- 12024最新版Android studio傻瓜式安装入门教程,学不会你来找我!_android studio最新版本安装教程
- 237、Flink 的CDC 格式:debezium部署以及mysql示例(1)-debezium的部署与示例_flink debeziumproperties 设置
- 3k8s知识点_maxsurge
- 4支付测试点_支付的测试点有哪些
- 5rosbridge入门教程_rosbridge_suite
- 6数据清洗【Python文本数据处理】_python 文本清洗
- 7PyTorch 8.权值初始化与损失函数_coneo w1ih
- 8探索Label Studio:一款强大的多模态标注工具
- 9MySQL面试宝典-文件篇_mysql默认表空间
- 10【隐私计算学习笔记】第一讲 数据可信流通:从运维信任到技术信任
防火墙配置(初学防火墙的小伙伴,带你了解防火墙,每天更新一篇关于防火墙的配置,零基础入手,快速了解防火墙,一起学习,讨论,进步)_set priority 85
赞
踩
1.简介
通过使用三层隧道协议GRE实现互联,配置维护相对简单,对于安全性要求不是太高的企业可以选择使用
2.测试拓扑

3.测试配置
a.配置FW1防火墙用于连接内外网的接口
端口1/0/1配置如下,用于连接内部网络
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.10.10.1 255.255.255.0
service-manage https permit
service-manage ping permit
return
端口1/0/0配置如下,用于连接互联网
interface GigabitEthernet1/0/0
undo shutdown
ip address 100.100.100.2 255.255.255.252
service-manage https permit
service-manage ping permit
b.将配置好的接口添加到相应区域
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/1
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
add interface Tunnel0
c.配置FW1防火墙安全策略,配置的是站点直接的,源区域和目标区域都添加local,trust,untrust,也可以配置多条细化安全策略
security-policy
rule name 1
source-zone local
source-zone trust
source-zone untrust
destination-zone local
destination-zone trust
destination-zone untrust
action permit
d.配置HFW1防火墙源NAT策略,如果防火墙内部网络不需要访问互联网,可以不配置
nat-policy
rule name 1
destination-zone untrust
action source-nat easy-ip
e.配置FW1防火墙用于连接内外网的接口
端口1/0/1配置如下,用于连接内部网络
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.10.20.1 255.255.255.0
service-manage https permit
service-manage ping permit
端口1/0/0配置如下,用于连接互联网
interface GigabitEthernet1/0/0
undo shutdown
ip address 200.200.200.2 255.255.255.252
service-manage https permit
service-manage ping permit
return
f.将配置好的接口添加到相应区域
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/1
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
add interface Tunnel0
g.配置FW1防火墙安全策略,配置的是站点直接的XXXX,源区域和目标区域都添加local,trust,untrust,也可以配置多条细化安全策略
security-policy
rule name 1
source-zone local
source-zone trust
source-zone untrust
destination-zone local
destination-zone trust
destination-zone untrust
action permit
h.配置HFW1防火墙源NAT策略,如果防火墙内部网络不需要访问互联网,可以不配置
nat-policy
rule name 1
destination-zone untrust
action source-nat easy-ip
i.配置FW1防火墙Tunnel接口做为XXXX隧道接口
interface Tunnel0 #使用tunnel
ip address 192.168.1.1 255.255.255.0
tunnel-protocol gre
source 100.100.100.2
destination 200.200.200.2
j.将创建的Tunnel接口添加到untrust区域
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
add interface Tunnel0
k.配置XXXX访问对端网络的静态路由,下一条指向Tunnel 0
ip route-static 10.10.20.0 255.255.255.0 Tunnel0
ip route-static 0.0.0.0 0.0.0.0 100.100.100.1
l.配置FW2防火墙Tunnel接口做为XXXX隧道接口
interface Tunnel0 #使用tunnel
ip address 192.168.1.2 255.255.255.0
tunnel-protocol gre
source 200.200.200.2
destination 100.100.100.2
m.将创建的Tunnel接口添加到untrust区域
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
add interface Tunnel0
n.配置XXXX访问对端网络的静态路由,下一条指向Tunnel 0
ip route-static 10.10.10.0 255.255.255.0 Tunnel0
ip route-static 0.0.0.0 0.0.0.0 200.200.200.1
4.业务测试
PC1配置10.10.10.100pingPC210.10.20.100

在FW1上查看会话
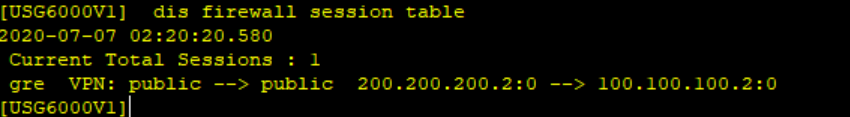
查看两端GER VPN隧道是否建立,状态是否为UP

查看FW1路由信息



