch ./myDemo/index.txt
- echo '02' > ./myDemo/serial
- # 2.生成CA私钥
- openssl ecparam -name SM2 -out ca.pem -param_enc explicit -genkey
- # 3.根据私钥产生公钥
- openssl ec -in ca.pem -pubout -out ca_pub.pem
- # 4.生成CA证书请求文件
- openssl req -new -key ca.pem -out ca.csr
- # 5.生成CA证书
- openssl x509 -req -in ca.csr -signkey ca.pem -days 3650 -out ca.cer
- # 6.CA签发证书
- openssl ca -in my_rsa.csr -cert ca.cer -keyfile ca.pem -out my_rsa.cer
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/weixin_40725706/article/detail/308336
推荐阅读
相关标签


