- 1Git常用命令:git stash 暂存,代码草稿本(持续更新中)_git暂存代码
- 2基于STM32的SYN6288语音播报模块驱动实验(代码开源)_syn6288语音模块_基于stm32的语音播报模块
- 3java的tcp实时接收json格式报文_tcp - 如何使用带有rsocket Java的TcpClientTransport将自定义数据格式转换为JSON - 堆栈内存溢出...
- 4SAP常用TCODE_sap tcode 功能对照表
- 5数据治理CDGA证书含金量为什么这么高?_cdga0
- 6hadoop之hdfs与yarn界面功能介绍_hdfs原生界面overview
- 7openGauss数据库源码解析系列文章——AI技术(2.1)_opengauss源码分析
- 8ChatGPT流式输出实现原理
- 9安卓Clean Architecture:实现模块化与可测试性的软件设计方法
- 10【Python+百度API】 文本情感倾向分析_百度情感分析api
前端CryptoJS和Java后端数据互相加解密(AES)_cryptojs.aes.decrypt
赞
踩
一、序言
最近刚好在做一个简单的保险代理人运营平台,主要是为了方便个人展业,由于有些客户数据比较敏感,所以在用户登录时准备对登录密码进行一波加密后再传输。
这里我准备用AES对称加密算法对数据进行加密传输,经过调研后前端加解密相关准备用CryptoJS,后端加解密工具类根据JDK1.8官方文档自己来实现。
二、关于前端CryptoJS
1、CryptoJS简单介绍
CryptoJS是标准安全加密算法的JavaScript实现,运行速度快,接口简单,见名知意。文档说明可参考:CryptoJS文档说明。
CryptoJS的实现主要有哈希算法,HMAC、加密算法、以及常用编解码算法。
哈希算法,如MD5、SHA-1、SHA-2等。
加密算法,如AES、DES等。
编解码算法,如Base64、Hex16等。
2、加密和填充模式选择
下图是CryptoJS支持的加密模式和填充模式,CryptoJS默认的加密模式为CBC,填充模式为Pkcs7。
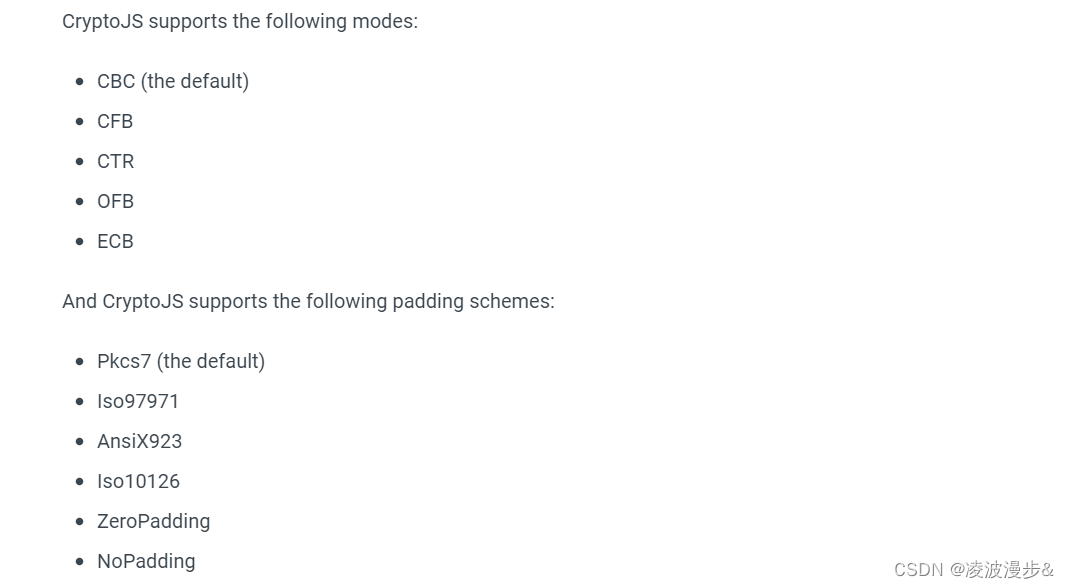
常用的加密模式有CBC和ECB,由于CBC安全性更高,我们可以选用CBC和Pkcs7的组合。
3、前端AES加解密示例
(1) cryptoutils工具类
这里我封装了一个CryptoJS工具类,加密模式选用的是ECB,填充模式为PKcs7。
import CryptoJS from 'crypto-js';
/**
* AES加密
* @param plainText 明文
* @param keyInBase64Str base64编码后的key
* @returns {string} base64编码后的密文
*/
export function encryptByAES(plainText, keyInBase64Str) {
let key = CryptoJS.enc.Base64.parse(keyInBase64Str);
let encrypted = CryptoJS.AES.encrypt(plainText, key, {
mode: CryptoJS.mode.ECB,
padding: CryptoJS.pad.Pkcs7,
});
// 这里的encrypted不是字符串,而是一个CipherParams对象
return encrypted.ciphertext.toString(CryptoJS.enc.Base64);
}
/**
* AES解密
* @param cipherText 密文
* @param keyInBase64Str base64编码后的key
* @return 明文
*/
export function decryptByAES(cipherText, keyInBase64Str) {
let key = CryptoJS.enc.Base64.parse(keyInBase64Str);
// 返回的是一个Word Array Object,其实就是Java里的字节数组
let decrypted = CryptoJS.AES.decrypt(cipherText, key, {
mode: CryptoJS.mode.ECB,
padding: CryptoJS.pad.Pkcs7,
});
return decrypted.toString(CryptoJS.enc.Utf8);
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
(2) 测试用例
const secretKey = 'sQPoC/1do9BZMkg8I5c09A==';
const cipherText = encryptByAES('Hello', secretKey);
const plainText = decryptByAES(cipherText, secretKey);
console.log(`Hello加密后的密文为:${cipherText}`);
console.log(`解密后的内容为:${plainText}`);
- 1
- 2
- 3
- 4
- 5
控制台输出内容如下:
Hello加密后的密文为:
iTgNXRqU80YZ52+iV7Ew2w==
解密后的内容为:Hello
(3) 加解密后输出内容说明
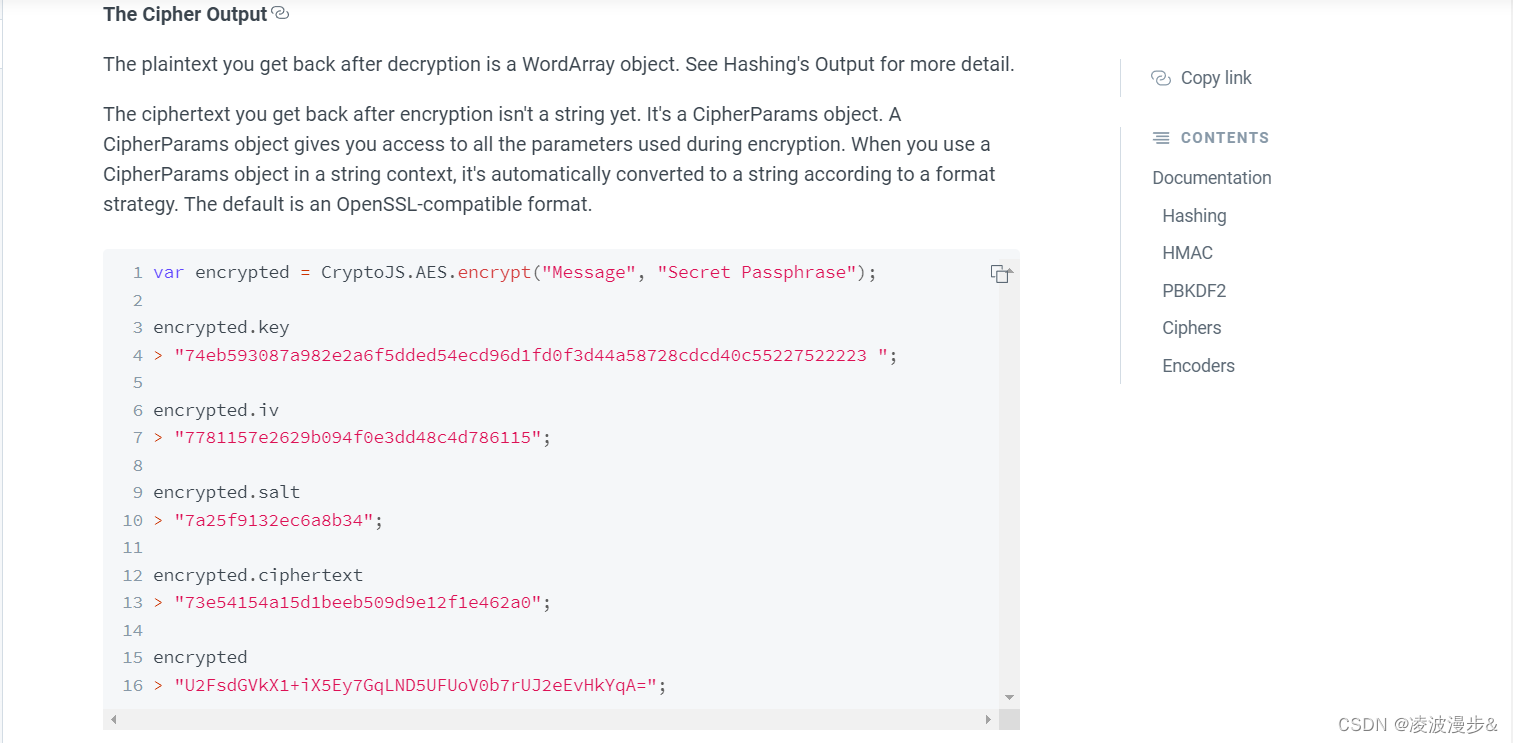
根据官方文档,解密后的明文是一个WordArray对象,也就是我们所说的Java中的字节数组,该对象有一个toString方法可以转换成16进制、Base64、UTF8等字符串。
加密后的密文也不是字符串,而是一个CipherParams对象,其中的ciphertext属性也是一个 WordArray对象。
三、Java后端AES加解密
1、Java中支持的加密模式和填充说明
前面我们前端AES加密模式用的是ECB,填充模式时是PKCS7。
现在我们先来看看Java中支持的加密模式和填充,在Java中这些被称为transformation,具体支持哪些transformation,请参考:JDK8中加密算法实现要求。
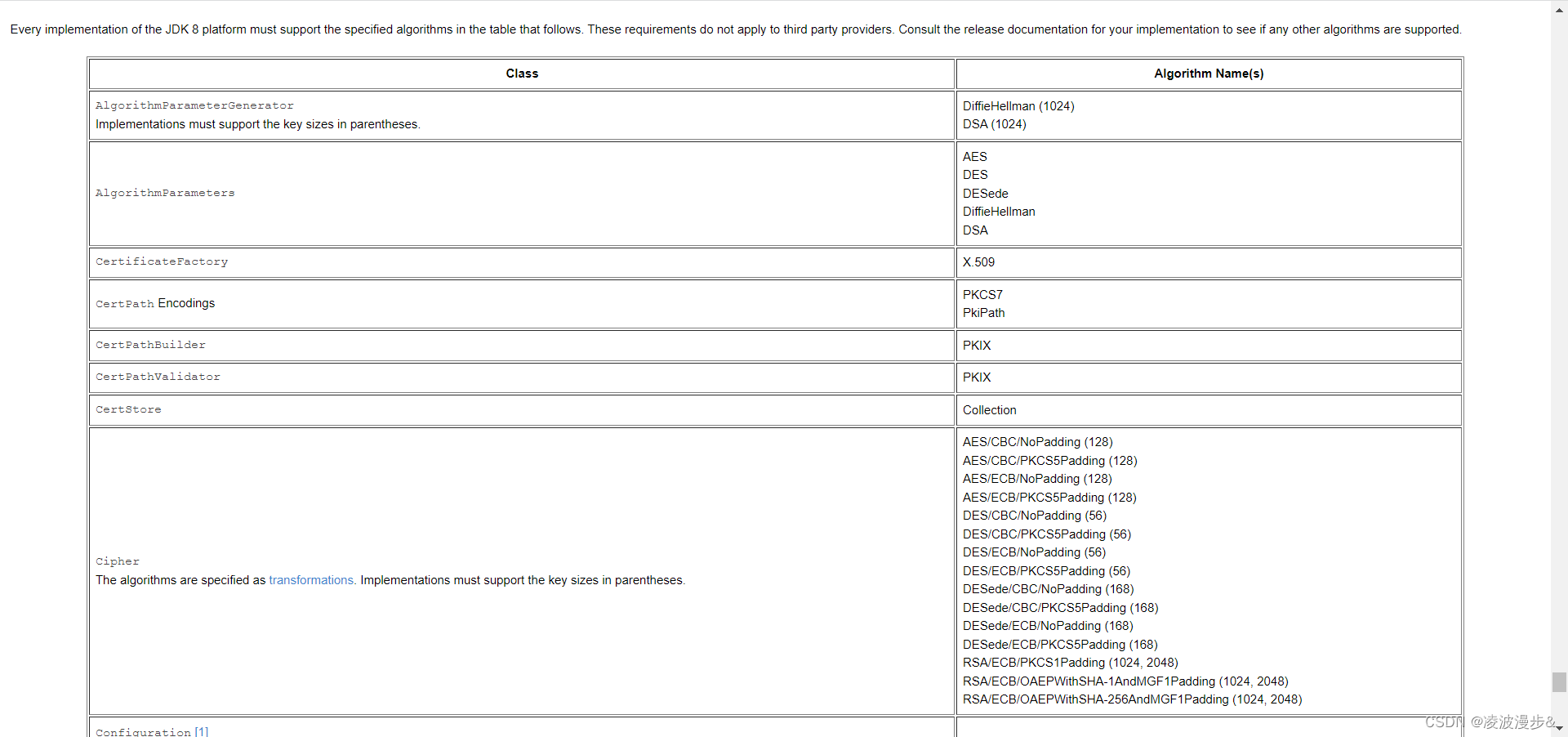
根据上图,我们只要算法、加密模式和填充模式和前端保持一致就行了,这里我们选用的transformation为AES/ECB/PKCS5Padding (128)。
备注:前端CryptoJS的填充模式为PKCS7,而Java中的填充模式为PKCS5,但这里并不会有啥影响。
2、工具类CryptoUtils
这里我自己封装了一个工具类,支持AES、DES、RSA、数字签名与校验等。
package com.universe.crypto;
import com.universe.crypto.CryptoUtils.Algorithm.Encryption;
import com.universe.crypto.CryptoUtils.Algorithm.Signing;
import lombok.AllArgsConstructor;
import lombok.Data;
import lombok.Getter;
import lombok.NoArgsConstructor;
import org.apache.commons.lang3.StringUtils;
import javax.crypto.Cipher;
import javax.crypto.KeyGenerator;
import javax.crypto.NoSuchPaddingException;
import javax.crypto.SecretKey;
import javax.crypto.spec.IvParameterSpec;
import javax.crypto.spec.SecretKeySpec;
import java.nio.charset.Charset;
import java.nio.charset.StandardCharsets;
import java.security.Key;
import java.security.KeyFactory;
import java.security.KeyPair;
import java.security.KeyPairGenerator;
import java.security.NoSuchAlgorithmException;
import java.security.PrivateKey;
import java.security.PublicKey;
import java.security.Signature;
import java.security.spec.InvalidKeySpecException;
import java.security.spec.KeySpec;
import java.security.spec.PKCS8EncodedKeySpec;
import java.security.spec.X509EncodedKeySpec;
import java.util.Base64;
import java.util.Base64.Decoder;
import java.util.Base64.Encoder;
import java.util.HashMap;
import java.util.Map;
import java.util.concurrent.ConcurrentHashMap;
/**
* 支持AES、DES、RSA加密、数字签名以及生成对称密钥和非对称密钥对
*/
public class CryptoUtils {
private static final Charset DEFAULT_CHARSET = StandardCharsets.UTF_8;
private static final Encoder BASE64_ENCODER = Base64.getEncoder();
private static final Decoder BASE64_DECODER = Base64.getDecoder();
private static final Map<Algorithm, KeyFactory> KEY_FACTORY_CACHE = new ConcurrentHashMap<>();
private static final Map<Algorithm, Cipher> CIPHER_CACHE = new HashMap<>();
/**
* 生成对称密钥,目前支持的算法有AES、DES
* @param algorithm
* @return
* @throws NoSuchAlgorithmException
*/
public static String generateSymmetricKey(Algorithm algorithm) throws NoSuchAlgorithmException {
KeyGenerator generator = KeyGenerator.getInstance(algorithm.getName());
generator.init(algorithm.getKeySize());
SecretKey secretKey = generator.generateKey();
return BASE64_ENCODER.encodeToString(secretKey.getEncoded());
}
/**
* 生成非对称密钥对,目前支持的算法有RSA、DSA。备注:默认生成的密钥格式为PKCS8
* @param algorithm
* @return
* @throws NoSuchAlgorithmException
*/
public static AsymmetricKeyPair generateAsymmetricKeyPair(Algorithm algorithm) throws NoSuchAlgorithmException {
KeyPairGenerator generator = KeyPairGenerator.getInstance(algorithm.getName());
generator.initialize(algorithm.getKeySize());
KeyPair keyPair = generator.generateKeyPair();
String publicKey = BASE64_ENCODER.encodeToString(keyPair.getPublic().getEncoded());
String privateKey = BASE64_ENCODER.encodeToString(keyPair.getPrivate().getEncoded());
return new AsymmetricKeyPair(publicKey, privateKey);
}
public static String encryptByRSA(String publicKeyText, String plainText) throws Exception {
return encryptAsymmetrically(publicKeyText, plainText, Encryption.RSA_ECB_PKCS1);
}
public static String decryptByRSA(String privateKeyText, String ciphertext) throws Exception {
return decryptAsymmetrically(privateKeyText, ciphertext, Encryption.RSA_ECB_PKCS1);
}
/**
* SHA1签名算法和DSA加密算法结合使用生成数字签名
* @param privateKeyText
* @param msg
* @return 数字签名
* @throws Exception
*/
public static String signBySHA1WithDSA(String privateKeyText, String msg) throws Exception {
return doSign(privateKeyText, msg, Encryption.DSA, Signing.SHA1WithDSA);
}
/**
* SHA1签名算法和RSA加密算法结合使用生成数字签名
* @param privateKeyText 私钥
* @param msg 待加签内容
* @return 数字签名
* @throws Exception
*/
public static String signBySHA1WithRSA(String privateKeyText, String msg) throws Exception {
return doSign(privateKeyText, msg, Encryption.RSA_ECB_PKCS1, Signing.SHA1WithRSA);
}
/**
* SHA256签名算法和RSA加密算法结合使用生成数字签名
* @param privateKeyText 私钥
* @param msg 待加签内容
* @return 数字签名
* @throws Exception
*/
public static String signBySHA256WithRSA(String privateKeyText, String msg) throws Exception {
return doSign(privateKeyText, msg, Encryption.RSA_ECB_PKCS1, Signing.SHA256WithRSA);
}
/**
* SHA1签名算法和DSA加密算法检验数字签名
* @param publicKeyText 公钥
* @param msg 待验签内容
* @param signatureText 数字
* @return 检验是否成功
* @throws Exception
*/
public static boolean verifyBySHA1WithDSA(String publicKeyText, String msg, String signatureText) throws Exception {
return doVerify(publicKeyText, msg, signatureText, Encryption.DSA, Signing.SHA1WithDSA);
}
/**
* SHA1签名算法和RSA加密算法检验数字签名
* @param publicKeyText 公钥
* @param msg 待验签内容
* @param signatureText 签名
* @return 校验是否成功
* @throws Exception
*/
public static boolean verifyBySHA1WithRSA(String publicKeyText, String msg, String signatureText) throws Exception {
return doVerify(publicKeyText, msg, signatureText, Encryption.RSA_ECB_PKCS1, Signing.SHA1WithRSA);
}
/**
* SHA256签名算法和RSA加密算法检验数字签名
* @param publicKeyText 公钥
* @param msg 待验签内容
* @param signatureText 签名
* @return 校验是否成功
* @throws Exception
*/
public static boolean verifyBySHA256WithRSA(String publicKeyText, String msg, String signatureText) throws Exception {
return doVerify(publicKeyText, msg, signatureText, Encryption.RSA_ECB_PKCS1, Signing.SHA256WithRSA);
}
/**
* 对称加密
* @param secretKey 密钥
* @param iv 加密向量,只有CBC模式才支持,如果是CBC则必传
* @param plainText 明文
* @param algorithm 对称加密算法,如AES、DES
* @return
* @throws Exception
*/
public static String encryptSymmetrically(String secretKey, String iv, String plainText, Algorithm algorithm) throws Exception {
SecretKey key = decodeSymmetricKey(secretKey, algorithm);
IvParameterSpec ivParameterSpec = StringUtils.isBlank(iv) ? null : decodeIv(iv);
byte[] plainTextInBytes = plainText.getBytes(DEFAULT_CHARSET);
byte[] ciphertextInBytes = transform(algorithm, Cipher.ENCRYPT_MODE, key, ivParameterSpec, plainTextInBytes);
return BASE64_ENCODER.encodeToString(ciphertextInBytes);
}
/**
* 对称解密
* @param secretKey 密钥
* @param iv 加密向量,只有CBC模式才支持,如果是CBC则必传
* @param ciphertext 密文
* @param algorithm 对称加密算法,如AES、DES
* @return
* @throws Exception
*/
public static String decryptSymmetrically(String secretKey, String iv, String ciphertext, Algorithm algorithm) throws Exception {
SecretKey key = decodeSymmetricKey(secretKey, algorithm);
IvParameterSpec ivParameterSpec = StringUtils.isBlank(iv) ? null : decodeIv(iv);
byte[] ciphertextInBytes = BASE64_DECODER.decode(ciphertext);
byte[] plainTextInBytes = transform(algorithm, Cipher.DECRYPT_MODE, key, ivParameterSpec, ciphertextInBytes);
return new String(plainTextInBytes, DEFAULT_CHARSET);
}
/**
* 非对称加密
* @param publicKeyText 公钥
* @param plainText 明文
* @param algorithm 非对称加密算法
* @return
* @throws Exception
*/
public static String encryptAsymmetrically(String publicKeyText, String plainText, Algorithm algorithm) throws Exception {
PublicKey publicKey = regeneratePublicKey(publicKeyText, algorithm);
byte[] plainTextInBytes = plainText.getBytes(DEFAULT_CHARSET);
byte[] ciphertextInBytes = transform(algorithm, Cipher.ENCRYPT_MODE, publicKey, plainTextInBytes);
return BASE64_ENCODER.encodeToString(ciphertextInBytes);
}
/**
* 非对称解密
* @param privateKeyText 私钥
* @param ciphertext 密文
* @param algorithm 非对称加密算法
* @return
* @throws Exception
*/
public static String decryptAsymmetrically(String privateKeyText, String ciphertext, Algorithm algorithm) throws Exception {
PrivateKey privateKey = regeneratePrivateKey(privateKeyText, algorithm);
byte[] ciphertextInBytes = BASE64_DECODER.decode(ciphertext);
byte[] plainTextInBytes = transform(algorithm, Cipher.DECRYPT_MODE, privateKey, ciphertextInBytes);
return new String(plainTextInBytes, DEFAULT_CHARSET);
}
/**
* 生成数字签名
* @param privateKeyText 私钥
* @param msg 传输的数据
* @param encryptionAlgorithm 加密算法,见Algorithm中的加密算法
* @param signatureAlgorithm 签名算法,见Algorithm中的签名算法
* @return 数字签名
* @throws Exception
*/
public static String doSign(String privateKeyText, String msg, Algorithm encryptionAlgorithm, Algorithm signatureAlgorithm)
throws Exception {
PrivateKey privateKey = regeneratePrivateKey(privateKeyText, encryptionAlgorithm);
// Signature只支持签名算法
Signature signature = Signature.getInstance(signatureAlgorithm.getName());
signature.initSign(privateKey);
signature.update(msg.getBytes(DEFAULT_CHARSET));
byte[] signatureInBytes = signature.sign();
return BASE64_ENCODER.encodeToString(signatureInBytes);
}
/**
* 数字签名验证
* @param publicKeyText 公钥
* @param msg 传输的数据
* @param signatureText 数字签名
* @param encryptionAlgorithm 加密算法,见Algorithm中的加密算法
* @param signatureAlgorithm 签名算法,见Algorithm中的签名算法
* @return 校验是否成功
* @throws Exception
*/
public static boolean doVerify(String publicKeyText, String msg, String signatureText, Algorithm encryptionAlgorithm,
Algorithm signatureAlgorithm) throws Exception {
PublicKey publicKey = regeneratePublicKey(publicKeyText, encryptionAlgorithm);
Signature signature = Signature.getInstance(signatureAlgorithm.getName());
signature.initVerify(publicKey);
signature.update(msg.getBytes(DEFAULT_CHARSET));
return signature.verify(BASE64_DECODER.decode(signatureText));
}
/**
* 将密钥进行Base64位解码,重新生成SecretKey实例
* @param secretKey 密钥
* @param algorithm 算法
* @return
*/
private static SecretKey decodeSymmetricKey(String secretKey, Algorithm algorithm) {
byte[] key = BASE64_DECODER.decode(secretKey);
return new SecretKeySpec(key, algorithm.getName());
}
private static IvParameterSpec decodeIv(String iv) {
byte[] ivInBytes = BASE64_DECODER.decode(iv);
return new IvParameterSpec(ivInBytes);
}
private static PublicKey regeneratePublicKey(String publicKeyText, Algorithm algorithm)
throws NoSuchAlgorithmException, InvalidKeySpecException {
byte[] keyInBytes = BASE64_DECODER.decode(publicKeyText);
KeyFactory keyFactory = getKeyFactory(algorithm);
// 公钥必须使用RSAPublicKeySpec或者X509EncodedKeySpec
KeySpec publicKeySpec = new X509EncodedKeySpec(keyInBytes);
PublicKey publicKey = keyFactory.generatePublic(publicKeySpec);
return publicKey;
}
private static PrivateKey regeneratePrivateKey(String key, Algorithm algorithm) throws Exception {
byte[] keyInBytes = BASE64_DECODER.decode(key);
KeyFactory keyFactory = getKeyFactory(algorithm);
// 私钥必须使用RSAPrivateCrtKeySpec或者PKCS8EncodedKeySpec
KeySpec privateKeySpec = new PKCS8EncodedKeySpec(keyInBytes);
PrivateKey privateKey = keyFactory.generatePrivate(privateKeySpec);
return privateKey;
}
private static KeyFactory getKeyFactory(Algorithm algorithm) throws NoSuchAlgorithmException {
KeyFactory keyFactory = KEY_FACTORY_CACHE.get(algorithm);
if (keyFactory == null) {
keyFactory = KeyFactory.getInstance(algorithm.getName());
KEY_FACTORY_CACHE.put(algorithm, keyFactory);
}
return keyFactory;
}
private static byte[] transform(Algorithm algorithm, int mode, Key key, byte[] msg) throws Exception {
return transform(algorithm, mode, key, null, msg);
}
private static byte[] transform(Algorithm algorithm, int mode, Key key, IvParameterSpec iv, byte[] msg) throws Exception {
Cipher cipher = CIPHER_CACHE.get(algorithm);
// double check,减少上下文切换
if (cipher == null) {
synchronized (CryptoUtils.class) {
if ((cipher = CIPHER_CACHE.get(algorithm)) == null) {
cipher = determineWhichCipherToUse(algorithm);
CIPHER_CACHE.put(algorithm, cipher);
}
cipher.init(mode, key, iv);
return cipher.doFinal(msg);
}
}
synchronized (CryptoUtils.class) {
cipher.init(mode, key, iv);
return cipher.doFinal(msg);
}
}
private static Cipher determineWhichCipherToUse(Algorithm algorithm) throws NoSuchAlgorithmException, NoSuchPaddingException {
Cipher cipher;
String transformation = algorithm.getTransformation();
// 官方推荐的transformation使用algorithm/mode/padding组合,SunJCE使用ECB作为默认模式,使用PKCS5Padding作为默认填充
if (StringUtils.isNotEmpty(transformation)) {
cipher = Cipher.getInstance(transformation);
} else {
cipher = Cipher.getInstance(algorithm.getName());
}
return cipher;
}
/**
* 算法分为加密算法和签名算法,更多算法实现见:<br/>
* <a href="https://docs.oracle.com/javase/8/docs/technotes/guides/security/StandardNames.html#impl">jdk8中的标准算法</a>
*/
public static class Algorithm {
public interface Encryption {
Algorithm AES_ECB_PKCS5 = new Algorithm("AES", "AES/ECB/PKCS5Padding", 128);
Algorithm AES_CBC_PKCS5 = new Algorithm("AES", "AES/CBC/PKCS5Padding", 128);
Algorithm DES_ECB_PKCS5 = new Algorithm("DES", "DES/ECB/PKCS5Padding", 56);
Algorithm DES_CBC_PKCS5 = new Algorithm("DES", "DES/CBC/PKCS5Padding", 56);
Algorithm RSA_ECB_PKCS1 = new Algorithm("RSA", "RSA/ECB/PKCS1Padding", 1024);
Algorithm DSA = new Algorithm("DSA", 1024);
}
public interface Signing {
Algorithm SHA1WithDSA = new Algorithm("SHA1withDSA", 1024);
Algorithm SHA1WithRSA = new Algorithm("SHA1WithRSA", 2048);
Algorithm SHA256WithRSA = new Algorithm("SHA256WithRSA", 2048);
}
@Getter
private String name;
@Getter
private String transformation;
@Getter
private int keySize;
public Algorithm(String name, int keySize) {
this(name, null, keySize);
}
public Algorithm(String name, String transformation, int keySize) {
this.name = name;
this.transformation = transformation;
this.keySize = keySize;
}
}
@Data
@NoArgsConstructor
@AllArgsConstructor
public static class AsymmetricKeyPair {
private String publicKey;
private String privateKey;
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
- 166
- 167
- 168
- 169
- 170
- 171
- 172
- 173
- 174
- 175
- 176
- 177
- 178
- 179
- 180
- 181
- 182
- 183
- 184
- 185
- 186
- 187
- 188
- 189
- 190
- 191
- 192
- 193
- 194
- 195
- 196
- 197
- 198
- 199
- 200
- 201
- 202
- 203
- 204
- 205
- 206
- 207
- 208
- 209
- 210
- 211
- 212
- 213
- 214
- 215
- 216
- 217
- 218
- 219
- 220
- 221
- 222
- 223
- 224
- 225
- 226
- 227
- 228
- 229
- 230
- 231
- 232
- 233
- 234
- 235
- 236
- 237
- 238
- 239
- 240
- 241
- 242
- 243
- 244
- 245
- 246
- 247
- 248
- 249
- 250
- 251
- 252
- 253
- 254
- 255
- 256
- 257
- 258
- 259
- 260
- 261
- 262
- 263
- 264
- 265
- 266
- 267
- 268
- 269
- 270
- 271
- 272
- 273
- 274
- 275
- 276
- 277
- 278
- 279
- 280
- 281
- 282
- 283
- 284
- 285
- 286
- 287
- 288
- 289
- 290
- 291
- 292
- 293
- 294
- 295
- 296
- 297
- 298
- 299
- 300
- 301
- 302
- 303
- 304
- 305
- 306
- 307
- 308
- 309
- 310
- 311
- 312
- 313
- 314
- 315
- 316
- 317
- 318
- 319
- 320
- 321
- 322
- 323
- 324
- 325
- 326
- 327
- 328
- 329
- 330
- 331
- 332
- 333
- 334
- 335
- 336
- 337
- 338
- 339
- 340
- 341
- 342
- 343
- 344
- 345
- 346
- 347
- 348
- 349
- 350
- 351
- 352
- 353
- 354
- 355
- 356
- 357
- 358
- 359
- 360
- 361
- 362
- 363
- 364
- 365
- 366
- 367
- 368
- 369
- 370
- 371
- 372
- 373
- 374
- 375
- 376
- 377
- 378
- 379
- 380
- 381
- 382
- 383
- 384
- 385
- 386
- 387
- 388
- 389
- 390
- 391
- 392
3、测试用例
public class AesDemo {
public static void main(String[] args) throws Exception {
String secretKey = CryptoUtils.generateSymmetricKey(Encryption.AES_ECB_PKCS5);
String cipherText = CryptoUtils.encryptSymmetrically(secretKey, null, "test", Encryption.AES_ECB_PKCS5);
System.out.println("生成的密钥为:" + secretKey);
System.out.println("加密后的密文为:" + cipherText);
System.out.println("解密后的明文为:" + CryptoUtils.decryptSymmetrically(secretKey, null, cipherText, Encryption.AES_ECB_PKCS5));
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
控制台输出如下:
生成的密钥为:
s44pylNUK38B+PdLJM9i6w==
加密后的密文为:xD3T5FQvikNc10jsv9G4Rg==
解密后的明文为:Hello World
四、前后端加解密交互测试
1、前端加密,后端解密
这里我们先在前端对明文进行AES加密。
const plainText = 'Hello World';
const secretKey = 'sQPoC/1do9BZMkg8I5c09A==';
const cipherText = encryptByAES(plainText, secretKey);
console.log(`加密后的密文为:${cipherText}`);
- 1
- 2
- 3
- 4
前端控制台输出如下:
加密后的密文为:
38guooCNqRJaxvL8vh+kLg==
然后在Java后端对密文进行AES解密。
/**
* @author Nick Liu
* @date 2023/4/23
*/
public class AesDemo {
public static void main(String[] args) throws Exception {
String secretKey = "sQPoC/1do9BZMkg8I5c09A==";
String cipherText = "38guooCNqRJaxvL8vh+kLg==";
System.out.println("解密后的明文为:" + CryptoUtils.decryptSymmetrically(secretKey, null, cipherText, Encryption.AES_ECB_PKCS5));
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
后端控制台输出如下:
解密后的明文为:
Hello World
2、后端加密,前端解密
我们先在Java后端对明文进行AES加密。
/**
* @author Nick Liu
* @date 2023/4/23
*/
public class AesDemo {
public static void main(String[] args) throws Exception {
String secretKey = "sQPoC/1do9BZMkg8I5c09A==";
String plainText = "Hello World";
System.out.println("加密后的密文为:" + CryptoUtils.encryptSymmetrically(secretKey, null, plainText, Encryption.AES_ECB_PKCS5));
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
控制台输出如下:
加密后的密文为:
38guooCNqRJaxvL8vh+kLg==
然后在前端对密文进行AES解密。
const secretKey = 'sQPoC/1do9BZMkg8I5c09A==';
const cipherText = '38guooCNqRJaxvL8vh+kLg==';
const plainText = decryptByAES(cipherText, secretKey);
console.log(`解密后的内容为:${plainText}`);
- 1
- 2
- 3
- 4
控制台输出如下:
解密后的内容为:
Hello World