热门标签
热门文章
- 1apache BeanUtils
- 2从SVN检出与提交到Git签出与提交的对比与注意事项_svn是先提后拉,还是先拉后提
- 3#NLP|文本生成#全网最全方法 一篇搞定文本摘要\关键字提取,包含SnowNLP|TextRank4ZH|大模型|TF-IDF_python snownlp 文本摘要提取算法代码
- 4Xilinx IDELAYE2应用笔记及仿真实操_idelaye2使用
- 5SpringBoot整合SSM框架及Ajax_springboot整合ajax
- 6常用的深度学习框架_深度学习常用框架介绍
- 756.Isaac教程--ROS_isaac-ros
- 8Android一点 修改jar的内容进阶_jar游戏修改
- 92020年 ICLR 国际会议最终接受论文(poster-paper)列表(四)_fundamental frequency layer-wise optimization of t
- 10Nginx篇03-负载均衡简单配置和算法原理_nginx 负载均衡 权重算法的配比是怎么改变的
当前位置: article > 正文
k8s中的RBAC鉴权将用户固定在某个namespace下
作者:笔触狂放9 | 2024-05-29 09:29:33
赞
踩
k8s中的RBAC鉴权将用户固定在某个namespace下
一、背景示例
用户:zhangsan
ns: b2b-pro-uat
允许用户zhangsan只访问b2b-pro-uat的ns下的pod,以及deploy。
二、创建SA
- [root@k8s-master05 tmp]# kubectl -n b2b-pro-uat create sa zhangsan
- serviceaccount/zhangsan created
三、创建对应的Role
PS:若不了解各自resoureces对应的apiGroup可用kubectl api-resources -o wide 查询对应关系。例如deploy对应的apiGroups可进行以下查询:
- [root@k8s-master05 tmp]# kubectl api-resources -o wide|grep deploy
- deployments deploy apps true Deployment [create delete deletecollection get list patch update watch]
- uniteddeployments ud apps.kruise.io true UnitedDeployment [delete deletecollection get list patch create update watch]
第三列对应的就为apiGroups的值,此处为apps,所以yaml如下:
- [root@k8s-master05 tmp]# cat zhangsan-role.yaml
- apiVersion: rbac.authorization.k8s.io/v1
- kind: Role
- metadata:
- name: zhangsan-role
- namespace: b2b-pro-uat
- rules:
- - apiGroups: [""]
- resources: ["pods","pods/logs"]
- verbs: ["get","watch","list"]
- - apiGroups: ["apps"]
- resources: ["deployments","replicasets"]
- verbs: ["get", "list", "watch", "create", "update", "patch", "delete"]
四、创建角色绑定
PS:此处在固定的ns下绑定权限,未涉及到整个集群全局权限,所以用Rolebinding即可
yaml如下:
- [root@k8s-master05 tmp]# cat zhangsan-rolebinding.yaml
- kind: RoleBinding
- apiVersion: rbac.authorization.k8s.io/v1
- metadata:
- name: zhangsan-rolebinding
- namespace: b2b-pro-uat
- subjects:
- - kind: ServiceAccount
- name: zhangsan
- namespace: b2b-pro-uat
- roleRef:
- kind: Role
- name: zhangsan-role
- apiGroup: rbac.authorization.k8s.io
将role和sa绑定。
五、测试
此处未涉及到命令行,仅用k8s原生dashboard进行测试。
获取sa对应的token:
- [root@k8s-master05 tmp]# kubectl -n b2b-pro-uat describe secret zhangsan-token-lvbwb
- Name: zhangsan-token-lvbwb
- Namespace: b2b-pro-uat
- Labels: <none>
- Annotations: kubernetes.io/service-account.name: zhangsan
- kubernetes.io/service-account.uid: aca7c6ca-10f6-41dc-8207-8e70fd1f4c93
-
- Type: kubernetes.io/service-account-token
-
- Data
- ====
- ca.crt: 1025 bytes
- namespace: 11 bytes
- token: eyJhbGciOiJSUzI1NiIsImtpZCI6IlZTSHUyeEFLcEM4bm9UOFBRWWhja3F6VXpiYy1RckJpa0ctRUt2anRuMG8ifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJiMmItcHJvLXVhdCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJ6aGFuZ3Nhbi10b2tlbi1sdmJ3YiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJ6aGFuZ3NhbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImFjYTdjNmNhLTEwZjYtNDFkYy04MjA3LThlNzBmZDFmNGM5MyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpiMmItcHJvLXVhdDp6aGFuZ3NhbiJ9.jC8sPAfUfdoIoaomR_K9PHxgvnK7CkASchsoq-OByW_dQngHm2FZfsL1_IC3isXinOAfH0g3F8O3IpGFkaLsP65XnfDGYd5GF5Rm8mtfSIp49joL-hDH0icntDrznhb-aeHJ2nE9U36gvqUACC9njv4dTbR8qI9_0uXMCmcniNVj-cgzqbGRsLmy7syjKwoQ067uEN5dJ80DyiOq7VXpR_u9-cj40RhvzaHKIFx9mRJ6o-xEBAYg2iOWkFb9DjP5VSYuWEiR0HH5G8zrA_TpWE0o4Wlz5aSMZzdnWMmfZAc0a5D1_8urj6_xp6N1fmOWstGCi5BtraFgWBW0hKt0JA
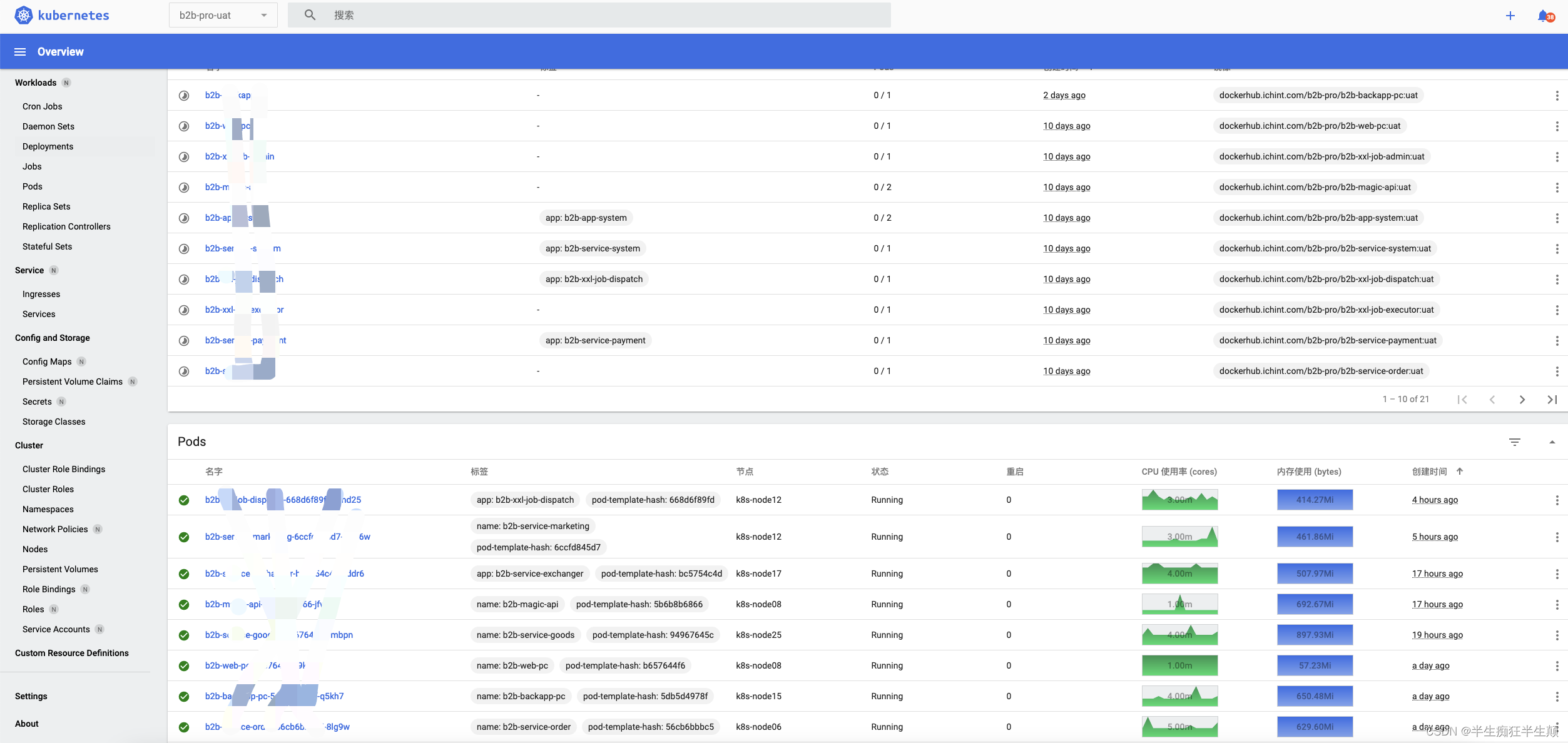
登录dashboard验证,因为没有赋予namespace相关权限,所以此处需要手动输入ns名称:
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/笔触狂放9/article/detail/641556
推荐阅读
相关标签


