- 1明星、公众人物人脸识别——Pytorch使用mtcnn+arcface搭建人脸识别平台_人脸识别arcface
- 2花了三个月从华为OD外包转正了~_华为外包转正容易吗
- 3C++进阶--哈希
- 4【已解决】git clone 失效,fatal: unable to access ‘https://github.com/XXX.git/‘: Recv failure: C_拉库的时候fatal: unable to access '': recv failure: con
- 5Python Scrapy 中报错SyntaxError: (unicode error) ‘utf-8‘ codec can‘t decode byte 0xce in position 0_syntaxerror: (unicode error) 'utf-8' codec can't d
- 6Homestead切换PHP版本_php 无法将“update-alternatives”项识
- 7天星数科聚势赋能,精准服务实体企业的产业金融需求
- 8NLP领域模型对抗攻击简介
- 9Gitee 上最不明觉厉的项目:用代码创造出一个人工生命_gitee 人工大脑
- 10一次配置Docker环境的完整记录_docker 换源
手把手教你ssh升级openssh9.2,升级失败回退,纯干货_linux-pam-1.3.1.tar.xz
赞
踩
对于解决openssh漏洞,最好的办法就是升级,本文以openssh9.2为例,升级方法都一样,主要区别在于不同openssh版本需要依赖包的版本不一样。
1准备:
我的现在版本:
zlib:zlib-1.2.7-18
perl:perl5 (revision 5 version 16 subversion 3)
pam:pam-1.1.8-22
openssl:openssl-1.0.2k-19
openssh:openssh-7.4p1-21
依赖包下载:zlib、perl、pam、openssl、openssh,升级openssl期间可能会报错。
没有vnc后台登录的,需要开启telnet服务防止万一,最好ftp服务也开下。
附上包下载地址
zlib-1.2.13.tar.gz:https://www.zlib.net/
perl-5.16.1.tar.gz:http://www.cpan.org/src/5.0/
openssl-1.1.1t.tar.gz:https://www.openssl.org/source/
Linux-PAM-1.3.1.tar.xz:https://www.linuxfromscratch.org/blfs/view/9.0/postlfs/linux-pam.html
openssh:Index of /pub/OpenBSD/OpenSSH/portable/
xinetd-2.3.15-14.el7.x86_64、telnet-0.17-65.el7_8.x86_64、telnet-server-0.17-65.el7_8.x86_64、vsftpd-3.0.2-28.el7.x86_64.rpm:http://www.rpmfind.net/linux/rpm2html/search.php
2.开启telnet服务
rpm -ivh xinetd-2.3.15-14.el7.x86_64
rpm -ivh elnet-0.17-65.el7_8.x86_64
rpm -ivh telnet-server-0.17-65.el7_8.x86_64
修改/etc/xinetd.d/telnet的disable= no,没有创建一个
service telnet
{
flags=REUSE
socket_type=stream
wait=no
user=root
server=/usr/sbin/in.telnetd
log_on_failure += USERID
disable= no
}
启动服务
service xinetd restart / systemctl restart xinetd.service
systemctl start telnet.socket
ss -ntl | grep 23
这时使用root登录可能出现Login incorrect,查看/var/log/secure
![]()
在/etc/securetty中加入对应的模拟终端,如pts/1
3.依赖包安装,我的没有升级perl、pam
zlib安装:
tar -xzvf zlib-1.2.13.tar.gz
cd zlib-1.2.13
./configure --prefix=/usr/local/zlib
make && make install
perl安装:
tar -xzf perl-5.16.1.tar.gz
cd perl-5.16.1
./Configure -de 缺省配置
make && make install
perl -v
pam安装:
tar -xf Linux-PAM-1.3.1.tar.xz
cd Linux-PAM-1.3.1
./configure
make && make install
openssl安装:
openssl version -a
tar -zxvf openssl-1.1.1t.tar.gz
mkdir -p /usr/bak/lib64 恢复版本需要
cp -ar /usr/lib64/* /usr/bak/lib64 恢复版本需要
cd openssl-1.1.1t
./config --prefix=/usr/local/ssl
make && make install
cp -a /usr/bin/openssl /usr/bin/openssl.bak
for i in $(rpm -qa | grep openssl);do rpm -e $i --nodeps ;done 卸载原包
ln -s /usr/local/ssl/bin/openssl /usr/bin/openssl
ln -s /usr/local/ssl/lib/libssl.so.1.1 /usr/lib/libssl.so.1.1
ln -s /usr/local/ssl/lib/libcrypto.so.1.1 /usr/lib/libcrypto.so.1.1
echo '/usr/local/ssl/lib' >> /etc/ld.so.conf
ldconfig -v
4.openssh安装
备份原配置
mkdir /usr/bin/ssh_old_bk
cp -ar /usr/bin/ssh* /usr/bin/ssh_old_bk
cp -a /usr/sbin/sshd /usr/sbin/sshd_old_bk
mkdir /etc/ssh_old_bk
cp -ar /etc/ssh/* /etc/ssh_old_bk
cp /etc/init.d/sshd /etc/init.d/sshd_old_bk
cp /etc/pam.d/sshd /etc/pam.d/sshd._old_bk
cp /etc/sysconfig/sshd /etc/sysconfig/sshd_old_bk
cp /usr/lib/systemd/system/sshd.service /usr/lib/systemd/system/sshd.service_old_bk
安装openssh
tar -zxvf openssh-9.2p1.tar.gz
cd openssh-9.2p1
./configure --prefix=/usr/local/openssh --with-zlib=/usr/local/zlib --with-ssl-dir=/usr/local/ssl
make && make install
make clean
for i in $(rpm -qa |grep openssh);do rpm -e $i --nodeps ;done 卸载原包
复制配置
cp -ar /usr/local/openssh/bin/* /usr/bin/
cp -a /usr/local/openssh/sbin/sshd /usr/sbin/sshd
mkdir /etc/ssh
cp -a /usr/local/openssh/etc/ssh_host_ecdsa_key.pub /etc/ssh/ssh_host_ecdsa_key.pub
cp -a /usr/openssh-9.2p1/contrib/redhat/sshd.init /etc/init.d/sshd
cp -a /usr/openssh-9.2p1/contrib/redhat/sshd.pam /etc/pam.d/sshd
chmod +x /etc/init.d/sshd
配置sshd_config
echo 'PermitRootLogin yes' >>/usr/local/openssh/etc/sshd_config
echo 'PasswordAuthentication yes' >>/usr/local/openssh/etc/sshd_config
运行服务
systemctl daemon-reload
systemctl enable sshd.service
systemctl start sshd.service
ssh -V
升级后xshell5远程连接提示:找不到匹配的host key算法,此时升级到xshell7可以了
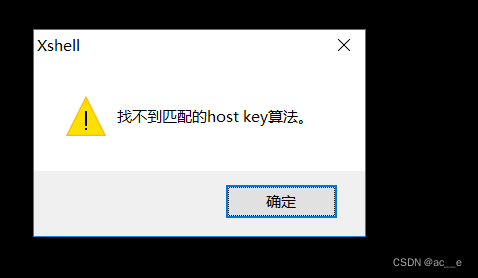
恢复版本openssh-7.4p1-21,提前下载原版本包:
删除zlib
rm -rf /usr/local/zlib
rpm -qa | grep zlib
openssl恢复
rpm -ivh --nodeps penssl-1.0.2k-19.el7.x86_64.rpm
mv /usr/bin/openssl.bak /usr/bin/openssl
cp -a libssl.so.1.0.2k /usr/lib64
cp -a libcrypto.so.1.0.2k /usr/lib64
ls -n libssl.so.1.0.2k libssl.so.10
ls -n libcrypto.so.1.0.2k libcrypto.so.10
rm -rf /usr/lib/libssl.so.1.1
rm -rf /usr/lib/libcrypto.so.1.1
vim /etc/ld.so.conf
ldconfig -v
rm -rf /usr/local/ssl
openssl version
openssh恢复
rpm -ivh --nodeps openssh-7.4p1-21.el7.x86_64.rpm
cp -ar /usr/bin/ssh_old_bk/ssh* /usr/bin/
mv /usr/sbin/sshd_old_bk /usr/sbin/sshd
cp -ar /etc/ssh_old_bk/* /etc/ssh/
mv /etc/init.d/sshd_old_bk /etc/init.d/sshd
chmod +x /etc/init.d/sshd
mv /etc/pam.d/sshd._old_bk /etc/pam.d/sshd
mv /etc/sysconfig/sshd_old_bk /etc/sysconfig/sshd
mv /usr/lib/systemd/system/sshd.service_old_bk /usr/lib/systemd/system/sshd.service
rm -rf /usr/local/openssh
重启服务
service sshd restart
恢复可能报错解决:
1.秘钥文件损坏
ssh-keygen -t rsa -f /etc/ssh/ssh_host_rsa_key
ssh-keygen -t ecdsa -f /etc/ssh/ssh_host_ecdsa_key
ssh-keygen -t ed25519 -f /etc/ssh/ssh_host_ed25519_key
2.
sshd -t 提示/var/empty报错
chown -R root.root /var/empty/sshd #将文件所述用户调整为root用户
chmod 744 /var/empty/sshd #调整文件权限
service sshd restart
ssh -V
3.账户名密码输入正确,sshd配置文件没错,就是提示Permission denied, please try again,可能是/etc/pam/下缺少sshd文件,复制一份就好了
参考链接:
https://blog.csdn.net/s619782146/article/details/125533781
https://www.cnblogs.com/yangweiting/articles/17061915.html




