- 1【ChatGPT】 Microsoft Edge 浏览器扩展使用 GPT_edge插件使用gpt
- 2本地运行Llama3极简中文傻瓜手把手教程,超越GPT4?能力如何?|文末赠2024AI工程师完整视频教程+源码资料_ollama3
- 3[AcWing]802. 区间和(C++实现)区间和模板题_c++区间怎么表示
- 4linux内核解析设备树节点_xilinx ethernet device tree
- 5基于Flask的上市公司数据分析与可视化系统设计与实现开题报告_完成本课题所需工作条件(如工具书、计算机、实验、调研等)及解决办法
- 6怎么在网上赚钱?7种方法总有一种适合你!
- 7机器学习 Christopher Bishop PRML_bishop 机器学习
- 8【Java】时间格式化注解_java 时间字段格式化注解
- 9python爬取人脸识别图片数据集_python 怎么把捕捉到的人脸数据放到数据库中
- 10Flink基础系列-DataSet广播变量_flink中广播流 建议缓存多少数据呀
Terraform实现负载均衡aws公有子网ec2实例_aws terraform 创建ec2
赞
踩
Terraform实现负载均衡aws公有子网ec2实例文档
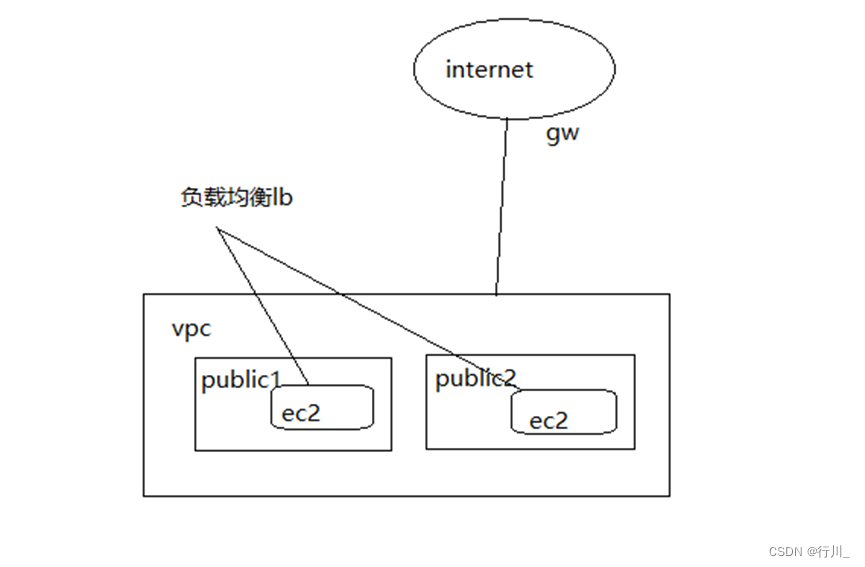
通过terraform创建一个vpc、igw、route_table、两个subnet_public、一个安全组开放80、22、443端口、一个负载均衡器lb、一个开放80端口的侦听器、一个目标群组、两台ec2实例;需要将gw与vpc关联、subnet_public与路由器关联
一.所需要的环境以及工具
- 所需要使用到的平台:aws
- 需要使用到的部署架构工具:terraform
- 一台手动创建的ec2实例,以便安装terraform工具并作为其运行环境来搭建负载均衡
需要实现的架构
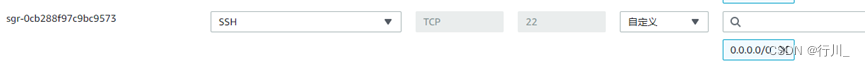
控制台启动一台新实例,选择默认vpv以及默认安全组,开放安全组的22端口以便于连接实例终端
启动新实例安装terraform命令行
手动创建实例安装terraform CLI
sudo yum install -y yum-utils
sudo yum-config-manager ----add-repo https: //rpm.releases.hashicorp.com/Amazonlinux/hashicorp.repo
sudo yum -y install terraform
二.搭建具体步骤
1.mkdir lb 创建tf文件存放目录(terraform是在同一目录下运行所有以.tf结尾的文件)
2.vim main.tf 主要部署内容
#插件来源,aws作为插件的提供者
provider "aws" {
region = "us-west-1"
access_key = "AKIAVRWD4Y2TR4EFJCV6"
secret_key = "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"
}
#网络结构
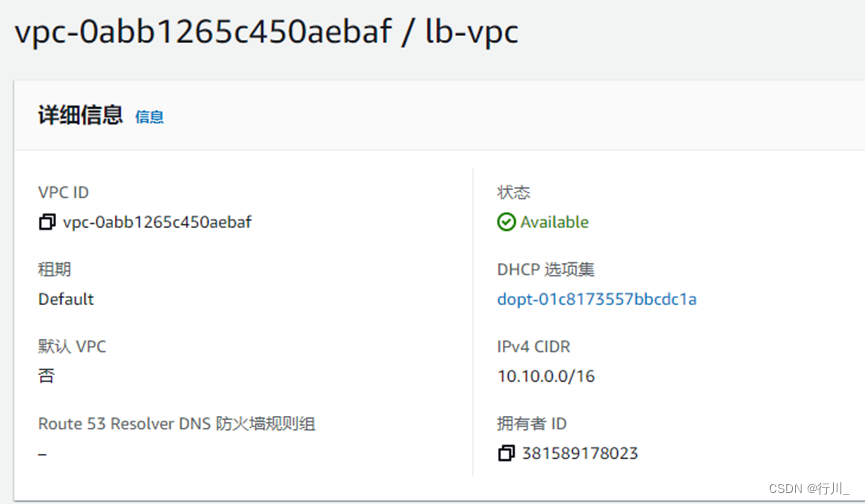
resource "aws_vpc" "lb-vpc" {
cidr_block = "10.10.0.0/16"
instance_tenancy = "default"
tags = {
Name = "lb-vpc"
}
}
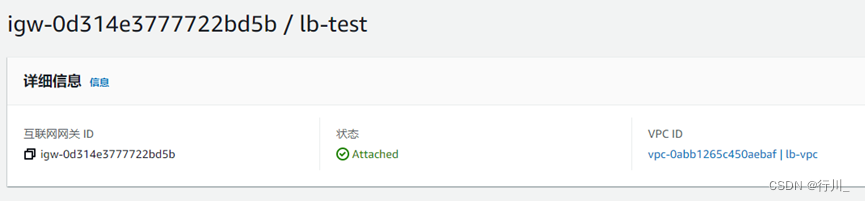
resource "aws_internet_gateway" "gw" {
vpc_id = aws_vpc.lb-vpc.id
tags = {
Name = "lb-test"
}
}
resource "aws_route_table" "lb-route-table" {
vpc_id = aws_vpc.lb-vpc.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.gw.id
}
route {
ipv6_cidr_block = "::/0"
gateway_id = aws_internet_gateway.gw.id
}
tags = {
Name = "test-lb"
}
}
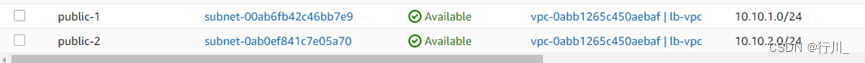
resource "aws_subnet" "public" {
vpc_id = aws_vpc.lb-vpc.id
count = length(var.tf-test-azs)
cidr_block = element(var.cidrlist , count.index)
availability_zone = element(var.tf-test-azs , count.index)
tags = {
Name = "public-${count.index+1}"
}
}
resource "aws_route_table_association" "a" {
count = length(var.cidrlist)
subnet_id = element(aws_subnet.public.*.id , count.index)
route_table_id = aws_route_table.lb-route-table.id
}
resource "aws_security_group" "allow_web" {
name = "allow_web_traffic"
description = "Allow TLS inbound traffic"
vpc_id = aws_vpc.lb-vpc.id
ingress {
description = "HTTPS"
from_port = 443
to_port = 443
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
description = "SSH"
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
description = "HTTP"
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
ipv6_cidr_blocks = ["::/0"]
}
tags = {
Name = "allow_lb"
}
}
#负载均衡器
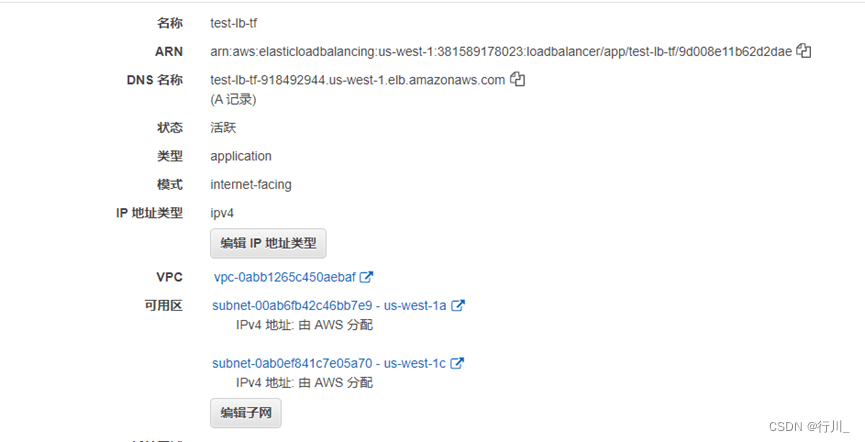
resource "aws_lb" "test" {
name = "test-lb-tf"
internal = false
load_balancer_type = "application"
security_groups = [aws_security_group.allow_web.id]
subnets = [for subnet in aws_subnet.public : subnet.id]
enable_deletion_protection = false
tags = {
Environment = "production"
}
}
resource "aws_lb_listener" "http" {
load_balancer_arn = aws_lb.test.arn
port = "80"
protocol = "HTTP"
default_action {
type = "forward"
target_group_arn = aws_lb_target_group.alb_target_group.arn
}
}
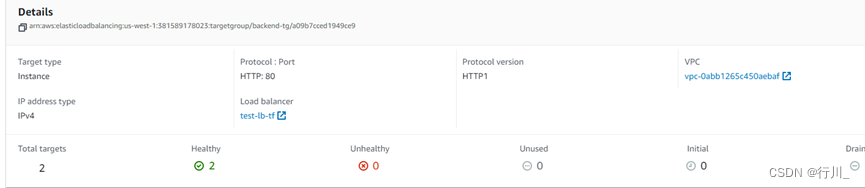
resource "aws_lb_target_group" "alb_target_group" {
name = "backend-tg"
port = 80
protocol = "HTTP"
target_type = "instance"
vpc_id = aws_vpc.lb-vpc.id
health_check {
enabled = true
path = "/"
port = "80"
protocol = "HTTP"
healthy_threshold = 3
unhealthy_threshold = 2
interval = 90
timeout = 20
matcher = "200"
}
depends_on = [aws_lb.test]
}
resource "aws_alb_target_group_attachment" "test1" {
count = length(aws_instance.web-server-instance)
target_group_arn = "${aws_lb_target_group.alb_target_group.arn}"
port = 80
target_id = "${aws_instance.web-server-instance[count.index].id}"
}
3.vim ec2.tf 负载均衡实例,实例创建完成是默认安全组,需要打开80端口
resource "aws_instance" "web-server-instance" {
count = length(var.cidrlist)
ami = "ami-0d9858aa3c6322f73"
instance_type = "t2.micro"
key_name = "ruiyin"
subnet_id = aws_subnet.public[count.index].id
#实例应具有可正常运行的Web服务器,以响应运行状况检查
user_data = <<EOF
#!/bin/bash
sudo amazon-linux-extras install nginx1 -y
echo "${count.index}">>/usr/share/nginx/html/index.html
sudo systemctl start nginx
EOF
tags = {
Name = "ExampleServerIstance-${count.index+1}"
}
}
resource "aws_eip" "web-server" {
instance = "${aws_instance.web-server-instance[count.index].id}"
count = length(aws_instance.web-server-instance)
vpc = true
}
4.vim var.tf 参数调用
variable "tf-test-azs" {
type = list
default = ["us-west-1a" , "us-west-1c"]
}
variable "cidrlist" {
type = list
default = ["10.10.1.0/24" , "10.10.2.0/24"]
}
三.实现部署
1.terraform init:初始化terraform,安装所需要的插件
2.terraform plan:将要做出的改变
3.terraform:完成部署
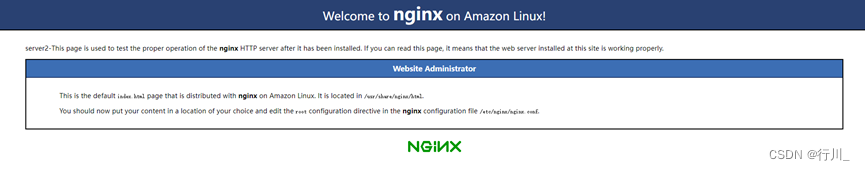
四.完成nginx web-server负载均衡
分别对两台实例nginx的index.html文件做出标识
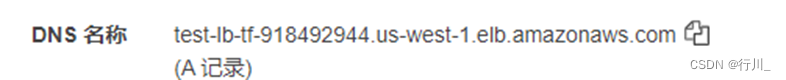
通过web端访问负载均衡的DNS: