热门标签
热门文章
- 1数据库没有备份无法打开处理方法之二dul_you have not specified a default database for this
- 2【java蓝桥杯基础试题】十六进制转十进制_integer valueof(string s, int radix)
- 3模型转换、模型压缩、模型加速工具汇总_onnx模型压缩
- 4Jetson Xavier NX 开发板Ubuntu18.04 安装arduino IDE详细步骤
- 5NRF52832实现Mifare K1门禁卡模拟的探索_nrf52832 nfc
- 6人工智能:技术的进步与未来展望_人工智能展望及风险评估
- 7TS和vue3.0学习笔记_vue3+ts定义数组类型
- 8Windows11 安卓子系统安装(附apk安装步骤)_win11安卓子系统安装apk
- 9Linux 查看硬件常用命令
- 10VSCode 插件 Codeium 打不开 Chat_vscode无法使用codeium
当前位置: article > 正文
关于k8s证书过期问题
作者:小丑西瓜9 | 2024-03-16 05:55:41
赞
踩
关于k8s证书过期问题
k8s证书过期的解决
照常打开服务器连接准备换包,突然发现k8s命令无法使用了,报错如下
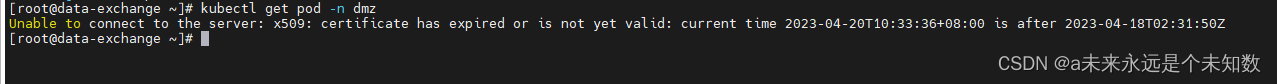
Unable to connect to the server: x509: certificate has expired or is not yet valid: current time
查了一下,这个报错是指k8s的证书过期了
这着实是知识盲区了,证书在哪里也不晓得,好在找到了一个脚本可以解决这个问题,说是可以延长10年
文件赋权之后执行命令
./update-kubeadm-cert.sh all
- 1
这里好像不能直接加文件唉,那我把内容贴出来好了
脚本内容是https://github.com/yuyicai/update-kube-cert这里的,但是有时候对github访问不是很顺畅
#!/bin/bash #脚本转载自https://github.com/yuyicai/update-kube-cert set -o errexit set -o pipefail # set -o xtrace log::err() { printf "[$(date +'%Y-%m-%dT%H:%M:%S.%N%z')]: \033[31mERROR: \033[0m$@\n" } log::info() { printf "[$(date +'%Y-%m-%dT%H:%M:%S.%N%z')]: \033[32mINFO: \033[0m$@\n" } log::warning() { printf "[$(date +'%Y-%m-%dT%H:%M:%S.%N%z')]: \033[33mWARNING: \033[0m$@\n" } check_file() { if [[ ! -r ${1} ]]; then log::err "can not find ${1}" exit 1 fi } # get x509v3 subject alternative name from the old certificate cert::get_subject_alt_name() { local cert=${1}.crt check_file "${cert}" local alt_name=$(openssl x509 -text -noout -in ${cert} | grep -A1 'Alternative' | tail -n1 | sed 's/[[:space:]]*Address//g') printf "${alt_name}\n" } # get subject from the old certificate cert::get_subj() { local cert=${1}.crt check_file "${cert}" local subj=$(openssl x509 -text -noout -in ${cert} | grep "Subject:" | sed 's/Subject:/\//g;s/\,/\//;s/[[:space:]]//g') printf "${subj}\n" } cert::backup_file() { local file=${1} if [[ ! -e ${file}.old-$(date +%Y%m%d) ]]; then cp -rp ${file} ${file}.old-$(date +%Y%m%d) log::info "backup ${file} to ${file}.old-$(date +%Y%m%d)" else log::warning "does not backup, ${file}.old-$(date +%Y%m%d) already exists" fi } # generate certificate whit client, server or peer # Args: # $1 (the name of certificate) # $2 (the type of certificate, must be one of client, server, peer) # $3 (the subject of certificates) # $4 (the validity of certificates) (days) # $5 (the x509v3 subject alternative name of certificate when the type of certificate is server or peer) cert::gen_cert() { local cert_name=${1} local cert_type=${2} local subj=${3} local cert_days=${4} local alt_name=${5} local cert=${cert_name}.crt local key=${cert_name}.key local csr=${cert_name}.csr local csr_conf="distinguished_name = dn\n[dn]\n[v3_ext]\nkeyUsage = critical, digitalSignature, keyEncipherment\n" check_file "${key}" check_file "${cert}" # backup certificate when certificate not in ${kubeconf_arr[@]} # kubeconf_arr=("controller-manager.crt" "scheduler.crt" "admin.crt" "kubelet.crt") # if [[ ! "${kubeconf_arr[@]}" =~ "${cert##*/}" ]]; then # cert::backup_file "${cert}" # fi case "${cert_type}" in client) openssl req -new -key ${key} -subj "${subj}" -reqexts v3_ext \ -config <(printf "${csr_conf} extendedKeyUsage = clientAuth\n") -out ${csr} openssl x509 -in ${csr} -req -CA ${CA_CERT} -CAkey ${CA_KEY} -CAcreateserial -extensions v3_ext \ -extfile <(printf "${csr_conf} extendedKeyUsage = clientAuth\n") -days ${cert_days} -out ${cert} log::info "generated ${cert}" ;; server) openssl req -new -key ${key} -subj "${subj}" -reqexts v3_ext \ -config <(printf "${csr_conf} extendedKeyUsage = serverAuth\nsubjectAltName = ${alt_name}\n") -out ${csr} openssl x509 -in ${csr} -req -CA ${CA_CERT} -CAkey ${CA_KEY} -CAcreateserial -extensions v3_ext \ -extfile <(printf "${csr_conf} extendedKeyUsage = serverAuth\nsubjectAltName = ${alt_name}\n") -days ${cert_days} -out ${cert} log::info "generated ${cert}" ;; peer) openssl req -new -key ${key} -subj "${subj}" -reqexts v3_ext \ -config <(printf "${csr_conf} extendedKeyUsage = serverAuth, clientAuth\nsubjectAltName = ${alt_name}\n") -out ${csr} openssl x509 -in ${csr} -req -CA ${CA_CERT} -CAkey ${CA_KEY} -CAcreateserial -extensions v3_ext \ -extfile <(printf "${csr_conf} extendedKeyUsage = serverAuth, clientAuth\nsubjectAltName = ${alt_name}\n") -days ${cert_days} -out ${cert} log::info "generated ${cert}" ;; *) log::err "unknow, unsupported etcd certs type: ${cert_type}, supported type: client, server, peer" exit 1 esac rm -f ${csr} } cert::update_kubeconf() { local cert_name=${1} local kubeconf_file=${cert_name}.conf local cert=${cert_name}.crt local key=${cert_name}.key # generate certificate check_file ${kubeconf_file} # get the key from the old kubeconf grep "client-key-data" ${kubeconf_file} | awk {'print$2'} | base64 -d > ${key} # get the old certificate from the old kubeconf grep "client-certificate-data" ${kubeconf_file} | awk {'print$2'} | base64 -d > ${cert} # get subject from the old certificate local subj=$(cert::get_subj ${cert_name}) cert::gen_cert "${cert_name}" "client" "${subj}" "${CAER_DAYS}" # get certificate base64 code local cert_base64=$(base64 -w 0 ${cert}) # backup kubeconf # cert::backup_file "${kubeconf_file}" # set certificate base64 code to kubeconf sed -i 's/client-certificate-data:.*/client-certificate-data: '${cert_base64}'/g' ${kubeconf_file} log::info "generated new ${kubeconf_file}" rm -f ${cert} rm -f ${key} # set config for kubectl if [[ ${cert_name##*/} == "admin" ]]; then mkdir -p ~/.kube cp -fp ${kubeconf_file} ~/.kube/config log::info "copy the admin.conf to ~/.kube/config for kubectl" fi } cert::update_etcd_cert() { PKI_PATH=${KUBE_PATH}/pki/etcd CA_CERT=${PKI_PATH}/ca.crt CA_KEY=${PKI_PATH}/ca.key check_file "${CA_CERT}" check_file "${CA_KEY}" # generate etcd server certificate # /etc/kubernetes/pki/etcd/server CART_NAME=${PKI_PATH}/server subject_alt_name=$(cert::get_subject_alt_name ${CART_NAME}) cert::gen_cert "${CART_NAME}" "peer" "/CN=etcd-server" "${CAER_DAYS}" "${subject_alt_name}" # generate etcd peer certificate # /etc/kubernetes/pki/etcd/peer CART_NAME=${PKI_PATH}/peer subject_alt_name=$(cert::get_subject_alt_name ${CART_NAME}) cert::gen_cert "${CART_NAME}" "peer" "/CN=etcd-peer" "${CAER_DAYS}" "${subject_alt_name}" # generate etcd healthcheck-client certificate # /etc/kubernetes/pki/etcd/healthcheck-client CART_NAME=${PKI_PATH}/healthcheck-client cert::gen_cert "${CART_NAME}" "client" "/O=system:masters/CN=kube-etcd-healthcheck-client" "${CAER_DAYS}" # generate apiserver-etcd-client certificate # /etc/kubernetes/pki/apiserver-etcd-client check_file "${CA_CERT}" check_file "${CA_KEY}" PKI_PATH=${KUBE_PATH}/pki CART_NAME=${PKI_PATH}/apiserver-etcd-client cert::gen_cert "${CART_NAME}" "client" "/O=system:masters/CN=kube-apiserver-etcd-client" "${CAER_DAYS}" # restart etcd docker ps | awk '/k8s_etcd/{print$1}' | xargs -r -I '{}' docker restart {} || true log::info "restarted etcd" } cert::update_master_cert() { PKI_PATH=${KUBE_PATH}/pki CA_CERT=${PKI_PATH}/ca.crt CA_KEY=${PKI_PATH}/ca.key check_file "${CA_CERT}" check_file "${CA_KEY}" # generate apiserver server certificate # /etc/kubernetes/pki/apiserver CART_NAME=${PKI_PATH}/apiserver subject_alt_name=$(cert::get_subject_alt_name ${CART_NAME}) cert::gen_cert "${CART_NAME}" "server" "/CN=kube-apiserver" "${CAER_DAYS}" "${subject_alt_name}" # generate apiserver-kubelet-client certificate # /etc/kubernetes/pki/apiserver-kubelet-client CART_NAME=${PKI_PATH}/apiserver-kubelet-client cert::gen_cert "${CART_NAME}" "client" "/O=system:masters/CN=kube-apiserver-kubelet-client" "${CAER_DAYS}" # generate kubeconf for controller-manager,scheduler,kubectl and kubelet # /etc/kubernetes/controller-manager,scheduler,admin,kubelet.conf cert::update_kubeconf "${KUBE_PATH}/controller-manager" cert::update_kubeconf "${KUBE_PATH}/scheduler" cert::update_kubeconf "${KUBE_PATH}/admin" # check kubelet.conf # https://github.com/kubernetes/kubeadm/issues/1753 set +e grep kubelet-client-current.pem /etc/kubernetes/kubelet.conf > /dev/null 2>&1 kubelet_cert_auto_update=$? set -e if [[ "$kubelet_cert_auto_update" == "0" ]]; then log::warning "does not need to update kubelet.conf" else cert::update_kubeconf "${KUBE_PATH}/kubelet" fi # generate front-proxy-client certificate # use front-proxy-client ca CA_CERT=${PKI_PATH}/front-proxy-ca.crt CA_KEY=${PKI_PATH}/front-proxy-ca.key check_file "${CA_CERT}" check_file "${CA_KEY}" CART_NAME=${PKI_PATH}/front-proxy-client cert::gen_cert "${CART_NAME}" "client" "/CN=front-proxy-client" "${CAER_DAYS}" # restart apiserve, controller-manager, scheduler and kubelet docker ps | awk '/k8s_kube-apiserver/{print$1}' | xargs -r -I '{}' docker restart {} || true log::info "restarted kube-apiserver" docker ps | awk '/k8s_kube-controller-manager/{print$1}' | xargs -r -I '{}' docker restart {} || true log::info "restarted kube-controller-manager" docker ps | awk '/k8s_kube-scheduler/{print$1}' | xargs -r -I '{}' docker restart {} || true log::info "restarted kube-scheduler" systemctl restart kubelet log::info "restarted kubelet" } main() { local node_tpye=$1 KUBE_PATH=/etc/kubernetes CAER_DAYS=3650 # backup $KUBE_PATH to $KUBE_PATH.old-$(date +%Y%m%d) cert::backup_file "${KUBE_PATH}" case ${node_tpye} in etcd) # update etcd certificates cert::update_etcd_cert ;; master) # update master certificates and kubeconf cert::update_master_cert ;; all) # update etcd certificates cert::update_etcd_cert # update master certificates and kubeconf cert::update_master_cert ;; *) log::err "unknow, unsupported certs type: ${cert_type}, supported type: all, etcd, master" printf "Documentation: https://github.com/yuyicai/update-kube-cert example: '\033[32m./update-kubeadm-cert.sh all\033[0m' update all etcd certificates, master certificates and kubeconf /etc/kubernetes ├── admin.conf ├── controller-manager.conf ├── scheduler.conf ├── kubelet.conf └── pki ├── apiserver.crt ├── apiserver-etcd-client.crt ├── apiserver-kubelet-client.crt ├── front-proxy-client.crt └── etcd ├── healthcheck-client.crt ├── peer.crt └── server.crt '\033[32m./update-kubeadm-cert.sh etcd\033[0m' update only etcd certificates /etc/kubernetes └── pki ├── apiserver-etcd-client.crt └── etcd ├── healthcheck-client.crt ├── peer.crt └── server.crt '\033[32m./update-kubeadm-cert.sh master\033[0m' update only master certificates and kubeconf /etc/kubernetes ├── admin.conf ├── controller-manager.conf ├── scheduler.conf ├── kubelet.conf └── pki ├── apiserver.crt ├── apiserver-kubelet-client.crt └── front-proxy-client.crt " exit 1 esac } main "$@"
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
- 166
- 167
- 168
- 169
- 170
- 171
- 172
- 173
- 174
- 175
- 176
- 177
- 178
- 179
- 180
- 181
- 182
- 183
- 184
- 185
- 186
- 187
- 188
- 189
- 190
- 191
- 192
- 193
- 194
- 195
- 196
- 197
- 198
- 199
- 200
- 201
- 202
- 203
- 204
- 205
- 206
- 207
- 208
- 209
- 210
- 211
- 212
- 213
- 214
- 215
- 216
- 217
- 218
- 219
- 220
- 221
- 222
- 223
- 224
- 225
- 226
- 227
- 228
- 229
- 230
- 231
- 232
- 233
- 234
- 235
- 236
- 237
- 238
- 239
- 240
- 241
- 242
- 243
- 244
- 245
- 246
- 247
- 248
- 249
- 250
- 251
- 252
- 253
- 254
- 255
- 256
- 257
- 258
- 259
- 260
- 261
- 262
- 263
- 264
- 265
- 266
- 267
- 268
- 269
- 270
- 271
- 272
- 273
- 274
- 275
- 276
- 277
- 278
- 279
- 280
- 281
- 282
- 283
- 284
- 285
- 286
- 287
- 288
- 289
- 290
- 291
- 292
- 293
- 294
- 295
- 296
- 297
- 298
- 299
- 300
- 301
- 302
- 303
- 304
- 305
- 306
- 307
- 308
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/小丑西瓜9/article/detail/247509
推荐阅读
相关标签



