- 1使用nvm管理node多版本(安装、卸载nvm,配置环境变量,更换npm淘宝镜像)
- 2把时间当作朋友
- 3oa平台部署与迁移_oa数据库和业务数据库分开
- 4maven与idea版本适配问题_idea和maven版本对照
- 5微软在汉诺威工业博览会上推出新制造业Copilot人工智能功能,强化Dynamics 365工具集
- 6【RAG实践】基于LlamaIndex和Qwen1.5搭建基于本地知识库的问答机器人_基于qwen的问答机器人
- 7树莓派4B串口及蓝牙连接HC-05_树莓派4b蓝牙
- 8大数据与云计算——部署Hadoop集群并运行MapReduce集群案例(超级详细!)_mapreduce配置hadoop集群的相关组件,确保集群正常运行。
- 9Linux部署自动化运维平台Spug
- 10【转】Endnote中英文混排及输出作者全名的解决办法_endnote参考文献作者姓氏不缩写
用ENSP模拟WLAN无线的隧道转发与直接转发配置与报文解析_ensp配置无线直接转发,客户端获取不到ip地址,隧道转发没问题
赞
踩
无线组网的概念
1、CAPWAP(无线接入点控制和配置协议):用于管理AP与AP配置的下发
2、熟悉各种模版的引入
3、隧道转发与直接转发流量转发的区别(抓包了解)
4、实现终端获取地址
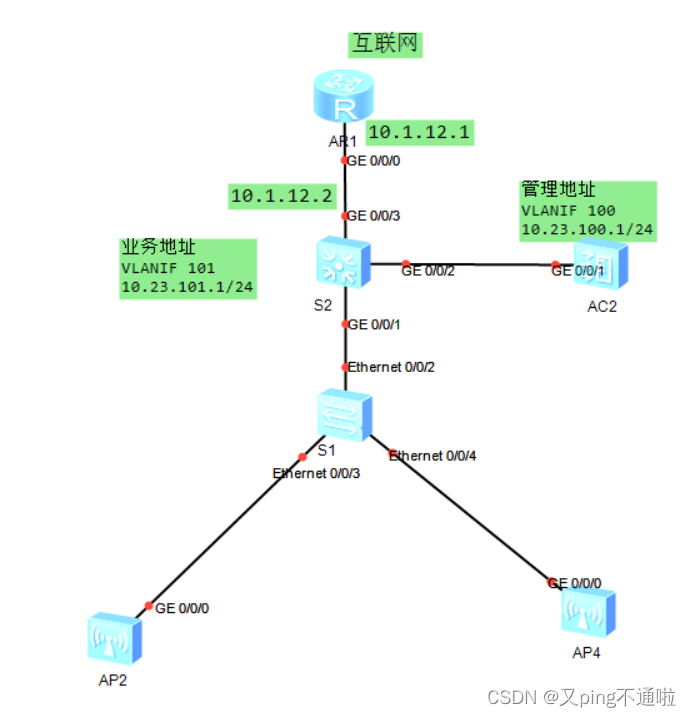
一、隧道转发:流量全部经过AC转发
AC配置:
WLAN模版配置
security-profile name hcie 创建安全模版名字为hcie(用于设置无线密码)
security wpa-wpa2 psk pass-phrase Huawei@123 aes 创建认证方式和加密方式和密码
ssid-profile name hcie 创建SSID模版名字为hcie(用于设置无线名称)
ssid hcie SSID名称为hcie(就是信号名字)
vap-profile name hcie 创建VAP模版名字为hcie(用于将安全与ssid模版引入)
forward-mode tunnel 设置转发方式为隧道转发
service-vlan vlan-id 101 设置业务VLAN(就是给终端下发业务地址的)
ssid-profile hcie 绑定SSID模版
security-profile hcie 绑定安全模版
AP组引入
ap-group name hcie
vap-profile hcie wlan 1 radio all 引入VAP模版 radio:射频信号时2.4g/5g
指定capwap隧道建立接口
capwap source interface vlanif100 指定接口为vlanif 100(也可以指ip地址)
AP手动加入
ap auth-mode mac-auth 开启AP认证为MAC认证
ap-id 1 ap-mac 00e0-fc53-5800 添加AP
ap-name hcie1 给AP改名字
ap-group hcie 添加到AP组(另一个AP同样配置)
AP管理地址分配以及互联接口配置
interface Vlanif100 创建vlan100并进入vlanif接口
ip address 10.23.100.1 255.255.255.0 配置地址
dhcp select interface 直接使用接口dhcp给AP分配管理地址(记得启用DHCP)
interface GigabitEthernet0/0/1 用于和核心交换机互联接口
port link-type trunk
port trunk allow-pass vlan 100 to 101 放通vlan100和vlan101
S2配置
终端业务地址
interface Vlanif101 业务vlan
ip address 10.23.101.1 255.255.255.0 AP的业务地址
dhcp select interface 直接接口分配(可以选择地址池)
互联口配置
interface GigabitEthernet0/0/1 接入互联口
port link-type trunk
port trunk allow-pass vlan 100 由于隧道转发只需要放通vlan100为AP管理vlan
#
interface GigabitEthernet0/0/2 AC互联口
port link-type trunk
port trunk allow-pass vlan 100 to 101 放通业务和管理VLAN
#
interface GigabitEthernet0/0/3 互联网互联口ACCESS口即可
port link-type access
port default vlan 200
S1配置
interface Ethernet0/0/2 核心互联口
port link-type trunk
port trunk allow-pass vlan 100 隧道转发只需要放通管理VLAN100
#
interface Ethernet0/0/3 AP互联口
port link-type trunk
port trunk pvid vlan 100 剥离VLAN100的标签,由于AP无法识别带标签的数据
port trunk allow-pass vlan 100 隧道转发只需放通管理VLAN100
#
interface Ethernet0/0/4 AP互联口
port link-type trunk
port trunk pvid vlan 100 剥离VLAN100的标签,由于AP无法识别带标签的数据
port trunk allow-pass vlan 100 隧道转发只需放通管理VLAN100
配置完成
验证结果
1、添加的两台AP已经获取地址并已经全部上线
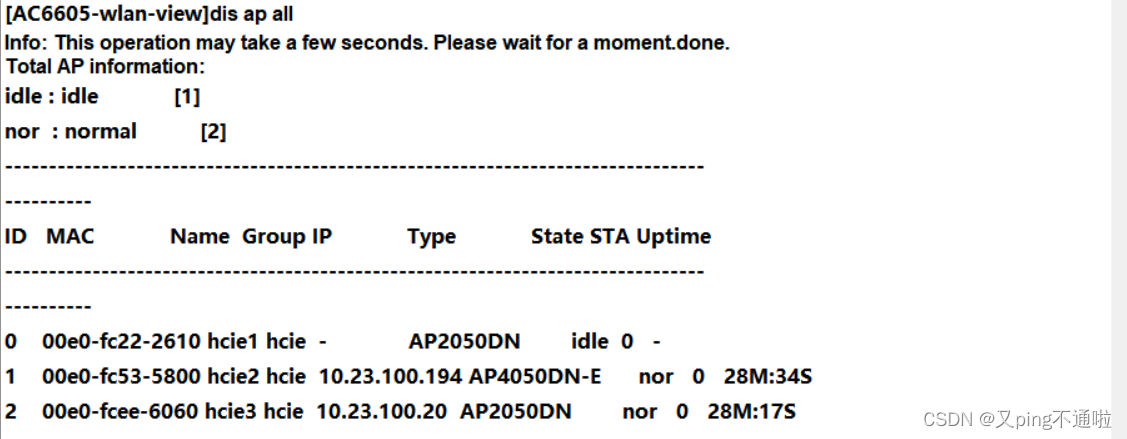
2、放出信号、终端已经搜到hcie信号
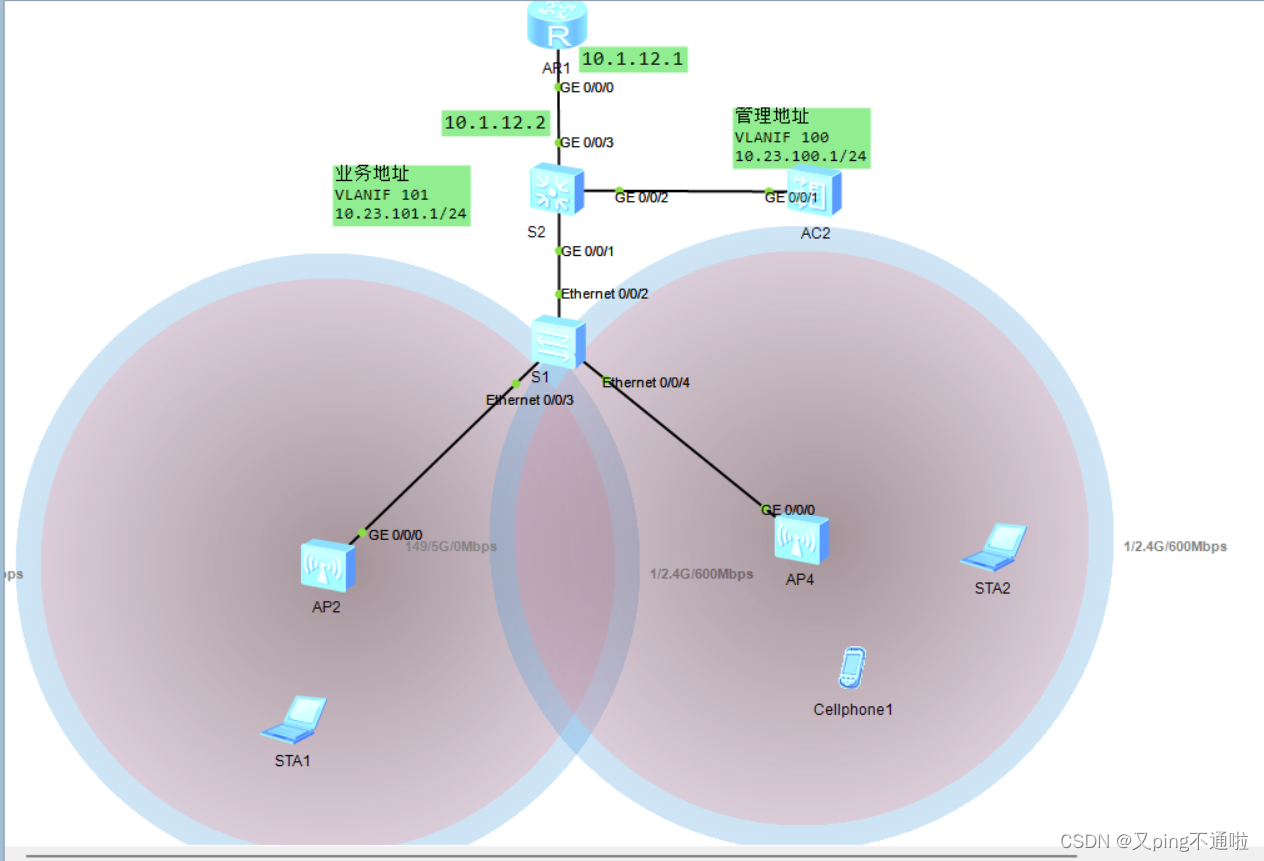
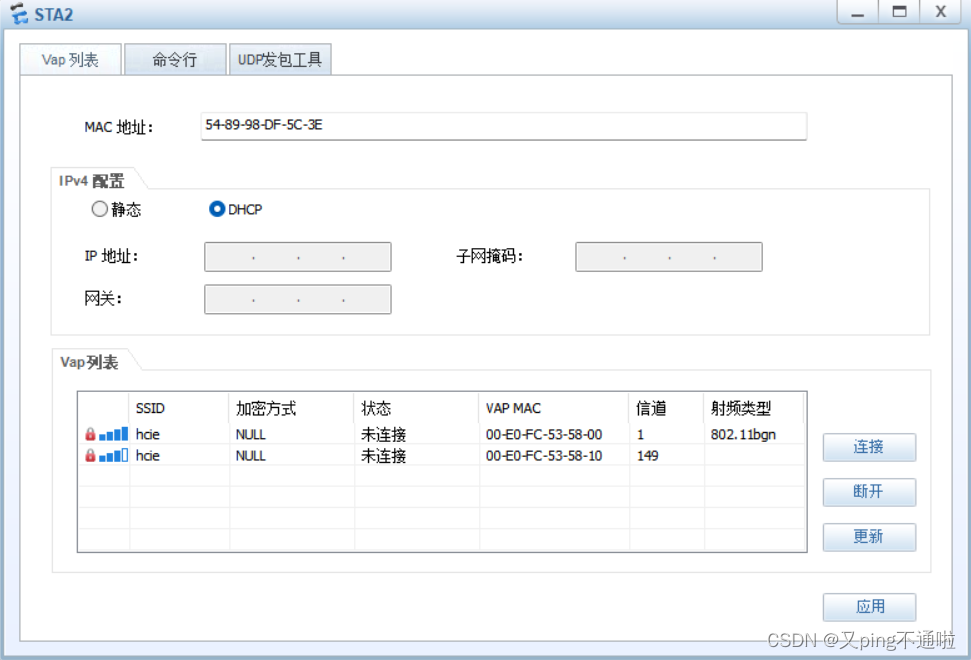
3、已经成功获取到地址
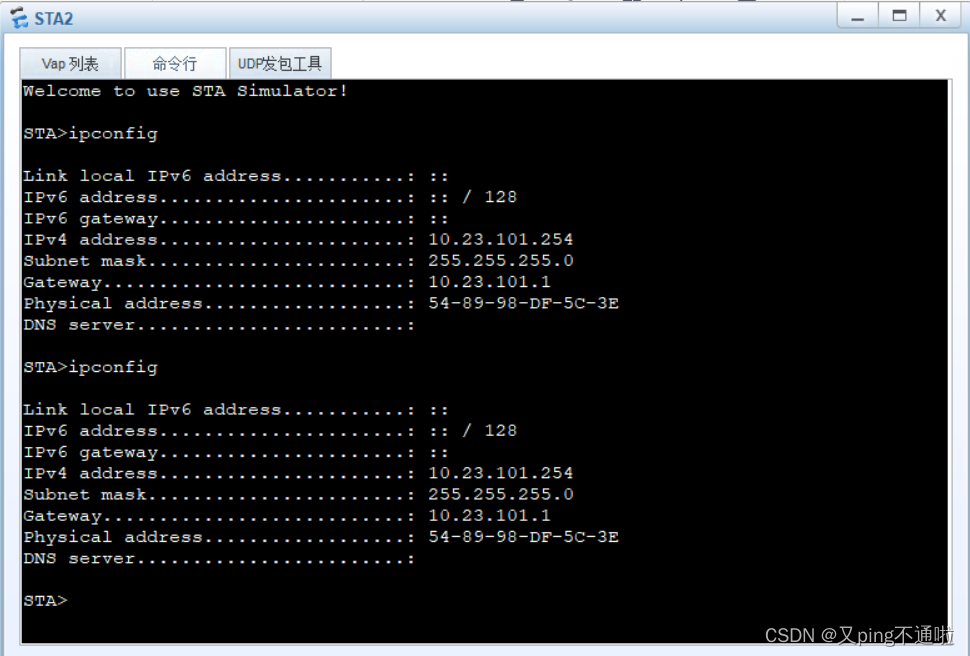
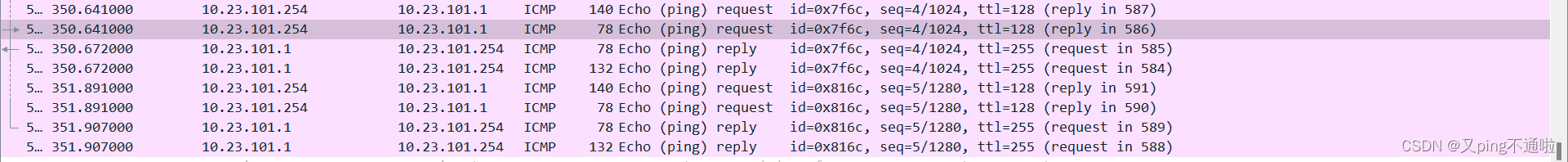
抓包认正AP获取地址流量走向
1、接入与核心之间链路抓包不会走业务DHCP的流量只会传输管理协议流量
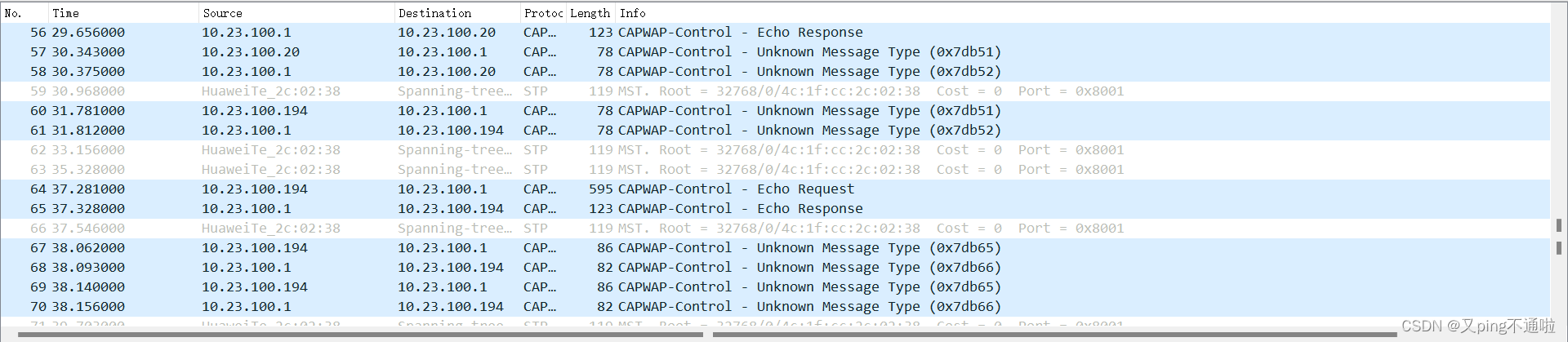
2、核心与AC之间抓包显示获取地址的过程,AC与AP通过隧道转发直接请求下发地址,没有经过中间接入
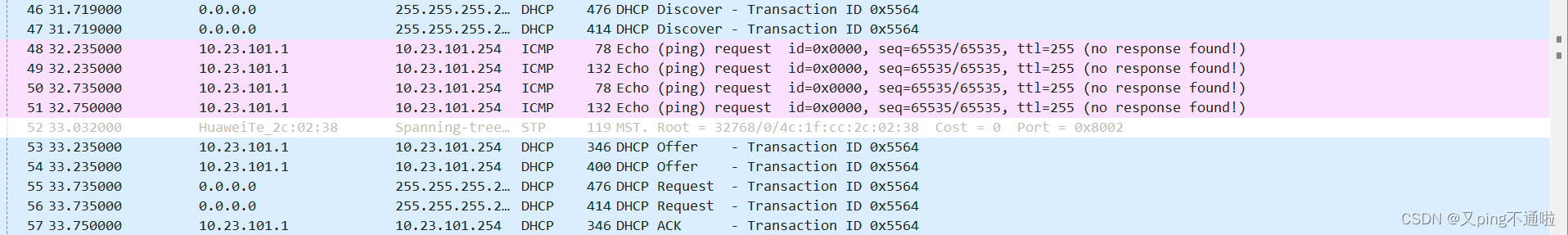
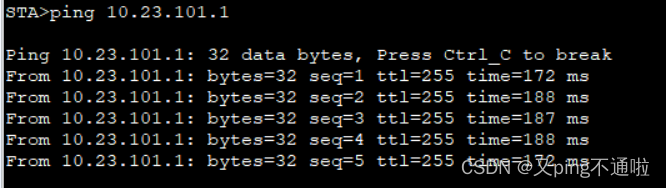
3、ping测试 请求直接从AC转发,不经过汇聚
二、直接转发
S1配置更改
interface Ethernet0/0/2 核心互联口放通vlan101(因为直接转发流量不经过AC)
port link-type trunk
port trunk allow-pass vlan 100 to 101
#
interface Ethernet0/0/3 AP互联口放通vlan101(因为直接转发流量不经过AC)
port link-type trunk
port trunk pvid vlan 100
port trunk allow-pass vlan 100 to 101
#
interface Ethernet0/0/4 AP互联口放通vlan101(因为直接转发流量不经过AC)
port link-type trunk
port trunk pvid vlan 100
port trunk allow-pass vlan 100 to 101
S2配置更改
interface GigabitEthernet0/0/1 接入互联口放通vlan101
port link-type trunk
port trunk allow-pass vlan 100 to 101
AC配置更改
wlan模版
vap-profile name hcie 进入VAP模版
forward-mode direct-forward 更改为直接转发
测试
依然可以拿到地址
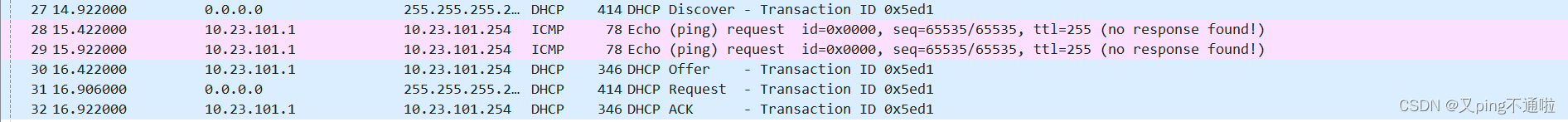
抓包测试
1、互联和接入之间抓包,显示DHCP请求与回复是经过接入到核心走的,不走AC
2、ping测试,看核心与AC互联链路有无流量
核心与AC之间链路抓包
显示无流量经过只是走CAPWAP控制流量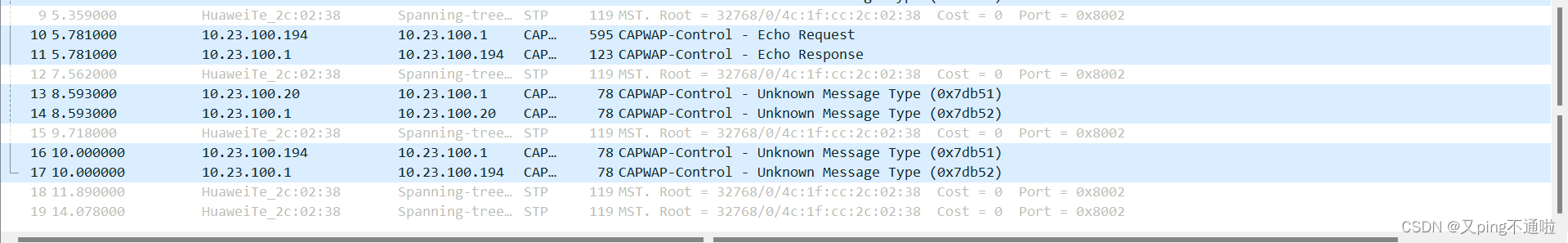
核心与接入抓包显示流量走的是核心与接入的链路
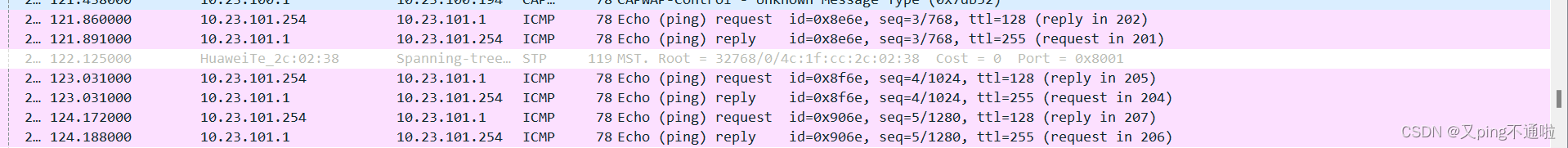
以上证明隧道转发,流量全部经过AC,AC负担大
直接转发,流量不经过AC减轻AC负担
AC全部配置
<AC6605>dis cu
#
set memory-usage threshold 0
#
ssl renegotiation-rate 1
#
vlan batch 100 to 101
#
authentication-profile name default_authen_profile
authentication-profile name dot1x_authen_profile
authentication-profile name mac_authen_profile
authentication-profile name portal_authen_profile
authentication-profile name macportal_authen_profile
#
dhcp enable
#
diffserv domain default
#
radius-server template default
#
pki realm default
rsa local-key-pair default
enrollment self-signed
#
ike proposal default
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
free-rule-template name default_free_rule
#
portal-access-profile name portal_access_profile
#
aaa
authentication-scheme default
authentication-scheme radius
authentication-mode radius
authorization-scheme default
accounting-scheme default
domain default
authentication-scheme radius
radius-server default
domain default_admin
authentication-scheme default
local-user admin password irreversible-cipher $1a$Bw{^=~2_';$DW-3TTPVl*@h!s@<^f
+;#a"-Yl=E>O^tq'8L%AoS$
local-user admin privilege level 15
local-user admin service-type http
#
interface Vlanif100
ip address 10.23.100.1 255.255.255.0
dhcp select interface
#
interface MEth0/0/1
undo negotiation auto
duplex half
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 100 to 101
#
interface GigabitEthernet0/0/2
#
interface GigabitEthernet0/0/3
#
interface GigabitEthernet0/0/4
#
interface GigabitEthernet0/0/5
#
interface GigabitEthernet0/0/6
#
interface GigabitEthernet0/0/7
#
interface GigabitEthernet0/0/8
#
interface GigabitEthernet0/0/9
#
interface GigabitEthernet0/0/10
#
interface GigabitEthernet0/0/11
#
interface GigabitEthernet0/0/12
#
interface GigabitEthernet0/0/13
#
interface GigabitEthernet0/0/14
#
interface GigabitEthernet0/0/15
#
interface GigabitEthernet0/0/16
#
interface GigabitEthernet0/0/17
#
interface GigabitEthernet0/0/18
#
interface GigabitEthernet0/0/19
#
interface GigabitEthernet0/0/20
#
interface GigabitEthernet0/0/21
undo negotiation auto
duplex half
#
interface GigabitEthernet0/0/22
undo negotiation auto
duplex half
#
interface GigabitEthernet0/0/23
undo negotiation auto
duplex half
#
interface GigabitEthernet0/0/24
undo negotiation auto
duplex half
#
interface XGigabitEthernet0/0/1
#
interface XGigabitEthernet0/0/2
#
interface NULL0
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
ssh server secure-algorithms cipher aes256_ctr aes128_ctr
ssh server key-exchange dh_group14_sha1
ssh client secure-algorithms cipher aes256_ctr aes128_ctr
ssh client secure-algorithms hmac sha2_256
ssh client key-exchange dh_group14_sha1
#
capwap source interface vlanif100
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
protocol inbound all
user-interface vty 16 20
protocol inbound all
#
wlan
traffic-profile name default
security-profile name hcie
security wpa-wpa2 psk pass-phrase %^%#qKXY(EX@W5wdut/TW\3QNG{a2`CAdU4:QLC{r@;E
%^%# aes
security-profile name hcip
security wpa-wpa2 psk pass-phrase %^%#M-+c;c6sU!5PtTD.Q$#U=[b}&bhbv+z(E6;P\$U4
%^%# aes
security-profile name default
security-profile name default-wds
security-profile name default-mesh
ssid-profile name hcie
ssid hcie
ssid-profile name hcip
ssid hcip
ssid-profile name default
vap-profile name hcie
service-vlan vlan-id 101
ssid-profile hcie
security-profile hcie
vap-profile name hcip
service-vlan vlan-id 101
ssid-profile hcip
security-profile hcip
vap-profile name default
wds-profile name default
mesh-handover-profile name default
mesh-profile name default
regulatory-domain-profile name hcie
regulatory-domain-profile name default
air-scan-profile name default
rrm-profile name default
radio-2g-profile name default
radio-5g-profile name default
wids-spoof-profile name default
wids-profile name default
wireless-access-specification
ap-system-profile name default
port-link-profile name default
wired-port-profile name default
serial-profile name preset-enjoyor-toeap
ap-group name hci
ap-group name hcie
regulatory-domain-profile hcie
radio 0
vap-profile hcie wlan 1
radio 1
vap-profile hcie wlan 1
radio 2
vap-profile hcie wlan 1
ap-group name hcip
ap-group name default
ap-id 0 type-id 69 ap-mac 00e0-fc22-2610 ap-sn 210235448310BB15E639
ap-name hcie1
ap-group hcie
ap-id 1 type-id 61 ap-mac 00e0-fc53-5800 ap-sn 210235448310BF555453
ap-name hcie2
ap-group hcie
ap-id 2 type-id 69 ap-mac 00e0-fcee-6060 ap-sn 210235448310F173CB10
ap-name hcie3
ap-group hcie
provision-ap
#
dot1x-access-profile name dot1x_access_profile
#
mac-access-profile name mac_access_profile
#
return
S2全部配置
[S2]dis cu
#
sysname S2
#
vlan batch 100 to 101 200
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
dhcp enable
#
diffserv domain default
#
acl number 2000
rule 5 permit
#
drop-profile default
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface Vlanif101
ip address 10.23.101.1 255.255.255.0
dhcp select interface
#
interface Vlanif200
ip address 10.1.12.2 255.255.255.0
#
interface MEth0/0/1
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 100 to 101
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 100 to 101
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 200
#
interface GigabitEthernet0/0/4
#
interface GigabitEthernet0/0/5
#
interface GigabitEthernet0/0/6
#
interface GigabitEthernet0/0/7
#
interface GigabitEthernet0/0/8
#
interface GigabitEthernet0/0/9
#
interface GigabitEthernet0/0/10
#
interface GigabitEthernet0/0/11
#
interface GigabitEthernet0/0/12
#
interface GigabitEthernet0/0/13
#
interface GigabitEthernet0/0/14
#
interface GigabitEthernet0/0/15
#
interface GigabitEthernet0/0/16
#
interface GigabitEthernet0/0/17
#
interface GigabitEthernet0/0/18
#
interface GigabitEthernet0/0/19
#
interface GigabitEthernet0/0/20
#
interface GigabitEthernet0/0/21
#
interface GigabitEthernet0/0/22
#
interface GigabitEthernet0/0/23
#
interface GigabitEthernet0/0/24
#
interface NULL0
#
user-interface con 0
user-interface vty 0 4
#
return
S1全部配置
[S1]
[S1]dis cu
#
sysname S1
#
vlan batch 100 to 101
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
diffserv domain default
#
drop-profile default
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface MEth0/0/1
#
interface Ethernet0/0/1
port link-type trunk
#
interface Ethernet0/0/2
port link-type trunk
port trunk allow-pass vlan 100 to 101
#
interface Ethernet0/0/3
port link-type trunk
port trunk pvid vlan 100
port trunk allow-pass vlan 100 to 101
#
interface Ethernet0/0/4
port link-type trunk
port trunk pvid vlan 100
port trunk allow-pass vlan 100 to 101
#
interface Ethernet0/0/5
#
interface Ethernet0/0/6
#
interface Ethernet0/0/7
#
interface Ethernet0/0/8
#
interface Ethernet0/0/9
#
interface Ethernet0/0/10
#
interface Ethernet0/0/11
#
interface Ethernet0/0/12
#
interface Ethernet0/0/13
#
interface Ethernet0/0/14
#
interface Ethernet0/0/15
#
interface Ethernet0/0/16
#
interface Ethernet0/0/17
#
interface Ethernet0/0/18
Jan 19 2024 20:48:33-08:00 S1 DS/4/DATASYNC_CFGCHANGE:OID 1.3.6.1.4.1.2011.5.25.
191.3.1 configurations have been changed. The current change number is 3, the ch
ange loop count is 0, and the maximum number of records is 4095.#
interface Ethernet0/0/19
#
interface Ethernet0/0/20
#
interface Ethernet0/0/21
#
interface Ethernet0/0/22
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
user-interface con 0
user-interface vty 0 4
#
return



