热门标签
热门文章
- 1计算机网络的性能指标(速率、带宽、吞吐量、时延、往返时延、时延带宽积、信道利用率)...
- 2(三)基于arm64/aarch64架构的Debian Linux中mysql5.7+详细安装过程_aarch mysql5.7
- 3写写k8s的四种service类型和使用场景_k8sservice4种模式
- 4KEIL编译器【C语言编译选项优化等级说明】【支持C99(变量声明在执行语句之后)】【反汇编设置】【C语言联合汇编】【use microlib选项】_keil use microlib
- 5DaZeng:web页面使用markdown编辑器组件_markdown web
- 6【多线程编程学习笔记4】终止线程执行的3种方法(pthread_exit()、pthread_cancel()、return)_c语言终止线程
- 7华为鸿蒙系统需要谷歌的服务器吗,如果谷歌服务不能用,华为P40或用鸿蒙!
- 8nginx通用日志采集工具将数据落地磁盘的同时传入kafka_nginx本地和日志服务器同时采集日志
- 9在CMD中无法运行python_py -0p,在cmd上无法运行
- 10ActiveMQ与Zookeeper高可用集群_dzookeeper和mq的关系
当前位置: article > 正文
麒麟KYLINOS通过命令行配置kysec的防火墙_kylin 防火墙
作者:小蓝xlanll | 2024-03-05 04:08:09
赞
踩
kylin 防火墙
原文链接:麒麟KYLINOS通过命令行配置kysec的防火墙
hello,大家好啊,今天给大家带来一篇使用命令行配置kysec的防火墙的文章,通过本篇文章的学习,大家可以了解到图形化界面中的防火墙信息是如何生成的,为后期我们将防火墙的相关配置放入到定制镜像中做准备。首先给大家演示在图形化界面上该怎么操作,然后对应的操作如何利用命令行界面完成。
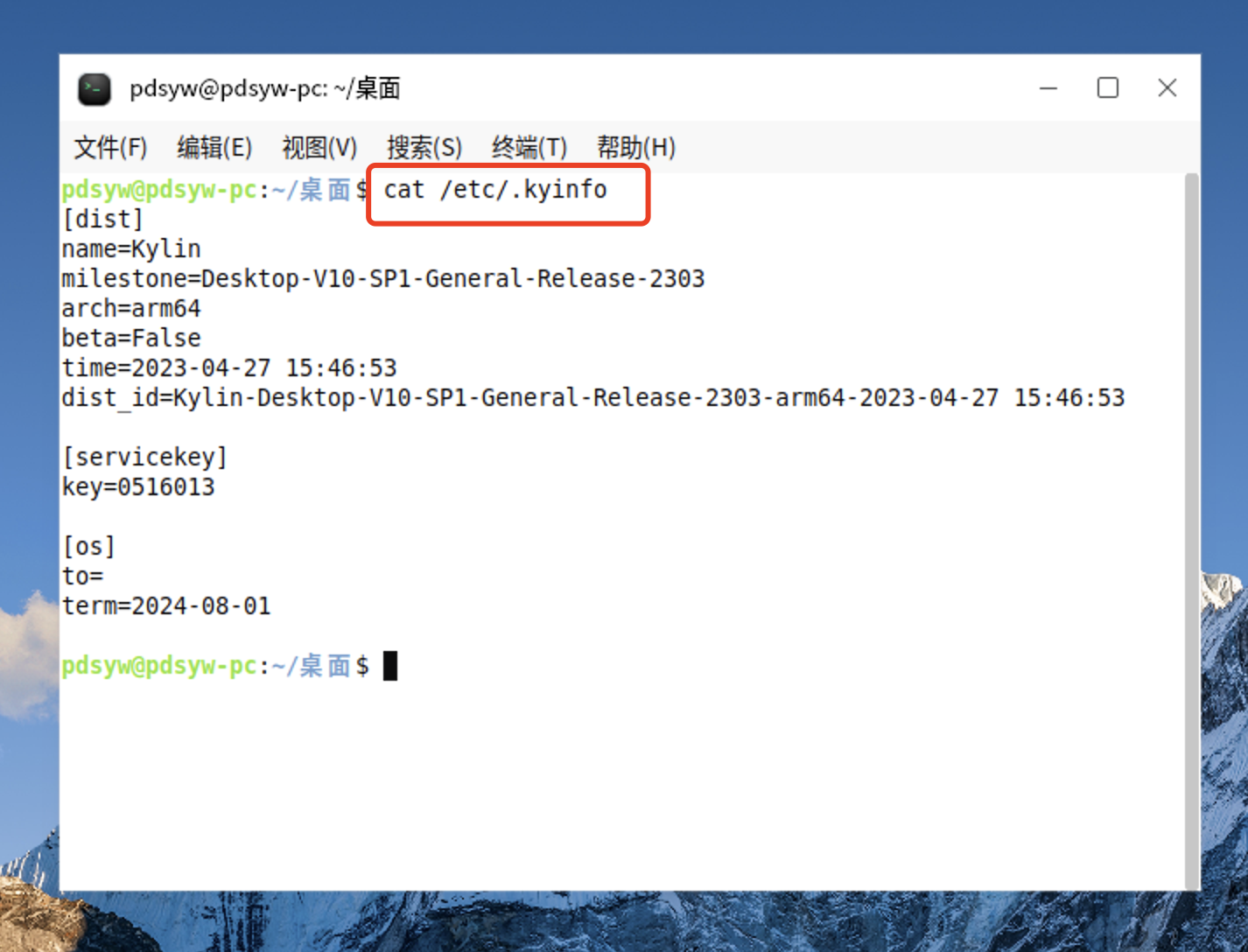
1、查看麒麟系统信息
pdsyw@pdsyw-pc:~/桌面$ cat /etc/.kyinfo [dist] name=Kylin milestone=Desktop-V10-SP1-General-Release-2303 arch=arm64 beta=False time=2023-04-27 15:46:53 dist_id=Kylin-Desktop-V10-SP1-General-Release-2303-arm64-2023-04-27 15:46:53 [servicekey] key=0516013 [os] to= term=2024-08-01 pdsyw@pdsyw-pc:~/桌面$
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
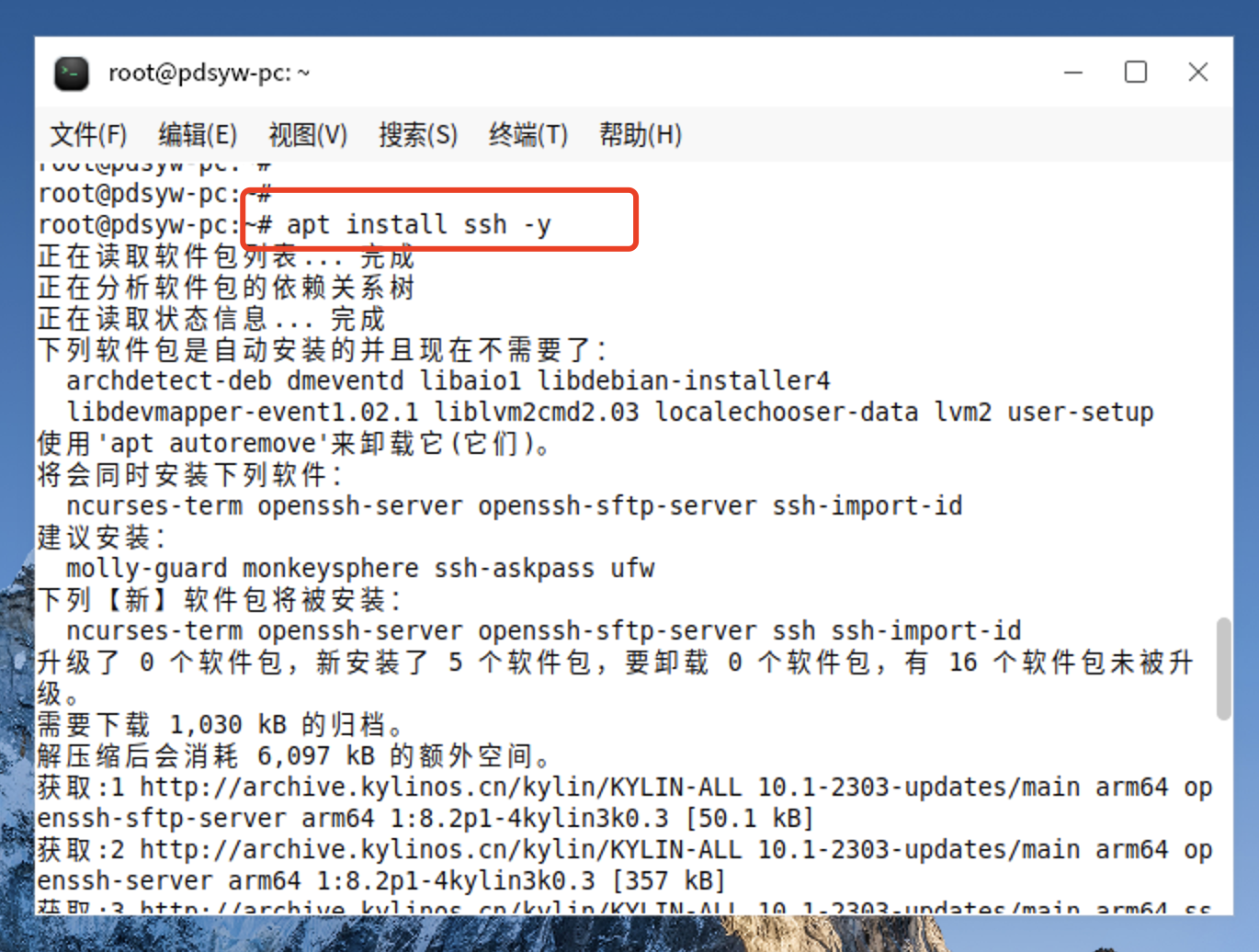
2、安装ssh
root@pdsyw-pc:~# apt install ssh -y 正在读取软件包列表... 完成 正在分析软件包的依赖关系树 正在读取状态信息... 完成 下列软件包是自动安装的并且现在不需要了: archdetect-deb dmeventd libaio1 libdebian-installer4 libdevmapper-event1.02.1 liblvm2cmd2.03 localechooser-data lvm2 user-setup 使用'apt autoremove'来卸载它(它们)。 将会同时安装下列软件: ncurses-term openssh-server openssh-sftp-server ssh-import-id 建议安装: molly-guard monkeysphere ssh-askpass ufw 下列【新】软件包将被安装: ncurses-term openssh-server openssh-sftp-server ssh ssh-import-id 升级了 0 个软件包,新安装了 5 个软件包,要卸载 0 个软件包,有 16 个软件包未被升级。 需要下载 1,030 kB 的归档。 解压缩后会消耗 6,097 kB 的额外空间。 获取:1 http://archive.kylinos.cn/kylin/KYLIN-ALL 10.1-2303-updates/main arm64 openssh-sftp-server arm64 1:8.2p1-4kylin3k0.3 [50.1 kB] 获取:2 http://archive.kylinos.cn/kylin/KYLIN-ALL 10.1-2303-updates/main arm64 openssh-server arm64 1:8.2p1-4kylin3k0.3 [357 kB] 获取:3 http://archive.kylinos.cn/kylin/KYLIN-ALL 10.1-2303-updates/main arm64 ssh all 1:8.2p1-4kylin3k0.3 [105 kB] 获取:4 http://archive.kylinos.cn/kylin/KYLIN-ALL 10.1/main arm64 ncurses-term all 6.2-0kylin2 [501 kB] 获取:5 http://archive.kylinos.cn/kylin/KYLIN-ALL 10.1/main arm64 ssh-import-id all 5.10-0kylin1 [17.2 kB] 已下载 1,030 kB,耗时 1秒 (1,489 kB/s) 正在预设定软件包 ... 正在选中未选择的软件包 openssh-sftp-server。 (正在读取数据库 ... 系统当前共安装有 191610 个文件和目录。) 准备解压 .../openssh-sftp-server_1%3a8.2p1-4kylin3k0.3_arm64.deb ... 正在解压 openssh-sftp-server (1:8.2p1-4kylin3k0.3) ... 正在选中未选择的软件包 openssh-server。 准备解压 .../openssh-server_1%3a8.2p1-4kylin3k0.3_arm64.deb ... 正在解压 openssh-server (1:8.2p1-4kylin3k0.3) ... 正在选中未选择的软件包 ssh。 准备解压 .../ssh_1%3a8.2p1-4kylin3k0.3_all.deb ... 正在解压 ssh (1:8.2p1-4kylin3k0.3) ... 正在选中未选择的软件包 ncurses-term。 准备解压 .../ncurses-term_6.2-0kylin2_all.deb ... 正在解压 ncurses-term (6.2-0kylin2) ... 正在选中未选择的软件包 ssh-import-id。 准备解压 .../ssh-import-id_5.10-0kylin1_all.deb ... 正在解压 ssh-import-id (5.10-0kylin1) ... 正在设置 openssh-sftp-server (1:8.2p1-4kylin3k0.3) ... 正在设置 openssh-server (1:8.2p1-4kylin3k0.3) ... Creating config file /etc/ssh/sshd_config with new version Creating SSH2 RSA key; this may take some time ... 3072 SHA256:KGiMMxfVed8XFMfJDAgboVL3LT/WWfU8szRWwe0IzuA root@pdsyw-pc (RSA) Creating SSH2 ECDSA key; this may take some time ... 256 SHA256:NMxxVNmzCAP21CttTPR2jljmf8dxfLAoo25PJ7/f7Jw root@pdsyw-pc (ECDSA) Creating SSH2 ED25519 key; this may take some time ... 256 SHA256:9MM0et35Ll8U28DnUbrDx0NR8LjQ81qgNFPCJodEjfE root@pdsyw-pc (ED25519) Created symlink /etc/systemd/system/sshd.service → /lib/systemd/system/ssh.servi ce. Created symlink /etc/systemd/system/multi-user.target.wants/ssh.service → /lib/s ystemd/system/ssh.service. rescue-ssh.target is a disabled or a static unit, not starting it. 正在设置 ssh-import-id (5.10-0kylin1) ... Attempting to convert /etc/ssh/ssh_import_id 正在设置 ncurses-term (6.2-0kylin2) ... 正在设置 ssh (1:8.2p1-4kylin3k0.3) ... 正在处理用于 man-db (2.9.1-1kylin0k1) 的触发器 ... 正在处理用于 systemd (245.4-4kylin3.15k0.26) 的触发器 ... root@pdsyw-pc:~#
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
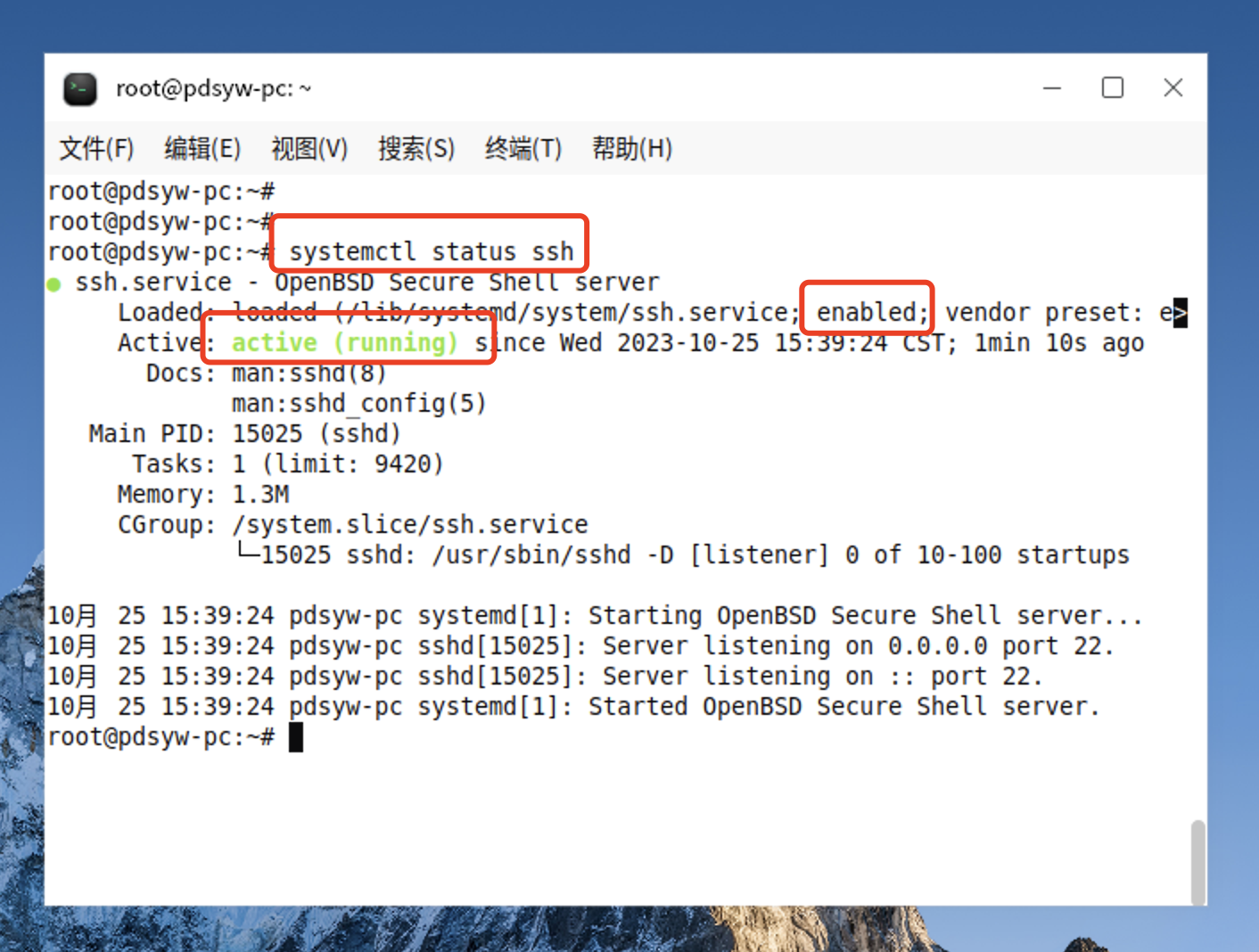
3、查看shh服务状态
root@pdsyw-pc:~# systemctl status ssh ● ssh.service - OpenBSD Secure Shell server Loaded: loaded (/lib/systemd/system/ssh.service; enabled; vendor preset: e> Active: active (running) since Wed 2023-10-25 16:58:06 CST; 23s ago Docs: man:sshd(8) man:sshd_config(5) Main PID: 10573 (sshd) Tasks: 1 (limit: 9420) Memory: 1.2M CGroup: /system.slice/ssh.service └─10573 sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups 10月 25 16:58:06 pdsyw-pc systemd[1]: Starting OpenBSD Secure Shell server... 10月 25 16:58:06 pdsyw-pc sshd[10573]: Server listening on 0.0.0.0 port 22. 10月 25 16:58:06 pdsyw-pc sshd[10573]: Server listening on :: port 22. 10月 25 16:58:06 pdsyw-pc systemd[1]: Started OpenBSD Secure Shell server. root@pdsyw-pc:~#
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
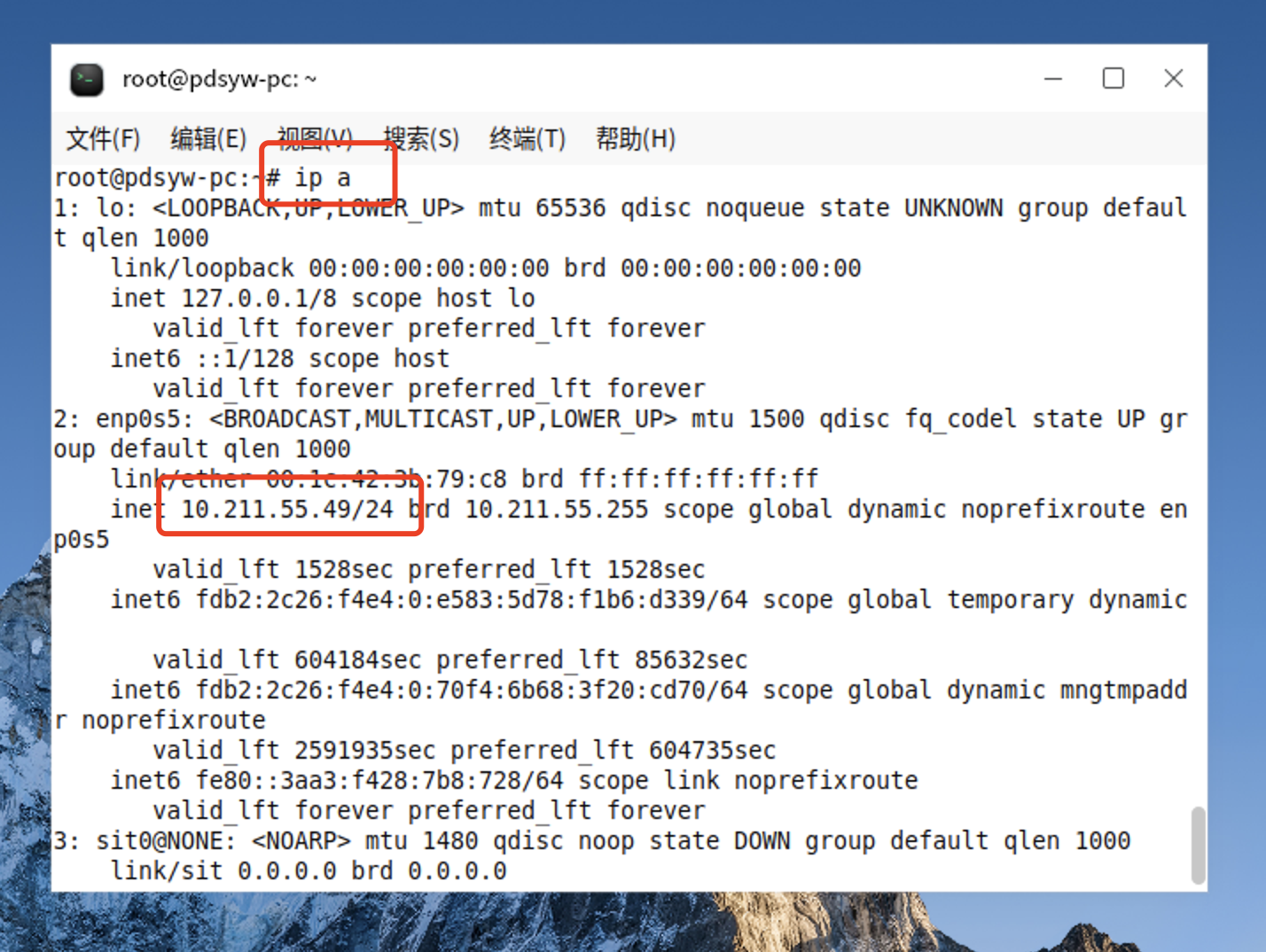
4、查看IP地址
root@pdsyw-pc:~# ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: enp0s5: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000 link/ether 00:1c:42:3b:79:c8 brd ff:ff:ff:ff:ff:ff inet 10.211.55.49/24 brd 10.211.55.255 scope global dynamic noprefixroute enp0s5 valid_lft 1564sec preferred_lft 1564sec inet6 fdb2:2c26:f4e4:0:e583:5d78:f1b6:d339/64 scope global temporary dynamic valid_lft 604445sec preferred_lft 85893sec inet6 fdb2:2c26:f4e4:0:70f4:6b68:3f20:cd70/64 scope global dynamic mngtmpaddr noprefixroute valid_lft 2591920sec preferred_lft 604720sec inet6 fe80::3aa3:f428:7b8:728/64 scope link noprefixroute valid_lft forever preferred_lft forever 3: sit0@NONE: <NOARP> mtu 1480 qdisc noop state DOWN group default qlen 1000 link/sit 0.0.0.0 brd 0.0.0.0 4: ip6tnl0@NONE: <NOARP> mtu 1452 qdisc noop state DOWN group default qlen 1000 link/tunnel6 :: brd :: root@pdsyw-pc:~#
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
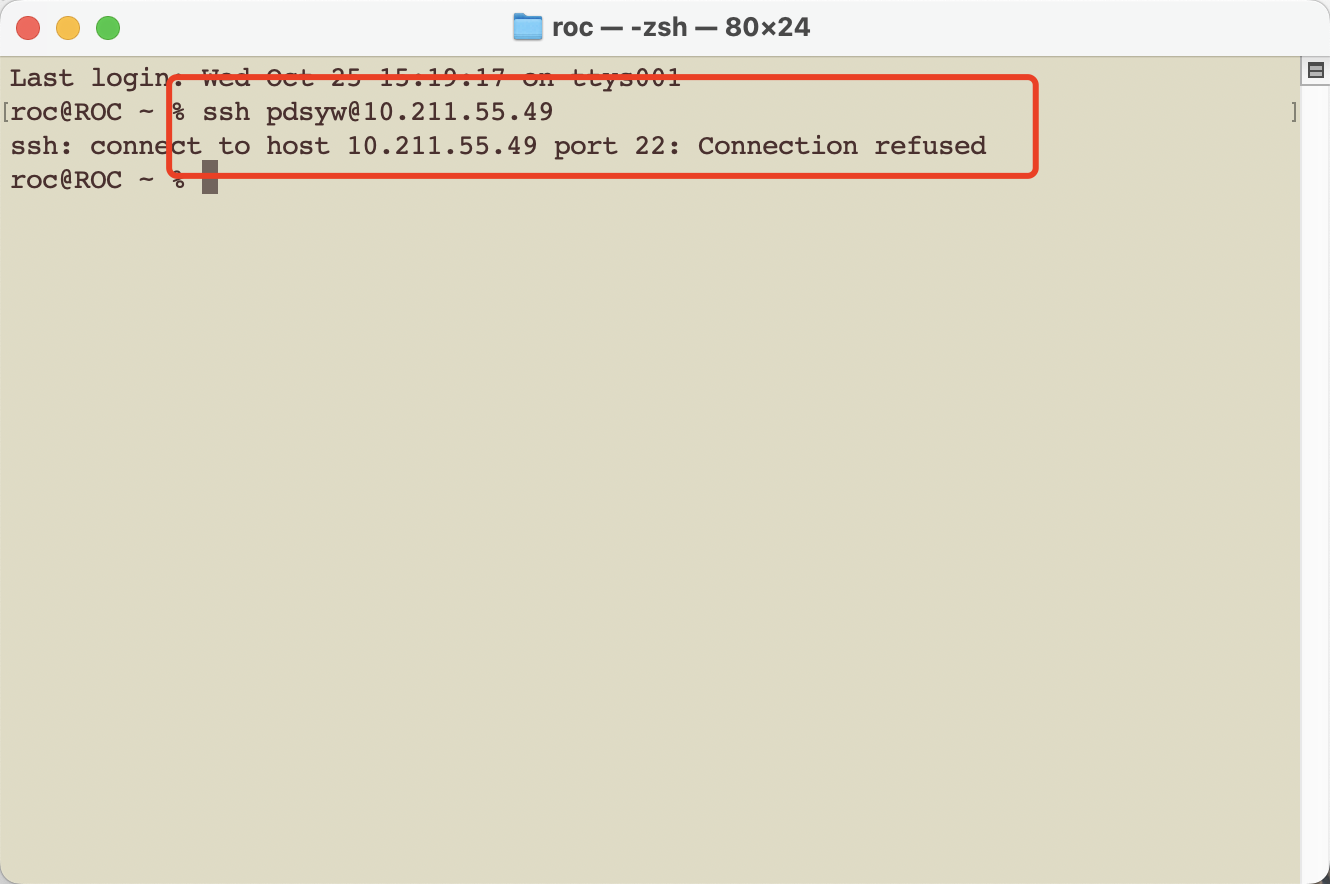
5、使用远程连接,发现连接失败
Last login: Wed Oct 25 15:19:17 on ttys001
roc@ROC ~ % ssh pdsyw@10.211.55.49
ssh: connect to host 10.211.55.49 port 22: Connection refused
roc@ROC ~ %
- 1
- 2
- 3
- 4
6、点击安全中心高级配置

7、添加22端口放开的防火墙
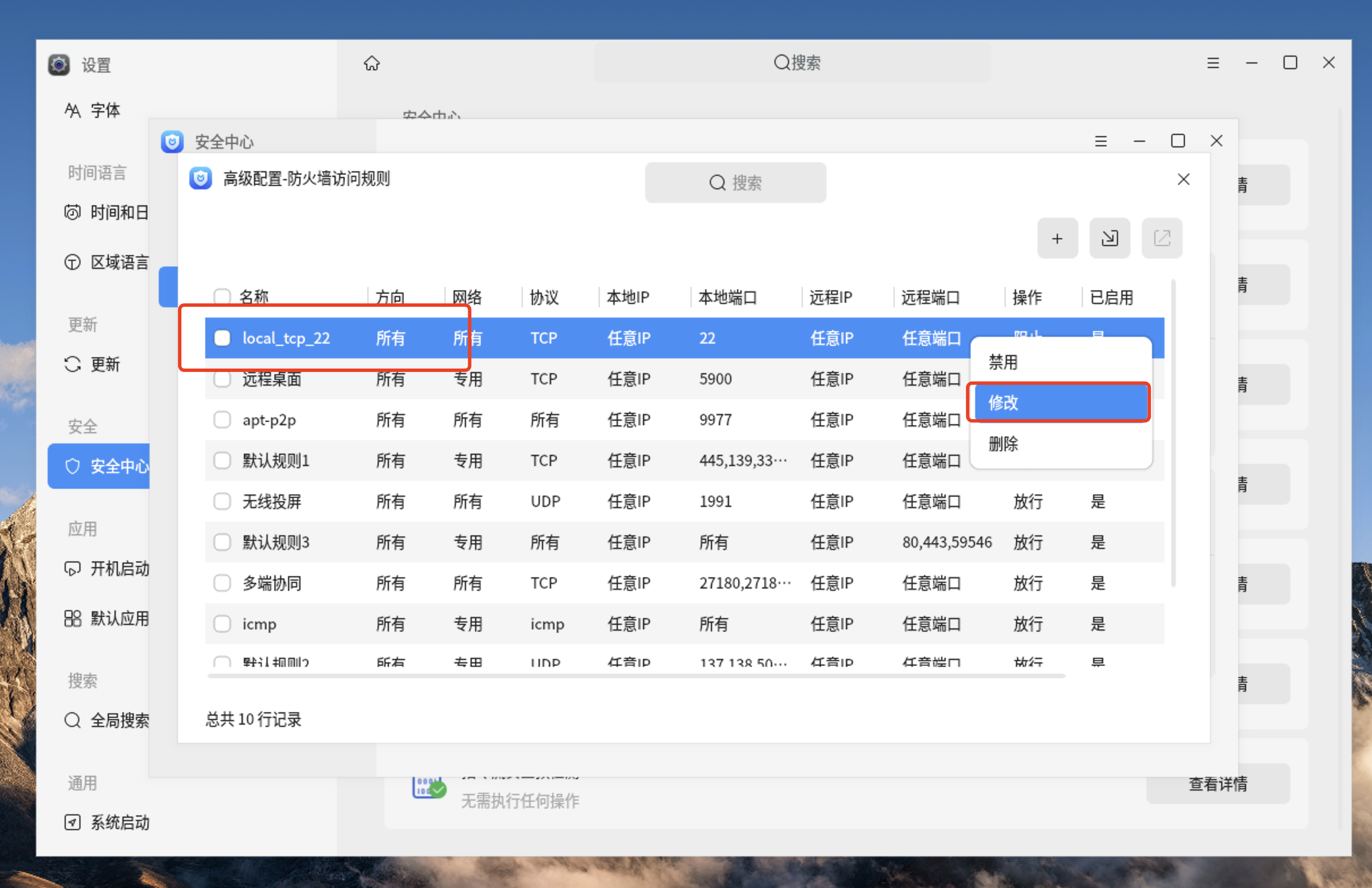
8、22端口放行

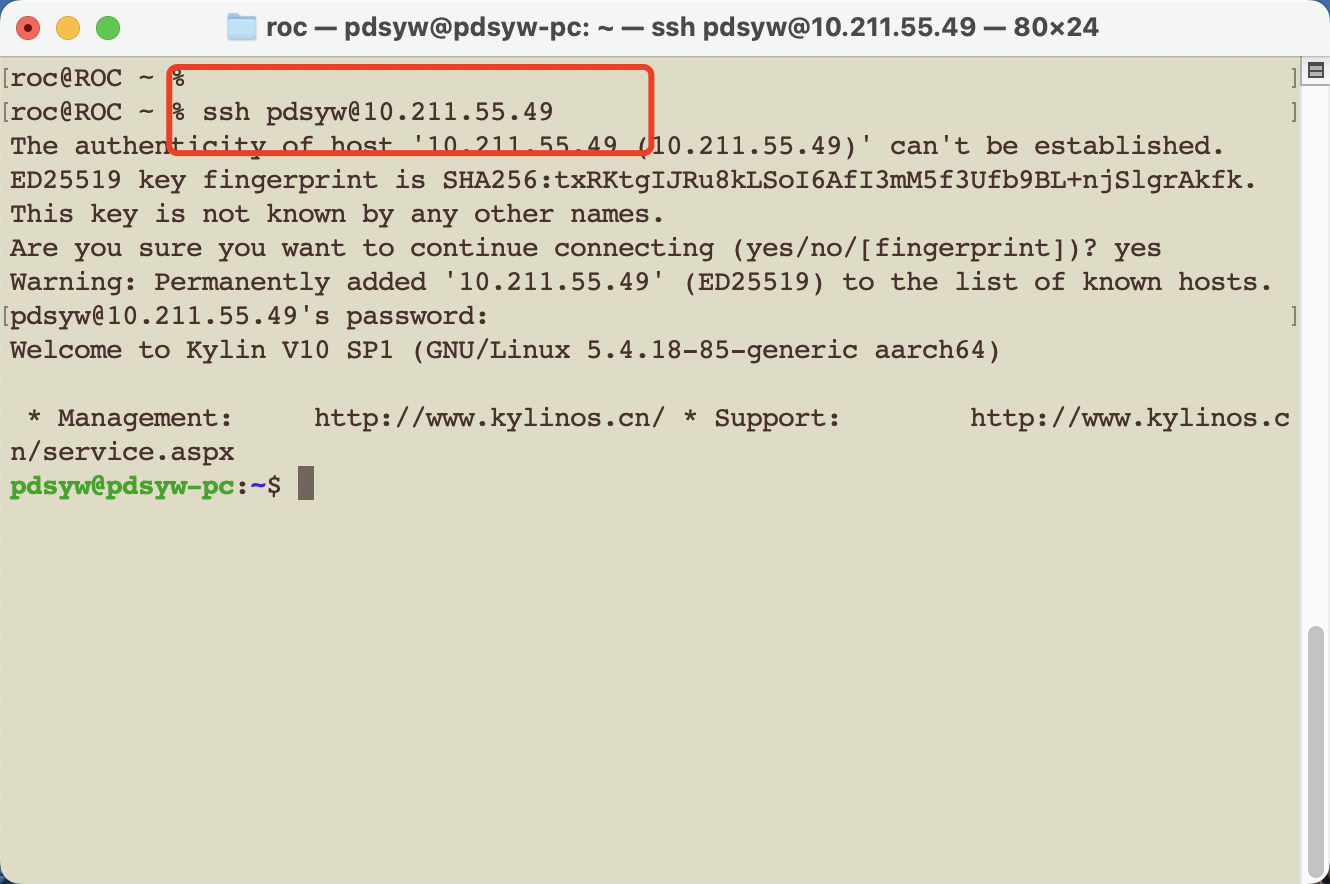
9、使用ssh连接成功
roc@ROC ~ % ssh pdsyw@10.211.55.49
The authenticity of host '10.211.55.49 (10.211.55.49)' can't be established.
ED25519 key fingerprint is SHA256:txRKtgIJRu8kLSoI6AfI3mM5f3Ufb9BL+njSlgrAkfk.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.211.55.49' (ED25519) to the list of known hosts.
pdsyw@10.211.55.49's password:
Welcome to Kylin V10 SP1 (GNU/Linux 5.4.18-85-generic aarch64)
* Management: http://www.kylinos.cn/ * Support: http://www.kylinos.cn/service.aspx
pdsyw@pdsyw-pc:~$
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
10、删除防火墙配置

11、再次使用ssh连接,发现连接失败
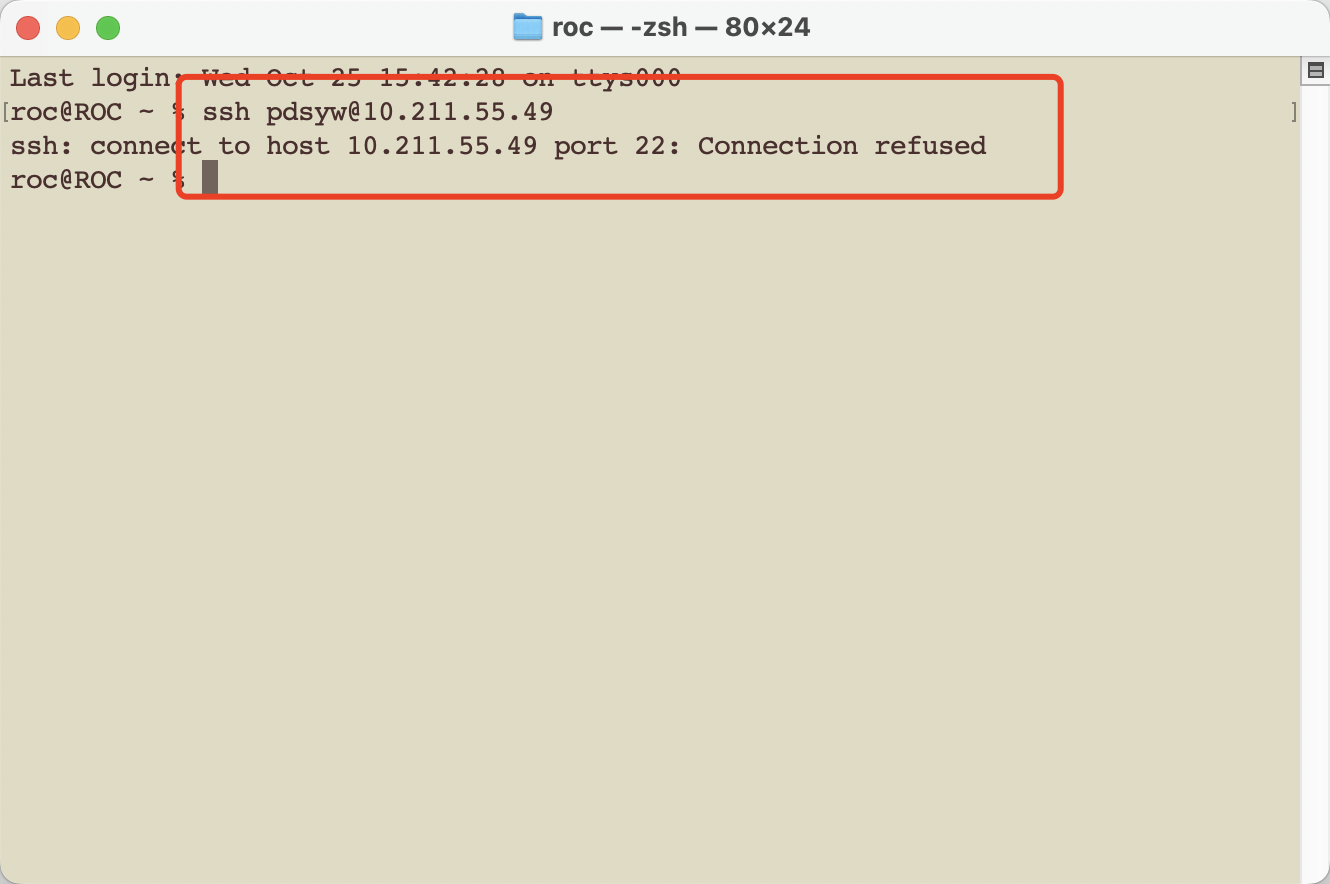
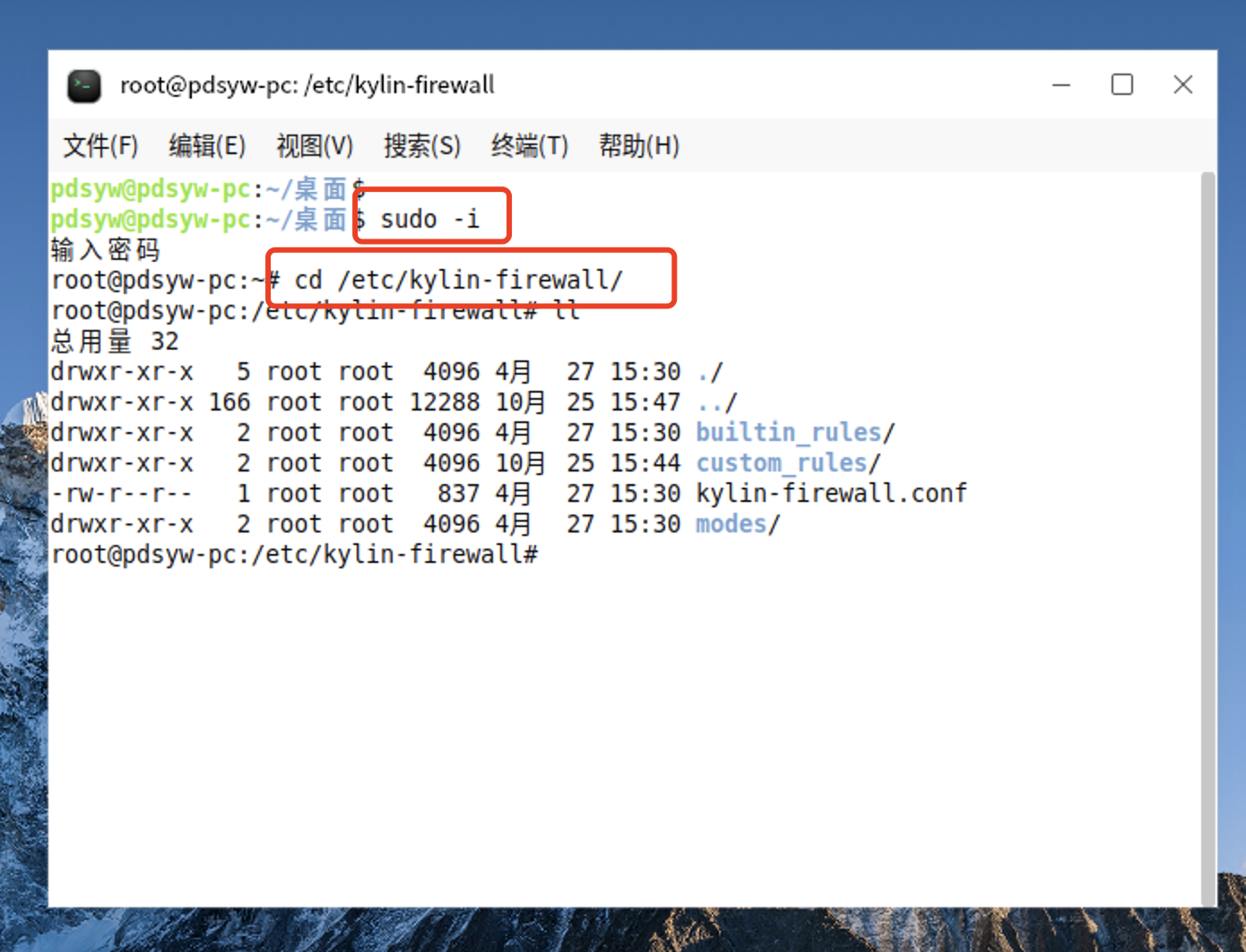
12、进入/etc/kylin-firewall/路径
pdsyw@pdsyw-pc:~/桌面$ sudo -i
root@pdsyw-pc:~# cd /etc/kylin-firewall/
root@pdsyw-pc:/etc/kylin-firewall# ll
总用量 32
drwxr-xr-x 5 root root 4096 4月 27 15:30 ./
drwxr-xr-x 165 root root 12288 10月 25 16:58 ../
drwxr-xr-x 2 root root 4096 4月 27 15:30 builtin_rules/
drwxr-xr-x 2 root root 4096 4月 27 15:30 custom_rules/
-rw-r--r-- 1 root root 837 4月 27 15:30 kylin-firewall.conf
drwxr-xr-x 2 root root 4096 4月 27 15:30 modes/
root@pdsyw-pc:/etc/kylin-firewall#
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
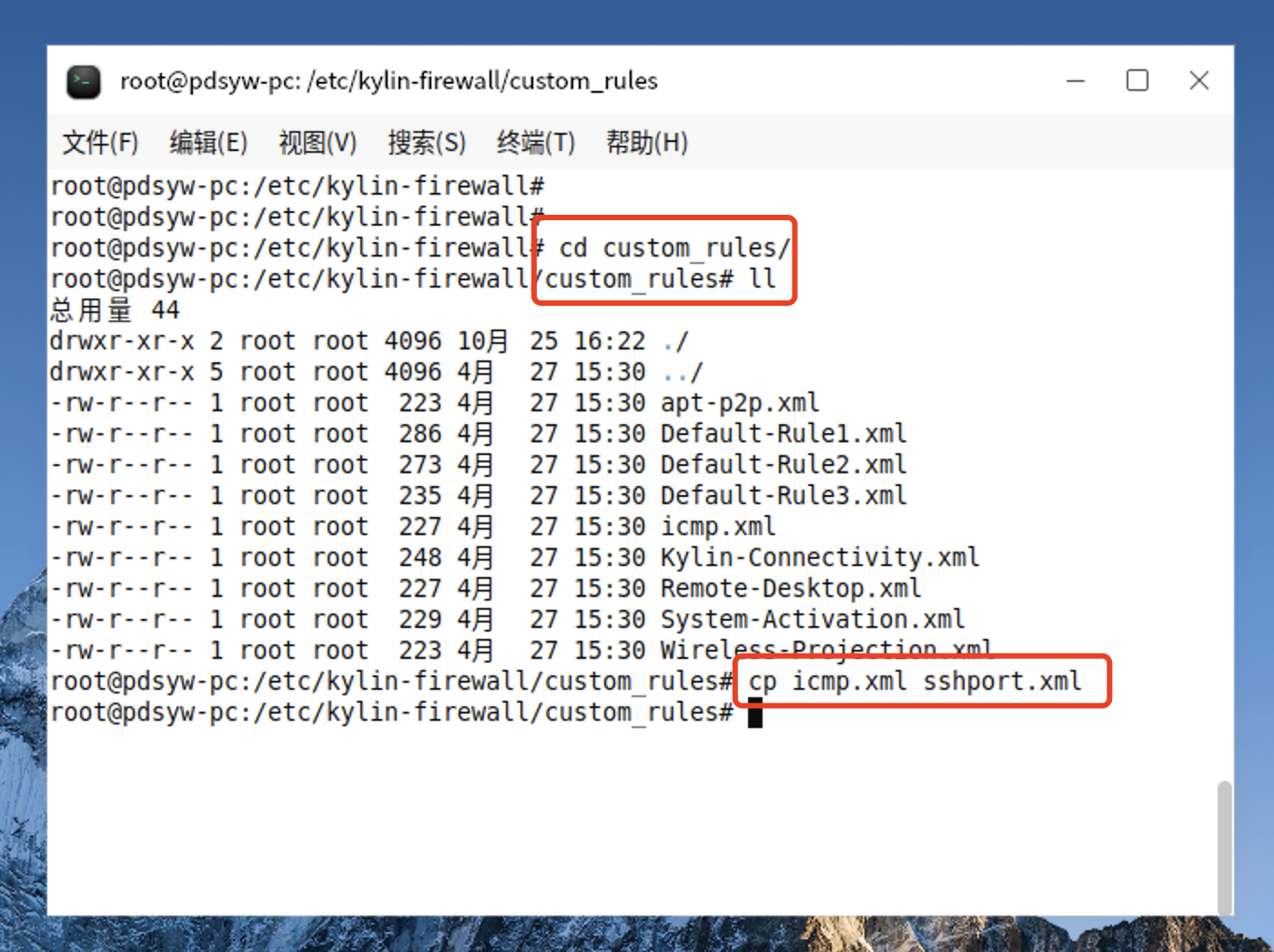
13、进入 custom_rules/下拷贝icmp.xml为sshport.xml
root@pdsyw-pc:/etc/kylin-firewall# cd custom_rules/ root@pdsyw-pc:/etc/kylin-firewall/custom_rules# ll 总用量 44 drwxr-xr-x 2 root root 4096 4月 27 15:30 ./ drwxr-xr-x 5 root root 4096 4月 27 15:30 ../ -rw-r--r-- 1 root root 223 4月 27 15:30 apt-p2p.xml -rw-r--r-- 1 root root 286 4月 27 15:30 Default-Rule1.xml -rw-r--r-- 1 root root 273 4月 27 15:30 Default-Rule2.xml -rw-r--r-- 1 root root 235 4月 27 15:30 Default-Rule3.xml -rw-r--r-- 1 root root 227 4月 27 15:30 icmp.xml -rw-r--r-- 1 root root 248 4月 27 15:30 Kylin-Connectivity.xml -rw-r--r-- 1 root root 227 4月 27 15:30 Remote-Desktop.xml -rw-r--r-- 1 root root 229 4月 27 15:30 System-Activation.xml -rw-r--r-- 1 root root 223 4月 27 15:30 Wireless-Projection.xml root@pdsyw-pc:/etc/kylin-firewall/custom_rules# cp icmp.xml sshport.xml root@pdsyw-pc:/etc/kylin-firewall/custom_rules#
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
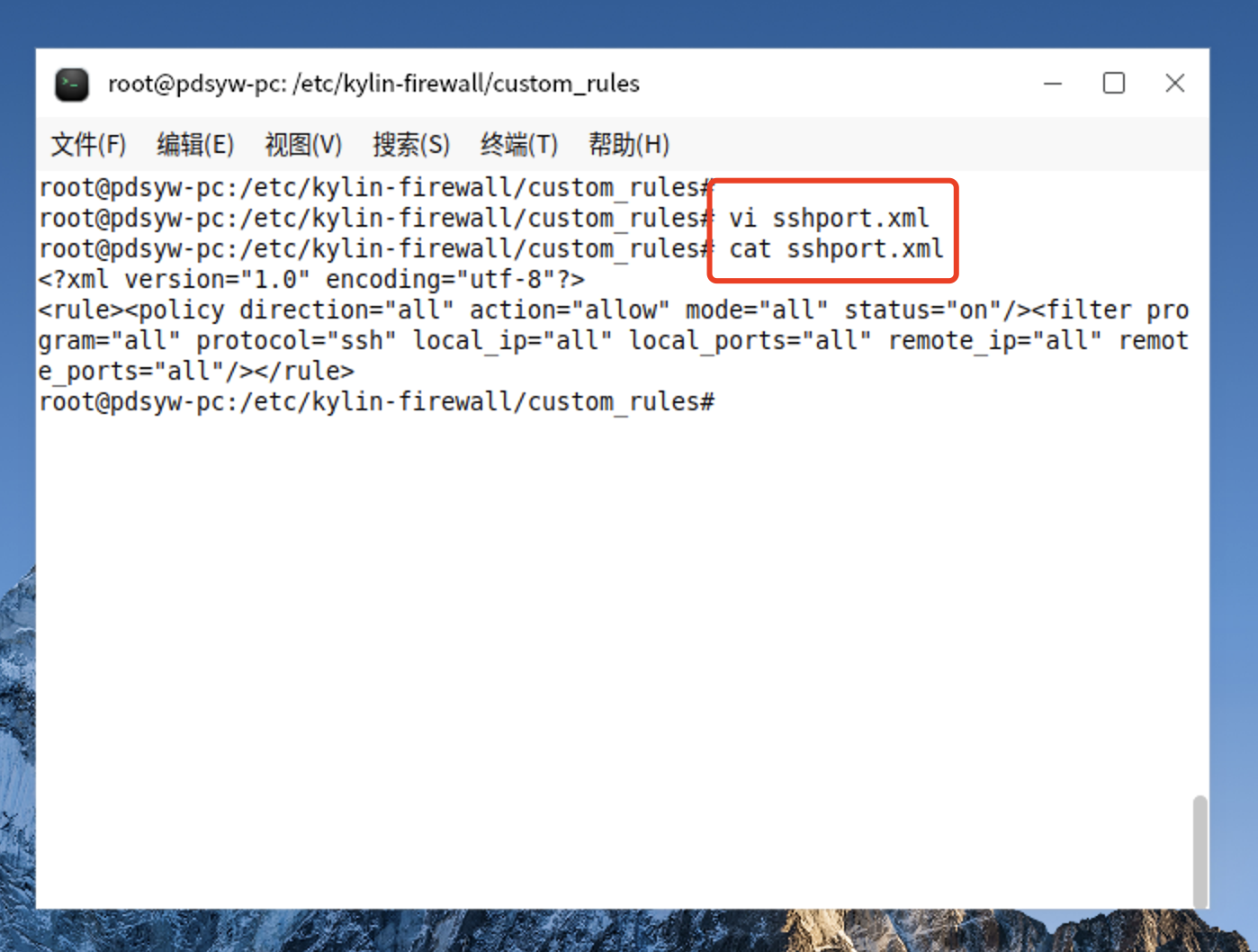
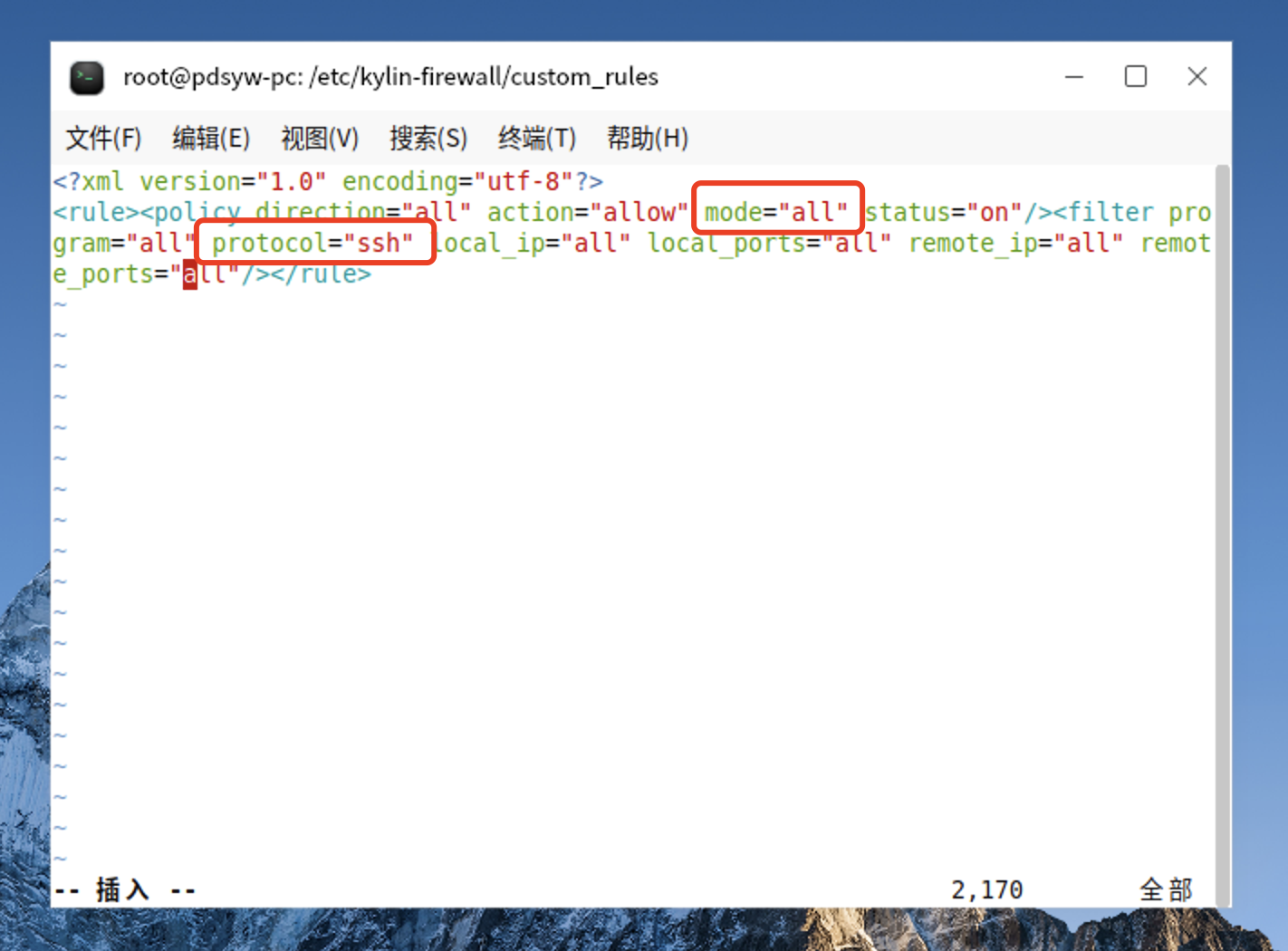
14、编辑sshport.xml文件
root@pdsyw-pc:/etc/kylin-firewall/custom_rules# vi sshport.xml
root@pdsyw-pc:/etc/kylin-firewall/custom_rules# cat sshport.xml
<?xml version="1.0" encoding="utf-8"?>
<rule><policy direction="all" action="allow" mode="all" status="on"/><filter program="all" protocol="ssh" local_ip="all" local_ports="all" remote_ip="all" remote_ports="all"/></rule>
root@pdsyw-pc:/etc/kylin-firewall/custom_rules#
- 1
- 2
- 3
- 4
- 5
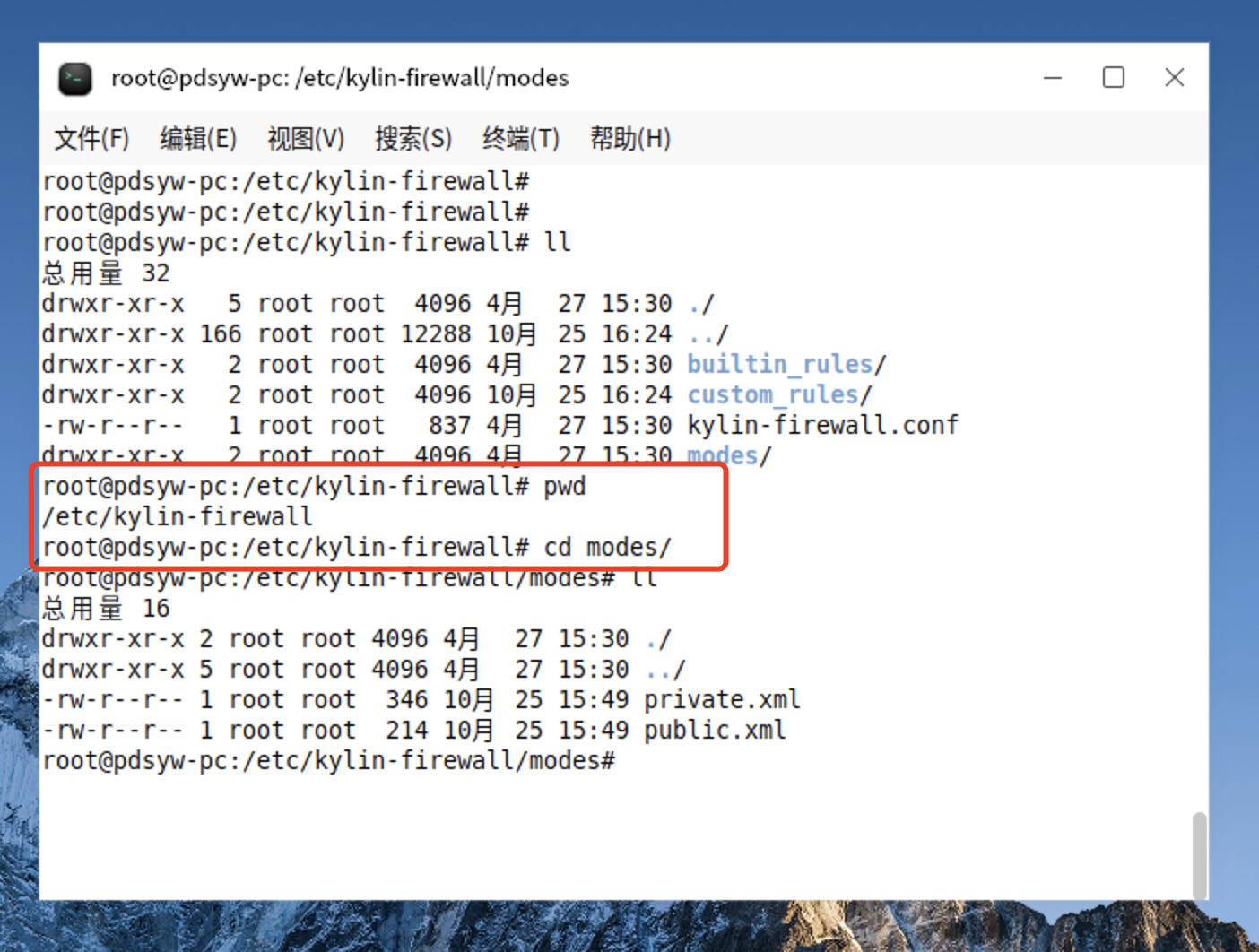
15、进入/etc/kylin-firewall/modes路径下
root@pdsyw-pc:/etc/kylin-firewall# root@pdsyw-pc:/etc/kylin-firewall# ll 总用量 32 drwxr-xr-x 5 root root 4096 4月 27 15:30 ./ drwxr-xr-x 165 root root 12288 10月 25 17:00 ../ drwxr-xr-x 2 root root 4096 4月 27 15:30 builtin_rules/ drwxr-xr-x 2 root root 4096 10月 25 17:00 custom_rules/ -rw-r--r-- 1 root root 837 4月 27 15:30 kylin-firewall.conf drwxr-xr-x 2 root root 4096 4月 27 15:30 modes/ root@pdsyw-pc:/etc/kylin-firewall# pwd /etc/kylin-firewall root@pdsyw-pc:/etc/kylin-firewall# cd modes/ root@pdsyw-pc:/etc/kylin-firewall/modes# ll 总用量 16 drwxr-xr-x 2 root root 4096 4月 27 15:30 ./ drwxr-xr-x 5 root root 4096 4月 27 15:30 ../ -rw-r--r-- 1 root root 346 4月 27 15:30 private.xml -rw-r--r-- 1 root root 214 4月 27 15:30 public.xml root@pdsyw-pc:/etc/kylin-firewall/modes#
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
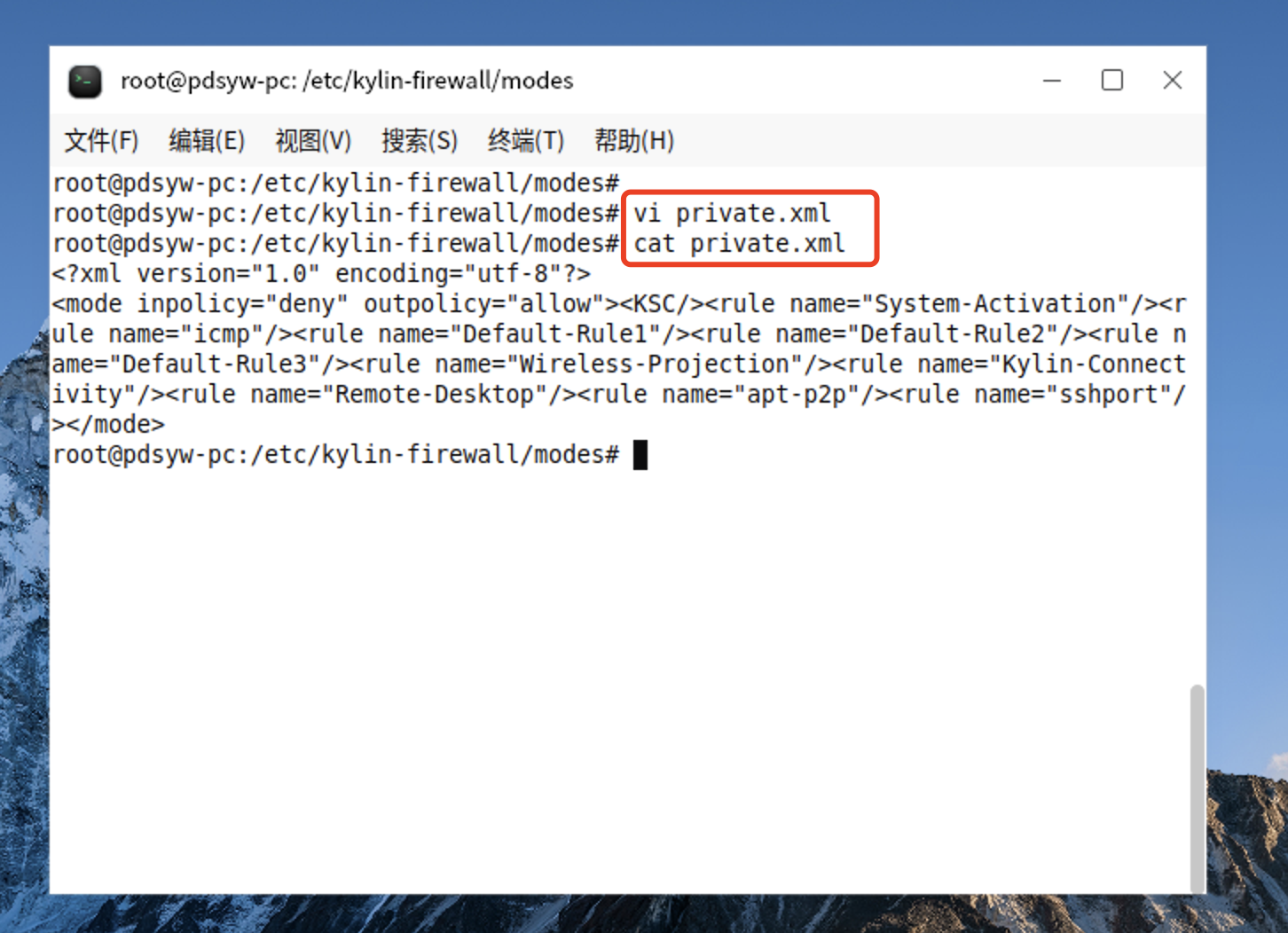
16、编辑private.xml文件
root@pdsyw-pc:/etc/kylin-firewall/modes# vi private.xml
root@pdsyw-pc:/etc/kylin-firewall/modes# cat private.xml
<?xml version="1.0" encoding="utf-8"?>
<mode inpolicy="deny" outpolicy="allow"><KSC/><rule name="System-Activation"/><rule name="icmp"/><rule name="Default-Rule1"/><rule name="Default-Rule2"/><rule name="Default-Rule3"/><rule name="Wireless-Projection"/><rule name="Kylin-Connectivity"/><rule name="Remote-Desktop"/><rule name="apt-p2p"/><rule name="sshport"/></mode>
root@pdsyw-pc:/etc/kylin-firewall/modes#
- 1
- 2
- 3
- 4
- 5

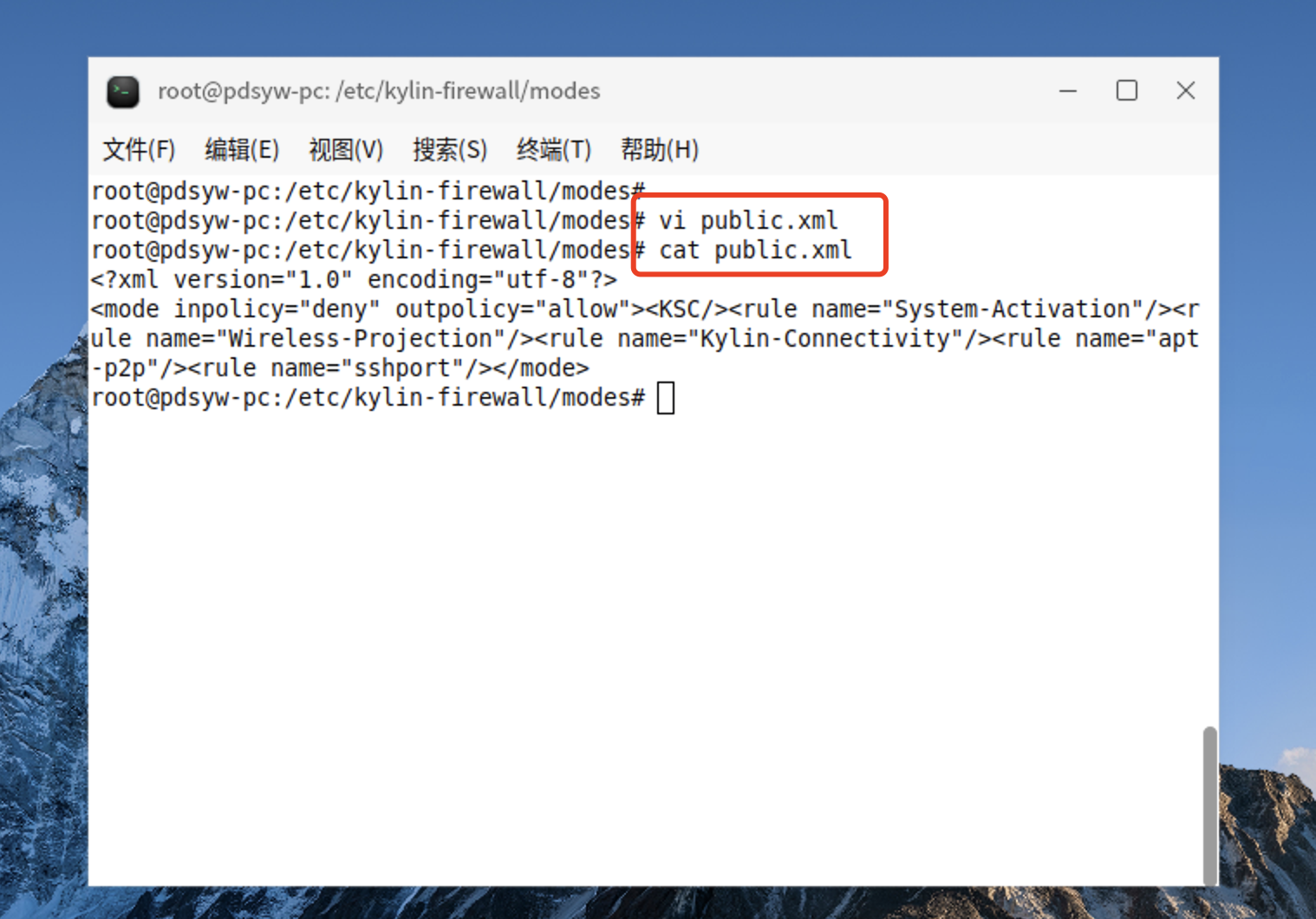
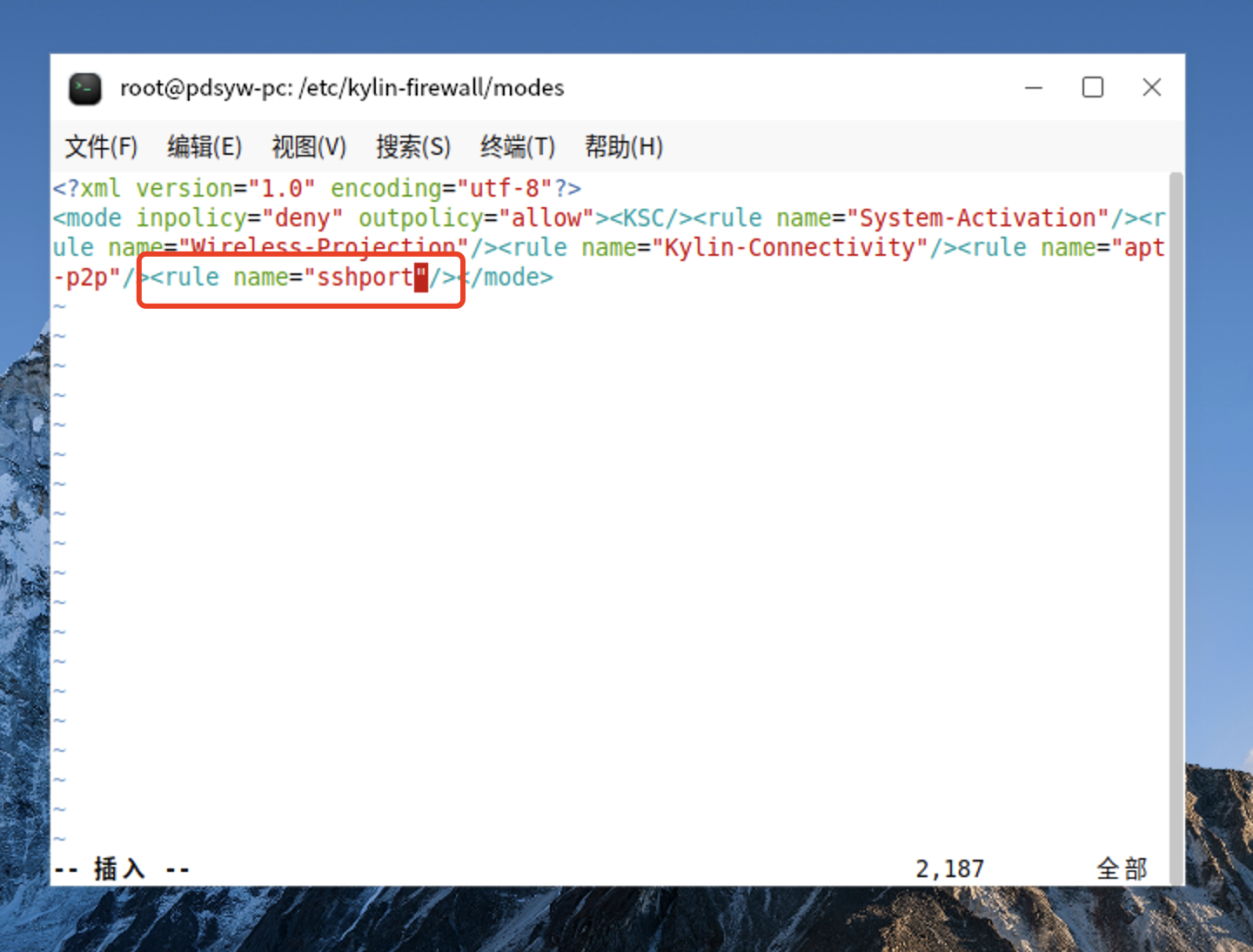
17、编辑public.xml文件
root@pdsyw-pc:/etc/kylin-firewall/modes# vi public.xml
root@pdsyw-pc:/etc/kylin-firewall/modes# cat public.xml
<?xml version="1.0" encoding="utf-8"?>
<mode inpolicy="deny" outpolicy="allow"><KSC/><rule name="System-Activation"/><rule name="Wireless-Projection"/><rule name="Kylin-Connectivity"/><rule name="apt-p2p"/><rule name="sshport"/></mode>
root@pdsyw-pc:/etc/kylin-firewall/modes#
- 1
- 2
- 3
- 4
- 5
18、重启系统
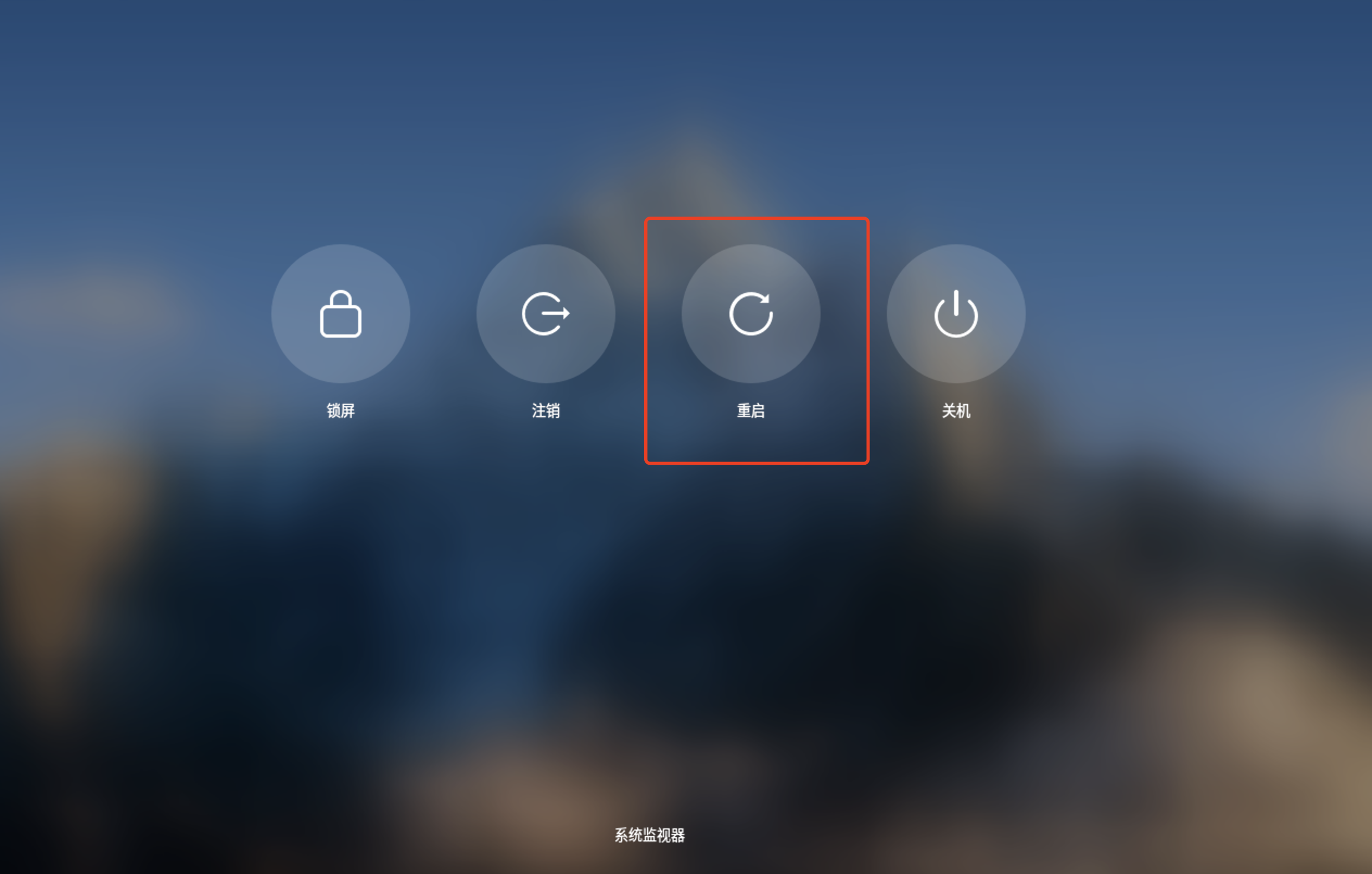
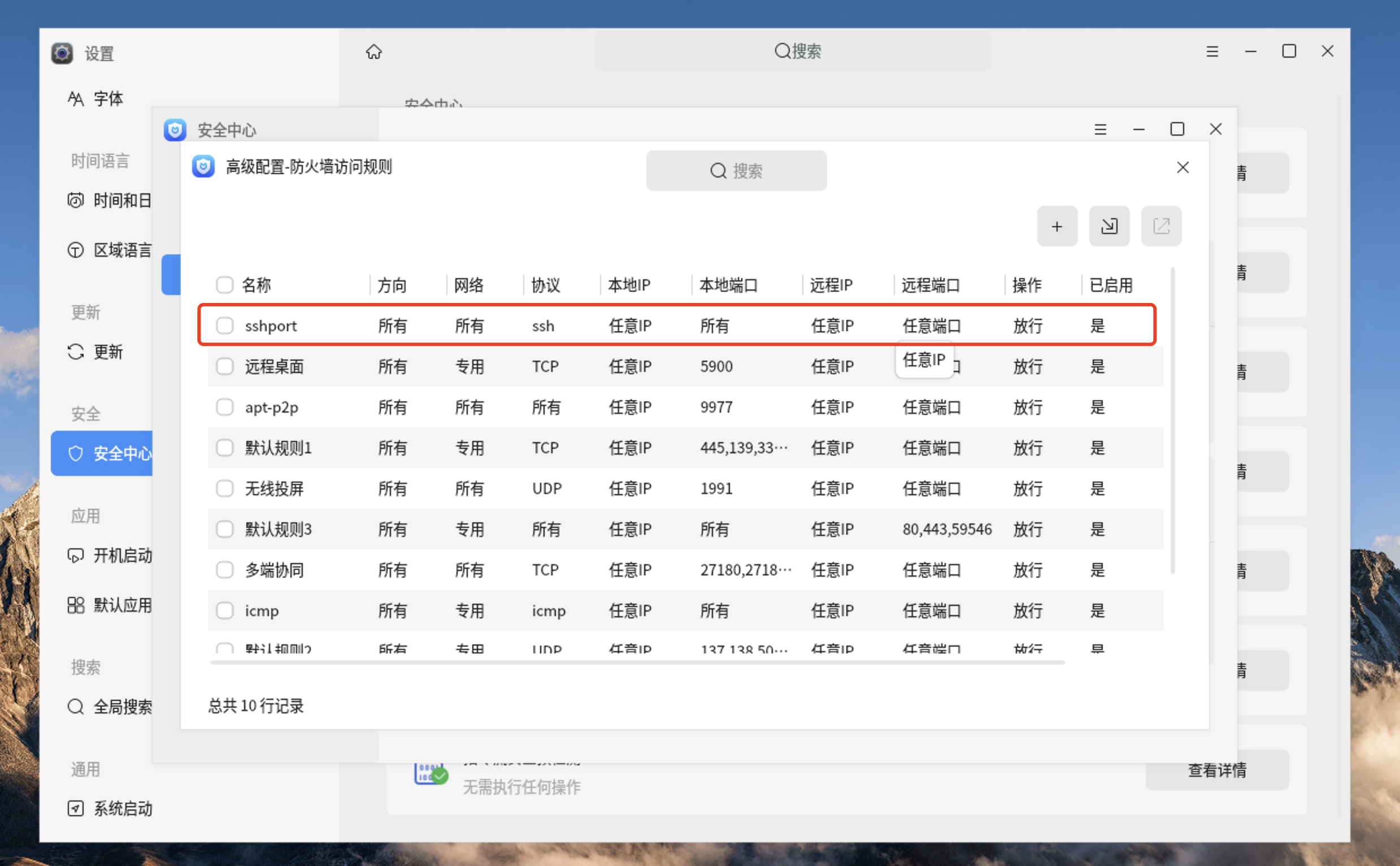
19、安全中心防火墙配置已经自动添加了
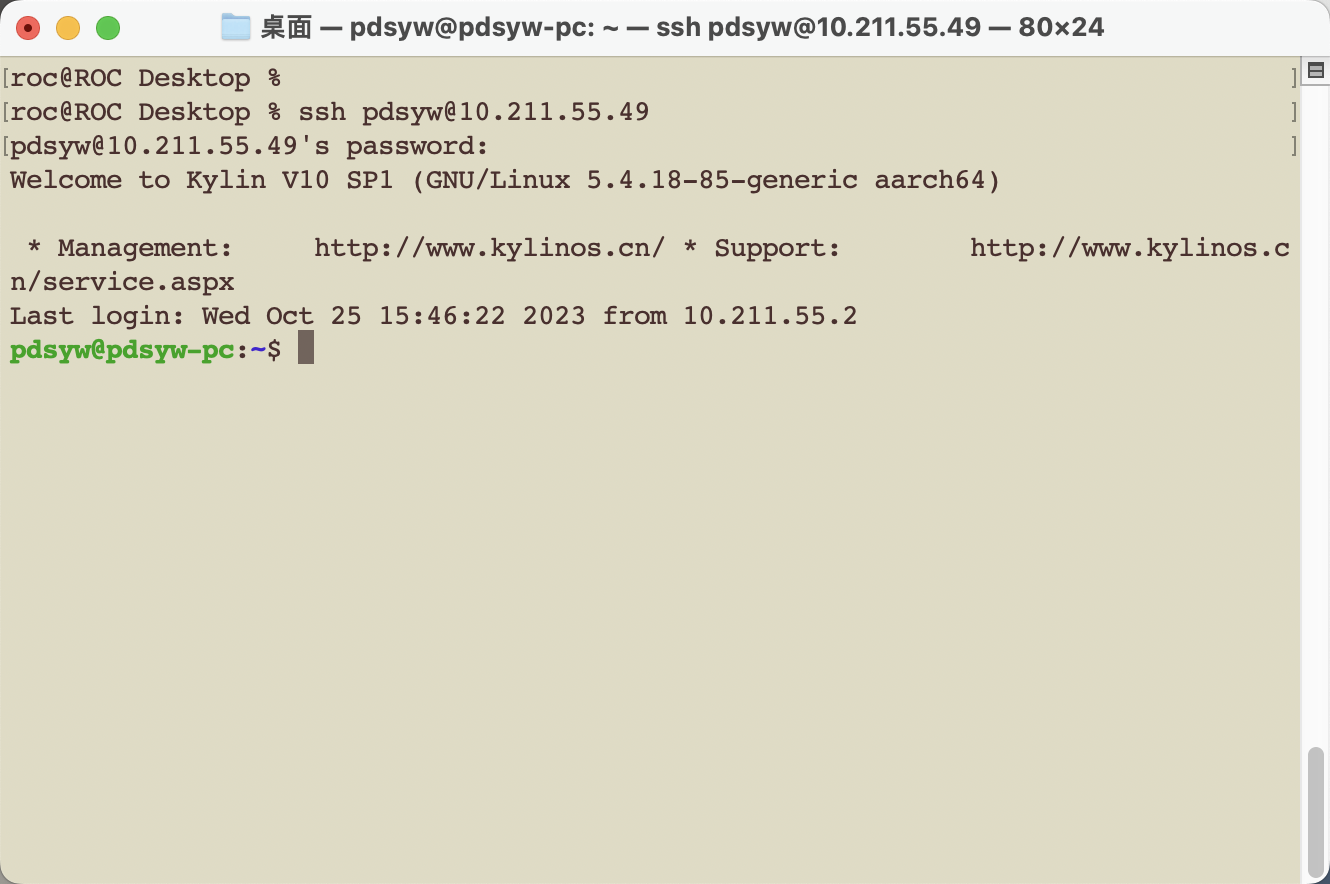
20、使用ssh连接成功
roc@ROC Desktop % ssh pdsyw@10.211.55.49
pdsyw@10.211.55.49's password:
Welcome to Kylin V10 SP1 (GNU/Linux 5.4.18-85-generic aarch64)
* Management: http://www.kylinos.cn/ * Support: http://www.kylinos.cn/service.aspx
Last login: Wed Oct 25 15:46:22 2023 from 10.211.55.2
pdsyw@pdsyw-pc:~$
- 1
- 2
- 3
- 4
- 5
- 6
- 7
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/小蓝xlanll/article/detail/189507
推荐阅读
相关标签



