热门标签
热门文章
- 1GB2312编码表_、一-…‘、∴n:r一,金,"乓:γ小兵.j‘:。斥,。.。.当事。.??pcpcy小.。白一
- 2[问题已处理]-记一次断电后mac报错networksetup -setv6off Ethernet_mac 无法运行networksetup
- 3自然语言处理中的文本聚类与语义分析_python 自然语言处理 语义分析
- 4IntelliJ IDEA 忽略Git提交_idea设置忽略git提交
- 5A10 STM32_HAL库函数 之 DAC扩展驱动器所有函数的介绍及使用
- 6文献阅读:RoFormer: Enhanced Transformer with Rotary Position Embedding
- 7chromiumUI中从处理url键盘输入到内建url页面内容准备的函数调用过程_chromium keyevent
- 8以太坊的geth java api调用_以太坊私链调用java的api接口
- 9米哈游校招前端面经(2020.10.13)_米哈游招前端吗
- 10Flink学习(五)-流式分析
当前位置: article > 正文
配置防火墙内网访问外网_配置防火墙安全策略,实现企业内网访问internet
作者:IT小白 | 2024-04-12 00:16:16
赞
踩
配置防火墙安全策略,实现企业内网访问internet
基于上篇《web登录防火墙》可能会出现的问题进行补充:
不能成功登陆WEB界⾯的解决⽅案
1、给接⼝配置IP地址(默认是存在的)

- interface g0/0/0
- ip address 192.168.0.1 24
2、允许接⼝所有服务类型,其中包括ping,https
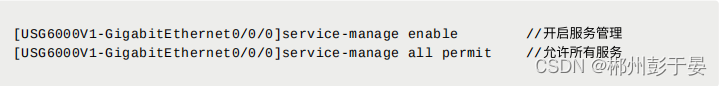
- service-manage enable //开启服务管理
- service-manage all permit //允许所有服务
3、将接⼝加⼊防⽕墙安全区域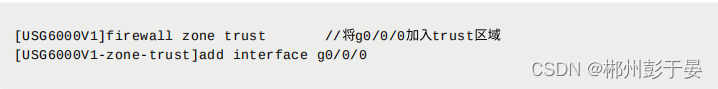
- firewall zone trust //将g0/0/0加⼊trust区域
- add interface g0/0/0
以下是内外网互通的介绍以及内容:
安全区域
华为防⽕墙的接⼝
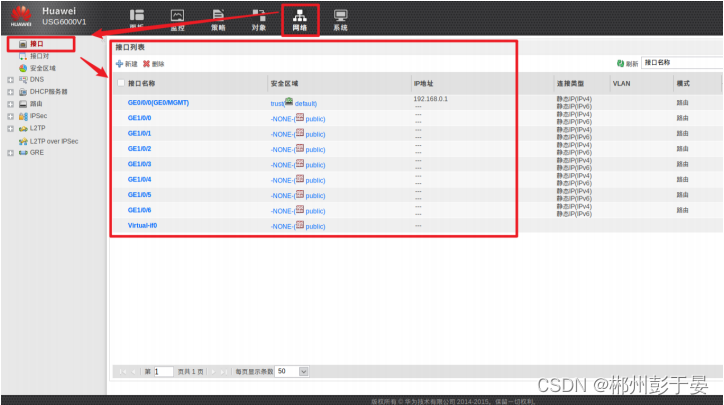
华为防⽕墙的安全区域

默认安全区:Trust、DMZ、Untrust
Local区域:代表防⽕墙本⾝
 主要安全级别
主要安全级别
Untrust(⾮受信任区域):安全级别5,通常⽤于定义互联⽹流量
DMZ(⾮军事化区域):安全级别50,通常⽤于定义服务器区域
Trust(受信任区域):安全级别85,通常⽤于定义内⽹所在区域
Local(本地区域):安全级别100,该区域主要定义设备⾃⾝发起的流量,或者是抵 达设备⾃⾝的流量
受信任程度
Local>Trust>DMZUntrust
修改接⼝属于的区域,IP地址,服务类型
1、点击接⼝,在弹窗可以修改区域类型,IP地址等...

2、也可以修改允许拒绝的服务类型
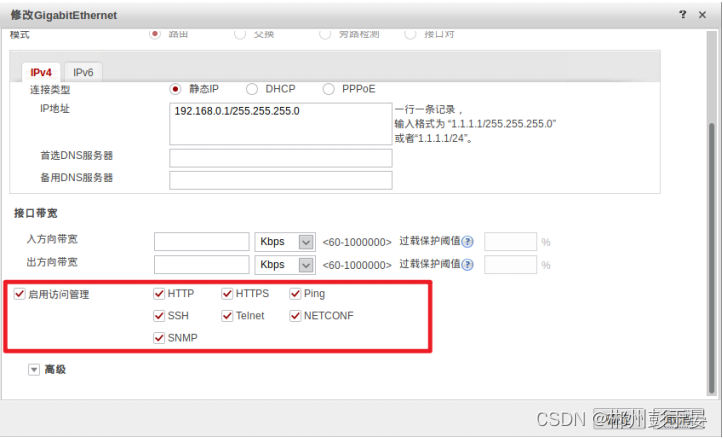
3、假设将ping服务取消,并点确定

4、在ping的时候是ping不通的

5、如果在将ping服务给打开,会发现可以正常通信

配置内⽹访问外⽹
1.配置接口
1、配置安全区域和接⼝IP地址


2、开启接⼝的Ping服务【可选】
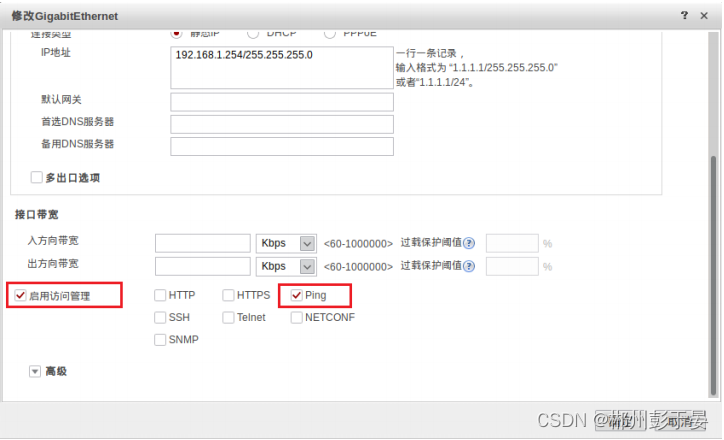


也可通过命令来配置IP地址、所属区域、服务类型
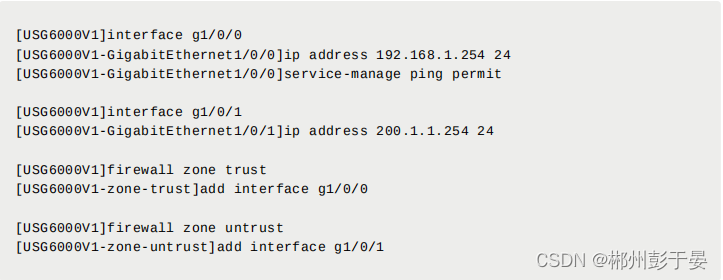
- [USG6000V1]interface g1/0/0
- [USG6000V1-GigabitEthernet1/0/0]ip address 192.168.1.254 24
- [USG6000V1-GigabitEthernet1/0/0]service-manage ping permit
- [USG6000V1]interface g1/0/1
- [USG6000V1-GigabitEthernet1/0/1]ip address 200.1.1.254 24
- [USG6000V1]firewall zone trust
- [USG6000V1-zone-trust]add interface g1/0/0
- [USG6000V1]firewall zone untrust
- [USG6000V1-zone-untrust]add interface g1/0/1
2.配置安全策略,允许安全区域的互相访问
1、配置trust可以访问untrst


可以成功ping通

web服务也可以访问

但是服务器ping客⼾端,不通
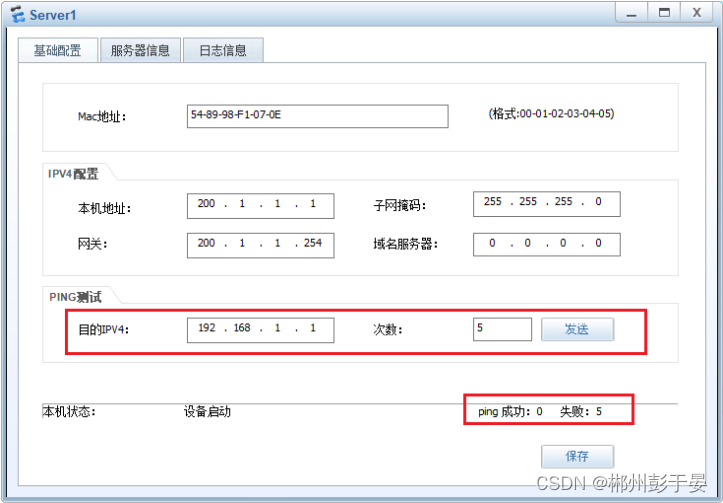
因为我们配置的是 trust 可以访问 untrust,⽽untrust不可以访问trust
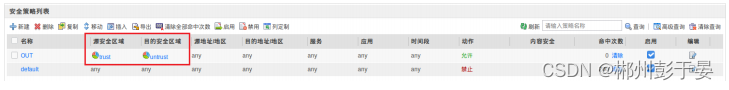
也可⽤命令配置

- [USG6000V1]security-policy
- [USG6000V1-policy-security]rule name OUT
- [USG6000V1-policy-security-rule-OUT]source-zone trust
- [USG6000V1-policy-security-rule-OUT]destination-zone untrust
- [USG6000V1-policy-security-rule-OUT]action permit
3.配置NAT策略
1、配置EasyIP
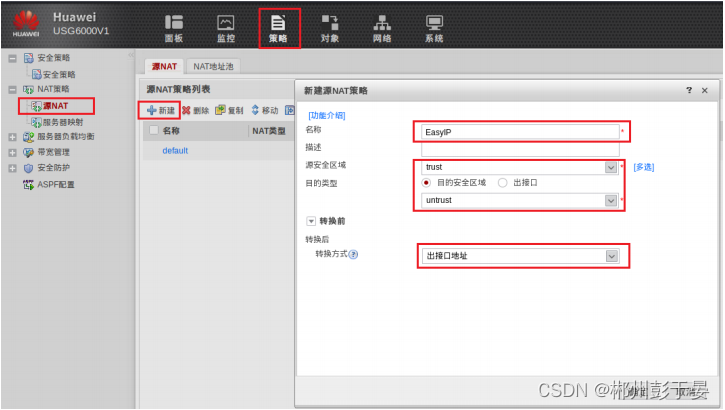
2、抓包查看,地址发⽣了转换,转换为出接⼝地址

3、也可以配置NAPT,这⾥需要配置地址池

4、将EasyIP的启⽤的对勾去掉,或者之间删除
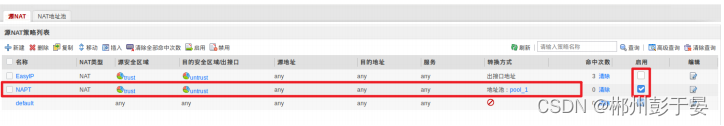
5、抓包查看,地址转换成了地址池中的地址


- [USG6000V1]nat-policy
- [USG6000V1-policy-nat]rule name EasyIP
- [USG6000V1-policy-nat-rule-EasyIP]source-zone trust
- [USG6000V1-policy-nat-rule-EasyIP]destination-zone untrust
- [USG6000V1-policy-nat-rule-EasyIP]action nat easy-ip
- //1.3版本的eNSP命令:action source-nat easy-ip

- [USG6000V1]nat-policy
- [USG6000V1-policy-nat]undo rule name EasyIP
- [USG6000V1]nat address-group pool

- [USG6000V1-address-group-pool]mode pat
- [USG6000V1-address-group-pool]section 200.1.1.10
-
- [USG6000V1]nat-policy
- [USG6000V1-policy-nat]rule name PNAT
- [USG6000V1-policy-nat-rule-PNAT]source-zone trust
- [USG6000V1-policy-nat-rule-PNAT]destination-zone untrust
- [USG6000V1-policy-nat-rule-PNAT]action nat address-group pool
配置服务器发布

1、将G1/0/0修改为DMZ

2、配置安全策略,允许untrust访问dmz
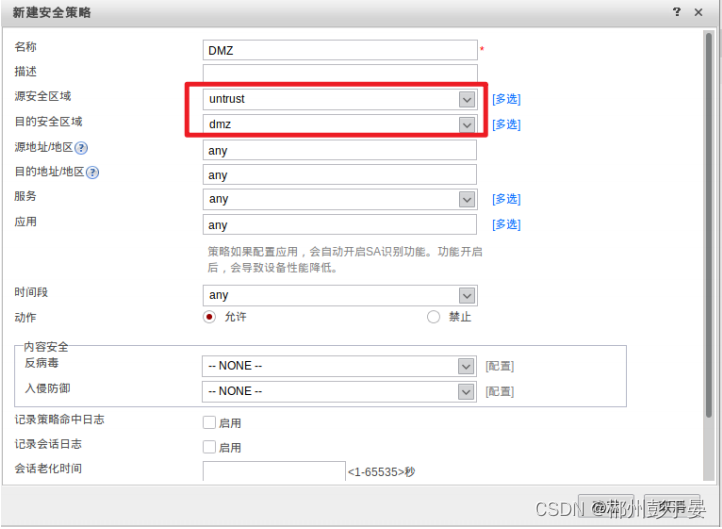
3、新建服务器映射,实现外⽹访问内⽹服务器

实现内网外网互通是一个复杂而又必要的过程,需要考虑多种因素并采取适当的措施。这包括了设置网络架构、配置防火墙规则、实现VPN和端口映射等等。在实现过程中,需要十分谨慎和细心,保证网络安全和数据的稳定传输。希望本文能对您了解以及配置内网外网互通有所帮助。如果您有任何问题,欢迎与网络安全专家咨询,他们将为您提供专业的建议和指导。
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/IT小白/article/detail/408321
推荐阅读
相关标签



