热门标签
当前位置: article > 正文
AWS S3 跨账号迁移_aws s3 sync copy
作者:Monodyee | 2024-06-02 06:02:34
赞
踩
aws s3 sync copy
目录
- 迁移架构:
- 具体实施:
- 1. 在目标账号创建策略(S3MigrationPolicy)和角色(S3MigrationRole)
- 2. 安装 aws cli,并配置$ aws configure,[请参阅 AWS CLI 文档中的安装或更新 AWS CLI 最新版本](https://docs.aws.amazon.com/zh_cn/cli/latest/userguide/getting-started-install.html)
- 3. 假设 S3 迁移角色
- 4. 运行以下命令验证您是否担任了 IAM 角色:
- 5. 附加 S3 存储桶策略
- 6. 使用 copy (cp) 或同步 (sync) 命令复制数据
- cp || sync 过程中的问题:
- 参考:
迁移架构:
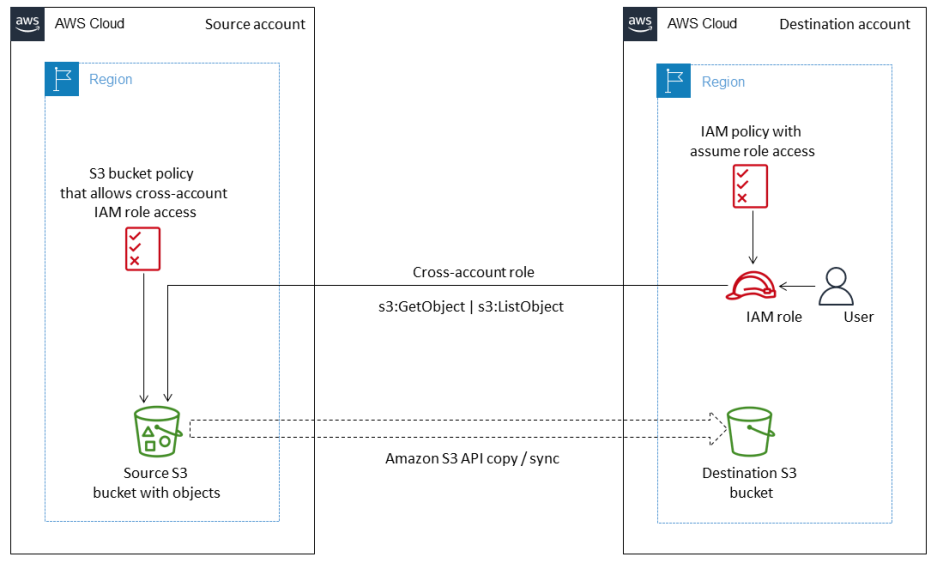
具体实施:
1. 在目标账号创建策略(S3MigrationPolicy)和角色(S3MigrationRole)
策略(S3MigrationPolicy)示例:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetObject"
],
"Resource": [
"arn:aws:s3:::awsexamplesourcebucket",
"arn:aws:s3:::awsexamplesourcebucket/*"
]
},
{
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:PutObject",
"s3:PutObjectAcl"
],
"Resource": [
"arn:aws:s3:::awsexampledestinationbucket",
"arn:aws:s3:::awsexampledestinationbucket/*"
]
}
]
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
角色(S3MigrationRole)示例:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::<destination_account>:user/<user_name>"
},
"Action": "sts:AssumeRole",
"Condition": {}
}
]
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
2. 安装 aws cli,并配置$ aws configure,请参阅 AWS CLI 文档中的安装或更新 AWS CLI 最新版本
3. 假设 S3 迁移角色
使用 AWS CLI 假设S3MigrationRole
aws sts assume-role --role-arn "arn:aws:iam::<destination_account>:role/S3MigrationRole" --role-session-name AWSCLI-Session
- 1
这里的 –role-arn 就是上述角色 S3MigrationRole 的 arn
4. 运行以下命令验证您是否担任了 IAM 角色:
aws sts get-caller-identity
- 1
5. 附加 S3 存储桶策略
登录到源账户的 AWS mazon 管理控制台,并打开 Amazon S3 控制台。选择您的源 S3 存储桶,然后选择权限。在 “存储桶策略” 下,选择 “编辑”,然后粘贴以下存储桶策略。选择保存。
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "DelegateS3Access",
"Effect": "Allow",
"Principal": {"AWS": "arn:aws:iam::<destination_account>:role/<RoleName>"},
"Action": ["s3:ListBucket","s3:GetObject"],
"Resource": [
"arn:aws:s3:::awsexamplesourcebucket/*",
"arn:aws:s3:::awsexamplesourcebucket"
]
}
]
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
此基于资源的策略允许目标角色S3MigrationRole访问源账户中的 S3 对象。
⭐️注:此处的 “Principal” 对应的值应该是运行命令 aws sts get-caller-identity 后返回的 arn 的值
6. 使用 copy (cp) 或同步 (sync) 命令复制数据
复制(有关详细信息,请参阅 AWS CLI 命令参考):
aws s3 cp s3:// DOC-EXAMPLE-BUCKET-SOURCE / \
s3:// DOC-EXAMPLE-BUCKET-TARGET / \
--recursive --source-region SOURCE-REGION-NAME --region DESTINATION-REGION-NAME
- 1
- 2
- 3
同步(有关详细信息,请参阅 AWS CLI 命令参考):
aws s3 sync s3:// DOC-EXAMPLE-BUCKET-SOURCE / \
s3:// DOC-EXAMPLE-BUCKET-TARGET / \
--source-region SOURCE-REGION-NAME --region DESTINATION-REGION-NAME
- 1
- 2
- 3
cp || sync 过程中的问题:
部分文件在 cp || sync 时报错:An error occurred (AccessDenied) when calling the GetObjectTagging operation: Access Denied
解决办法:
在源桶策略中添加:“s3:GetObjectTagging” 即可。
参考:
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/Monodyee/article/detail/661469
推荐阅读
相关标签


