SpringBoot——整合数据库,springSecurity,shiro、整合thymeleaf_springboot整合数据库
赞
踩
一、springboot——JDBC
1、引入web、JDBC API、mysql Driver
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-jdbc</artifactId>
</dependency>
<dependency>
<groupId>mysql</groupId>
<artifactId>mysql-connector-java</artifactId>
<scope>runtime</scope>
</dependency>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
2、编辑jdbc配置文件
- 在resources下新建application.yaml
spring: datasource: username: root password: 1234qwer # 如果时区报错就配置serverTimezone=UTC url: jdbc:mysql://localhost:3306/ssmbuild?userUnicode=true&characterEncoding=utf8&serverTimezone=UTC driver-class-name: com.mysql.cj.jdbc.Driver- 1
- 2
- 3
- 4
- 5
- 6
- 7
3、测试连接数据库
在测试类里测试连接数据库,查看默认数据源
package com.jjl;
import org.junit.jupiter.api.Test;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.boot.test.context.SpringBootTest;
import javax.annotation.Resource;
import javax.sql.DataSource;
import java.sql.Connection;
import java.sql.SQLException;
@SpringBootTest
class Springboot04DataApplicationTests {
@Resource
DataSource dataSource;
@Test
void contextLoads() throws SQLException {
//查看默认的数据源 com.zaxxer.hikari.HikariDataSource
System.out.println(dataSource.getClass());
//获得数据库连接
Connection connection = dataSource.getConnection();
//关闭
connection.close();
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 输出结果:我们可以看到他默认给我们配置的数据源为:class com.zaxxer.hikari.HikariDataSource,我们并没有手动配置
- 我们来全局搜索一下,找到数据源的所有自动配置都在:DataSourceProperties 文件下;我们可以来探究下这里自动配置的原理以及能配置哪些属性;
- 可以看出 Spring Boot 2.7.4默认使用com.zaxxer.hikari.HikariDataSource 数据源,而以前版本,如Spring Boot 1.5 默认使用org.apache.tomcat.jdbc.pool.DataSource作为数据源;
- HikariDataSource号称Java WEB当前速度最快的数据源,相比于传统的C3PO、DBCP、Tomcatjdbc 等连接池更加优秀;
4、测试增删改查
新建一个测试类JDBCController测试连接,测试增删改查
package com.jjl.controller;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.jdbc.core.JdbcTemplate;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.PathVariable;
import org.springframework.web.bind.annotation.RestController;
import java.util.List;
import java.util.Map;
@RestController
public class JDBCController {
@Autowired
JdbcTemplate jdbcTemplate;
@GetMapping("/userList")
//查询数据库的book表所有信息
public List<Map<String,Object>> userList(){
String sql = "select * from books";
List<Map<String, Object>> maps = jdbcTemplate.queryForList(sql);
return maps;
}
//增加书籍
@GetMapping("/addbook")
public String addUser(){
String sql = "insert into books(bookID,bookName,bookCounts,detail) values(4,'jjl',10,'book')";
jdbcTemplate.update(sql);
return "update-ok";
}
//修改书籍
@GetMapping("/updatebook/{id}")
public String updateUser(@PathVariable("id")int id){
String sql = "update books set bookName=?,bookCounts=? where bookID="+id;
//封装参数
Object[] objects = new Object[2];
objects[0] = "边城";
objects[1] = 10;
jdbcTemplate.update(sql,objects);
return "update-ok";
}
//删除书籍
@GetMapping("/deletebook/{id}")
public String deleteUser(@PathVariable("id") int id){
String sql = "delete from books where bookID=?";
jdbcTemplate.update(sql,id);
return "delete-ok";
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
JDBCTemplate
1、有了数据源(com.zaxxer.hikari.HikariDataSource),然后可以拿到数据库连接(java.sql.Connection),有了连接,就可以使用原生的 JDBC 语句来操作数据库;
2、即使不使用第三方第数据库操作框架,如 MyBatis等,Spring 本身也对原生的JDBC 做了轻量级的封装,即JdbcTemplate。
3、数据库操作的所有 CRUD 方法都在 JdbcTemplate 中。
4、Spring Boot 不仅提供了默认的数据源,同时默认已经配置好了 JdbcTemplate 放在了容器中,程序员只需自己注入即可使用
5、JdbcTemplate 的自动配置是依赖 org.springframework.boot.autoconfigure.jdbc 包下的 JdbcTemplateConfiguration 类
JdbcTemplate主要提供以下几类方法:
-
execute方法:可以用于执行任何SQL语句,一般用于执行DDL语句;
-
update方法及batchUpdate方法:update方法用于执行新增、修改、删除等语句;batchUpdate方法用于执行批处理相关语句;
-
query方法及queryForXXX方法:用于执行查询相关语句;
-
call方法:用于执行存储过程、函数相关语句。
二、自定义数据源DruidDataSource
狂神说SpringBoot08:整合Druid
DRUID简介
Druid是阿里巴巴开源平台上一个数据库连接池实现,结合了C3P0、DBCP、PROXOOL等 DB池的优点,同时加入了日志监控。
Druid 可以很好的监控DB池连接和SQL的执行情况,天生就是针对监控而生的DB 连接池。
Spring Boot 2.0以上默认使用Hikari 数据源,可以说Hikari与 Driud都是当前Java Web上最优秀的数据源,我们来重点介绍Spring Boot如何集成 Druid 数据源,如何实现数据库监控。
1、添加上 Druid 数据源依赖。
<dependency>
<groupId>com.alibaba</groupId>
<artifactId>druid</artifactId>
<version>1.2.13</version>
</dependency>
- 1
- 2
- 3
- 4
- 5
2、切换数据源
之前已经说过 Spring Boot 2.0 以上默认使用 com.zaxxer.hikari.HikariDataSource 数据源,但可以 通过 spring.datasource.type 指定数据源。
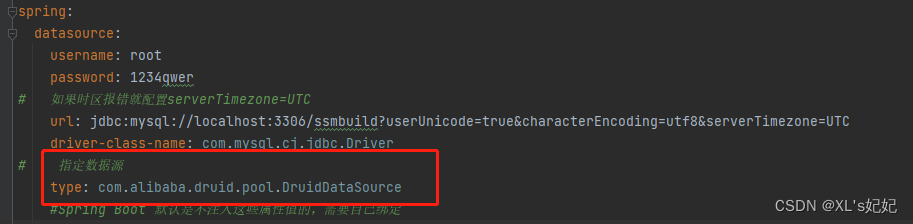
3、这测试类中测试
4、配置Druid参数
spring:
datasource:
username: root
password: 1234qwer
# 如果时区报错就配置serverTimezone=UTC
url: jdbc:mysql://localhost:3306/ssmbuild?userUnicode=true&characterEncoding=utf8&serverTimezone=UTC
driver-class-name: com.mysql.cj.jdbc.Driver
# 指定数据源
type: com.alibaba.druid.pool.DruidDataSource
#Spring Boot 默认是不注入这些属性值的,需要自己绑定
#druid 数据源专有配置
initialSize: 5
minIdle: 5
maxActive: 20
maxWait: 60000
timeBetweenEvictionRunsMillis: 60000
minEvictableIdleTimeMillis: 300000
validationQuery: SELECT 1 FROM DUAL
testWhileIdle: true
testOnBorrow: false
testOnReturn: false
poolPreparedStatements: true
#配置监控统计拦截的filters,stat:监控统计、log4j:日志记录、wall:防御sql注入
#如果允许时报错 java.lang.ClassNotFoundException: org.apache.log4j.Priority
#则导入 log4j 依赖即可,Maven 地址:https://mvnrepository.com/artifact/log4j/log4j
filters: stat,wall,log4j
maxPoolPreparedStatementPerConnectionSize: 20
useGlobalDataSourceStat: true
connectionProperties: druid.stat.mergeSql=true;druid.stat.slowSqlMillis=500
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
5、导入Log4j 的依赖
<dependency>
<groupId>log4j</groupId>
<artifactId>log4j</artifactId>
<version>1.2.17</version>
</dependency>
- 1
- 2
- 3
- 4
- 5
6、将 DruidDataSource 绑定全局配置文件中的参数
新建config目录,新建DruidConfig,将 DruidDataSource 绑定全局配置文件中的参数,再添加到容器中,而不再使用 Spring Boot 的自动生成了;我们需要 自己添加 DruidDataSource 组件到容器中,并绑定属性;
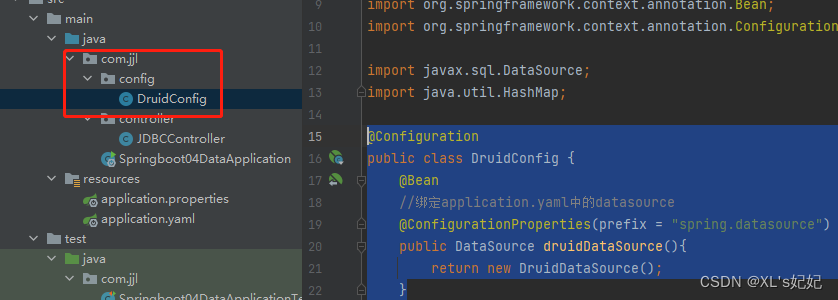
@Configuration
public class DruidConfig {
/*
将自定义的 Druid数据源添加到容器中,不再让 Spring Boot 自动创建
绑定全局配置文件中的 druid 数据源属性到 com.alibaba.druid.pool.DruidDataSource从而让它们生效
@ConfigurationProperties(prefix = "spring.datasource"):作用就是将 全局配置文件中
前缀为 spring.datasource的属性值注入到 com.alibaba.druid.pool.DruidDataSource 的同名参数中
*/
@Bean
@ConfigurationProperties(prefix = "spring.datasource")
public DataSource druidDataSource(){
return new DruidDataSource();
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
7、配置Druid数据源监控
Druid 数据源具有监控的功能,并提供了一个 web 界面方便用户查看,类似安装 路由器 时,人家也提供了一个默认的 web 页面。
所以第一步需要继续DruidConfig添加设置 Druid 的后台管理页面,比如 登录账号、密码 等;配置后台管理;
//后台监控 :
// 因为spring 内置了servlet容器,so没有web.xml.替代方法:ServletRegistrationBean
@Bean
public ServletRegistrationBean statViewServlet (){
ServletRegistrationBean<StatViewServlet> bean = new ServletRegistrationBean<>(new StatViewServlet(), "/druid/*");
//后台需要有人登录,账号密码配置
HashMap<String,String> initParameters = new HashMap<>();
//增加配置("loginUsername"、"loginPassword" 固定值)
initParameters.put("loginUsername","admin");
initParameters.put("loginPassword","123456");
//允许谁能访问, "allow","" 后面值为空表示所有人能访问
initParameters.put("allow","");
//禁止谁能访问
initParameters.put("jjl","192.168.29.15");
bean.setInitParameters(initParameters);//设置初始化参数
return bean;
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
测试登录
http://localhost:8080/druid/login.html


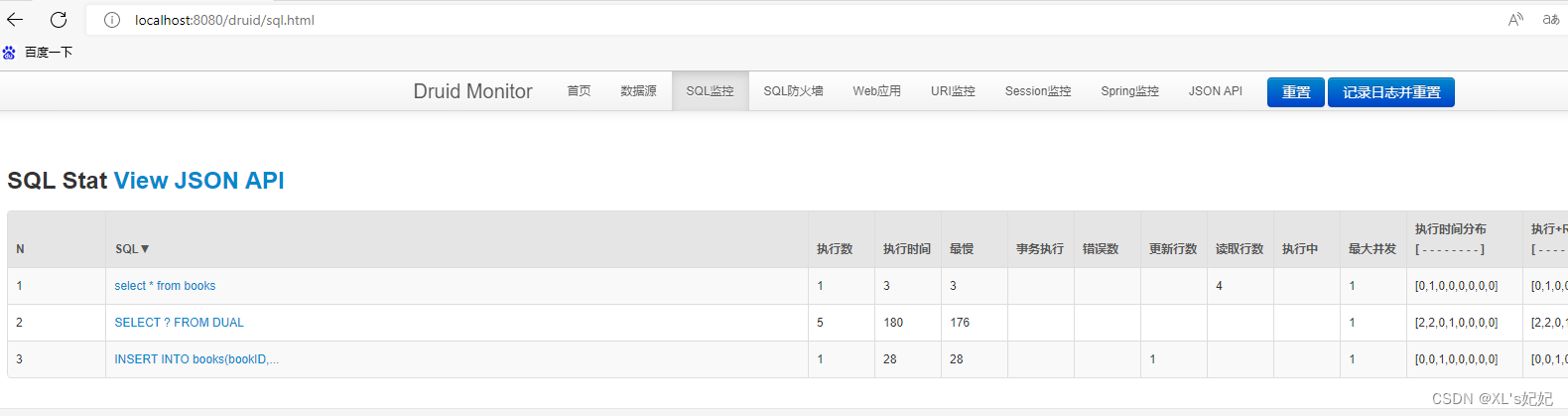
8、配置 Druid web 监控 filter 过滤器
继续DruidConfig添加配置
//配置 Druid 监控 之 web 监控的 filter
//WebStatFilter:用于配置Web和Druid数据源之间的管理关联监控统计
@Bean
public FilterRegistrationBean webStatFilter() {
FilterRegistrationBean bean = new FilterRegistrationBean();
bean.setFilter(new WebStatFilter());
//exclusions:设置哪些请求进行过滤排除掉,从而不进行统计
Map<String, String> initParams = new HashMap<>();
initParams.put("exclusions", "*.js,*.css,/druid/*,/jdbc/*");
bean.setInitParameters(initParams);
//"/*" 表示过滤所有请求
bean.setUrlPatterns(Arrays.asList("/*"));
return bean;
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
三、整合mybatis
1、导入maven包
<dependency>
<groupId>org.mybatis.spring.boot</groupId>
<artifactId>mybatis-spring-boot-starter</artifactId>
<version>2.2.2</version>
</dependency>
- 1
- 2
- 3
- 4
- 5
2、编写数据库连接信息
application.properties(可以与”二、4“不变)
spring.datasource.username=root
spring.datasource.password=1234qwer
spring.datasource.url=jdbc:mysql://localhost:3306/ssmbuild?serverTimezone=UTC&useUnicode=true&characterEncoding=utf-8
spring.datasource.driver-class-name=com.mysql.cj.jdbc.Driver
- 1
- 2
- 3
- 4
测试是否连接成功
3、编写实体类pojo
导入lombok
package com.jjl.pojo;
import lombok.AllArgsConstructor;
import lombok.Data;
import lombok.NoArgsConstructor;
@Data
@NoArgsConstructor
@AllArgsConstructor
public class Books {
private int bookID;
private String bookName;
private int bookCounts;
private String detail;
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
4、创建mapper目录以及对应的 Mapper 接口
package com.jjl.mapper;
import com.jjl.pojo.Books;
import org.apache.ibatis.annotations.Mapper;
import org.springframework.stereotype.Repository;
import java.util.List;
//表示这是一个mybatis的mapper类;
@Mapper
@Repository //被spring整合
public interface BookMapper {
//查询所有书籍的信息:无需接收参数,返回一个列表
List<Books> queryBookList();
//根据书籍id查询书籍信息:接收一个书籍的id,返回一个对象
Books queryBookByBookId(int bookID);
//添加书籍:接收一个对象,返回一个状态)
int addBook(Books books);
//更新书籍信息:接收一个对象,返回一个状态
int updateBook(Books books);
//根据id删除一本书籍:接收一个id,返回一个状态
int deleteBook(int id);
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
5、对应的Mapper映射文件
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE mapper
PUBLIC "-//mybatis.org//DTD Mapper 3.0//EN"
"http://mybatis.org/dtd/mybatis-3-mapper.dtd">
<!--绑定mapper接口类-->
<mapper namespace="com.jjl.mapper.BookMapper">
<select id="queryBookList" resultType="Books">
select * from books
</select>
<select id="queryBookByBookId" resultType="Books">
select * from books where bookID=#{bookID}
</select>
<insert id="addBook" parameterType="Books">
insert into books (bookID,bookName,bookCounts,detail)
values (#{bookID},#{bookName},#{bookCounts},#{detail})
</insert>
<update id="updateBook" parameterType="Books">
update Books set bookName=#{bookName},bookCounts=#{bookCounts},detail=#{detail} where bookID=#{bookID}
</update>
<delete id="deleteBook" parameterType="int">
delete from Books where bookID=#{bookID}
</delete>
</mapper>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
maven配置资源过滤问题
6、整合mybatis
application.properties
# 整合mybatis
mybatis.type-aliases-package=com.jjl.pojo
mybatis.mapper-locations=classpath:mybatis/mapper/*.xml
- 1
- 2
- 3
7、controller测试
package com.jjl.controller;
import com.jjl.mapper.BookMapper;
import com.jjl.pojo.Books;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.RestController;
import java.util.List;
@RestController
public class BookController {
@Autowired
private BookMapper bookMapper;
@GetMapping("/queryBookList")
public List<Books> queryBookList(){
List<Books> booksList = bookMapper.queryBookList();
for (Books books : booksList) {
System.out.println(books);
}
return booksList;
}
//根据id查书籍
@GetMapping("/selectBookByBookId")
public String queryBookByBookId(){
Books book = bookMapper.queryBookByBookId(3);
System.out.println(book);
return "ok";
}
//添加用户
@GetMapping("/addbook")
public String addbooks(){
System.out.println("controller");
int addBook = bookMapper.addBook(new Books(6, "qwer", 5, "good"));
System.out.println("sql结果"+addBook);
return "ok";
}
//更新一个用户
@GetMapping("/update")
public String updatebook(){
bookMapper.updateBook(new Books(6, "计算机", 5, "网络"));
return "ok";
}
//删除一本书籍
@GetMapping("/delete")
public String delete(){
bookMapper.deleteBook(6);
return "ok";
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
四、SpringSecurity(安全)
狂神说SpringBoot18:集成SpringSecurity
- Spring Security是一个功能强大、高度可定制的身份验证和访问控制框架。它是保护基于spring的应用程序的事实上的标准。
- Spring Security是一个专注于为Java应用程序提供身份验证和授权的框架。与所有Spring项目一样,Spring Security的真正威力在于它可以很容易地进行扩展以满足定制需求
特性
- 对身份验证和授权的全面和可扩展支持
- 防止攻击,如会话固定,点击劫持,跨站请求伪造等
- Servlet API的集成
- 与Spring Web MVC的可选集成
- ……
我们仅需要引入spring-boot-starter-security模块,进行少量的配置,即可实现强大的安全管理!
记住几个类:
- webSecurityConfigurerAdapter:自定义Security策略
- AuthenticationManagerBuilder:自定义认证策略。
- @EnableWebSecurity:开启WebSecurity模式
Spring Security的两个主要目标是“认证"和“授权”(访问控制)。
“认证”(Authentication)
授权”(Authorization)
这个概念是通用的,而不是只在Spring Security中存在。
1、登录拦截:
测试目的:
- 实现登录拦截,被拦截之后自动跳转到登录页
- 不同的用户只能访问指定的页面
1、新建一个初始的springboot项目web模块,thymeleaf模块
2、导入静态资源
3、controller跳转!
package com.jjl.controller;
import org.springframework.stereotype.Controller;
import org.springframework.web.bind.annotation.PathVariable;
import org.springframework.web.bind.annotation.RequestMapping;
@Controller
public class RouterController {
@RequestMapping({"/","index"})
public String index(){
return "index";
}
@RequestMapping("/toLogin")
public String toLogin(){
return "views/login";
}
@RequestMapping("/level1/{id}")
public String level1(@PathVariable("id") int id){
return "views/level1/"+id;
}
@RequestMapping("/level2/{id}")
public String level2(@PathVariable("id") int id){
return "views/level2/"+id;
}
@RequestMapping("/level3/{id}")
public String level3(@PathVariable("id") int id){
return "views/level3/"+id;
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
5、引入 Spring Security 模块
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>
- 1
- 2
- 3
- 4
6、编写基础配置
- 开启WebSecurity模式
- 定制请求的授权规则
- 用户密码加密处理
package com.jjl.config;
import org.springframework.security.config.annotation.authentication.builders.AuthenticationManagerBuilder;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
@EnableWebSecurity // 开启WebSecurity模式
public class securityConfig extends WebSecurityConfigurerAdapter {
//授权
@Override
protected void configure(HttpSecurity http) throws Exception {
//首页所有人可以访问,功能页只有对应权限的人才能访问
//请求授权的规则
http.authorizeHttpRequests()
.antMatchers("/").permitAll()
.antMatchers("/level1/**").hasRole("vip1")//vip1可以访问/level1/下所有的文件
.antMatchers("/level2/**").hasRole("vip2")
.antMatchers("/level3/**").hasRole("vip3");
//没有权限默认到登录页,开启登录的页面
http.formLogin();
}
//认证
//密码编码:PasswordEncoder
@Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
//绑定加密策略:passwordEncoder(new BCryptPasswordEncoder())
//解密策略:new BCryptPasswordEncoder().encode("1234")
//用户名和密码,可以从数据库和内存中获取,这里为了方便测试就采用从内存中获取
auth.inMemoryAuthentication().passwordEncoder(new BCryptPasswordEncoder())
.withUser("jjl").password(new BCryptPasswordEncoder().encode("1234")).roles("vip1","vip2")
.and()
.withUser("root").password(new BCryptPasswordEncoder().encode("1234")).roles("vip1","vip2","vip3")
.and()
.withUser("guest").password(new BCryptPasswordEncoder().encode("1234")).roles("vip1");
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
2、整合thymeleaf(注销,权限控制)
- 注销用户,并跳转到首页
- 控制首页内容动态显示
- 当已登录时显示用户名和注销按钮
- 当未登录时显示只登录
1、开启注销功能
给页面添加一个注销按钮

开启注销请求,并且注销成功后跳转到首页
2、实现导航栏的动态显示
用户没有登录的时候,导航栏上只显示登录按钮,用户登录之后,导航栏可以显示登录的用户信息及注销按钮!
导入thymeleaf与security整合的依赖
<!-- https://mvnrepository.com/artifact/org.thymeleaf.extras/thymeleaf-extras-springsecurity5 -->
<dependency>
<groupId>org.thymeleaf.extras</groupId>
<artifactId>thymeleaf-extras-springsecurity5</artifactId>
<version>3.0.4.RELEASE</version>
</dependency>
- 1
- 2
- 3
- 4
- 5
- 6
导入命名空间

修改导航栏,增加认证判断
<div class="right menu">
<!--如果未登录显示:未登录-->
<div sec:authorize="!isAuthenticated()">
<a class="item" th:href="@{/login}">
<i class="address card icon"></i> 登录
</a>
</div>
<!--如果已登录就显示:用户名、注销-->
<div sec:authorize="isAuthenticated()">
<a class="item">
用户名:<span sec:authentication="name"></span>
</a>
</div>
<div sec:authorize="isAuthenticated()">
<a class="item" th:href="@{/logout}">
<i class="sign-out icon"></i> 注销
</a>
</div>
</div>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
测试,如果注销404了,就是因为它默认防止csrf跨站请求伪造,因为会产生安全问题,我们可以将请求改为post表单提交,或者在spring security中关闭csrf功能;我们试试:在 配置中增加 http.csrf().disable();
3、实现角色功能的动态显示
<!--sec:authentication="hasRole('vip1')":::如果登录的人有vip1的权限则就显示此div模块-->
<div class="column" sec:authorize="hasRole('vip1')">
<div class="ui raised segment">
<div class="ui">
<div class="content">
<h5 class="content">Level 1</h5>
<hr>
<div><a th:href="@{/level1/1}"><i class="bullhorn icon"></i> Level-1-1</a></div>
<div><a th:href="@{/level1/2}"><i class="bullhorn icon"></i> Level-1-2</a></div>
<div><a th:href="@{/level1/3}"><i class="bullhorn icon"></i> Level-1-3</a></div>
</div>
</div>
</div>
</div>
<div class="column" sec:authorize="hasRole('vip2')">
<div class="ui raised segment">
<div class="ui">
<div class="content">
<h5 class="content">Level 2</h5>
<hr>
<div><a th:href="@{/level2/1}"><i class="bullhorn icon"></i> Level-2-1</a></div>
<div><a th:href="@{/level2/2}"><i class="bullhorn icon"></i> Level-2-2</a></div>
<div><a th:href="@{/level2/3}"><i class="bullhorn icon"></i> Level-2-3</a></div>
</div>
</div>
</div>
</div>
<div class="column" sec:authorize="hasRole('vip3')">
<div class="ui raised segment">
<div class="ui">
<div class="content">
<h5 class="content">Level 3</h5>
<hr>
<div><a th:href="@{/level3/1}"><i class="bullhorn icon"></i> Level-3-1</a></div>
<div><a th:href="@{/level3/2}"><i class="bullhorn icon"></i> Level-3-2</a></div>
<div><a th:href="@{/level3/3}"><i class="bullhorn icon"></i> Level-3-3</a></div>
</div>
</div>
</div>
</div>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
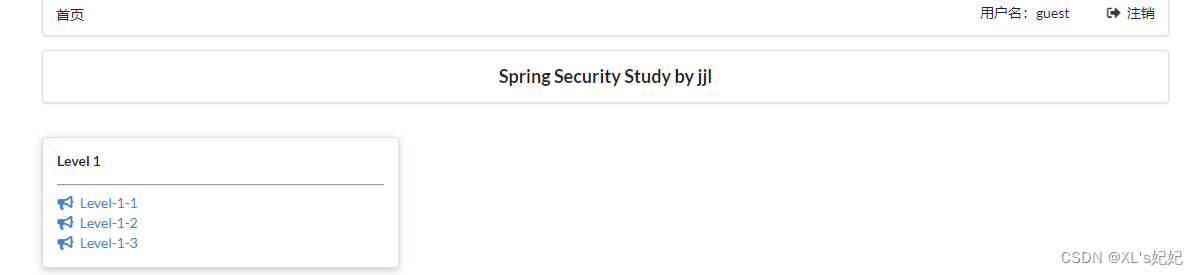
测试:
已登录:

未登录:
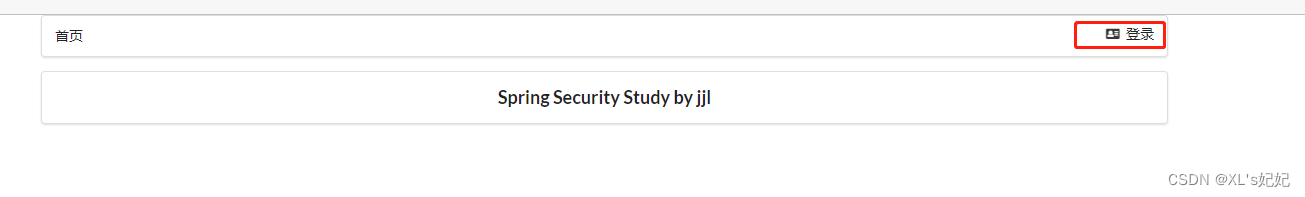
登录root拥有所有权限的用户,所显示的内容

登录来宾用户,所显示的内容
3、实现记住我功能
现在的情况,我们只要登录之后,关闭浏览器,再登录,就会让我们重新登录,但是很多网站的情况,就是有一个记住密码的功能
1、开启springSecurity自带的记住我功能,
在security基本配置类securityConfig,添加http.rememberMe()即可

开启之后,会在前端的默认登录页面,自动添加一个remember的复选框,默认记住时间时两周。
登录成功后,将cookie发送给浏览器保存,以后登录带上这个cookie,只要通过检查就可以免登录了。如果点击注销,则会删除这个cookie。
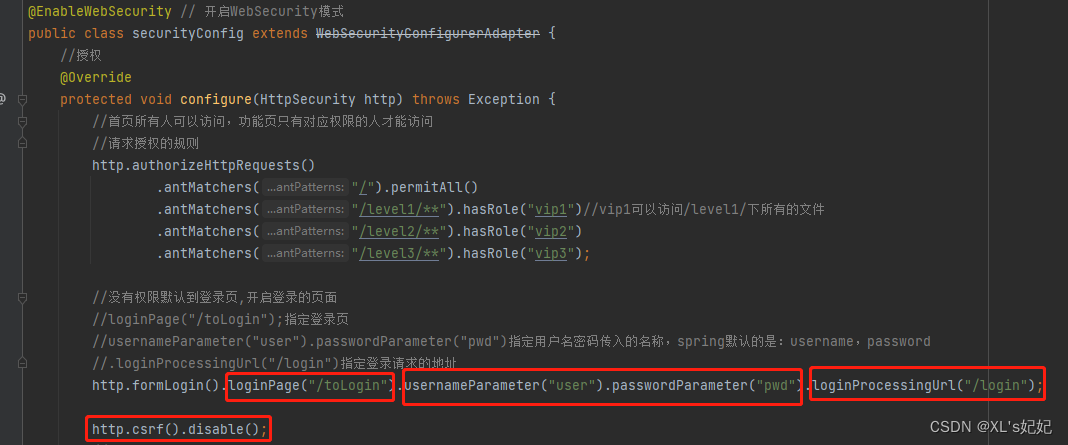
4、自定义登录页
刚才用的这个登录页面都是spring security 默认的
修改前端跳转到登录页的请求

- 开启自定义登录页,并指定登录的请求链接
- 绑定登录页里面用户名和密码的属性名(spring security 默认是username和password,如果前端页面的属性名称是一样的,则不用绑定)
- 指定登陆时提交的请求链接
- 修改了登录页之后,出现的注销失败,需要spring security中关闭csrf功能,在 配置中增加 http.csrf().disable();
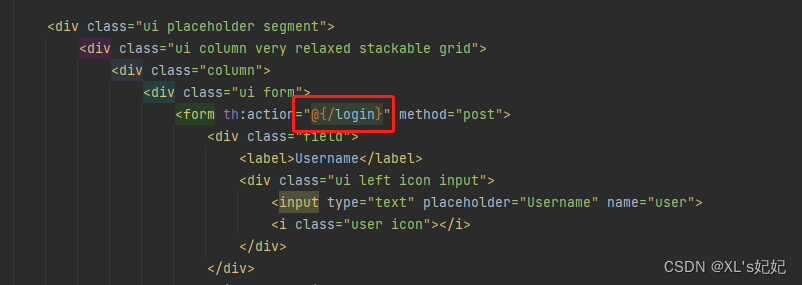
指定提交的登录请求地址
“/login”是springSecurity的默认登录请求
5、在自定义登录页中实现“记住我”
在前端登录页中添加一个“记住我”复选框,并指定属性名称
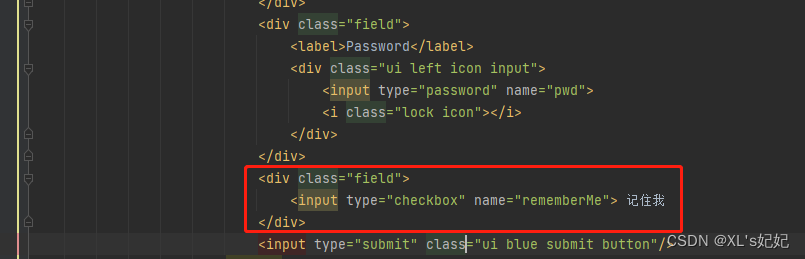
在springsecurity配置中开启“记住我”上接收参数

完整的spring security配置类
package com.jjl.config;
import org.springframework.security.config.annotation.authentication.builders.AuthenticationManagerBuilder;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
@EnableWebSecurity // 开启WebSecurity模式
public class securityConfig extends WebSecurityConfigurerAdapter {
//授权
@Override
protected void configure(HttpSecurity http) throws Exception {
//首页所有人可以访问,功能页只有对应权限的人才能访问
//请求授权的规则
http.authorizeHttpRequests()
.antMatchers("/").permitAll()
.antMatchers("/level1/**").hasRole("vip1")//vip1可以访问/level1/下所有的文件
.antMatchers("/level2/**").hasRole("vip2")
.antMatchers("/level3/**").hasRole("vip3");
//没有权限默认到登录页,开启登录的页面
//loginPage("/toLogin");指定登录页
//usernameParameter("user").passwordParameter("pwd")指定用户名密码传入的名称,spring默认的是:username,password
//.loginProcessingUrl("/login")指定登录请求的地址
http.formLogin().loginPage("/toLogin").usernameParameter("user").passwordParameter("pwd").loginProcessingUrl("/login");
http.csrf().disable();
//注销,开启注销功能
//【deleteCookies("remove"):删除cookies,invalidateHttpSession(true):清空session】一般不用这些
//http.logout().deleteCookies("remove").invalidateHttpSession(true);
http.logout().logoutSuccessUrl("/");
//开启“记住我”功能,默认保存两周,rememberMeParameter("rememberMe");接收前端传来的“rememberMe”请求
http.rememberMe().rememberMeParameter("rememberMe");
}
//认证
//密码编码:PasswordEncoder
@Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
//绑定加密策略:passwordEncoder(new BCryptPasswordEncoder())
//解密策略:new BCryptPasswordEncoder().encode("1234")
//用户名和密码,可以从数据库和内存中获取,这里为了方便测试就采用从内存中获取
auth.inMemoryAuthentication().passwordEncoder(new BCryptPasswordEncoder())
.withUser("jjl").password(new BCryptPasswordEncoder().encode("1234")).roles("vip1","vip2")
.and()
.withUser("root").password(new BCryptPasswordEncoder().encode("1234")).roles("vip1","vip2","vip3")
.and()
.withUser("guest").password(new BCryptPasswordEncoder().encode("1234")).roles("vip1");
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
五、Shiro
1、shiro简介
- Apache Shiro是一个Java的安全(权限)框架。
- Shiro 可以非常容易的开发出足够好的应用,其不仅可以用在JavaSE环境,也可以用在JavaEE环境。
- Shiro可以完成,认证,授权,加密,会话管理,Web集成,缓存等。
- 下载地址:http://shiro.apache.org
1、下载官方的案例
2、导入依赖和案例文件
3、运行案例,分析案例
- Subject currentUser = SecurityUtils.getSubject(); 获取用户对象
- Session session = currentUser.getSession();获取对象的session
- currentUser.isAuthenticated()判断是否登录
- currentUser.getPrincipal()获取用户名
- currentUser.hasRole(“schwartz”)获取用户角色
- currentUser.isPermitted(“lightsaber:wield”)获取用户权限
- currentUser.logout();注销
2、springboot集成shiro环境搭建
shiro的三大对象:Subject(用户)、SecurityManager (管理所有用户)、Realm(连接数据)
1、导入shiro
<dependency>
<groupId>org.apache.shiro</groupId>
<artifactId>shiro-spring</artifactId>
<version>1.9.1</version>
</dependency>
- 1
- 2
- 3
- 4
- 5
2、//自定义UserRealm
package com.jjl.config;
import org.apache.shiro.authc.AuthenticationException;
import org.apache.shiro.authc.AuthenticationInfo;
import org.apache.shiro.authc.AuthenticationToken;
import org.apache.shiro.authz.AuthorizationInfo;
import org.apache.shiro.realm.AuthorizingRealm;
import org.apache.shiro.subject.PrincipalCollection;
//自定义UserRealm
public class UserRealm extends AuthorizingRealm {
//授权
@Override
protected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principalCollection) {
System.out.println("执行了授权=>doGetAuthorizationInfo");
return null;
}
//认证
@Override
protected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken authenticationToken) throws AuthenticationException {
System.out.println("执行了认证=>doGetAuthenticationInfo");
return null;
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
3、创建三个核心对象
package com.jjl.config;
import org.apache.shiro.spring.web.ShiroFilterFactoryBean;
import org.apache.shiro.web.mgt.DefaultWebSecurityManager;
import org.springframework.beans.factory.annotation.Qualifier;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
@Configuration
public class ShiroConfig {
//创建realm对象,需要自定义
@Bean
public UserRealm userRealm(){
return new UserRealm();
}
@Bean
//DafaultWebSecurityManager
public DefaultWebSecurityManager getDefaultWebSecurityManager(@Qualifier("userRealm") UserRealm userRealm){
DefaultWebSecurityManager securityManager = new DefaultWebSecurityManager();
//关联UserRealm
securityManager.setRealm(userRealm);
return securityManager;
}
//ShiroFillterFactoryBean
@Bean
public ShiroFilterFactoryBean getShiroFilterFactoryBean(@Qualifier("getDefaultWebSecurityManager") DefaultWebSecurityManager defaultWebSecurityManager){
ShiroFilterFactoryBean factoryBean = new ShiroFilterFactoryBean();
factoryBean.setSecurityManager(defaultWebSecurityManager);
return factoryBean;
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
4、编写测试页,实现跳转
<!DOCTYPE html>
<html lang="en" xmlns:th="http://www.thymeleaf.org">
<head>
<meta charset="UTF-8">
<title>首页</title>
</head>
<body>
<h1>首页</h1>
<p th:text="${msg}"></p>
<a th:href="@{/user/add}">add</a> | <a th:href="@{/user/update}">update</a>
</body>
</html>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
add和update页面略:
package com.jjl.controller;
import org.springframework.stereotype.Controller;
import org.springframework.ui.Model;
import org.springframework.web.bind.annotation.RequestMapping;
@Controller
public class MyController {
@RequestMapping({"/","index"})
public String toIndex(Model model){
model.addAttribute("msg","hello word!");
return "index";
}
@RequestMapping({"/user/add"})
public String add(){
return "user/add";
}
@RequestMapping({"/user/update"})
public String update(){
return "user/update";
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
目录结构
3、登录拦截
1、编写一个登录页,并配置跳转请求
@RequestMapping({"/toLogin"})
public String toLogin(){
return "login";
}
- 1
- 2
- 3
- 4
2、添加拦截配置
//ShiroFillterFactoryBean
@Bean
public ShiroFilterFactoryBean getShiroFilterFactoryBean(@Qualifier("getDefaultWebSecurityManager") DefaultWebSecurityManager defaultWebSecurityManager){
ShiroFilterFactoryBean factoryBean = new ShiroFilterFactoryBean();
//配置安全管理器
factoryBean.setSecurityManager(defaultWebSecurityManager);
//添加shiro的内置过滤器
/*
* anon:无需认证就可以访问
* authc:必须认证了才能访问
* user:必须拥有“记住我”功能才能访问
* perms:拥有对某个资源的权限才能访问
* role:拥有某个角色权限才能访问*/
//filterMap.put("/user/add","authc");
//filterMap.put("/user/update","authc");
LinkedHashMap<String, String> filterMap = new LinkedHashMap<>();
/*认证了才能访问*/
filterMap.put("/user/*","authc");
factoryBean.setFilterChainDefinitionMap(filterMap);
//设置登录的请求(配有权限时就会跳转到登录页)
factoryBean.setLoginUrl("/toLogin");
return factoryBean;
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
4、实现用户认证
1、在controller中添加一个处理登录请求的方法
- 调用SecurityUtils获取当前用户
- 将当前用户的用户名和密码封装到UsernamePasswordToken里面
- 执行登录财政,并做判断是否登录成功
@RequestMapping("/login")
public String login(String username,String password,Model model){
//获取当前用户
Subject subject = SecurityUtils.getSubject();
UsernamePasswordToken token = new UsernamePasswordToken(username, password);
try {
subject.login(token);//执行登录操作
return "index";
} catch (UnknownAccountException e) {
model.addAttribute("msg","用户名错误");
return "login";
} catch (IncorrectCredentialsException e) {
model.addAttribute("msg","密码错误");
return "login";
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
2、配置认证
- 调用UsernamePasswordToken中封装的用户名和密码
- 与数据库的用户信息做匹配
@Override
protected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken authenticationToken) throws AuthenticationException {
System.out.println("执行了认证=>doGetAuthenticationInfo");
//用户名密码
String name = "root";
String password = "1234";
//UsernamePasswordToken:是通用调用MyController中login登录方法封装之后的
UsernamePasswordToken userToken = (UsernamePasswordToken) authenticationToken;
if (!userToken.getUsername().equals(name)){
return null;//这里会自动抛出MyController类中login登录方法定义的UnknownAccountException异常
}
//密码认证,shiro做
return new SimpleAuthenticationInfo("",password,"");
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
5、整合 Druid、Mybatis
1、导入依赖
<dependency>
<groupId>mysql</groupId>
<artifactId>mysql-connector-java</artifactId>
</dependency>
<dependency>
<groupId>com.alibaba</groupId>
<artifactId>druid</artifactId>
<version>1.2.13</version>
</dependency>
<!-- https://mvnrepository.com/artifact/log4j/log4j -->
<dependency>
<groupId>log4j</groupId>
<artifactId>log4j</artifactId>
<version>1.2.17</version>
</dependency>
<dependency>
<groupId>org.mybatis.spring.boot</groupId>
<artifactId>mybatis-spring-boot-starter</artifactId>
<version>2.2.2</version>
</dependency>
<dependency>
<groupId>org.projectlombok</groupId>
<artifactId>lombok</artifactId>
</dependency>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
2、添加数据库连接配置
与“二、4、配置Druid参数"相同 application.yml
3、整合mybatis
application.properties添加mybatis配置
mybatis.type-aliases-package=com.jjl.pojo
mybatis.mapper-locations=classpath:mapper/*.xml
- 1
- 2
4、创建pojo实体类
导入Lombok
package com.jjl.pojo;
import lombok.AllArgsConstructor;
import lombok.Data;
import lombok.NoArgsConstructor;
@Data
@AllArgsConstructor
@NoArgsConstructor
public class User {
private int id;
private String name;
private String pwd;
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
5、创建mapper层
新建接口
package com.jjl.mapper;
import com.jjl.pojo.User;
import org.apache.ibatis.annotations.Mapper;
import org.springframework.stereotype.Repository;
@Repository
@Mapper
public interface UserMapper {
public User queryUserByName(String name);
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
resources/mapper中新建UserMapper.xml实现接口
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE mapper
PUBLIC "-//mybatis.org//DTD Mapper 3.0//EN"
"http://mybatis.org/dtd/mybatis-3-mapper.dtd">
<!--绑定mapper接口类-->
<mapper namespace="com.jjl.mapper.UserMapper">
<select id="queryUserByName" parameterType="String" resultType="User">
select * from user where name=#{name}
</select>
</mapper>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
6、创建service层
新建接口
package com.jjl.service;
import com.jjl.mapper.UserMapper;
import com.jjl.pojo.User;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.stereotype.Service;
@Service
public class UserServiceImpl implements UserService{
@Autowired
UserMapper userMapper;
@Override
public User queryUserByName(String name) {
return userMapper.queryUserByName(name);
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
实现接口
package com.jjl.service;
import com.jjl.pojo.User;
public interface UserService {
public User queryUserByName(String name);
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
7、shiro与数据库的整合
@Autowired
UserServiceImpl userService;
//认证
@Override
protected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken authenticationToken) throws AuthenticationException {
System.out.println("执行了认证=>doGetAuthenticationInfo");
//UsernamePasswordToken:是通用调用MyController中login登录方法封装之后的
UsernamePasswordToken userToken = (UsernamePasswordToken) authenticationToken;
//获取数据库的数据
User user = userService.queryUserByName(userToken.getUsername());
if (user==null){//说明没这个人,登录失败
return null;//这里会自动抛出MyController类中login登录方法定义的UnknownAccountException异常
}
//可以对密码进行加密 MD5:加密(可逆) MD5盐值加密(不可逆)
//密码认证,shiro做
return new SimpleAuthenticationInfo("",user.getPwd(),"");
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
目录结构
6、实现请求授权
1、在ShiroConfig的getShiroFilterFactoryBean方法中设置权限
//授权
filterMap.put("/user/add","perms[user:add]");//有user:add权限才能访问/user/add
filterMap.put("/user/update","perms[user:update]");
- 1
- 2
- 3
2、添加一个未授权时跳转的提示页面
在MyController中添加一个未授权时的跳转请求
//未授权时跳转的页面
@RequestMapping("/noauth")
@ResponseBody
public String unauthorized(){
return "你无权限访问此页面";
}
- 1
- 2
- 3
- 4
- 5
- 6
在ShiroConfig的getShiroFilterFactoryBean方法中设置未授权时跳转的连接
//设置未授权时跳转的提示页面
factoryBean.setUnauthorizedUrl("/noauth");
- 1
- 2
3、在数据库用户表中添加一个权限字段
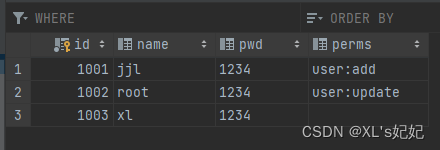
修改实体类
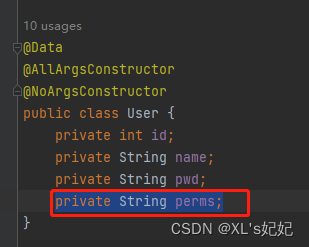
4、获取当前用户对象
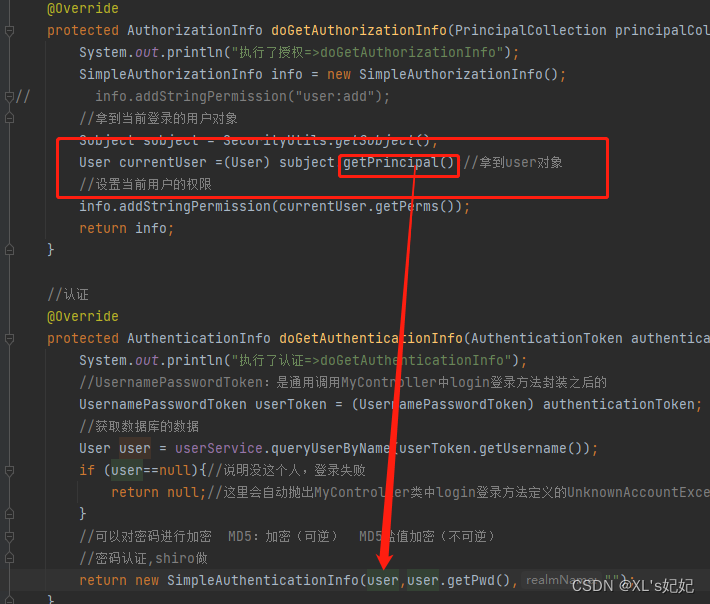
在UserRealm的doGetAuthorizationInfo方法中添加
Subject subject = SecurityUtils.getSubject();
- 1
5、获取当前user用户的参数
6、获取当前用户的权限,并返回权限

7、完整的ShiroConfig类和UserRealm类
ShiroConfig
package com.jjl.config;
import org.apache.shiro.spring.web.ShiroFilterFactoryBean;
import org.apache.shiro.web.mgt.DefaultWebSecurityManager;
import org.springframework.beans.factory.annotation.Qualifier;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import java.util.LinkedHashMap;
@Configuration
public class ShiroConfig {
//创建realm对象,需要自定义
@Bean
public UserRealm userRealm(){
return new UserRealm();
}
@Bean
//DafaultWebSecurityManager
public DefaultWebSecurityManager getDefaultWebSecurityManager(@Qualifier("userRealm") UserRealm userRealm){
DefaultWebSecurityManager securityManager = new DefaultWebSecurityManager();
//关联UserRealm
securityManager.setRealm(userRealm);
return securityManager;
}
//ShiroFillterFactoryBean
@Bean
public ShiroFilterFactoryBean getShiroFilterFactoryBean(@Qualifier("getDefaultWebSecurityManager") DefaultWebSecurityManager defaultWebSecurityManager){
ShiroFilterFactoryBean factoryBean = new ShiroFilterFactoryBean();
//配置安全管理器
factoryBean.setSecurityManager(defaultWebSecurityManager);
//添加shiro的内置过滤器
/*
* anon:无需认证就可以访问
* authc:必须认证了才能访问
* user:必须拥有“记住我”功能才能访问
* perms:拥有对某个资源的权限才能访问
* role:拥有某个角色权限才能访问*/
//filterMap.put("/user/add","authc");
//filterMap.put("/user/update","authc");
//拦截
LinkedHashMap<String, String> filterMap = new LinkedHashMap<>();
//授权
filterMap.put("/user/add","perms[user:add]"); //有user:add权限才能访问/user/add
filterMap.put("/user/update","perms[user:update]");
//设置未授权时跳转的提示页面
factoryBean.setUnauthorizedUrl("/noauth");
/*认证了才能访问*/
filterMap.put("/user/*","authc");
factoryBean.setFilterChainDefinitionMap(filterMap);
//设置登录的请求(配有权限时就会跳转到登录页)
factoryBean.setLoginUrl("/toLogin");
return factoryBean;
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
UserRealm
package com.jjl.config;
import com.jjl.pojo.User;
import com.jjl.service.UserServiceImpl;
import org.apache.shiro.SecurityUtils;
import org.apache.shiro.authc.*;
import org.apache.shiro.authz.AuthorizationInfo;
import org.apache.shiro.authz.SimpleAuthorizationInfo;
import org.apache.shiro.realm.AuthorizingRealm;
import org.apache.shiro.subject.PrincipalCollection;
import org.apache.shiro.subject.Subject;
import org.apache.shiro.util.ByteSource;
import org.springframework.beans.factory.annotation.Autowired;
//自定义UserRealm
public class UserRealm extends AuthorizingRealm {
@Autowired
UserServiceImpl userService;
//授权
@Override
protected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principalCollection) {
System.out.println("执行了授权=>doGetAuthorizationInfo");
SimpleAuthorizationInfo info = new SimpleAuthorizationInfo();
// info.addStringPermission("user:add");
//拿到当前登录的用户对象
Subject subject = SecurityUtils.getSubject();
User currentUser =(User) subject.getPrincipal();//拿到user对象
//设置当前用户的权限
info.addStringPermission(currentUser.getPerms());
return info;
}
//认证
@Override
protected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken authenticationToken) throws AuthenticationException {
System.out.println("执行了认证=>doGetAuthenticationInfo");
//UsernamePasswordToken:是通用调用MyController中login登录方法封装之后的
UsernamePasswordToken userToken = (UsernamePasswordToken) authenticationToken;
//获取数据库的数据
User user = userService.queryUserByName(userToken.getUsername());
if (user==null){//说明没这个人,登录失败
return null;//这里会自动抛出MyController类中login登录方法定义的UnknownAccountException异常
}
//可以对密码进行加密 MD5:加密(可逆) MD5盐值加密(不可逆)
//密码认证,shiro做
return new SimpleAuthenticationInfo(user,user.getPwd(),"");
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
7、整合thymeleaf
1、首页只显示有权限访问的内容
1、导入thymeleaf依赖
<!-- https://mvnrepository.com/artifact/com.github.theborakompanioni/thymeleaf-extras-shiro -->
<dependency>
<groupId>com.github.theborakompanioni</groupId>
<artifactId>thymeleaf-extras-shiro</artifactId>
<version>2.1.0</version>
</dependency>
- 1
- 2
- 3
- 4
- 5
- 6
2、在ShiroConfig中整合thymeleaf
//整合ShiroDialect:用来整合shiro thymeleaf
@Bean
public ShiroDialect getShiroDialect(){
return new ShiroDialect();
}
- 1
- 2
- 3
- 4
- 5
3、在首页导入命名空间
xmlns:shiro=“http://www.thymeleaf.org/thymeleaf-extras-shiro”
4、在首页中shiro:hasPermission获取当前登录用户的权限
<div shiro:hasPermission="user:add">
<a th:href="@{/user/add}">add</a>
</div>
<div shiro:hasPermission="user:update">
<a th:href="@{/user/update}">update</a>
</div>
- 1
- 2
- 3
- 4
- 5
- 6
2、登录时显示当前的用户名和注销,未登录随时显示登录
1、通过当前用户是否授权的方法(Unauthorized)来判断是否登录
<div shiro:notAuthenticated>
<a th:href="@{/toLogin}">登录</a>
</div>
<div shiro:Authenticated>
<a th:href="@{/logout}">注销</a>
</div>
- 1
- 2
- 3
- 4
- 5
- 6
2、通过将当前登录对象存在在session中的方法,来判断当前用户是否登录,和获取用户名
在UserRealm中获取当前用户对象并存放到session中,并且获取当前用户和用户名
Subject currentSubject = SecurityUtils.getSubject();
Session session = currentSubject.getSession();
session.setAttribute("loginUser",user);
session.setAttribute("getName",user.getName());
- 1
- 2
- 3
- 4
3、在首页获取判断
<div th:if="${session.loginUser!=null}">
<a th:href="@{/logout}">注销系统</a>
<p th:text="${session.getName}"></p>
</div>
<div th:if="${session.loginUser=null}">
<a th:href="@{/toLogin}">登录</a>
</div>
- 1
- 2
- 3
- 4
- 5
- 6
- 7


