- 1玩转微服务-基础篇-maven_maven和微服务
- 2C语言 —— 数组_c语言数组
- 3chatgpt api极简入门(参考官网教程)
- 420年不变的初心,亚马逊云科技为初创企业的独角兽梦想加速赋能!_能够获得和大型企业一样先进的基础设施和成本来实现自己的创新。andy jassy aws
- 5【数模比赛】2023华为杯数学建模比赛(思路、代码......)_2023年华为数学建模比赛结果公布时间
- 6[论文解读]All in one:: Multi-Task Prompting for Graph Neural Networks图神经网络的多任务提示_all in one: multi-task prompting for graph neural
- 7AndroidX了解一下
- 8FPGA设计入门——一位全加速器的实现_单比特全加器门级原理图
- 9Uniapp 应用未读角标插件 Ba-Shortcut-Badge_uniapp 手机桌面显示消息未读
- 10数据仓库与ODS的区别
【华为】华为防火墙双机热备
赞
踩
【华为】华为防火墙双机热备

实验需求
① 实验的地址自行规划(或者按照下面的也可以)
② 在出口的两台防火墙(AUG6000v)做双机热备,FW5作为主墙,FW6作为备墙,提高网络稳定性
③ 分别创建VLAN10、VLAN20和VLAN30,能让这三个VLAN流量能够访问到ISP(SNAT)
④ 能够在公网访问到Server服务器(DNAT)
实验拓扑

华为防火墙
账号:admin
密码:Admin@123
配置
FW5-M
前骤
<USG6000V1>system-view
Enter system view, return user view with Ctrl+Z.
[USG6000V1]sysn FW5-M
[FW5-M]undo info-center enable ## 关闭消息弹窗
Info: Information center is disabled.
- 1
- 2
- 3
- 4
- 5
- 6
单臂路由和VRRP
[FW5-M]int g1/0/1.10 ## 进入g1/0/1.10
[FW5-M-GigabitEthernet1/0/1.10]vlan-type dot1q 10 ## 给VLAN10使用
[FW5-M-GigabitEthernet1/0/1.10]ip address 192.168.10.251 24 ## 配置IP地址(不要与网关地址一样)
[FW5-M-GigabitEthernet1/0/1.10]vrrp vrid 10 virtual-ip 192.168.10.254 active ## 部署VRRP组10 虚拟IP为192.168.10.254 并且为主IP
[FW5-M-GigabitEthernet1/0/1.10]service-manage ping permit ## 开启防火墙接口ping服务
[FW5-M-GigabitEthernet1/0/1.10]quit
[FW5-M]int g1/0/1.20
[FW5-M-GigabitEthernet1/0/1.20]vlan-type dot1q 20
[FW5-M-GigabitEthernet1/0/1.20]ip address 192.168.20.251 24
[FW5-M-GigabitEthernet1/0/1.20]vrrp vrid 20 virtual-ip 192.168.20.254 active
[FW5-M-GigabitEthernet1/0/1.20]service-manage ping permit
[FW5-M-GigabitEthernet1/0/1.20]quit
[FW5-M]int g1/0/1.30
[FW5-M-GigabitEthernet1/0/1.30]vlan-type dot1q 30
[FW5-M-GigabitEthernet1/0/1.30]ip address 192.168.30.251 24
[FW5-M-GigabitEthernet1/0/1.30]vrrp vrid 30 virtual-ip 192.168.30.254 active
[FW5-M-GigabitEthernet1/0/1.30]service-manage ping permit
[FW5-M-GigabitEthernet1/0/1.30]quit
[FW5-M]int g1/0/0
[FW5-M-GigabitEthernet1/0/0]ip address 192.168.100.100 24
[FW5-M-GigabitEthernet1/0/0]quit
[FW5-M]int g1/0/2
[FW5-M-GigabitEthernet1/0/2]ip address 202.101.1.2 24
[FW5-M-GigabitEthernet1/0/2]service-manage ping permit
[FW5-M-GigabitEthernet1/0/2]quit
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
划分防火墙基本区域
[FW5-M]firewall zone trust ## 进入Trust区域
[FW5-M-zone-trust]add interface g1/0/1.10 ## 添加接口g1/0/1.10到Trust区域
[FW5-M-zone-trust]add interface g1/0/1.20 ## 添加接口g1/0/1.20到Trust区域
[FW5-M-zone-trust]quit ## 回退
[FW5-M]firewall zone dmz ## 进入DMZ区域
[FW5-M-zone-dmz]add interface g1/0/1.30 ## 添加接口g1/0/1.30到DMZ区域
[FW5-M-zone-dmz]quit
[FW5-M]firewall zone untrust
[FW5-M-zone-untrust]add interface g1/0/2
[FW5-M-zone-untrust]quit
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
部署HRP(华为心跳协议)
[FW5-M]firewall zone name HRP id 6 ## 先创建一个区域名为HRP,id为6
[FW5-M-zone-HRP]set priority 90 ## 设置区域优先级为 90
[FW5-M-zone-HRP]add interface g1/0/0 ## 将接口g1/0/0添加到HRP区域
[FW5-M-zone-HRP]quit ## 回退
[FW5-M]hrp enable ## 开启HRP协议
Info: NAT IP detect function is disabled.
HRP_S[FW5-M]hrp interface GigabitEthernet 1/0/0 remote 192.168.100.200
##指定HRP的心跳口为g1/0/0 对端地址为192.168.100.200
HRP_S[FW5-M]quit
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
FW6-B
前骤
<USG6000V1>system-view
Enter system view, return user view with Ctrl+Z.
[USG6000V1]sysn FW6-B
[FW6-B]undo info-center enable
Info: Information center is disabled.
- 1
- 2
- 3
- 4
- 5
- 6
单臂路由和VRRP
[FW6-B]int g1/0/1.10
[FW6-B-GigabitEthernet1/0/1.10]vlan-type dot1q 10
[FW6-B-GigabitEthernet1/0/1.10]ip address 192.168.10.252 24
[FW6-B-GigabitEthernet1/0/1.10]vrrp vrid 10 virtual-ip 192.168.10.254 standby
## 部署VRRP组10 虚拟IP为192.168.10.254 并且为备用IP
[FW6-B-GigabitEthernet1/0/1.10]service-manage ping permit
[FW6-B-GigabitEthernet1/0/1.10]quit
[FW6-B]int g1/0/1.20
[FW6-B-GigabitEthernet1/0/1.20]vlan-type dot1q 20
[FW6-B-GigabitEthernet1/0/1.20]ip address 192.168.20.252 24
[FW6-B-GigabitEthernet1/0/1.20]vrrp vrid 20 virtual-ip 192.168.20.254 standby
[FW6-B-GigabitEthernet1/0/1.20]service-manage ping permit
[FW6-B-GigabitEthernet1/0/1.20]quit
[FW6-B]int g1/0/1.30
[FW6-B-GigabitEthernet1/0/1.30] vlan-type dot1q 30
[FW6-B-GigabitEthernet1/0/1.30] service-manage ping permit
[FW6-B-GigabitEthernet1/0/1.30]ip address 192.168.30.252 24
[FW6-B-GigabitEthernet1/0/1.30]vrrp vrid 30 virtual-ip 192.168.30.254 standby
[FW6-B-GigabitEthernet1/0/1.30]quit
[FW6-B]int g1/0/0
[FW6-B-GigabitEthernet1/0/0]ip address 192.168.100.200 24
[FW6-B-GigabitEthernet1/0/0]quit
[FW6-B]int g1/0/2
[FW6-B-GigabitEthernet1/0/2]ip address 202.101.1.3 24
[FW6-M-GigabitEthernet1/0/2]service-manage ping permit
[FW6-B-GigabitEthernet1/0/2]quit
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
划分防火墙基本区域
[FW6-B]firewall zone trust
[FW6-B-zone-trust]add interface g1/0/1.10
[FW6-B-zone-trust]add interface g1/0/1.20
[FW6-B-zone-trust]quit
[FW6-B]firewall zone dmz
[FW6-B-zone-dmz]add interface GigabitEthernet1/0/1.30
[FW6-B-zone-dmz]quit
[FW6-B]firewall zone untrust
[FW6-B-zone-untrust]add interface g0/0/2
[FW6-B-zone-untrust]quit
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
部署HRP(华为心跳协议)
[FW6-B]firewall zone name HRP id 6
[FW6-B-zone-HRP]set priority 90
[FW6-B-zone-HRP]add interface g1/0/0
[FW6-B-zone-HRP]quit
[FW6-B]hrp enable
HRP_S[FW6-B]hrp interface GigabitEthernet 1/0/0 remote 192.168.100.100
HRP_S[FW6-B]quit
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
HRP_M[FW5-M]security-policy (+B) ## +B是同步的意思

HRP_S[FW6-B]security-policy
Error: The device is in HRP standby state, so this command can not be executed.

在有一些配置上面,只有主墙可以进行配置,并对背墙进行同步,备墙不可以
LSW2
[LSW2]sysname LSW2
[LSW2]undo info-center enable
Info: Information center is disabled.
[LSW2]vlan batch 10 20 30
Info: This operation may take a few seconds. Please wait for a moment...done.
[LSW2]interface Ethernet0/0/1
[LSW2-Ethernet0/0/1] port link-type trunk
[LSW2-Ethernet0/0/1] port trunk allow-pass vlan all
[LSW2-Ethernet0/0/1]quit
[LSW2]interface Ethernet0/0/2
[LSW2-Ethernet0/0/2] port link-type trunk
[LSW2-Ethernet0/0/2] port trunk allow-pass vlan all
[LSW2-Ethernet0/0/2]quit
[LSW2]interface Ethernet0/0/3
[LSW2-Ethernet0/0/3] port link-type access
[LSW2-Ethernet0/0/3] port default vlan 10
[LSW2-Ethernet0/0/3]quit
[LSW2]interface Ethernet0/0/4
[LSW2-Ethernet0/0/4] port link-type access
[LSW2-Ethernet0/0/4] port default vlan 20
[LSW2-Ethernet0/0/4]quit
[LSW2]interface Ethernet0/0/5
[LSW2-Ethernet0/0/5] port link-type access
[LSW2-Ethernet0/0/5] port default vlan 30
[LSW2-Ethernet0/0/5] quit
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
PC



NAT
SNAT :Easy IP
## 先放行Trust到UnTrust的流量
HRP_M[FW5-M]security-policy (+B)
HRP_M[FW5-M-policy-security]rule name T_U (+B)
HRP_M[FW5-M-policy-security-rule-T_U]source-zone trust (+B)
HRP_M[FW5-M-policy-security-rule-T_U]destination-zone untrust (+B)
HRP_M[FW5-M-policy-security-rule-T_U]action permit (+B)
## 配置SNAT
HRP_M[FW5-M]nat-policy (+B)
HRP_M[FW5-M-policy-nat]rule name SNAT (+B)
HRP_M[FW5-M-policy-nat-rule-SNAT]source-zone trust (+B)
HRP_M[FW5-M-policy-nat-rule-SNAT]destination-zone untrust (+B)
HRP_M[FW5-M-policy-nat-rule-SNAT]action source-nat easy-ip (+B)
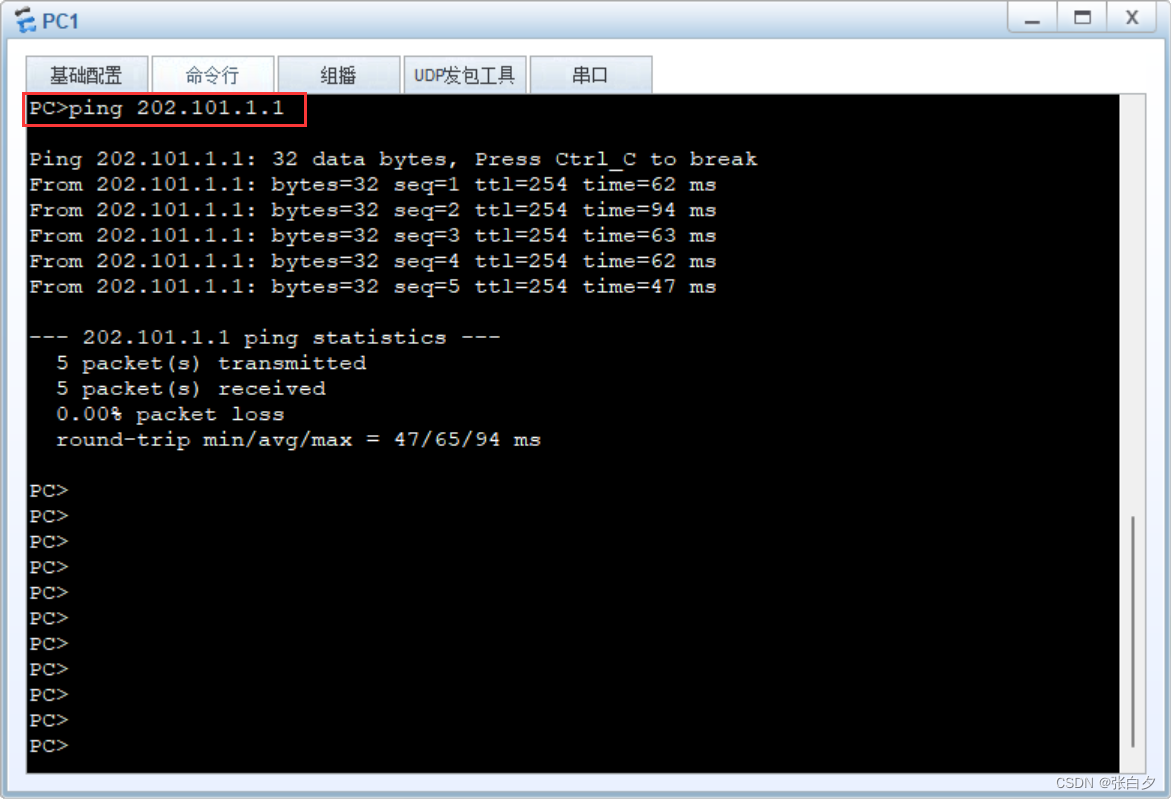
公网能通,说明SNAT做的也没问题
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
能通信啦
DNAT:将内网服务器业务映射到公网
HRP_M[FW5-M]security-policy (+B)
HRP_M[FW5-M-policy-security-rule-U_D]source-zone untrust (+B)
HRP_M[FW5-M-policy-security-rule-U_D]destination-address 192.168.30.100 32 (+B)
HRP_M[FW5-M-policy-security-rule-U_D]action permit (+B)
HRP_M[FW5-M]nat-policy (+B)
HRP_M[FW5-M-policy-nat]rule name DNAT (+B)
HRP_M[FW5-M-policy-nat-rule-DNAT]source-zone untrust (+B)
HRP_M[FW5-M-policy-nat-rule-DNAT]destination-address 202.101.1.100 mask 255.25
5.255.255 (+B)
HRP_M[FW5-M-policy-nat-rule-DNAT]action destination-nat static address-to-addr
ess address 192.168.30.100 (+B)
HRP_M[FW5-M-policy-nat-rule-DNAT]quit
HRP_M[FW5-M-policy-nat]quit
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
成功映射到公网,使公网能访问到该服务器,说明DNAT做成功啦

查看会话表项

HRP
HRP(Huawei Redundancy Protocol) — 华为心跳协议
用来实现防火墙双机热备的设备之间的状态数据同步,以及策略和关键命令备份
如果主墙出现故障,就会通过备墙进行传输
备份通道:心跳线(两台设备直连的这跟线)
对应的接口:HRP心跳接口
两台FW之间备份的数据是通过心跳口发送和接收的,是通过心跳链路(备份通道)传输的。
– 心跳口必须是状态独立且具有IP地址的接口,可以是一个物理接口(GE接口),也可以是为了增加带宽,由多个物理接口捆绑而成的一个逻辑接口Eth-Trunk。
HRP 的优先级默认:local_priority=45000
① 默认情况下,优先级高的为master
② 如果双方优先级一致,就根据VGMP组状态进行主备选举,VRRP主→HRP 主
如果使用修改优先级的方式进行主备选举的话,需要注意不要把备墙优先级修改过低,可能导致出现故障后,由于优先级主墙仍然比备墙高,而导致主备不会切换。
HRP_M :HRP主
HRP_S :HRP备
配置文档
FW5_M
#
sysname FW5-M
#
undo info-center enable
#
hrp enable
hrp interface GigabitEthernet1/0/0 remote 192.168.100.200
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 192.168.100.100 255.255.255.0
#
interface GigabitEthernet1/0/1.10
vlan-type dot1q 10
ip address 192.168.10.251 255.255.255.0
vrrp vrid 10 virtual-ip 192.168.10.254 active
service-manage ping permit
#
interface GigabitEthernet1/0/1.20
vlan-type dot1q 20
ip address 192.168.20.251 255.255.255.0
vrrp vrid 20 virtual-ip 192.168.20.254 active
service-manage ping permit
#
interface GigabitEthernet1/0/1.30
vlan-type dot1q 30
ip address 192.168.30.251 255.255.255.0
vrrp vrid 30 virtual-ip 192.168.30.254 active
service-manage ping permit
#
interface GigabitEthernet1/0/2
ip address 202.101.1.2 255.255.255.0
service-manage ping permit
#
firewall zone trust
add interface GigabitEthernet1/0/1.10
add interface GigabitEthernet1/0/1.20
#
firewall zone untrust
add interface GigabitEthernet1/0/2
#
firewall zone dmz
add interface GigabitEthernet1/0/1.30
#
firewall zone name HRP id 6
set priority 90
add interface GigabitEthernet1/0/0
#
ip route-static 0.0.0.0 0.0.0.0 202.101.1.1
#
security-policy
rule name SNAT
source-zone trust
destination-zone untrust
rule name T_U
source-zone trust
destination-zone untrust
action permit
rule name U_D
source-zone untrust
destination-address 192.168.30.100 mask 255.255.255.255
action permit
#
nat-policy
rule name DNAT
source-zone untrust
destination-address 202.101.1.100 mask 255.255.255.255
action destination-nat static address-to-address address 192.168.30.100
rule name SNAT
source-zone trust
destination-zone untrust
action source-nat easy-ip
#
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
FW6_B
#
sysname FW6-B
#
undo info-center enable
#
hrp enable
hrp interface GigabitEthernet1/0/0 remote 192.168.100.100
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 192.168.100.200 255.255.255.0
#
interface GigabitEthernet1/0/1
undo shutdown
#
interface GigabitEthernet1/0/1.10
vlan-type dot1q 10
ip address 192.168.10.252 255.255.255.0
vrrp vrid 10 virtual-ip 192.168.10.254 standby
service-manage ping permit
#
interface GigabitEthernet1/0/1.20
vlan-type dot1q 20
ip address 192.168.20.252 255.255.255.0
vrrp vrid 20 virtual-ip 192.168.20.254 standby
service-manage ping permit
#
interface GigabitEthernet1/0/1.30
vlan-type dot1q 30
ip address 192.168.30.252 255.255.255.0
vrrp vrid 30 virtual-ip 192.168.30.254 standby
service-manage ping permit
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 202.101.1.3 255.255.255.0
service-manage ping permit
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/1.10
add interface GigabitEthernet1/0/1.20
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/2
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/1.30
#
firewall zone name HRP id 6
set priority 90
add interface GigabitEthernet1/0/0
#
ip route-static 0.0.0.0 0.0.0.0 202.101.1.1
#
security-policy
rule name SNAT
source-zone trust
destination-zone untrust
rule name T_U
source-zone trust
destination-zone untrust
action permit
rule name U_D
source-zone untrust
destination-address 192.168.30.100 mask 255.255.255.255
action permit
#
nat-policy
rule name DNAT
source-zone untrust
destination-address 202.101.1.100 mask 255.255.255.255
action destination-nat static address-to-address address 192.168.30.100
rule name SNAT
source-zone trust
destination-zone untrust
action source-nat easy-ip
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
LSW2
#
sysname LSW2
#
undo info-center enable
#
vlan batch 10 20 30
#
interface Ethernet0/0/1
port link-type trunk
port trunk allow-pass vlan all
#
interface Ethernet0/0/2
port link-type trunk
port trunk allow-pass vlan all
#
interface Ethernet0/0/3
port link-type access
port default vlan 10
#
interface Ethernet0/0/4
port link-type access
port default vlan 20
#
interface Ethernet0/0/5
port link-type access
port default vlan 30
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
ISP
#
interface GigabitEthernet0/0/0
ip address 202.101.1.1 255.255.255.0
#
interface LoopBack0
ip address 8.8.8.8 255.255.255.255
#
- 1
- 2
- 3
- 4
- 5
- 6
- 7


