- 1vue 调用后端接口导出excel无效果,直接访问后端url可以_vue3单独用网址可以调取 但是用接口的形式就无法下载
- 2Spock单元测试框架简介及实践
- 3详解MySQL执行计划分析
- 4自然语言处理课程论文:《Attention is all you need》复现与解读
- 5新手入门:大语言模型训练指南_大语言模型 专业词汇训练
- 6react 封装API_react封装请求api接口
- 7Vision Transformer (ViT)初识:原理详解及代码_vit代码详解
- 8k8s安装elasticsearch
- 9大模型 GLM-4-9B 开源,模型表现超越!!!_glm-4v-9b embedding 接口
- 10Flink 实践教程-进阶(9):自定义表值函数(UDTF)_flink udtf
华为ensp园区网防火墙双机热备_ensp中大型园区配置
赞
踩
一、实验简介
企业有线网络需实现不同功能和要求。
利用acl+traffic-filter、端口隔离、防火墙实现不同用户的联网需求;通过vvrp+dhcp、easy-ip、bfd+ospf、链路聚合、mstp、流量抑制、mstp生成树等技术实现网络整体的稳定性和安全性。
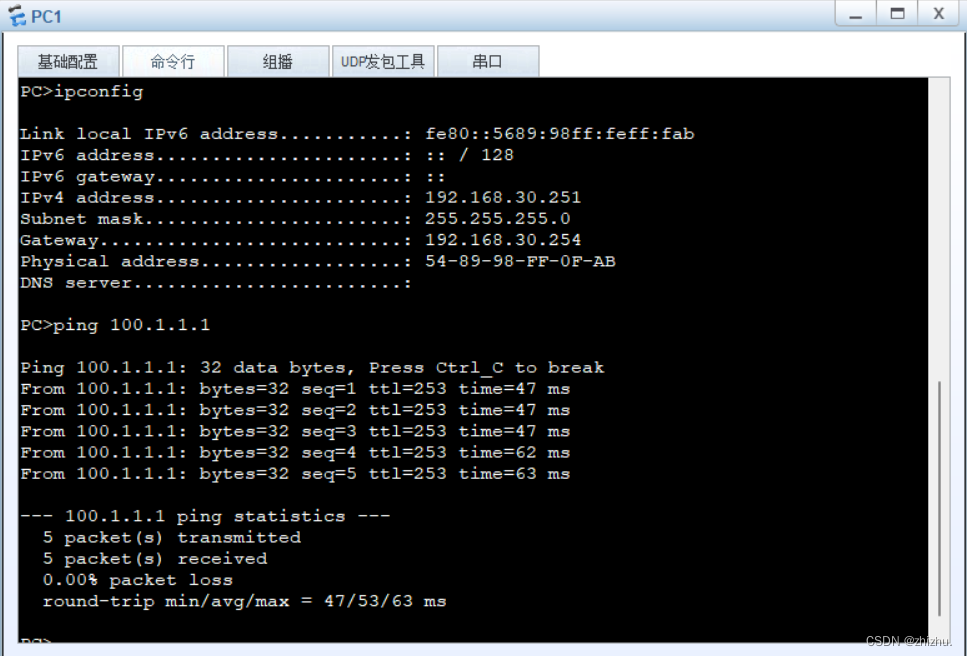
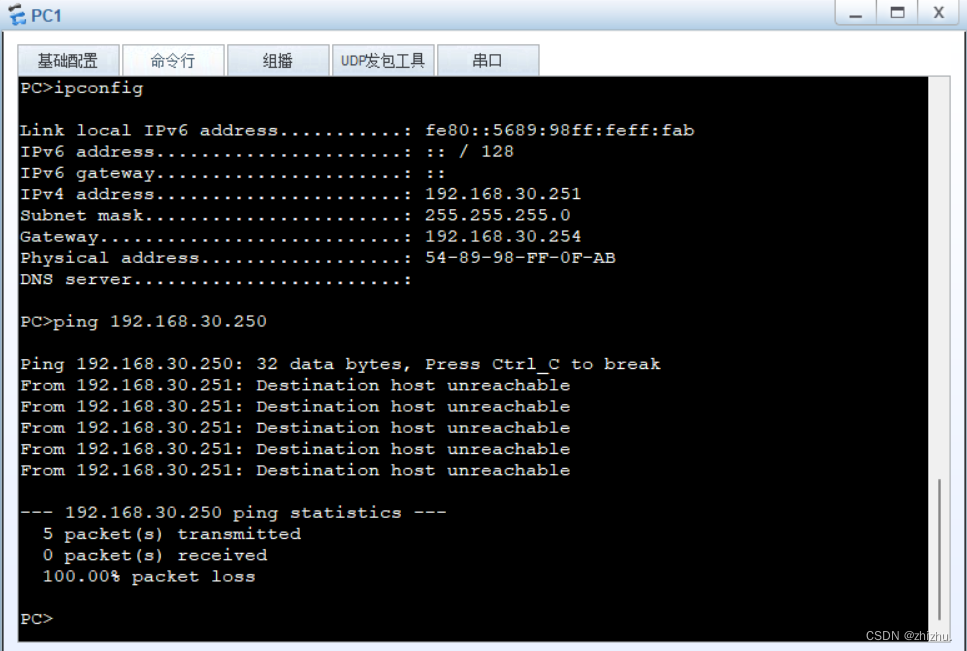
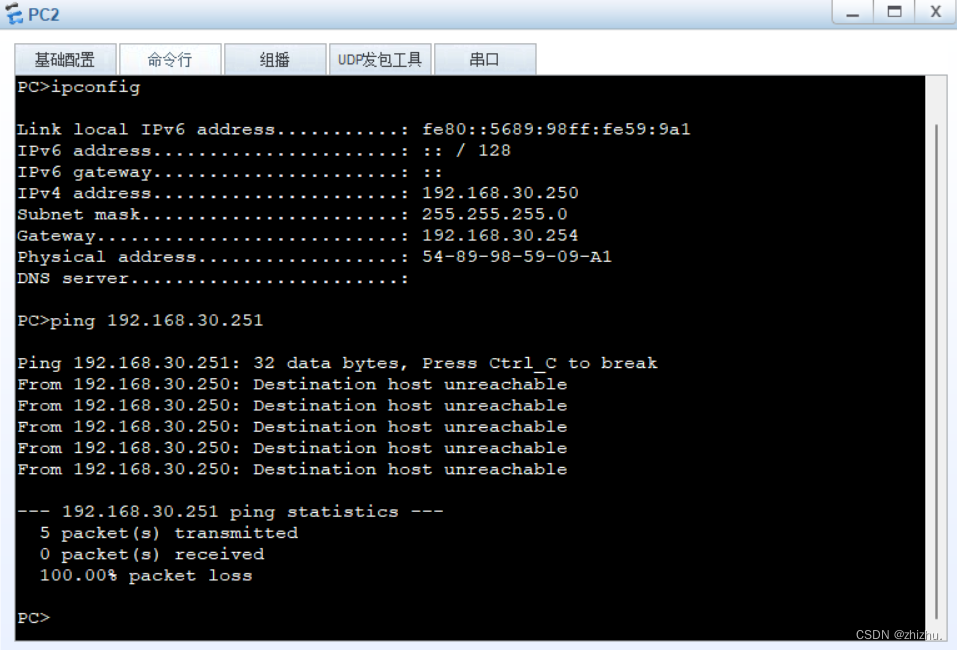
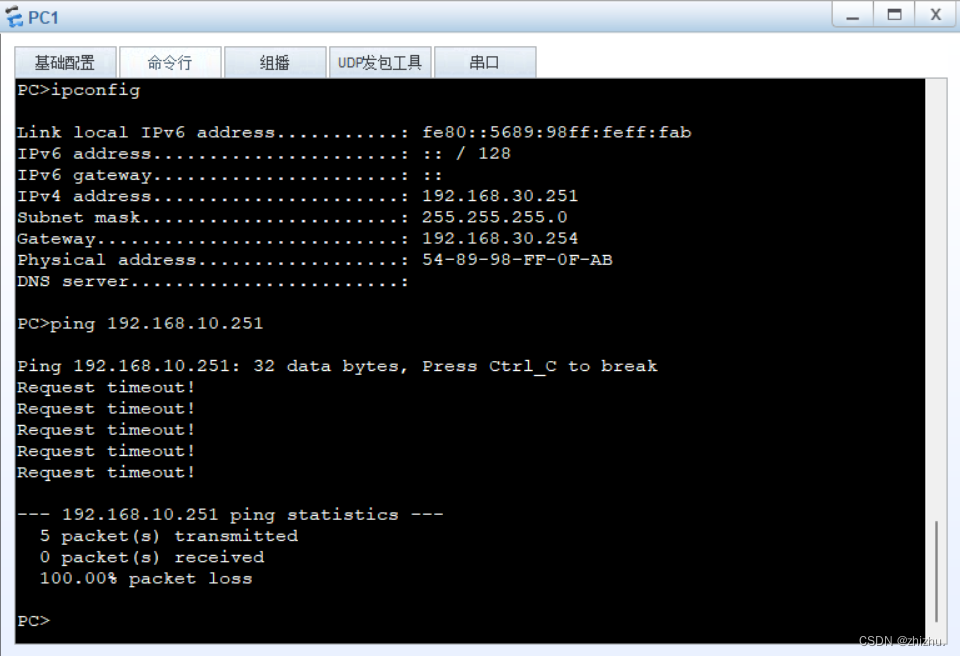
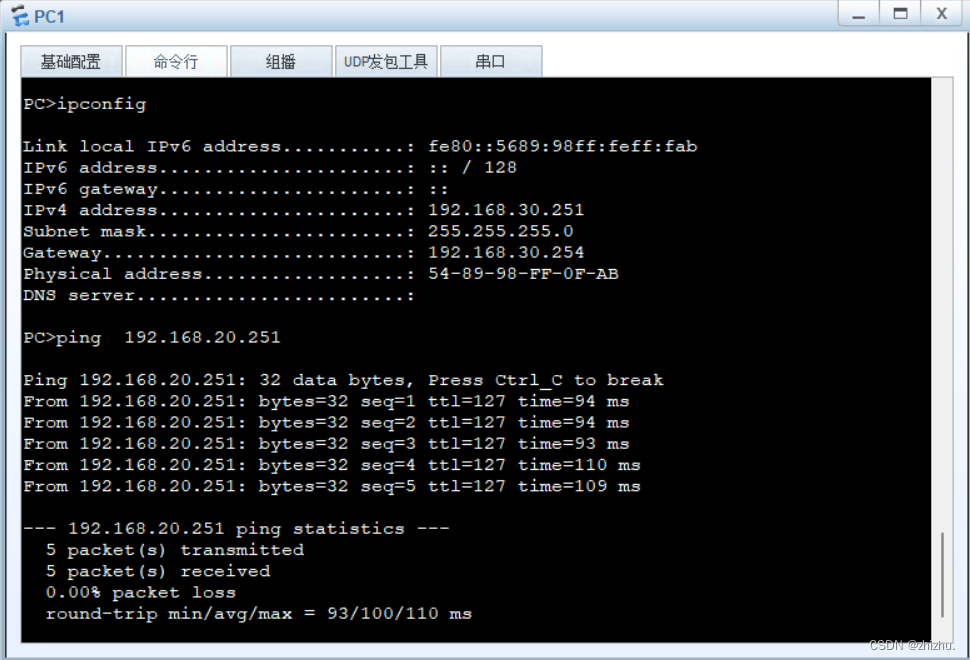
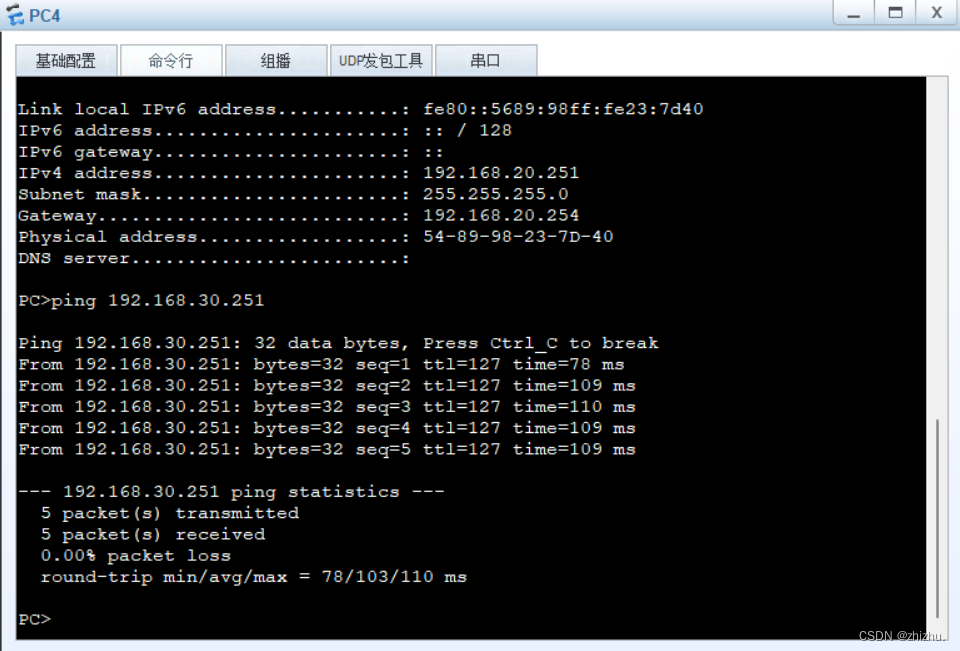
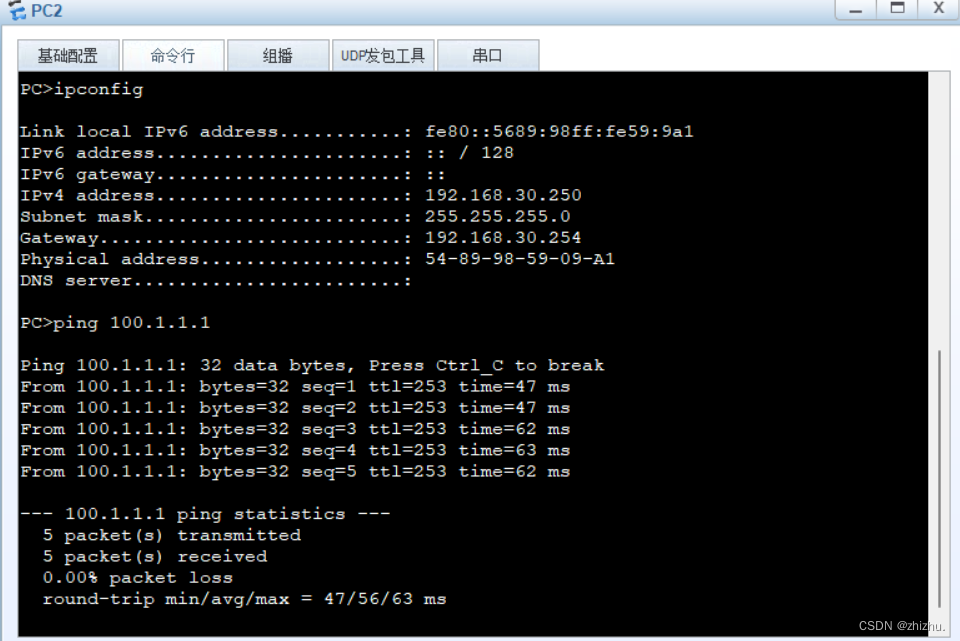
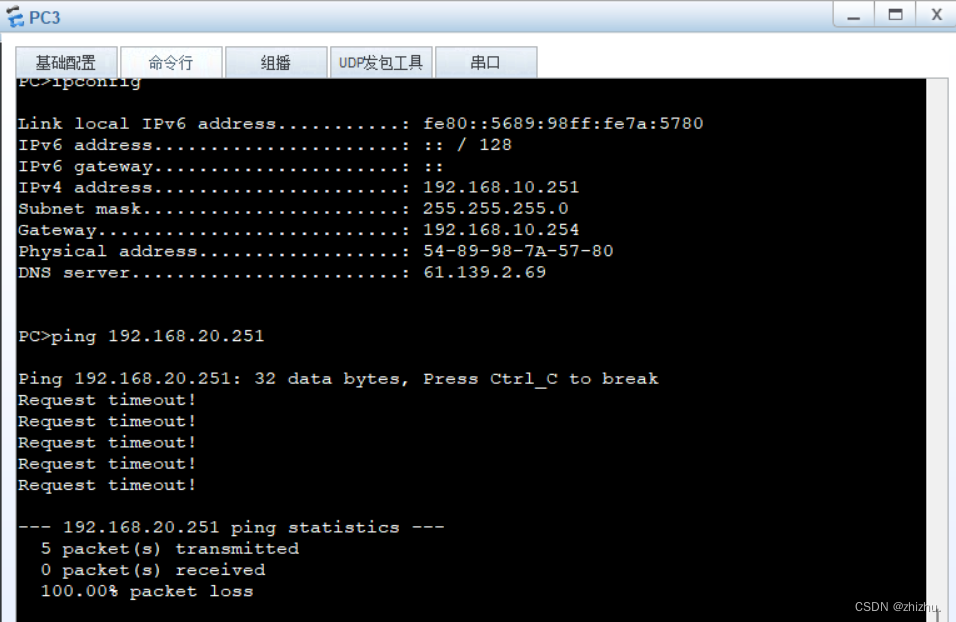
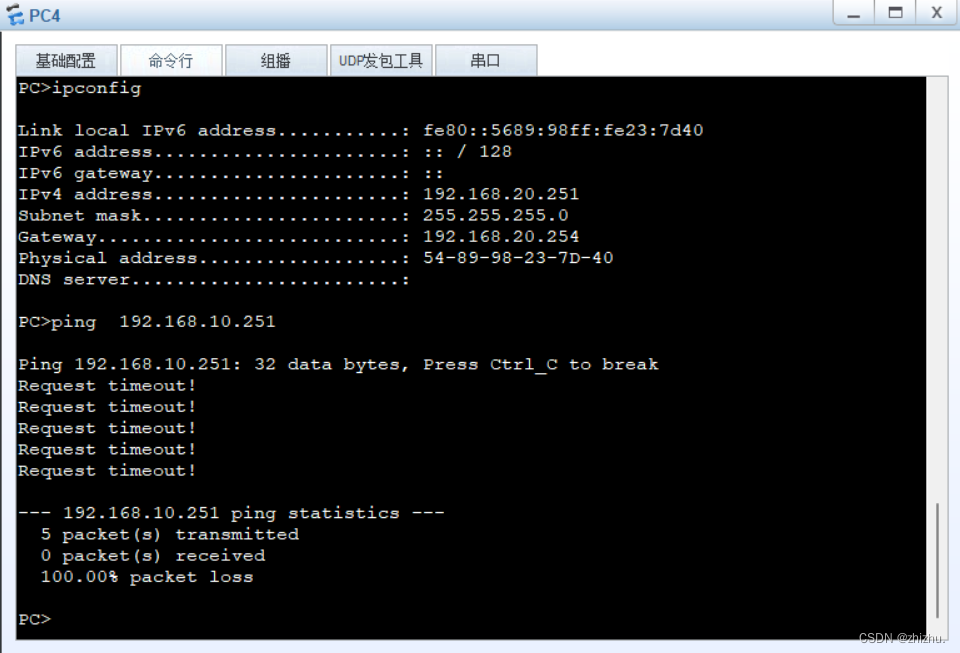
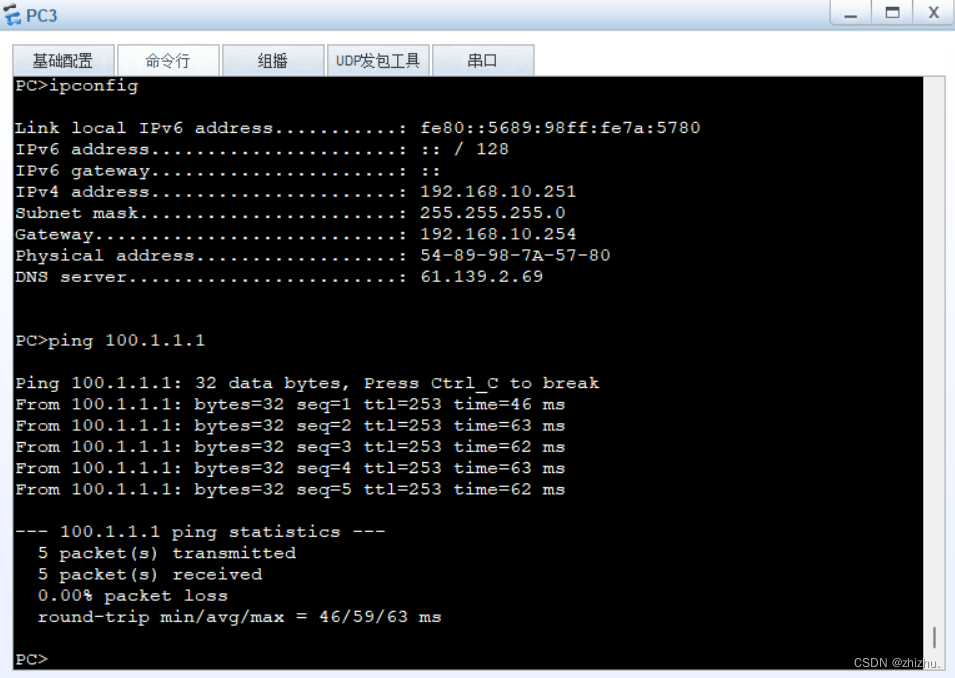
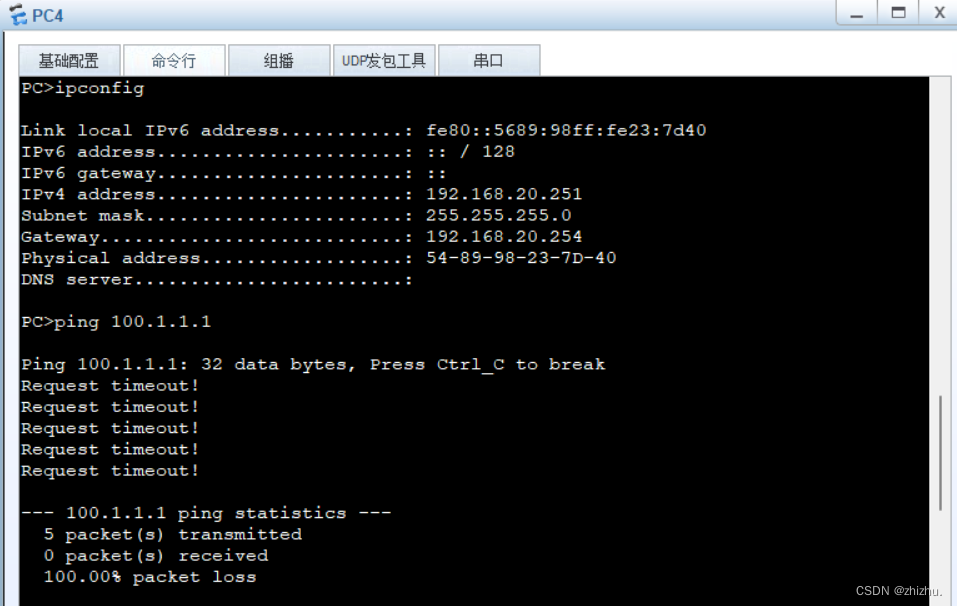
组网需求:PC1与PC2在同一网段,PC3与PC4不在同一网段;PC1不能与PC2、PC3互相通信;PC2不能与PC1、PC3通信;PC3不能与PC1、PC2、PC4通信;PC4能与PC1、PC2通信;PC1和PC2、PC3可以访问公网;PC4不可以访问公网。
二、实验拓扑
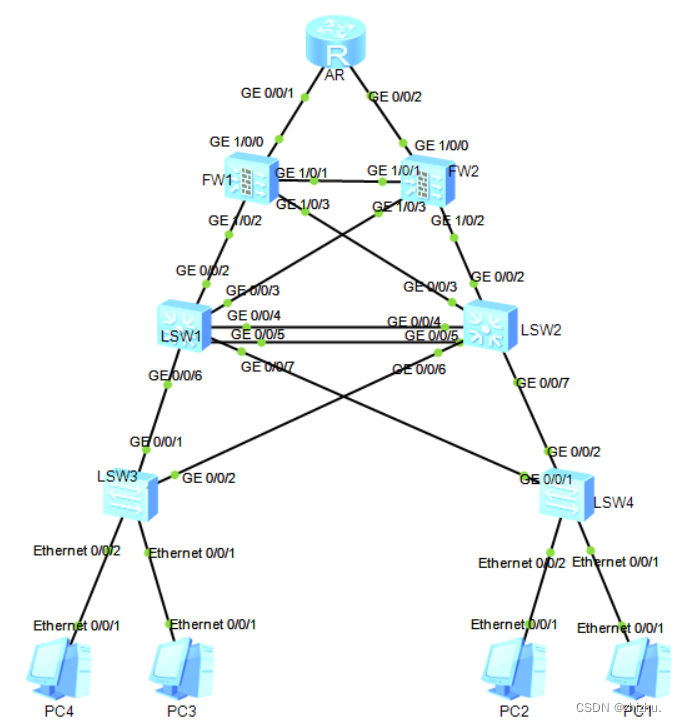
三、网段划分
假设电信运营商给企业划分的公网IPv4地址为100.10.10.0 29网段。
1、AR
| 接口 | IP地址 |
| 模拟公网路由loop back0 | 100.1.1.1 32 |
| Eth-trunk 5:G0/0/1、G0/0/2 | 100.10.10.3 29 |
2、FW1
| 接口 | IP地址 |
| G1/0/0 | 100.10.10.1 29 |
| 心跳线:G1/0/1 | 10.10.10.1 30 |
| G1/0/2 | 10.10.121.2 29 |
| G1/0/3 | 10.10.122.2 29 |
3、FW2
| 接口 | IP地址 |
| G1/0/0 | 100.10.10.2 29 |
| 心跳线:G1/0/1 | 10.10.10.2 30 |
| G1/0/2 | 10.10.121.3 29 |
| G1/0/3 | 10.10.122.3 29 |
4、SW1
| 接口 | IP地址 |
| VLAN 121:G0/0/2、G0/0/3 | 10.10.121.1 29 |
| vlan 10 | 192.168.10.253 24 |
| vlan 20 | 192.168.20.253 24 |
| vlan 30 | 192.168.30.252 24 |
5、SW2
| 接口 | IP地址 |
| VLAN 122:G0/0/2、G0/0/3 | 10.10.122.1 29 |
| vlan 10 | 192.168.10.252 24 |
| vlan 20 | 192.168.20.252 24 |
| vlan 30 | 192.168.30.253 24 |
四、具体配置:
1、FW1
interface GigabitEthernet1/0/0
ip address 100.10.10.1 255.255.255.248
service-manage all permit (放通所有协议)
interface GigabitEthernet1/0/1
ip address 10.10.10.1 255.255.255.252
service-manage all permit
interface GigabitEthernet1/0/2
ip address 10.10.121.2 255.255.255.248
service-manage all permit
interface GigabitEthernet1/0/3
ip address 10.10.122.2 255.255.255.248
service-manage all permit
firewall zone trust(进入信任区域)
add interface GigabitEthernet1/0/1(添加接口)
add interface GigabitEthernet1/0/2
add interface GigabitEthernet1/0/3
firewall zone untrust(进入非信任区域)
add interface GigabitEthernet1/0/0
security-policy(配置安全策略)
rule name SW
source-zone trust(设置数据的源为信任区域)
destination-zone untrust(设置数据的出方向为非信任区域)
source-address 192.168.10.0 0.0.0.255(设置数据的源网段)
source-address 192.168.30.0 0.0.0.255
action permit(允许通过)
nat-policy(配置nat策略)
rule name NATSW
source-zone trust
destination-zone untrust
source-address 192.168.10.0 0.0.0.255
source-address 192.168.30.0 0.0.0.255
action source-nat easy-ip(设置地址转换使用easy-ip)
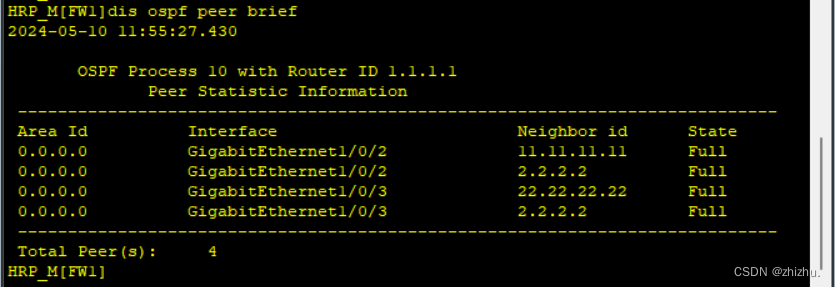
ospf 10 router-id 1.1.1.1
area 0.0.0.0
authentication-mode hmac-md5 10 cipher ospfarea0QYRZ(配置ospf区域认证)
network 10.10.121.0 0.0.0.7
network 10.10.122.0 0.0.0.7
ip route-static 0.0.0.0 0.0.0.0 100.10.10.3(配置静态默认路由,下一跳地址为对端AR路由器接口地址)
bfd(全局使能BFD)
ospf 10 router-id 1.1.1.1
default-route-advertise(允许引入静态默认路由)
import-route static(引入静态路由)
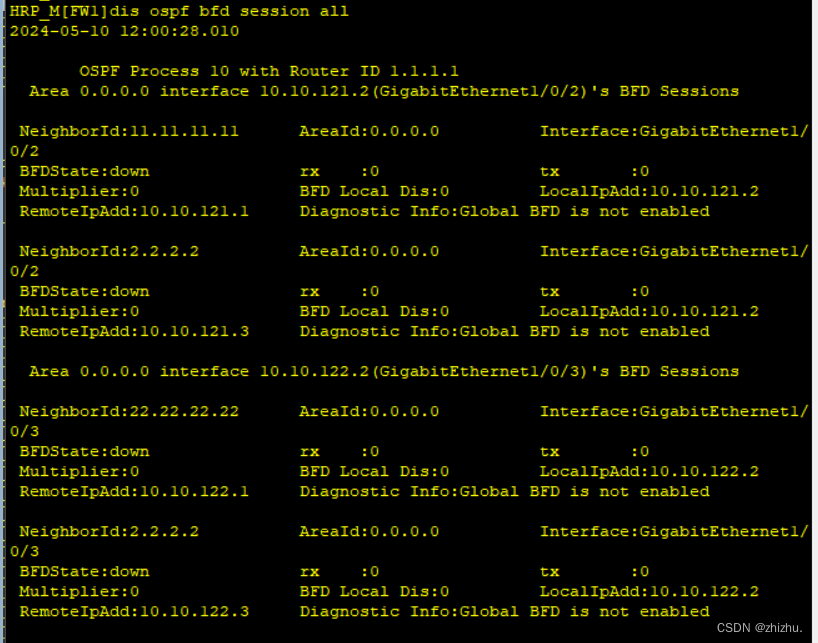
bfd all-interfaces enable(使能BFD与ospf联动)
bfd all-interfaces min-tx-interval 100 min-rx-interval 100(指定BFD报文的发送最小间隔和接收最小间隔)
防火墙双机热备配置命令
interface GigabitEthernet1/0/0
vrrp vrid 3 virtual-ip 100.10.10.6 active(设置该虚拟网关地址,并且该接口为主接口)
interface GigabitEthernet1/0/2
vrrp vrid 1 virtual-ip 10.10.121.6 active
interface GigabitEthernet1/0/3
vrrp vrid 2 virtual-ip 10.10.122.6 active
hrp enable(启动双机热备)
hrp interface GigabitEthernet1/0/1 remote 10.10.10.2(设置双机热备的接口和对端IP地址)
2、FW2
interface GigabitEthernet1/0/0
ip address 100.10.10.2 255.255.255.248
service-manage all permit (放通所有协议)
interface GigabitEthernet1/0/1
ip address 10.10.10.2 255.255.255.252
service-manage all permit
interface GigabitEthernet1/0/2
ip address 10.10.122.3 255.255.255.248
service-manage all permit
interface GigabitEthernet1/0/3
ip address 10.10.121.3 255.255.255.248
service-manage all permit
firewall zone trust(进入信任区域)
add interface GigabitEthernet1/0/1(添加接口)
add interface GigabitEthernet1/0/2
add interface GigabitEthernet1/0/3
firewall zone untrust(进入非信任区域)
add interface GigabitEthernet1/0/0
security-policy(配置安全策略)
rule name SW
source-zone trust(设置数据的源为信任区域)
destination-zone untrust(设置数据的出方向为非信任区域)
source-address 192.168.10.0 0.0.0.255(设置数据的源网段)
source-address 192.168.30.0 0.0.0.255
action permit(允许通过)
nat-policy(配置nat策略)
rule name NATSW
source-zone trust
destination-zone untrust
source-address 192.168.10.0 0.0.0.255
source-address 192.168.30.0 0.0.0.255
action source-nat easy-ip(设置地址转换使用easy-ip)
ospf 10 router-id 2.2.2.2
area 0.0.0.0
authentication-mode hmac-md5 10 cipher ospfarea0QYRZ(配置ospf区域认证)
network 10.10.121.0 0.0.0.7
network 10.10.122.0 0.0.0.7
ip route-static 0.0.0.0 0.0.0.0 100.10.10.3(配置静态默认路由,下一跳地址为对端AR路由器接口地址)
bfd(全局使能BFD)
ospf 10 router-id 2.2.2.2
default-route-advertise(允许引入静态默认路由)
import-route static(引入静态路由)
bfd all-interfaces enable(使能BFD与ospf联动)
bfd all-interfaces min-tx-interval 100 min-rx-interval 100(指定BFD报文的发送最小间隔和接收最小间隔)
防火墙双机热备配置命令
interface GigabitEthernet1/0/0
vrrp vrid 3 virtual-ip 100.10.10.6 standby(设置该虚拟网关地址,并且该接口为备用接口)
interface GigabitEthernet1/0/2
vrrp vrid 1 virtual-ip 10.10.122.6 standby
interface GigabitEthernet1/0/3
vrrp vrid 2 virtual-ip 10.10.121.6 standby
hrp enable(启动双机热备)
hrp interface GigabitEthernet1/0/1 remote 10.10.10.1(设置双机热备的接口和对端IP地址)
3、LSW1
vlan batch 10 20 30 121(创建vlan)
interface Eth-Trunk10
port link-type trunk(设置接口为trunk类型)
port trunk allow-pass vlan 10 20 30 45(允许携带这些vlan标签的数据通过)
interface GigabitEthernet0/0/2
port link-type access(设置接口为access类型)
port default vlan 121(给数据打上或剥离此vlan标签)
interface GigabitEthernet0/0/3
port link-type access
port default vlan 121
interface GigabitEthernet0/0/4
eth-trunk 10
interface GigabitEthernet0/0/5
eth-trunk 10
interface GigabitEthernet0/0/6
port link-type trunk
port trunk allow-pass vlan 10 20
interface GigabitEthernet0/0/7
port link-type trunk
port trunk allow-pass vlan 30
interface Vlanif10
ip address 192.168.10.253 255.255.255.0
interface Vlanif20
ip address 192.168.20.253 255.255.255.0
interface Vlanif30
ip address 192.168.30.252 255.255.255.0
interface Vlanif121
ip address 10.10.121.1 255.255.255.248
bfd
ospf 10 router-id 11.11.11.11
bfd all-interfaces enable
bfd all-interfaces min-tx-interval 100 min-rx-interval 100
import-route direct
area 0.0.0.0
authentication-mode hmac-md5 10 cipher ospfarea0QYRZ
network 10.10.121.0 0.0.0.7
配置流量抑制
interface GigabitEthernet0/0/6
unicast-suppression 60(设置允许通过的最大未知单播报文为60%)
multicast-suppression 50(设置允许通过的最大组播报文为50%)
broadcast-suppression 40(设置允许通过的最大广播报文为40%)
interface GigabitEthernet0/0/7
unicast-suppression 60
multicast-suppression 50
broadcast-suppression 40
配置MSTP生成树
stp region-configuration(进入stp视图)
region-name mstp(设置stp的模式为mstp)
instance 1 vlan 10 20 (设置mstp实例)
instance 2 vlan 30 45
active region-configuration
stp instance 1 root primary (设置该交换机为实例1的主根)
stp instance 2 root secondary(设置该交换机为实例2的备根)
interface GigabitEthernet0/0/2
stp edged-port enable(设置该接口为边缘接口)
interface GigabitEthernet0/0/3
stp edged-port enable
配置dhcp服务器
dhcp enable(全局使能dhcp)
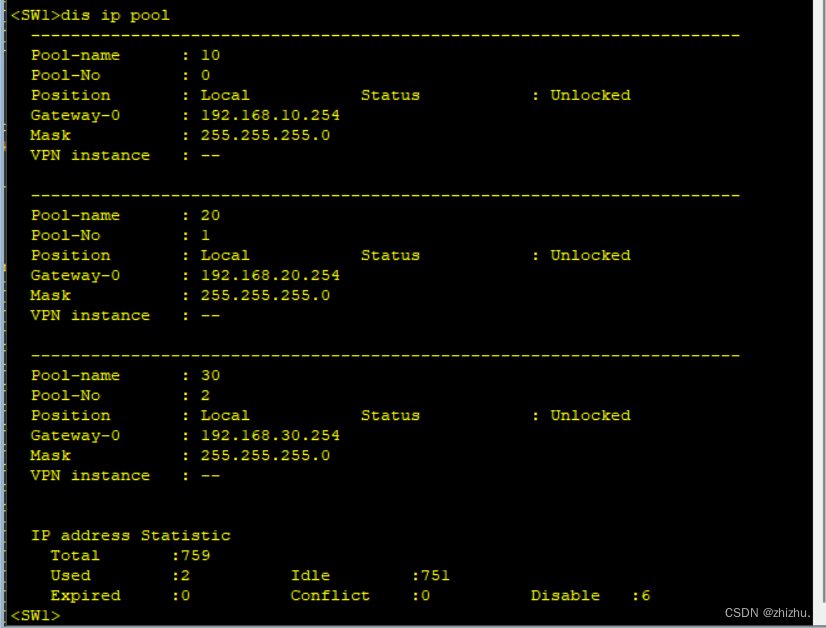
ip pool 10(创建dhcp地址池10)
gateway-list 192.168.10.254 (设置网关地址)
network 192.168.10.0 mask 255.255.255.0 (设置地址池网段)
excluded-ip-address 192.168.10.252 192.168.10.253 (设置排除地址池中的地址)
dns-list 61.139.2.69 (设置dns服务器地址)
ip pool 20
gateway-list 192.168.20.254
network 192.168.20.0 mask 255.255.255.0
excluded-ip-address 192.168.20.252 192.168.20.253
ip pool 30
gateway-list 192.168.30.254
network 192.168.30.0 mask 255.255.255.0
excluded-ip-address 192.168.30.252 192.168.30.253
配置vrrp与dhcp联动
interface Vlanif10
dhcp select global(启用dhcp全局地址池)
vrrp vrid 10 virtual-ip 192.168.10.254(设置虚拟网关地址)
vrrp vrid 10 priority 120(设置该虚拟网关的优先级为120)
interface Vlanif20
dhcp select global
vrrp vrid 20 virtual-ip 192.168.20.254
vrrp vrid 20 priority 120
interface Vlanif30
dhcp select global
vrrp vrid 30 virtual-ip 192.168.30.254
配置acl+ traffic-filter
acl number 3000 (创建acl 3000)
rule 5 deny ip source 192.168.30.0 0.0.0.255 destination 192.168.10.0 0.0.0.255 (拒绝源地址为192.168.30.0 24网段,目的地为192.168.10.0 24网段地址的数据通信)
rule 10 permit ip (允许所有网段互访)
acl number 3001
rule 5 deny ip source 192.168.10.0 0.0.0.255 destination 192.168.30.0 0.0.0.255
rule 10 deny ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
rule 15 deny ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
rule 20 permit ip
interface GigabitEthernet0/0/6
traffic-filter inbound acl 3001(在接口的入方向启用 traffic-filter并调用acl 3001)
interface GigabitEthernet0/0/7
traffic-filter inbound acl 3000
4、LSW2
vlan batch 10 20 30 122(创建vlan)
interface Eth-Trunk10
port link-type trunk(设置接口为trunk类型)
port trunk allow-pass vlan 10 20 30 45(允许携带这些vlan标签的数据通过)
interface GigabitEthernet0/0/2
port link-type access(设置接口为access类型)
port default vlan 122(给数据打上或剥离此vlan标签)
interface GigabitEthernet0/0/3
port link-type access
port default vlan 122
interface GigabitEthernet0/0/4
eth-trunk 10
interface GigabitEthernet0/0/5
eth-trunk 10
interface GigabitEthernet0/0/6
port link-type trunk
port trunk allow-pass vlan 10 20
interface GigabitEthernet0/0/7
port link-type trunk
port trunk allow-pass vlan 30
interface Vlanif10
ip address 192.168.10.252 255.255.255.0
interface Vlanif20
ip address 192.168.20.252 255.255.255.0
interface Vlanif30
ip address 192.168.30.253 255.255.255.0
interface Vlanif122
ip address 10.10.122.1 255.255.255.248
bfd
ospf 10 router-id 22.22.22.22
bfd all-interfaces enable
bfd all-interfaces min-tx-interval 100 min-rx-interval 100
import-route direct
area 0.0.0.0
authentication-mode hmac-md5 10 cipher ospfarea0QYRZ
network 10.10.122.0 0.0.0.7
配置流量抑制
interface GigabitEthernet0/0/6
unicast-suppression 60(设置允许通过的最大未知单播报文为60%)
multicast-suppression 50(设置允许通过的最大组播报文为50%)
broadcast-suppression 40(设置允许通过的最大广播报文为40%)
interface GigabitEthernet0/0/7
unicast-suppression 60
multicast-suppression 50
broadcast-suppression 40
配置MSTP生成树
stp region-configuration(进入stp视图)
region-name mstp(设置stp的模式为mstp)
instance 1 vlan 10 20 (设置mstp实例)
instance 2 vlan 30 45
active region-configuration
stp instance 1 root secondary(设置该交换机为实例1的备根)
stp instance 2 root primary(设置该交换机为实例2的主根)
interface GigabitEthernet0/0/2
stp edged-port enable(设置该接口为边缘接口)
interface GigabitEthernet0/0/3
stp edged-port enable
配置dhcp服务器
dhcp enable(全局使能dhcp)
ip pool 10(创建dhcp地址池10)
gateway-list 192.168.10.254 (设置网关地址)
network 192.168.10.0 mask 255.255.255.0 (设置地址池网段)
excluded-ip-address 192.168.10.252 192.168.10.253 (设置排除地址池中的地址)
dns-list 61.139.2.69 (设置dns服务器地址)
ip pool 20
gateway-list 192.168.20.254
network 192.168.20.0 mask 255.255.255.0
excluded-ip-address 192.168.20.252 192.168.20.253
ip pool 30
gateway-list 192.168.30.254
network 192.168.30.0 mask 255.255.255.0
excluded-ip-address 192.168.30.252 192.168.30.253
配置vrrp与dhcp联动
interface Vlanif10
dhcp select global(启用dhcp全局地址池)
vrrp vrid 10 virtual-ip 192.168.10.254(设置虚拟网关地址)
interface Vlanif20
dhcp select global
vrrp vrid 20 virtual-ip 192.168.20.254
interface Vlanif30
dhcp select global
vrrp vrid 30 virtual-ip 192.168.30.254
vrrp vrid 30 priority 120
配置acl+ traffic-filter
acl number 3000 (创建acl 3000)
rule 5 deny ip source 192.168.30.0 0.0.0.255 destination 192.168.10.0 0.0.0.255(拒绝源地址为192.168.30.0 24网段,目的地为192.168.10.0 24网段地址的数据通信)
rule 10 permit ip (允许所有网段互访)
acl number 3001
rule 5 deny ip source 192.168.10.0 0.0.0.255 destination 192.168.30.0 0.0.0.255
rule 10 deny ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
rule 15 deny ip source 192.168.20.0 0.0.0.255 destination 192.168.10.0 0.0.0.255
rule 20 permit ip
interface GigabitEthernet0/0/6
traffic-filter inbound acl 3001(在接口的入方向启用 traffic-filter并调用acl 3001)
interface GigabitEthernet0/0/7
traffic-filter inbound acl 3000
5、LSW3
vlan batch 5 10 20
stp region-configuration
region-name mstp
instance 1 vlan 10 20
instance 2 vlan 30 45
active region-configuration
interface Ethernet0/0/1
port link-type access
port default vlan 10
stp edged-port enable
interface Ethernet0/0/2
port link-type access
port default vlan 20
stp edged-port enable
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 10 20
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 10 20
静态MAC绑定
mac-address static 5489-9823-7d40 Ethernet0/0/2 vlan 20(将mac地址与接口、vlan进行绑定)
mac-address static 5489-987a-5780 Ethernet0/0/1 vlan 10
6、LSW4
vlan batch 30
stp region-configuration
region-name mstp
instance 1 vlan 10 20
instance 2 vlan 30 45
active region-configuration
interface Ethernet0/0/1
port link-type access
port default vlan 30
stp edged-port enable
interface Ethernet0/0/2
port link-type access
port default vlan 30
stp edged-port enable
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 30
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 30
设置端口三层隔离
interface Ethernet0/0/1
am isolate Ethernet0/0/2 (绑定对端相互隔离的端口)
port-isolate enable group 10(绑定到隔离组10中)
静态MAC绑定
mac-address static 5489-98ff-0fab Ethernet0/0/1 vlan 30(将mac地址与接口、vlan进行绑定)
mac-address static 5489-9859-09a1 Ethernet0/0/2 vlan 30
五、验证
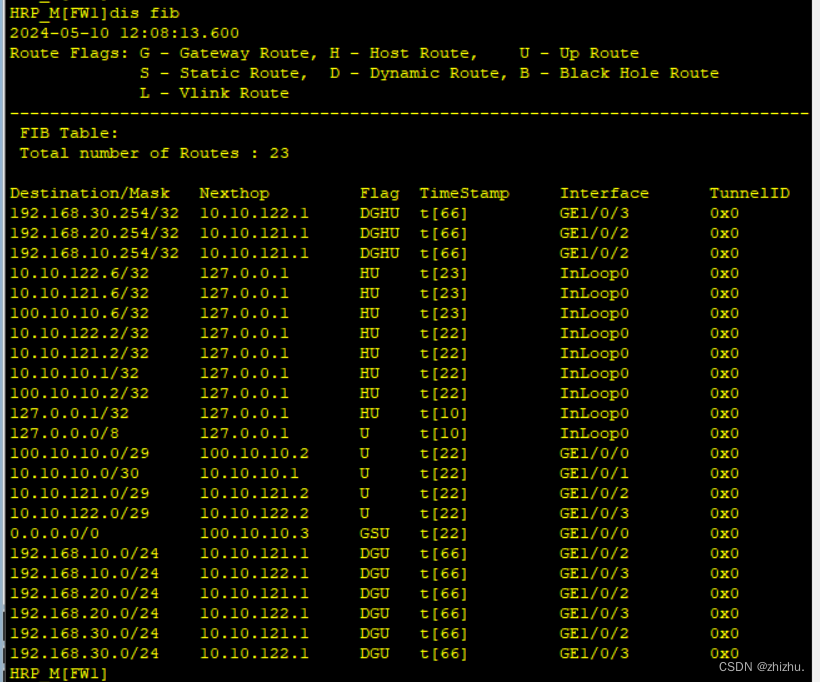
1、设备表项验证
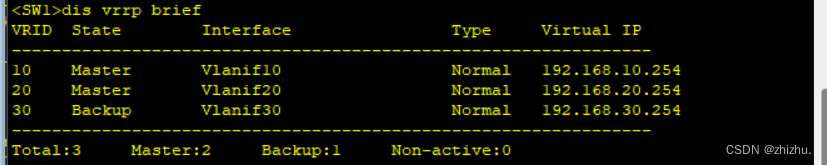

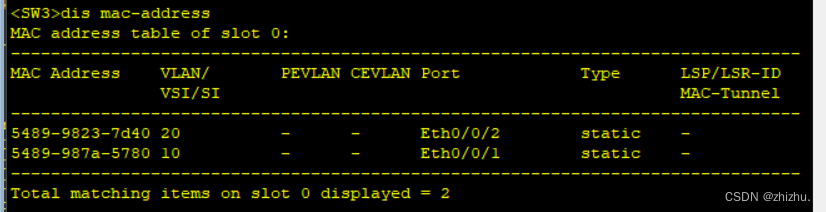
2、PC连通性验证