热门标签
热门文章
- 1python安装nltk
- 2Flink——Flink集群架构及应用程序执行模式_springboot flink 打包到 flink运行
- 3Docker超详细基础教程,快速入门docker首选(万字长文建议收藏)_docker入门教程_首次运行docker
- 4【数据结构之二叉树简介·顺序存储·应用:堆·堆排序·TOPK问题】_二叉树 堆存储
- 5机器学习——线性判别准则(LDA)和线性分类算法(SVM)_svm和lda区别
- 6Android 系统背光设置_android automaticbrightnesscontroller
- 7快速调整毕业论文格式:在Word中使用EndNote插入参考文献_硕士毕业论文参考文献endnote
- 8火车头采集器伪原创【php源码】
- 9ICLR 2022哪篇论文最火?这个「集邮」狂魔放出3400篇大礼包_iclr2022论文合集
- 10利用RCLCPP实现话题的发布与订阅
当前位置: article > 正文
在Ambari上添加Kerberos_ambari 部署 kerberos
作者:你好赵伟 | 2024-07-05 21:03:43
赞
踩
ambari 部署 kerberos
一、准备阶段
1.下载jce并解压
jce下载地址: http://www.oracle.com/technetwork/java/javase/downloads/jce8-download-2133166.html
百度云链接:https://pan.baidu.com/s/1QKQSHLU83xUKBYiRCCgHlg?pwd=cqrd
提取码:cqrd
[root@manager ~]# ls
jce_policy-8.zip
[root@manager ~]# unzip -o -j -q jce_policy-8.zip -d /usr/local/jdk/jre/lib/security/
- 1
- 2
- 3
2.安装krb5
[root@manager ~]# yum install -y krb5-libs krb5-workstation
- 1
3.修改配置文件
[root@manager ~]# cat /etc/krb5.conf # Configuration snippets may be placed in this directory as well includedir /etc/krb5.conf.d/ [logging] default = FILE:/var/log/krb5libs.log kdc = FILE:/var/log/krb5kdc.log admin_server = FILE:/var/log/kadmind.log [libdefaults] dns_lookup_realm = false ticket_lifetime = 24h renew_lifetime = 7d forwardable = true rdns = false default_realm = KRB.COM #修改为认证域 default_ccache_name = KEYRING:persistent:%{uid} [realms] KRB.COM = { kdc = 192.168.10.131 #KDC的地址 admin_server = 192.168.10.131 #kadmin服务地址 } [domain_realm]
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
#以上需要在服务端和客户端都配置,可以在服务端配置好以后使用scp拷贝。
4.在服务端安装krb5-server
[root@manager ~]# yum install -y krb5-server
- 1
5.修改服务端的配置文件
[root@manager ~]# cat /var/kerberos/krb5kdc/kdc.conf
[kdcdefaults]
kdc_ports = 88
kdc_tcp_ports = 88
[realms]
KRB.COM = {
#master_key_type = aes256-cts
acl_file = /var/kerberos/krb5kdc/kadm5.acl
dict_file = /usr/share/dict/words
admin_keytab = /var/kerberos/krb5kdc/kadm5.keytab
supported_enctypes = aes256-cts:normal aes128-cts:normal des3-hmac-sha1:normal arcfour-hmac:normal camellia256-cts:normal camellia128-cts:normal des-hmac-sha1:normal des-cbc-md5:normal des-cbc-crc:normal
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
二、配置阶段
1.创建kerberos数据库
[root@manager ~]# kdb5_util create -s -r KRB.COM
Loading random data
Initializing database '/var/kerberos/krb5kdc/principal' for realm 'KRB.COM',
master key name 'K/M@KRB.COM'
You will be prompted for the database Master Password.
It is important that you NOT FORGET this password.
Enter KDC database master key:
Re-enter KDC database master key to verify:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
2.创建管理员
[root@manager ~]# kadmin.local -q "addprinc admin/admin"
Authenticating as principal root/admin@KRB.COM with password.
WARNING: no policy specified for admin/admin@KRB.COM; defaulting to no policy
Enter password for principal "admin/admin@KRB.COM":
Re-enter password for principal "admin/admin@KRB.COM":
Principal "admin/admin@KRB.COM" created.
- 1
- 2
- 3
- 4
- 5
- 6
3.给管理员账户添加acl权限
[root@manager ~]# cat /var/kerberos/krb5kdc/kadm5.acl
*/admin@KRB.COM *
- 1
- 2
4.启动服务和设置开机自启
[root@manager ~]# systemctl start krb5kdc
[root@manager ~]# systemctl start kadmin
[root@manager ~]# systemctl enable krb5kdc
[root@manager ~]# systemctl enable kadmin
- 1
- 2
- 3
- 4
5.在客户端测试连接
[root@vm1 ~]# kadmin -p admin/admin
Authenticating as principal admin/admin with password.
Password for admin/admin@KRB.COM:
kadmin: listprincs
K/M@KRB.COM
admin/admin@KRB.COM
kadmin/admin@KRB.COM
kadmin/changepw@KRB.COM
kadmin/manager@KRB.COM
kiprop/manager@KRB.COM
krbtgt/KRB.COM@KRB.COM
kadmin: quit
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
6.重新启动ambari-server
[root@manager ~]# ambari-server restart
- 1
三、 在Ambari上添加kerberos
1.开启Kerberos
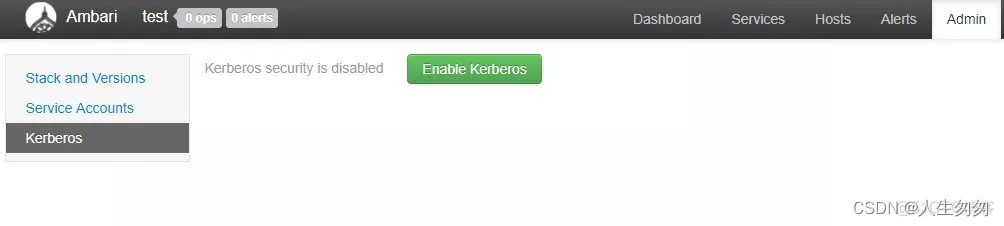
2.选择MIT
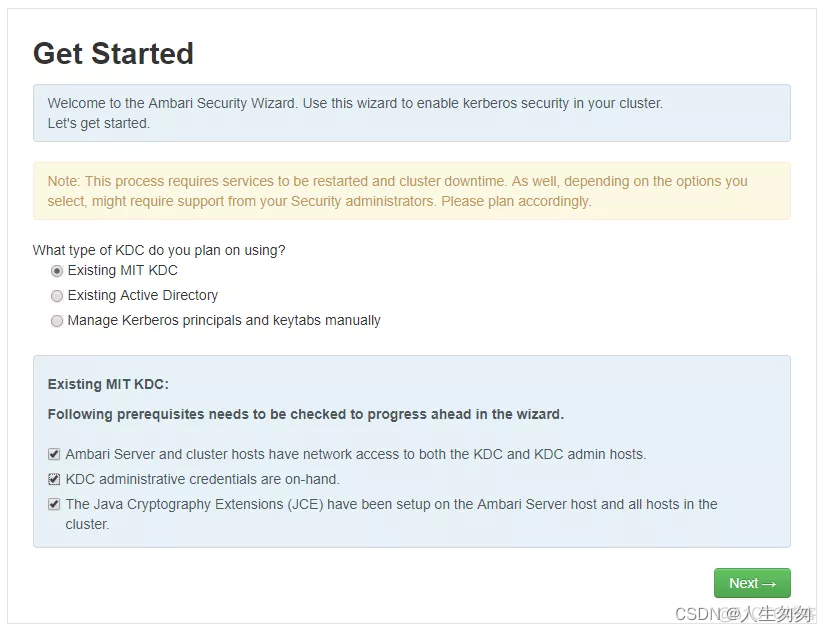
3.输入KDC和Kadmin相关信息
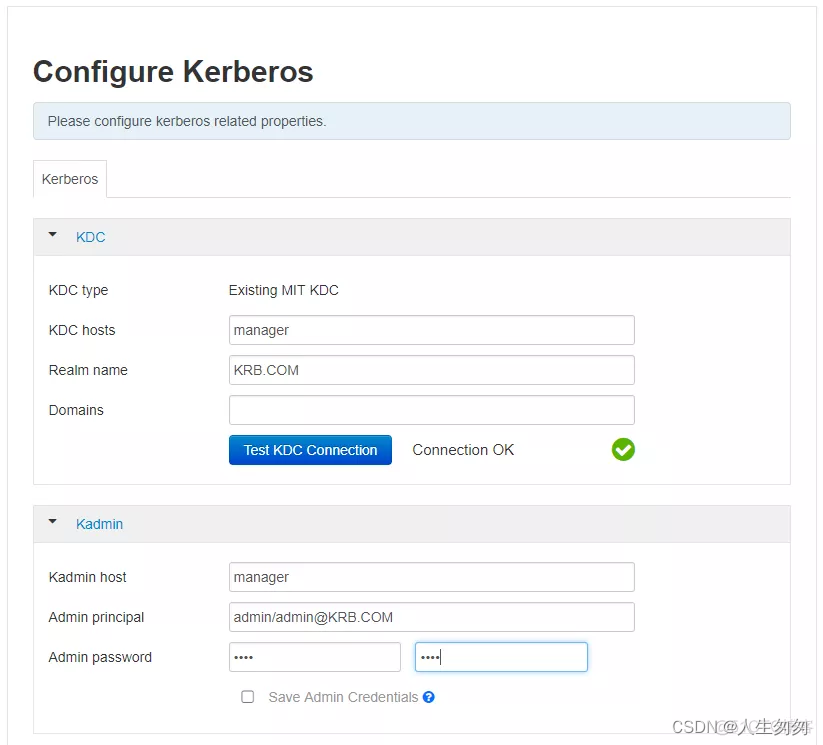
4.安装和测试
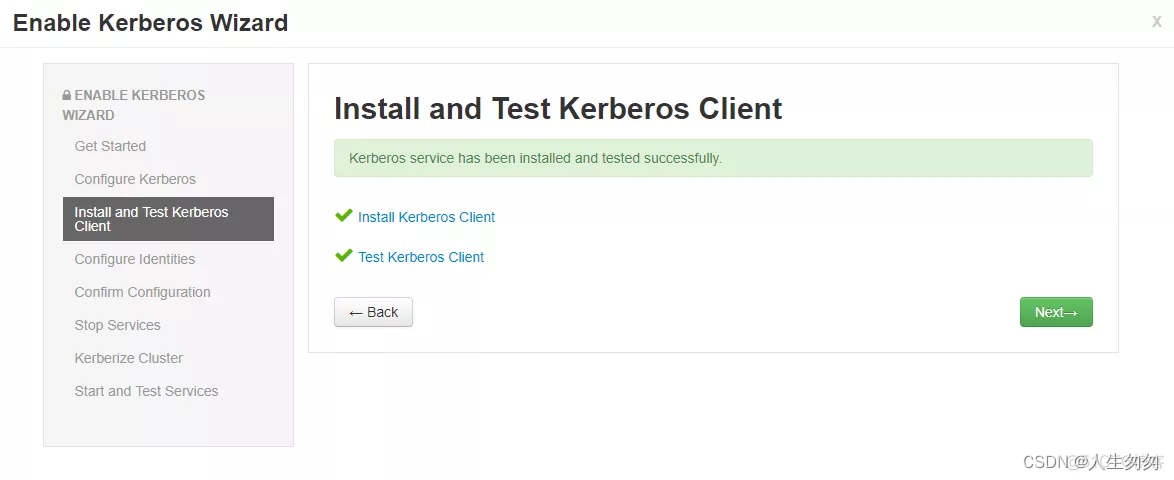
5.配置文件设置
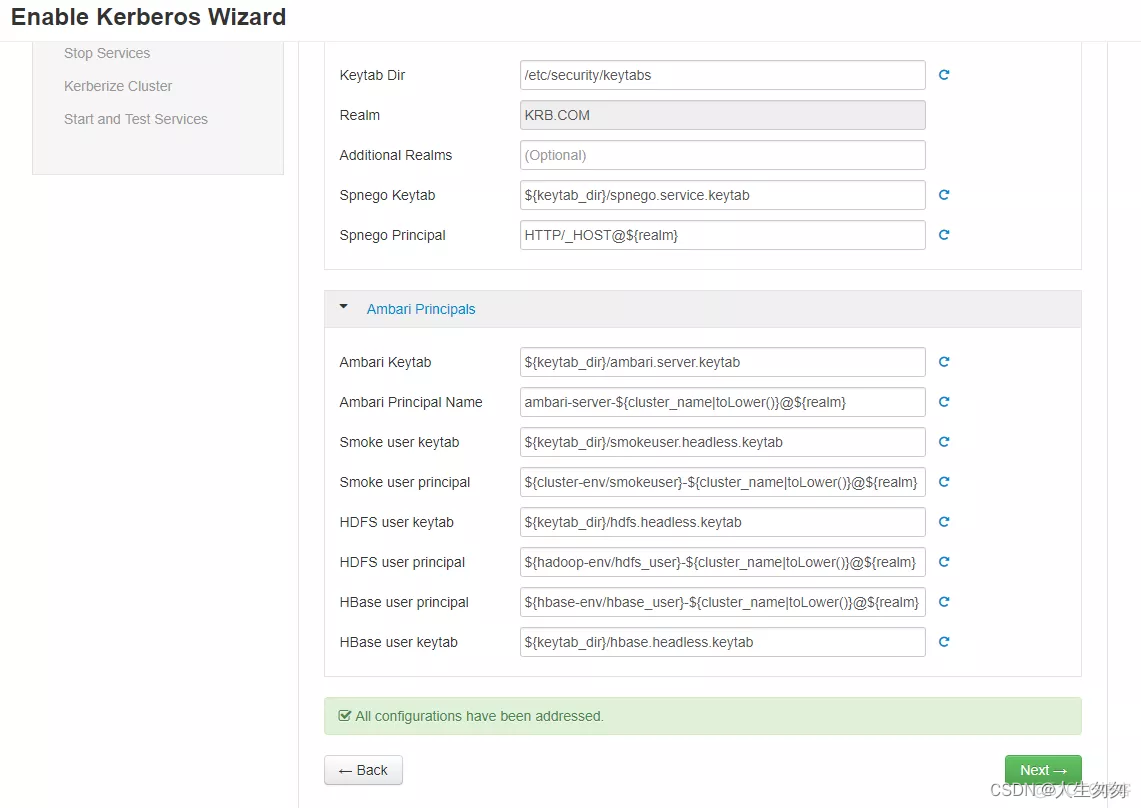
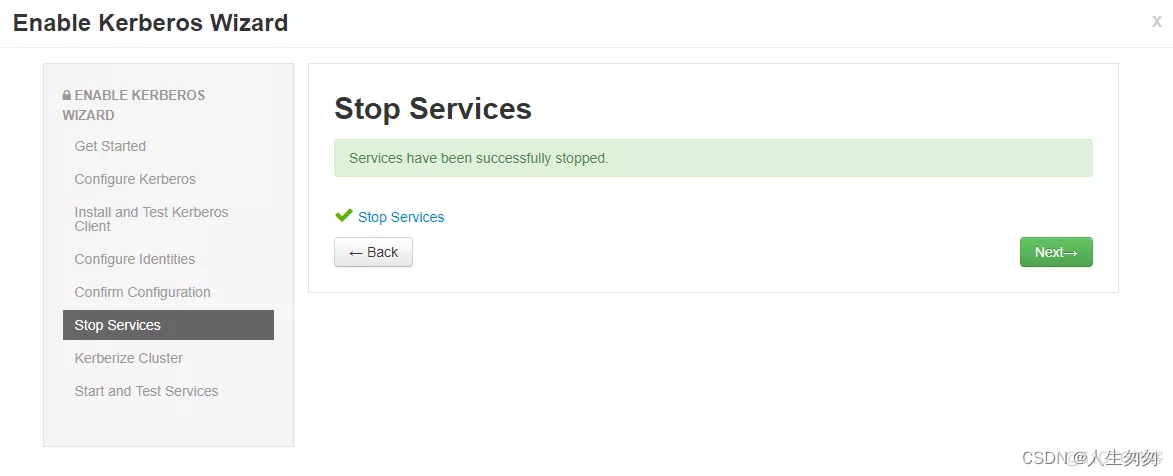
6.等待停止其他服务
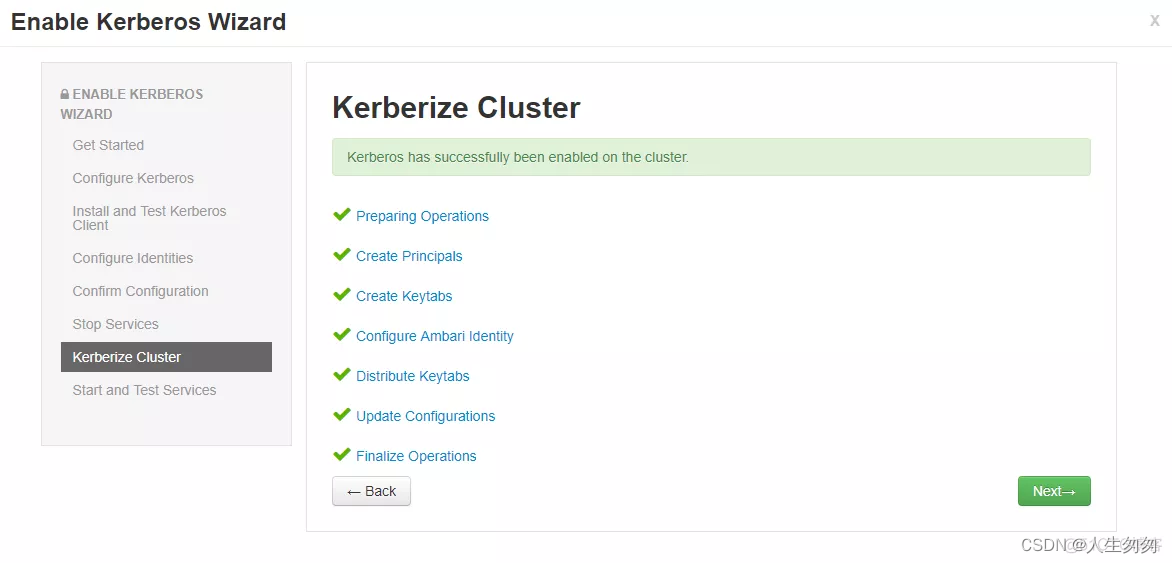
7.添加完成
8.等待开启服务
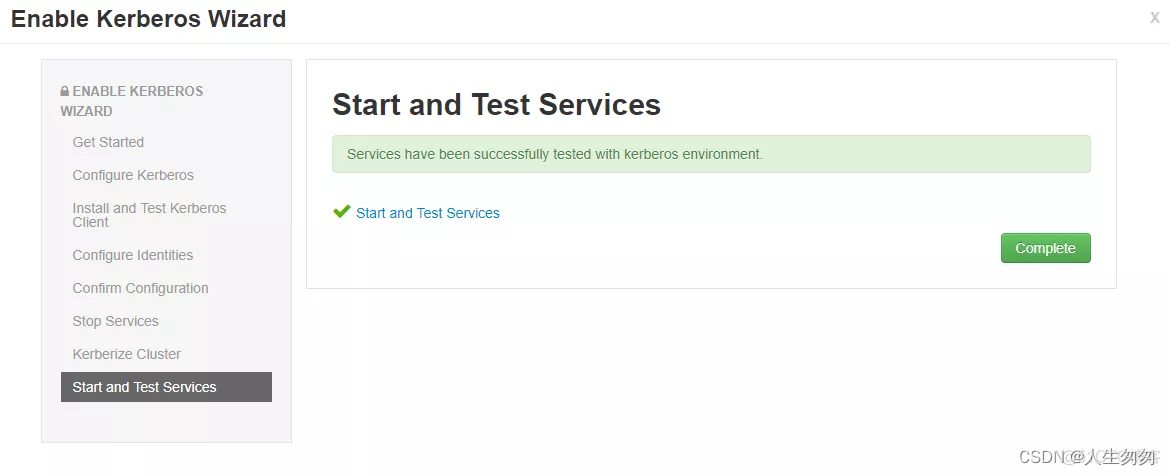
9.完成
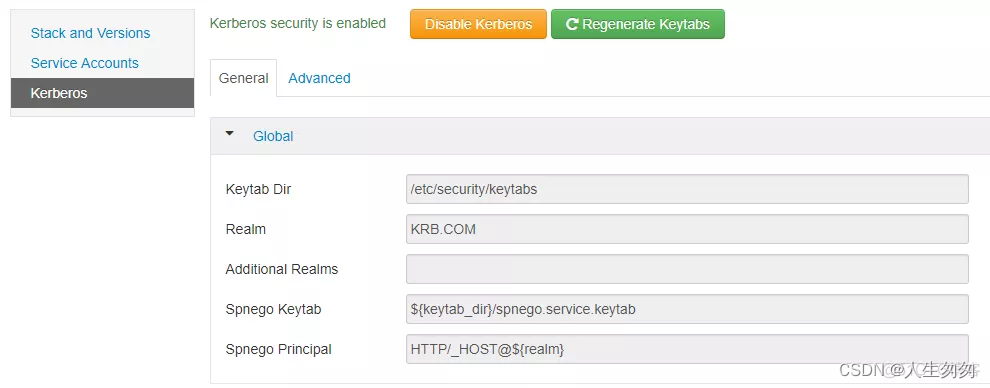
10、新增用户(add_principal USER)
使用默认配置
sudo kadmin.local kadmin.local: add_principal futeng # 新增 futeng 用户 WARNING: no policy specified for futeng@MYREALM; defaulting to no policy Enter password for principal "futeng@MYREALM": # 输入密码 Re-enter password for principal "futeng@MYREALM":# 确认密码 Principal "futeng@MYREALM" created. kadmin.local: quit # 退出 # 测试 $ kinit futeng Password for futeng@MYREALM: # 输入密码 $ klist Ticket cache: FILE:/tmp/krb5cc_1000 # 登录成功 Default principal: futeng@MYREALM Valid starting Expires Service principal 09/07/20 17:14:45 09/08/20 17:14:45 krbtgt/MYREALM@MYREALM renew until 09/14/20 17:14:45
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
生成 keytab(ktadd)
$ sudo kadmin.local
kadmin.local: ktadd -k /tmp/futeng.keytab futeng
Entry for principal futeng with kvno 4, encryption type des3-cbc-sha1 added to keytab WRFILE:/tmp/futeng.keytab.
Entry for principal futeng with kvno 4, encryption type arcfour-hmac added to keytab WRFILE:/tmp/futeng.keytab.
Entry for principal futeng with kvno 4, encryption type des-hmac-sha1 added to keytab WRFILE:/tmp/futeng.keytab.
Entry for principal futeng with kvno 4, encryption type des-cbc-md5 added to keytab
kadmin.local: xst -norandkey -k /home/chen/cwd.keytab futeng
#注意:在生成keytab文件时需要加参数”-norandkey”,否则会导致直接使用kinit test@HADOOP.COM初始化时会提示密码错误。
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
使用keytab登录
[root@ /etc/security/keytabs]# kinit -kt /root/futeng.keytab futeng
[root@ /etc/security/keytabs]# klist
Ticket cache: FILE:/tmp/krb5cc_0
Default principal: futeng@KRB.COM
Valid starting Expires Service principal
11/01/2022 16:53:28 11/02/2022 16:53:28 krbtgt/KRB.COM@KRB.COM
- 1
- 2
- 3
- 4
- 5
- 6
- 7
删除用户(delete_principal)
$ sudo kadmin.local
kadmin.local: delete_principal futeng
Are you sure you want to delete the principal "futeng@MYREALM"? (yes/no): yes
Principal "futeng@MYREALM" deleted.
Make sure that you have removed this principal from all ACLs before reusing.
- 1
- 2
- 3
- 4
- 5
归作者所有:来自51CTO博客作者一语成谶灬的原创作品,请联系作者获取转载授权,否则将追究法律责任
在Ambari上添加Kerberos
https://blog.51cto.com/lullaby/2053660
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/你好赵伟/article/detail/791009
推荐阅读
相关标签



