- 1实操教学|用Serverless 分分钟部署一个 Spring Boot 应用,真香!
- 2色彩校正及OpenCV mcc模块介绍_有mcc的opencv
- 3文本----简单编写文章的方法(中),后端接口的编写,自己编写好页面就上传到自己的服务器上,使用富文本编辑器进行编辑,想写好一个项目,先分析一下需求,再理一下实现思路,再搞几层,配好参数校验,lomb
- 4【Flink实战系列】Flink+kafka+redis 实时计算 wordcount_flink 读写redis
- 5【ViViT】A Video Vision Transformer 用于视频数据特征提取的ViT详解_视频vit
- 6数据结构之——简说链表
- 7【专题】2024中国汽车业人工智能行业应用发展图谱报告合集PDF分享(附原数据表)...
- 8浅谈Nginx负载均衡原理与实现_nginx 负载均衡 必须在局域网吗为什么
- 9二、Neo4j的使用(知识图谱构建射雕人物关系)
- 10推荐9个好玩的AI作图网站_mental ai
端口扫描工具 NMAP_服务器端口扫描工具
赞
踩
免费福利
前言
为了保护计算机不受攻击和各种病毒、木马的侵扰,其实我们可以在网络设备上采取措施,对某些数据包进行阻挡、过滤等,但重要的还是用户需要有一定的意识,采取措施对自己的计算机进行保护安全;
那么,今天主要想跟大家分享的是在 Linux 操作系统下除了使用 netstat、natcat、lsof 命令来查看本机的状态以外,还有什么方式来查看呢?
一、什么是网络端口?
网络端口:可以认为是传输层协议 TCP 或 UDP 与各种应用层协议进行通信时的一种通道。TCP 和 UDP 协议的数据报文头部都用一个 16 位的域来存放目的端口号和源端口号,最大是:65535。
二、网络端口两种使用方法
- 由某个程序监听某个端口,等待户机发送数据包到这个端口,一旦有数据产生,应用程序将会做出反应;
- 通过某个端口主动发送数据包到其他计算机;
三、netstat、netcat、lsof 查看端口状态示例
netstat
命令格式:netstat [ - 选项 1 ] [ - 选项 2 ] …
常用参数:
- -l:显示正在监听的 TCP 和 UDP 端口;
- -a:显示所有活动的 TCP 连接;
- -A <网络类型>或 - <网络类型>列出该网络类型连线中的相关地址;
- -n:以数字的形式表示地址和端口号;
- -s:显示所有协议的统计信息;
- -r:显示 IP 路由表的内容;
- -p:显示每一个正在使用的活动连接程序识别码及程序名称;
- -i:显示网络接口的统计信息;
- -t:只显示与 TCP 协议有关的连接和端口监听状态;
- -u:只显示与 UDP 协议有关的端口监听状态;
- -w:只显示原始接口状态;
[root@localhost ~]# netstat -anpt | grep 631
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 1218/cupsd
tcp 0 0 ::1:631 :::* LISTEN 1218/cupsd
- 1
- 2
- 3
netcat
nc -vv IP 端口号:意思是只显示该 IP 地址的某端口是否处于正常状态(succeeded:成功,Connection refused:连接拒绝)
nc -z IP 端口号; echo $?:意思是判断该 IP 地址的某端口是否有误(0:无误,1:有误)
[root@localhost ~]# nc -vv 192.168.1.127 22
Connection to 192.168.1.127 22 port [tcp/ssh] succeeded!
SSH-2.0-OpenSSH_5.3
[root@localhost ~]# nc -z 192.168.1.127 22; echo $?
Connection to 192.168.1.127 22 port [tcp/ssh] succeeded!
0
[root@localhost ~]# nc -vv 192.168.1.127 3306
nc: connect to 192.168.1.127 port 3306 (tcp) failed: Connection refused
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
lsof
lsof 查看端口占用语法格式:lsof -i :端口号
[root@localhost ~]# lsof -i:631
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
cupsd 1218 root 6u IPv6 12257 0t0 TCP localhost:ipp (LISTEN)
cupsd 1218 root 7u IPv4 12258 0t0 TCP localhost:ipp (LISTEN)
cupsd 1218 root 9u IPv4 12261 0t0 UDP *:ipp
- 1
- 2
- 3
- 4
- 5
以上几种方式,虽是一种实现方法,接下来就是今天我所要跟大家所分享的 NMAP 端口扫描工具~
四、NMAP 介绍
NMAP 是一款免费开源的网络扫描和主机监测工具,主要用于扫描一组主机的网络端口以及所有服务器间程序都要通过网络端口对外提供服务。比如一些常见的端口号:21(FTP服务)、22(SSH连接)、80(HTTP服务)等等,那么我们通过这些服务器开放的端口可以得到很多信息。
NMAP 也是一种常用的网络安全工具,黑客在攻击前,一般会使用这类工具搜索攻击目标、搜索目标主机的网络端口信息,从而来采取其他手段进行攻击。
那么,我们也可以通过这类工具对网络的安全性能进行检测,以防攻击。
官网地址:nmap.org/
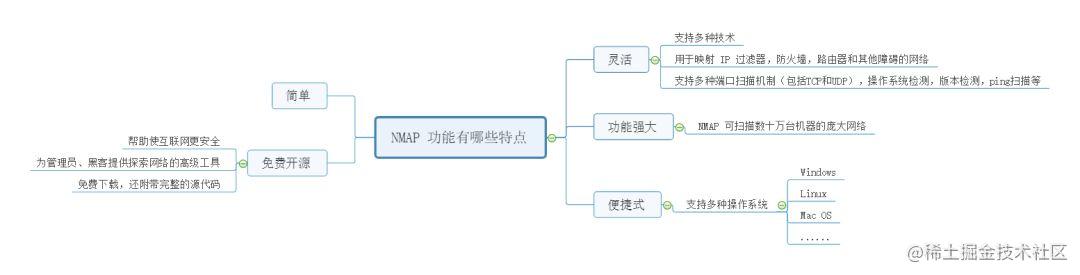
五、NMAP 功能特点
- 灵活
- 功能强大
- 便捷式
- 简单
- 免费开源
六、NMAP 命令格式
nmap [ 扫描类型 ] [ 扫描选项 ] <目标>
七、NMAP 参数基本操作
nmap 127.0.0.1 不加任何参数将以默认的方式扫描 127.0.0.1 主机的开放端口和服务名称。
[root@localhost ~]# nmap 127.0.0.1
Starting Nmap 5.51 ( http://nmap.org ) at 2019-05-27 10:59 CST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.0000040s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
111/tcp open rpcbind
631/tcp open ipp
Nmap done: 1 IP address (1 host up) scanned in 0.08 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
使用 -sT 参数尝试同目标主机的每个 TCP 端口建立连接、观察有哪些端口处于开放状态以及所运行的有哪些服务;
例如:扫描 GitHub 网站,看看存在哪些开放的端口。
[root@localhost ~]# nmap -sT www.github.com
Starting Nmap 5.51 ( http://nmap.org ) at 2019-05-27 10:24 CST
Nmap scan report for www.github.com (52.74.223.119)
Host is up (0.15s latency).
rDNS record for 52.74.223.119: ec2-52-74-223-119.ap-southeast-1.compute.amazonaws.com
Not shown: 996 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
9418/tcp open git
Nmap done: 1 IP address (1 host up) scanned in 70.72 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
扫描指定的 IP ,看看存在哪些开放的端口。
[root@localhost ~]# nmap -sT 220.181.38.150
Starting Nmap 5.51 ( http://nmap.org ) at 2019-05-27 10:40 CST
Nmap scan report for 220.181.38.150
Host is up (0.0056s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE
443/tcp open https
Nmap done: 1 IP address (1 host up) scanned in 4.64 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- -O 参数:探测主机操作系统;
- -sV 参数:探测端口上运行的软件;
通过上述两项参数,结合在一起,扫描 baidu 网站主机操作系统和扫描出的端口上运行着什么软件?
扫描后,我们可以看出端口号为:80 和 443 所运行着 Microsoft Windows UPnP(微软视窗)的软件;
[root@localhost ~]# sudo nmap -O -sV www.baidu.com Starting Nmap 5.51 ( http://nmap.org ) at 2019-05-27 10:32 CST Nmap scan report for www.baidu.com (220.181.38.150) Host is up (0.015s latency). Other addresses for www.baidu.com (not scanned): 220.181.38.149 Not shown: 998 filtered ports PORT STATE SERVICE VERSION 80/tcp open upnp Microsoft Windows UPnP 443/tcp open ssl/upnp Microsoft Windows UPnP Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: switch Running: HP embedded OS details: HP 4000M ProCurve switch (J4121A) Service Info: OS: Windows OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 22.87 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
通过上述扫描域名的方式以外,也可以采用 IP 的方式来进行扫描指定主机的操作系统和端口上所运行的软件;
[root@localhost ~]# sudo nmap -O -sV 220.181.38.150 Starting Nmap 5.51 ( http://nmap.org ) at 2019-05-27 10:35 CST Nmap scan report for 220.181.38.150 Host is up (0.015s latency). Not shown: 998 filtered ports PORT STATE SERVICE VERSION 80/tcp open upnp Microsoft Windows UPnP 443/tcp open ssl/upnp Microsoft Windows UPnP Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: switch Running (JUST GUESSING): HP embedded (86%) Aggressive OS guesses: HP 4000M ProCurve switch (J4121A) (86%) No exact OS matches for host (test conditions non-ideal). Service Info: OS: Windows OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 21.82 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- -sS 参数:通过向目标的某一个端口发送 TCP SYN 包,然后根据对方不同的回应来判断该端口是否处于监听状态。
[root@localhost ~]# nmap -sS www.github.com
Starting Nmap 5.51 ( http://nmap.org ) at 2019-05-28 05:03 CST
Nmap scan report for www.github.com (13.229.188.59)
Host is up (0.15s latency).
rDNS record for 13.229.188.59: ec2-13-229-188-59.ap-southeast-1.compute.amazonaws.com
Not shown: 996 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
9418/tcp open git
Nmap done: 1 IP address (1 host up) scanned in 32.39 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- -sA 参数是 TCP ACK 扫描,只用来确定防火墙的规则集,本身并不扫描目标主机的端口。
[root@localhost ~]# nmap -sA www.newrank.cn
Starting Nmap 5.51 ( http://nmap.org ) at 2019-05-28 05:25 CST
Nmap scan report for www.newrank.cn (47.99.2.204)
Host is up (0.029s latency).
All 1000 scanned ports on www.newrank.cn (47.99.2.204) are filtered
Nmap done: 1 IP address (1 host up) scanned in 17.63 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- -sW 参数类似于 TCP ACK 扫描,可以检测到处于打开状态的端口。
[root@localhost ~]# nmap -sW www.newrank.cn
Starting Nmap 5.51 ( http://nmap.org ) at 2019-05-28 05:55 CST
Nmap scan report for www.newrank.cn (47.99.2.204)
Host is up (0.032s latency).
All 1000 scanned ports on www.newrank.cn (47.99.2.204) are filtered
Nmap done: 1 IP address (1 host up) scanned in 46.43 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- -PN 参数是强制 nmap 对这类主机进行扫描。
[root@localhost ~]# nmap -sT -PN 220.181.38.150 Starting Nmap 5.51 ( http://nmap.org ) at 2019-05-27 10:41 CST Nmap scan report for 220.181.38.150 Host is up (0.0053s latency). Not shown: 998 filtered ports PORT STATE SERVICE 80/tcp open http 443/tcp open https Nmap done: 1 IP address (1 host up) scanned in 4.00 seconds 复制代码 [root@localhost ~]# nmap -sT -PN -p1-5000 192.168.1.127 Starting Nmap 5.51 ( http://nmap.org ) at 2019-05-27 10:51 CST Nmap scan report for 192.168.1.127 Host is up (0.00058s latency). Not shown: 4998 closed ports PORT STATE SERVICE 22/tcp open ssh 111/tcp open rpcbind Nmap done: 1 IP address (1 host up) scanned in 0.25 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
除上述参数之外,还有一些不常用的参数。
例如:
- -sF:向目标发送 TCP FIN 包,根据目标的响应进行判断;
[root@localhost ~]# nmap -sF www.newrank.cn
- 1
- -sX:向目标发送 TCP NULL 包,根据目标的响应进行判断;
[root@localhost ~]# nmap -sX www.newrank.cn
- 1
- -sN:向目标发送 FIN、PSH、URG 的包,根据目标的响应进行判断;
[root@localhost ~]# nmap -sN www.newrank.cn
- 1
- -sR:用于确认是否是 RPC 端口;
[root@localhost ~]# nmap -sR www.newrank.cn
- 1
- -sU:确认哪些是 UDP 端口处于开放的;
[root@localhost ~]# nmap -sU www.newrank.cn
- 1
- -sP:向目标发送 TCP ACK 的包,如果有响应,则表明目标处于活动状态;
[root@localhost ~]# nmap -sP www.newrank.cn
- 1
原创不易,如果你觉得这篇文章对你有点用的话,麻烦你为本文点个赞、评论或转发一下,因为这将是我输出更多优质文章的动力,感谢!



