- 1m3u8源地址,抓片....下片....看片都透露给你_index网站入口m3u8
- 2计算机视觉实战项目3(图像分类+目标检测+目标跟踪+姿态识别+车道线识别+车牌识别+无人机检测+A*路径规划+单目测距与测速+行人车辆计数等)
- 3【Linux系统进阶详解】Linux压缩工具zip,unzip,tar,zcat,gzip精讲_zip linux
- 4分享一个好用的个人网址导航网站,无广告干净强大
- 5redis详解、哨兵模式、集群模式_redis 3.2.5哨兵搭建
- 6diffusion训练提示Sizes of tensors must match except in dimension 1. Expected size 20 but got size 21 for_return self._call_impl(*args, **kwargs)
- 7Android应用程序开发以及背后的设计思想深度剖析(5)_android 可移植性方面的设计思想和方法。
- 8Linux安装jdk、tomcat、MySQL离线安装与启动
- 9后端接口数据没有分页,导致前端卡顿_接收后端的一颗树 前端卡顿
- 10HarmonyOS4.0从零开始的开发教程09页签切换
基于Docker部署OpenLDAP,同时集成第三方系统(GitLab、JIRA、Nexus、Harbor)_docker openldap
赞
踩
基于Docker部署OpenLDAP,同时集成第三方系统(GitLab、JIRA等)

一、通过docker-compose部署open-ldap
下面通过docker-compose一键部署openLDAP、phpldapadmin和self-service-password。(通过K8s部署的方式大同小异)
准备open-ldap的docker-compose文件
version: '2' services: openldap: image: osixia/openldap:1.5.0 ### 如果有私有仓库可以从自己的私有仓库拉取镜像 container_name: openldap restart: always environment: LDAP_LOG_LEVEL: "256" LDAP_ORGANISATION: "xxx" ### 您的组织名称 LDAP_DOMAIN: "zaq.test" ### 公司域名 LDAP_BASE_DN: "dc=zaq,dc=test" ### 根据域名组成 LDAP_ADMIN_PASSWORD: "XXX" ### 密码自己来设置 LDAP_CONFIG_PASSWORD: "XXX" LDAP_READONLY_USER: "false" #LDAP_READONLY_USER_USERNAME: "readonly" #LDAP_READONLY_USER_PASSWORD: "readonly" LDAP_RFC2307BIS_SCHEMA: "false" LDAP_BACKEND: "mdb" #LDAP_TLS: "true" #LDAP_TLS_CRT_FILENAME: "zaq.test.pem" #LDAP_TLS_KEY_FILENAME: "zaq.test.key" #LDAP_TLS_DH_PARAM_FILENAME: "dhparam.pem" #LDAP_TLS_CA_CRT_FILENAME: "ca.crt" #LDAP_TLS_ENFORCE: "false" #LDAP_TLS_CIPHER_SUITE: "SECURE256:-VERS-SSL3.0" # LDAP_TLS_VERIFY_CLIENT: "demand" LDAP_REPLICATION: "false" #LDAP_REPLICATION_CONFIG_SYNCPROV: 'binddn="cn=admin,cn=config" bindmethod=simple credentials="$$LDAP_CONFIG_PASSWORD" searchbase="cn=config" type=refreshAndPersist retry="60 +" timeout=1 starttls=critical' #LDAP_REPLICATION_DB_SYNCPROV: 'binddn="cn=admin,$$LDAP_BASE_DN" bindmethod=simple credentials="$$LDAP_ADMIN_PASSWORD" searchbase="$$LDAP_BASE_DN" type=refreshAndPersist interval=00:00:00:10 retry="60 +" timeout=1 starttls=critical' #LDAP_REPLICATION_HOSTS: "#PYTHON2BASH:['ldap://ldap.example.org','ldap://ldap2.example.org']" KEEP_EXISTING_CONFIG: "false" LDAP_REMOVE_CONFIG_AFTER_SETUP: "true" #LDAP_SSL_HELPER_PREFIX: "ldap" tty: true stdin_open: true volumes: - /opt/openldap/ldap:/var/lib/ldap - /opt/openldap/slapd.d:/etc/ldap/slapd.d - /opt/openldap/certs:/container/service/lapd/assets/certs ports: - "389:389" - "636:636" # For replication to work correctly, domainname and hostname must be # set correctly so that "hostname"."domainname" equates to the # fully-qualified domain name for the host. domainname: "zaq.test" hostname: "ldap-server" phpldapadmin: image: osixia/phpldapadmin:latest container_name: phpldapadmin restart: always environment: PHPLDAPADMIN_LDAP_HOSTS: "openldap" ### 如果部署后登录不进去有可能是这里出了问题,直接换为部署openldap服务的公网IP试试 PHPLDAPADMIN_HTTPS: "false" ports: - "50081:80" depends_on: - openldap self-service-password: container_name: self-service-password image: tiredofit/self-service-password:latest restart: always ports: - "50080:80" environment: - LDAP_SERVER=ldap://openldap:389 - LDAP_BINDDN=cn=admin,dc=zaq,dc=test - LDAP_BINDPASS=XXXX - LDAP_BASE_SEARCH=dc=zaq,dc=test - MAIL_FROM=it@open.com - MAIL_FROM_NAME=账号自助服务平台 - SMTP_DEBUG=0 - SMTP_HOST=smtp.qiye.aliyun.com - SMTP_USER=it@open.com - SMTP_PASS=jYda52VZ8Ftw1111 - SMTP_PORT=465 - SMTP_SECURE_TYPE=ssl - SMTP_AUTH_ON=true - NOTIFY_ON_CHANGE=true volumes: - /etc/localtime:/etc/localtime - /opt/openldap/self-service-password/htdocs:/www/ssp - /opt/openldap/self-service-password/logs:/www/logs deploy: resources: limits: memory: 2G reservations: memory: 512M
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
执行docker-compose up命令,就可以一键部署openldap、phpldapadmin(他就是openldap的操作页面)、self-service-password(用户用来修改密码的操作页面)。
接下来可以通过访问IP:50081访问phpldapadmin了。账号就是cn=admin,dc=zaq,dc=test,密码就是通过LDAP_ADMIN_PASSWORD设置的。
二、操作指南
这里先在dc下面创建一个ou=group和一个ou=user。暂时先不按部分区分,如果想再按部分区分则就先创建一个ou,再在该ou下创建一个ou=group即可。
创建ou

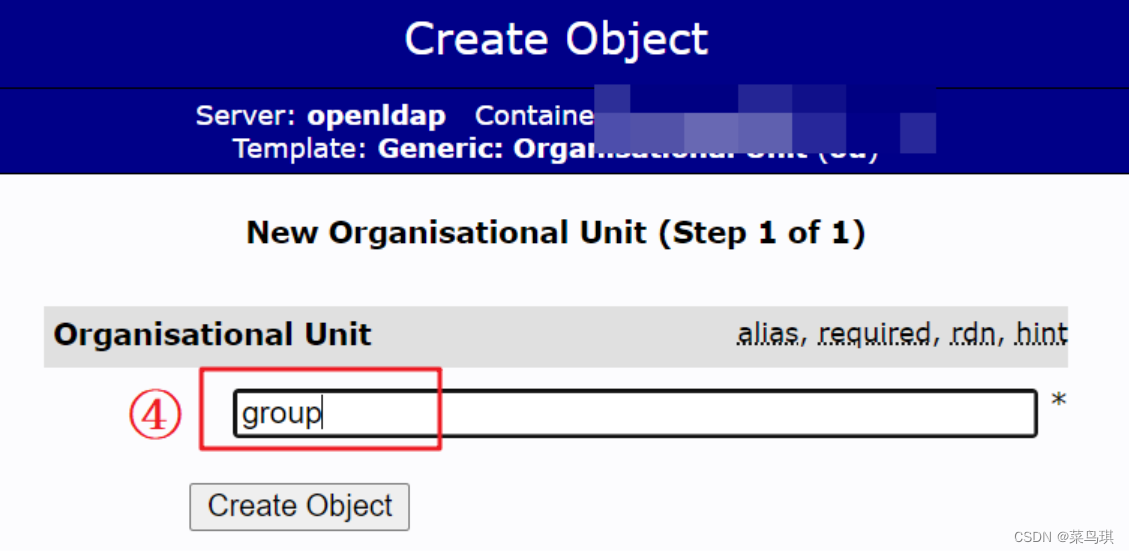
创建Group
在ou=group下创建dev
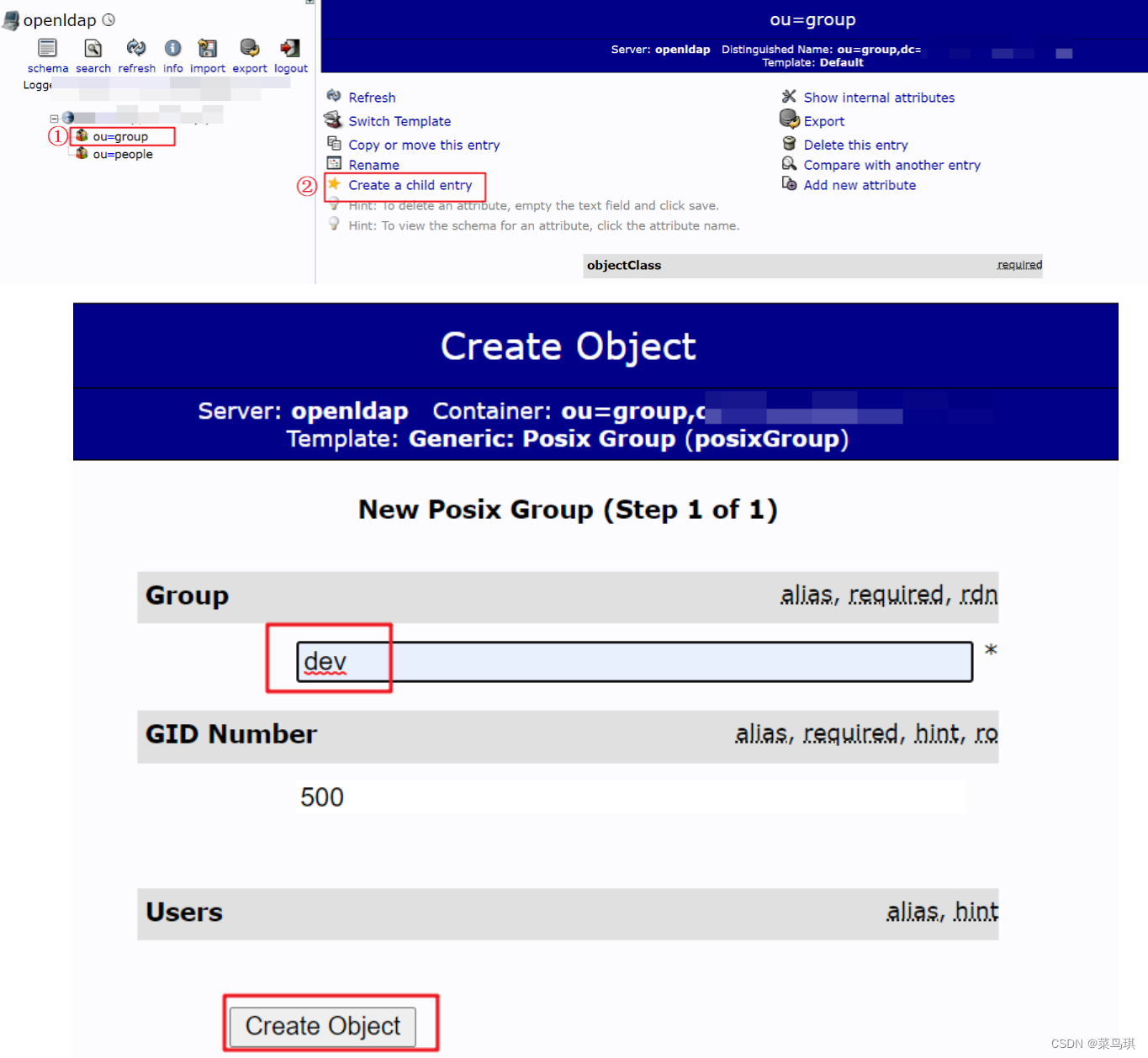
创建User Account
在ou=people下创建用户
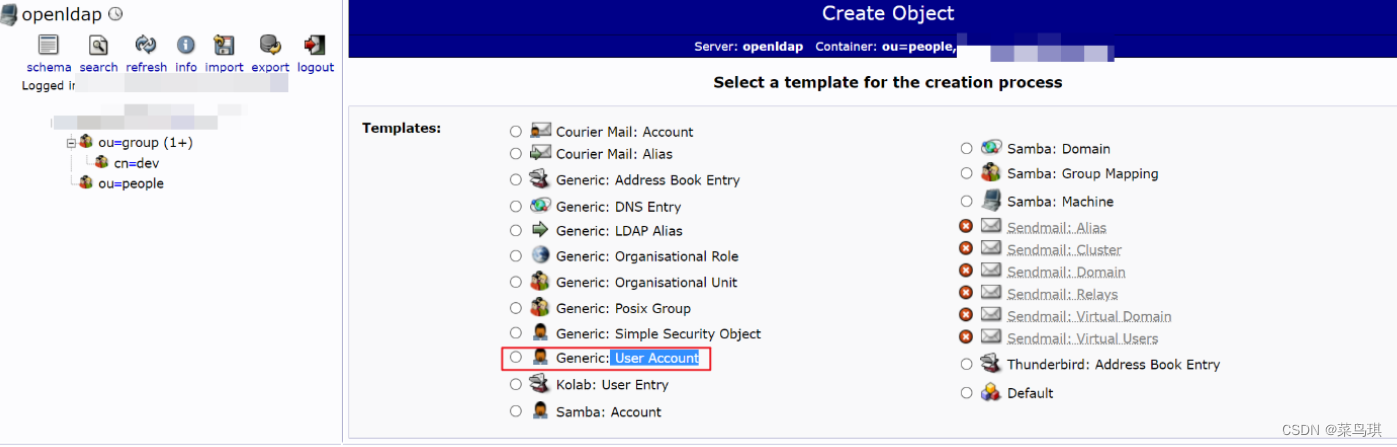
填写用户信息
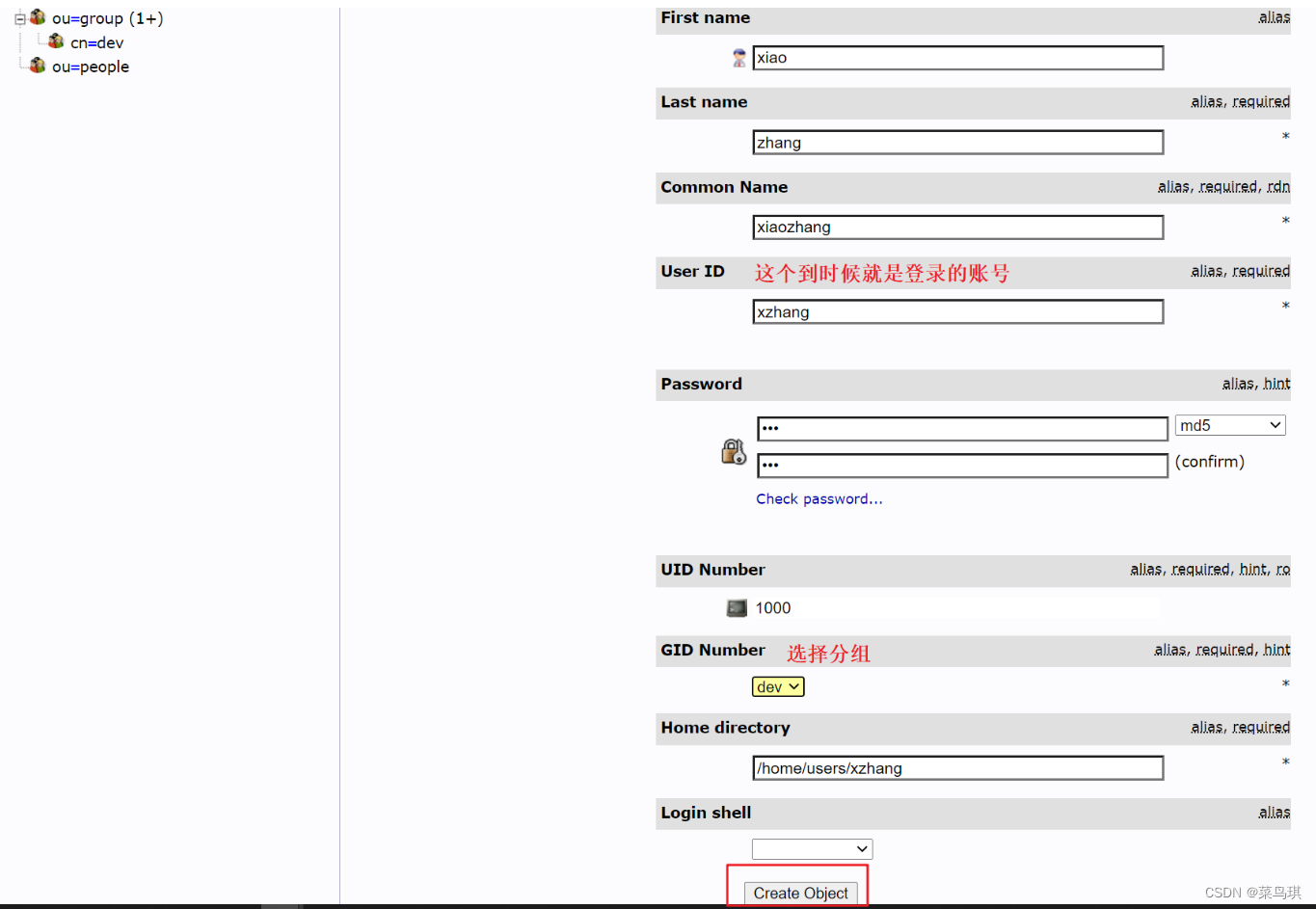
为用户填写其他属性
为用户添加真实姓名和邮箱(有些系统需要用户的这两个信息!比如gitlab)
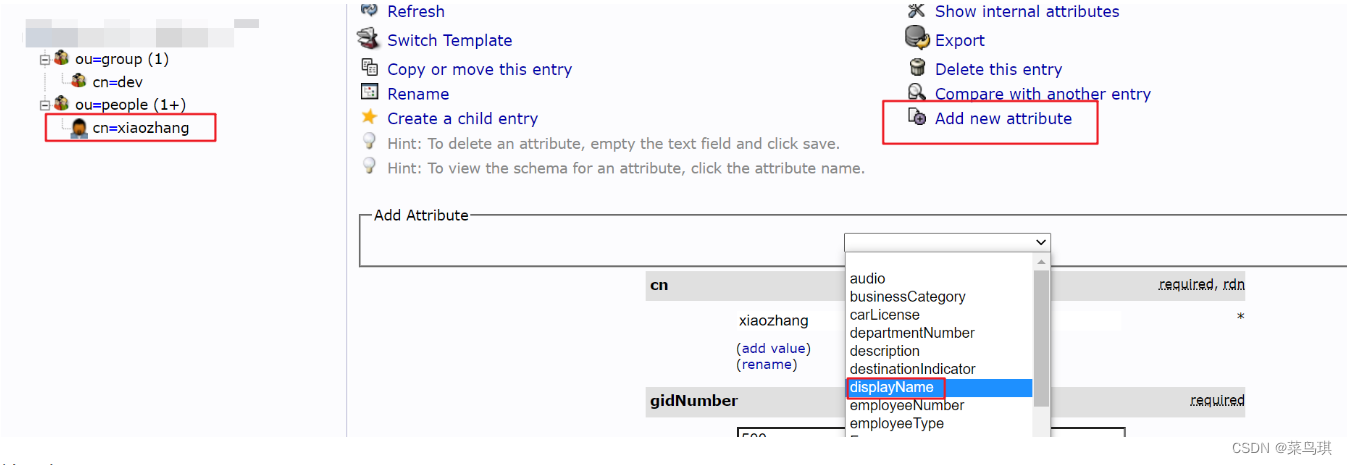
效果如下:
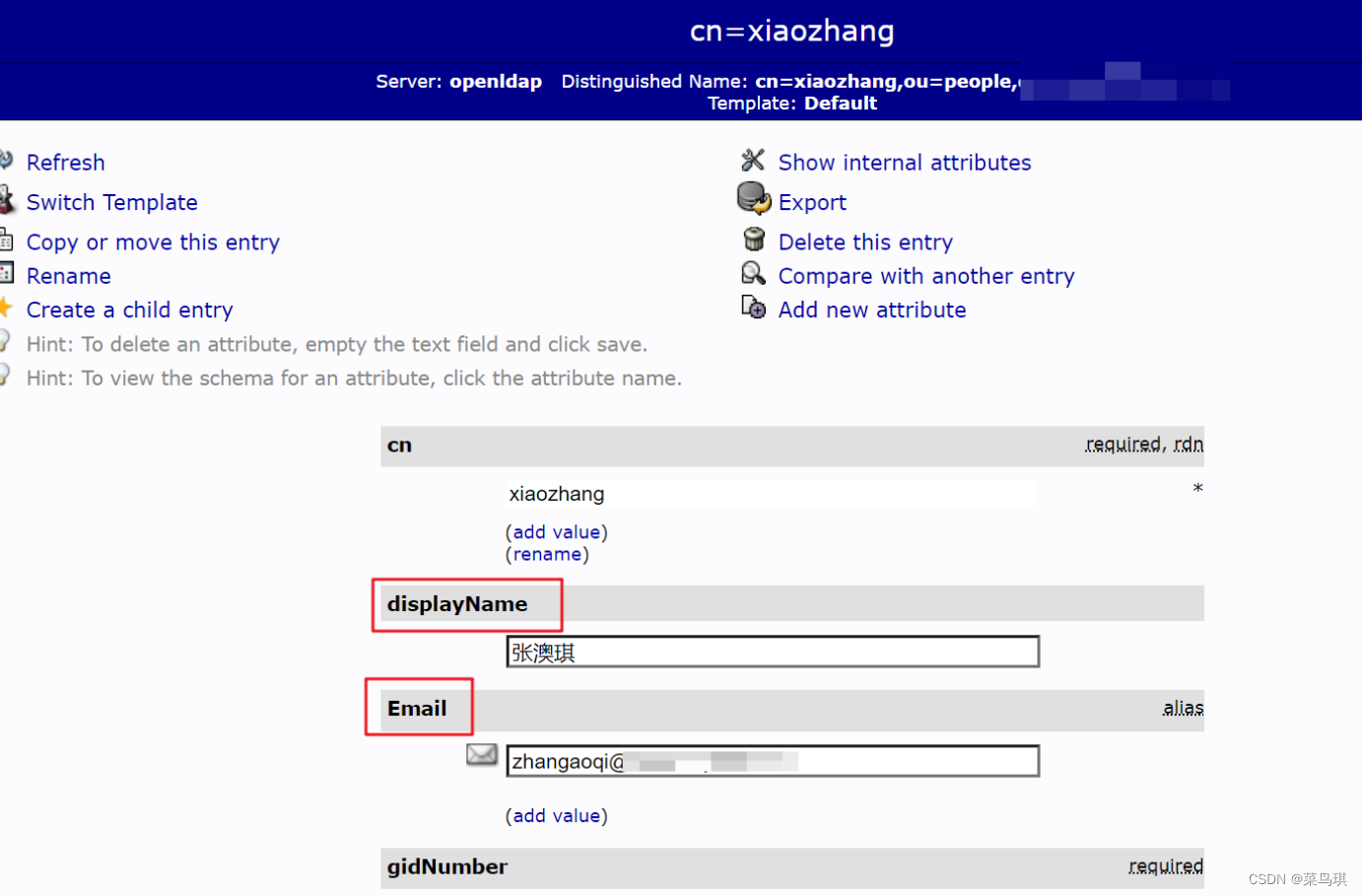
LDAP统一账号管理——与第三方集成
一、LDAP和JRIA的集成
- 登录进JRIA的控制台(需要是管理员身份)
- 点击:配置—>用户管理—>用户目录—>添加目录—>LDAP
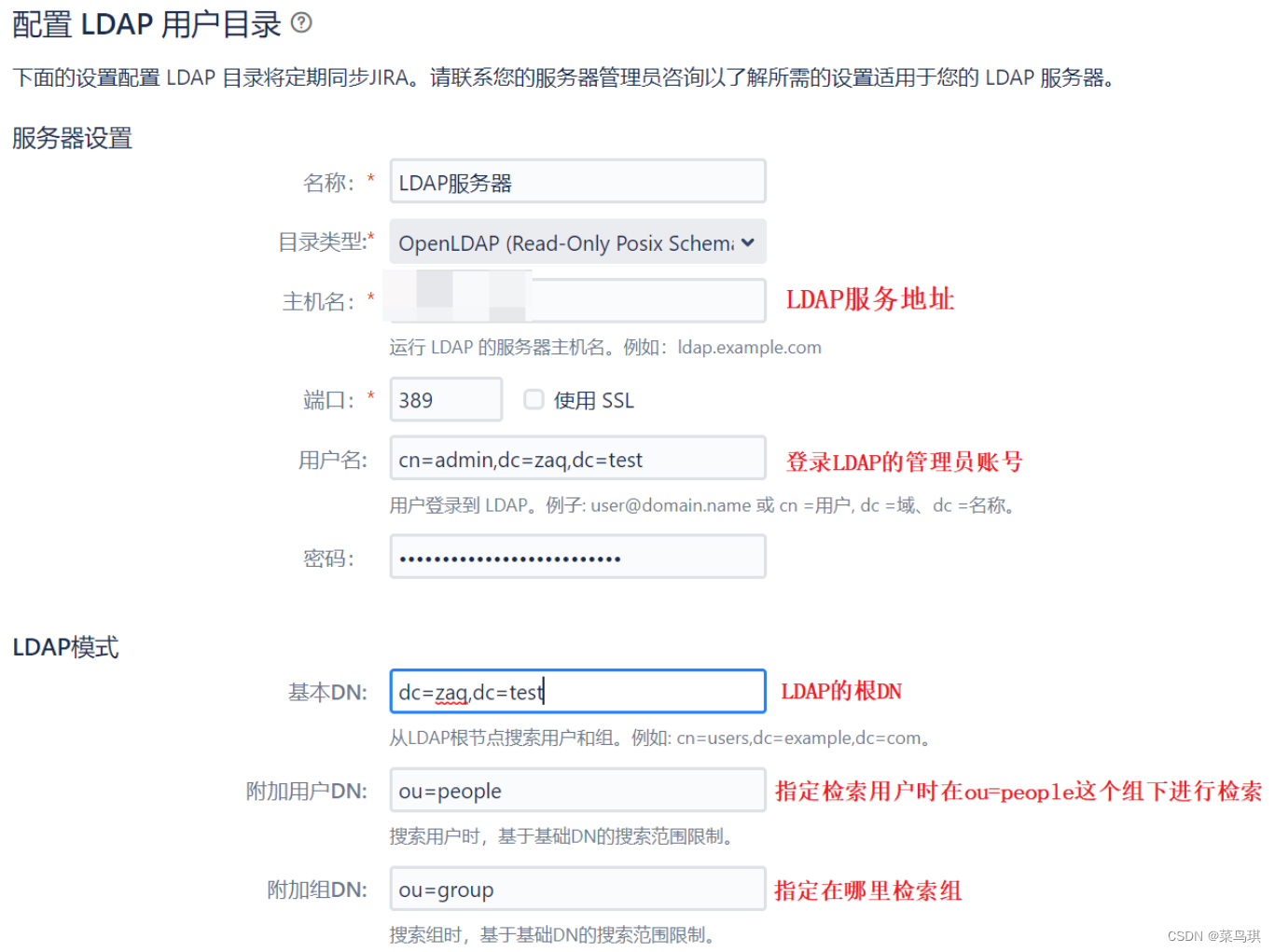
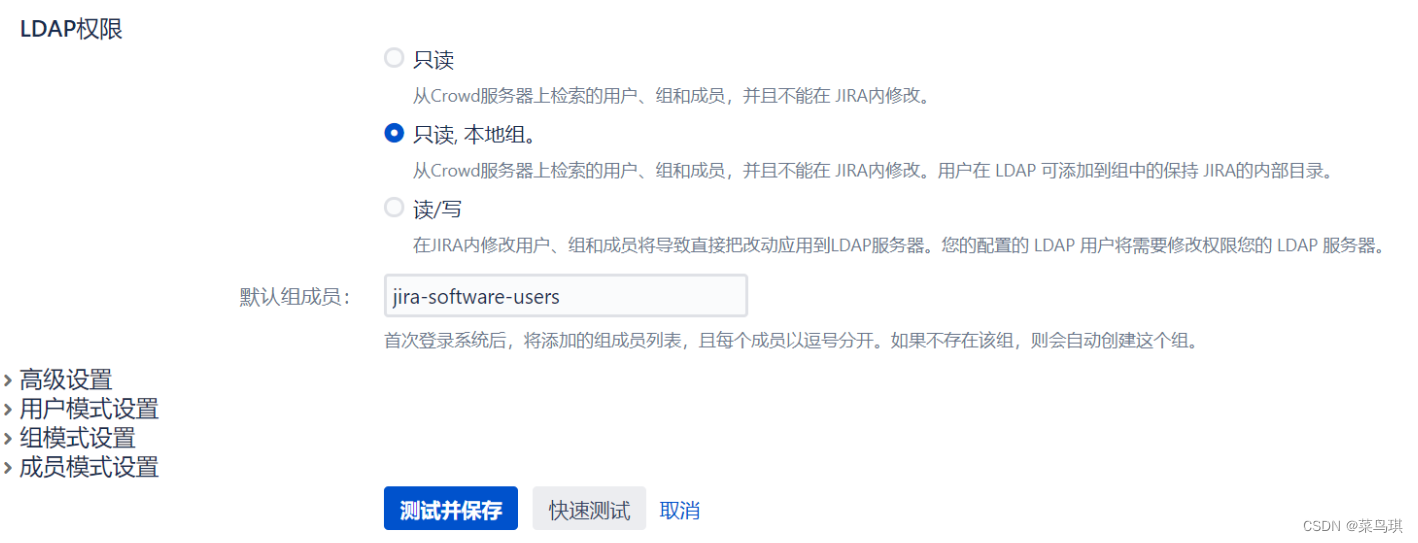
特别解释几个属性的含义:
- LDAP模式
- “基础DN” 填写LDAP的根节点,类似dc=zaq,dc=test;
- “附加用户DN” 填写限制用户搜索范围的值,类似ou=people,不填的话从基础DN开始搜索;
- “附加组DN” 填写限制用户组搜索范围的值,和上一项类似;
- LDAP权限
- 只读:JIRA只能从LDAP中读取用户以及用户组信息,所有对用户及用户组的修改不能通过JIRA进行。
- 本地只读:相比只读来说,可以在JIRA中添加组,并且会将LDAP同步过来的用户加入到该组中。
- 读写:不但可以读取LDAP上的用户及组信息,还可以通过JIRA修改这些信息,这些信息会自动同步到LDAP。
二、LDAP和Confluence的集成
右上角设置 → 用户管理 → 用户目录 → 添加目录 → LDAP
接下来的流程和JIRA一模一样。(这里也可以直接让JIRA和Confluence联动,就只需要配置好JIRA的LDAP就行了)
三、LDAP和GitLab的集成
找到gitlab的配置文件:/etc/gitlab/gitlab.rb,然后修改下面的内容
### LDAP Settings ###! Docs: https://docs.gitlab.com/omnibus/settings/ldap.html ###! **Be careful not to break the indentation in the ldap_servers block. It is ###! in yaml format and the spaces must be retained. Using tabs will not work.** gitlab_rails['ldap_enabled'] = true # gitlab_rails['prevent_ldap_sign_in'] = false ###! **remember to close this block with 'EOS' below** gitlab_rails['ldap_servers'] = YAML.load <<-'EOS' main: # 'main' is the GitLab 'provider ID' of this LDAP server label: 'LDAP' host: 'xx.xx.xx.xx' ### LDAP服务地址 port: 389 uid: 'uid' ### 指定登录gitlab使用LDAP的哪个字段作为账号 bind_dn: 'cn=admin,dc=zaq,dc=test' ### 这里用自己的管理员账号(需要一个有read权限的账号验证通过后搜索用户输入的用户名是否存在) password: 'XXX' encryption: 'plain' # "start_tls" or "simple_tls" or "plain" # verify_certificates: true # smartcard_auth: false active_directory: false ### 如果是 Active Directory LDAP server 则设为true allow_username_or_email_login: true ### 是否允许email登录 # lowercase_usernames: false ### 是否将用户名转为小写 block_auto_created_users: false ### 是否自动创建用户。如果设置为true则自动注册的账户是被锁定的,需要管理员账户手动的为这些账户解锁,因此此处将其设置为false。当设置为false的时候,就需要保证,对于第三方登录的用户完全可控。 base: 'ou=people,dc=zaq,dc=com' ### 从哪个位置搜索用户,这里填自己的 user_filter: '' ### 表示以某种过滤条件筛选用户,比如我们只希望组为gitlab的用户来访问GitLab,则这里可以设置为:memberOf=ou=gitlab,ou=people,dc=zaq,dc=com # attributes: # LDAP 中用户的属性 # username: ['uid', 'userid', 'sAMAccountName'] # email: ['mail', 'email', 'userPrincipalName'] # name: 'cn' # first_name: 'givenName' # last_name: 'sn' ## EE only group_base: '' admin_group: '' sync_ssh_keys: false EOS
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
修改完后重启GitLab!最后最好再取消GitLab的注册功能,新用户只能通过 LDAP 认证的方式进行登陆。
拉取代码时要用LDAP创建的账号密码拉取。
四、LDAP和Nexus的集成
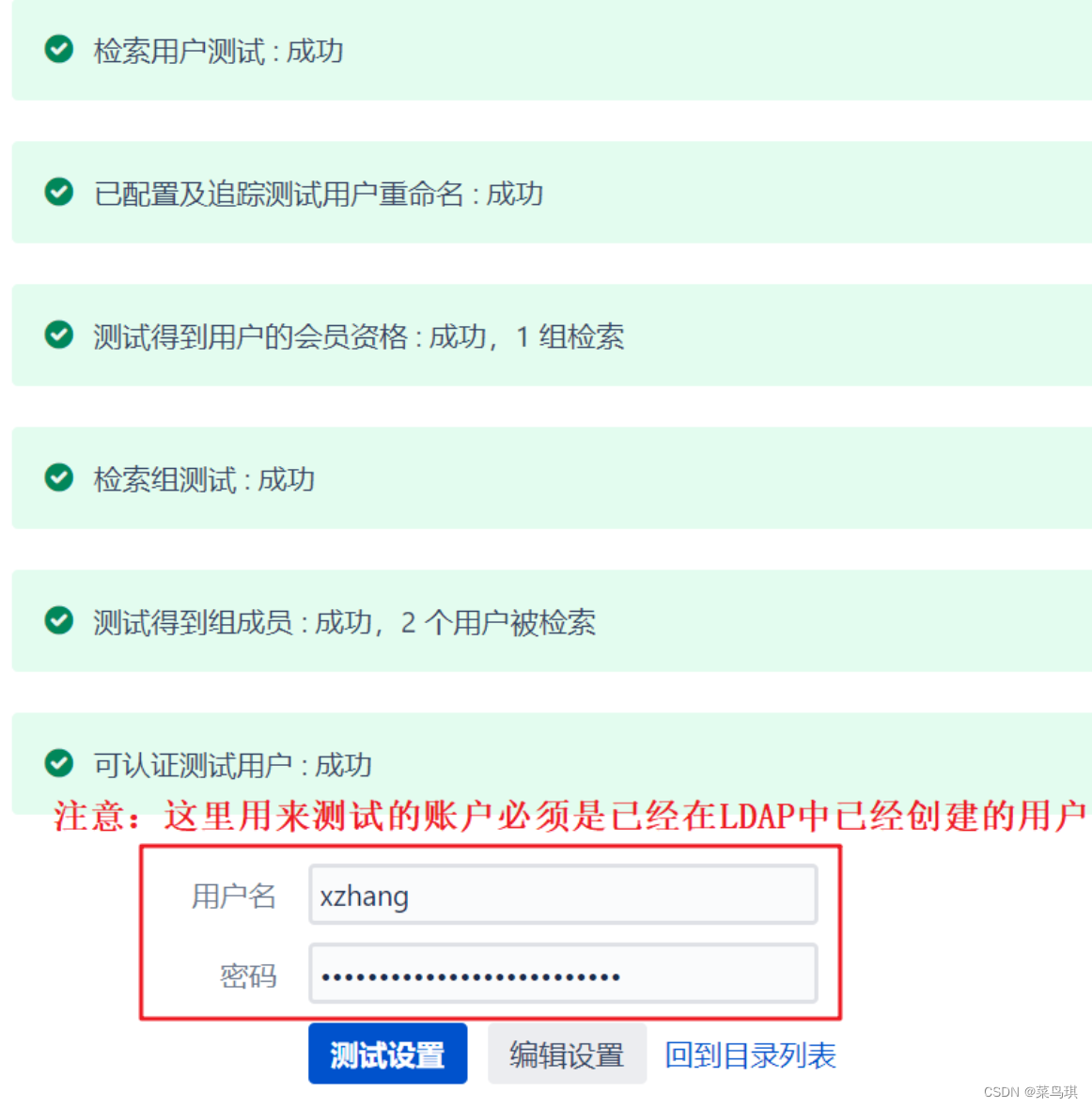
- 登录管理员账号
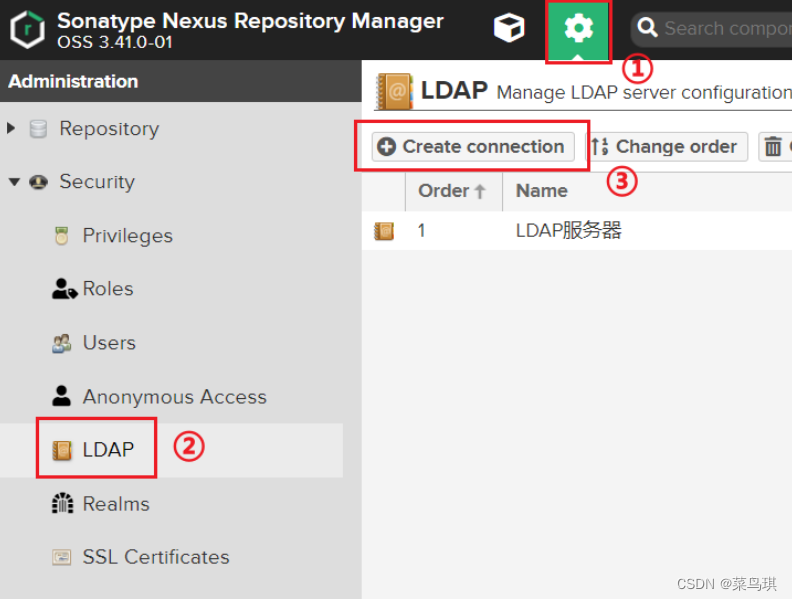
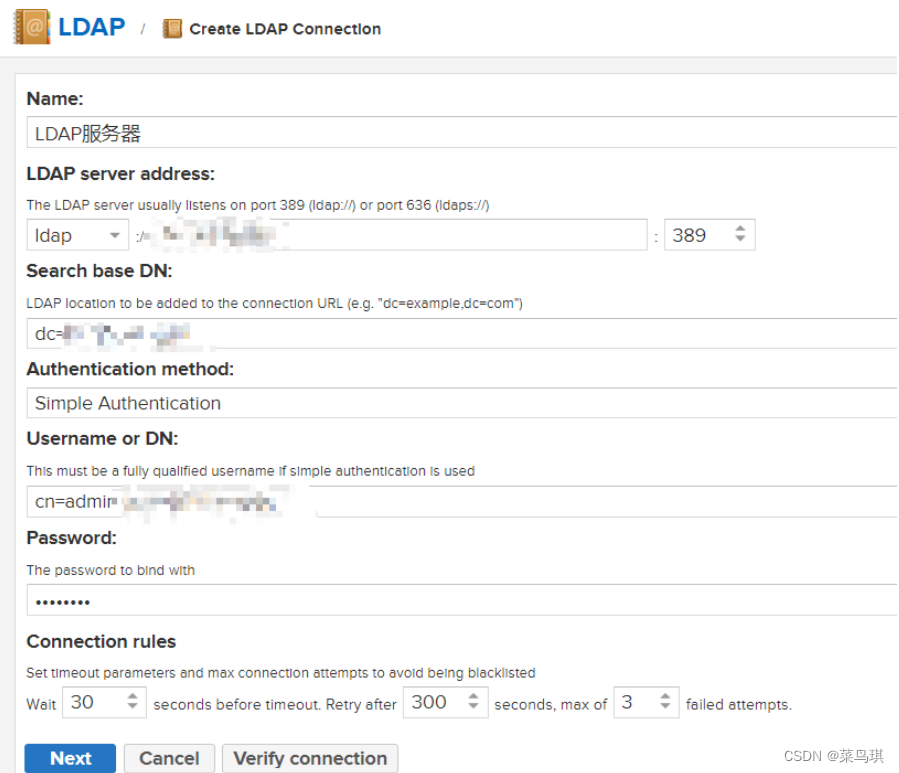
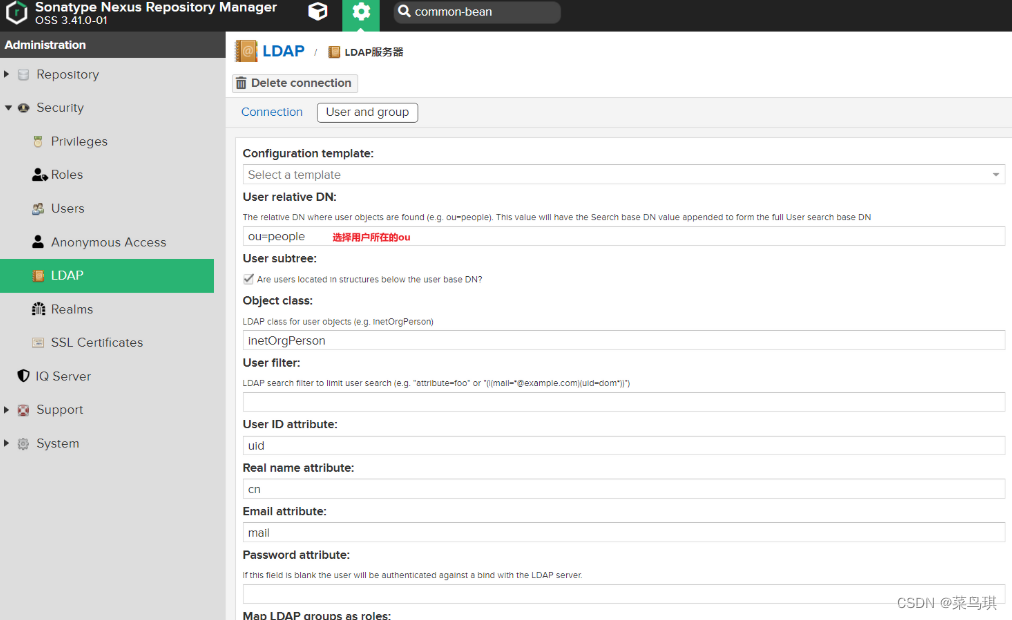
- 配置完后别忘了Users中选中LDAP用户,为LDAP用户分配角色
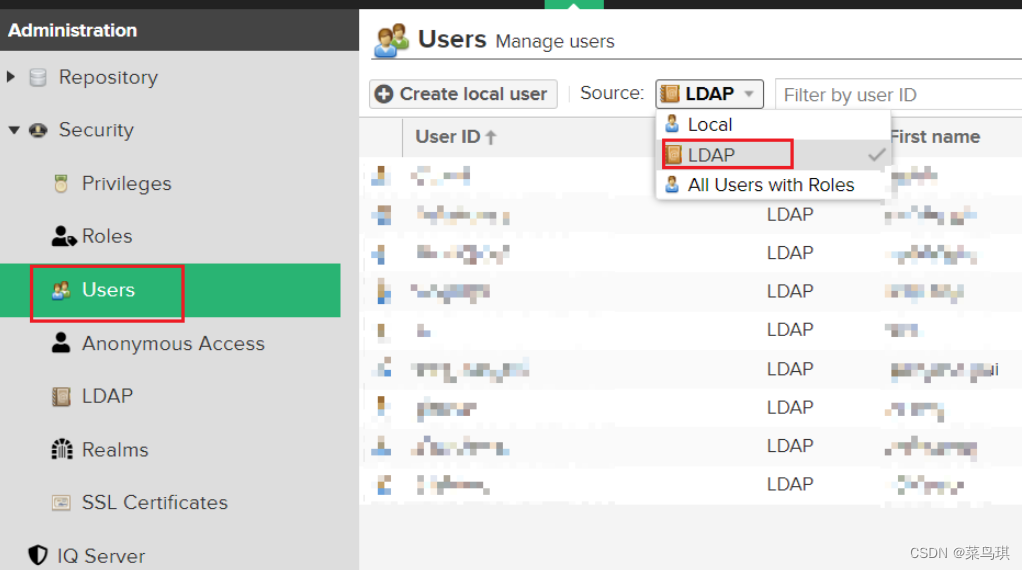
五、LDAP和Harbor的集成
特别注意:在没有添加任何用户之前,你可以修改认证模式(Database模式或者LDAP模式), 但当Harbor系统中已经有至少一个用户之后(除了admin用户外),将不能够修改认证模式。
新版本的可以直接在页面进行修改,如下:
登录管理员账户,选中配置管理
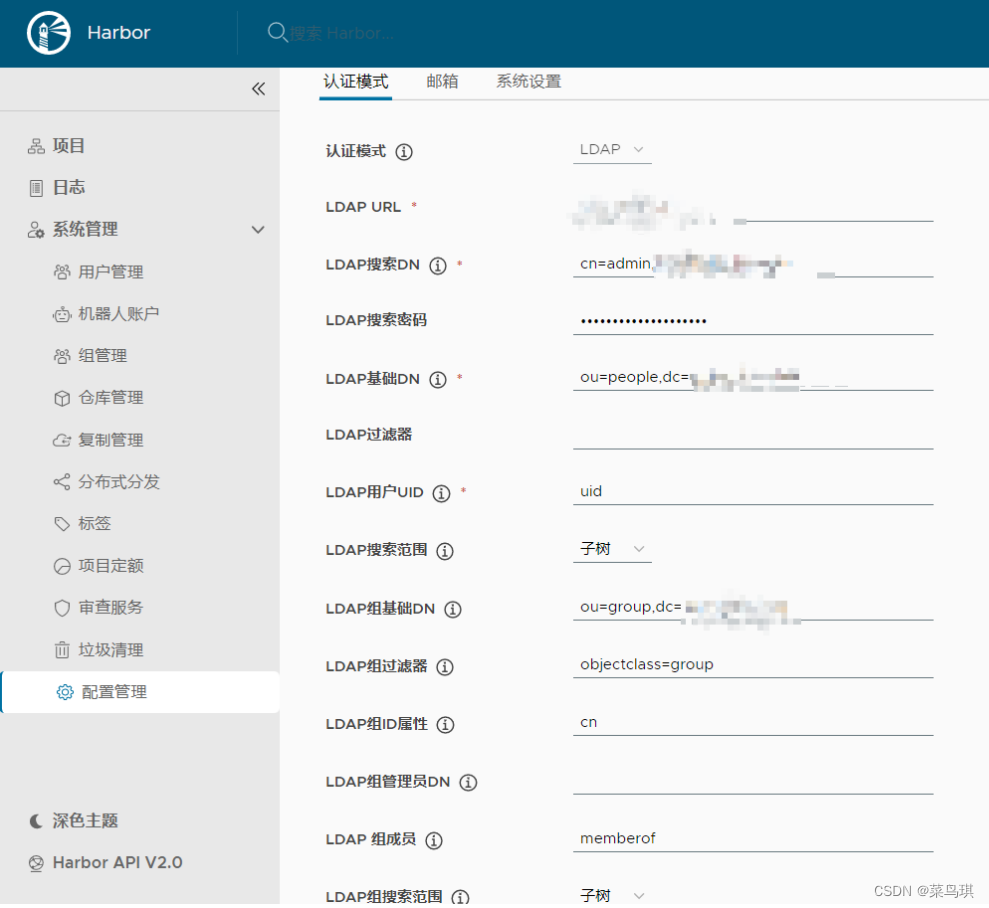
如果是老版本,则需要修改harbor.cfg文件,如下:
##By default the auth mode is db_auth, i.e. the credentials are stored in a local database. #Set it to ldap_auth if you want to verify a user's credentials against an LDAP server. auth_mode = ldap_auth #The url for an ldap endpoint. ldap_url = xx.xx.xx.xx #A user's DN who has the permission to search the LDAP/AD server. #If your LDAP/AD server does not support anonymous search, you should configure this DN and ldap_search_pwd. ldap_searchdn = cn=admin,dc=zaq,dc=test #the password of the ldap_searchdn ldap_search_pwd = xxx #The base DN from which to look up a user in LDAP/AD ldap_basedn = dc=zaq,dc=com #Search filter for LDAP/AD, make sure the syntax of the filter is correct. #ldap_filter = (objectClass=person) # The attribute used in a search to match a user, it could be uid, cn, email, sAMAccountName or other attributes depending on your LDAP/AD ldap_uid = uid #the scope to search for users, 0-LDAP_SCOPE_BASE, 1-LDAP_SCOPE_ONELEVEL, 2-LDAP_SCOPE_SUBTREE ldap_scope = 2 #Timeout (in seconds) when connecting to an LDAP Server. The default value (and most reasonable) is 5 seconds. ldap_timeout = 5 #Verify certificate from LDAP server ldap_verify_cert = true #The base dn from which to lookup a group in LDAP/AD ldap_group_basedn = ou=IT,dc=shileizcc,dc=com #filter to search LDAP/AD group ldap_group_filter = objectclass=group #The attribute used to name a LDAP/AD group, it could be cn, name ldap_group_gid = cn #The scope to search for ldap groups. 0-LDAP_SCOPE_BASE, 1-LDAP_SCOPE_ONELEVEL, 2-LDAP_SCOPE_SUBTREE ldap_group_scope = 2
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43



