How to Join the vCSA 6.5 to an Active Directory Domain
In vSphere 6.5 the underlying operating system from the vCenter Server Appliance (vCSA) has been changed to VMwares PhotonOS. With the new OS, you can still join an Active Directory domain to comply with company policies, or if you want to use windows session authentication. Joining an Active Directory domain is included in the infrastructure node configuration which is part of the Platform Services Controller. Please verify standard AD requirements like time synchronization and naming prior to joining a domain.
If you want to log in with the "Windows session authentication" checkbox, you have to add the appliance running the Platform Services Controller (PSC) to the domain. For embedded deployments, join the appliance running both, the vCenter and the PSC to the domain.
Join AD Domain with the vSphere Web Client
Open vSphere Web Client (https://[vcenter]/vsphere-client)
Login as Single Sign-On Administrator or a user with global permissions.
Navigate to Administration > Deployment > System Configuration

Open Nodes and select the vCenter or external PSC

Navigate to Manage > Settings > Advanced > Active Directory and click Join...

Enter AD domain information

Press OK
You don't see the configured domain immediately, you have to reboot the Appliance.
Hint: You can reboot infrastructure nodes from the context menu
When the appliance is back online it is part of the Active Directory domain
Join AD Domain from the Command Line
(optional) Enable SSH login
vSphere Web Client > Administration > Deployment > System Configuration > Nodes > Manage > Settings > Access
Connect to the vCenter Server Appliance with SSH
Activate the bash shell
Command> shell
Use the domainjoin-cli tool to join the domain
# /opt/likewise/bin/domainjoin-cli join [domain] [user name] [password]

Reboot the appliance
# reboot
When the appliance is back online it is part of the Active Directory domain
Verify Domain Status
Verify domain status from the domain controller
Verify domain status with the vSphere Web Client
Verify domain status from vCSA command line:
# /opt/likewise/bin/domainjoin-cli query

How to add AD Authentication in vCenter 6.5
The vCenter Server has an internal user database that allows you to add and manage users with the vSphere Web Client. Users management and Single Sign-On is provided by the Platform Service Controller which is available since vSphere 6.0. In a large environment, you might want to connect your virtualization infrastructure to a centrally manage Active Directory.
This article explains how to add AD authentication in vSphere 6.5 and how to get the "Use Windows session authentication" checkbox to work with the enhanced authentication plugin. This works for both, the vCenter Server 6.5 installed on a Windows Server and the vCenter Server Appliance (vCSA).
Open vSphere Web Client (https://[vcenter]/vsphere-client)
Login as Single Sign-On Administrator (Password set during installation)
Navigate to Administration > Single Sign-On > Configuration

Open the Identity Sources tab
Click the green + to add an identity source
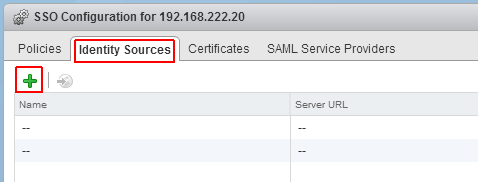
Select Identity Source Type:
A) Active Directory (Integrated Windows Authentication)
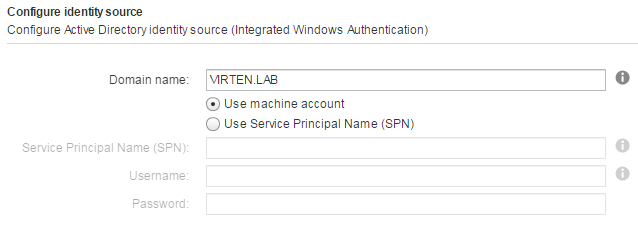
This option works with both, the Windows-based vCenter Server and the vCenter Server Appliance. The underlying system has to be a member of the Active Directory domain. (To join the vCSA to an AD, read this post.)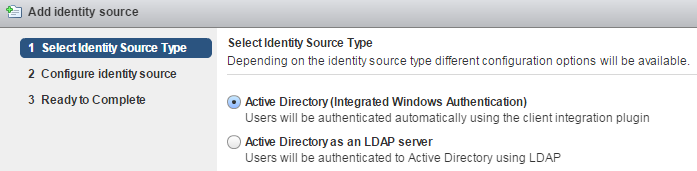
 B) Active Directory as a LDAP Server
B) Active Directory as a LDAP Server
If the underlying system is not part of the Active Directory domain.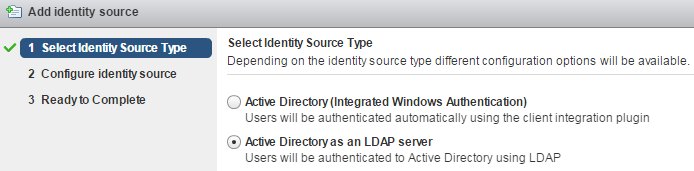 Fill out the remaining fields as follows:
Fill out the remaining fields as follows:Name: Label for identification
Base DN for users: The Distinguished Name (DN) of the starting point for directory server searches. Example: If your domain name is virten.lab the DN for the entire directory is "DC=virten,DC=lab".
Base DN for groups: The Distinguished Name (DN) of the starting point for directory server searches.
Domain name: Your domain name. Example: "virten.lab"
Domain alias: Your NetBIOS name. Example: "virten"
Username: A user in the AD Domain with at least browse privileges. Example virten\vcenterssoSelect "Connect to any domain controller in the domain" of you want to use DNS to identify domain controllers or configure static primary and secondary URLs. When using static entries, you can either query the local directory (Port 389), or the global catalog (Port 3268).
Example: "ldap://dc01.virten.lab:3268"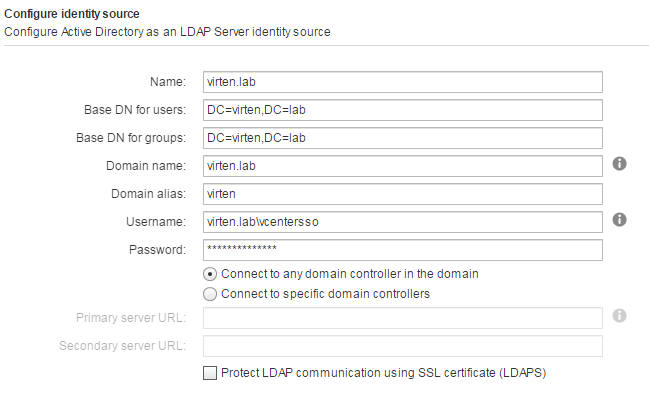
Click Next and finish the configuration wizard
Back at Identity Sources your AD should appear in the list and from now on you are able to assign vCenter permissions to users and groups from your active directory.
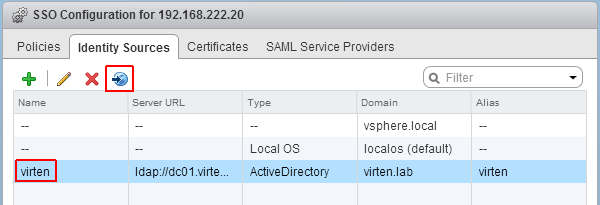
Select you Active Directory and click the world with arrow button to make AD to your default domain.
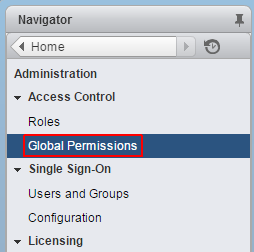
To login with AD users, you have to set permissions. To add a AD user as global Administrator navigate to Administration > Access Control > Global Permissions
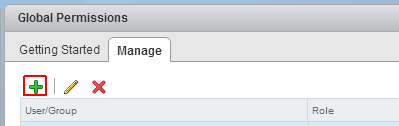
Click Add permission
Click Add...
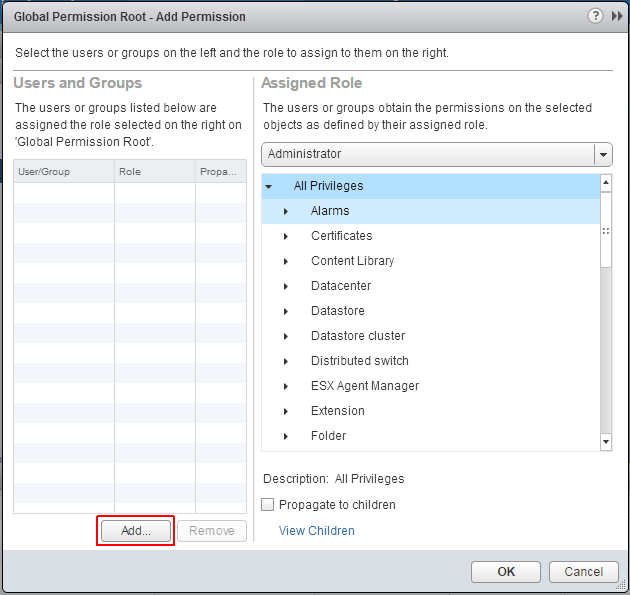
Select the Active Directory domain under Domain, choose a user and press Add
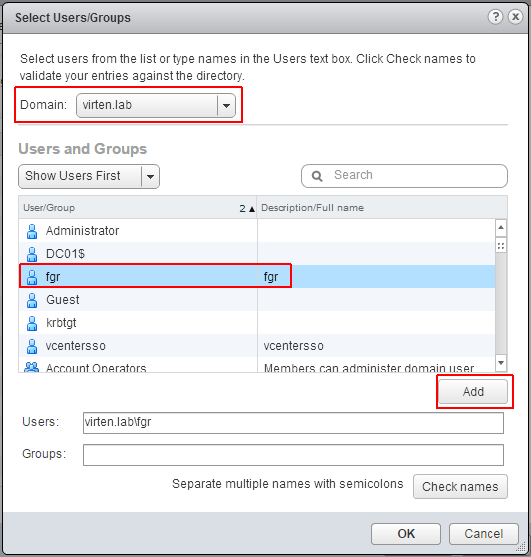
Press OK twice
You should now be able to login to the vCenter 6.5 with your Active Directory account.
Use Windows session authentication
The "Use Windows session authentication" checkbox is disabled unless the Enhanced Authentication Plugin is installed. You can find the download link at the bottom of the login screen.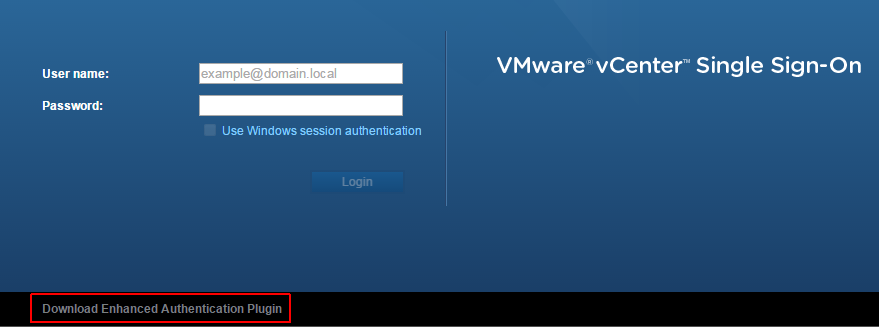
The vCenter Single Sign-On server is not currently joined to any domain.
When the following message is displayed:
The vCenter Single Sign-On server is not currently joined to any domain. You cannot complete the current operation.
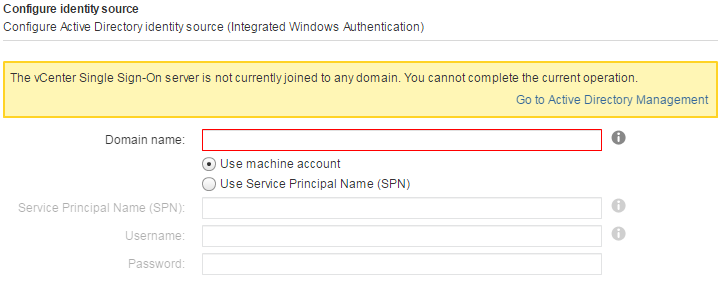
Join the underlying operating system to an Active Directory domain or use this guide to add the vCenter Server Appliance is an AD.


