热门标签
热门文章
- 1ai论文开题报告(免费ai生成论文)硕士论文文献综述总结!超全!看完全会了!
- 2代码随想录第51天 | 309.最佳买卖股票时机含冷冻期 、 714.买卖股票的最佳时机含手续费
- 3[目标识别-论文笔记]Object Detection in Videos by Short and Long Range Object Linking_object detection in videos by high quality object
- 4python 排序统计滤波器_这里有一份Python习题集,赶紧来测测吧
- 5电子科技大学计算机通信网-基于Simulink的2ASK 2FSK 2PSK的调制和解调_2fsk解调相干和非相干simulink
- 6探索ChatGPT-Nine-AI:一款强大的对话式AI工具
- 7集合覆盖模型例题_Java 进阶:集合框架1
- 8Qt/C++编写安防视频监控系统(支持win/linux/mac/海康/大华/宇视/264/265等)_qt 视频监控
- 9UWB信号对服务器有没有干扰,uwb定位技术原理及应用分析
- 10香蕉派 BPI-R3 开源路由器开发板采用 联发科MT7986(Filogic 830)芯片设计,支持Wi-Fi 6/6E,2.5GbE SFP光电口_mt7986 bpi r3
当前位置: article > 正文
安全防御 --- IPSec理论(02)_encapsulation-mode transport
作者:小小林熬夜学编程 | 2024-04-26 15:30:10
赞
踩
encapsulation-mode transport
附:
协议与模式分类
esp 和 ah 的分类:
- 数据的安全性:ESP有机密性;AH无机密性
- 场景:ESP适合公网场景;AH适合内网 / 私网场景
(数据的安全性主要依赖于传输端之间需要做认证)
传输模式和隧道模式的分类:
- 传输端的可达性:传输模式有可达性;隧道模式无可达性
- 场景:传输模式(私网数据通过公网传输;异种网络之间通过其他网络传输);隧道模式(专线,隧道已做,本身路由可达)
ipsec配置(路由器)

静态路由协议下的IPSec
- 保证基础网络可达
- [r1]int g0/0/0
- [r1-GigabitEthernet0/0/0]ip add 100.1.1.1 24
- [r1]ip route-static 0.0.0.0 0 100.1.1.2
-
-
- [ISP]int g0/0/0
- [ISP-GigabitEthernet0/0/0]ip add 100.1.1.2 24
- [ISP]int g0/0/1
- [ISP-GigabitEthernet0/0/1]ip ad 100.1.2.1 24
-
- [r2]int g0/0/0
- [r2-GigabitEthernet0/0/0]ip add 100.1.2.2 24
- [r2]ip route-static 0.0.0.0 0 100.1.2.1
-
- [r1]int LoopBack 0
- [r1-LoopBack0]ip add 172.16.10.1 24
- [r2]int LoopBack 0
- [r2-LoopBack0]ip add 172.16.1.1 24

(1)配置 IKE SA
<1> 安全提议
- [r1]ike proposal 1 // 安全提议编号
- [r1-ike-proposal-1]encryption-algorithm 3des-cbc // 加密算法(3des)
- [r1-ike-proposal-1]authentication-algorithm sha1 // 认证算法(sha1)
- [r1-ike-proposal-1]authentication-method pre-share // 认证模式(预共享:pre)
- [r1-ike-proposal-1]dh group2 // 非对称加密算法强度
-
- [r1]dis ike proposal --- 查看未显示以及默认配置
-
- Number of IKE Proposals: 2
-
- -------------------------------------------
- IKE Proposal: 1
- Authentication method : pre-shared
- Authentication algorithm : SHA1
- Encryption algorithm : 3DES-CBC
- DH group : MODP-1024
- SA duration : 3600
- PRF : PRF-HMAC-SHA
- -------------------------------------------
-
- -------------------------------------------
- IKE Proposal: Default
- Authentication method : pre-shared
- Authentication algorithm : SHA1
- Encryption algorithm : DES-CBC
- DH group : MODP-768
- SA duration : 86400
- PRF : PRF-HMAC-SHA
- -------------------------------------------
-
- [r2]ike proposal 1
- [r2-ike-proposal-1]encryption-algorithm 3des-cbc
- [r2-ike-proposal-1]dh group2
- [r2-ike-proposal-1]sa duration 3600

PRF:完美向前法。
<2> 安全认证
- [r1]ike peer 12 v1 // ike认证名称和版本
- [r1-ike-peer-12]exchange-mode main // 模式选择(默认主模式)
- [r1-ike-peer-12]pre-shared-key cipher 234 // 编译预共享密钥
- [r1-ike-peer-12]ike-proposal 1 // 调用安全提议
- [r1-ike-peer-12]remote-address 100.1.2.2 // 调用远端地址
-
- [r2]ike peer 12 v1
- [r2-ike-peer-12]ike-proposal 1
- [r2-ike-peer-12]pre-shared-key cipher 234
- [r2-ike-peer-12]remote-address 100.1.1.1
- [r2-ike-peer-12]exchange-mode main
(2)配置IPSec SA 安全提议信息
- [r1]ipsec proposal 1 // ipsec提议
- [r1-ipsec-proposal-1]transform esp // 选择传输协议
- [r1-ipsec-proposal-1]esp authentication-algorithm sha2-512 // 认证算法
- [r1-ipsec-proposal-1]esp encryption-algorithm aes-128 // 加密算法
- [r1-ipsec-proposal-1]encapsulation-mode tunnel // 封装模式(隧道模式)
-
- [r1]dis ipsec proposal --- 查看
-
- Number of proposals: 1
-
- IPSec proposal name: 1
- Encapsulation mode: Tunnel
- Transform : esp-new
- ESP protocol : Authentication SHA2-HMAC-512
- Encryption AES-128
-
- [r2]ipsec proposal 1
- [r2-ipsec-proposal-1]transform esp
- [r2-ipsec-proposal-1]encapsulation-mode tunnel
- [r2-ipsec-proposal-1]esp authentication-algorithm sha2-512
- [r2-ipsec-proposal-1]esp encryption-algorithm aes-128

(3)定义加密流量(感兴趣流)
- [r1]acl 3000
- [r1-acl-adv-3000]rule 5 permit ip source 172.16.10.1 0.0.0.0 destination 172.16.1.1 0.0.0.0
-
- [r2]acl 3000
- [r2-acl-adv-3000]rule 5 permit ip source 172.16.1.1 0.0.0.0 destination 172.16.10.1 0.0.0.0
(4)配置安全策略集
- [r1]ipsec policy k 10 isakmp --- 定义名为k,序列号为10,运用isakmp(IKE)进行协商
- [r1-ipsec-policy-isakmp-k-10]ike-peer 12 // 关联ike-peer
- [r1-ipsec-policy-isakmp-k-10]security acl 3000 // 关联感兴趣流
- [r1-ipsec-policy-isakmp-k-10]pfs dh-group2 // pfs:完美向前法
-
- [r2]ipsec policy k 10 isakmp
- [r2-ipsec-policy-isakmp-k-10]ike-peer 12
- [r2-ipsec-policy-isakmp-k-10]proposal 1
- [r2-ipsec-policy-isakmp-k-10]security acl 3000
- [r2-ipsec-policy-isakmp-k-10]pfs dh-group2
(5)接口调用安全策略集
- [r1]int g0/0/0
- [r1-GigabitEthernet0/0/0]ipsec policy k
- [r2]int g0/0/0
- [r2-GigabitEthernet0/0/0]ipsec policy k
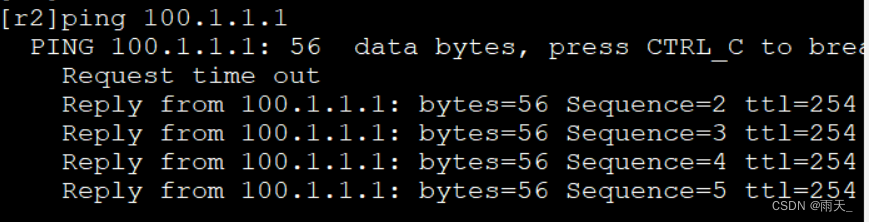
进行触发:
(6)查看安全联盟建立情况
- <r1>dis ike sa
- Conn-ID Peer VPN Flag(s) Phase
- ---------------------------------------------------------------
- 2 100.1.2.2 0 RD|ST 2
- 1 100.1.2.2 0 RD|ST 1
-
- Flag Description:
- RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT
- HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP
- <r1>dis ipsec sa
- [Outbound ESP SAs]
- SPI: 1407390962 (0x53e314f2)
- Proposal: ESP-ENCRYPT-AES-128 SHA2-512-256
- SA remaining key duration (bytes/sec): 1887329280/2740
- Max sent sequence-number: 5
- UDP encapsulation used for NAT traversal: N
-
- [Inbound ESP SAs]
- SPI: 3197321182 (0xbe933fde)
- Proposal: ESP-ENCRYPT-AES-128 SHA2-512-256
- SA remaining key duration (bytes/sec): 1887436380/2740
- Max received sequence-number: 5
- Anti-replay window size: 32
- UDP encapsulation used for NAT traversal: N

动态路由协议下的IPSec
- 新建环回
- [r1]int LoopBack 0
- [r1-LoopBack1]ip ad 1.1.1.1 24
- gre下的隧道配置
- [r1]int t0/0/0
- [r1-Tunnel0/0/0]tunnel-protocol gre
- [r1-Tunnel0/0/0]source g0/0/0
- [r1-Tunnel0/0/0]destination 100.1.2.2
- [r1-Tunnel0/0/0]ip add 10.1.1.1 24
-
- [r2]int lo 1
- [r2-LoopBack1]ip add 2.2.2.2 24
- [r2]int t0/0/0
- [r2-Tunnel0/0/0]tunnel-protocol gre
- [r2-Tunnel0/0/0]source g0/0/0
- [r2-Tunnel0/0/0]destination 100.1.1.1
- [r2-Tunnel0/0/0]ip add 10.1.1.2 24
-
- ospf配置
- [r1]ospf 1
- [r1-ospf-1]a 0
- [r1-ospf-1-area-0.0.0.0]network 1.1.1.1 0.0.0.0
- [r1-ospf-1-area-0.0.0.0]network 10.1.1.1 0.0.0.0
- [r2]ospf 1
- [r2-ospf-1]a 0
- [r2-ospf-1-area-0.0.0.0]network 2.2.2.2 0.0.0.0
- [r2-ospf-1-area-0.0.0.0]network 10.1.1.2 0.0.0.0
-
- 查看邻居建立情况
- [r1]dis ospf peer brief
- OSPF Process 1 with Router ID 100.1.1.1
- Peer Statistic Information
- ----------------------------------------------------------------------------
- Area Id Interface Neighbor id State
- 0.0.0.0 Tunnel0/0/0 100.1.2.2 Full
- ----------------------------------------------------------------------------

(1)配置 IKE SA
<1> 安全提议
- [r1]ike proposal 10
- [r1-ike-proposal-10]encryption-algorithm 3des-cbc
- [r1-ike-proposal-10]authentication-algorithm sha1
- [r1-ike-proposal-10]authentication-method pre-share
- [r1-ike-proposal-10]dh group2
-
- [r2]ike proposal 10
- [r2-ike-proposal-10]encryption-algorithm 3des-cbc
- [r2-ike-proposal-10]authentication-algorithm sha1
- [r2-ike-proposal-10]authentication-method pre-share
- [r2-ike-proposal-10]dh group2
<2> 安全认证
- [r1]ike peer gre v1
- [r1-ike-peer-gre]pre-shared-key simple aaa // 设置预共享密钥(simple:本地不加密)
- [r1-ike-peer-gre]exchange-mode aggressive // 采用野蛮模式
- [r1-ike-peer-gre]local-id-type name // 采用name定义
- [r1-ike-peer-gre]remote-name a1 // 远端name为a1
- [r1-ike-peer-gre]remote-address 100.1.2.2 // 远端IP
- [r1-ike-peer-gre]ike-proposal 10 // 引用ike
- [r1]ike local-name a1 // 全局定义本地name
-
- [r2]ike peer gre v1
- [r2-ike-peer-gre]ike-proposal 10
- [r2-ike-peer-gre]pre-shared-key simple aaa
- [r2-ike-peer-gre]remote-address 100.1.1.1
- [r2-ike-peer-gre]exchange-mode aggressive
- [r2-ike-peer-gre]local-id-type name
- [r2-ike-peer-gre]remote-name a1

(2)配置ipsec sa 的安全提议信息
- [r1]ipsec proposal gre
- [r1-ipsec-proposal-gre]encapsulation-mode transport
-
- [r2]ipsec proposal gre
- [r2-ipsec-proposal-gre]encapsulation-mode transport
(3)定义加密流量(感兴趣流)
- [r1]acl 3001
- [r1-acl-adv-3001]rule 10 permit gre source 100.1.1.1 0 destination 100.1.2.2 0
-
- [r2]acl 3001
- [r2-acl-adv-3001]rule 10 permit gre source 100.1.2.2 0 destination 100.1.1.1 0
(4)配置安全策略集
- [r1]ipsec policy gre 10 isakmp
- [r1-ipsec-policy-isakmp-gre-10]ike-peer gre
- [r1-ipsec-policy-isakmp-gre-10]proposal gre
- [r1-ipsec-policy-isakmp-gre-10]security acl 3001
-
- [r2]ipsec policy gre 10 isakmp
- [r2-ipsec-policy-isakmp-gre-10]security acl 3001
- [r2-ipsec-policy-isakmp-gre-10]proposal gre
- [r2-ipsec-policy-isakmp-gre-10]ike-peer gre
(5)接口调用安全策略集
- [r1]int g0/0/0
- [r1-GigabitEthernet0/0/0]ipsec policy gre
-
- [r2]int g0/0/0
- [r2-GigabitEthernet0/0/0]ipsec policy gre
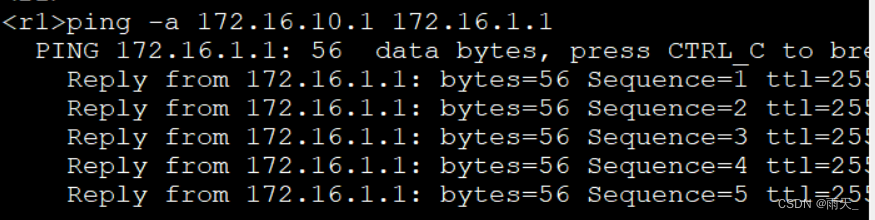
ping进行触发:
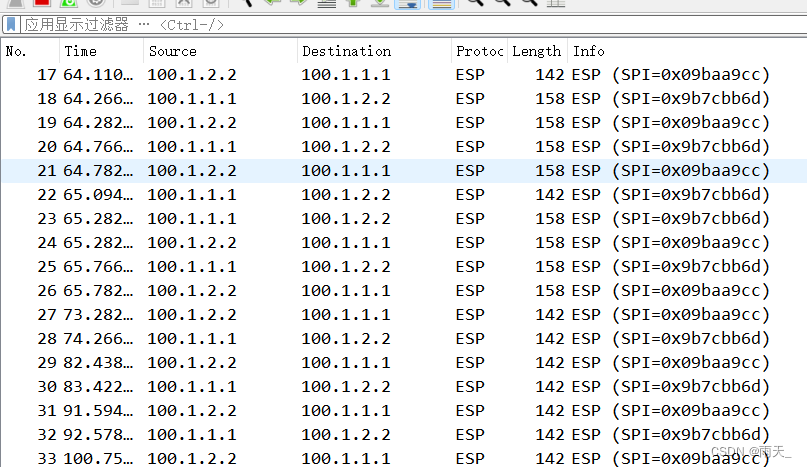
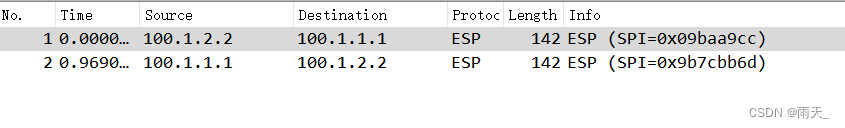
流量已加密
(6)分析
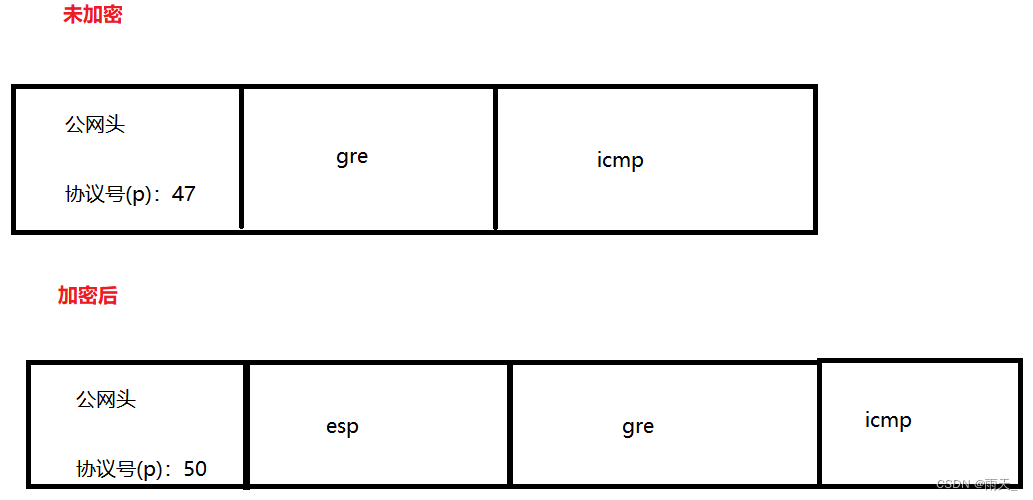
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/小小林熬夜学编程/article/detail/491732
推荐阅读
相关标签


