- 1docker安装postgresql_docker postgres
- 2gitee的操作(创建仓库-克隆本地-提交代码-分支管理)_gitte 怎么提交merge
- 3爱心代码(C语言简易版本)_爱心代码编程c语言简单
- 4面试:Promise.all一个请求失败也能得到其余正确的请求结果_promise.all有一个报错后面的数据怎么获取
- 5LEECODE:DFS算法(104、494、547、37)——java实现
- 6手把手教你安装python第三方库_python手动安装第三方库_python第三方库手动安装方法
- 7【Unity声音与视频播放】播放声音视频、代码控制、UI播放视频_unity 播放声音
- 8springBoot集成Kafka
- 9Seq2Seq+Attention生成式文本摘要_生成式摘要算法
- 10[日语学习] 稻妻_农夫导航
如何正确使用Nessus进行基线(合规)管理_nessus基线
赞
踩
如何正确使用Nessus进行基线(合规)管理
本文重点介绍如何使用Nessus工具进行基线的定制和管理。
1. 基线的基本概念
安全基线是一组配置设置要求,它由多个元子化的基线条目组成,每一个基线条目均会对安全设置产生影响。 企业的安全配置要求可能来自于您企业内部的信息安全政策,合规性要求,安全团队,甚至是产品组、合作伙伴和客户的反馈。您将这些安全配置要求组合在一起,就可以初步形成能满足您企业运行要求的安全基线。
2. 安全基线的难点
- 配置项多
例如仅Windows 10就有超过3000个组策略设置,其中不包括超过 1800 个 Internet Explorer 11 设置。 在这 4800 个设置中,只有一部分与安全相关。而且您还必须自行确定每个设置的安全影响。 然后,您还需要确定每个设置的相应值。
因此在企业定制安全基线时,建议采纳国内外专业机构编制的安全基线规范,其中CIS就是业内使用最广泛,最权威的基线标准。
当前国际范围内还有:
DISA(美国国防信息系统局)标准
MSCT(Microsoft Security Compliance Toolkit)标准
信息安全等级保护标准
等… - 需要进行大量测试
以CIS的CentOS 7 基线为例,共有300多个检查项,这些检查项不一定全部适用于您组织的需要,例如启用SELINUX,如果没有SElinux方面的专业人事,启用该功能是一个危害的操作,这可能导致你的业务无法运行,因此认真阅读和测试每个基线条目是您必须要进行的基本操作。
3. 如何使用Nessus进行基线扫描
Nessus进行基线扫描,根据Nessus的部署方式不同,有2种方法:
3.1 方法一:基于用户名密码方式扫描
在Linux下,基线扫描的本质是检查各个配置文件的键和值,因此必须进行登陆扫描。(Windows下主要是检查注册表的键值)
操作步骤:
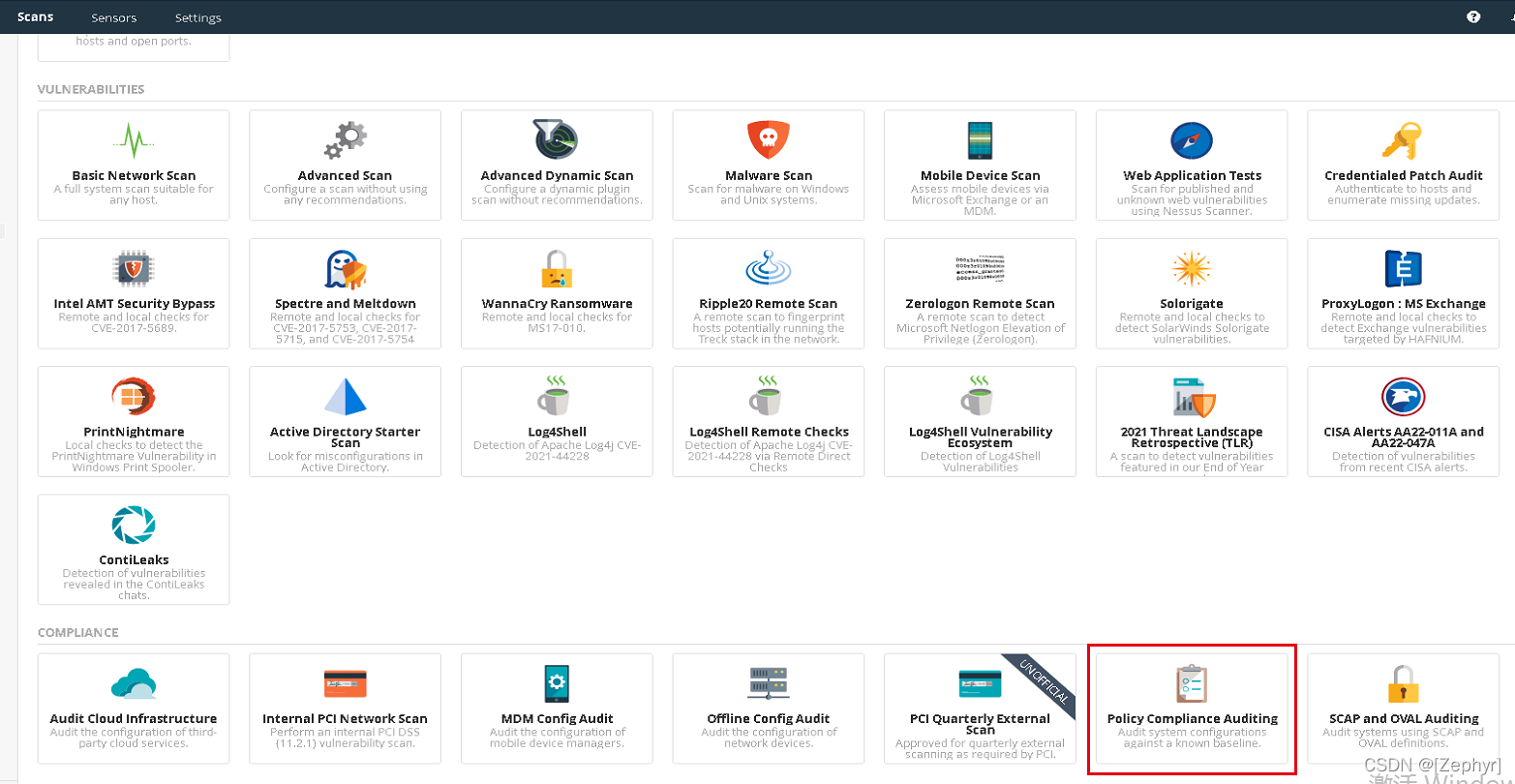
- 登陆nessus,选择Scans->New Scan->Policy Compliance Auditing
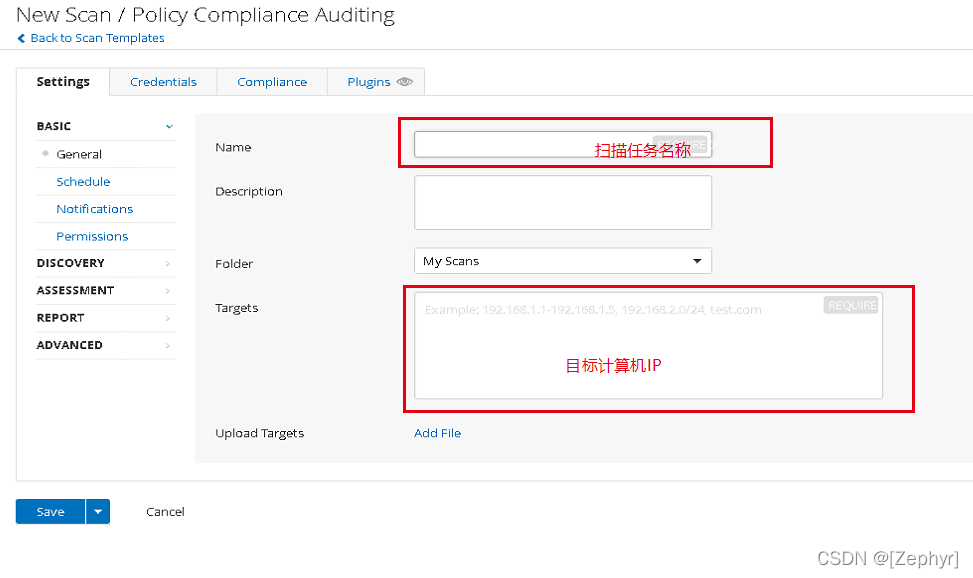
- 在Settings界面输入任务名称和目标计算机IP。
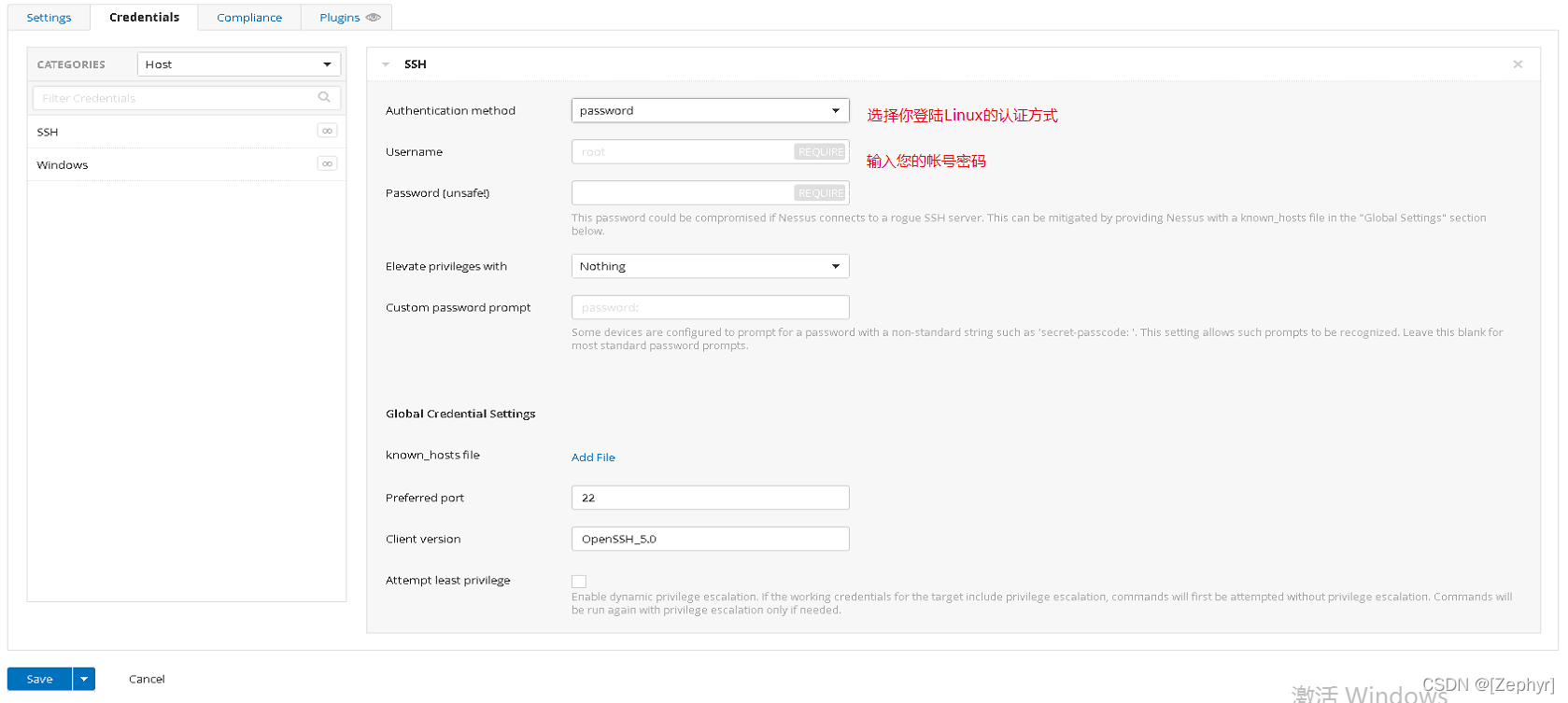
- 进入Credentials选项卡左侧选择:如果是Linux或网络设备选择SSH登陆,如果是Windows选择Windows。
在Authentication method中选择您的登陆方式,如果是Linux,并使用帐号密码登陆,请选择Password,并输入username和password
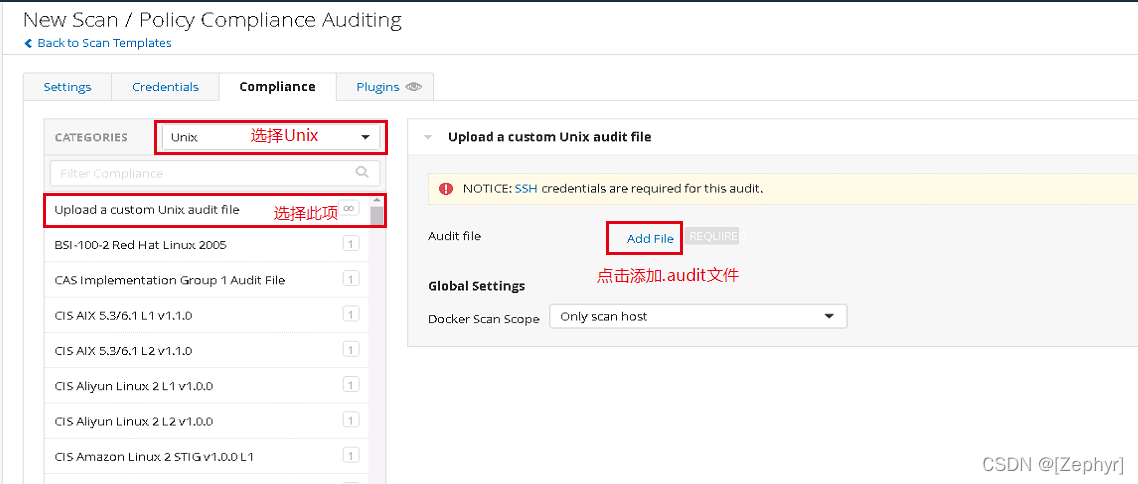
- 在Compliance选项卡,如果是Centos 7请在输入框中输入centos 7进行基线搜索。然后点击如“CIS CentOS 7 v3.1.2 Server L1”,将该基线标准添加到扫描队列。
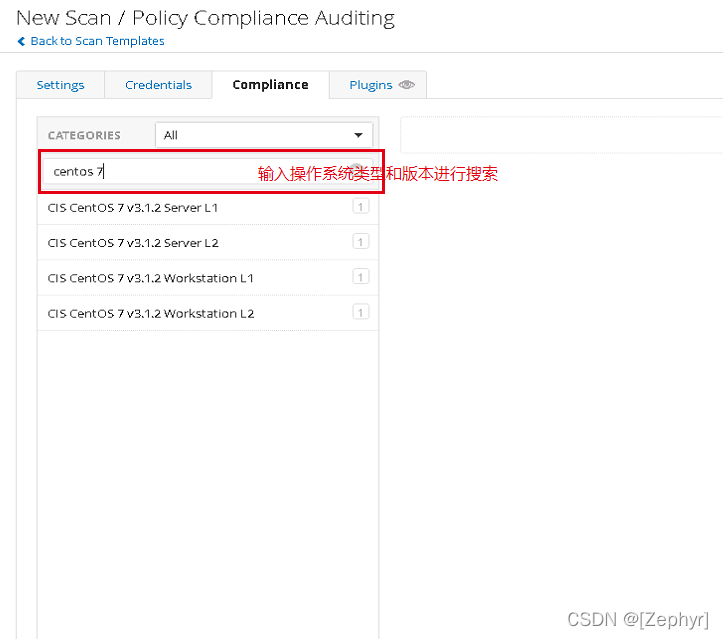
- 配置基线:
在您添加好基线标准后,比如“CIS CentOS 7 v3.1.2 Server L1”,会出现配置界面,需要根据您组织的实际情况进行配置。
比如: 登陆Banner消息、时间服务器IP、日志服务器IP等,请根据您企业的实际情况进行配置。
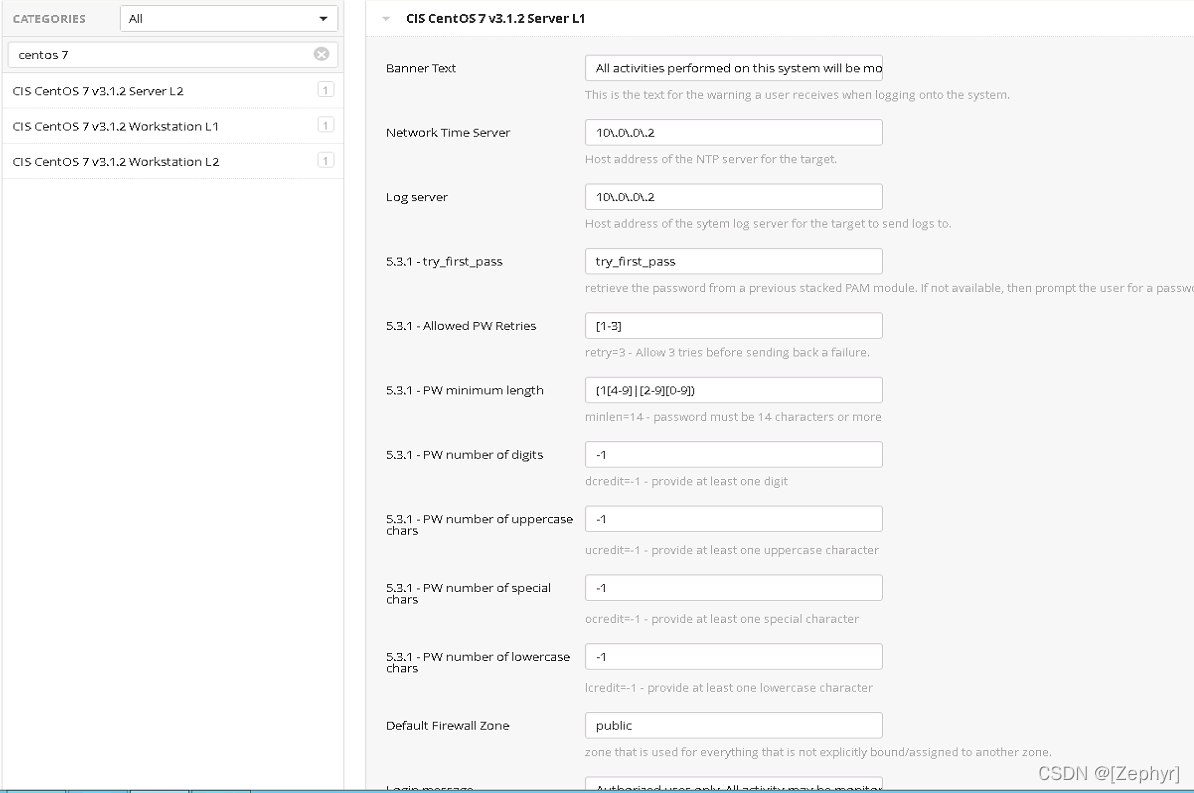
- 配置完成后,点击正文的Save保存,进行到你的任务目录,点击三角形按钮就可以开始您的基线扫描。
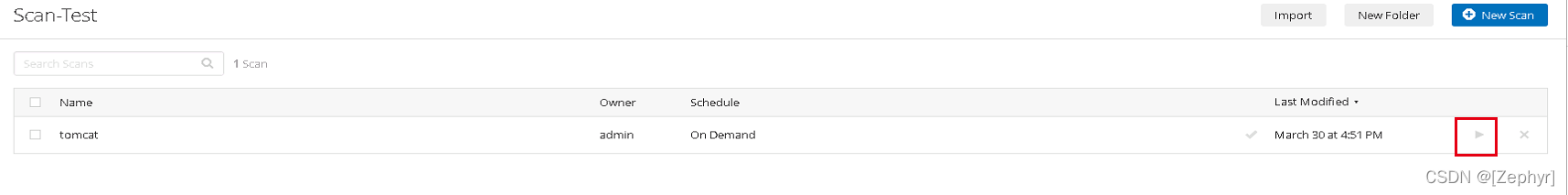
扫描任务保存后,无需再次配置,可以进行多次扫描。
您也可以下载.audit文件,您可以修改.audit做好预配置,扫描时直接上传该文件。
3.2 方法二: Agent方式扫描
- 登陆nessus,选择Scans->New Scan->Agnet->Policy Compliance Auditing
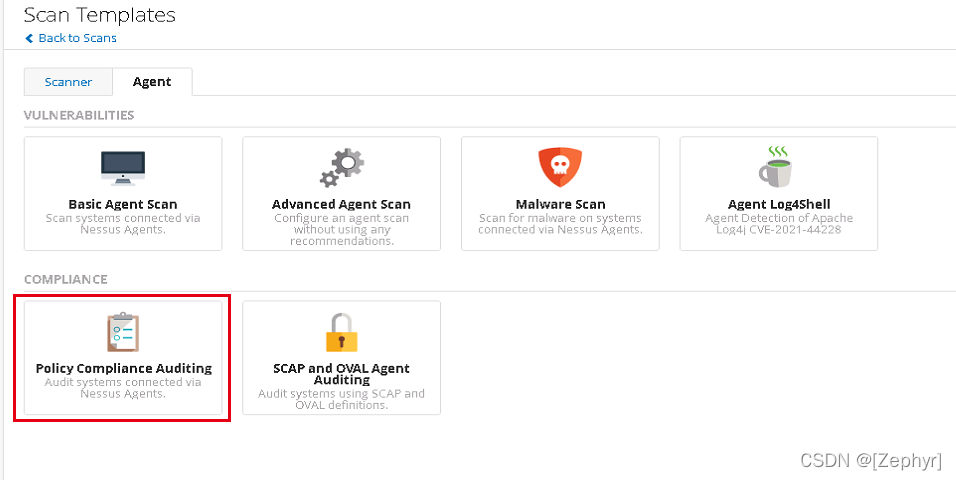
- 配置与用户名密码扫描类似。
前提: 必须安装Nessus Manager并在环境中部署Nessus Agent。
优势: 扫描时无需在扫描器上输入密码,且扫描速度快,网络流量低。
4. 编辑.audit基线脚本
4.1 下载.audit文件
上文提到了Nessus进行基线扫描时,可以加载.audit文件。.audit文件是Nessus专用的基线检查脚本文件,该文件使用YML语言定义了一系列基线检查条目,感兴趣的同学可以点击此处下载。
4.2 .audit文件说明
解压下载的audits.tar.gz包,以CIS_Google_Chrome_L1_v2.1.0.audit文件为例。
以下截取部分内容:
<check_type:"Windows" version:"2"> <group_policy:"Google Chrome"> <if> <condition type:"OR"> <custom_item> type : REG_CHECK description : "Check if Chrome is installed - ApplicationName" value_type : POLICY_TEXT value_data : "HKLM\Software\Clients\Startmenuinternet\Google Chrome\Capabilities" reg_option : MUST_EXIST key_item : "ApplicationName" </custom_item> <custom_item> type : REG_CHECK description : "Check if Chrome is installed - DisplayName" value_type : POLICY_TEXT value_data : "HKLM\Software\Microsoft\Windows\Currentversion\Uninstall\Google Chrome" reg_option : MUST_EXIST key_item : "DisplayName" </custom_item> </condition> <then> <custom_item> type : REGISTRY_SETTING description : "1.1.1 Ensure 'Cross-origin HTTP Authentication prompts' is set to 'Disabled'" info : "This setting controls whether third-party sub-content can open a HTTP Basic Auth dialog and is typically disabled. The recommended state for this setting is: Disabled (0) Rationale: This setting is typically disabled to help combat phishing attempts. Impact: None - This is the default behavior." solution : "To establish the recommended configuration via GP, set the following UI path to Disabled: Computer Configuration\Policies\Administrative Templates\Google\Google Chrome\HTTP authentication\Cross-origin HTTP Authentication prompts Default Value: Unset (Same as Disabled, but user can change)" reference : "800-171|3.4.2,800-53|CM-6b.,CIS_Recommendation|1.1.1,CN-L3|8.1.10.6(d),CSF|PR.IP-1,ITSG-33|CM-6b.,LEVEL|1A,NESA|T3.2.1,SWIFT-CSCv1|2.3" see_also : "https://workbench.cisecurity.org/files/3653" value_type : POLICY_DWORD value_data : 0 reg_key : "HKLM\Software\Policies\Google\Chrome" reg_item : "AllowCrossOriginAuthPrompt" reg_option : CAN_NOT_BE_NULL </custom_item> </then> <else> <report type:"WARNING"> description : "CIS_Google_Chrome_L1_v2.1.0.audit from CIS Google Chrome Benchmark v2.1.0" info : "NOTE: Nessus has not identified that the chosen audit applies to the target device." see_also : "https://workbench.cisecurity.org/files/3653" </report> </else> </if> </group_policy> </check_type>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
以上文为例,整个.audit文件的基本结构,如下:
- 最外层为
<check_type> </check_type>定义了检查脚本文件的类型,如<check_type:"Windows" version:"2">则定义了检查类型为"Windows",版本号为"2"。 <group_policy></group_policy>定义了检查策略,如"Google Chrome",此项为非必需项。如:CIS_CentOS_7_v3.1.2_Server_L1.audit文件中没有此项定义。<if><then></then><else></else></if>类似于编程语言中的if …else…,<if><then>之间为条件检查,nessus读取.audit文件后首先会运行此检查,如果之间的检查条件不满足,则运行<else></else>中的内容。<condition type:"OR"> </condition>指定为OR(或)检查,也可以为AND(与)。<custom_item> </custom_item>中定义了检查的具体内容,.audit文件由多个<custom_item></custom_item>组成。
<custom_item> type : REGISTRY_SETTING #定义了检查类型为注册表设置 description : "1.1.1 Ensure 'Cross-origin HTTP Authentication prompts' is set to 'Disabled'" #定义检查项的名称 info : "This setting controls whether third-party sub-content can open a HTTP Basic Auth dialog and is typically disabled. The recommended state for this setting is: Disabled (0) Rationale: This setting is typically disabled to help combat phishing attempts. Impact: None - This is the default behavior." solution : "To establish the recommended configuration via GP, set the following UI path to Disabled: Computer Configuration\Policies\Administrative Templates\Google\Google Chrome\HTTP authentication\Cross-origin HTTP Authentication prompts Default Value: Unset (Same as Disabled, but user can change)" #定义了检查项的描述信息 reference : "800-171|3.4.2,800-53|CM-6b.,CIS_Recommendation|1.1.1,CN-L3|8.1.10.6(d),CSF|PR.IP-1,ITSG-33|CM-6b.,LEVEL|1A,NESA|T3.2.1,SWIFT-CSCv1|2.3" #参考资料 see_also : "https://workbench.cisecurity.org/files/3653" #参考网站 value_type : POLICY_DWORD #检查值类型 value_data : 0 #注册表值 reg_key : "HKLM\Software\Policies\Google\Chrome" #注册表位置 reg_item : "AllowCrossOriginAuthPrompt" #注册表键 reg_option : CAN_NOT_BE_NULL #不能为空
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
4.3 .audit文件修改举例
以Linux下检查日志接收服务器配置为例:
<custom_item> system : "Linux" type : CMD_EXEC description : "4.2.1.5 Ensure rsyslog is configured to send logs to a remote log host" info : "The rsyslog utility supports the ability to send logs it gathers to a remote log host running syslogd(8) or to receive messages from remote hosts, reducing administrative overhead. Note: Ensure that the selection of logfiles being sent follows local site policy Rationale: Storing log data on a remote host protects log integrity from local attacks. If an attacker gains root access on the local system, they could tamper with or remove log data that is stored on the local system NOTE: Nessus did not detect that rsyslogd was listening on any open ports, and as a result has scanned this target as a rsyslog client." solution : "Edit the /etc/rsyslog.conf and /etc/rsyslog.d/*.conf files and add one of the following lines: Newer syntax: <files to sent to the remote log server> action(type='omfwd' target='<FQDN or ip of loghost>' port='<port number>' protocol='tcp' action.resumeRetryCount='<number of re-tries>' queue.type='LinkedList' queue.size=<number of messages to queue>') Example: *.* action(type='omfwd' target='192.168.2.100' port='514' protocol='tcp' action.resumeRetryCount='100' queue.type='LinkedList' queue.size='1000') Older syntax: *.* @@<FQDN or ip of loghost> Example: *.* @@192.168.2.100 Run the following command to reload the rsyslog configuration: # systemctl restart rsyslog" reference : "800-171|3.3.8,800-53|AU-9(2),CIS_Recommendation|4.2.1.5,CN-L3|8.1.3.5(d),CN-L3|8.1.4.3(c),CSCv7|6.6,CSCv7|6.8,CSF|PR.PT-1,ISO/IEC-27001|A.12.4.2,ITSG-33|AU-9(2),LEVEL|1A,NESA|M5.2.3,NESA|M5.5.2,NIAv2|SS13e,QCSC-v1|8.2.1,QCSC-v1|13.2" see_also : "https://workbench.cisecurity.org/files/3490" # Note: Variable @SYSLOG_SERVER@ replaced with "10\\.0\\.0\\.2" in field "cmd". cmd : "/usr/bin/egrep '^\\*\\.\\*[^I][^I]*\\@\\@10\\.0\\.0\\.2' /etc/rsyslog.conf /etc/rsyslog.d/*.conf | /usr/bin/awk '{print} END {if (NR != 0) print \"pass\" ; else print \"fail\"}'" expect : "pass" </custom_item>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
此项定义了日志服务器的IP和端口,默认情况下检查脚本会检查rsyslog.conf文件中是否配置了*.* @10.0.0.2,这基本上不符合您组织的实际需求,此时则需要修改.audit文件,以符合您组织的实际情况。
例如,您组织的syslog服务器IP为192.168.1.100,则需要您修改@10\\.0\\.0\\.2部分为@192\\.168\\.1\\.100。
最终结果为:cmd : "/usr/bin/egrep '^\\*\\.\\*[^I][^I]*\\@\\@192\\.168\\.1\\.100' /etc/rsyslog.conf /etc/rsyslog.d/*.conf | /usr/bin/awk '{print} END {if (NR != 0) print \"pass\" ; else print \"fail\"}'" ,修改完毕保存该文件,重新上传到Nessus扫描器。
此外,如果只是修改一个条目就要运行一次Nessus扫描,工作效率较低,您也可以将以上命令复制出来,注意去掉命令中的转义反斜杠。在命令行下运行:
[root@rsyslog_uatdevice ~]# /usr/bin/egrep '^\\*\\.\\*[^I][^I]*\\@\\@10\\.0\\.0\\.2' /etc/rsyslog.conf /etc/rsyslog.d/*.conf | /usr/bin/awk '{print} END {if (NR != 0) print "pass" ; else print "fail"}'
fail
- 1
- 2