- 1几大开源免费的 JavaScript 富文本编辑器测评_javascript中国免费
- 2AAAI 2020 | 多模态基准指导的生成式多模态自动文摘_多模态多输出摘要生成
- 3python网络渗透之:DOS攻击篇_ddos攻击脚本
- 418款好用的网络安全渗透测试工具推荐_网络渗透工具
- 5看看这模型!“桥梁建设国家队”是如何用CC来三维建模的?_cc三维成果图片
- 6Android应用程序开发以及背后的设计思想深度剖析(4)_掌握android 编程的基本思想
- 7多个微信同时发朋友圈!一键搞定朋友圈运营,告别多账号来回切换和复制粘贴的繁琐操作!超赞~_微信怎么一次发跟多个微信号的朋友圈
- 8maven基础入门_maven3.9.3
- 9神经网络中,正则化L1与L2的区别、如何选择以及代码验证_l1和l2正则化怎么选
- 10JS执行原理大揭秘:事件循环Event Loop与宏任务、微任务
【kali工具使用】Tcpdump 抓包查看三次握手过程
赞
踩
Tcpdump 抓包查看三次握手过程
tcpdump 常用参数:
-c
指定要抓取的数据包数量
-n 对 IP 地址以数字方式显式,否则显式为主机名
port 指定端口
-I
指定 tcpdump 需要监听的接口。默认会抓取第一个网络接口
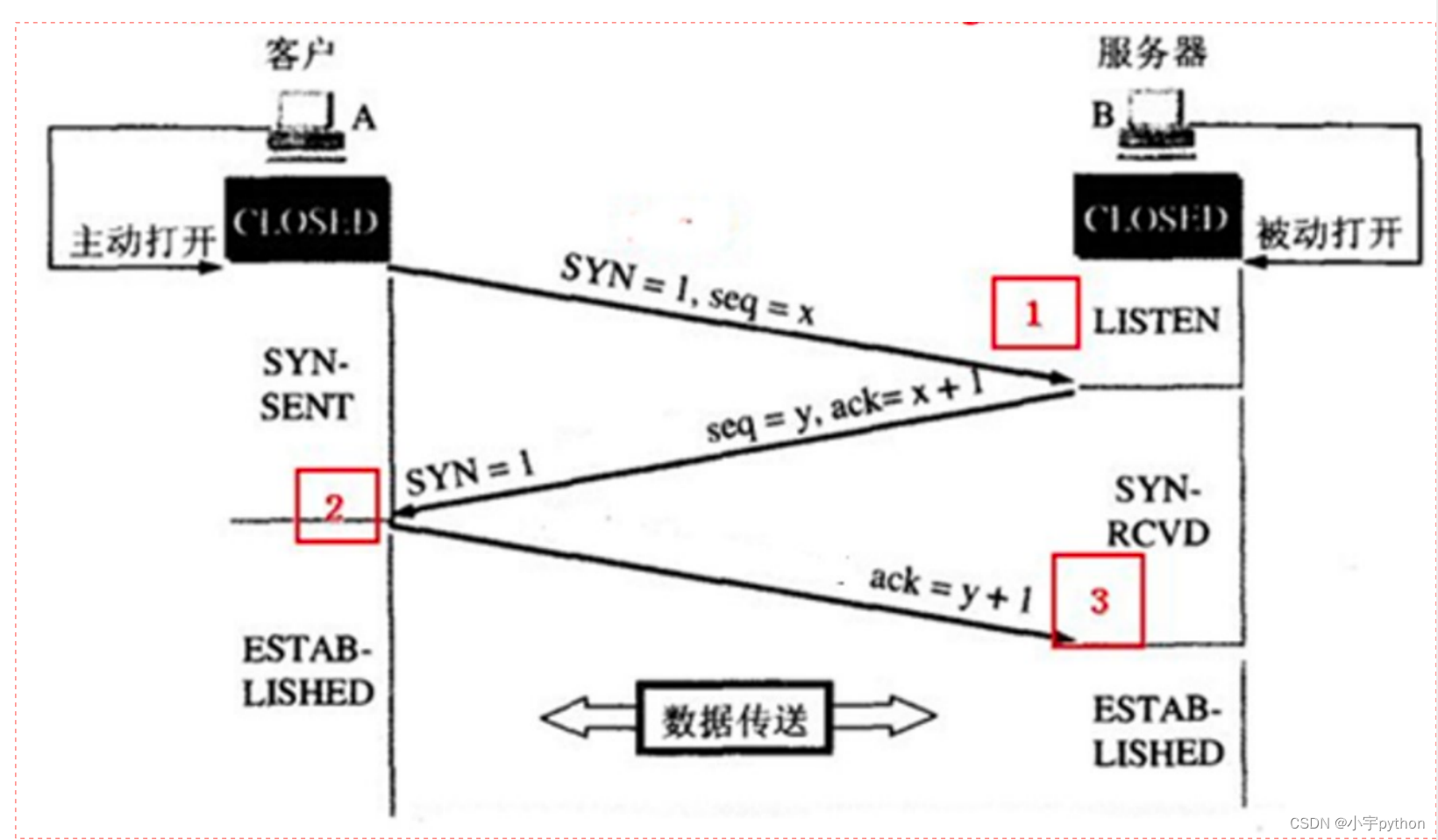
tcp
1ClientSYN=1seq=x
2Server SYN=1 seq=y, ack=x+1,
3Client ack=y+1.
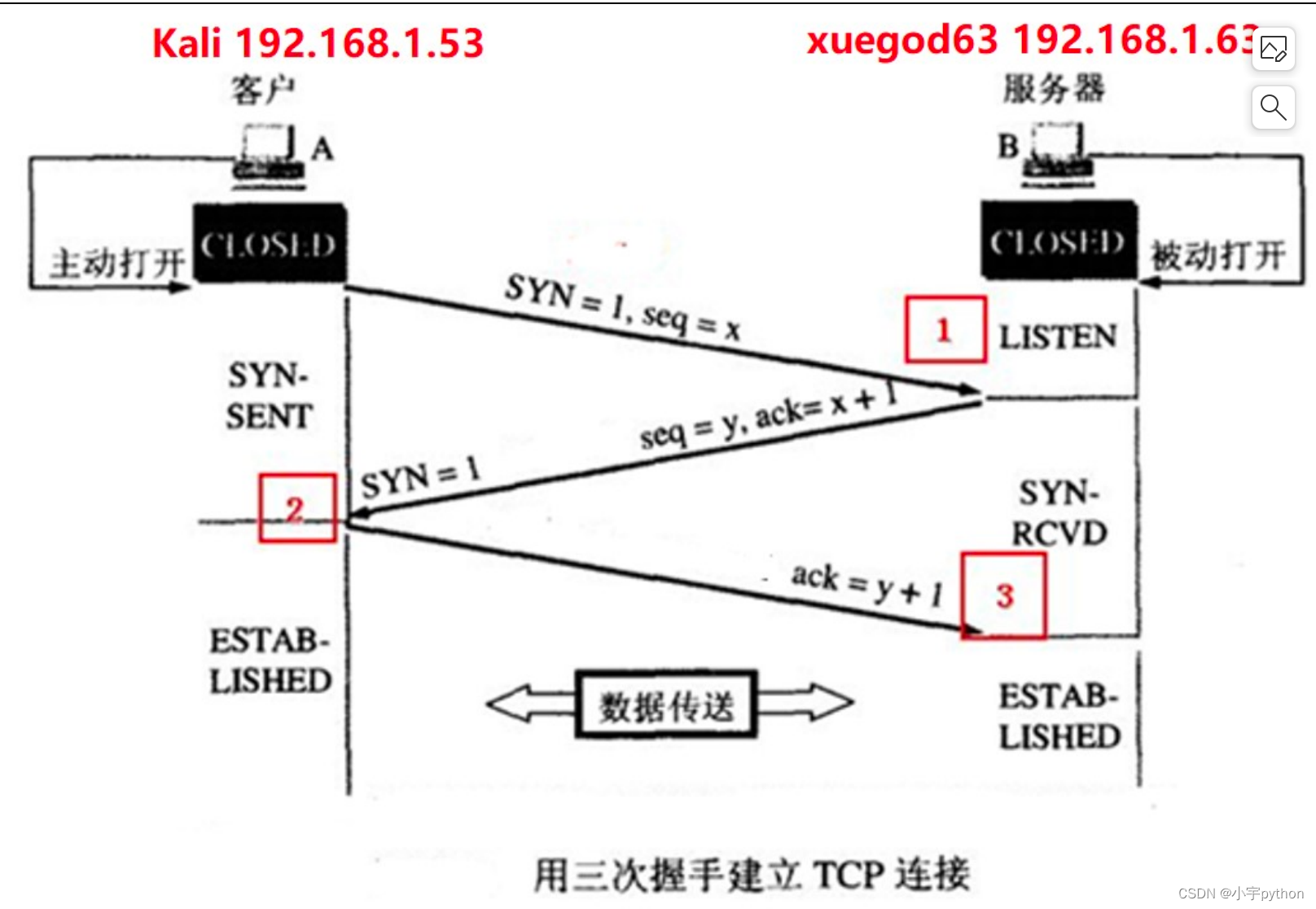
在 kali 上登录 x63,抓取 ssh 远程登录 x63 时,产生的 tcp 三次握手包:
┌──(root
x53)-[~]
└─# tcpdump -n -c 3 port 22 -i eth0
打开另一个终端,开始建立 tcp 连接:
┌──(root
x53)-[~]
└─# ssh 192.168.1.63
The authenticity of host '192.168.1.63 (192.168.1.63)' can't be established.
ED25519 key fingerprint is
SHA256:8kYEhyucVtzLJmSnDKOoYzaheaxjnTFxh36vkiFCGDs.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? #到这里就不用执
行了,tcp 已经建立连接
查看数据包:
┌──(root
x)-[~]
└─# tcpdump -n -c 3 port 22 -i eth0
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
13:47:56.525038 IP 192.168.1.53.42544 > 192.168.1.63.22: Flags [S], seq 2919893900,
win 64240, options [mss 1460,sackOK,TS val 2812743846 ecr 0,nop,wscale 7], length 0
13:47:56.525178 IP 192.168.1.63.22 > 192.168.1.53.42544: Flags [S.], seq 3068407345,
ack 2919893901, win 28960, options [mss 1460,sackOK,TS val 6767151 ecr
2812743846,nop,wscale 7], length 0
13:47:56.525200 IP 192.168.1.53.42544 > 192.168.1.63.22: Flags [.], ack 1, win 502,
options [nop,nop,TS val 2812743847 ecr 6767151], length 0
注:Flags [S] 中的 S 表示为 SYN 标志位为 1
client 主机返回 ACK,包序号为 ack=1 ,这是相对序号,如果需要看绝对序号,可以在 tcpdump
命令中加-S
┌──(root
x)-[~]
└─# tcpdump -n -c 3 port 22 -i eth0 -S
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
13:56:53.720739 IP 192.168.1.53.42546 > 192.168.1.63.22: Flags [S], seq 4191281358,
win 64240, options [mss 1460,sackOK,TS val 2813281042 ecr 0,nop,wscale 7], length 0
13:56:53.721168 IP 192.168.1.63.22 > 192.168.1.53.42546: Flags [S.], seq 4015819851,
ack 4191281359, win 28960, options [mss 1460,sackOK,TS val 7304354 ecr
2813281042,nop,wscale 7], length 0
13:56:53.721187 IP 192.168.1.53.42546 > 192.168.1.63.22: Flags [.], ack 4015819852,
win 502, options [nop,nop,TS val 2813281043 ecr 7304354], length 0
TCP 三次握手连接状态详解:
TCP 连接状态详解:
服务器端:LISTEN:侦听来自远方的 TCP 端口的连接请求
客户端:SYN-SENT:在发送连接请求后等待匹配的连接请求
服务器端:SYN-RECEIVED:在收到和发送一个连接请求后等待对方对连接请求的确认
客户端/服务器端:ESTABLISHED:代表一个打开的连接


