- 1漏洞&修复规范描述_httplimitreqmodule and httplimitzonemodule
- 2短视频seo抖音矩阵源码开发搭建技术解析_抖音矩阵一键发布 用的什么接口
- 3复旦微JFM7VX690计算后IO接口模块,用于雷达信号处理、数据处理等需要高速密集计算的应用场景
- 4GPT实战系列-LangChain如何构建基通义千问的多工具链_通义千问 集成langchain好多样例跑不通
- 5微信公众号&小程序 -- 获取并解密用户数据(获取openId、unionId)
- 6android studio简单实现登录注册界面的跳转,新手教学android期末项目点击简单跳转界面的实现_android登录跳转简单界面
- 7chatGPT与传统搜索引擎的比较_chatgpt跟csdn对比
- 8OAuth 2.1 带来了哪些变化_说透oauth 2.1
- 9inpaint-anything:分割任何东西遇到图像修复_inpaint anything macos 12错误
- 10PX4 OffBoard Control_offboard_control
Linux系统安全与应用【二】
赞
踩
目录
1.开关机安全控制
1.1 GRUB限制

限制更改GRUB引导参数
通常情况下在系统开机进入GRUB菜单时,按e键可以查看并修改GRUB引导参数,这对服务器是一个极大的威胁。
可以为GRUB 菜单设置一个密码,只有提供正确的密码才被允许修改引导参数。
1.2 实例:GRUB 菜单设置密码
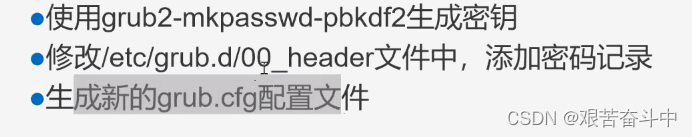
(1)根据提示设置GRUB菜单的密码;
(2)备份密码字符串、grub.cfg文件以及00_header文件;
(3)设置能够修改GRUB菜单的用户名和密码;

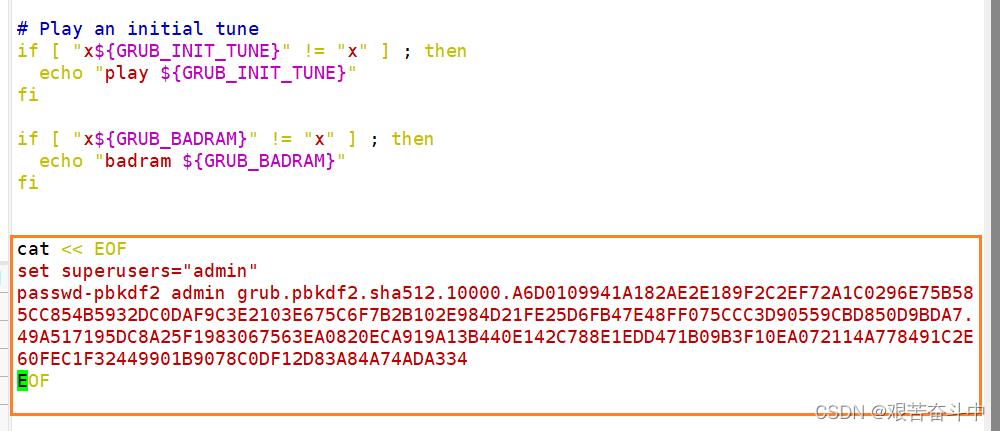
(4)生成新的grub.cfg文件;


2.终端登录安全控制
2.1 限制root只在安全终端登录


/etc/securetty:保存虚拟终端的配置文件,注释指定虚拟主机,将无法登录到系统;

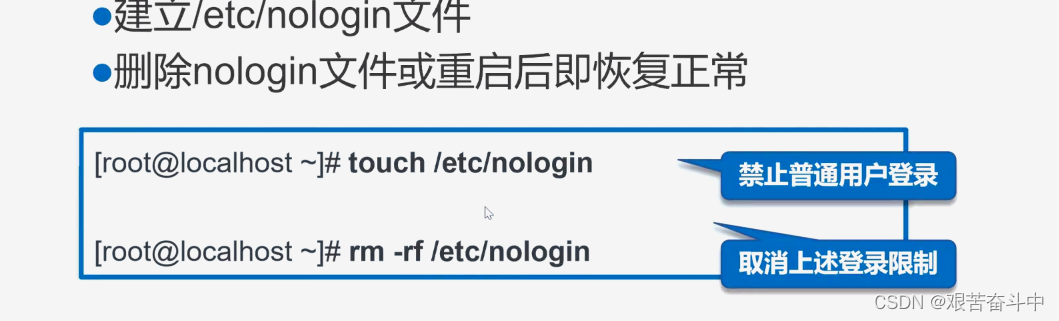
2.2 禁止普通用户登录
 A
A
/etc/nologin:创建该文件后,普通用户将无法再登录到系统中;
- [root@localhost ~]# touch /etc/nologin #创建文件,禁止普通用户登录
- [root@localhost ~]# rm -f /etc/nologin #删除该文件后,其他普通文件仍然又可以继续登录到系统中
 3.弱口令检测
3.弱口令检测
3.1 Joth the Ripper,JR
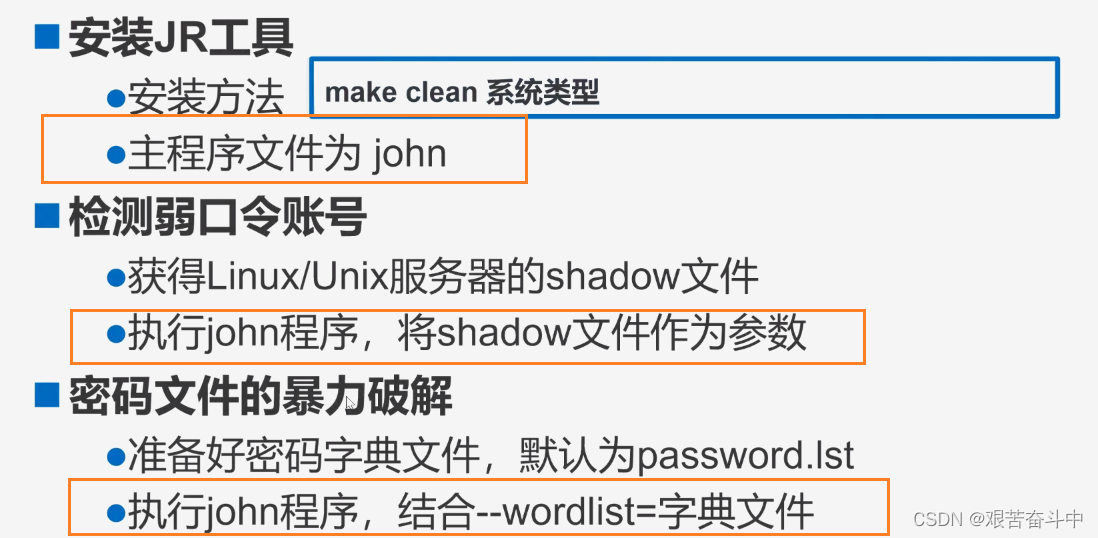
使用jr工具密码破解 ,步骤如下:
(1) 解压工具包
- [root@localhost ~]# cd /opt
- [root@localhost opt]# ls #将john压缩工具包拉入虚拟机中
- john-1.8.0.tar.gz rh
- [root@localhost opt]# tar xf john-1.8.0.tar.gz #解压工具包
(2)切换到src子目录
- [root@localhost opt]# ls
- john-1.8.0 john-1.8.0.tar.gz rh
- [root@localhost opt]# cd john-1.8.0/
- [root@localhost john-1.8.0]# ls
- doc README run src
- [root@localhost john-1.8.0]# cd src/
(3)进行编译安装
- [root@localhost src]# yum install -y gcc gcc-c++ make #编码安装之前先安装gcc
- 已加载插件:fastestmirror, langpacks
- Loading mirror speeds from cached hostfile
- * base: ftp.sjtu.edu.cn
- * extras: mirrors.163.com
- * updates: mirrors.163.com
- 软件包 gcc-4.8.5-44.el7.x86_64 已安装并且是最新版本
- 软件包 gcc-c++-4.8.5-44.el7.x86_64 已安装并且是最新版本
- 软件包 1:make-3.82-24.el7.x86_64 已安装并且是最新版本
- 无须任何处理
- rm -f ../run/unshadow
- ln -s john ../run/unshadow
- rm -f ../run/unafs
- ln -s john ../run/unafs
- rm -f ../run/unique
- ln -s john ../run/unique
- make[1]: 离开目录“/opt/john-1.8.0/src

(4)准备待破解的密码文件
- [root@localhost src]# cd ..
- [root@localhost john-1.8.0]# ls
- doc README run src
- [root@localhost john-1.8.0]# cd run/
- [root@localhost run]# ls
- ascii.chr john lm_ascii.chr makechr relbench unique
- digits.chr john.conf mailer password.lst unafs unshadow
- [root@localhost run]# cp /etc/shadow ./shadow #将/etc/shadow下的文件复制到当前目录下的shadow.txt文件中
( 5)执行暴力破解(./john --wordlist=[指定字典文件的绝对路径] [需要破解的文件名]:使用指定的字典文件进行破解)
- [root@localhost run]# ./john shadow --wordlist=./password.lst #执行暴力破解密码
- Loaded 4 password hashes with 4 different salts (crypt, generic crypt(3) [?/64])
- Press 'q' or Ctrl-C to abort, almost any other key for status
- 123456 (zhangsan)
- 123123 (lisi)
- 2g 0:00:01:02 100% 0.03212g/s 56.96p/s 123.1c/s 123.1C/s !@#$%..sss
- Use the "--show" option to display all of the cracked passwords reliably
- Session completed
- [root@localhost run]#
password.lst:该文件保存密码字典
- [root@localhost /opt/john-1.8.0/run]# vim password.lst #该文件保存密码字典,只有保存在字典里的密码才能够破解出来,对于字典里没有的密码,将无法破解(字典里的文件越全,破解能力越强)
- slip
- stivers
- test2
- test3
- tula
- unix
- user1
- xanth
john.pot:破解后的密码信息都保存在该文件中,加密后的字符串对应解密后的密码
- [root@localhost run]# vim john.pot
-
- $6$BZfw4ECl$6X4RYQDDzbDlmXYN1N7E4lz9sA7VmSpVfPkfLFDh8bvUSHPYODst3h9kEnz/k4UU7M0gybLdnjqi0ofSpc41J/:123456
- $6$ir9lWkcD$NbNigOetdQuBSrfwXwB63z9cg8rCMasotwVb5WgfdEKdKD6VzZyjz8ey4agu5axJChKy.KwT94XO1NE/lXXcX/:123123
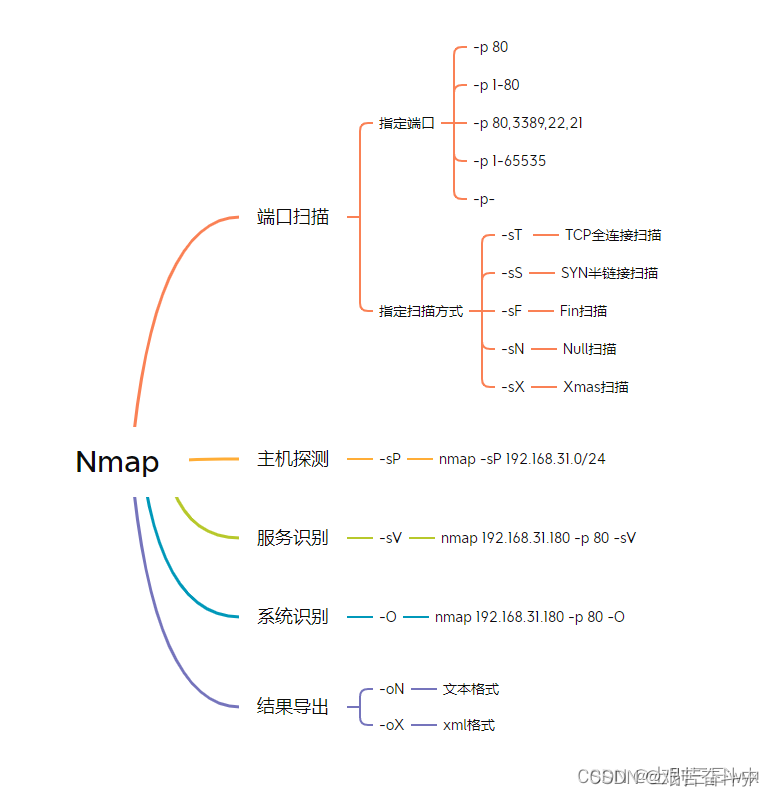
4.网络端口扫描
4.1 nmap命令

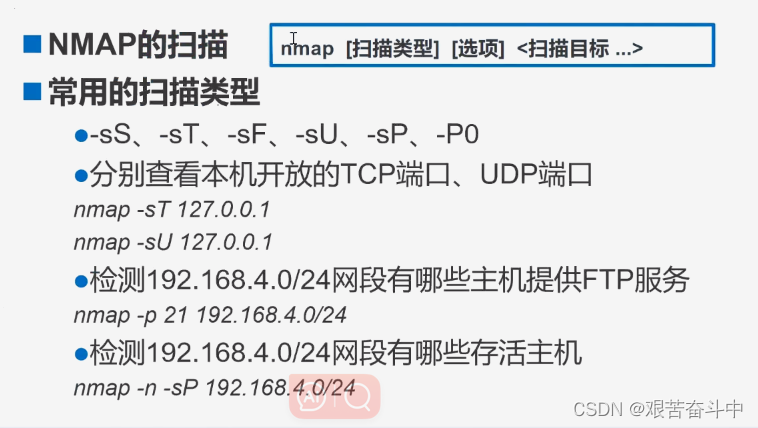
netstat -lntp:以数字形式显示TCP处于监听状态的网络连接及端口信息
- [root@localhost yum.repos.d]# netstat -lntp
- Active Internet connections (only servers)
- Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
- tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1099/sshd
- tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 1101/cupsd
- tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 1425/master
- tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN 1134/named
- tcp 0 0 127.0.0.1:6010 0.0.0.0:* LISTEN 4199/sshd: root@pts
- tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN 715/rpcbind
- tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN 1134/named
- tcp 0 0 192.168.80.100:53 0.0.0.0:* LISTEN 1134/named
- tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 1134/named
- tcp6 0 0 :::22 :::* LISTEN 1099/sshd
- tcp6 0 0 ::1:631 :::* LISTEN 1101/cu
netstat -antp:以数字形式显示TCP所有状态下的网络连接及端口信息
- [root@localhost yum.repos.d]# netstat -antp
- Active Internet connections (servers and established)
- Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
- tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1099/sshd
- tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 1101/cupsd
- tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 1425/master
- tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN 1134/named
- tcp 0 0 127.0.0.1:6010 0.0.0.0:* LISTEN 4199/sshd: root@pts
- tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN 715/rpcbind
- tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN 1134/named
- tcp 0 0 192.168.80.100:53 0.0.0.0:* LISTEN 1134/named
- tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 1134/named
- tcp 0 36 192.168.80.100:22 192.168.80.1:60425 ESTABLISHED 4199/ss
ss -antp:以数字形式显示TCP所有状态下的网络连接及端口信息;(效果和netstat命令相同,但执行效率比netstat命令更高)
- [root@localhost yum.repos.d]# ss -antp
- State Recv-Q Send-Q Local Address:Port Peer Address:Port
- LISTEN 0 128 *:22 *:* users:(("sshd",pid=1099,fd=3))
- LISTEN 0 128 127.0.0.1:631 *:* users:(("cupsd",pid=1101,fd=11))
- LISTEN 0 100 127.0.0.1:25 *:* users:(("master",pid=1425,fd=13))
- LISTEN 0 128 127.0.0.1:953 *:* users:(("named",pid=1134,fd=23))
- LISTEN 0 128 127.0.0.1:6010 *:* users:(("sshd",pid=4199,fd=9))
- LISTEN 0 128 *:111 *:* users:(("rpcbind",pid=715,fd=8))
- LISTEN 0 10 192.168.122.1:53 *:* users:(("named",pid=1134,fd=25))
- LISTEN 0 10 192.168.80.100:53 *:*
查看进程是否开启的四种方法
- [root@localhost opt]# ps -elf | grep ssdh
- 0 S root 5375 4207 0 80 0 - 28206 pipe_w 16:14 pts/0 00:00:00 grep --color=auto ssdh
- [root@localhost opt]# netstat -lntp | grep sshd #第一种
- tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1099/sshd
- tcp 0 0 127.0.0.1:6010 0.0.0.0:* LISTEN 4199/sshd: root@pts
- tcp6 0 0 :::22 :::* LISTEN 1099/sshd
- tcp6 0 0 ::1:6010 :::* LISTEN 4199/sshd: root@pts
- [root@localhost opt]# ps aux | grep httpd #第二种
- root 5464 0.0 0.0 112824 988 pts/0 S+ 16:19 0:00 grep --color=auto httpd
- [root@localhost opt]# lsof -i :80 #第三种
- COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
- httpd 5563 root 4u IPv6 71872 0t0 TCP *:http (LISTEN)
- httpd 5568 apache 4u IPv6 71872 0t0 TCP *:http (LISTEN)
- httpd 5569 apache 4u IPv6 71872 0t0 TCP *:http (LISTEN)
- httpd 5570 apache 4u IPv6 71872 0t0 TCP *:http (LISTEN)
- httpd 5571 apache 4u IPv6 71872 0t0 TCP *:http (LISTEN)
- httpd 5572 apache 4u IPv6 71872 0t0 TCP *:http (LISTEN)
- [root@localhost opt]# systemctl status httpd #第四种
- ● httpd.service - The Apache HTTP Server
- Loaded: loaded (/usr/lib/systemd/system/httpd.service; disabled; vendor preset: disabled)
- Active: active (running) since 六 2024-04-27 16:27:02 CST; 11s ago
- Docs: man:httpd(8)
- man:apachectl(8)
- Main PID: 5563 (httpd)
- Status: "Total requests: 0; Current requests/sec: 0; Current traffic: 0 B/sec"
- Tasks: 6
- CGroup: /system.slice/httpd.service
- ├─5563 /usr/sbin/httpd -DFOREGROUND
- ├─5568 /usr/sbin/httpd -DFOREGROUND
- ├─5569 /usr/sbin/httpd -DFOREGROUND
- ├─5570 /usr/sbin/httpd -DFOREGROUND
- ├─5571 /usr/sbin/httpd -DFOREGROUND
- └─5572 /usr/sbin/httpd -DFOREGROUND
-

如何通过端口查看进程号
- [root@localhost opt]# netstat -lntp | grep sshd
- tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1099/sshd
- tcp 0 0 127.0.0.1:6010 0.0.0.0:* LISTEN 4199/sshd: root@pts
- tcp6 0 0 :::22 :::* LISTEN 1099/sshd
- tcp6 0 0 ::1:6010 :::* LISTEN 4199/sshd: root@pts
- [root@localhost opt]# lsof -i :80
- COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
- httpd 5563 root 4u IPv6 71872 0t0 TCP *:http (LISTEN)
- httpd 5568 apache 4u IPv6 71872 0t0 TCP *:http (LISTEN)
- httpd 5569 apache 4u IPv6 71872 0t0 TCP *:http (LISTEN)
- httpd 5570 apache 4u IPv6 71872 0t0 TCP *:http (LISTEN)
- httpd 5571 apache 4u IPv6 71872 0t0 TCP *:http (LISTEN)
- httpd 5572 apache 4u IPv6 71872 0t0 TCP *:http (LISTEN)
- [root@localhost opt]# ss -lntup | grep :80
- tcp LISTEN 0 128 [::]:80 [::]:* users:(("httpd",pid=5572,fd=4),("httpd",pid=5571,fd=4),("httpd",pid=5570,fd=4),("httpd",pid=5569,fd=4),("httpd",pid=5568,fd=4),("httpd",pid=5563,fd=4))
nmap -p 80 192.168.80.0/24 :扫描出指定192.168.80.0网段内有哪些主机开启了80端口
- [root@localhost opt]# nmap -p 80 192.168.80.0/24
-
- Starting Nmap 6.40 ( http://nmap.org ) at 2024-04-27 16:59 CST
- Nmap scan report for 192.168.80.1
- Host is up (0.00051s latency).
- PORT STATE SERVICE
- 80/tcp closed http
- MAC Address: 00:50:56:C0:00:08 (VMware)
-
- Nmap scan report for 192.168.80.2
- Host is up (0.00025s latency).
- PORT STATE SERVICE
- 80/tcp closed http
- MAC Address: 00:50:56:E7:A2:D5 (VMware)
-
- Nmap scan report for 192.168.80.254
- Host is up (-0.10s latency).
- PORT STATE SERVICE
- 80/tcp filtered http
- MAC Address: 00:50:56:E8:8F:B7 (VMware)
-
- Nmap scan report for 192.168.80.100
- Host is up (0.00020s latency).
- PORT STATE SERVICE
- 80/tcp open http
-
- Nmap done: 256 IP addresses (4 hosts up) scanned in 2.69 seconds

nmap -n -sP 192.168.80.0/24:查看192.168.80.0网段内,有哪些主机存活
- [root@localhost opt]# nmap -n -sP 192.168.80.0/24
-
- Starting Nmap 6.40 ( http://nmap.org ) at 2024-04-27 17:04 CST
- Nmap scan report for 192.168.80.1
- Host is up (0.0011s latency).
- MAC Address: 00:50:56:C0:00:08 (VMware)
- Nmap scan report for 192.168.80.2
- Host is up (0.00013s latency).
- MAC Address: 00:50:56:E7:A2:D5 (VMware)
- Nmap scan report for 192.168.80.254
- Host is up (-0.10s latency).
- MAC Address: 00:50:56:E8:8F:B7 (VMware)
- Nmap scan report for 192.168.80.100
- Host is up.
- Nmap done: 256 IP addresses (4 hosts up) scanned in 2.17 seconds
4.2 nmap使用方法