热门标签
热门文章
- 1ElasticSearch7.0 关联查询之父子文档及RestHighLevelClient实现_indexrequest写父子文档内容
- 2Android渐变色_"android:angle=\"45"
- 3pandas报错FutureWarning: elementwise comparison failed...的解决办法_e:\annaconda\lib\site-packages\pandas\_testing.py:
- 4Git下载安装教程:Git安装步骤手把手图文【超详细】
- 510秒完成pip在线安装(Linux、Windows通用)_linux 安装pip
- 6【论文阅读】Patch n‘ Pack: NaViT, a Vision Transformer for any Aspect Ratio and Resolution_patch n’ pack: navit, a vision transformer for any
- 7MediaMate for mac v3.2.0 开心版 把MacBook 刘海变成动态岛 使用注意事项_mediamate 免费
- 8【Oracle】关于表外键相关查询_oracle 查询外键
- 9最详细的ubuntu 安装 docker教程,文末获取实用干货大礼包!_ubuntu docker
- 10华为实习校招机试真题目录
当前位置: article > 正文
RabbitMQ配置SSL_rabbitmq ssl
作者:知新_RL | 2024-04-20 16:02:22
赞
踩
rabbitmq ssl
引言
主要介绍了如何通过Docker安装RabbitMQ并配置SSL;配置成功之后给出了SpringBoot和Python集成的例子。
生成证书
$ git clone https://github.com/Berico-Technologies/CMF-AMQP-Configuration.git
$ cd CMF-AMQP-Configuration/ssl/
# Greyfoss 为自定义的证书签发机构名称,该脚本会生成一个ca目录,存储证书颁发机构的信息以及签发的证书
$ sh setup_ca.sh Greyfoss
# 生成服务端公钥和私钥 rabbit-server为生成的密钥前缀 123456为该秘钥自定义的密码
$ sh make_server_cert.sh rabbit-server 123456
# 生成客户端公钥和私钥
$ sh create_client_cert.sh rabbit-client 123456
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
生成Java客户端需要的证书
使用java的keytool工具生成客户端需要的证书。
keytool -import -alias rabbit-server -file server/rabbit-server.cert.pem -keystore server.keystore -storepass 123456
- 1
- import 将已签名数字证书导入密钥库
- alias 指定导入条目的别名
- file 指定要导入的证书
- keystore 指定密钥库的名称
- storepass 指定生成密钥库的密码
运行该命令会生成密钥库文件server.keystore。
安装Rabbitmq配置SSL
先启动rabbitmq容器
docker run --name rabbitmq --restart=unless-stopped -d -p 5672:5672 -p 15672:15672 rabbitmq:management
- 1
在宿主机上创建以下文件夹:
mkdir -p ~/rabbitmq/etc/rabbitmq/ssl
- 1
拷贝容器中的文件到宿主机~/rabbitmq/etc/rabbitmq/目录下:
$ docker cp rabbitmq:/etc/rabbitmq/conf.d ~/rabbitmq/etc/rabbitmq/
$ docker cp rabbitmq:/etc/rabbitmq/enabled_plugins ~/rabbitmq/etc/rabbitmq/
$ docker cp rabbitmq:/etc/rabbitmq/rabbitmq.conf ~/rabbitmq/etc/rabbitmq/
- 1
- 2
- 3
拷贝需要的证书到~/rabbitmq/etc/rabbitmq/ssl下
$ cp server/rabbit-server.cert.pem ~/rabbitmq/etc/rabbitmq/ssl/
$ cp server/rabbit-server.key.pem ~/rabbitmq/etc/rabbitmq/ssl/
$ cp ca/cacert.pem ~/rabbitmq/etc/rabbitmq/ssl/
- 1
- 2
- 3
编辑~/rabbitmq/etc/rabbitmq/rabbitmq.conf文件,替换为以下内容:
# 禁用非tls连接 listeners.tcp = none # SSL\TLS通信的端口 listeners.ssl.default = 5671 # 管理控制台端口 management.tcp.port = 15672 # 服务端私钥和证书文件配置 ssl_options.cacertfile = /etc/rabbitmq/ssl/cacert.pem ssl_options.certfile = /etc/rabbitmq/ssl/rabbit-server.cert.pem ssl_options.keyfile = /etc/rabbitmq/ssl/rabbit-server.key.pem # 有verify_none和verify_peer两个选项,verify_none表示完全忽略验证证书的结果,verify_peer表示要求验证对方证书 ssl_options.verify = verify_peer # 若为true,服务端会向客户端索要证书,若客户端无证书则中止SSL握手;若为false,则客户端没有证书时依然可完成SSL握手 ssl_options.fail_if_no_peer_cert = true # 指定开启的tls版本 ssl_options.versions.1=tlsv1.2 ssl_options.versions.2=tlsv1.1 # 指定对应的cipher suites ssl_options.ciphers.1 = ECDHE-ECDSA-AES256-GCM-SHA384 ssl_options.ciphers.2 = ECDHE-RSA-AES256-GCM-SHA384 ssl_options.ciphers.3 = ECDHE-ECDSA-AES256-SHA384 ssl_options.ciphers.4 = ECDHE-RSA-AES256-SHA384 ssl_options.ciphers.5 = ECDHE-ECDSA-DES-CBC3-SHA ssl_options.ciphers.6 = ECDH-ECDSA-AES256-GCM-SHA384 ssl_options.ciphers.7 = ECDH-RSA-AES256-GCM-SHA384 ssl_options.ciphers.8 = ECDH-ECDSA-AES256-SHA384 ssl_options.ciphers.9 = ECDH-RSA-AES256-SHA384 ssl_options.ciphers.10 = DHE-DSS-AES256-GCM-SHA384 ssl_options.ciphers.11= DHE-DSS-AES256-SHA256 ssl_options.ciphers.12 = AES256-GCM-SHA384 ssl_options.ciphers.13 = AES256-SHA256 ssl_options.ciphers.14 = ECDHE-ECDSA-AES128-GCM-SHA256 ssl_options.ciphers.15 = ECDHE-RSA-AES128-GCM-SHA256 ssl_options.ciphers.16 = ECDHE-ECDSA-AES128-SHA256 ssl_options.ciphers.17 = ECDHE-RSA-AES128-SHA256 ssl_options.ciphers.18 = ECDH-ECDSA-AES128-GCM-SHA256 ssl_options.ciphers.19= ECDH-RSA-AES128-GCM-SHA256 ssl_options.ciphers.20 = ECDH-ECDSA-AES128-SHA256 ssl_options.ciphers.21 = ECDH-RSA-AES128-SHA256 ssl_options.ciphers.22 = DHE-DSS-AES128-GCM-SHA256 ssl_options.ciphers.23 = DHE-DSS-AES128-SHA256 ssl_options.ciphers.24 = AES128-GCM-SHA256 ssl_options.ciphers.25 = AES128-SHA256 ssl_options.ciphers.26 = ECDHE-ECDSA-AES256-SHA ssl_options.ciphers.27 = ECDHE-RSA-AES256-SHA ssl_options.ciphers.28 = DHE-DSS-AES256-SHA ssl_options.ciphers.29 = ECDH-ECDSA-AES256-SHA ssl_options.ciphers.30 = ECDH-RSA-AES256-SHA ssl_options.ciphers.31= AES256-SHA ssl_options.ciphers.32 = ECDHE-ECDSA-AES128-SHA ssl_options.ciphers.33 = ECDHE-RSA-AES128-SHA ssl_options.ciphers.34 = DHE-DSS-AES128-SHA ssl_options.ciphers.35 = DHE-DSS-AES128-SHA256 ssl_options.ciphers.36 = ECDH-ECDSA-AES128-SHA ssl_options.ciphers.37 = ECDH-RSA-AES128-SHA ssl_options.ciphers.38 = AES128-SHA
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
删除正在运行的rabbitmq:
docker rm -f rabbitmq
- 1
使用下面命令重新创建rabbitmq容器
docker run --restart=unless-stopped -d \
-p 15672:15672 -p 5671:5671 \
-v /home/yjw/rabbitmq/etc/rabbitmq/:/etc/rabbitmq/ \
--name rabbitmq \
rabbitmq:management
- 1
- 2
- 3
- 4
- 5
docker logs -f rabbitmq 看到日志内以下内容说明配置成功。
2021-07-09 02:47:14.453 [info] <0.882.0> started TLS (SSL) listener on [::]:5671
{removed_failing_handler,rabbit_log}
2021-07-09 02:47:17.092 [info] <0.736.0> Server startup complete; 4 plugins started.
* rabbitmq_prometheus
* rabbitmq_management
* rabbitmq_web_dispatch
* rabbitmq_management_agent
completed with 4 plugins.
2021-07-09 02:47:17.093 [info] <0.736.0> Resetting node maintenance status
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
默认的guest用户不能远程访问,因此需要创建一个可以远程访问的用户。
# 进入容器内部 $ docker exec -it rabbitmq bash # 创建一个用户名为rabbit,密码为rabbit的用户 $ rabbitmqctl add_user rabbit rabbit # 设置用户权限为超级管理员 $ rabbitmqctl set_user_tags rabbit administrator # 授权远程访问 $ rabbitmqctl set_permissions -p / rabbit "." "." ".*" # 退出容器 $ exit # 重启rabbitmq $ docker restart rabbitmq
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
通过刚才创建的用户rabbit访问管理员页面http://ip:15672
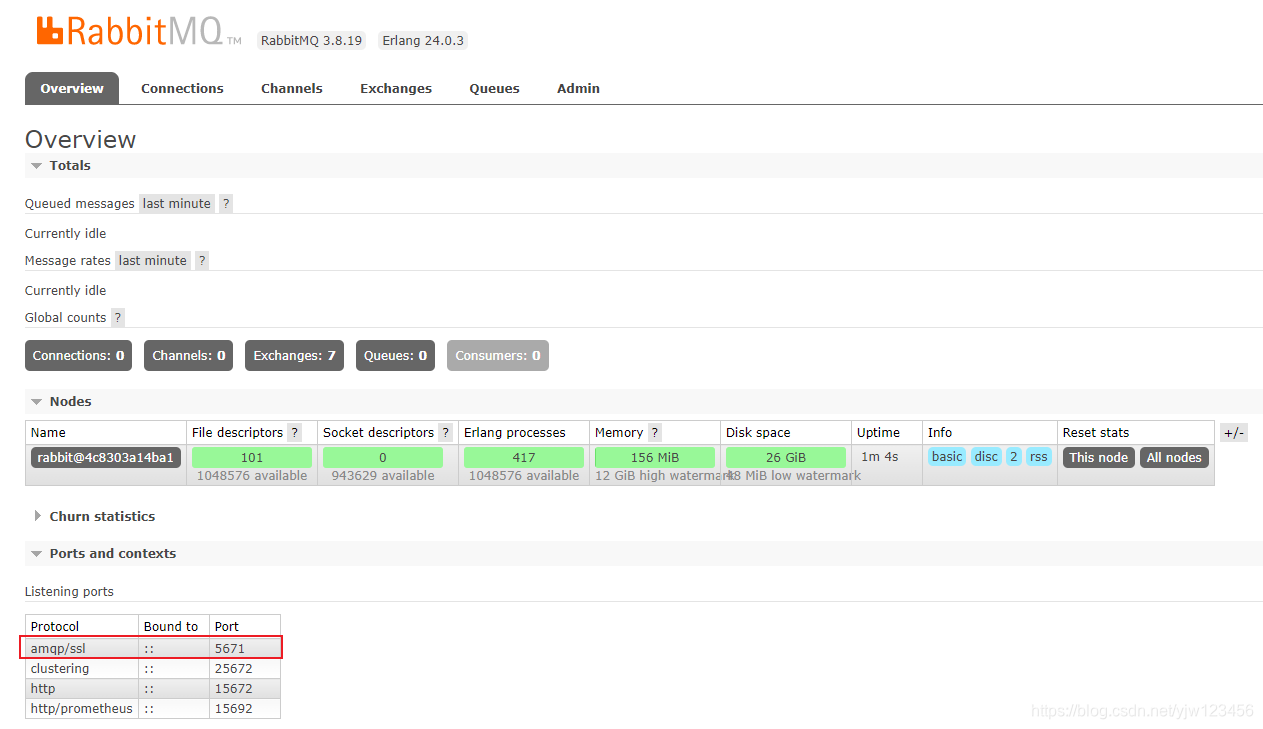
看到amqp/ssl 5671说明配置成功!
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/知新_RL/article/detail/458161
推荐阅读
相关标签
Copyright © 2003-2013 www.wpsshop.cn 版权所有,并保留所有权利。



