- 1org.apache.hadoop.fs.UnsupportedFileSystemException: No FileSystem for scheme “hdfs“_exception in thread "main" org.apache.hadoop.fs.un
- 2《促进和规范数据跨境流动规定》朗言数安专家解读
- 3Spring架构揭秘-声明式事务
- 4Git详解——安装、使用、搭建、IDEA集成_idea安装git
- 5OneNET 数据可视化 按键控制_新版onenet如何创建图表和按键
- 6已解决java.lang.RuntimeException: 运行时异常的正确解决方法,亲测有效!!!_java.lang.runtimeexception: cannot start service o
- 7EDA实验-----3-8译码器设计(QuartusII)_eda开发板拨动开关
- 8聚焦国内银行核心业务系统
- 9postgresql不能连接问题FATAL: password authentication failed for user “root“
- 10Android程序员的天敌是谁?
中型公司网络-双出口_双路由器出口配置实例
赞
踩
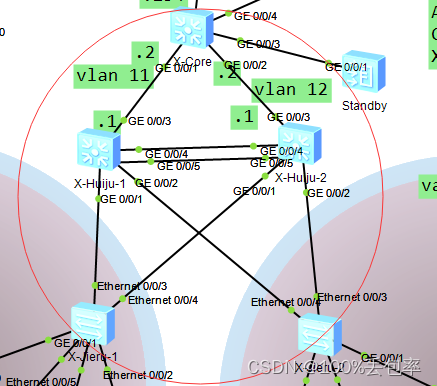
拓扑图如下:

一.配置思路
1.配置接入层交换机
2.配置汇聚层交换机
3.配置核心层交换机
4.配置MSTP+VRRP
5.配置防火墙和路由器的基础ip地址配置
6.配置内网OSPF互通
7.配置DHCP,使AP和PC能获取ip地址
8.配置AC,以及基于VRRP的热备
9.AP上线
10.WLAN业务配置下发
11.STA上线
12.模拟其中一个AC故障
13.在防火墙配置策略,使内网用户能访问外网和服务器
14.配置策略,使CW-PC1不能访问CW-PC2,而CW-PC2可以访问CW-PC1
二.详细配置
1.配置接入层交换机
X-Jieru-1:
vlan batch 10 20 100 to 102
interface Ethernet0/0/1
port link-type access
port default vlan 10
#
interface Ethernet0/0/2
port link-type access
port default vlan 20
#
interface Ethernet0/0/3 --连接汇聚交换机
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 10 20 100 to 102
#
interface Ethernet0/0/4 --连接汇聚交换机
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 10 20 100 to 102
#
interface Ethernet0/0/5
port link-type access
port default vlan 10
interface GigabitEthernet0/0/1 --连接AP,放行AP和业务的vlan
port link-type trunk
port trunk pvid vlan 100
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 100 to 101
X-Jieru-2:
vlan batch 10 20 100 to 102
interface Ethernet0/0/1
port link-type access
port default vlan 10
#
interface Ethernet0/0/2
port link-type access
port default vlan 20
#
interface Ethernet0/0/3
port link-type trunk
port trunk allow-pass vlan 10 20 100 to 102
#
interface Ethernet0/0/4
port link-type trunk
port trunk allow-pass vlan 10 20 100 to 102
2.配置汇聚层交换机
X-Huiju-1:
vlan batch 10 to 12 20 100 to 102
interface GigabitEthernet0/0/1
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 10 20 100 to 102
#
interface GigabitEthernet0/0/2
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 10 20 100 to 102
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 11 to 12
#
interface GigabitEthernet0/0/4
eth-trunk 1
#
interface GigabitEthernet0/0/5
eth-trunk 1
interface Eth-Trunk1
port link-type trunk
port trunk allow-pass vlan 10 to 12 20 100 to 102
mode lacp-static
X-Huiju-2:
vlan batch 10 to 12 20 100 to 102
interface GigabitEthernet0/0/1
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 10 20 100 to 102
#
interface GigabitEthernet0/0/2
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 10 20 100 to 102
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 11 to 12
#
interface GigabitEthernet0/0/4
eth-trunk 1
#
interface GigabitEthernet0/0/5
eth-trunk 1
interface Eth-Trunk1
port link-type trunk
port trunk allow-pass vlan 10 to 12 20 100 to 102
mode lacp-static
3.配置核心层交换机
X-Core:
vlan batch 11 to 13 99
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 11 to 12
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 11 to 12
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 99
#
interface GigabitEthernet0/0/4
port link-type trunk
port trunk allow-pass vlan 99
#
interface GigabitEthernet0/0/5
port link-type access
port default vlan 13
4.配置MSTP+VRRP
在接入、汇聚、核心这三个等级路由上配置MSTP:
stp region-configuration
region-name X
instance 1 vlan 10 100
instance 2 vlan 20 101 to 102
instance 3 vlan 11 to 12
active region-configuration
配置X-Huiju-1为实例1主根。实例2、3备根:
stp instance 1 root primary
stp instance 2 root secondary
stp instance 3 root secondary
配置X-Huiju-2为实例2主根。实例1备根:
stp instance 1 root secondary
stp instance 2 root primary
配置X-Core为实例3主根:
stp instance 3 root primary
VRRP配置:
X-Huiju-1:
interface Vlanif10
ip address 192.168.10.252 255.255.255.0
vrrp vrid 10 virtual-ip 192.168.10.254
vrrp vrid 10 priority 120
vrrp vrid 10 timer advertise 10
#
interface Vlanif20
ip address 192.168.20.252 255.255.255.0
vrrp vrid 20 virtual-ip 192.168.20.254
vrrp vrid 20 timer advertise 10
#
interface Vlanif100
ip address 192.168.100.252 255.255.255.0
vrrp vrid 100 virtual-ip 192.168.100.254
vrrp vrid 100 priority 120
vrrp vrid 100 timer advertise 10
#
interface Vlanif101
ip address 192.168.101.252 255.255.255.0
vrrp vrid 101 virtual-ip 192.168.101.254
vrrp vrid 101 timer advertise 10
#
interface Vlanif102
ip address 192.168.102.252 255.255.255.0
vrrp vrid 102 virtual-ip 192.168.102.254
vrrp vrid 102 timer advertise 10
X-Huiju-2:
interface Vlanif10
ip address 192.168.10.253 255.255.255.0
vrrp vrid 10 virtual-ip 192.168.10.254
vrrp vrid 10 timer advertise 10
#
interface Vlanif20
ip address 192.168.20.253 255.255.255.0
vrrp vrid 20 virtual-ip 192.168.20.254
vrrp vrid 20 priority 120
vrrp vrid 20 timer advertise 10
#
interface Vlanif100
ip address 192.168.100.253 255.255.255.0
vrrp vrid 100 virtual-ip 192.168.100.254
vrrp vrid 100 timer advertise 10
#
interface Vlanif101
ip address 192.168.101.253 255.255.255.0
vrrp vrid 101 virtual-ip 192.168.101.254
vrrp vrid 101 priority 120
vrrp vrid 101 timer advertise 10
#
interface Vlanif102
ip address 192.168.102.253 255.255.255.0
vrrp vrid 102 virtual-ip 192.168.102.254
vrrp vrid 102 priority 120
vrrp vrid 102 timer advertise 10
查看vrrp状态:
[X-Huiju-2-Eth-Trunk1]display vrrp brief
VRID State Interface Type Virtual IP
----------------------------------------------------------------
10 Backup Vlanif10 Normal 192.168.10.254
20 Master Vlanif20 Normal 192.168.20.254
100 Backup Vlanif100 Normal 192.168.100.254
101 Master Vlanif101 Normal 192.168.101.254
102 Master Vlanif102 Normal 192.168.102.254
----------------------------------------------------------------
Total:5 Master:3 Backup:2 Non-active:0
5.配置防火墙和路由器的基础ip地址配置
防火墙:
interface GigabitEthernet1/0/0 --连接服务器的交换机
undo shutdown
ip address 192.168.14.254 255.255.255.0
#
interface GigabitEthernet1/0/1 --连接出口路由器2
undo shutdown
ip address 192.168.16.254 255.255.255.0
#
interface GigabitEthernet1/0/2 ----连接出口路由器1
undo shutdown
ip address 192.168.15.254 255.255.255.0
#
interface GigabitEthernet1/0/3 --连接核心交换机
undo shutdown
ip address 192.168.13.1 255.255.255.0
service-manage ping permit ---允许接口ping
将每个接口划入对应安全区域:
firewall zone trust
add interface GigabitEthernet1/0/3
#
firewall zone untrust
add interface GigabitEthernet1/0/1
add interface GigabitEthernet1/0/2
#
firewall zone dmz
add interface GigabitEthernet1/0/0
配置策略:
security-policy
rule name trust-local-permit-ospf --定义一个策略,使trust和local能够建立ospf
source-zone local
source-zone trust
destination-zone local
destination-zone trust
service icmp
service ospf
action permit
rule name untrust-local-ospf --定义一个策略,使untrust和local能够建立ospf
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
service icmp
service ospf
action permit
X-Export-1:
interface GigabitEthernet0/0/0
ip address 192.168.15.1 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 172.16.1.1 255.255.255.252
#
interface GigabitEthernet1/0/0 --连接internet
ip address 20.1.1.2 255.255.255.252
X-Export-2:
interface GigabitEthernet0/0/0
ip address 192.168.16.1 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 172.16.1.2 255.255.255.252
#
interface GigabitEthernet1/0/0 --连接internet
ip address 20.1.2.2 255.255.255.252
internet:
interface GigabitEthernet0/0/0
ip address 20.1.1.1 255.255.255.252
#
interface GigabitEthernet0/0/1
ip address 20.1.2.1 255.255.255.252
#
interface LoopBack0
ip address 8.8.8.8 255.255.255.255
6.配置内网OSPF互通

X-Huiju-1:
interface Vlanif11
ip address 192.168.11.1 255.255.255.0
ospf network-type p2p
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
ospf enable 1 area 0.0.0.0
ospf 1 router-id 1.1.1.1
silent-interface Vlanif10
silent-interface Vlanif20
silent-interface Vlanif100
silent-interface Vlanif101
silent-interface Vlanif102
area 0.0.0.0
network 192.168.10.0 0.0.0.255
network 192.168.20.0 0.0.0.255
network 192.168.100.0 0.0.0.255
network 192.168.101.0 0.0.0.255
network 192.168.102.0 0.0.0.255
network 192.168.11.1 0.0.0.0
X-Huiju-2:
interface Vlanif12
ip address 192.168.12.1 255.255.255.0
ospf network-type p2p
interface LoopBack0
ip address 2.2.2.2 255.255.255.255
ospf enable 1 area 0.0.0.0
ospf 1 router-id 2.2.2.2
silent-interface Vlanif10
silent-interface Vlanif20
silent-interface Vlanif100
silent-interface Vlanif101
silent-interface Vlanif102
area 0.0.0.0
network 192.168.10.0 0.0.0.255
network 192.168.20.0 0.0.0.255
network 192.168.100.0 0.0.0.255
network 192.168.101.0 0.0.0.255
network 192.168.102.0 0.0.0.255
network 192.168.12.1 0.0.0.0
X-Core:
interface LoopBack0
ip address 3.3.3.3 255.255.255.255
ospf enable 1 area 0.0.0.0
ospf 1 router-id 3.3.3.3
silent-interface Vlanif99
area 0.0.0.0
network 192.168.99.0 0.0.0.255
network 192.168.11.0 0.0.0.255
network 192.168.12.0 0.0.0.255
network 192.168.13.254 0.0.0.0
X-FW:
interface LoopBack0
ip address 4.4.4.4 255.255.255.255
ospf enable 1 area 0.0.0.0
ospf 1 router-id 4.4.4.4
area 0.0.0.0
network 192.168.13.1 0.0.0.0
network 192.168.14.0 0.0.0.255
network 192.168.15.254 0.0.0.0
network 192.168.16.254 0.0.0.0
X-Export-1:
interface LoopBack0
ip address 5.5.5.5 255.255.255.255
ospf enable 1 area 0.0.0.0
ospf 1 router-id 5.5.5.5
area 0.0.0.0
network 172.16.1.1 0.0.0.0
network 192.168.15.1 0.0.0.0
X-Export-2:
interface LoopBack0
ip address 6.6.6.6 255.255.255.255
ospf enable 1 area 0.0.0.0
ospf 1 router-id 6.6.6.6
area 0.0.0.0
network 172.16.1.2 0.0.0.0
network 192.168.16.1 0.0.0.0
查看OSPF邻居和路由:
[X-FW]display ospf peer brief
2023-06-27 14:28:30.090
OSPF Process 1 with Router ID 4.4.4.4
Peer Statistic Information
----------------------------------------------------------------------------
Area Id Interface Neighbor id State
0.0.0.0 GigabitEthernet1/0/1 6.6.6.6 Full
0.0.0.0 GigabitEthernet1/0/2 5.5.5.5 Full
0.0.0.0 GigabitEthernet1/0/3 3.3.3.3 Full
----------------------------------------------------------------------------
Total Peer(s): 3
[X-FW]display ospf routing
2023-06-27 14:28:44.930
OSPF Process 1 with Router ID 4.4.4.4
Routing Tables
Routing for Network
Destination Cost Type NextHop AdvRouter Area
4.4.4.4/32 0 Stub 4.4.4.4 4.4.4.4 0.0.0.0
192.168.13.0/24 1 Transit 192.168.13.1 4.4.4.4 0.0.0.0
192.168.14.0/24 1 Stub 192.168.14.254 4.4.4.4 0.0.0.0
192.168.15.0/24 1 Transit 192.168.15.254 4.4.4.4 0.0.0.0
192.168.16.0/24 1 Transit 192.168.16.254 4.4.4.4 0.0.0.0
1.1.1.1/32 2 Stub 192.168.13.254 1.1.1.1 0.0.0.0
2.2.2.2/32 2 Stub 192.168.13.254 2.2.2.2 0.0.0.0
3.3.3.3/32 1 Stub 192.168.13.254 3.3.3.3 0.0.0.0
5.5.5.5/32 1 Stub 192.168.15.1 5.5.5.5 0.0.0.0
6.6.6.6/32 1 Stub 192.168.16.1 6.6.6.6 0.0.0.0
172.16.1.0/30 2 Transit 192.168.15.1 6.6.6.6 0.0.0.0
172.16.1.0/30 2 Transit 192.168.16.1 6.6.6.6 0.0.0.0
192.168.10.0/24 3 Stub 192.168.13.254 2.2.2.2 0.0.0.0
192.168.10.254/32 3 Stub 192.168.13.254 1.1.1.1 0.0.0.0
192.168.11.0/24 2 Stub 192.168.13.254 3.3.3.3 0.0.0.0
192.168.12.0/24 2 Stub 192.168.13.254 3.3.3.3 0.0.0.0
192.168.20.0/24 3 Stub 192.168.13.254 2.2.2.2 0.0.0.0
192.168.20.254/32 3 Stub 192.168.13.254 2.2.2.2 0.0.0.0
192.168.99.0/24 2 Stub 192.168.13.254 3.3.3.3 0.0.0.0
192.168.100.0/24 3 Stub 192.168.13.254 2.2.2.2 0.0.0.0
192.168.100.254/32 3 Stub 192.168.13.254 1.1.1.1 0.0.0.0
192.168.101.0/24 3 Stub 192.168.13.254 2.2.2.2 0.0.0.0
192.168.101.254/32 3 Stub 192.168.13.254 2.2.2.2 0.0.0.0
192.168.102.0/24 3 Stub 192.168.13.254 2.2.2.2 0.0.0.0
192.168.102.254/32 3 Stub 192.168.13.254 2.2.2.2 0.0.0.0
Total Nets: 25
Intra Area: 25 Inter Area: 0 ASE: 0 NSSA: 0
在汇聚1能够ping同出接口2:
[X-Huiju-1]ping -a 1.1.1.1 6.6.6.6
PING 6.6.6.6: 56 data bytes, press CTRL_C to break
Reply from 6.6.6.6: bytes=56 Sequence=1 ttl=253 time=70 ms
Reply from 6.6.6.6: bytes=56 Sequence=2 ttl=253 time=60 ms
Reply from 6.6.6.6: bytes=56 Sequence=3 ttl=253 time=70 ms
Reply from 6.6.6.6: bytes=56 Sequence=4 ttl=253 time=50 ms
Reply from 6.6.6.6: bytes=56 Sequence=5 ttl=253 time=60 ms
--- 6.6.6.6 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 50/62/70 ms
7.配置DHCP,使AP和PC能获取ip地址
我在两台汇聚上配置DHCP服务器:(两台配置一样)
ip pool ap
gateway-list 192.168.100.254
network 192.168.100.0 mask 255.255.255.0
excluded-ip-address 192.168.100.250 192.168.100.253
option 43 sub-option 2 ip-address 192.168.99.254
#
ip pool cw
gateway-list 192.168.101.254
network 192.168.101.0 mask 255.255.255.0
excluded-ip-address 192.168.101.250 192.168.101.253
#
ip pool pc-10
gateway-list 192.168.10.254
network 192.168.10.0 mask 255.255.255.0
excluded-ip-address 192.168.10.250 192.168.10.253
#
ip pool pc-20
gateway-list 192.168.20.254
network 192.168.20.0 mask 255.255.255.0
excluded-ip-address 192.168.20.250 192.168.20.253
#
ip pool xs
gateway-list 192.168.102.254
network 192.168.102.0 mask 255.255.255.0
excluded-ip-address 192.168.102.250 192.168.102.253
在vlanif接口上应用:(两台配置一样)
interface Vlanif10
dhcp select global
#
interface Vlanif20
dhcp select global
#
interface Vlanif100
dhcp select global
#
interface Vlanif101
dhcp select global
#
interface Vlanif102
dhcp select global
8.配置AC,以及基于VRRP的热备
Master:
vlan batch 99
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 99
interface Vlanif99
ip address 192.168.99.252 255.255.255.0
vrrp vrid 99 virtual-ip 192.168.99.254
admin-vrrp vrid 99
vrrp vrid 99 priority 120
vrrp vrid 99 preempt-mode timer delay 30
vrrp vrid 99 timer advertise 10
Standby:
vlan batch 99
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 99
interface Vlanif99
ip address 192.168.99.253 255.255.255.0
vrrp vrid 99 virtual-ip 192.168.99.254
admin-vrrp vrid 99
vrrp vrid 99 preempt-mode timer delay 30
vrrp vrid 99 timer advertise 10
查看vrrp状态:
[Master]display vrrp brief
Total:1 Master:1 Backup:0 Non-active:0
VRID State Interface Type Virtual IP
----------------------------------------------------------------
99 Master Vlanif99 Admin 192.168.99.254
hsb备份:
两台配置基本一样,除了本地地址和对端地址两边要互换一下!!!
hsb-service 0
service-ip-port local-ip 192.168.99.252 peer-ip 192.168.99.253 local-data-port
20001 peer-data-port 20001
hsb-group 0
track vrrp vrid 99 interface Vlanif99
bind-service 0
hsb-service-type access-user hsb-group 0
hsb-service-type ap hsb-group 0
hsb-group 0
hsb enable
查看hsb备份:
[Master]display hsb-service 0
Hot Standby Service Information:
----------------------------------------------------------
Local IP Address : 192.168.99.252
Peer IP Address : 192.168.99.253
Source Port : 20001
Destination Port : 20001
Keep Alive Times : 5
Keep Alive Interval : 3
Service State : Connected
Service Batch Modules :
----------------------------------------------------------
[Master]display hsb-group 0
Hot Standby Group Information:
----------------------------------------------------------
HSB-group ID : 0
Vrrp Group ID : 99
Vrrp Interface : Vlanif99
Service Index : 0
Group Vrrp Status : Master
Group Status : Active
Group Backup Process : Realtime
Peer Group Device Name : AC6605
Peer Group Software Version : V200R007C10SPC300B220
Group Backup Modules : Access-user
AP
----------------------------------------------------------
9.AP上线
两台都要配置:
capwap source ip-address 192.168.99.254 --指定AP和AC通信的隧道地址,记得是vrrp的虚拟IP地址
wlan视图下:
wlan
ap-group name X-CW-AP --定义财务的AP组
ap-group name X-XS-AP --定义销售的AP组
ap auth-mode mac-auth --华为默认是mac地址认证
ap-id 0 ap-mac 00e0-fc43-2d40 --静态绑定CW-AP的MAC地址
ap-name X-CW-AP
ap-group X-CW-AP
ap-id 1 ap-mac 00e0-fc08-1930 --静态绑定XS-AP的MAC地址
ap-name X-XS-AP
ap-group X-XS-AP
查看AP是否上线:
[Master]display ap all
Info: This operation may take a few seconds. Please wait for a moment.done.
Total AP information:
nor : normal [2]
--------------------------------------------------------------------------------
-------------------
ID MAC Name Group IP Type State STA Up
time
--------------------------------------------------------------------------------
-------------------
0 00e0-fc43-2d40 X-CW-AP X-CW-AP 192.168.100.249 AP6050DN nor 1 1H
:30M:26S
1 00e0-fc08-1930 X-XS-AP X-XS-AP 192.168.100.248 AP6050DN nor 1 1H
:30M:26S
--------------------------------------------------------------------------------
-------------------
Total: 2
10.WLAN业务配置下发
wlan
security-profile name X-CW-AP --定义财务AP的密码
security wpa psk pass-phrase Huawei@123 aes
security-profile name X-XS-AP --定义销售AP的密码
security wpa-wpa2 psk pass-phrase admin@123 aes
ssid-profile name X-CW-AP --定义财务AP的SSID
ssid X-CW-AP
ssid-profile name X-XS-AP --定义销售AP的SSID
ssid X-XS-AP
vap-profile name X-CW-AP --在虚拟AP下关联SSID/安全认证/下发的vlan等
service-vlan vlan-id 101
ssid-profile X-CW-AP
security-profile X-CW-AP
forward-mode direct-forward --默认是直接转发模式
vap-profile name X-XS-AP --在虚拟AP下关联SSID/安全认证/下发的vlan等
service-vlan vlan-id 102
ssid-profile X-XS-AP
security-profile X-XS-AP
forward-mode direct-forward
ap-group name X-CW-AP --在AP组内应用VAP
vap-profile X-CW-AP wlan 1 radio all
ap-group name X-XS-AP --在AP组内应用VAP
vap-profile X-CW-AP wlan 6 radio all
看见AP发出光圈就是WLAN配置下发生效

11.STA上线
STA开机,选择想连接的SSID。输入密码,认证成功即可上线

可以看见分配的ip地址

12.模拟其中一个AC故障
先看一下vrrp备份是否起来了
[Master]display ap all
0 00e0-fc43-2d40 X-CW-AP X-CW-AP 192.168.100.249 AP6050DN nor 1 1H
:41M:52S
1 00e0-fc08-1930 X-XS-AP X-XS-AP 192.168.100.248 AP6050DN nor 1 1H
:41M:52S
<Standby>display ap all
--------------------------------------------------------------------------------
---------------
ID MAC Name Group IP Type State STA Up
time
--------------------------------------------------------------------------------
---------------
0 00e0-fc43-2d40 X-CW-AP X-CW-AP 192.168.100.249 AP6050DN stdby 1 -
1 00e0-fc08-1930 X-XS-AP X-XS-AP 192.168.100.248 AP6050DN stdby 0 -
很好一主一备。起来了,接下来测试:
先让STA1不断ping出接口地址

接下来将主设备接口shutdown
[Master]int g 0/0/1
[Master-GigabitEthernet0/0/1]shutdown
<Standby>display ap all ---此时备设备AP状态nor,STA业务没有收到影响
ID MAC Name Group IP Type State STA Up
time
--------------------------------------------------------------------------------
-------------------
0 00e0-fc43-2d40 X-CW-AP X-CW-AP 192.168.100.249 AP6050DN nor 1 1H
:44M:48S
1 00e0-fc08-1930 X-XS-AP X-XS-AP 192.168.100.248 AP6050DN nor 0 1H
:44M:48S

接着再将主设备接口恢复,看一下业务和接口收到影响吗?
由于我设置的vrrp抢占时延为30秒,所以能看见vrrp状态转变的过程:由initialize变为backup再变为master
[Master-GigabitEthernet0/0/1]undo shutdown
[Master-GigabitEthernet0/0/1]display vrrp brief
99 Initialize Vlanif99 Admin 192.168.99.254
[Master-GigabitEthernet0/0/1]display vrrp brief
99 Backup Vlanif99 Admin 192.168.99.254
[Master-GigabitEthernet0/0/1]display vrrp brief
99 Master Vlanif99 Admin 192.168.99.254
[Master-GigabitEthernet0/0/1]display ap all
0 00e0-fc43-2d40 X-CW-AP X-CW-AP 192.168.100.249 AP6050DN nor 1 1H
:49M:23S
1 00e0-fc08-1930 X-XS-AP X-XS-AP 192.168.100.248 AP6050DN nor 0 1H
:49M:23S
此时AP主为master设备,在时候看看业务有没有受到影响

业务没有受到影响,证明基于VRRP的AC双机热备成功!!!
13.在防火墙配置策略,使内网用户能访问外网和服务器
security-policy
rule name trust-to-dmz
source-zone trust
destination-zone dmz
service dns
service ftp
service http
service icmp
action permit
rule name permit-trust_to_untrust
source-zone trust
destination-zone untrust
action permit
先在两台出口路由配置默认路由和NAT策略:(这里我以其中一台为例)
出口路由器1:
acl number 2000
rule 5 permit
ip route-static 0.0.0.0 0 20.1.1.1
interface GigabitEthernet1/0/0 ---配置easy-ip
nat outbound 2000
ospf 1 ---在ospf中下发默认路由
default-route-advertise
测试:
CW-PC1:
PC>ping 192.168.15.1 --服务器HTTP的地址
Ping 192.168.15.1: 32 data bytes, Press Ctrl_C to break
From 192.168.15.1: bytes=32 seq=1 ttl=252 time=94 ms
From 192.168.15.1: bytes=32 seq=2 ttl=252 time=94 ms
--- 192.168.15.1 ping statistics ---
2 packet(s) transmitted
2 packet(s) received
0.00% packet loss
round-trip min/avg/max = 94/94/94 ms
PC>ping 8.8.8.8 --internet的环回口地址
Ping 8.8.8.8: 32 data bytes, Press Ctrl_C to break
From 8.8.8.8: bytes=32 seq=1 ttl=251 time=109 ms
From 8.8.8.8: bytes=32 seq=2 ttl=251 time=78 ms
From 8.8.8.8: bytes=32 seq=3 ttl=251 time=109 ms
From 8.8.8.8: bytes=32 seq=4 ttl=251 time=94 ms
14.配置策略,使CW-PC1不能访问CW-PC2,而CW-PC2可以访问CW-PC1
在接入1上配置:
acl number 3000
rule 5 deny ip source 192.168.10.249 0 destination 192.168.10.248 0 --拒绝PC1pingPC2
rule 10 permit ip ---允许其他流量
[X-Jieru-1-Ethernet0/0/1] traffic-filter inbound acl 3000 --在入接口应用
测试:

反ping能通



