- 1FPGA两种实现除法的方法和一种实现平方根的方法_fpga里面处理有乘法和除法的公式
- 2m基于FPGA的OFDM调制解调系统verilog实现,包括IFFT,FFT以及成型滤波器,包含testbench_ofdm调制解调的fpga实现
- 3第二弹!又来5个Jupyter Notebook使用技巧!
- 4《Python自然语言处理》第二章 习题解答 练习6
- 5【免费】【前言】Stable Diffusion WebUI 课程简介_stable diffusion系统图文课堂
- 6java数据结构-栈_java 栈
- 7小白如何快速 Web 安全入门?(内附学习笔记)_小白学web安全
- 8自定义类型:结构体 枚举 联合体 那些你不知道的事_stu s1={"zhangsan
- 9[Git]Git Config
- 10Ubuntu 23.10/24.04 LTS 放弃默认使用 snap 版 CUPS 打印堆栈
云原生|kubernetes|安全漏扫神器trivy的部署和使用
赞
踩
前言:
云原生领域内的安全漏扫工具有clair和trivy是比较常用的,而安全漏扫工具是可以和harbor这样的私有仓库集成的,自harbor-1.21版以后都是默认使用trivy这个漏扫工具的,而在此之前是使用clair的。
那么,本文将就什么是trivy,trivy如何正确的部署,如何正确的使用做一个简单的探讨。
一,
什么是trivy?
trivy是一个主要运用在云原生领域的安全漏扫工具,是一种易于使用的开源漏洞扫描器,可帮助团队“左移”将安全性纳入构建管道。
那么,trivy的工作范围主要是对用于生产或者即将用于生产的镜像进行安全漏洞扫描,例如,centos的某个基础镜像,这个 CentOS 在 2021 年 7 月 29 日至 8 月 10 日期间的下载量已超过 700 万次,但该镜像具有大量未修补漏洞并且没有正式弃用。如果在生产中使用这样的镜像无疑是一个巨大的安全隐患。
其次是文件系统,也可以扫描git 远程仓库以及kubernetes集群和kubernetes内的资源。
- Targets:
- - Container Image
- - Filesystem
- - Git repository (remote)
- - Kubernetes cluster or resource
二,
如何正确的部署trivy?
trivy的安装方式比较多,可以rpm的形式安装,也可以apt的形式安装,也可以helm形式的直接集成到kubernetes内,也可以直接docker run 镜像的方式部署。
那么,比较常见的也是难度比较小的是rpm形式安装了。
下面是部署方式,
- Get Trivy by your favorite installation method. See [installation] section in the documentation for details. For example:
-
- - `apt-get install trivy`
- - `yum install trivy`
- - `brew install aquasecurity/trivy/trivy`
- - `docker run aquasec/trivy`
- - Download binary from https://github.com/aquasecurity/trivy/releases/latest/
这么说还是比较抽象,直接从GitHub下载rpm包上传到服务器上安装即可,我这里的服务器是centos7 64位的机器,因此选择下载trivy_0.34.0_Linux-64bit.rpm
下载地址: Release v0.34.0 · aquasecurity/trivy · GitHub

rpm安装就不用说了,直接安装即可,没有依赖。
trivy使用中的主要的困扰是需要联网从GitHub下载trivy-db 数据库,虽然有离线的trivy-db下载,但离线的通常是v1版本的,而高版本的trivy是使用的是v2
目前还没有比较好的解决办法,只有科学上网这一个办法了。
Releases · aquasecurity/trivy-db · GitHub
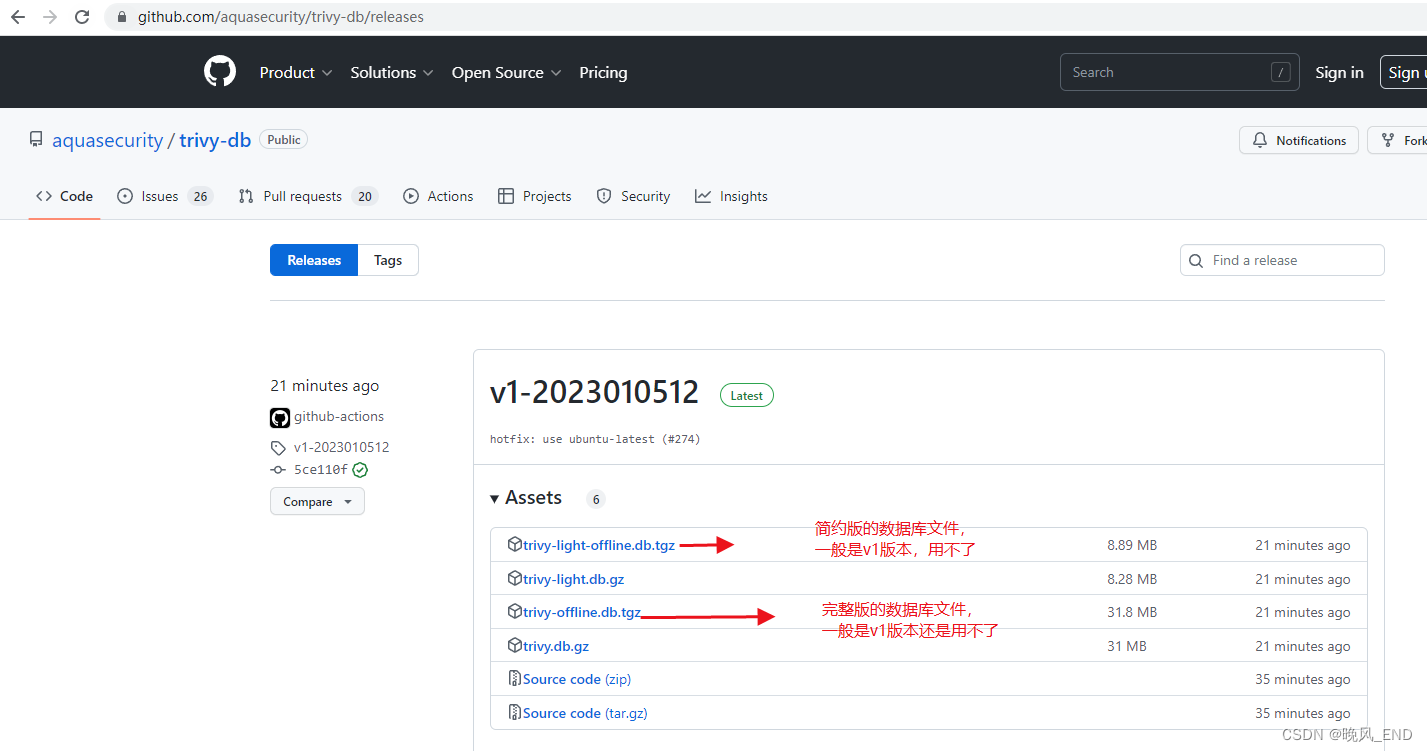
三,
trivy的使用
kubernetes集群的检测
检测内容有kubernetes集群的所有镜像,集群使用的role和clusterrole和静态pod
- [root@k8s-master ~]# trivy k8s --report summary cluster
- 2023-01-06T04:56:44.547+0800 INFO Need to update DB
- 2023-01-06T04:56:44.547+0800 INFO DB Repository: ghcr.io/aquasecurity/trivy-db
- 2023-01-06T04:56:44.547+0800 INFO Downloading DB...
- 35.96 MiB / 35.96 MiB [------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------] 100.00% 5.23 MiB p/s 7.1s
- 159 / 159 [------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------] 100.00% 1 p/s
-
- Summary Report for kubernetes-admin@kubernetes
-
-
- Workload Assessment
- ┌─────────────┬────────────────────────────────────────┬────────────────────────┬────────────────────┬───────────────────┐
- │ Namespace │ Resource │ Vulnerabilities │ Misconfigurations │ Secrets │
- │ │ ├────┬─────┬────┬────┬───┼───┬───┬───┬────┬───┼───┬───┬───┬───┬───┤
- │ │ │ C │ H │ M │ L │ U │ C │ H │ M │ L │ U │ C │ H │ M │ L │ U │
- ├─────────────┼────────────────────────────────────────┼────┼─────┼────┼────┼───┼───┼───┼───┼────┼───┼───┼───┼───┼───┼───┤
- │ kube-system │ DaemonSet/kube-flannel-ds │ 12 │ 124 │ 56 │ 16 │ 4 │ │ 1 │ 7 │ 16 │ │ │ │ │ │ │
- │ kube-system │ Pod/kube-controller-manager-k8s-master │ │ │ │ │ │ │ 1 │ 3 │ 8 │ │ │ │ │ │ │
- │ kube-system │ Service/kube-dns │ │ │ │ │ │ │ │ 1 │ │ │ │ │ │ │ │
- │ kube-system │ Pod/kube-apiserver-k8s-master │ │ │ │ │ │ │ 1 │ 3 │ 9 │ │ │ │ │ │ │
- │ kube-system │ DaemonSet/kube-proxy │ 15 │ 14 │ 20 │ 58 │ │ │ 2 │ 4 │ 10 │ │ │ │ │ │ │
- │ kube-system │ Pod/etcd-k8s-master │ │ 16 │ 8 │ │ │ │ 1 │ 3 │ 7 │ │ │ │ │ │ │
- │ kube-system │ Deployment/coredns │ │ 7 │ 3 │ 1 │ │ │ │ 3 │ 5 │ │ │ │ │ │ │
- │ kube-system │ Pod/kube-scheduler-k8s-master │ │ │ │ │ │ │ 1 │ 3 │ 8 │ │ │ │ │ │ │
- │ default │ Job/kube-bench │ 5 │ 34 │ 9 │ 1 │ │ │ 1 │ 3 │ 10 │ │ │ │ │ │ │
- │ default │ Job/kube-bench-master │ 1 │ 30 │ 9 │ 1 │ │ │ 1 │ 4 │ 10 │ │ │ │ │ │ │
- └─────────────┴────────────────────────────────────────┴────┴─────┴────┴────┴───┴───┴───┴───┴────┴───┴───┴───┴───┴───┴───┘
- Severities: C=CRITICAL H=HIGH M=MEDIUM L=LOW U=UNKNOWN
-
-
- RBAC Assessment
- ┌─────────────┬─────────────────────────────────────────────────────────────────┬───────────────────┐
- │ Namespace │ Resource │ RBAC Assessment │
- │ │ ├───┬───┬───┬───┬───┤
- │ │ │ C │ H │ M │ L │ U │
- ├─────────────┼─────────────────────────────────────────────────────────────────┼───┼───┼───┼───┼───┤
- │ kube-system │ Role/system::leader-locking-kube-scheduler │ │ │ 1 │ │ │
- │ kube-system │ Role/system:controller:bootstrap-signer │ 1 │ │ │ │ │
- │ kube-system │ Role/system:controller:token-cleaner │ 1 │ │ │ │ │
- │ kube-system │ Role/system::leader-locking-kube-controller-manager │ │ │ 1 │ │ │
- │ kube-system │ Role/system:controller:cloud-provider │ │ │ 1 │ │ │
- │ kube-public │ Role/system:controller:bootstrap-signer │ │ │ 1 │ │ │
- │ │ ClusterRole/system:controller:horizontal-pod-autoscaler │ 1 │ │ │ │ │
- │ │ ClusterRole/system:controller:deployment-controller │ │ 2 │ │ │ │
- │ │ ClusterRole/edit │ 2 │ 7 │ 1 │ │ │
- │ │ ClusterRole/admin │ 3 │ 7 │ 1 │ │ │
- │ │ ClusterRole/system:controller:cronjob-controller │ │ 2 │ │ │ │
- │ │ ClusterRole/system:controller:endpointslicemirroring-controller │ │ 1 │ │ │ │
- │ │ ClusterRole/system:kube-controller-manager │ 5 │ 2 │ │ │ │
- │ │ ClusterRole/system:aggregate-to-edit │ 2 │ 7 │ 1 │ │ │
- │ │ ClusterRole/system:controller:persistent-volume-binder │ 1 │ 2 │ │ │ │
- │ │ ClusterRole/system:controller:root-ca-cert-publisher │ │ │ 1 │ │ │
- │ │ ClusterRole/system:controller:replicaset-controller │ │ 1 │ │ │ │
- │ │ ClusterRole/system:aggregate-to-admin │ 1 │ │ │ │ │
- │ │ ClusterRole/system:controller:resourcequota-controller │ 1 │ │ │ │ │
- │ │ ClusterRole/system:controller:endpoint-controller │ │ 1 │ │ │ │
- │ │ ClusterRole/system:node │ 1 │ │ │ │ │
- │ │ ClusterRole/system:controller:replication-controller │ │ 1 │ │ │ │
- │ │ ClusterRole/system:controller:job-controller │ │ 1 │ │ │ │
- │ │ ClusterRole/system:controller:endpointslice-controller │ │ 1 │ │ │ │
- │ │ ClusterRole/system:controller:expand-controller │ 1 │ │ │ │ │
- │ │ ClusterRole/cluster-admin │ 2 │ │ │ │ │
- │ │ ClusterRole/system:controller:namespace-controller │ 1 │ │ │ │ │
- │ │ ClusterRole/system:controller:generic-garbage-collector │ 1 │ │ │ │ │
- │ │ ClusterRole/system:kube-scheduler │ │ 2 │ │ │ │
- └─────────────┴─────────────────────────────────────────────────────────────────┴───┴───┴───┴───┴───┘
- Severities: C=CRITICAL H=HIGH M=MEDIUM L=LOW U=UNKNOWN
-
-
- Infra Assessment
- ┌─────────────┬────────────────────────────────────────┬─────────────────────────────┐
- │ Namespace │ Resource │ Kubernetes Infra Assessment │
- │ │ ├────┬────┬────┬─────┬────────┤
- │ │ │ C │ H │ M │ L │ U │
- ├─────────────┼────────────────────────────────────────┼────┼────┼────┼─────┼────────┤
- │ kube-system │ Pod/kube-apiserver-k8s-master │ │ │ 1 │ 10 │ │
- │ kube-system │ Pod/kube-controller-manager-k8s-master │ │ │ │ 3 │ │
- │ kube-system │ Pod/kube-scheduler-k8s-master │ │ │ │ 1 │ │
- └─────────────┴────────────────────────────────────────┴────┴────┴────┴─────┴────────┘
- Severities: C=CRITICAL H=HIGH M=MEDIUM L=LOW U=UNKNOWN
检测namespace kube-system下的所有镜像:
- a=`kubectl get po -n kube-system --output=custom-columns="IMAGE:.spec.containers[*].image"`
-
- for i in $a;do trivy image --skip-update -s 'HIGH,CRITICAL' $i;done
这里解释一下,kubectl get po -n kube-system --output=custom-columns="IMAGE:.spec.containers[*].image"是获取namespace下所有镜像的名称
- [root@k8s-master ~]# kubectl get po -n kube-system --output=custom-columns="IMAGE:.spec.containers[*].image"
- IMAGE
- registry.aliyuncs.com/google_containers/coredns:v1.8.6
- registry.aliyuncs.com/google_containers/coredns:v1.8.6
- registry.aliyuncs.com/google_containers/etcd:3.5.6-0
- registry.aliyuncs.com/google_containers/kube-apiserver:v1.23.15
- registry.aliyuncs.com/google_containers/kube-controller-manager:v1.23.15
- quay.io/coreos/flannel:v0.13.0
- quay.io/coreos/flannel:v0.13.0
- quay.io/coreos/flannel:v0.13.0
- registry.aliyuncs.com/google_containers/kube-proxy:v1.23.15
- registry.aliyuncs.com/google_containers/kube-proxy:v1.23.15
- registry.aliyuncs.com/google_containers/kube-proxy:v1.23.15
- registry.aliyuncs.com/google_containers/kube-scheduler:v1.23.15
然后把这些镜像名称赋值给了变量a, 然后for循环trivy 检测这些镜像,检测的结果如下:
- 前面的内容略略略了
- registry.aliyuncs.com/google_containers/kube-proxy:v1.23.15 (debian 11.0)
- =========================================================================
- Total: 29 (HIGH: 14, CRITICAL: 15)
-
- ┌─────────────────┬────────────────┬──────────┬───────────────────┬─────────────────────────┬──────────────────────────────────────────────────────────────┐
- │ Library │ Vulnerability │ Severity │ Installed Version │ Fixed Version │ Title │
- ├─────────────────┼────────────────┼──────────┼───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ dpkg │ CVE-2022-1664 │ CRITICAL │ 1.20.9 │ 1.20.10 │ Dpkg::Source::Archive in dpkg, the Debian package management │
- │ │ │ │ │ │ system, b ... │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-1664 │
- ├─────────────────┼────────────────┼──────────┼───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ gzip │ CVE-2022-1271 │ HIGH │ 1.10-4 │ 1.10-4+deb11u1 │ gzip: arbitrary-file-write vulnerability │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-1271 │
- ├─────────────────┼────────────────┼──────────┼───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ libc-bin │ CVE-2021-33574 │ CRITICAL │ 2.31-13 │ 2.31-13+deb11u3 │ glibc: mq_notify does not handle separately allocated thread │
- │ │ │ │ │ │ attributes │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2021-33574 │
- │ ├────────────────┤ │ │ ├──────────────────────────────────────────────────────────────┤
- │ │ CVE-2022-23218 │ │ │ │ glibc: Stack-based buffer overflow in svcunix_create via │
- │ │ │ │ │ │ long pathnames │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-23218 │
- │ ├────────────────┤ │ │ ├──────────────────────────────────────────────────────────────┤
- │ │ CVE-2022-23219 │ │ │ │ glibc: Stack-based buffer overflow in sunrpc clnt_create via │
- │ │ │ │ │ │ a long pathname │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-23219 │
- │ ├────────────────┼──────────┤ ├─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ │ CVE-2021-3999 │ HIGH │ │ 2.31-13+deb11u4 │ glibc: Off-by-one buffer overflow/underflow in getcwd() │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2021-3999 │
- ├─────────────────┼────────────────┼──────────┤ ├─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ libc6 │ CVE-2021-33574 │ CRITICAL │ │ 2.31-13+deb11u3 │ glibc: mq_notify does not handle separately allocated thread │
- │ │ │ │ │ │ attributes │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2021-33574 │
- │ ├────────────────┤ │ │ ├──────────────────────────────────────────────────────────────┤
- │ │ CVE-2022-23218 │ │ │ │ glibc: Stack-based buffer overflow in svcunix_create via │
- │ │ │ │ │ │ long pathnames │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-23218 │
- │ ├────────────────┤ │ │ ├──────────────────────────────────────────────────────────────┤
- │ │ CVE-2022-23219 │ │ │ │ glibc: Stack-based buffer overflow in sunrpc clnt_create via │
- │ │ │ │ │ │ a long pathname │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-23219 │
- │ ├────────────────┼──────────┤ ├─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ │ CVE-2021-3999 │ HIGH │ │ 2.31-13+deb11u4 │ glibc: Off-by-one buffer overflow/underflow in getcwd() │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2021-3999 │
- ├─────────────────┼────────────────┤ ├───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ libcom-err2 │ CVE-2022-1304 │ │ 1.46.2-2 │ │ e2fsprogs: out-of-bounds read/write via crafted filesystem │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-1304 │
- ├─────────────────┼────────────────┼──────────┼───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ libdb5.3 │ CVE-2019-8457 │ CRITICAL │ 5.3.28+dfsg1-0.8 │ │ sqlite: heap out-of-bound read in function rtreenode() │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2019-8457 │
- ├─────────────────┼────────────────┼──────────┼───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ libgcrypt20 │ CVE-2021-33560 │ HIGH │ 1.8.7-6 │ │ libgcrypt: mishandles ElGamal encryption because it lacks │
- │ │ │ │ │ │ exponent blinding to address a... │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2021-33560 │
- ├─────────────────┼────────────────┤ ├───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ libgmp10 │ CVE-2021-43618 │ │ 2:6.2.1+dfsg-1 │ 2:6.2.1+dfsg-1+deb11u1 │ gmp: Integer overflow and resultant buffer overflow via │
- │ │ │ │ │ │ crafted input │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2021-43618 │
- ├─────────────────┼────────────────┤ ├───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ libgnutls30 │ CVE-2022-2509 │ │ 3.7.1-5 │ 3.7.1-5+deb11u2 │ gnutls: Double free during gnutls_pkcs7_verify │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-2509 │
- ├─────────────────┼────────────────┤ ├───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ liblzma5 │ CVE-2022-1271 │ │ 5.2.5-2 │ 5.2.5-2.1~deb11u1 │ gzip: arbitrary-file-write vulnerability │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-1271 │
- ├─────────────────┼────────────────┼──────────┼───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ libpcre2-8-0 │ CVE-2022-1586 │ CRITICAL │ 10.36-2 │ 10.36-2+deb11u1 │ pcre2: Out-of-bounds read in compile_xclass_matchingpath in │
- │ │ │ │ │ │ pcre2_jit_compile.c │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-1586 │
- │ ├────────────────┤ │ │ ├──────────────────────────────────────────────────────────────┤
- │ │ CVE-2022-1587 │ │ │ │ pcre2: Out-of-bounds read in get_recurse_data_length in │
- │ │ │ │ │ │ pcre2_jit_compile.c │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-1587 │
- ├─────────────────┼────────────────┤ ├───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ libssl1.1 │ CVE-2021-3711 │ │ 1.1.1k-1 │ 1.1.1k-1+deb11u1 │ openssl: SM2 Decryption Buffer Overflow │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2021-3711 │
- │ ├────────────────┤ │ ├─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ │ CVE-2022-1292 │ │ │ 1.1.1n-0+deb11u2 │ openssl: c_rehash script allows command injection │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-1292 │
- │ ├────────────────┤ │ ├─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ │ CVE-2022-2068 │ │ │ 1.1.1n-0+deb11u3 │ openssl: the c_rehash script allows command injection │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-2068 │
- │ ├────────────────┼──────────┤ ├─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ │ CVE-2021-3712 │ HIGH │ │ 1.1.1k-1+deb11u1 │ openssl: Read buffer overruns processing ASN.1 strings │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2021-3712 │
- │ ├────────────────┤ │ ├─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ │ CVE-2022-0778 │ │ │ 1.1.1k-1+deb11u2 │ openssl: Infinite loop in BN_mod_sqrt() reachable when │
- │ │ │ │ │ │ parsing certificates │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-0778 │
- ├─────────────────┼────────────────┼──────────┼───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ libtasn1-6 │ CVE-2021-46848 │ CRITICAL │ 4.16.0-2 │ 4.16.0-2+deb11u1 │ libtasn1: Out-of-bound access in ETYPE_OK │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2021-46848 │
- ├─────────────────┼────────────────┼──────────┼───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ libtirpc-common │ CVE-2021-46828 │ HIGH │ 1.3.1-1 │ 1.3.1-1+deb11u1 │ libtirpc: DoS vulnerability with lots of connections │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2021-46828 │
- ├─────────────────┤ │ │ │ │ │
- │ libtirpc3 │ │ │ │ │ │
- │ │ │ │ │ │ │
- ├─────────────────┼────────────────┤ ├───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ perl-base │ CVE-2020-16156 │ │ 5.32.1-4+deb11u1 │ │ perl-CPAN: Bypass of verification of signatures in CHECKSUMS │
- │ │ │ │ │ │ files │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2020-16156 │
- ├─────────────────┼────────────────┼──────────┼───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ zlib1g │ CVE-2022-37434 │ CRITICAL │ 1:1.2.11.dfsg-2 │ 1:1.2.11.dfsg-2+deb11u2 │ zlib: heap-based buffer over-read and overflow in inflate() │
- │ │ │ │ │ │ in inflate.c via a... │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-37434 │
- │ ├────────────────┼──────────┤ ├─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ │ CVE-2018-25032 │ HIGH │ │ 1:1.2.11.dfsg-2+deb11u1 │ zlib: A flaw found in zlib when compressing (not │
- │ │ │ │ │ │ decompressing) certain inputs... │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2018-25032 │
- └─────────────────┴────────────────┴──────────┴───────────────────┴─────────────────────────┴──────────────────────────────────────────────────────────────┘
-
- registry.aliyuncs.com/google_containers/kube-scheduler:v1.23.15 (debian 11.4)
- =============================================================================
- Total: 0 (HIGH: 0, CRITICAL: 0)
可以看到,kubernetes集群的核心组件用的镜像还是比较好的,漏洞基本没有,但flannel,etcd这些组件就比较多了。因此,kubernetes部署的时候还是推荐使用二进制部署etcd集群以及二进制部署flannel这些网络组件
单独检测一下kube-apiserver:
- [root@k8s-master ~]# trivy image --skip-db-update registry.aliyuncs.com/google_containers/kube-apiserver:v1.23.15
- 2023-01-06T06:08:45.348+0800 INFO Vulnerability scanning is enabled
- 2023-01-06T06:08:45.348+0800 INFO Secret scanning is enabled
- 2023-01-06T06:08:45.348+0800 INFO If your scanning is slow, please try '--security-checks vuln' to disable secret scanning
- 2023-01-06T06:08:45.348+0800 INFO Please see also https://aquasecurity.github.io/trivy/v0.34/docs/secret/scanning/#recommendation for faster secret detection
- 2023-01-06T06:08:45.355+0800 INFO Detected OS: debian
- 2023-01-06T06:08:45.356+0800 INFO Detecting Debian vulnerabilities...
- 2023-01-06T06:08:45.356+0800 INFO Number of language-specific files: 0
-
- registry.aliyuncs.com/google_containers/kube-apiserver:v1.23.15 (debian 11.4)
-
- Total: 0 (UNKNOWN: 0, LOW: 0, MEDIUM: 0, HIGH: 0, CRITICAL: 0)
OK,这个kube-apiserver是一个比较完美的目前还没有发现漏洞的镜像
单独检测一下kube-controller-manager,这个镜像同样表现完美:
- [root@k8s-master ~]# trivy image --skip-db-update registry.aliyuncs.com/google_containers/kube-controller-manager:v1.23.15
- 2023-01-06T06:10:10.749+0800 INFO Vulnerability scanning is enabled
- 2023-01-06T06:10:10.749+0800 INFO Secret scanning is enabled
- 2023-01-06T06:10:10.749+0800 INFO If your scanning is slow, please try '--security-checks vuln' to disable secret scanning
- 2023-01-06T06:10:10.749+0800 INFO Please see also https://aquasecurity.github.io/trivy/v0.34/docs/secret/scanning/#recommendation for faster secret detection
- 2023-01-06T06:10:10.755+0800 INFO Detected OS: debian
- 2023-01-06T06:10:10.755+0800 INFO Detecting Debian vulnerabilities...
- 2023-01-06T06:10:10.756+0800 INFO Number of language-specific files: 0
-
- registry.aliyuncs.com/google_containers/kube-controller-manager:v1.23.15 (debian 11.4)
-
- Total: 0 (UNKNOWN: 0, LOW: 0, MEDIUM: 0, HIGH: 0, CRITICAL: 0)
单独检测一下kube-proxy:
trivy image --skip-db-update registry.aliyuncs.com/google_containers/kube-proxy:v1.23.15这个输出就比较多了,漏洞很多,14个高危漏洞,15个致命漏洞:
- 2023-01-06T06:11:19.285+0800 INFO Vulnerability scanning is enabled
- 2023-01-06T06:11:19.285+0800 INFO Secret scanning is enabled
- 2023-01-06T06:11:19.285+0800 INFO If your scanning is slow, please try '--security-checks vuln' to disable secret scanning
- 2023-01-06T06:11:19.285+0800 INFO Please see also https://aquasecurity.github.io/trivy/v0.34/docs/secret/scanning/#recommendation for faster secret detection
- 2023-01-06T06:11:19.292+0800 INFO Detected OS: debian
- 2023-01-06T06:11:19.292+0800 INFO Detecting Debian vulnerabilities...
- 2023-01-06T06:11:19.307+0800 INFO Number of language-specific files: 0
-
- registry.aliyuncs.com/google_containers/kube-proxy:v1.23.15 (debian 11.0)
-
- Total: 107 (UNKNOWN: 0, LOW: 58, MEDIUM: 20, HIGH: 14, CRITICAL: 15)
-
- ┌──────────────────┬──────────────────┬──────────┬───────────────────┬─────────────────────────┬──────────────────────────────────────────────────────────────┐
- │ Library │ Vulnerability │ Severity │ Installed Version │ Fixed Version │ Title │
- ├──────────────────┼──────────────────┼──────────┼───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ apt │ CVE-2011-3374 │ LOW │ 2.2.4 │ │ It was found that apt-key in apt, all versions, do not │
- │ │ │ │ │ │ correctly... │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2011-3374 │
- ├──────────────────┼──────────────────┼──────────┼───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ bsdutils │ CVE-2021-3995 │ MEDIUM │ 2.36.1-8 │ 2.36.1-8+deb11u1 │ util-linux: Unauthorized unmount of FUSE filesystems │
- │ │ │ │ │ │ belonging to users with similar uid... │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2021-3995 │
- │ ├──────────────────┤ │ │ ├──────────────────────────────────────────────────────────────┤
- │ │ CVE-2021-3996 │ │ │ │ util-linux: Unauthorized unmount of filesystems in libmount │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2021-3996 │
- │ ├──────────────────┼──────────┤ ├─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ │ CVE-2022-0563 │ LOW │ │ │ util-linux: partial disclosure of arbitrary files in chfn │
- │ │ │ │ │ │ and chsh when compiled... │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-0563 │
- ├──────────────────┼──────────────────┤ ├───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ coreutils │ CVE-2016-2781 │ │ 8.32-4 │ │ coreutils: Non-privileged session can escape to the parent │
- │ │ │ │ │ │ session in chroot │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2016-2781 │
- │ ├──────────────────┤ │ ├─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ │ CVE-2017-18018 │ │ │ │ coreutils: race condition vulnerability in chown and chgrp │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2017-18018 │
- ├──────────────────┼──────────────────┼──────────┼───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ dpkg │ CVE-2022-1664 │ CRITICAL │ 1.20.9 │ 1.20.10 │ Dpkg::Source::Archive in dpkg, the Debian package management │
- │ │ │ │ │ │ system, b ... │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-1664 │
- ├──────────────────┼──────────────────┼──────────┼───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ gpgv │ CVE-2022-34903 │ MEDIUM │ 2.2.27-2 │ 2.2.27-2+deb11u2 │ gpg: Signature spoofing via status line injection │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-34903 │
- ├──────────────────┼──────────────────┼──────────┼───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ gzip │ CVE-2022-1271 │ HIGH │ 1.10-4 │ 1.10-4+deb11u1 │ gzip: arbitrary-file-write vulnerability │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-1271 │
- ├──────────────────┼──────────────────┼──────────┼───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ iptables │ CVE-2012-2663 │ LOW │ 1.8.7-1 │ │ iptables: --syn flag bypass │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2012-2663 │
- ├──────────────────┼──────────────────┤ ├───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ libapt-pkg6.0 │ CVE-2011-3374 │ │ 2.2.4 │ │ It was found that apt-key in apt, all versions, do not │
- │ │ │ │ │ │ correctly... │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2011-3374 │
- ├──────────────────┼──────────────────┼──────────┼───────────────────┼─────────────────────────┼──────────────────────────────────────────────────────────────┤
- 。。。。。。。。。。。。。。。。。。。。。。。。。后面的省略了
单独检测一下kube-scheduler,这个镜像同样表现接近完美:
- [root@k8s-master ~]# trivy image --skip-db-update registry.aliyuncs.com/google_containers/kube-scheduler:v1.23.15
- 2023-01-06T06:15:00.739+0800 INFO Vulnerability scanning is enabled
- 2023-01-06T06:15:00.739+0800 INFO Secret scanning is enabled
- 2023-01-06T06:15:00.739+0800 INFO If your scanning is slow, please try '--security-checks vuln' to disable secret scanning
- 2023-01-06T06:15:00.739+0800 INFO Please see also https://aquasecurity.github.io/trivy/v0.34/docs/secret/scanning/#recommendation for faster secret detection
- 2023-01-06T06:15:00.744+0800 INFO Detected OS: debian
- 2023-01-06T06:15:00.744+0800 INFO Detecting Debian vulnerabilities...
- 2023-01-06T06:15:00.744+0800 INFO Number of language-specific files: 0
-
- registry.aliyuncs.com/google_containers/kube-scheduler:v1.23.15 (debian 11.4)
-
- Total: 0 (UNKNOWN: 0, LOW: 0, MEDIUM: 0, HIGH: 0, CRITICAL: 0)
单独检测pause,这个镜像同样表现接近完美:
- [root@k8s-master ~]# trivy image --skip-db-update registry.aliyuncs.com/google_containers/pause:3.6
- 2023-01-06T06:16:36.227+0800 INFO Vulnerability scanning is enabled
- 2023-01-06T06:16:36.227+0800 INFO Secret scanning is enabled
- 2023-01-06T06:16:36.227+0800 INFO If your scanning is slow, please try '--security-checks vuln' to disable secret scanning
- 2023-01-06T06:16:36.227+0800 INFO Please see also https://aquasecurity.github.io/trivy/v0.34/docs/secret/scanning/#recommendation for faster secret detection
- 2023-01-06T06:16:36.232+0800 INFO Number of language-specific files: 0
单独检测coredns,这个镜像表现接近完美,只有一页的漏洞报告:
- [root@k8s-master ~]# trivy image --skip-db-update registry.aliyuncs.com/google_containers/coredns:v1.8.6
- 2023-01-06T06:17:43.783+0800 INFO Vulnerability scanning is enabled
- 2023-01-06T06:17:43.783+0800 INFO Secret scanning is enabled
- 2023-01-06T06:17:43.783+0800 INFO If your scanning is slow, please try '--security-checks vuln' to disable secret scanning
- 2023-01-06T06:17:43.783+0800 INFO Please see also https://aquasecurity.github.io/trivy/v0.34/docs/secret/scanning/#recommendation for faster secret detection
- 2023-01-06T06:17:43.790+0800 INFO Number of language-specific files: 1
- 2023-01-06T06:17:43.790+0800 INFO Detecting gobinary vulnerabilities...
-
- coredns (gobinary)
-
- Total: 11 (UNKNOWN: 0, LOW: 1, MEDIUM: 3, HIGH: 7, CRITICAL: 0)
-
- ┌─────────────────────────────────────┬────────────────┬──────────┬────────────────────────────────────┬───────────────────────────────────┬──────────────────────────────────────────────────────────────┐
- │ Library │ Vulnerability │ Severity │ Installed Version │ Fixed Version │ Title │
- ├─────────────────────────────────────┼────────────────┼──────────┼────────────────────────────────────┼───────────────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ github.com/aws/aws-sdk-go │ CVE-2020-8911 │ MEDIUM │ v1.40.54 │ │ aws/aws-sdk-go: CBC padding oracle issue in AWS S3 Crypto │
- │ │ │ │ │ │ SDK for golang... │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2020-8911 │
- │ ├────────────────┼──────────┤ ├───────────────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ │ CVE-2020-8912 │ LOW │ │ │ aws-sdk-go: In-band key negotiation issue in AWS S3 Crypto │
- │ │ │ │ │ │ SDK for golang... │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2020-8912 │
- ├─────────────────────────────────────┼────────────────┼──────────┼────────────────────────────────────┼───────────────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ github.com/prometheus/client_golang │ CVE-2022-21698 │ HIGH │ v1.11.0 │ 1.11.1 │ prometheus/client_golang: Denial of service using │
- │ │ │ │ │ │ InstrumentHandlerCounter │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-21698 │
- ├─────────────────────────────────────┼────────────────┤ ├────────────────────────────────────┼───────────────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ golang.org/x/crypto │ CVE-2021-43565 │ │ v0.0.0-20210513164829-c07d793c2f9a │ 0.0.0-20211202192323-5770296d904e │ golang.org/x/crypto: empty plaintext packet causes panic │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2021-43565 │
- │ ├────────────────┤ │ ├───────────────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ │ CVE-2022-27191 │ │ │ 0.0.0-20220314234659-1baeb1ce4c0b │ golang: crash in a golang.org/x/crypto/ssh server │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-27191 │
- ├─────────────────────────────────────┼────────────────┤ ├────────────────────────────────────┼───────────────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ golang.org/x/net │ CVE-2021-44716 │ │ v0.0.0-20210614182718-04defd469f4e │ 0.0.0-20211209124913-491a49abca63 │ golang: net/http: limit growth of header canonicalization │
- │ │ │ │ │ │ cache │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2021-44716 │
- │ ├────────────────┤ │ ├───────────────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ │ CVE-2022-27664 │ │ │ 0.0.0-20220906165146-f3363e06e74c │ golang: net/http: handle server errors after sending GOAWAY │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-27664 │
- │ ├────────────────┼──────────┤ ├───────────────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ │ CVE-2022-41717 │ MEDIUM │ │ 0.4.0 │ An attacker can cause excessive memory growth in a Go server │
- │ │ │ │ │ │ accepting... │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-41717 │
- ├─────────────────────────────────────┼────────────────┤ ├────────────────────────────────────┼───────────────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ golang.org/x/sys │ CVE-2022-29526 │ │ v0.0.0-20210917161153-d61c044b1678 │ 0.0.0-20220412211240-33da011f77ad │ golang: syscall: faccessat checks wrong group │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-29526 │
- ├─────────────────────────────────────┼────────────────┼──────────┼────────────────────────────────────┼───────────────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ golang.org/x/text │ CVE-2021-38561 │ HIGH │ v0.3.6 │ 0.3.7 │ golang: out-of-bounds read in golang.org/x/text/language │
- │ │ │ │ │ │ leads to DoS │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2021-38561 │
- │ ├────────────────┤ │ ├───────────────────────────────────┼──────────────────────────────────────────────────────────────┤
- │ │ CVE-2022-32149 │ │ │ 0.3.8 │ golang: golang.org/x/text/language: ParseAcceptLanguage │
- │ │ │ │ │ │ takes a long time to parse complex tags │
- │ │ │ │ │ │ https://avd.aquasec.com/nvd/cve-2022-32149 │
- └─────────────────────────────────────┴────────────────┴──────────┴────────────────────────────────────┴───────────────────────────────────┴──────────────────────────────────────────────────────────────┘
flannel的表现是比较差劲的,漏洞比较多,47个高危漏洞,5个致命漏洞:
- [root@k8s-master ~]# trivy image --skip-db-update quay.io/coreos/flannel:v0.13.0
- 2023-01-06T06:19:46.810+0800 INFO Vulnerability scanning is enabled
- 2023-01-06T06:19:46.810+0800 INFO Secret scanning is enabled
- 2023-01-06T06:19:46.810+0800 INFO If your scanning is slow, please try '--security-checks vuln' to disable secret scanning
- 2023-01-06T06:19:46.810+0800 INFO Please see also https://aquasecurity.github.io/trivy/v0.34/docs/secret/scanning/#recommendation for faster secret detection
- 2023-01-06T06:19:46.818+0800 INFO Detected OS: alpine
- 2023-01-06T06:19:46.819+0800 INFO Detecting Alpine vulnerabilities...
- 2023-01-06T06:19:46.821+0800 INFO Number of language-specific files: 1
- 2023-01-06T06:19:46.821+0800 INFO Detecting gobinary vulnerabilities...
- 2023-01-06T06:19:46.833+0800 WARN This OS version is no longer supported by the distribution: alpine 3.12.0
- 2023-01-06T06:19:46.833+0800 WARN The vulnerability detection may be insufficient because security updates are not provided
-
- quay.io/coreos/flannel:v0.13.0 (alpine 3.12.0)
-
- Total: 77 (UNKNOWN: 0, LOW: 6, MEDIUM: 19, HIGH: 47, CRITICAL: 5)
- 。。。。。。。。。。。。。。。。省略
由此,我们可以得出一个结论:
kubernetes集群的部署使用kubeadm是没什么问题的,但etcd,flannel。kube-proxy这些组件最好还是二进制部署。
附:
查看版本号命令可以看到,比较新的trivy是使用v2的数据库哦,并且trivy非常注意更新数据库,因此,第一次更新完数据库后,在使用的时候为了避免升级麻烦,最好还是命令加 --skip-db-update 这个参数
- [root@k8s-master db]# trivy version
- Version: 0.34.0
- Vulnerability DB:
- Version: 2
- UpdatedAt: 2023-01-05 12:09:26.44058254 +0000 UTC
- NextUpdate: 2023-01-05 18:09:26.44058214 +0000 UTC
- DownloadedAt: 2023-01-05 20:56:55.46729581 +0000 UTC


