- 1第五章 过 JDBC 连接 SQL 网关
- 2[mongo]JPA继承SimpleMongoRepository实现Springboot整合Mongo JPA复杂条件分页查询
- 3LeetCode.1686. 石子游戏 VI
- 4adb pull 某一路径下的同一类文件_adb pull拉取相同后缀名文件
- 5若依框架(RuoYi-Vue):权限功能模块设计分析_若依框架权限控制
- 6SDCC 2016讲师、知名JavaScript专家周爱民议题公布:有前端思想的物联网系统架构...
- 7【经验分享】Docker容器部署方法说明_docker部署
- 8python在多卡服务器中指定某块显卡允许程序 -- 本机为mac,服务器为Linux, nvidia_python 指定显卡
- 9python基础:循环语句的数学运用_python编写程序输出: :1 1 2 1 2 3 1234
- 10第五章 保护模式进阶,向内核迈进_ards bios
SpringCloud Gateway + Jwt + Oauth2 实现网关的鉴权操作
赞
踩
点击上方“芋道源码”,选择“设为星标”
管她前浪,还是后浪?
能浪的浪,才是好浪!
每天 10:33 更新文章,每天掉亿点点头发...
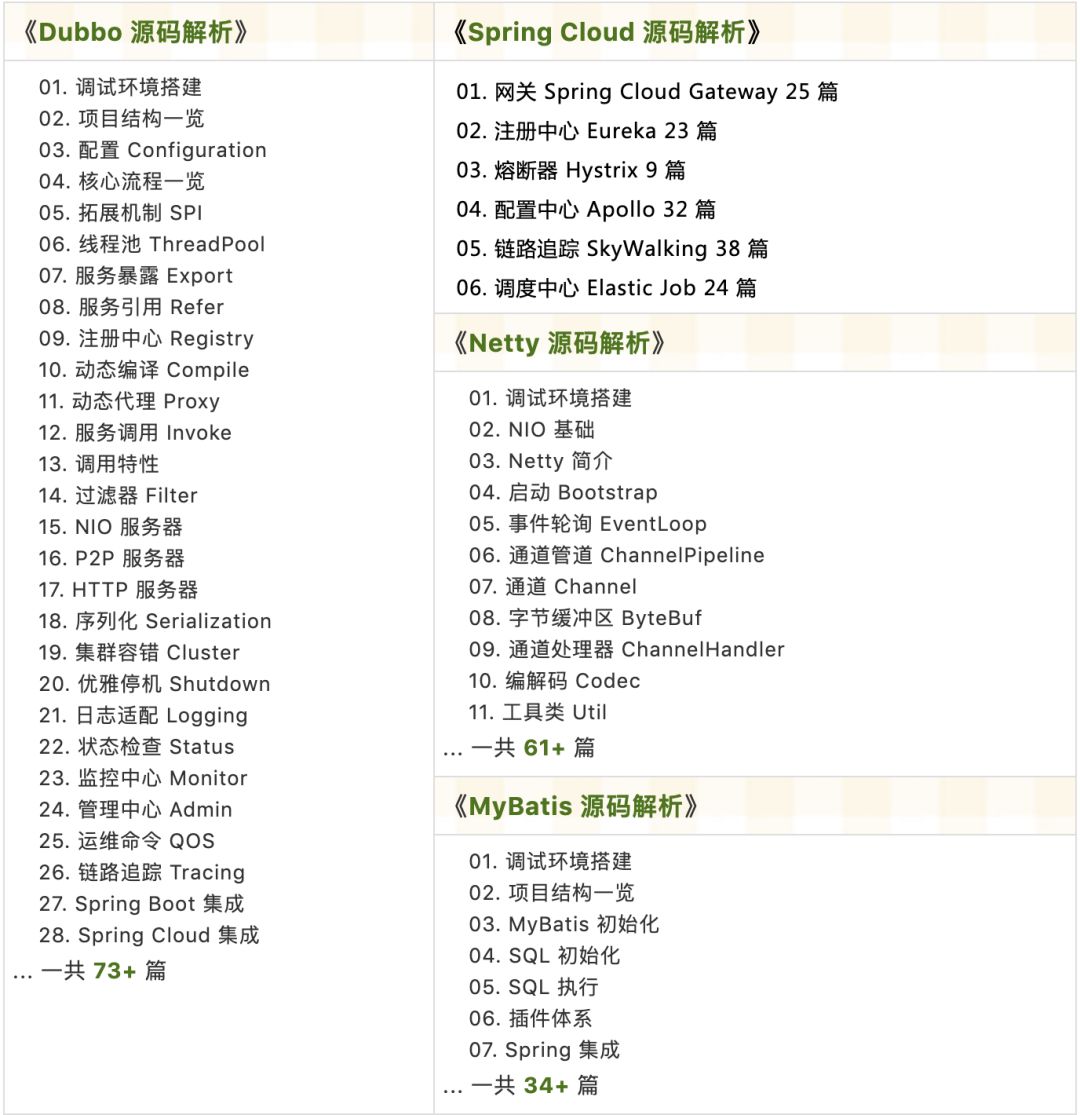
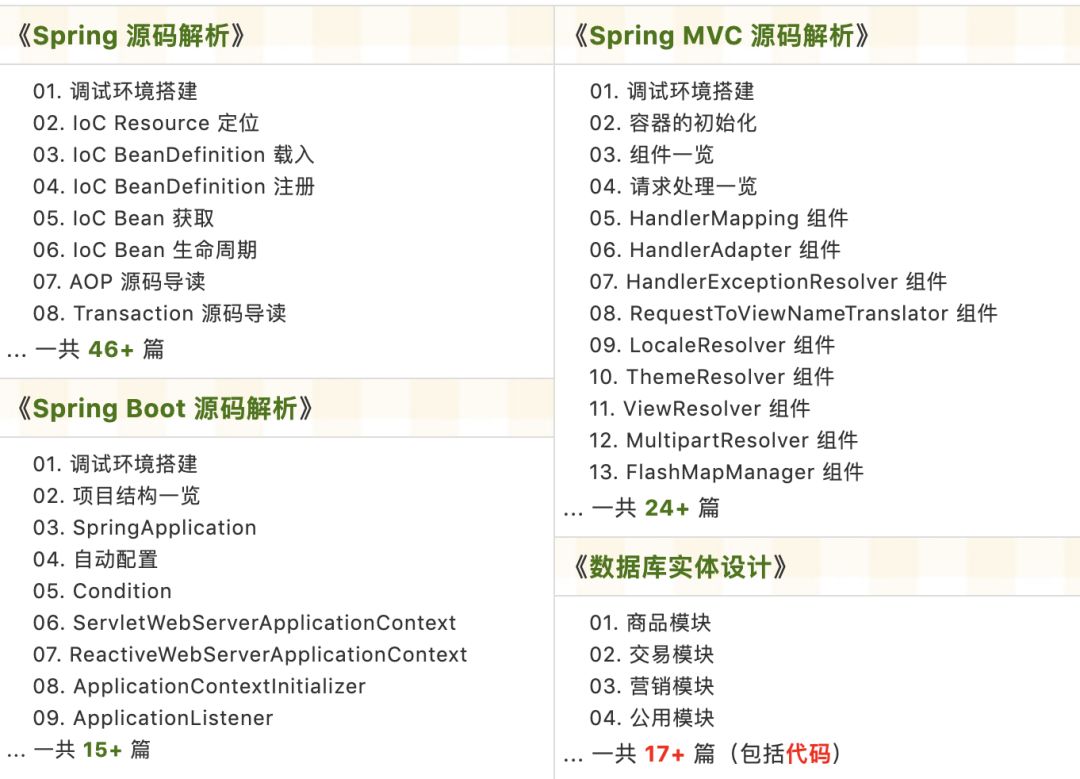
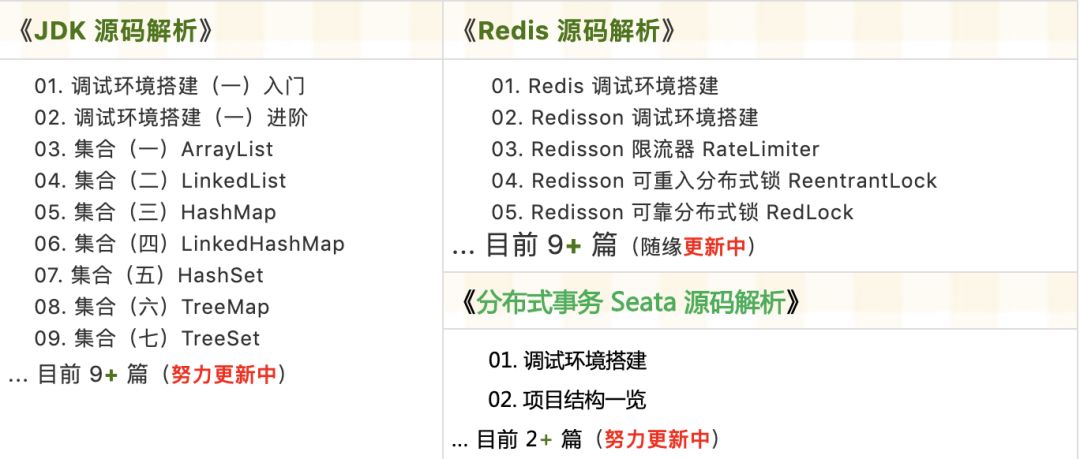
源码精品专栏
一、背景
随着我们的微服务越来越多,如果每个微服务都要自己去实现一套鉴权操作,那么这么操作比较冗余,因此我们可以把鉴权操作统一放到网关去做,如果微服务自己有额外的鉴权处理,可以在自己的微服务中处理。
基于 Spring Boot + MyBatis Plus + Vue & Element 实现的后台管理系统 + 用户小程序,支持 RBAC 动态权限、多租户、数据权限、工作流、三方登录、支付、短信、商城等功能
项目地址:https://gitee.com/zhijiantianya/ruoyi-vue-pro
视频教程:https://doc.iocoder.cn/video/
二、需求
1、在网关层完成url层面的鉴权操作。
所有的
OPTION请求都放行。所有不存在请求,直接都拒绝访问。
user-provider服务的findAllUsers需要user.userInfo权限才可以访问。
2、将解析后的jwt token当做请求头传递到下游服务中。3、整合Spring Security Oauth2 Resource Server
基于 Spring Cloud Alibaba + Gateway + Nacos + RocketMQ + Vue & Element 实现的后台管理系统 + 用户小程序,支持 RBAC 动态权限、多租户、数据权限、工作流、三方登录、支付、短信、商城等功能
项目地址:https://gitee.com/zhijiantianya/yudao-cloud
视频教程:https://doc.iocoder.cn/video/
三、前置条件
1、搭建一个可用的认证服务器
https://juejin.cn/post/6985411823144615972
2、知道Spring Security Oauth2 Resource Server资源服务器如何使用
https://juejin.cn/post/6985893815500406791
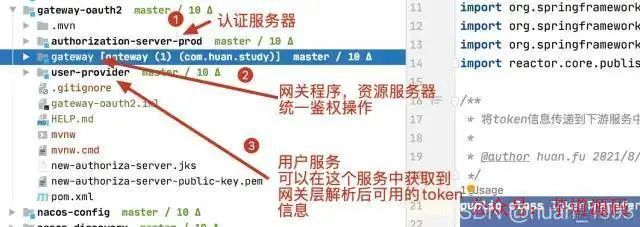
四、项目结构
五、网关层代码的编写
1、引入jar包
2、自定义授权管理器
自定义授权管理器,判断用户是否有权限访问
此处我们简单判断
放行所有的 OPTION 请求。
判断某个请求(url)用户是否有权限访问。
所有不存在的请求(url)直接无权限访问。
- package com.huan.study.gateway.config;
-
- import com.google.common.collect.Maps;
- import lombok.extern.slf4j.Slf4j;
- import org.springframework.http.HttpMethod;
- import org.springframework.http.server.reactive.ServerHttpRequest;
- import org.springframework.security.authentication.AbstractAuthenticationToken;
- import org.springframework.security.authorization.AuthorizationDecision;
- import org.springframework.security.authorization.ReactiveAuthorizationManager;
- import org.springframework.security.core.Authentication;
- import org.springframework.security.core.GrantedAuthority;
- import org.springframework.security.oauth2.server.resource.authentication.JwtAuthenticationToken;
- import org.springframework.security.web.server.authorization.AuthorizationContext;
- import org.springframework.stereotype.Component;
- import org.springframework.util.AntPathMatcher;
- import org.springframework.util.PathMatcher;
- import org.springframework.util.StringUtils;
- import org.springframework.web.server.ServerWebExchange;
- import reactor.core.publisher.Mono;
-
- import javax.annotation.PostConstruct;
- import java.util.Map;
- import java.util.Objects;
-
- /**
- * 自定义授权管理器,判断用户是否有权限访问
- */
- @Component
- @Slf4j
- public class CustomReactiveAuthorizationManager implements ReactiveAuthorizationManager<AuthorizationContext> {
-
- /**
- * 此处保存的是资源对应的权限,可以从数据库中获取
- */
- private static final Map<String, String> AUTH_MAP = Maps.newConcurrentMap();
-
- @PostConstruct
- public void initAuthMap() {
- AUTH_MAP.put("/user/findAllUsers", "user.userInfo");
- AUTH_MAP.put("/user/addUser", "ROLE_ADMIN");
- }
-
-
- @Override
- public Mono<AuthorizationDecision> check(Mono<Authentication> authentication, AuthorizationContext authorizationContext) {
- ServerWebExchange exchange = authorizationContext.getExchange();
- ServerHttpRequest request = exchange.getRequest();
- String path = request.getURI().getPath();
-
- // 带通配符的可以使用这个进行匹配
- PathMatcher pathMatcher = new AntPathMatcher();
- String authorities = AUTH_MAP.get(path);
- log.info("访问路径:[{}],所需要的权限是:[{}]", path, authorities);
-
- // option 请求,全部放行
- if (request.getMethod() == HttpMethod.OPTIONS) {
- return Mono.just(new AuthorizationDecision(true));
- }
-
- // 不在权限范围内的url,全部拒绝
- if (!StringUtils.hasText(authorities)) {
- return Mono.just(new AuthorizationDecision(false));
- }
-
- return authentication
- .filter(Authentication::isAuthenticated)
- .filter(a -> a instanceof JwtAuthenticationToken)
- .cast(JwtAuthenticationToken.class)
- .doOnNext(token -> {
- System.out.println(token.getToken().getHeaders());
- System.out.println(token.getTokenAttributes());
- })
- .flatMapIterable(AbstractAuthenticationToken::getAuthorities)
- .map(GrantedAuthority::getAuthority)
- .any(authority -> Objects.equals(authority, authorities))
- .map(AuthorizationDecision::new)
- .defaultIfEmpty(new AuthorizationDecision(false));
- }
- }

3、token认证失败、或超时的处理
- package com.huan.study.gateway.config;
-
- import org.springframework.core.io.buffer.DataBuffer;
- import org.springframework.core.io.buffer.DataBufferUtils;
- import org.springframework.http.HttpStatus;
- import org.springframework.security.core.AuthenticationException;
- import org.springframework.security.web.server.ServerAuthenticationEntryPoint;
- import org.springframework.web.server.ServerWebExchange;
- import reactor.core.publisher.Mono;
-
- import java.nio.charset.StandardCharsets;
-
- /**
- * 认证失败异常处理
- */
- public class CustomServerAuthenticationEntryPoint implements ServerAuthenticationEntryPoint {
- @Override
- public Mono<Void> commence(ServerWebExchange exchange, AuthenticationException ex) {
-
- return Mono.defer(() -> Mono.just(exchange.getResponse()))
- .flatMap(response -> {
- response.setStatusCode(HttpStatus.UNAUTHORIZED);
- String body = "{\"code\":401,\"msg\":\"token不合法或过期\"}";
- DataBuffer buffer = response.bufferFactory().wrap(body.getBytes(StandardCharsets.UTF_8));
- return response.writeWith(Mono.just(buffer))
- .doOnError(error -> DataBufferUtils.release(buffer));
- });
- }
- }

4、用户没有权限的处理
- package com.huan.study.gateway.config;
-
- import lombok.extern.slf4j.Slf4j;
- import org.springframework.context.annotation.Bean;
- import org.springframework.core.io.buffer.DataBuffer;
- import org.springframework.core.io.buffer.DataBufferUtils;
- import org.springframework.http.HttpStatus;
- import org.springframework.http.server.reactive.ServerHttpRequest;
- import org.springframework.http.server.reactive.ServerHttpResponse;
- import org.springframework.security.access.AccessDeniedException;
- import org.springframework.security.web.server.authorization.ServerAccessDeniedHandler;
- import org.springframework.web.server.ServerWebExchange;
- import reactor.core.publisher.Mono;
-
- import java.nio.charset.StandardCharsets;
-
- /**
- * 无权限访问异常
- */
- @Slf4j
- public class CustomServerAccessDeniedHandler implements ServerAccessDeniedHandler {
-
- @Override
- public Mono<Void> handle(ServerWebExchange exchange, AccessDeniedException denied) {
-
- ServerHttpRequest request = exchange.getRequest();
-
- return exchange.getPrincipal()
- .doOnNext(principal -> log.info("用户:[{}]没有访问:[{}]的权限.", principal.getName(), request.getURI()))
- .flatMap(principal -> {
- ServerHttpResponse response = exchange.getResponse();
- response.setStatusCode(HttpStatus.FORBIDDEN);
- String body = "{\"code\":403,\"msg\":\"您无权限访问\"}";
- DataBuffer buffer = response.bufferFactory().wrap(body.getBytes(StandardCharsets.UTF_8));
- return response.writeWith(Mono.just(buffer))
- .doOnError(error -> DataBufferUtils.release(buffer));
- });
- }
- }

5、将token信息传递到下游服务器中
- package com.huan.study.gateway.config;
-
- import com.fasterxml.jackson.core.JsonProcessingException;
- import com.fasterxml.jackson.databind.ObjectMapper;
- import com.fasterxml.jackson.datatype.jdk8.Jdk8Module;
- import com.fasterxml.jackson.datatype.jsr310.JavaTimeModule;
- import org.springframework.http.server.reactive.ServerHttpRequest;
- import org.springframework.security.core.context.ReactiveSecurityContextHolder;
- import org.springframework.security.core.context.SecurityContext;
- import org.springframework.security.oauth2.server.resource.authentication.JwtAuthenticationToken;
- import org.springframework.web.server.ServerWebExchange;
- import org.springframework.web.server.WebFilter;
- import org.springframework.web.server.WebFilterChain;
- import reactor.core.publisher.Mono;
-
- /**
- * 将token信息传递到下游服务中
- *
- * @author huan.fu 2021/8/25 - 下午2:49
- */
- public class TokenTransferFilter implements WebFilter {
-
- private static final ObjectMapper OBJECT_MAPPER = new ObjectMapper();
-
- static {
- OBJECT_MAPPER.registerModule(new Jdk8Module());
- OBJECT_MAPPER.registerModule(new JavaTimeModule());
- }
-
- @Override
- public Mono<Void> filter(ServerWebExchange exchange, WebFilterChain chain) {
- return ReactiveSecurityContextHolder.getContext()
- .map(SecurityContext::getAuthentication)
- .cast(JwtAuthenticationToken.class)
- .flatMap(authentication -> {
- ServerHttpRequest request = exchange.getRequest();
- request = request.mutate()
- .header("tokenInfo", toJson(authentication.getPrincipal()))
- .build();
-
- ServerWebExchange newExchange = exchange.mutate().request(request).build();
-
- return chain.filter(newExchange);
- });
- }
-
- public String toJson(Object obj) {
- try {
- return OBJECT_MAPPER.writeValueAsString(obj);
- } catch (JsonProcessingException e) {
- return null;
- }
- }
- }

6、网关层面的配置
- package com.huan.study.gateway.config;
-
- import org.springframework.beans.factory.annotation.Autowired;
- import org.springframework.context.annotation.Bean;
- import org.springframework.context.annotation.Configuration;
- import org.springframework.core.convert.converter.Converter;
- import org.springframework.core.io.FileSystemResource;
- import org.springframework.core.io.Resource;
- import org.springframework.security.authentication.AbstractAuthenticationToken;
- import org.springframework.security.config.annotation.web.reactive.EnableWebFluxSecurity;
- import org.springframework.security.config.web.server.SecurityWebFiltersOrder;
- import org.springframework.security.config.web.server.ServerHttpSecurity;
- import org.springframework.security.oauth2.jose.jws.SignatureAlgorithm;
- import org.springframework.security.oauth2.jwt.Jwt;
- import org.springframework.security.oauth2.jwt.NimbusReactiveJwtDecoder;
- import org.springframework.security.oauth2.jwt.ReactiveJwtDecoder;
- import org.springframework.security.oauth2.server.resource.authentication.JwtAuthenticationConverter;
- import org.springframework.security.oauth2.server.resource.authentication.JwtGrantedAuthoritiesConverter;
- import org.springframework.security.oauth2.server.resource.authentication.ReactiveJwtAuthenticationConverterAdapter;
- import org.springframework.security.oauth2.server.resource.web.server.ServerBearerTokenAuthenticationConverter;
- import org.springframework.security.web.server.SecurityWebFilterChain;
- import reactor.core.publisher.Mono;
-
- import java.io.IOException;
- import java.nio.file.Files;
- import java.security.KeyFactory;
- import java.security.NoSuchAlgorithmException;
- import java.security.interfaces.RSAPublicKey;
- import java.security.spec.InvalidKeySpecException;
- import java.security.spec.X509EncodedKeySpec;
- import java.util.Base64;
-
- /**
- * 资源服务器配置
- */
- @Configuration
- @EnableWebFluxSecurity
- public class ResourceServerConfig {
-
- @Autowired
- private CustomReactiveAuthorizationManager customReactiveAuthorizationManager;
-
- @Bean
- public SecurityWebFilterChain securityWebFilterChain(ServerHttpSecurity http) throws NoSuchAlgorithmException, IOException, InvalidKeySpecException {
- http.oauth2ResourceServer()
- .jwt()
- .jwtAuthenticationConverter(jwtAuthenticationConverter())
- .jwtDecoder(jwtDecoder())
- .and()
- // 认证成功后没有权限操作
- .accessDeniedHandler(new CustomServerAccessDeniedHandler())
- // 还没有认证时发生认证异常,比如token过期,token不合法
- .authenticationEntryPoint(new CustomServerAuthenticationEntryPoint())
- // 将一个字符串token转换成一个认证对象
- .bearerTokenConverter(new ServerBearerTokenAuthenticationConverter())
- .and()
- .authorizeExchange()
- // 所有以 /auth/** 开头的请求全部放行
- .pathMatchers("/auth/**", "/favicon.ico").permitAll()
- // 所有的请求都交由此处进行权限判断处理
- .anyExchange()
- .access(customReactiveAuthorizationManager)
- .and()
- .exceptionHandling()
- .accessDeniedHandler(new CustomServerAccessDeniedHandler())
- .authenticationEntryPoint(new CustomServerAuthenticationEntryPoint())
- .and()
- .csrf()
- .disable()
- .addFilterAfter(new TokenTransferFilter(), SecurityWebFiltersOrder.AUTHENTICATION);
-
- return http.build();
- }
-
- /**
- * 从jwt令牌中获取认证对象
- */
- public Converter<Jwt, ? extends Mono<? extends AbstractAuthenticationToken>> jwtAuthenticationConverter() {
-
- // 从jwt 中获取该令牌可以访问的权限
- JwtGrantedAuthoritiesConverter authoritiesConverter = new JwtGrantedAuthoritiesConverter();
- // 取消权限的前缀,默认会加上SCOPE_
- authoritiesConverter.setAuthorityPrefix("");
- // 从那个字段中获取权限
- authoritiesConverter.setAuthoritiesClaimName("scope");
-
- JwtAuthenticationConverter jwtAuthenticationConverter = new JwtAuthenticationConverter();
- // 获取 principal name
- jwtAuthenticationConverter.setPrincipalClaimName("sub");
- jwtAuthenticationConverter.setJwtGrantedAuthoritiesConverter(authoritiesConverter);
-
- return new ReactiveJwtAuthenticationConverterAdapter(jwtAuthenticationConverter);
- }
-
- /**
- * 解码jwt
- */
- public ReactiveJwtDecoder jwtDecoder() throws IOException, NoSuchAlgorithmException, InvalidKeySpecException {
- Resource resource = new FileSystemResource("/Users/huan/code/study/idea/spring-cloud-alibaba-parent/gateway-oauth2/new-authoriza-server-public-key.pem");
- String publicKeyStr = String.join("", Files.readAllLines(resource.getFile().toPath()));
- byte[] publicKeyBytes = Base64.getDecoder().decode(publicKeyStr);
- X509EncodedKeySpec keySpec = new X509EncodedKeySpec(publicKeyBytes);
- KeyFactory keyFactory = KeyFactory.getInstance("RSA");
- RSAPublicKey rsaPublicKey = (RSAPublicKey) keyFactory.generatePublic(keySpec);
-
- return NimbusReactiveJwtDecoder.withPublicKey(rsaPublicKey)
- .signatureAlgorithm(SignatureAlgorithm.RS256)
- .build();
- }
- }

7、网关yaml配置文件
- spring:
- application:
- name: gateway-auth
- cloud:
- nacos:
- discovery:
- server-addr: localhost:8847
- gateway:
- routes:
- - id: user-provider
- uri: lb://user-provider
- predicates:
- - Path=/user/**
- filters:
- - RewritePath=/user(?<segment>/?.*), $\{segment}
- compatibility-verifier:
- # 取消SpringCloud SpringCloudAlibaba SpringBoot 等的版本检查
- enabled: false
- server:
- port: 9203
- debug: true

六、演示
1、客户端 gateway 在认证服务器拥有的权限为 user.userInfo
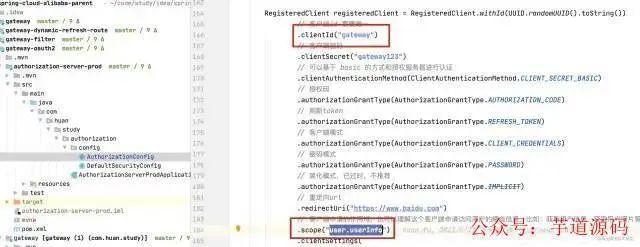
2、user-provider服务提供了一个api findAllUsers,它会返回 系统中存在的用户(假的数据) 和 解码后的token信息。
3、在网关层面,findAllUsers 需要的权限为 user.userInfo,正好 gateway这个客户端有这个权限,所以可以访问。
七、代码路径
https://gitee.com/huan1993/spring-cloud-alibaba-parent/tree/master/gateway-oauth2
欢迎加入我的知识星球,一起探讨架构,交流源码。加入方式,长按下方二维码噢:

已在知识星球更新源码解析如下:
最近更新《芋道 SpringBoot 2.X 入门》系列,已经 101 余篇,覆盖了 MyBatis、Redis、MongoDB、ES、分库分表、读写分离、SpringMVC、Webflux、权限、WebSocket、Dubbo、RabbitMQ、RocketMQ、Kafka、性能测试等等内容。
提供近 3W 行代码的 SpringBoot 示例,以及超 4W 行代码的电商微服务项目。
获取方式:点“在看”,关注公众号并回复 666 领取,更多内容陆续奉上。
- 文章有帮助的话,在看,转发吧。
- 谢谢支持哟 (*^__^*)