- 1【大厂AI课学习笔记】【2.2机器学习开发任务实例】(8)模型训练
- 2微服务学习 | Spring Cloud 中使用 Sentinel 实现服务限流_sentinel的client单机限流
- 3计算机视觉基础知识(十三)--推理和训练
- 4深度学习疆界:探索基本原理与算法,揭秘应用力量,展望未来发展与智能交互的新纪元
- 5python文本分类特征选择_文本分类特征选择方法
- 6Unity API - A_unity animation 的 add loop frame
- 7docker 获取Nvidia 镜像 | cuda |cudnn_docker获取nvidia镜像
- 8Prometheus监控K8S
- 9PCL ICP算法实现点云配准(C++详细过程版)_c++ pcl点云配准融合
- 105月书讯 | 《这就是ChatGPT》来了!
【华为_安全】防火墙IPsec双机实验_华为ensp ipsec 双机热备
赞
踩
【华为_安全】防火墙IPsec双机实验
- 1. 前言
- 2. 拓扑
- 3. 需求
- 4. 解法
- 4.1 思路
- 总部
- IP-Link
- 双机热备
- IPsec
- 路由部署
- 分公司(Fw3 动态公网IP)
- IPsec
- IP-Link
- 路由部署
- 4.2 参考命令
- Fw1
- Fw2
- Fw3
- Fw4
- ISP1
- ISP2
- ISP3
- ISP4
- NAT-Device
- 4.3 故障测试
- FW1正常时
- PC1测试
- isp1链路故障模拟
- 关闭ISP1接口
- Fw1成为备墙
- Fw2成为主墙
- PC1测试
- isp1链路故障恢复
- 恢复ISP1接口
- Fw1成为主墙
- Fw2成为备墙
- PC1测试
- 4.4 流量走向诉求描述
1. 前言
学习华为防火墙IPsec双机实验记录
防火墙登录账号都为admin
密码为Huawei@123
2. 拓扑
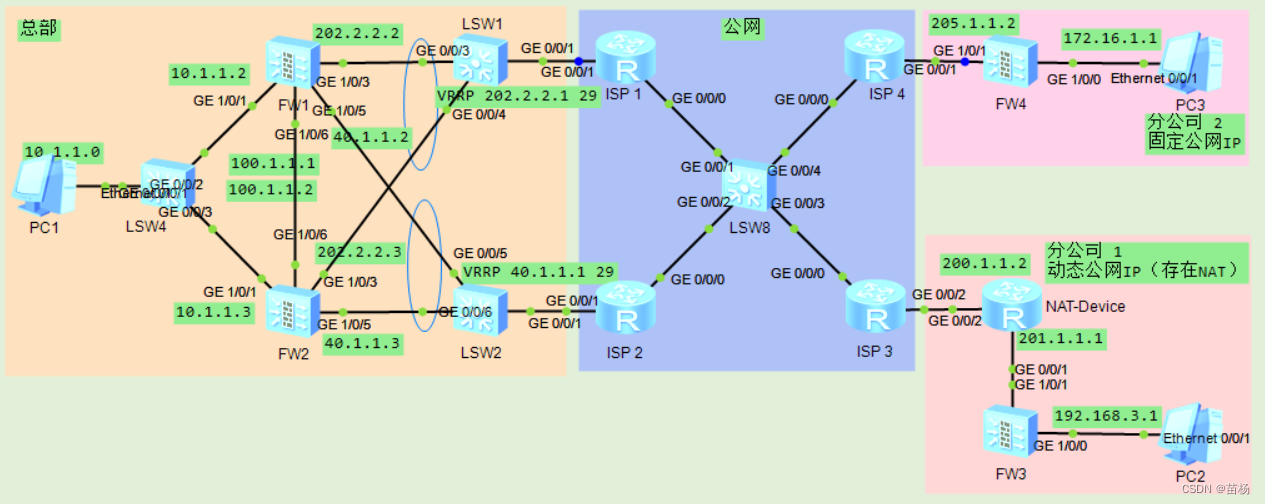
总部:
两台防火墙 采用双机部署,分别连接到ISP1、ISP2
总部两台防火墙的 ISP1 出口是 G0/0/3,连接 ISP2 的出口是 G0/0/5,缺省情况下,流量走 FW1 的 G0/0/3 接口
两台防火墙 作为内网用户的上网网关
两台防火墙 需要基于双机双出口与两个分公司分别建立 IPSec VPN。
分公司1:
路由器NAT-Device作为NAT设备,连接到ISP3
出口防火墙Fw3作为内网用户的上网网关,以及与总部对接IPSec VPN。
分公司2:
出口防火墙Fw4连接到ISP4,作为内网用户的上网网关,以及与总部对接IPSec VPN。
3. 需求
链路故障:
- FW1
连接 ISP1 链路故障,但是 ISP1 未故障,流量走 FW2 的 G0/0/3;- FW1 连接 ISP1 链路未故障,但是
ISP1 故障,流量走 FW2 的 G0/0/5;- FW1
连接 ISP1 链路恢复,ISP1 恢复,流量走 FW1 的 G0/0/3;
设备故障:
- FW1 正常情况下,流量走 FW1 的 G0/0/3;
- FW1 设备故障,流量走 FW2 的 G0/0/3;
- FW1 及 ISP1 设备故障,流量走 FW2 的 G0/0/5
4. 解法
4.1 思路
总部
IP-Link
- 在Fw1、Fw2上开启IP-Link探测功能,探测连接到IPS1的网络,当ISP1网络发生故障,可以及时发现故障。
双机热备
-
在Fw1、Fw2配置双机热备,采用主备备份模式,Fw1作为主设备、Fw2作为备设备。同时配置VGMP组监控接口和IP-Link状态,确保在遇到故障的时候实现快速切换。
- 配置VGMP组监控连接到ISP1、ISP2、内网的接口
- 配置VGMP组监控连接到ISP1的网络,即关联上一步的IP-Link
-
在Fw1、Fw2配置部署VRRP备份组:
- Fw1、Fw2连接到ISP1的接口加入到同一VRRP备份组中,虚拟IP地址配置为ISP1的公网地址,同时启用虚拟MAC地址功能。
- Fw1、Fw2连接到ISP2的接口加入到同一VRRP备份组中,虚拟IP地址配置为ISP2的公网地址,同时启用虚拟MAC地址功能。
- Fw1、Fw2连接到内网的接口加入到同一VRRP备份组中,虚拟IP地址配置为内网网关地址,同时启用虚拟MAC地址功能。
- 因为F1作为主设备,所以Fw1的VRRP备份组的状态都设置为active。
- 因为F2作为备设备,所以Fw2的VRRP备份组的状态都设置为standby。
IPsec
- 总部对接IPSec VPN的分公司,存在对端为 非固定公网IP和固定公网IP的情况,所以总部对接非固定公网IP的Fw3采用IPSec策略模板方式,对接固定公网IP的Fw4采用IPSec策略方式。
- 根据总部和分部需要互访的流量,使用高级ACL定义 需要 受IPSec VPN保护 的感兴趣流。
- 配置IKE提议、IPSec提议,根据用户需求配置安全参数,确保两端参数一致。
- 配置针对Fw3的IKE Peer。使用预共享密钥进行认证,引用IKE提议,由于对端为非固定公网IP,无需配置对端IP地址,但是需要开启NAT穿越功能。
- 配置针对Fw4的IKE Peer。使用预共享密钥进行认证,引用IKE提议,配置对端IP地址。
- 配置针对Fw3的IPsec策略模板。引用感兴趣流、IPSec提议、Fw3的IKE Peer,配置本端地址。
- 配置针对从ISP1和ISP2到达Fw4的2个IPsec策略。引用感兴趣流、IPSec提议、Fw4的IKE Peer,配置本端地址、对端地址。
- 将IPsec策略模板引用到2个IPsec策略中。切记 IPsec策略模板 的序列号 一定要大于 IPsec策略 的序列号。
- 分别在两个出接口调用对应的IPsec策略。
- 由于配置了双机热备,只需在主墙配置,配置会自动同步到备墙。
路由部署
- 根据需求,需要配置两条缺省路由,一主一备:
- 主路由为去往ISP1,并绑定IP-Link “to_isp1”,实现ISP1故障时的路由快速切换。
- 备路由为去往ISP2。
分公司(Fw3 动态公网IP)
IPsec
- 根据总部和分部需要互访的流量,使用高级ACL定义 需要 受IPSec VPN保护 的感兴趣流。
- 配置IKE提议、IPSec提议,根据用户需求配置安全参数,确保两端参数一致。
- 配置针对总部ISP1和ISP2的两个IKE Peer。使用预共享密钥进行认证(需要与总部一致),引用IKE提议,由于本端为非固定公网IP,需要开启NAT穿越功能。在ISP1的IKE Peer中,对端IP地址为总部连接到ISP1的VRRP备份组虚拟IP地址;在ISP2的IKE Peer中,对端IP地址为总部连接到ISP2的VRRP备份组虚拟IP地址。
- 配置针对总部ISP1和ISP2的两个IPsec策略。引用感兴趣流、IPSec提议。对接总部ISP1的IPsec策略中,调用ISP1的IKE Peer;对接总部ISP2的IPsec策略中,调用ISP2的IKE Peer。
- 配置两个tunnel接口,分别为tunnel1和tunnel2,加入到与外网侧物理接口相同的安全区域中,协议类型为IPSec,同时借用外网侧接口的IP地址。Tunnel1作为主隧道,调用对接总部ISP1的IPsec策略;Tunnel2作为备隧道,调用对接总部ISP2的IPsec策略
IP-Link
- 在Fw3上开启IP-Link探测功能,探测 总部 连接到ISP1 所在的 VRRP备份组虚拟IP地址,当发生故障时,可以及时发现故障。
路由部署
- 配置一条到达运营商的缺省路由。
- 配置两条到达 总部内部网络 的路由,一主一备:
- 主路由:下一跳指向Tunnel1,并绑定IP-Link“to_ZongBu_isp1”,实现总部ISP1故障时的路由快速切换。
- 备路由:下一跳指向Tunnel2。
4.2 参考命令
Fw1
# sysname Fw1 # hrp enable hrp interface GigabitEthernet1/0/6 remote 100.1.1.2 hrp track interface GigabitEthernet1/0/1 hrp track interface GigabitEthernet1/0/3 hrp track interface GigabitEthernet1/0/5 hrp track ip-link to_isp1 # ip-link check enable ip-link name to_isp1 destination 202.2.2.6 interface GigabitEthernet1/0/3 mode icmp next-hop 202.2.2.6 # acl number 3000 rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 172.16.1.0 0.0.0.255 acl number 3001 rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 192.168.3.0 0.0.0.255 # ipsec proposal 1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256 # ike proposal 1 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # ike peer to_fw4 pre-shared-key Huawei@123 ike-proposal 1 remote-address 205.1.1.2 ike peer to_fw3 pre-shared-key Huawei@123 ike-proposal 1 dpd type periodic dpd idle-time 10 dpd retransmit-interval 2 # ipsec policy-template FenBu 10 security acl 3001 ike-peer to_fw3 proposal 1 # ipsec policy POLICY_1 5 isakmp security acl 3000 ike-peer to_fw4 proposal 1 tunnel local 202.2.2.1 ipsec policy POLICY_1 50 isakmp template FenBu ipsec policy POLICY_2 5 isakmp security acl 3000 ike-peer to_fw4 proposal 1 tunnel local 40.1.1.1 sa trigger-mode auto ipsec policy POLICY_2 50 isakmp template FenBu # interface GigabitEthernet1/0/1 ip address 10.1.1.2 255.255.255.0 vrrp vrid 3 virtual-ip 10.1.1.254 active vrrp virtual-mac enable link-group 1 service-manage ping permit dhcp select interface # interface GigabitEthernet1/0/3 ip address 202.2.2.2 255.255.255.248 vrrp vrid 1 virtual-ip 202.2.2.1 active vrrp virtual-mac enable link-group 1 service-manage ping permit ipsec policy POLICY_1 # interface GigabitEthernet1/0/5 ip address 40.1.1.2 255.255.255.248 vrrp vrid 2 virtual-ip 40.1.1.1 active vrrp virtual-mac enable link-group 1 service-manage ping permit ipsec policy POLICY_2 # interface GigabitEthernet1/0/6 ip address 100.1.1.1 255.255.255.0 service-manage ping permit # firewall zone trust set priority 85 add interface GigabitEthernet1/0/1 # firewall zone untrust set priority 5 # firewall zone dmz set priority 50 add interface GigabitEthernet1/0/6 # firewall zone name isp1 id 4 set priority 10 add interface GigabitEthernet1/0/3 # firewall zone name isp2 id 5 set priority 20 add interface GigabitEthernet1/0/5 # ip route-static 0.0.0.0 0.0.0.0 202.2.2.6 track ip-link to_isp1 ip route-static 0.0.0.0 0.0.0.0 40.1.1.6 preference 70 # security-policy rule name ipsec_ike source-zone isp1 source-zone isp2 source-zone local destination-zone isp1 destination-zone isp2 destination-zone local source-address 202.2.2.1 mask 255.255.255.255 source-address 205.1.1.2 mask 255.255.255.255 source-address 40.1.1.1 mask 255.255.255.255 destination-address 202.2.2.1 mask 255.255.255.255 destination-address 205.1.1.2 mask 255.255.255.255 destination-address 40.1.1.1 mask 255.255.255.255 service protocol udp source-port 500 destination-port 500 action permit rule name ipsec_office_FengGongSi_2 source-zone isp1 source-zone isp2 source-zone trust destination-zone isp1 destination-zone isp2 destination-zone trust source-address 10.1.1.0 mask 255.255.255.0 source-address 172.16.1.0 mask 255.255.255.0 destination-address 10.1.1.0 mask 255.255.255.0 destination-address 172.16.1.0 mask 255.255.255.0 action permit rule name ipsec_esp source-zone isp1 source-zone isp2 destination-zone local destination-address 202.2.2.1 mask 255.255.255.255 destination-address 40.1.1.1 mask 255.255.255.255 service esp action permit rule name ipsec_ike_ChanYue source-zone isp1 source-zone isp2 source-zone local destination-zone isp1 destination-zone isp2 destination-zone local service protocol udp destination-port 500 4500 action permit rule name icmp source-zone local service icmp action permit rule name to_internet source-zone trust destination-zone isp1 destination-zone isp2 source-address 10.1.1.0 mask 255.255.255.0 action permit rule name ipsec_office_FengGongSi_1 source-zone isp1 source-zone isp2 source-zone trust destination-zone isp1 destination-zone isp2 destination-zone trust source-address 10.1.1.0 mask 255.255.255.0 source-address 192.168.3.0 mask 255.255.255.0 destination-address 10.1.1.0 mask 255.255.255.0 destination-address 192.168.3.0 mask 255.255.255.0 action permit # nat-policy rule name no-nat source-zone trust destination-zone isp1 destination-zone isp2 source-address 10.1.1.0 mask 255.255.255.0 source-address 172.16.1.0 mask 255.255.255.0 source-address 192.168.3.0 mask 255.255.255.0 destination-address 10.1.1.0 mask 255.255.255.0 destination-address 172.16.1.0 mask 255.255.255.0 destination-address 192.168.3.0 mask 255.255.255.0 action no-nat rule name to_internet source-zone trust destination-zone isp1 destination-zone isp2 source-address 10.1.1.0 mask 255.255.255.0 action source-nat easy-ip #
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
- 166
- 167
- 168
- 169
- 170
- 171
- 172
- 173
- 174
- 175
- 176
- 177
- 178
- 179
- 180
- 181
- 182
- 183
- 184
- 185
- 186
- 187
- 188
- 189
- 190
- 191
- 192
- 193
- 194
- 195
- 196
- 197
- 198
- 199
- 200
- 201
- 202
- 203
- 204
- 205
- 206
Fw2
Fw2只配置基础命令,双机热备会同步配置
sys sys Fw2 interface GigabitEthernet1/0/3 ip address 202.2.2.3 255.255.255.248 vrrp vrid 1 virtual-ip 202.2.2.1 s vrrp virtual-mac enable service-manage ping permit interface GigabitEthernet1/0/5 ip address 40.1.1.3 255.255.255.248 vrrp vrid 2 virtual-ip 40.1.1.1 s vrrp virtual-mac enable service-manage ping permit interface GigabitEthernet1/0/6 ip add 100.1.1.2 24 service-manage ping permit dhcp enable interface GigabitEthernet1/0/1 undo shutdown ip address 10.1.1.3 255.255.255.0 vrrp vrid 3 virtual-ip 10.1.1.254 s vrrp virtual-mac enable service-manage ping permit dhcp select interface firewall zone trust add interface GigabitEthernet1/0/1 # firewall zone dmz set priority 50 add interface GigabitEthernet1/0/6 # firewall zone name isp1 id 4 add interface GigabitEthernet1/0/3 # firewall zone name isp2 id 5 add interface GigabitEthernet1/0/5 ipsec policy POLICY_1 5 isakmp security acl 3000 proposal 1 tunnel local 202.2.2.1 ipsec policy POLICY_2 5 isakmp security acl 3000 proposal 1 tunnel local 40.1.1.1 ip-link check enable ip-link name to_isp1 destination 202.2.2.6 interface GigabitEthernet1/0/3 mode icmp next-hop 202.2.2.6 ip route-static 0.0.0.0 0.0.0.0 202.2.2.6 track ip-link to_isp1 ip route-static 0.0.0.0 0.0.0.0 40.1.1.6 preference 70 hrp enable hrp interface GigabitEthernet1/0/6 remote 100.1.1.1
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
Fw3
sysname Fw3 # ip-link check enable ip-link name to_isp1 destination 202.2.2.1 interface GigabitEthernet1/0/1 mode icmp next-hop 201.1.1.1 # acl number 3000 rule 5 permit ip source 192.168.3.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 # ipsec proposal 1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256 # ike proposal 1 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # ike peer to_isp1 pre-shared-key Huawei@123 ike-proposal 1 dpd type periodic dpd idle-time 10 dpd retransmit-interval 2 remote-address 202.2.2.1 ike peer to_isp2 pre-shared-key Huawei@123 ike-proposal 1 dpd type periodic dpd idle-time 10 dpd retransmit-interval 2 remote-address 40.1.1.1 # ipsec policy POLICY_1 5 isakmp security acl 3000 ike-peer to_isp1 proposal 1 sa trigger-mode auto ipsec policy POLICY_2 5 isakmp security acl 3000 ike-peer to_isp2 proposal 1 sa trigger-mode auto # interface GigabitEthernet1/0/0 ip address 192.168.3.1 255.255.255.0 # interface GigabitEthernet1/0/1 undo shutdown ip address dhcp-alloc # interface Tunnel1 ip address unnumbered interface GigabitEthernet1/0/1 tunnel-protocol ipsec ipsec policy POLICY_1 # interface Tunnel2 ip address unnumbered interface GigabitEthernet1/0/1 tunnel-protocol ipsec ipsec policy POLICY_2 # firewall zone trust set priority 85 add interface GigabitEthernet1/0/0 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/1 add interface Tunnel1 add interface Tunnel2 # ip route-static 0.0.0.0 0.0.0.0 GigabitEthernet1/0/1 ip route-static 10.1.1.0 255.255.255.0 Tunnel1 track ip-link to_isp1 ip route-static 10.1.1.0 255.255.255.0 Tunnel2 preference 70 # security-policy rule name to_internet source-zone trust destination-zone untrust source-address 192.168.3.0 mask 255.255.255.0 action permit rule name ipsec_ike source-zone local source-zone untrust destination-zone local destination-zone untrust service protocol udp destination-port 500 4500 action permit rule name ipsec_office source-zone trust source-zone untrust destination-zone trust destination-zone untrust source-address 10.1.1.0 mask 255.255.255.0 source-address 192.168.3.0 mask 255.255.255.0 destination-address 10.1.1.0 mask 255.255.255.0 destination-address 192.168.3.0 mask 255.255.255.0 action permit rule name icmp source-zone local service icmp action permit # nat-policy rule name no-nat source-zone trust destination-zone untrust source-address 10.1.1.0 mask 255.255.255.0 source-address 192.16.3.0 mask 255.255.255.0 destination-address 10.1.1.0 mask 255.255.255.0 destination-address 192.16.3.0 mask 255.255.255.0 action no-nat rule name to_internet source-zone trust destination-zone untrust source-address 192.16.3.0 mask 255.255.255.0 action source-nat easy-ip
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
Fw4
sysname fw4 # acl number 3000 rule 5 permit ip source 172.16.1.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 # ipsec proposal 1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256 # ike proposal 1 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # ike peer to_isp1 pre-shared-key Huawei@123 ike-proposal 1 dpd type periodic dpd idle-time 10 dpd retransmit-interval 2 remote-address 202.2.2.1 ike peer to_isp2 pre-shared-key Huawei@123 ike-proposal 1 remote-address 40.1.1.1 # ipsec policy POLICY_1 5 isakmp security acl 3000 ike-peer to_isp1 proposal 1 ipsec policy POLICY_2 5 isakmp security acl 3000 ike-peer to_isp2 proposal 1 # interface GigabitEthernet1/0/0 undo shutdown ip address 172.16.1.1 255.255.255.0 service-manage ping permit # interface GigabitEthernet1/0/1 undo shutdown ip address 205.1.1.2 255.255.255.0 service-manage ping permit # interface Tunnel1 ip address unnumbered interface GigabitEthernet1/0/1 tunnel-protocol ipsec ipsec policy POLICY_1 # interface Tunnel2 ip address unnumbered interface GigabitEthernet1/0/1 tunnel-protocol ipsec ipsec policy POLICY_2 # firewall zone trust set priority 85 add interface GigabitEthernet1/0/0 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/1 add interface Tunnel1 add interface Tunnel2 # firewall zone dmz set priority 50 # ip route-static 0.0.0.0 0.0.0.0 205.1.1.1 # security-policy rule name to_internet source-zone trust destination-zone untrust source-address 172.16.1.0 mask 255.255.255.0 action permit rule name ipsec_ike source-zone local source-zone untrust destination-zone local destination-zone untrust source-address 202.2.2.1 mask 255.255.255.255 source-address 205.1.1.2 mask 255.255.255.255 source-address 40.1.1.1 mask 255.255.255.255 destination-address 202.2.2.1 mask 255.255.255.255 destination-address 205.1.1.2 mask 255.255.255.255 destination-address 40.1.1.1 mask 255.255.255.255 service protocol udp source-port 500 destination-port 500 action permit rule name ipsec_esp source-zone untrust destination-zone local source-address 202.2.2.1 mask 255.255.255.255 source-address 40.1.1.1 mask 255.255.255.255 destination-address 205.1.1.2 mask 255.255.255.255 service esp action permit rule name ipsec_office source-zone trust source-zone untrust destination-zone trust destination-zone untrust source-address 10.1.1.0 mask 255.255.255.0 source-address 172.16.1.0 mask 255.255.255.0 destination-address 10.1.1.0 mask 255.255.255.0 destination-address 172.16.1.0 mask 255.255.255.0 action permit
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
ISP1
sys
sys isp1
int g0/0/1
ip add 202.2.2.6 29
int g0/0/0
ip add 18.1.1.1 24
ospf 10 router-id 1.1.1.1
a 0
net 202.2.2.6 0.0.0.7
net 18.1.1.0 0.0.0.255
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
ISP2
sys
sys isp2
int g0/0/1
ip add 40.1.1.6 29
int g0/0/0
ip add 18.1.1.2 24
ospf 10 router-id 2.2.2.2
a 0
net 40.1.1.6 0.0.0.7
net 18.1.1.0 0.0.0.255
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
ISP3
sys
sys isp3
int g0/0/2
ip add 200.1.1.1 24
int g0/0/0
ip add 18.1.1.3 24
ospf 10 router-id 3.3.3.3
a 0
net 200.1.1.2 0.0.0.255
net 18.1.1.0 0.0.0.255
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
ISP4
sys
sys isp4
int g0/0/1
ip add 205.1.1.1 24
int g0/0/0
ip add 18.1.1.4 24
ospf 10 router-id 4.4.4.4
a 0
net 205.1.1.1 0.0.0.255
net 18.1.1.0 0.0.0.255
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
NAT-Device
sys sys NAT-Device acl number 2000 rule 5 permit source 201.1.1.0 0.0.0.255 dhcp en nat address-group 1 200.1.1.100 200.1.1.200 interface GigabitEthernet0/0/1 ip address 201.1.1.1 255.255.255.0 dhcp select interface interface GigabitEthernet0/0/2 ip address 200.1.1.2 255.255.255.0 nat outbound 2000 address-group 1 ip route-static 0.0.0.0 0.0.0.0 200.1.1.1
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
4.3 故障测试
FW1正常时
HRP_M[Fw1] HRP_M[Fw1]display ip routing-table 2023-12-08 03:33:19.840 Route Flags: R - relay, D - download to fib ------------------------------------------------------------------------------ Routing Tables: Public Destinations : 14 Routes : 14 Destination/Mask Proto Pre Cost Flags NextHop Interface 0.0.0.0/0 Static 60 0 RD 202.2.2.6 GigabitEthernet1/0/3 10.1.1.0/24 Direct 0 0 D 10.1.1.2 GigabitEthernet1/0/1 10.1.1.2/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/1 10.1.1.254/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/1 40.1.1.0/29 Direct 0 0 D 40.1.1.2 GigabitEthernet1/0/5 40.1.1.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/5 40.1.1.2/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/5 100.1.1.0/24 Direct 0 0 D 100.1.1.1 GigabitEthernet1/0/6 100.1.1.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/6 127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0 127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0 202.2.2.0/29 Direct 0 0 D 202.2.2.2 GigabitEthernet1/0/3 202.2.2.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/3 202.2.2.2/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/3 HRP_M[Fw1] HRP_M[Fw1]display vrrp brief 2023-12-08 03:28:56.630 Total:3 Master:3 Backup:0 Non-active:0 VRID State Interface Type Virtual IP ---------------------------------------------------------------- 1 Master GE1/0/3 Vgmp 202.2.2.1 2 Master GE1/0/5 Vgmp 40.1.1.1 3 Master GE1/0/1 Vgmp 10.1.1.254 HRP_M[Fw1] HRP_M[Fw1]display ike sa 2023-12-08 03:29:08.260 IKE SA information : Conn-ID Peer VPN Flag(s) Phase RemoteType RemoteID ------------------------------------------------------------------------------------------------------------------------------------ 33 200.1.1.198:65064 RD|M v2:2 IP 201.1.1.254 30 200.1.1.198:65064 RD|M v2:1 IP 201.1.1.254 44 205.1.1.2:500 RD|ST|M v2:2 IP 205.1.1.2 39 205.1.1.2:500 RD|ST|M v2:1 IP 205.1.1.2 32 200.1.1.198:64552 RD|M v2:2 IP 201.1.1.254 31 200.1.1.198:64552 RD|M v2:1 IP 201.1.1.254 43 205.1.1.2:500 RD|M v2:2 IP 205.1.1.2 41 205.1.1.2:500 RD|M v2:1 IP 205.1.1.2 Number of IKE SA : 8 ------------------------------------------------------------------------------------------------------------------------------------ Flag Description: RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP M--ACTIVE S--STANDBY A--ALONE NEG--NEGOTIATING HRP_M[Fw1] HRP_M[Fw1]display ipsec sa brief 2023-12-08 03:29:26.490 IPSec SA information: Src address Dst address SPI VPN Protocol Algorithm -------------------------------------------------------------------------------------------------------------------------- 202.2.2.1 200.1.1.198 196662029 ESP E:AES-256 A:SHA2_256_128 40.1.1.1 200.1.1.198 194138009 ESP E:AES-256 A:SHA2_256_128 40.1.1.1 205.1.1.2 200362542 ESP E:AES-256 A:SHA2_256_128 200.1.1.198 202.2.2.1 194760684 ESP E:AES-256 A:SHA2_256_128 205.1.1.2 40.1.1.1 185700354 ESP E:AES-256 A:SHA2_256_128 202.2.2.1 205.1.1.2 197910612 ESP E:AES-256 A:SHA2_256_128 205.1.1.2 202.2.2.1 190270246 ESP E:AES-256 A:SHA2_256_128 200.1.1.198 40.1.1.1 194466263 ESP E:AES-256 A:SHA2_256_128 Number of IPSec SA : 8 -------------------------------------------------------------------------------------------------------------------------- HRP_M[Fw1] HRP_M[Fw1]
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
PC1测试
PC> PC>ping 172.16.1.10 Ping 172.16.1.10: 32 data bytes, Press Ctrl_C to break Request timeout! Request timeout! From 172.16.1.10: bytes=32 seq=3 ttl=126 time=94 ms From 172.16.1.10: bytes=32 seq=4 ttl=126 time=78 ms From 172.16.1.10: bytes=32 seq=5 ttl=126 time=78 ms --- 172.16.1.10 ping statistics --- 5 packet(s) transmitted 3 packet(s) received 40.00% packet loss round-trip min/avg/max = 0/83/94 ms PC> PC> PC>ping 192.168.3.10 Ping 192.168.3.10: 32 data bytes, Press Ctrl_C to break Request timeout! From 192.168.3.10: bytes=32 seq=2 ttl=126 time=78 ms From 192.168.3.10: bytes=32 seq=3 ttl=126 time=109 ms From 192.168.3.10: bytes=32 seq=4 ttl=126 time=78 ms From 192.168.3.10: bytes=32 seq=5 ttl=126 time=79 ms --- 192.168.3.10 ping statistics --- 5 packet(s) transmitted 4 packet(s) received 20.00% packet loss round-trip min/avg/max = 0/86/109 ms PC>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
isp1链路故障模拟
关闭ISP1接口
[isp1-GigabitEthernet0/0/1]shutdown
- 1
Fw1成为备墙
HRP_M[Fw1]
HRP_M[Fw1]
Dec 8 2023 03:34:52 Fw1 %%01HEALTHCHECK/4/DOWN(l)[93]:Detect changed status to down (Protocol=icmp,DestinationIp=202.2.2.6,DestinationPort=0).
Dec 8 2023 03:34:52 Fw1 %%01HRPI/4/PRIORITY_CHANGE(l)[94]:The priority of the local VGMP group changed. (change_reason="The IP-link went Down.", local_old_priority=45000, local_new_priority=44998)
Dec 8 2023 03:34:52 Fw1 %%01HEALTHCHECK/3/DOWN(l)[95]:IP-Link to_isp1 changed status to down (Protocol=icmp,DestinationIp=202.2.2.6,DestinationPort=0).
Dec 8 2023 03:34:52 Fw1 HEALTHCHECK/2/DOWN:OID 1.3.6.1.4.1.2011.6.122.45.2.2 IP-link to_isp1 changes status to down.
Dec 8 2023 03:34:52 Fw1 HRPI/1/CORE_STATE:1.3.6.1.4.1.2011.6.122.51.2.2.1 The HRP core state changed due to "Ip-link change to Down". (old_state=normal,new_state=abnormal(standby), local_priority=44998, peer_priority=45000)
Dec 8 2023 03:34:52 Fw1 %%01RM/4/IPV4_DEFT_RT_CHG(l)[96]:IPV4 default Route is changed. (ChangeType=Delete, InstanceId=0, Protocol=Static, ExitIf=GigabitEthernet1/0/3, Nexthop=202.2.2.6, Neighbour=0.0.0.0, Preference=60, Label=NULL, Metric=0)
Dec 8 2023 03:34:52 Fw1 %%01RM/4/IPV4_DEFT_RT_CHG(l)[97]:IPV4 default Route is changed. (ChangeType=Add, InstanceId=0, Protocol=Static, ExitIf=GigabitEthernet1/0/5, Nexthop=40.1.1.6, Neighbour=0.0.0.0, Preference=70, Label=NULL, Metric=0)
Dec 8 2023 03:34:52 Fw1 %%01HRPI/4/CORE_STATE(l)[98]:The HRP core state changed due to "Ip-link change to Down". (old_state=normal, new_state=abnormal(standby), local_priority=44998, peer_priority=45000)
HRP_S[Fw1]
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
Fw2成为主墙
HRP_M<Fw2> HRP_M<Fw2>display ip routing-table 2023-12-08 03:35:47.240 Route Flags: R - relay, D - download to fib ------------------------------------------------------------------------------ Routing Tables: Public Destinations : 14 Routes : 14 Destination/Mask Proto Pre Cost Flags NextHop Interface 0.0.0.0/0 Static 70 0 RD 40.1.1.6 GigabitEthernet1/0/5 10.1.1.0/24 Direct 0 0 D 10.1.1.3 GigabitEthernet1/0/1 10.1.1.3/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/1 10.1.1.254/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/1 40.1.1.0/29 Direct 0 0 D 40.1.1.3 GigabitEthernet1/0/5 40.1.1.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/5 40.1.1.3/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/5 100.1.1.0/24 Direct 0 0 D 100.1.1.2 GigabitEthernet1/0/6 100.1.1.2/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/6 127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0 127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0 202.2.2.0/29 Direct 0 0 D 202.2.2.3 GigabitEthernet1/0/3 202.2.2.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/3 202.2.2.3/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/3 HRP_M<Fw2> HRP_M<Fw2>display ip-link 2023-12-08 03:35:52.990 Current Total Ip-link Number : 1 Name Member State Up/Down/Init to_isp1 1 down 0 1 0 HRP_M<Fw2> HRP_M<Fw2>display ike sa 2023-12-08 03:36:00.940 IKE SA information : Conn-ID Peer VPN Flag(s) Phase RemoteType RemoteID ------------------------------------------------------------------------------------------------------------------------------------ 22 200.1.1.198:64552 RD|M v2:2 IP 201.1.1.254 21 200.1.1.198:64552 RD|M v2:1 IP 201.1.1.254 20 205.1.1.2:500 RD|ST|M v2:2 IP 205.1.1.2 19 205.1.1.2:500 RD|ST|M v2:1 IP 205.1.1.2 18 205.1.1.2:500 RD|M v2:2 IP 205.1.1.2 17 205.1.1.2:500 RD|M v2:1 IP 205.1.1.2 Number of IKE SA : 6 ------------------------------------------------------------------------------------------------------------------------------------ Flag Description: RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP M--ACTIVE S--STANDBY A--ALONE NEG--NEGOTIATING HRP_M<Fw2> HRP_M<Fw2> HRP_M<Fw2>display vrrp brief 2023-12-08 03:36:23.660 Total:3 Master:3 Backup:0 Non-active:0 VRID State Interface Type Virtual IP ---------------------------------------------------------------- 1 Master GE1/0/3 Vgmp 202.2.2.1 2 Master GE1/0/5 Vgmp 40.1.1.1 3 Master GE1/0/1 Vgmp 10.1.1.254 HRP_M<Fw2> HRP_M<Fw2> HRP_M<Fw2>display ipsec sa brief 2023-12-08 03:36:09.140 IPSec SA information: Src address Dst address SPI VPN Protocol Algorithm -------------------------------------------------------------------------------------------------------------------------- 40.1.1.1 200.1.1.198 196406332 ESP E:AES-256 A:SHA2_256_128 40.1.1.1 205.1.1.2 200362542 ESP E:AES-256 A:SHA2_256_128 205.1.1.2 40.1.1.1 185700354 ESP E:AES-256 A:SHA2_256_128 202.2.2.1 205.1.1.2 197910612 ESP E:AES-256 A:SHA2_256_128 205.1.1.2 202.2.2.1 190270246 ESP E:AES-256 A:SHA2_256_128 200.1.1.198 40.1.1.1 200558179 ESP E:AES-256 A:SHA2_256_128 Number of IPSec SA : 6 -------------------------------------------------------------------------------------------------------------------------- HRP_M<Fw2> HRP_M<Fw2>display hrp state 2023-12-08 03:36:41.460 Role: active, peer: standby (should be "standby-active") Running priority: 45000, peer: 44998 Backup channel usage: 0.00% Stable time: 0 days, 0 hours, 3 minutes Last state change information: 2023-12-08 3:33:36 HRP core state changed, old_state = normal, new_state = abnormal(active), local_priority = 45000, peer_priority = 44998. HRP_M<Fw2> HRP_M<Fw2>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
PC1测试
PC> PC>ping 172.16.1.10 Ping 172.16.1.10: 32 data bytes, Press Ctrl_C to break Request timeout! From 172.16.1.10: bytes=32 seq=2 ttl=126 time=94 ms From 172.16.1.10: bytes=32 seq=3 ttl=126 time=94 ms From 172.16.1.10: bytes=32 seq=4 ttl=126 time=78 ms From 172.16.1.10: bytes=32 seq=5 ttl=126 time=94 ms --- 172.16.1.10 ping statistics --- 5 packet(s) transmitted 4 packet(s) received 20.00% packet loss round-trip min/avg/max = 0/90/94 ms PC> PC>ping 192.168.3.10 Ping 192.168.3.10: 32 data bytes, Press Ctrl_C to break Request timeout! From 192.168.3.10: bytes=32 seq=2 ttl=126 time=125 ms From 192.168.3.10: bytes=32 seq=3 ttl=126 time=110 ms From 192.168.3.10: bytes=32 seq=4 ttl=126 time=78 ms From 192.168.3.10: bytes=32 seq=5 ttl=126 time=93 ms --- 192.168.3.10 ping statistics --- 5 packet(s) transmitted 4 packet(s) received 20.00% packet loss round-trip min/avg/max = 0/101/125 ms PC>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
isp1链路故障恢复
恢复ISP1接口
[isp1-GigabitEthernet0/0/1]undo shutdown
- 1
Fw1成为主墙
HRP_S[Fw1] HRP_S[Fw1] Dec 8 2023 03:43:22 Fw1 %%01HRPI/4/PRIORITY_CHANGE(l)[99]:The priority of the local VGMP group changed. (change_reason="The IP-link went Up.", local_old_priority=44998, local_new_priority=45000) Dec 8 2023 03:43:22 Fw1 HEALTHCHECK/6/UP:OID 1.3.6.1.4.1.2011.6.122.45.2.1 IP-link to_isp1 changes status to up. Dec 8 2023 03:43:22 Fw1 %%01RM/4/IPV4_DEFT_RT_CHG(l)[100]:IPV4 default Route is changed. (ChangeType=Add, InstanceId=0, Protocol=Static, ExitIf=GigabitEthernet1/0/3, Nexthop=202.2.2.6, Neighbour=0.0.0.0, Preference=60, Label=NULL, Metric=0) Dec 8 2023 03:43:22 Fw1 %%01RM/4/IPV4_DEFT_RT_CHG(l)[101]:IPV4 default Route is changed. (ChangeType=Delete, InstanceId=0, Protocol=Static, ExitIf=GigabitEthernet1/0/5, Nexthop=40.1.1.6, Neighbour=0.0.0.0, Preference=70, Label=NULL, Metric=0) HRP_S[Fw1] Dec 8 2023 03:44:23 Fw1 HRPI/1/CORE_STATE:1.3.6.1.4.1.2011.6.122.51.2.2.1 The HRP core state changed due to "Ip-link change to UP". (old_state=abnormal(standby),new_state=normal, local_priority=45000, peer_priority=45000) Dec 8 2023 03:44:23 Fw1 %%01HRPI/4/CORE_STATE(l)[102]:The HRP core state changed due to "Ip-link change to UP". (old_state=abnormal(standby), new_state=normal, local_priority=45000, peer_priority=45000) HRP_M[Fw1] HRP_M[Fw1] HRP_M<Fw1> HRP_M<Fw1> HRP_M<Fw1>display ip routing-table 2023-12-08 04:49:14.320 Route Flags: R - relay, D - download to fib ------------------------------------------------------------------------------ Routing Tables: Public Destinations : 14 Routes : 14 Destination/Mask Proto Pre Cost Flags NextHop Interface 0.0.0.0/0 Static 60 0 RD 202.2.2.6 GigabitEthernet1/0/3 10.1.1.0/24 Direct 0 0 D 10.1.1.2 GigabitEthernet1/0/1 10.1.1.2/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/1 10.1.1.254/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/1 40.1.1.0/29 Direct 0 0 D 40.1.1.2 GigabitEthernet1/0/5 40.1.1.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/5 40.1.1.2/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/5 100.1.1.0/24 Direct 0 0 D 100.1.1.1 GigabitEthernet1/0/6 100.1.1.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/6 127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0 127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0 202.2.2.0/29 Direct 0 0 D 202.2.2.2 GigabitEthernet1/0/3 202.2.2.1/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/3 202.2.2.2/32 Direct 0 0 D 127.0.0.1 GigabitEthernet1/0/3 HRP_M<Fw1> HRP_M<Fw1>display ip-link 2023-12-08 04:49:19.270 Current Total Ip-link Number : 1 Name Member State Up/Down/Init to_isp1 1 up 1 0 0 HRP_M<Fw1> HRP_M<Fw1>display vrrp brief 2023-12-08 04:49:22.630 Total:3 Master:3 Backup:0 Non-active:0 VRID State Interface Type Virtual IP ---------------------------------------------------------------- 1 Master GE1/0/3 Vgmp 202.2.2.1 2 Master GE1/0/5 Vgmp 40.1.1.1 3 Master GE1/0/1 Vgmp 10.1.1.254 HRP_M<Fw1> HRP_M<Fw1> HRP_M<Fw1>dis HRP_M<Fw1>display ike sa 2023-12-08 04:49:26.730 IKE SA information : Conn-ID Peer VPN Flag(s) Phase RemoteType RemoteID ------------------------------------------------------------------------------------------------------------------------------------ 54 200.1.1.198:23849 RD|ST|M v2:2 IP 201.1.1.254 47 200.1.1.198:23849 RD|M v2:1 IP 201.1.1.254 52 200.1.1.198:64552 RD|ST|M v2:2 IP 201.1.1.254 45 200.1.1.198:64552 RD|M v2:1 IP 201.1.1.254 51 205.1.1.2:500 RD|ST|M v2:2 IP 205.1.1.2 39 205.1.1.2:500 RD|ST|M v2:1 IP 205.1.1.2 53 205.1.1.2:500 RD|ST|M v2:2 IP 205.1.1.2 49 205.1.1.2:500 RD|M v2:1 IP 205.1.1.2 Number of IKE SA : 8 ------------------------------------------------------------------------------------------------------------------------------------ Flag Description: RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP M--ACTIVE S--STANDBY A--ALONE NEG--NEGOTIATING HRP_M<Fw1> HRP_M<Fw1> HRP_M<Fw1>display ipsec sa brief 2023-12-08 04:49:45.770 IPSec SA information: Src address Dst address SPI VPN Protocol Algorithm -------------------------------------------------------------------------------------------------------------------------- 40.1.1.1 205.1.1.2 185561417 ESP E:AES-256 A:SHA2_256_128 202.2.2.1 200.1.1.198 189671080 ESP E:AES-256 A:SHA2_256_128 40.1.1.1 200.1.1.198 184812195 ESP E:AES-256 A:SHA2_256_128 205.1.1.2 40.1.1.1 199431858 ESP E:AES-256 A:SHA2_256_128 200.1.1.198 202.2.2.1 198882347 ESP E:AES-256 A:SHA2_256_128 200.1.1.198 40.1.1.1 199012368 ESP E:AES-256 A:SHA2_256_128 205.1.1.2 202.2.2.1 195484779 ESP E:AES-256 A:SHA2_256_128 202.2.2.1 205.1.1.2 194413064 ESP E:AES-256 A:SHA2_256_128 Number of IPSec SA : 8 -------------------------------------------------------------------------------------------------------------------------- HRP_M<Fw1> HRP_M<Fw1>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
Fw2成为备墙
HRP_M<Fw2>
HRP_M<Fw2>
Dec 8 2023 03:42:09 Fw2 HEALTHCHECK/6/UP:OID 1.3.6.1.4.1.2011.6.122.45.2.1 IP-link to_isp1 changes status to up.
Dec 8 2023 03:42:09 Fw2 %%01RM/4/IPV4_DEFT_RT_CHG(l)[1]:IPV4 default Route is changed. (ChangeType=Add, InstanceId=0, Protocol=Static, ExitIf=GigabitEthernet1/0/3, Nexthop=202.2.2.6, Neighbour=0.0.0.0, Preference=60, Label=NULL, Metric=0)
Dec 8 2023 03:42:09 Fw2 %%01RM/4/IPV4_DEFT_RT_CHG(l)[2]:IPV4 default Route is changed. (ChangeType=Delete, InstanceId=0, Protocol=Static, ExitIf=GigabitEthernet1/0/5, Nexthop=40.1.1.6, Neighbour=0.0.0.0, Preference=70, Label=NULL, Metric=0)
HRP_M<Fw2>
HRP_M<Fw2>
HRP_M<Fw2>
HRP_M<Fw2>
HRP_M<Fw2>
HRP_M<Fw2>
Dec 8 2023 03:43:07 Fw2 HRPI/1/CORE_STATE:1.3.6.1.4.1.2011.6.122.51.2.2.1 The HRP core state changed due to "Unknown". (old_state=abnormal(active),new_state=normal, local_priority=45000, peer_priority=45000)
Dec 8 2023 03:43:07 Fw2 %%01HRPI/4/CORE_STATE(l)[3]:The HRP core state changed due to "Unknown". (old_state=abnormal(active), new_state=normal, local_priority=45000, peer_priority=45000)
HRP_S<Fw2>
HRP_S<Fw2>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
PC1测试
PC> PC>ping 192.168.3.10 Ping 192.168.3.10: 32 data bytes, Press Ctrl_C to break From 192.168.3.10: bytes=32 seq=1 ttl=126 time=93 ms From 192.168.3.10: bytes=32 seq=2 ttl=126 time=63 ms From 192.168.3.10: bytes=32 seq=3 ttl=126 time=94 ms From 192.168.3.10: bytes=32 seq=4 ttl=126 time=110 ms From 192.168.3.10: bytes=32 seq=5 ttl=126 time=94 ms --- 192.168.3.10 ping statistics --- 5 packet(s) transmitted 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 63/90/110 ms PC> PC> PC>ping 172.16.1.10 Ping 172.16.1.10: 32 data bytes, Press Ctrl_C to break Request timeout! From 172.16.1.10: bytes=32 seq=2 ttl=126 time=109 ms From 172.16.1.10: bytes=32 seq=3 ttl=126 time=63 ms From 172.16.1.10: bytes=32 seq=4 ttl=126 time=93 ms From 172.16.1.10: bytes=32 seq=5 ttl=126 time=94 ms --- 172.16.1.10 ping statistics --- 5 packet(s) transmitted 4 packet(s) received 20.00% packet loss round-trip min/avg/max = 0/89/109 ms PC>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
4.4 流量走向诉求描述
-
当FW1 连接 ISP1 链路故障 或者 设备故障,但是 ISP1 未故障。可以通过VRRP感知故障,并联动双机热备 触发防火墙主备切换,即Fw2成为主墙。此时FW2上 主用缺省路由 绑定的 ip-link isp1并未感知ISP1网络出现故障,流量通过去往ISP1的G0/0/3口转发,且通过双机热备技术 同步状态会话表项,保证业务不中断。
-
当FW1 连接 ISP1 链路未故障,但是 ISP1 故障。可以通过IP-Link感知故障,并联动双机热备 触发防火墙主备切换,即Fw2成为主墙。此时FW2上 主用缺省路由 绑定的 ip-link isp1感知ISP1网络出现故障,流量通过去往ISP2的G0/0/5口转发,且通过双机热备技术 同步状态会话表项,保证业务不中断。
-
当FW1 设备故障,但是 ISP1 故障。可以通过VRRP感知故障,并联动双机热备 触发防火墙主备切换,即Fw2成为主墙。此时FW2上 主用缺省路由 绑定的 ip-link isp1感知ISP1网络出现故障,流量通过去往ISP2的G0/0/5口转发,且通过双机热备技术 同步状态会话表项,保证业务不中断。
-
当FW1 连接 ISP1 链路恢复,ISP1 恢复。可以通过VRRP、IP-Link感知故障恢复,触发防火墙以及浮动缺省路由主备回切,流量通过FW1的G0/0/3接口转发,且通过双机热备技术 同步状态会话表项,保证业务不中断。



