- 1VUE学习第五天(父子组件传参与路由)_vue 父子路由
- 2Maven学习&Git学习_熟悉管理及版本控制工具: maven ,git 。
- 3基于微信小程序的运动场馆预约小程序开发笔记_体育馆预约小程序开发
- 4@drawable" href="/w/从前慢现在也慢/article/detail/144679" target="_blank">Android产品研发(二)-->启动页优化_"
- @drawable
- 5基于springboot仓库管理系统(完美运行、数据库源代码、可远程调试)_spring boot的仓库管理系统
- 6SQL注入的测试_sql注入异常检测是什么
- 7Promise面试题合集(问题+答案)_前端promise面试题
- 8React入门 制作简单的todolist_制作todolist
- 9python 伪多线程_python伪多线程
- 10信息科技风险管理:合规管理、技术防控与数字化【十二期】_信息科技风险管理提升
37.云原生之springcloud+k8s+GitOps+istio+安全实践
赞
踩
文章目录
准备工作
- 安装gitlab,将https://gitee.com/zhouwei1996/spring-cloud-bookinfo.git迁移至gitlab
- gitlab中创建全局变量,如镜像仓库账号密码,保证gitlab-ci.yaml中内容安全
- 共享runner创建,获取token如下:glrt-wfzAecJmszsZb3GorS8J
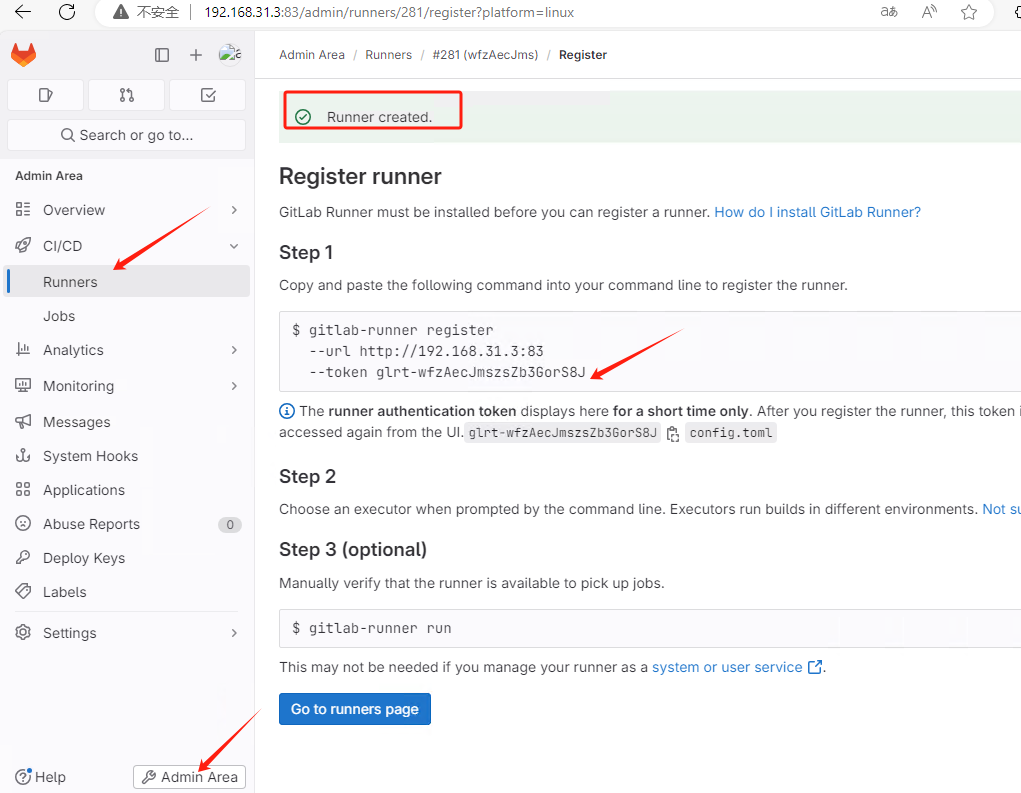
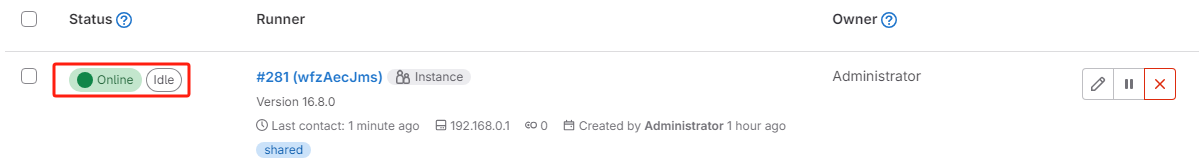
- 安装gitlab-runner,参考:22.云原生之GitLab CICD实战及解析
#以下两个在gitlab页面获取
gitlabUrl: http://192.168.31.3:83/
runnerRegistrationToken: "glrt-wfzAecJmszsZb3GorS8J" #gitlab-runner注册用到的tocken
concurrent: 10 #最大作业并发数
checkInterval: 30 #新作业检查间隔
tags: "shared" #runner的标签
#rbac权限打开
rbac:
create: true
resources: ["pods", "pods/exec", "secrets","configmaps"]
verbs: ["get", "list", "watch", "create", "patch", "delete","update"]
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
修改ConfigMap下config.template.toml配置:
[[runners]]
builds_dir = "/builds"
[runners.kubernetes]
namespace = "base"
image = "alpine"
pull_policy = "if-not-present" # 拉取镜像策略,本地有是有本地无需拉取
[[runners.kubernetes.volumes.pvc]] # 挂载数据卷持久化
name = "k8s-running-pod-data"
mount_path = "/builds"
[[runners.kubernetes.volumes.host_path]] # 使用docker命令需要配置引擎
name = "docker"
mount_path = "/var/run/docker.sock"
host_path = "/var/run/docker.sock"
[[runners.kubernetes.host_aliases]] # 用于解析内网中的harbor域名
ip = "192.168.31.11"
hostnames = ["harbor域名"]
[[runners.kubernetes.host_aliases]] # 用于解析k8s集群中Kubernetes API Server 的地址
ip = "192.168.31.21" # k8s集群master ip
hostnames = ["lb.kubesphere.local"]
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 安装harbor,此处小编使用阿里云镜像仓库
- 安装sealed-secrets,参考24.云原生ArgoCD高级之数据加密seale sealed | 使用 Sealed Secrets 在 Kubernetes 中管理密钥安全
- 开启istio自动注入,参考:29.云原生KubeSphere服务网格实战之Istio安装配置
项目结构介绍
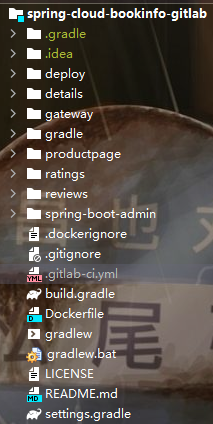
整个微服务应用中包含了5个组件
productpage 是一个由 react 开发的前端组件
gateway 是一个由 spring-cloud-gateway 提供的 API 网关服务
details 是一个 spring-cloud 微服务,提供了书籍详情 API
reviews提供了基础的书籍评论信息, review-v2 在 review-v1 的基础之上额外的提供了评分数据,依赖 ratings 服务
ratings 是一个 golang 开发的微服务组件
配置安全测试
改造Springcloud-bookinfo中Gateway网关,将reviews权重加密,从Secret中获取权重值进行测试
ConfigMap
ConfigMap 主要用于存储非敏感的配置数据
application.yml中经常会配置账号密码这些,此时资源清单中这些内容就不能以明文暴露到gitlab中
server:
port: ${SERVER_PORT:8080}
spring:
application:
name: gateway
cloud:
gateway:
routes:
- id: ratings
uri: lb://ratings
predicates:
- Path=/api/v1/reviews/*/ratings
- id: details
uri: lb://details
predicates:
- Path=/api/v1/products/*
- id: reviews-v1
uri: lb://reviews-v1
predicates:
- Path=/api/v1/products/*/reviews
- Weight=reviews, ${reviews-v1:0}
- id: reviews-v2
uri: lb://reviews-v2
predicates:
- Path=/api/v1/products/*/reviews
- Weight=reviews, ${reviews-v2:100}
management:
endpoints:
web:
exposure:
include: "*"
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
此时访问页面一直是红星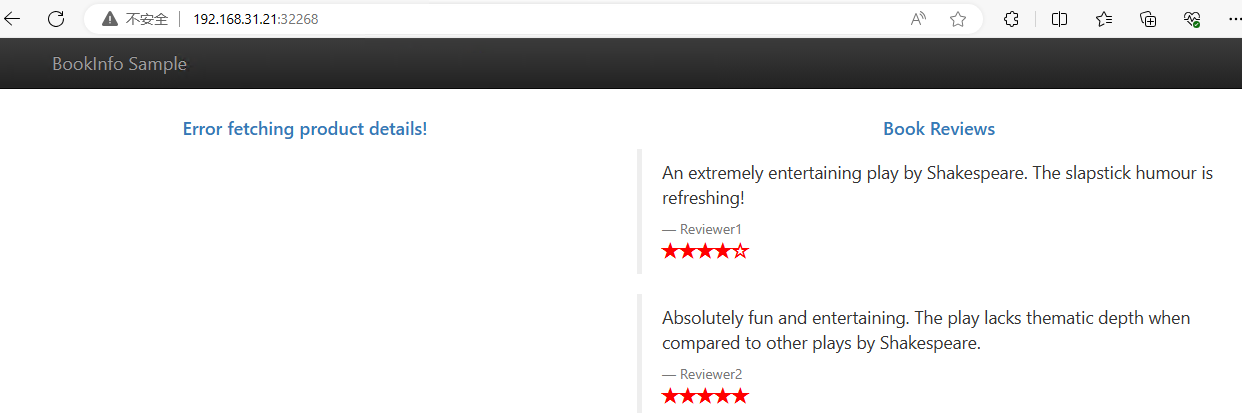
Secret
Secret 用于存储敏感数据,例如密码、API 密钥等。
kind: Secret
apiVersion: v1
metadata:
name: gateway
namespace: spring-cloud
annotations:
kubesphere.io/creator: admin
data:
reviews-v1: NTA=
reviews-v2: NTA=
type: Opaque
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
明文数据如下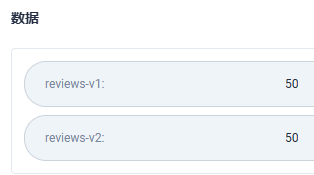
使用Secret中数据的方式
- 通过环境变量传递Secret中的数据:
- 在 Pod 的配置文件中,将 Secret 中的数据通过环境变量传递给容器。你可以在 Pod 的 spec.containers.env 部分中设置环境变量,将 Secret 中的数据作为值传递给容器。示例:
env:
- name: server.port
valueFrom:
secretKeyRef:
name: details
key: server-port
- 1
- 2
- 3
- 4
- 5
- 6
- 通过卷挂载Secret中的数据:
- 你还可以将 Secret 中的数据作为文件挂载到 Pod 中。在 Pod 的配置文件中,可以通过 volumes 和 volumeMounts 将 Secret 中的数据挂载到容器中。示例:
volumes:
- name: secret-volume
secret:
secretName: my-secret
containers:
volumeMounts:
- name: secret-volume
mountPath: /etc/my-app
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
这样,你可以在 ConfigMap 中引用这些环境变量或挂载的文件,间接地使用 Secret 中的数据。记住,Secret 中的数据是加密存储的,应该小心处理以确保安全性。
Deployment使用Secret配置
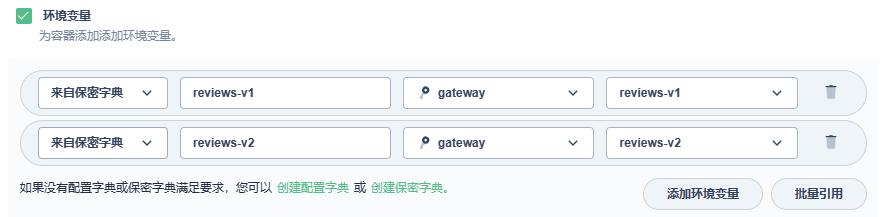
env:
- name: reviews-v1
valueFrom:
secretKeyRef:
name: gateway
key: reviews-v1
- name: reviews-v2
valueFrom:
secretKeyRef:
name: gateway
key: reviews-v2
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
访问页面测试,多次访问出现v1和v2版本页面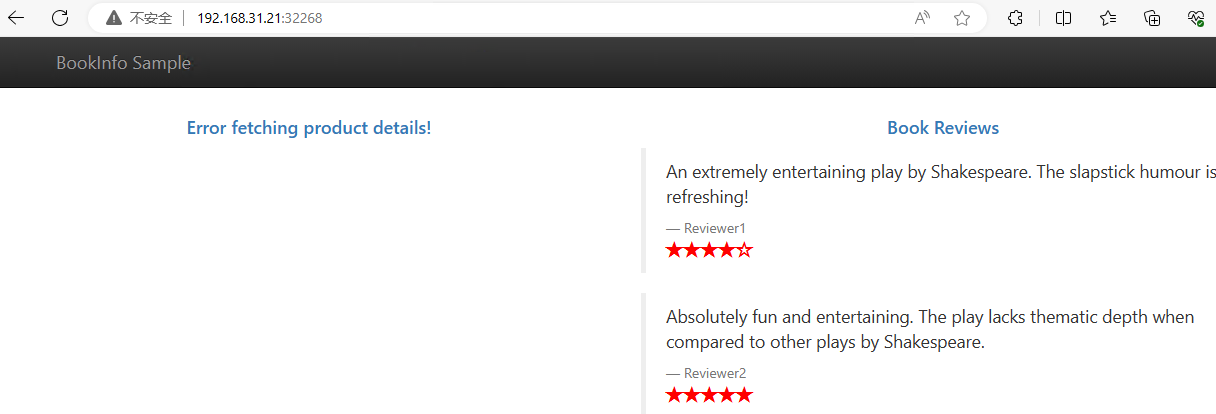
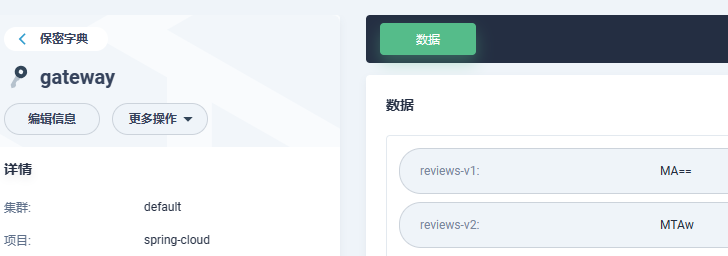
Secret加密
- 创建bookinfo-gateway-secret.yaml
kind: Secret
apiVersion: v1
metadata:
name: gateway
namespace: spring-cloud
annotations:
kubesphere.io/creator: admin
data:
reviews-v1: MA==
reviews-v2: MTAw
type: Opaque
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 加密bookinfo-gateway-secret.yaml
# 备份公钥
kubeseal --fetch-cert > public-cert.pem
kubeseal --format=yaml --cert ./public-cert-0.26.0.pem < bookinfo-gateway-secret.yaml > bookinfo-gateway-secret-sealed.yaml
- 1
- 2
- 3
- 4
- 查看bookinfo-gateway-secret-sealed.yaml
apiVersion: bitnami.com/v1alpha1
kind: SealedSecret
metadata:
creationTimestamp: null
name: gateway
namespace: spring-cloud
spec:
encryptedData:
reviews-v1: AgCQ1PwFXeAitYGhDd5Pz+VFZYzsKsGUEqhK/mSQk/3Fhxut+z7lX8+fZReEAt+CPGpOObdHvTwPMeT9eCD3KrKulUgRfLU0ViJw5oU8ESXfoHOIcmAFi58ChtW3vA6Ww6bKoPmdtbKH8OVkLou+8Rw/BG3N+H3+NqSeBvLE7ITv2ZCX2eaH0pOARWG8vQfw65eAnwuYb7LyRoizlAO7eXdJ1V4r7mhqvYGIPMISFw7h3P229ZRYoXwZpOdPyfA3fb6eKQU2JBXUNWp+IT9iNImEt8j6ZGbH/Q49C+tvDRb27Yw13OzAf0QCy88ZbQr4ZixhWi7qUHv3Lhfso++/Ps8/V6svz+p2Ecfsb/+2B7cpBvTLeIH3s6IE+hm7OomnnyQT5wEenBchflsf4/PWd6AuJBm94rtquy5QmPplpy4mig3C68anSYe2fARgK4CPBgczqeVjUJVmOd0HuNjsGXnssC5j8C10y92pXNvu9f7txIANEj5UCul+ovIUZslqof3wMs7OCGsDpJTXVHCL6fF4N0EAHTgjHJgaZQIvjPm1CGmG1igK6wM4QyGmfSGtfc9mn68v1xVKFqAE3eWJsoWuMOaZ09HGwNfS8oMN1DUUjTZfZbR7iJgtAkUcrwoSKfxe4kKrXAa3RDff/9WK/WzQl5/beLNOT5XwcC8lXK43xcILH1MNqrP5zYdv+erIH3DO
reviews-v2: AgBtPBz/ANesC/HP7UVhtJbZ2g5oyI08RWck3tQ78pCJzF1w7r9s4p1YWB3zbZ+xgL+rjCnl6IVlaB5UBwsYG1EgkT/g5e0Nfxy0aUigcKu87Qvaj1zmtn3rzP/xZ1RNmcKfK8MRiU4NTj8OwhyjKYe/Qy/pPX7D53880wTdZsuhLFTyF5egZCnRdJekq297hwGH+B7cp4pCbfxoZmTjO5b8jim2YGmc1hEMFKhqObb1AyqMMTJ1G3kF2dmVenlU+jTDRGAlndZLRO9HbeGjBPtjhZuLO4sOLPp6Nd0Cjzzkxe9CylzsTT4SynKN6cgpWcYRweYnelMnVDBoa58X47quMc6LTvo7UmYobfIk//NT34r6qDZ4MR160onHxYUxtGyI3k6ZQJn2wqdDIJEWdMaY+r/DYqG7pgM4XGickNtgKS8o1UFh7fip71a5HGy0q/dPb9URtbKzzABcd91SsVnxK9QYFDFqsUblmpDkCcWm7hMSClAvE8+wvC5+s1bq6+V6QO21coXMqoulU3DVujh0zJE8VSuxIbKvzeVOs0peCNSRpxfF53DCf5JSawseKFkwNn2E47zPHSsHZ2sxQy9Wm7lrfIIsc26oyFhwBhDR416bZ7mRNyJbvjSKWN2iUtF7cLr+WMU2LFszroQMbwkBlciWA9W9pgTrV3Tv+Zi+10yTq199KxShuZ09rcEGsoXWtqQ=
template:
metadata:
annotations:
kubesphere.io/creator: admin
creationTimestamp: null
name: gateway
namespace: spring-cloud
type: Opaque
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
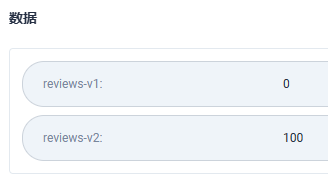
- 删除bookinfo-gateway-secret.yaml部署
- 部署bookinfo-gateway-secret-sealed.yaml
kubectl apply -f bookinfo-gateway-secret-sealed.yaml
- 1
执行上述命令会创建原始的secret,生成如下:
- 重新部署Gateway
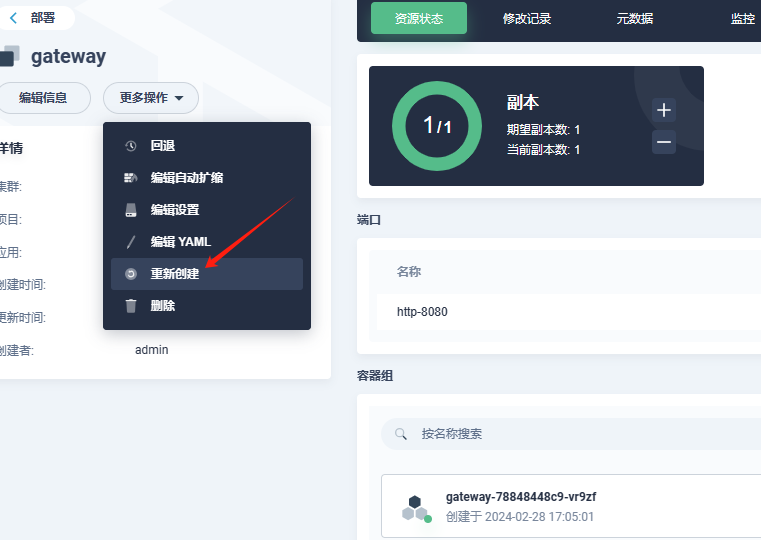
- 访问页面测试
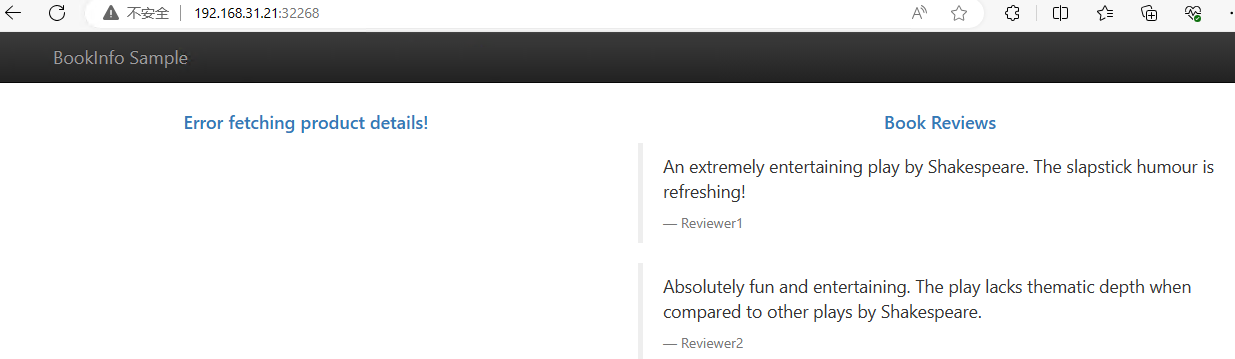
此时无论怎么访问都是显示红色星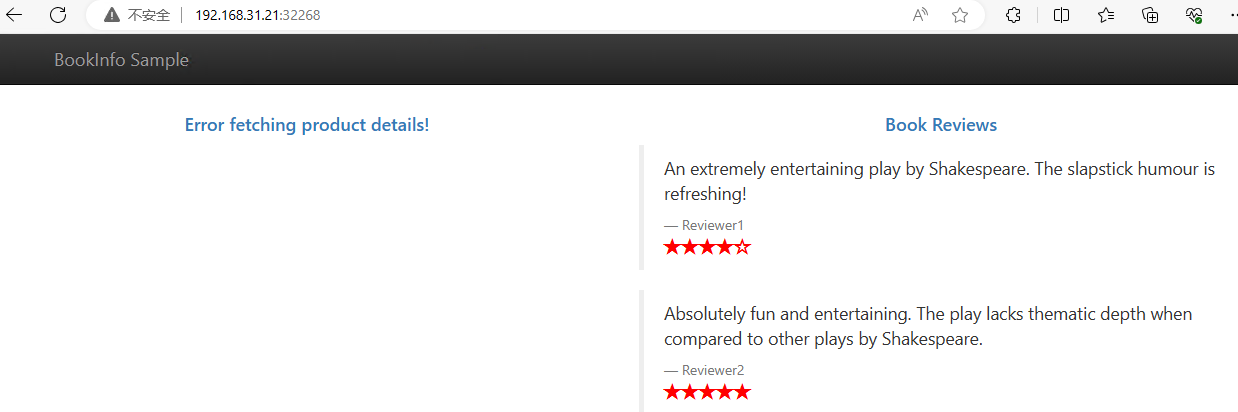
kustomize部署清单
https://gitee.com/zhouwei1996/kustomize
kustomize-bookinfo-reviews通过Istio实现金丝雀部署,结构中资源与其他项目有区别
下述以reviews项目为例,其他项目类似,可编写为kustomize资源清单,通过app of apps模式一键部署。
├─kustomize(父kustomize)
│ ├─kustomize-bookinfo-reviews(bookinfo-reviews部署清单)
│ ├─├─base(公用资源)
│ ├─├─├─kustomization.yaml(组织资源)
│ ├─├─├─svc.yaml
│ ├─├─├─dr.yaml
│ ├─├─├─sa.yaml
│ ├─├─├─vs.yaml
│ ├─├─build(cicd过程生成汇总资源)
│ ├─├─├─build.yaml
│ ├─├─├─kustomization.yaml
│ ├─├─overlay(补丁路径)
│ ├─├─├─v1
│ ├─├─├─configmap.yaml(存放springboot的application.yml配置)
│ ├─├─├─deployment.yaml
│ ├─├─├─kustomization.yaml
│ ├─├─├─v2
│ ├─├─├─configmap.yaml(存放springboot的application.yml配置)
│ ├─├─├─deployment.yaml
│ ├─├─├─kustomization.yaml
------------------------------------
│ ├─kustomize-bookinfo-productpage(bookinfo-productpage部署清单)
│ ├─├─base(公用资源)
│ ├─├─├─kustomization.yaml(组织资源)
│ ├─├─├─istio-gateway.yaml
│ ├─├─├─svc.yaml
│ ├─├─├─dr.yaml
│ ├─├─├─sa.yaml
│ ├─├─├─vs.yaml
│ ├─├─├─deployment.yaml
│ ├─├─build(cicd过程生成汇总资源)
│ ├─├─├─build.yaml
│ ├─├─├─kustomization.yaml
│ ├─├─overlay(补丁路径)
│ ├─├─├─dev
│ ├─├─├─kustomization.yaml
----------------------------------------
│ ├─kustomize-bookinfo-gateway(bookinfo-productpage部署清单)
│ ├─├─base(公用资源)
│ ├─├─├─kustomization.yaml(组织资源)
│ ├─├─├─configmap.yaml
│ ├─├─├─svc.yaml
│ ├─├─├─dr.yaml
│ ├─├─├─sa.yaml
│ ├─├─├─vs.yaml
│ ├─├─├─deployment.yaml
│ ├─├─build(cicd过程生成汇总资源)
│ ├─├─├─build.yaml
│ ├─├─├─kustomization.yaml
│ ├─├─overlay(补丁路径)
│ ├─├─├─dev
│ ├─├─├─kustomization.yaml
--------------下述结构类似查看gitee---------------------
|--kustomize-bookinfo-admin
|--kustomize-bookinfo-ratings
|--kustomize-bookinfo-details
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
ConfigMap改造
假设配置中ratings下所有内容为需加密数据,改造如下:
kind: ConfigMap
apiVersion: v1
metadata:
name: reviews
namespace: spring-cloud
annotations:
kubesphere.io/creator: admin
data:
application.yml: |-
server:
port: ${SERVER_PORT:8080}
spring:
application:
name: reviews
ratings:
enabled: ${ratings_enabled:false}
server-addr: ${ratings_server_addr:http://ratings}
color: ${ratings_color:red}
management:
endpoints:
web:
exposure:
include: "*"
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
Secret
bookinfo-reviews-secret.yaml
kind: Secret
apiVersion: v1
metadata:
name: reviews
namespace: spring-cloud
annotations:
kubesphere.io/creator: admin
data:
ratings_color: cmVk
ratings_enabled: dHJ1ZQ==
ratings_server_addr: aHR0cDovL3JhdGluZ3M=
type: Opaque
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
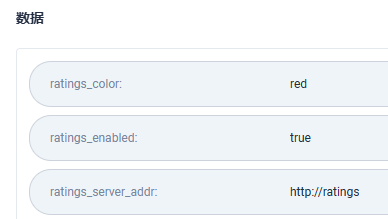
SealedSecret
- 加密Secret
kubeseal --format=yaml --cert ./public-cert-0.26.0.pem < bookinfo-reviews-secret.yaml > bookinfo-reviews-secret-sealed.yaml
- 1
- 加密后SealedSecret,替换部署清单中Secret
apiVersion: bitnami.com/v1alpha1
kind: SealedSecret
metadata:
creationTimestamp: null
name: reviews
namespace: spring-cloud
spec:
encryptedData:
ratings_color: AgCfoIXX43E/KCSqtmC2HPXqUky2tOMs5ZrOesM7c19eeGSLSZUJiZ58mv407couvVTAKy0f5HazHeGOvQzW5QmMQtFM38yrKrNrwInuWal8XGMRUo/pwbxlPQ2K5X8L9g/jJg7eykaXHoYA/n0r1XRq0ZgN3M8I+uhZqrABhtT7oxb+yQB2w2BCOdfCpnogblgfZQkgEiYoBqfmMH4SZ+Uz//fi3EKekIItBq94ZvjpaS/w+G1+DE7suhsYp4gKRUwcJBY9D6qWJc4LBXwOGKfKI6Lg5cKOs6UYi0qAUPeU0fU+zpp3uyFia2ghWuXHUhe2E4zwEFbMJ/CFiQO76bHHblo4+aLWi0SQHLVDR6h0jtNTjRk+IkxMwFlxji2UqHa5J6giCJwMpTx44UHicQ5RPbwbVCtpog/U+vjTejszxRZDU0SWeIlH2gHRtFdIIl8uKy2/SFhjE6i/0NN2F1hXGHfCGE7rLZXGXUxNRvvMa/IPHKahn/HfunURXODo/kwdqoEuaoRnEjk4LD1oWdhUZxume/jC2riTMTTcQBEEyNWJIwdJzooACj7Z0Qn5AG0Gs/A23yea6WCL5ZCn0b0k8KzHQHZRcIPWddZStYaqO5l2B4F8rblL7XwpDk9lXXbPgktKlou19HMcUmZu3Vuu7DNuehrAr0K5bUR8qiillfOLbO5RFmZsr7rOSAe4bhGCE2U=
ratings_enabled: AgBsOa0HGRi+m/KArc1WZcHOB6pouyq4inkfDXUpKkOkZXhhJsk97qr/dTBQCae7ey+myUPPWpQhJLjcXFzE/f0lk0jRklZvUV8tdYUE6nj+MKmDHFf/tpe4+buB4nhcKOXsjzgBheuElXqObNmXaDxnHOdyDJJarG1eL3v+/cbcZ+mYPEmZQ4fzCSvLGQuN37ZKljjM5Mq5S6UhL8VK/2Niy+7weQZkVg5B/4P5L8I5n77//fUR5SNP79PxaeiY5dFgHU1+CiITTuC5igBTyqTFUrStZlo/pfbTtBDuAa//I1hgQhFF3l0Rb+HdySv1nrgbL6aWcJojpxIw3JJe4aEv/DGoF7jGRMsFPrSHk18DtO0+g0pLJ9SRxLCX8nNHDCynVFZfF6PIQx56kEFzv4I6zQEichstkTZq7rFPqjK7ROy8ctmJQHyVx3jbW4kBqAzwT5UhbVk0Kk/uwXjthgb+SA6EQoN5PNhcgtcU4YRxXgsmiy7r73qa5monqEBITD9icAVE2Ni8qtKDwU+q6j8L1qsSe2BM74JEeKmRQUTJYj2uzZjUCtS077BYAEQ6mts2eNOEIskHaDK09YwnZHThQ78Sslqv52scrHM65AT7UV1GVG/v010z9AWX8c0bRfObbFtYkxwy3l9GTWsyUw3ShJrGGY35jROsKBtlNdIg4Y6AOqSRyQ+7Hksz9CbkWA2Qaejq
ratings_server_addr: AgBpinPNNUcEwEQqAKnMZKrGLDr7f3RFJZTtDxJcjPX5/nWJ2W4Wo2OKu/7Cj9qp7L+KddEELPpuXZP5BfFfjHJrq/QOUAIQYxQnwof/rem6lWMs+bxN3GTzsVakBwW1zi9oLAbpWjB8mblFnskbtRFF7r7jAFX7UFi5Ad6WyF0Bxitys9Jb64trjhhDeb4+yzV61raL+jqs3dhU/ObFPHmu6XIb0I4EUEy2IHPfWkL3gIn2rEpLzX71Tp1WfOjHLPFuOK81jaqgVQOtempQ8USsZQMJ2K4Lft9Sm2XoUfYjDCl56RnGYqtUKYQfDRr/YV5wFhOt15VBO/M0xsaYTYFKoyUw8SS85slkPe5nIyoRe5MdCjsWlQsVWS/nCo3ZCwPzEzsPMDGf0k8mNg2POgRFARr8iFy4Zp1uTxhy2h1ohw9TRDkD6U/gyj+ETCXdlRGRC8UFuVOHXz4+H8aXMMmPeIlCZ3t/6HU4xFc9TOghZQQqxgEt+lQU8aBNJKmHFUqIdtG01OdZ39aYSK0kGUqdp+Gh8UdE/JXa4aXV0u5EWUt5gcPg+8sAjstyWeozr1cg/26KvKj3JfcGflmMIg0CWZxc/Rm1acuM4LuCFKgkGPg5dWuTo3ZbXVz4d8WZxRpXgBsd6VGCCDDOfFPvuwpsOmC7yMVsQo+4mbiP3gBqf+pl8zP7PbA+RT/5puvBODGBMGUYNXvTyTVst1zQlQ==
template:
metadata:
annotations:
kubesphere.io/creator: admin
creationTimestamp: null
name: reviews
namespace: spring-cloud
type: Opaque
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
Deployment改造
apiVersion: apps/v1
kind: Deployment
metadata:
name: reviews
labels:
app: reviews
version: v1
spec:
replicas: 1
revisionHistoryLimit: 3
selector:
matchLabels:
app: reviews
version: v1
template:
metadata:
labels:
app: reviews
version: v1
spec:
containers:
- image: registry.cn-hangzhou.aliyuncs.com/yxymzw/reviews:latest
name: reviews
ports:
- containerPort: 8080
env:
# 将secret加密配置引入
- name: ratings_enabled
valueFrom:
secretKeyRef:
name: reviews
key: ratings_enabled
- name: ratings_server_addr
valueFrom:
secretKeyRef:
name: reviews
key: ratings_server_addr
- name: ratings_color
valueFrom:
secretKeyRef:
name: reviews
key: ratings_color
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
Service
svc.yaml
apiVersion: v1
kind: Service
metadata:
name: reviews
labels:
app: reviews
service: reviews
spec:
ports:
- port: 80
targetPort: 8080
selector:
app: reviews
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
istio相关资源
DestinationRule
dr.yaml
apiVersion: networking.istio.io/v1alpha3
kind: DestinationRule
metadata:
name: reviews
spec:
host: reviews
subsets:
- name: v1
labels:
version: v1
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
Gateway
istio-gateway.yaml,流量入口建议放在bookinfo-productpage项目中,或者通过ArgoCD的app of apps放在顶级app中
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
# 指定了这个 Gateway 的名称
name: kustomize-bookinfo-gateway
spec:
# 指定了这个 Gateway 的目标选择器为 istio: ingressgateway,表示这个网关将指向 Istio 中的 Ingress Gateway
selector:
istio: ingressgateway
servers: # 定义了网关监听的端口信息
- port:
number: 99
name: http
protocol: HTTP
hosts:
- "*"
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
该资源会与istio-ingressgateway绑定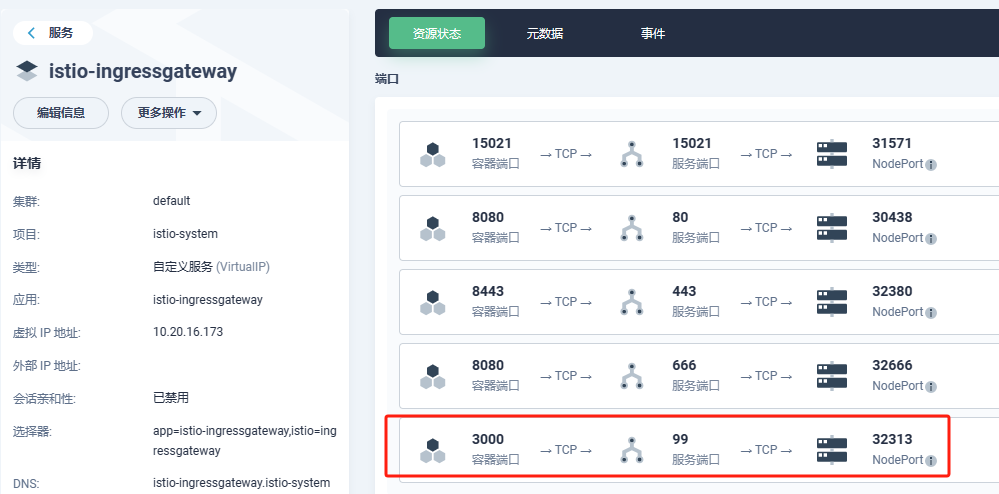
VirtualService
vs.yaml
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: reviews
spec:
hosts:
- reviews
http: # 定义了虚拟服务的 HTTP 路由规则
- route: # 定义了路由规则,指定了流量的目的地
- destination: # 指定了路由的目的地,即将流量发送到的服务
host: reviews # 指定了目标服务的主机为 reviews
subset: v1 # 指定了要发送流量到的服务的子集为 v1,这表示将流量路由到 reviews 服务的 v1 版本
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
ServiceAccount
sa.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: bookinfo-reviews
labels:
account: reviews
- 1
- 2
- 3
- 4
- 5
- 6
在 Istio 中,ServiceAccount 用于定义服务在 Istio 网格中的身份。Istio 构建在 Kubernetes 上,并扩展了 Kubernetes 的功能,包括对服务身份和访问控制的增强支持。使用 ServiceAccount 可以为服务提供以下几个重要用途:
- 身份验证:ServiceAccount 可以用于验证服务的身份。在 Istio 中,每个服务都有一个关联的 ServiceAccount,可以使用该 ServiceAccount 来验证服务的身份,确保只有经过身份验证的服务才能相互通信。
- 授权和访问控制:通过 ServiceAccount,可以为服务定义访问控制策略。在 Istio 中,可以使用 ServiceAccount 来定义哪些服务可以与其他服务通信,以及允许的通信方式和权限级别。
- 安全策略:ServiceAccount 可以与 Istio 的安全功能结合使用,如基于角色的访问控制(RBAC)和网络策略,以实现微服务之间的安全通信。通过为每个服务分配特定的 ServiceAccount,并为这些 ServiceAccount 配置适当的权限,可以确保服务之间的通信是安全的。
- 跟踪和监控:使用 ServiceAccount 可以帮助跟踪和监控服务在 Istio 网格中的活动。通过为每个服务分配独特的 ServiceAccount,可以更容易地跟踪服务的活动、生成日志和监控指标。
总的来说,ServiceAccount 在 Istio 中扮演着关键的角色,用于定义和管理服务在 Istio 网格中的身份和访问权限,从而确保服务之间的通信是安全、可控和可管理的。
kustomize-bookinfo-apps
通过该项目可以一键部署bookinfo
https://gitee.com/zhouwei1996/kustomize
kustomize-bookinfo-apps
|--root-app
|--rootapp.yaml # 指定apps位置
|--apps # 指定各个项目位置
|--bookinfo-productpage.yaml
|--bookinfo-gateway.yaml
|--bookinfo-details.yaml
|--bookinfo-reviews.yaml
|--bookinfo-ratings.yaml
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
如何编写Application?部署一个测试Application,查看部署后生成的Application资源yaml
kubectl get app -n argocd
kubectl get app <application> -n argocd -o yaml
- 1
- 2
rootapp.yaml
apiVersion: argoproj.io/v1alpha1
# Application 资源,用于定义应用程序的部署配置
kind: Application
metadata:
name: root-application
namespace: argocd
spec:
# 指定了应用程序所属的项目为 default
project: default
# 指定了应用程序的源码信息
source:
repoURL: https://gitee.com/zhouwei1996/kustomize.git
# 指定了要部署的代码版本为 HEAD
targetRevision: HEAD
# 指定了部署时的目录配置
path: ./kustomize-bookinfo-apps/apps
directory:
# 指定了不递归处理目录
recurse: false
# 指定了应用程序的部署目的地
destination:
server: https://kubernetes.default.svc
# 指定了部署到的命名空间为 default
namespace: default
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
targetRevision: HEAD
在软件开发中,targetRevision: HEAD 表示在版本控制系统(如 Git)中使用最新的提交作为部署的目标版本。在 Git 中,HEAD 是指向当前所在分支最新提交的指针。
具体来说,当在部署流程中指定 targetRevision: HEAD 时,系统会将部署目标设置为当前所在分支的最新提交。这意味着每次部署时都会使用当前分支的最新代码版本,确保部署的是最新的代码更改。
使用 targetRevision: HEAD 可以确保部署的应用程序始终是基于最新的代码提交构建的,有助于保持部署的应用程序与代码仓库的同步,并确保部署的应用程序包含了最新的功能和修复。
bookinfo-productpage.yaml
apiVersion: argoproj.io/v1alpha1
kind: Application
metadata:
# 指定了 Application 资源的名称
name: bookinfo-ratings
# 指定了资源所在的命名空间为 argocd
namespace: argocd
spec:
# 指定了应用程序的部署目的地
destination:
# 指定了部署到的命名空间
namespace: spring-cloud
# 指定了部署到的 Kubernetes 集群的 API 服务器地址
server: https://kubernetes.default.svc
# 指定了应用程序所属的项目为 default
project: default
source:
# 指定了应用程序的路径
path: kustomize-bookinfo-ratings
# 指定了应用程序的源代码存储库的 URL
repoURL: https://gitee.com/zhouwei1996/kustomize.git
# 指定了要部署的代码版本为 main (分支名称)
targetRevision: HEAD
# 指定了同步策略
syncPolicy:
# 指定了应用程序的同步策略为自动化,以便 Argo CD 可以自动监视并同步应用程序的状态。
automated: {}
syncOptions: # 指定了同步选项
# 启用了创建命名空间的选项,即在部署应用程序时会创建指定的命名空间
- CreateNamespace=true
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
bookinfo-gateway.yaml
apiVersion: argoproj.io/v1alpha1
kind: Application
metadata:
name: bookinfo-gateway
namespace: argocd
spec:
destination:
namespace: spring-cloud
server: https://kubernetes.default.svc
project: default
source:
path: kustomize-bookinfo-gateway/base
repoURL: https://gitee.com/zhouwei1996/kustomize.git
targetRevision: HEAD
syncPolicy:
automated: {}
syncOptions:
- CreateNamespace=true
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
bookinfo-details.yaml
apiVersion: argoproj.io/v1alpha1
kind: Application
metadata:
name: bookinfo-details
namespace: argocd
spec:
destination:
namespace: spring-cloud
server: https://kubernetes.default.svc
project: default
source:
path: kustomize-bookinfo-details/base
repoURL: https://gitee.com/zhouwei1996/kustomize.git
targetRevision: HEAD
syncPolicy:
automated: {}
syncOptions:
- CreateNamespace=true
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
bookinfo-reviews-v1.yaml
apiVersion: argoproj.io/v1alpha1
kind: Application
metadata:
name: bookinfo-reviews
namespace: argocd
spec:
destination:
namespace: spring-cloud
server: https://kubernetes.default.svc
project: default
source:
path: kustomize-bookinfo-reviews/overlay/v1
repoURL: https://gitee.com/zhouwei1996/kustomize.git
targetRevision: HEAD
syncPolicy:
automated: {}
syncOptions:
- CreateNamespace=true
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
bookinfo-reviews-v2.yaml
apiVersion: argoproj.io/v1alpha1
kind: Application
metadata:
name: bookinfo-reviews
namespace: argocd
spec:
destination:
namespace: spring-cloud
server: https://kubernetes.default.svc
project: default
source:
path: kustomize-bookinfo-reviews/overlay/v2
repoURL: https://gitee.com/zhouwei1996/kustomize.git
targetRevision: HEAD
syncPolicy:
automated: {}
syncOptions:
- CreateNamespace=true
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
bookinfo-ratings.yaml
apiVersion: argoproj.io/v1alpha1
kind: Application
metadata:
name: bookinfo-ratings
namespace: argocd
spec:
destination:
namespace: spring-cloud
server: https://kubernetes.default.svc
project: default
source:
path: kustomize-bookinfo-ratings/base
repoURL: https://gitee.com/zhouwei1996/kustomize.git
targetRevision: HEAD
syncPolicy:
automated: {}
syncOptions:
- CreateNamespace=true
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
通过argocd一键部署bookinfo
在argocd中创建app
- kubesphere中安装devops组件,参考16.云原生之kubesphere组件安装卸载
- 暴露argocd,参考19.云原生CICD之ArgoCD入门CD过程实战
- 登录argocd,配置仓库地址
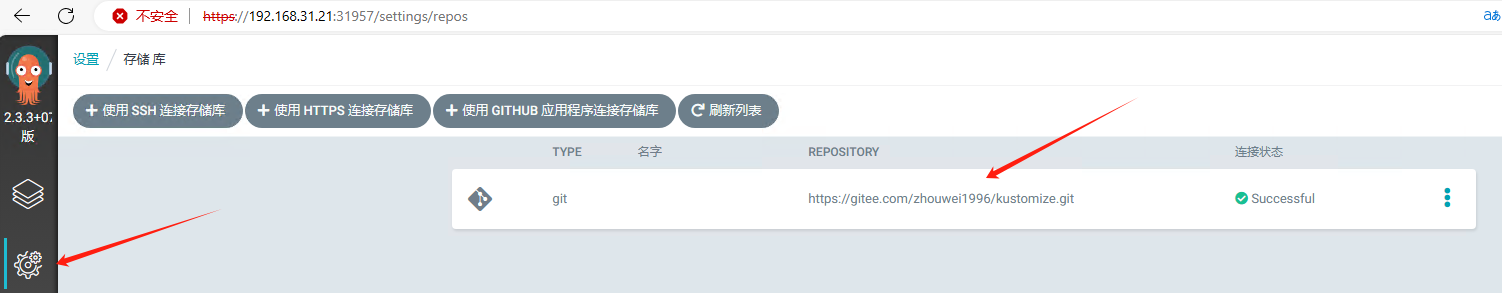
- 创建应用,参考23.云原生之ArgoCD CICD实战
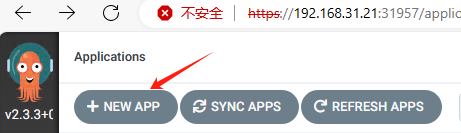
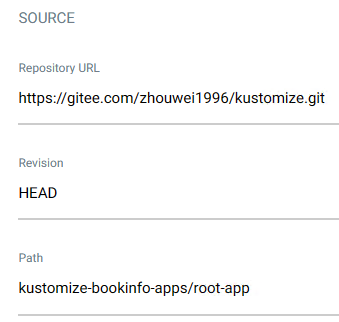
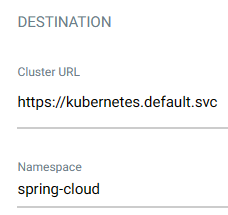
查看部署情况
- 查看ArgoCD部署情况
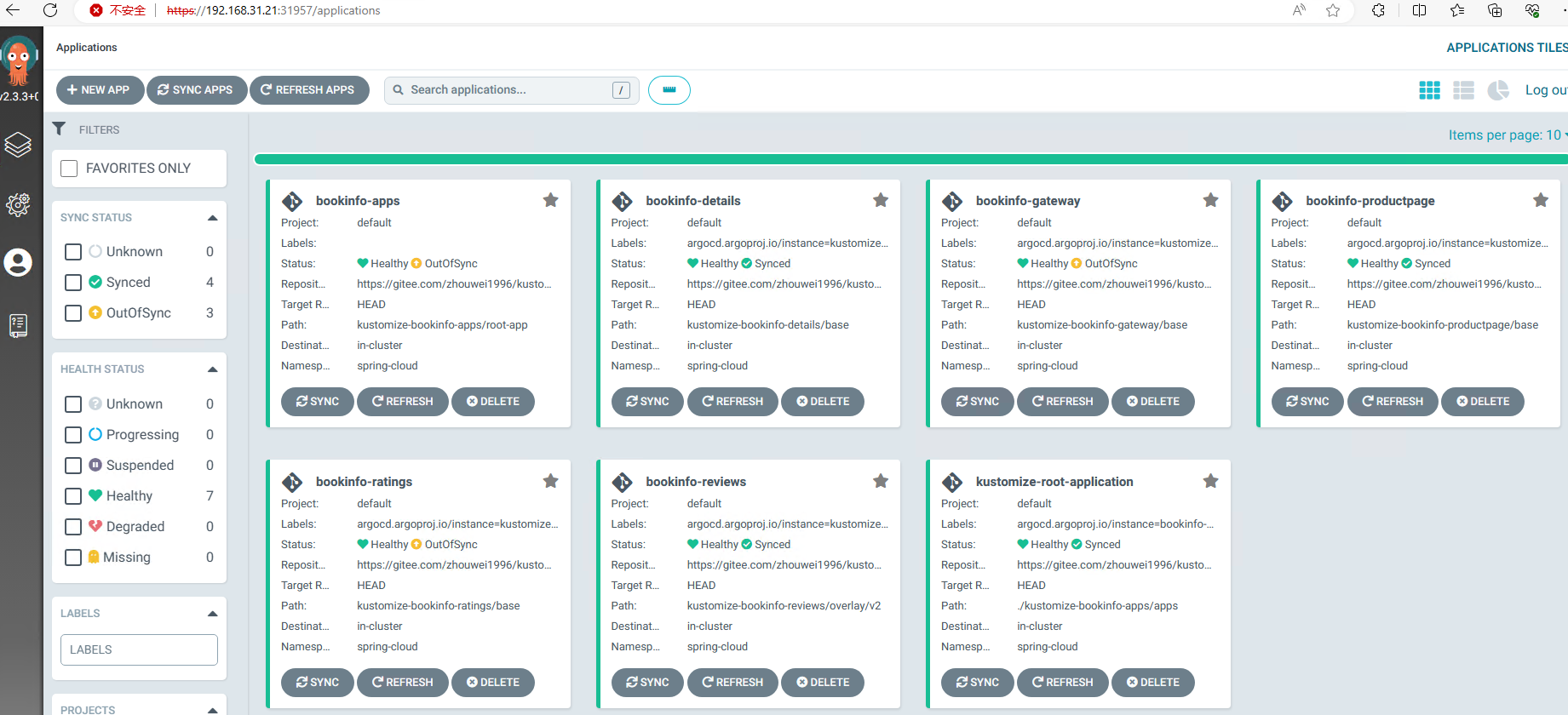
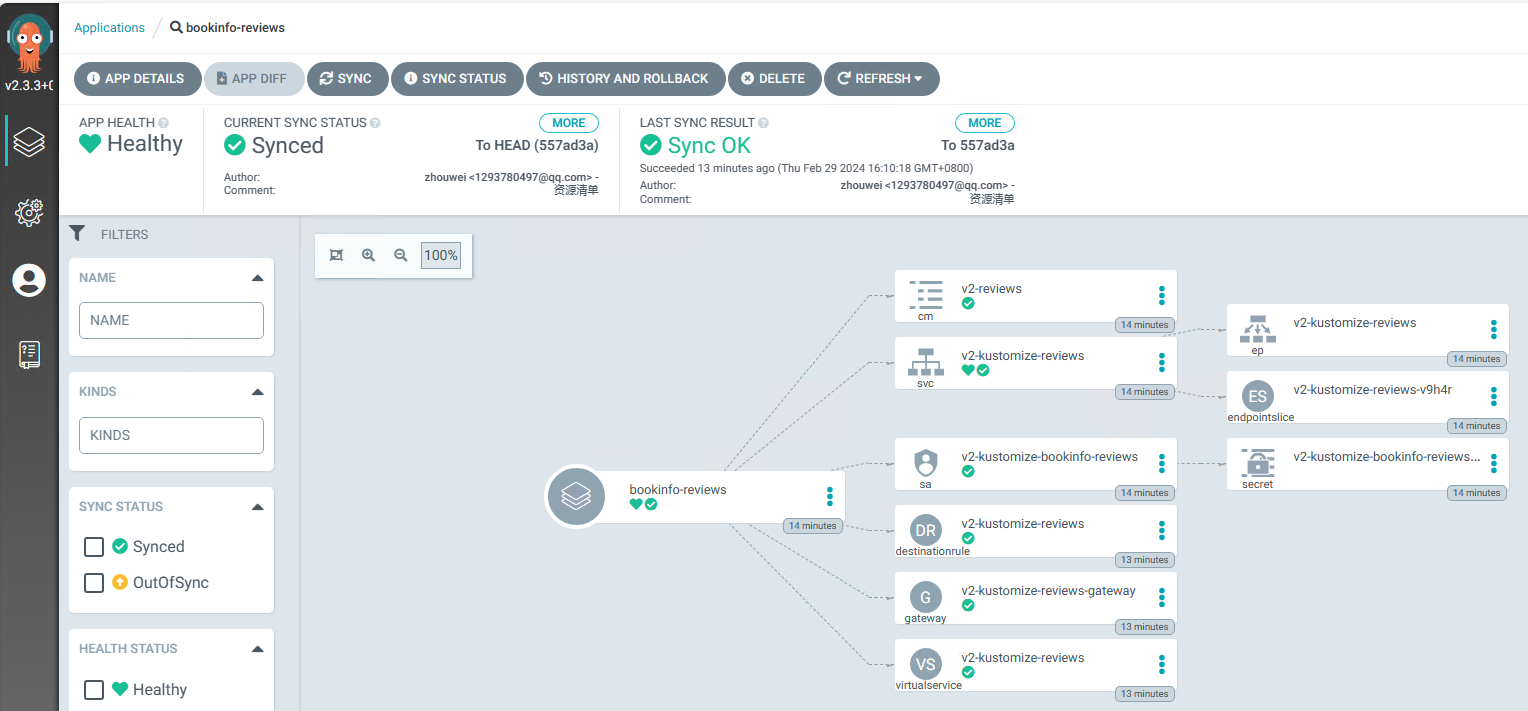
- 查看kubesphere部署情况
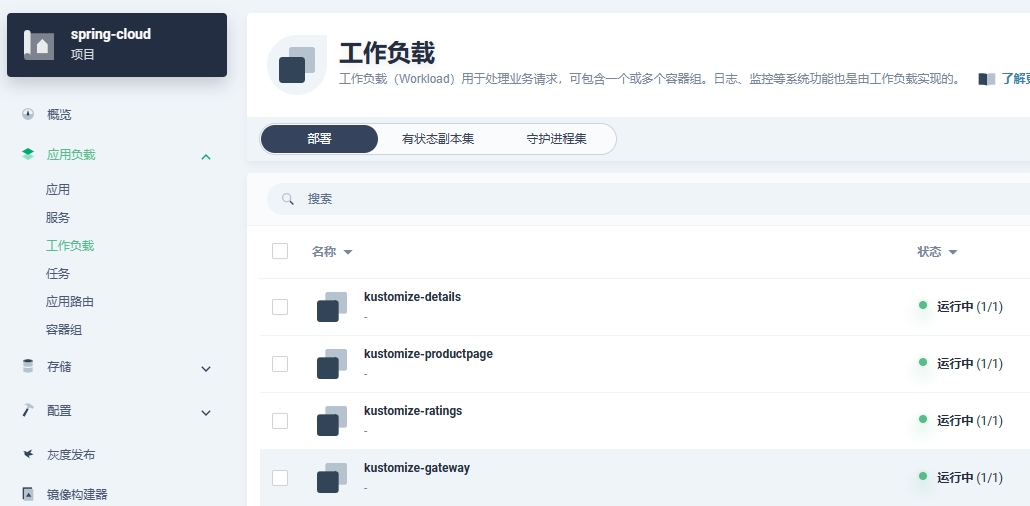
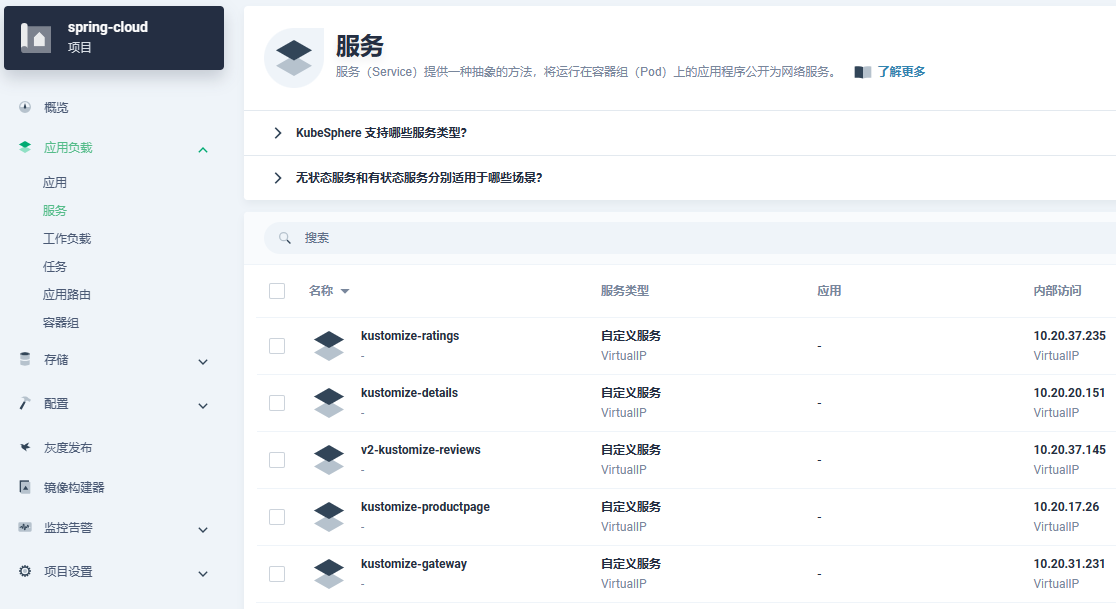
注意:通过上述观察发现我们部署的svc资源带上了前缀,跟我们VirtualService中使用的hosts不一致,这儿需要修改
查看istio资源是否也添加了前缀:
# kubectl get gw -A
NAMESPACE NAME AGE
bookinfo bookinfo-gateway 7d2h
spring-cloud devops-web-gateway 6m10s
spring-cloud gateway 6m10s
spring-cloud kustomize-devops-web-gateway 27m
spring-cloud kustomize-gateway 27m
spring-cloud reviews-gateway 6m10s
spring-cloud v2-kustomize-reviews-gateway 27m
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 删除所有资源
kubectl delete all --all -n <namespace>
kubectl delete all --all -n spring-cloud
- 1
- 2
查看istio资源
Istio 是一个服务网格解决方案,它引入了许多自定义资源(Custom Resource Definitions,CRDs)来管理服务间的通信、流量控制和安全策略等。以下是 Istio 中常见的一些资源类型:
- VirtualService:定义了服务之间的路由规则,允许你控制流量的路由和转发。
- DestinationRule:定义了服务的目标规则,用于指定服务的负载均衡策略、连接池设置等。
- Gateway:定义了入口网关,允许外部流量访问 Istio 网格中的服务。
- ServiceEntry:允许你将外部服务引入 Istio 网格,或者定义对外部服务的访问规则。
- VirtualServiceSubset:用于定义虚拟服务的子集,可以用于进一步细化路由规则。
- IstioOperator:用于配置和管理 Istio 控制平面的自定义资源。
- AuthorizationPolicy:定义了服务间的访问控制策略,用于实现服务级别的安全控制。
- Sidecar:用于配置 Envoy sidecar 代理的自定义资源。
所有命名空间中的 Istio 资源
kubectl get virtualservices --all-namespaces
kubectl get destinationrules --all-namespaces
kubectl get gw --all-namespaces
kubectl get ServiceAccount --all-namespaces
kubectl get serviceentries --all-namespaces
kubectl get istiooperators --all-namespaces
kubectl get authorizationpolicies --all-namespaces
kubectl get sidecars --all-namespaces
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
查看项目日志
gateway: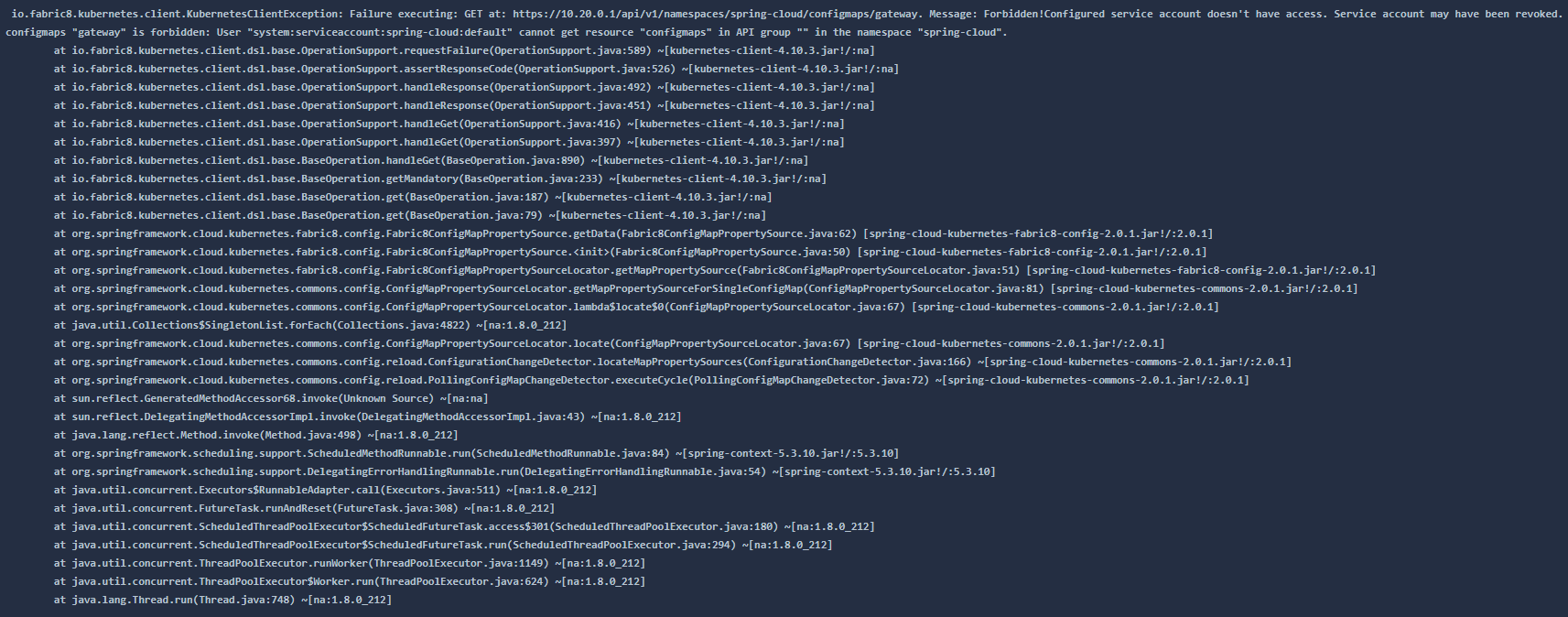
该错误是服务账户没有访问权限,配置如下: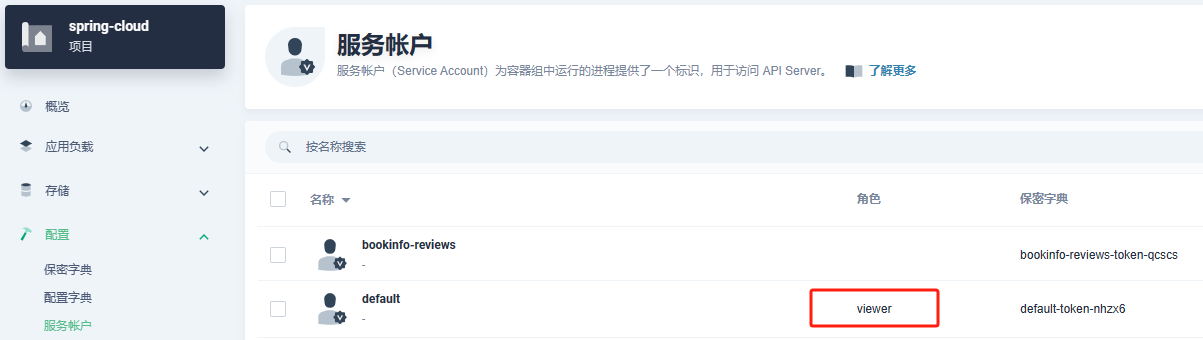
删除Argocd部署
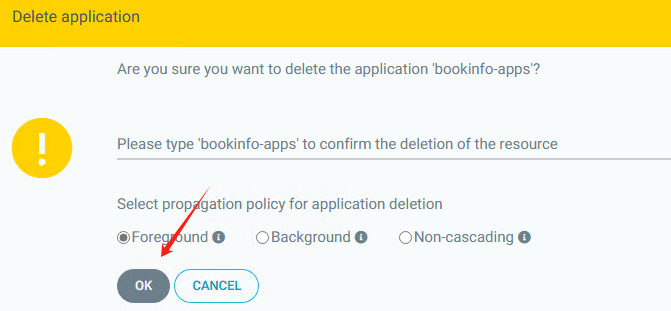
在 Argo CD 中删除应用程序(app)时,可以选择不同的删除策略,包括 Foreground、Background 和 Non-cascading。这些策略决定了删除操作的行为方式。下面是它们的区别:
- Foreground(前台):
- 在 Foreground 删除策略下,Argo CD 将首先删除应用程序的资源对象,然后再删除应用程序本身。
- 这意味着删除应用程序的操作会等待所有资源对象被删除后才会完成,这可能会导致删除操作需要一些时间才能完成。
- Foreground 删除策略通常用于确保资源对象被正确清理,以避免可能的冲突或问题。
- Background(后台):
- 在 Background 删除策略下,Argo CD 将直接删除应用程序本身,而不等待资源对象被删除。
- 这意味着删除应用程序的操作会立即返回,而资源对象的删除将在后台进行,不会阻塞删除操作的完成。
- Background 删除策略通常用于快速删除应用程序,而不需要等待资源对象的清理。
- Non-cascading(非级联):
- Non-cascading 删除策略指示 Argo CD 仅删除应用程序本身,而不会删除应用程序创建的任何资源对象。
- 这意味着应用程序关联的资源对象将保留在集群中,不会被删除。
- Non-cascading 删除策略通常用于保留应用程序创建的资源对象,以便稍后重新使用或进行其他操作。
在使用 Argo CD 删除应用程序时,根据具体需求选择适合的删除策略是很重要的。根据是否需要等待资源对象的删除以及是否需要级联删除资源对象,选择合适的删除策略可以更好地管理应用程序的生命周期。
删除k8s中部署资源
删除指定空间所有资源
kubectl delete all --all -n spring-cloud
- 1
删除 Istio 资源:
kubectl delete virtualservice <virtualservice-name> -n <namespace>
kubectl delete destinationrule <destinationrule-name> -n <namespace>
kubectl delete gw <gateway-name> -n <namespace>
kubectl delete serviceentry <serviceentry-name> -n <namespace>
kubectl delete istiooperator <istiooperator-name> -n <namespace>
kubectl delete authorizationpolicy <authorizationpolicy-name> -n <namespace>
kubectl delete sidecar <sidecar-name> -n <namespace>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
删除查询到的资源
kubectl get gw -n spring-cloud | awk '{print $1}' | xargs kubectl delete gw -n spring-cloud
kubectl get virtualservice -n spring-cloud | awk '{print $1}' | xargs kubectl delete virtualservice -n spring-cloud
kubectl get ServiceAccount -n spring-cloud | awk '{print $1}' | xargs kubectl delete ServiceAccount -n spring-cloud
kubectl get destinationrule -n spring-cloud | awk '{print $1}' | xargs kubectl delete destinationrule -n spring-cloud
- 1
- 2
- 3
- 4
- 5
- 6
- 7
访问测试
通过nodeport方式暴露istio-ingressgateway流量入口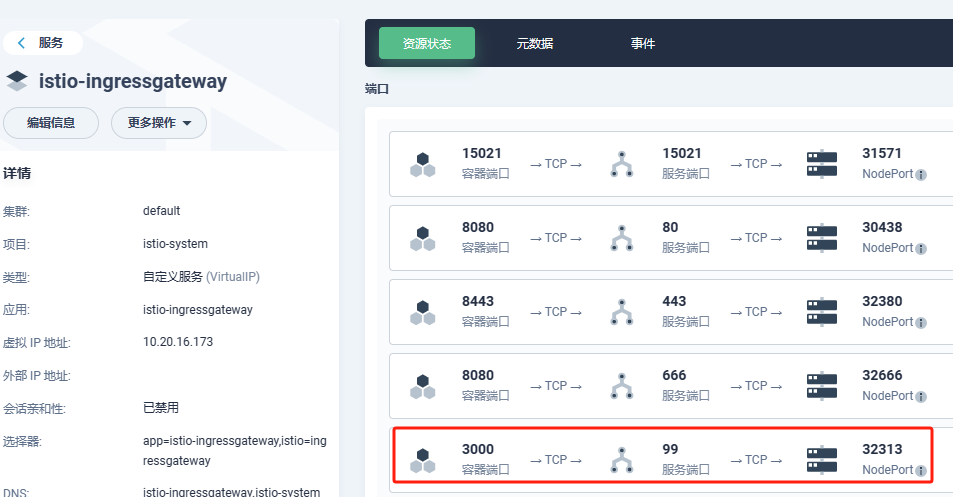
访问页面,若是访问出错检查bookinfo-productpage部署时环境变量API_SERVER是否配置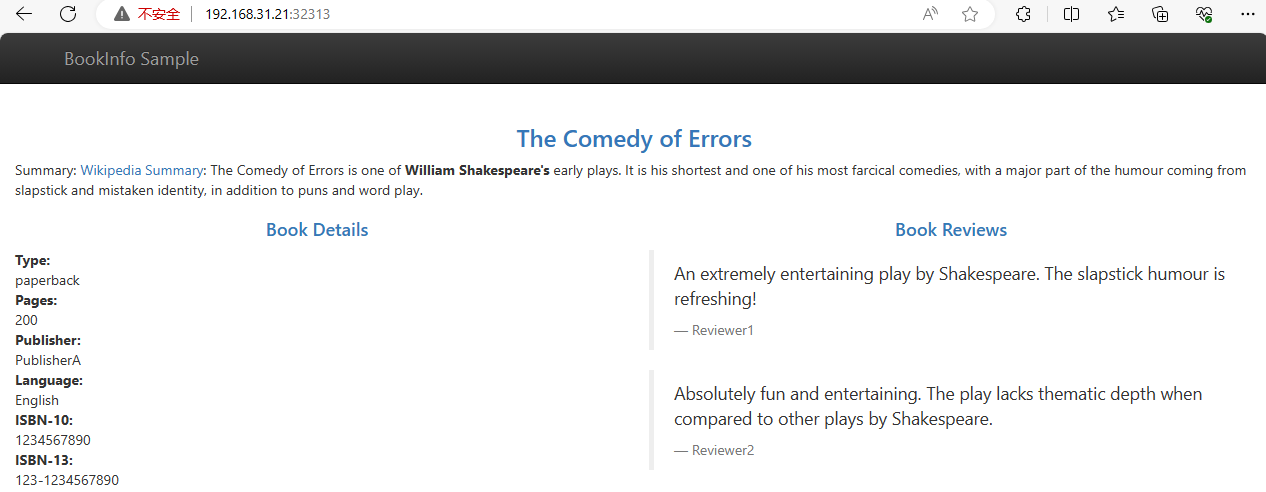
Istio流量加密
回顾ingress入口流量加密
参考下述文章进行配置:
4. 服务暴露方式
5.云原生安全之kubesphere应用网关配置域名TLS证书
验证结果如下: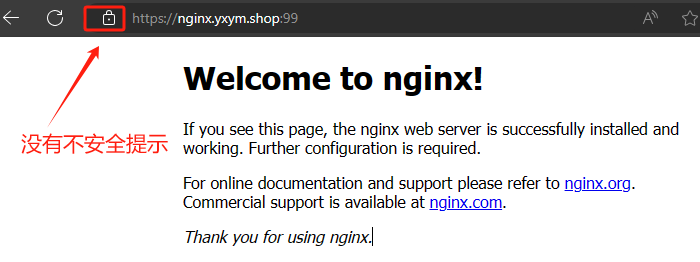
bookinfo安全暴露服务: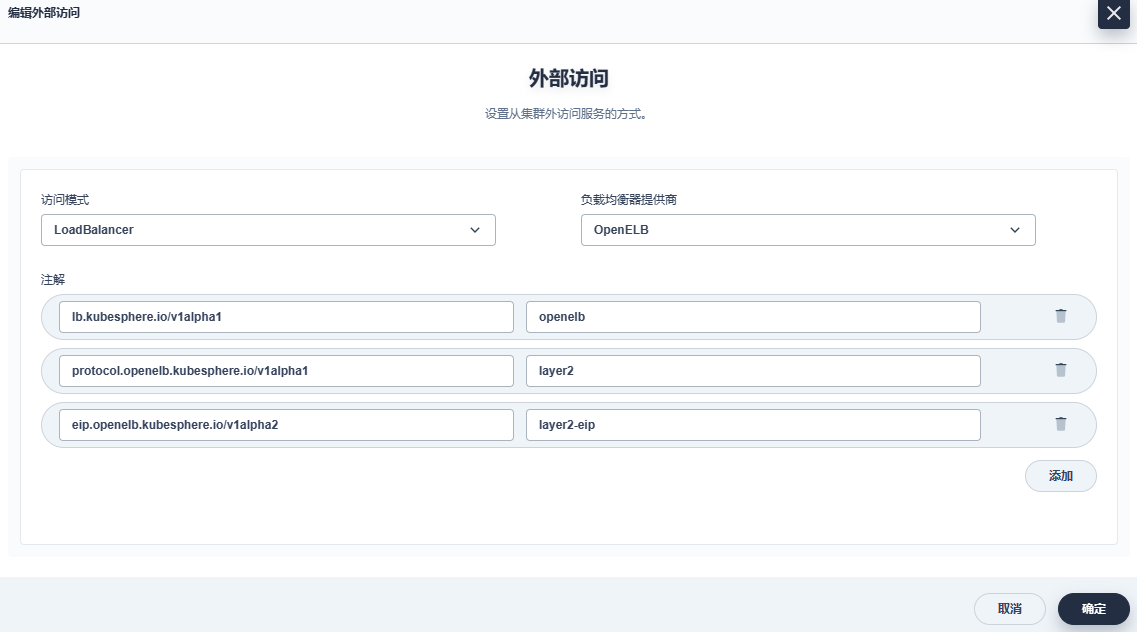

修改爱快软路由暴露192.168.31.12内网ip
访问测试
istio-gateway暴露服务
- 配置LoadBalancer暴露

- ip访问测试
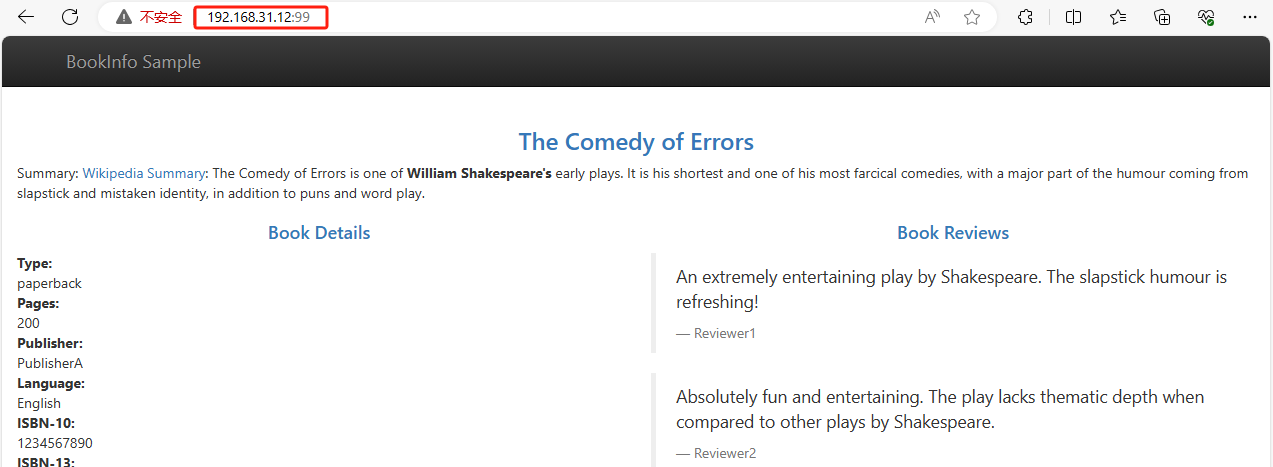
- 配置爱快映射内网ip

这个内网和外网端口保持一致,端口为istio-ingressgateway服务端口如下: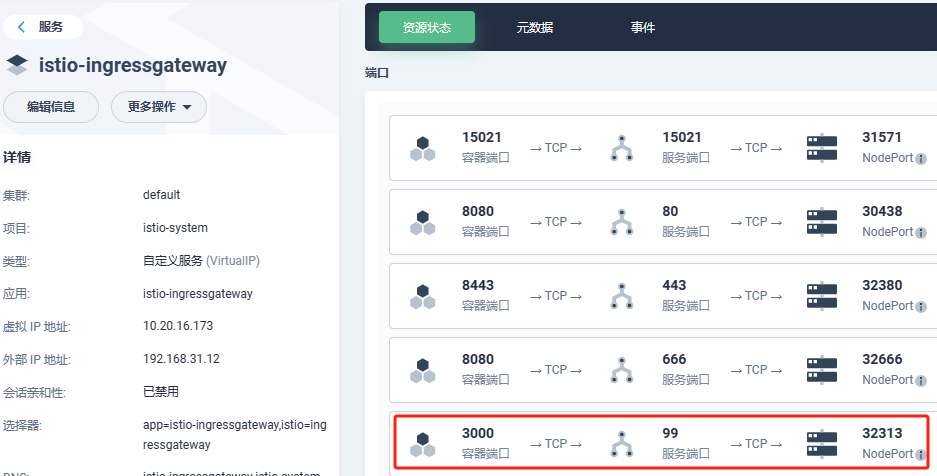
- 域名访问
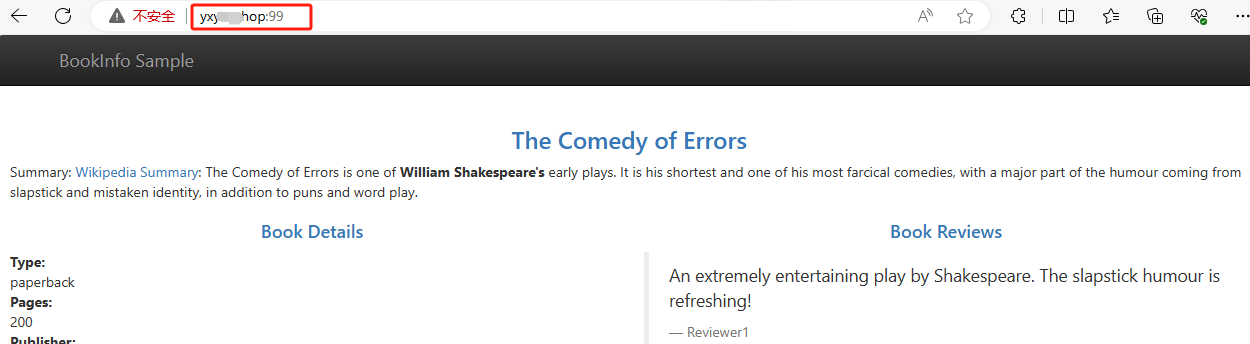
istio-gateway配置https
官网:理解 TLS 配置
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: kustomize-bookinfo-gateway
spec:
selector:
istio: ingressgateway
servers:
- port:
number: 99
name: http
protocol: HTTP
hosts:
- "*"
# 重定向到https上
tls:
httpsRedirect: true
- port:
number: 77
name: https
protocol: HTTPS
tls:
mode: SIMPLE
# 配置证书secret
credentialName: your-cert-secret-name
hosts:
- "*"
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
mode选项介绍:
在 Istio 中,当配置 Gateway 的 TLS 设置时,tls.mode 选项用于指定 TLS 连接的模式。tls.mode 可以设置为以下几种模式之一:
- SIMPLE: 这是最基本的 TLS 模式,用于启用基本的 TLS 加密和解密。在 SIMPLE 模式下,必须提供证书和私钥,以便进行 TLS 握手和加密通信。
- MUTUAL: 在 MUTUAL 模式下,除了要求客户端验证服务器的证书外,还要求服务器验证客户端的证书。这种模式也称为双向 TLS 或 mTLS(mutual TLS)。在这种模式下,客户端和服务器之间的通信将进行双向身份验证,增强了通信的安全性。
- ISTIO_MUTUAL: 这是 Istio 特定的一种 TLS 模式,类似于 MUTUAL 模式,但是 Istio 自动处理证书的生成和分发。在 ISTIO_MUTUAL 模式下,Istio Pilot 会自动为服务生成证书,并确保双向 TLS 通信的安全性。
在 Istio Gateway 中配置 TLS 模式时,根据您的安全需求和环境,选择适当的 tls.mode 设置是很重要的。您可以根据实际情况选择 SIMPLE、MUTUAL 或 ISTIO_MUTUAL 模式,以保障通信的安全性和完整性。
此处配置访问测试【问题暂时还未解决】
通过gitops部署项目
案例项目地址:https://gitee.com/zhouwei1996/spring-cloud-bookinfo.git
此处小编不进行演示给出关键gitlab-ci.yml流水线脚本,可根据实际情况改造
variables:
KUBECONFIG: /etc/deploy/config
MAVEN_OPTS: >-
-Dmaven.repo.local=/builds/maven
-Dorg.slf4j.simpleLogger.showDateTime=true
-Djava.awt.headless=true
MAVEN_CLI_OPTS: >-
--batch-mode
--errors
--fail-at-end
--show-version
--no-transfer-progress
-DinstallAtEnd=true
-DdeployAtEnd=true
# 设置自定义的镜像源
# DOCKER_REGISTRY_MIRROR: https://registry.example.com
DOCKER_IMAGE_NAME: $CI_REGISTRY_IMAGE:$CI_COMMIT_REF_SLUG
DOCKER_DRIVER: overlay
stages:
- package
- build
- deploy
package:
stage: package
image: maven:3.6.3-jdk-8
tags:
- k8s
script:
- mvn clean package -Dmaven.test.skip=true
- rm -rf /builds/project-target/reviews
- rm -rf /builds/project-target/productpage
- cp -rf ./reviews /builds/project-target
- cp -rf ./productpage /builds/project-target
docker-build:
image: docker:cli
services:
- docker:latest
stage: build
tags:
- k8s
script:
- cd /builds/project-target
- docker login -u $aliimarepo_user -p $aliimarepo_password registry.cn-hangzhou.aliyuncs.com
- docker build -t registry.cn-hangzhou.aliyuncs.com/yxymzw/productpage:latest -f ./productpage/Dockerfile ./productpage/
- docker push registry.cn-hangzhou.aliyuncs.com/yxymzw/productpage:latest
- docker build -t registry.cn-hangzhou.aliyuncs.com/yxymzw/reviews:latest -f ./reviews/Dockerfile ./reviews/
- docker push registry.cn-hangzhou.aliyuncs.com/yxymzw/productpage:latest
deploy:
stage: deploy
image: cnych/kustomize:v1.0
before_script:
- git config --global user.email "gitlab@git.k8s.local"
- git config --global user.name "GitLab CI/CD"
script:
- cd /builds/project-target
- rm -rf ./kustomize
- git clone http://$gitlab_user:$gitlab_password@192.168.31.3:83/root/kustomize.git
- cd ./kustomize/kustomize-bookinfo-productpage/overlay/dev
- kustomize edit set image registry.cn-hangzhou.aliyuncs.com/yxymzw/productpage:latest
- kustomize build > ../../build/build.yaml
- cd ./kustomize/kustomize-bookinfo-reviews/overlay/dev
- kustomize edit set image registry.cn-hangzhou.aliyuncs.com/yxymzw/reviews:latest
- kustomize build > ../../build/build.yaml
- git add /builds/project-target/kustomize/kustomize-productpage/
- git add /builds/project-target/kustomize/kustomize-reviews/
- git commit -am "image update"
- git push -u origin main
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77



